A Visitor Assistance System Based on LoRa for Nature Forest Parks
Abstract
1. Introduction
- The proposal of a specific medium access control protocol for the LoRa network, which connects user terminals to totems and among themselves. A lightweight variation of CSMA (Carrier-Sense Multiple Access) is implemented using the different spreading factors of the LoRa PHY layer;
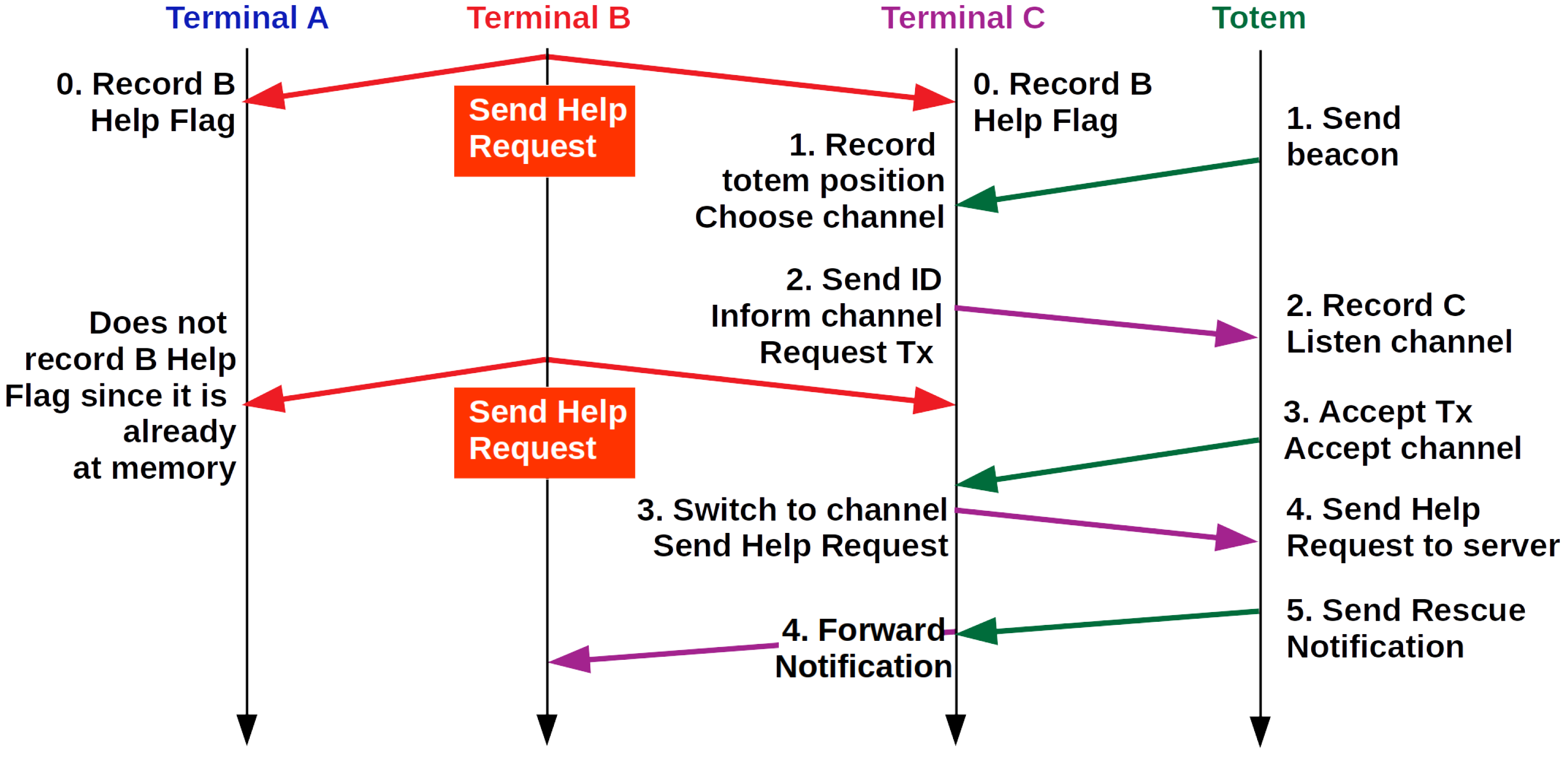
- A protocol for the collaborative localization of visitors inside the park, which builds upon the one proposed in the CenWits project [7]. The proposed protocol includes visitor’s active requests for rescue and dynamic group creation. Groups allow to optimize terminal memory and battery utilization, as well as reducing the load offered to the network.
2. Contribution
3. Related Work
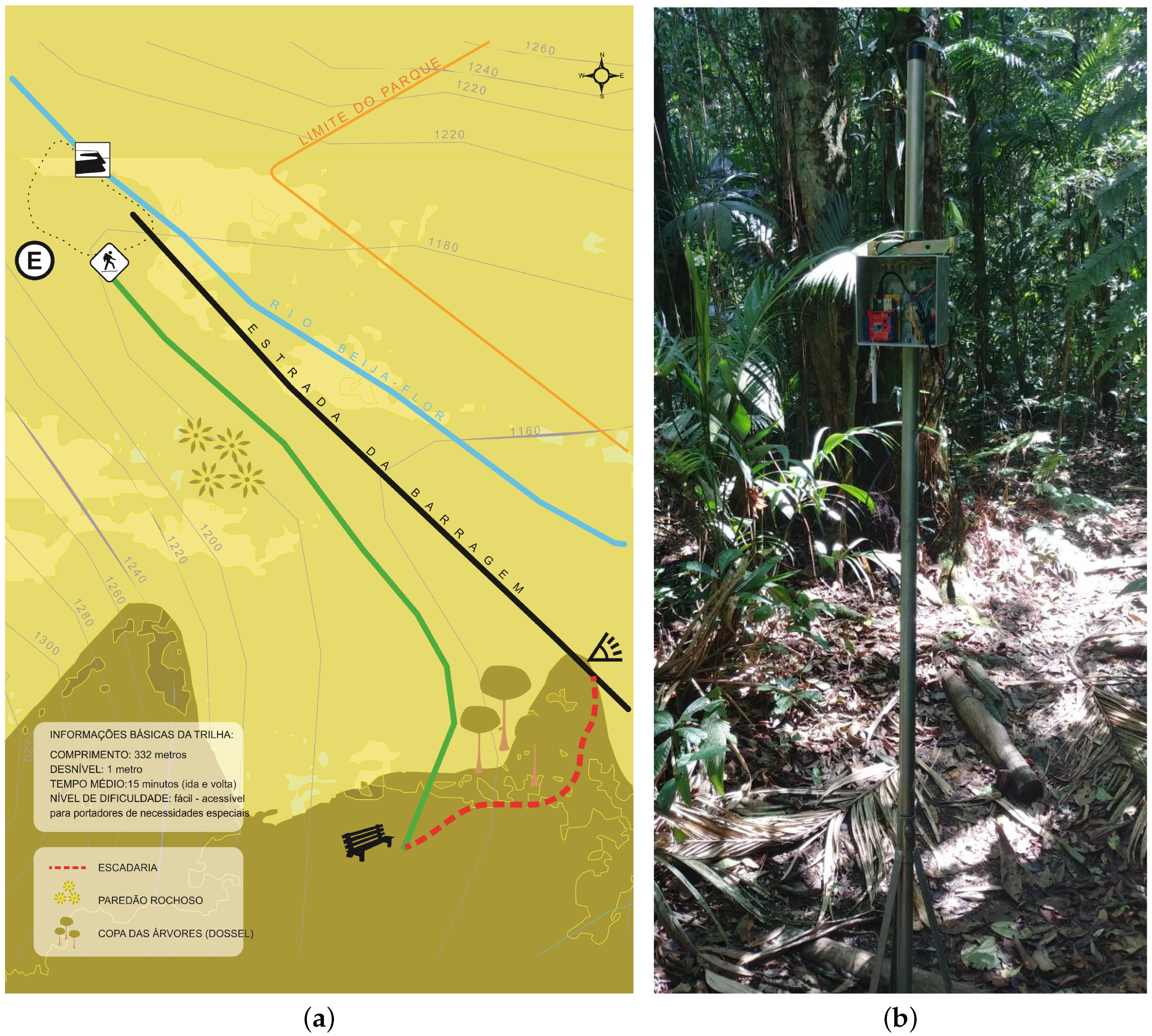
4. Environment
5. The Proposed Visitor Assistance System
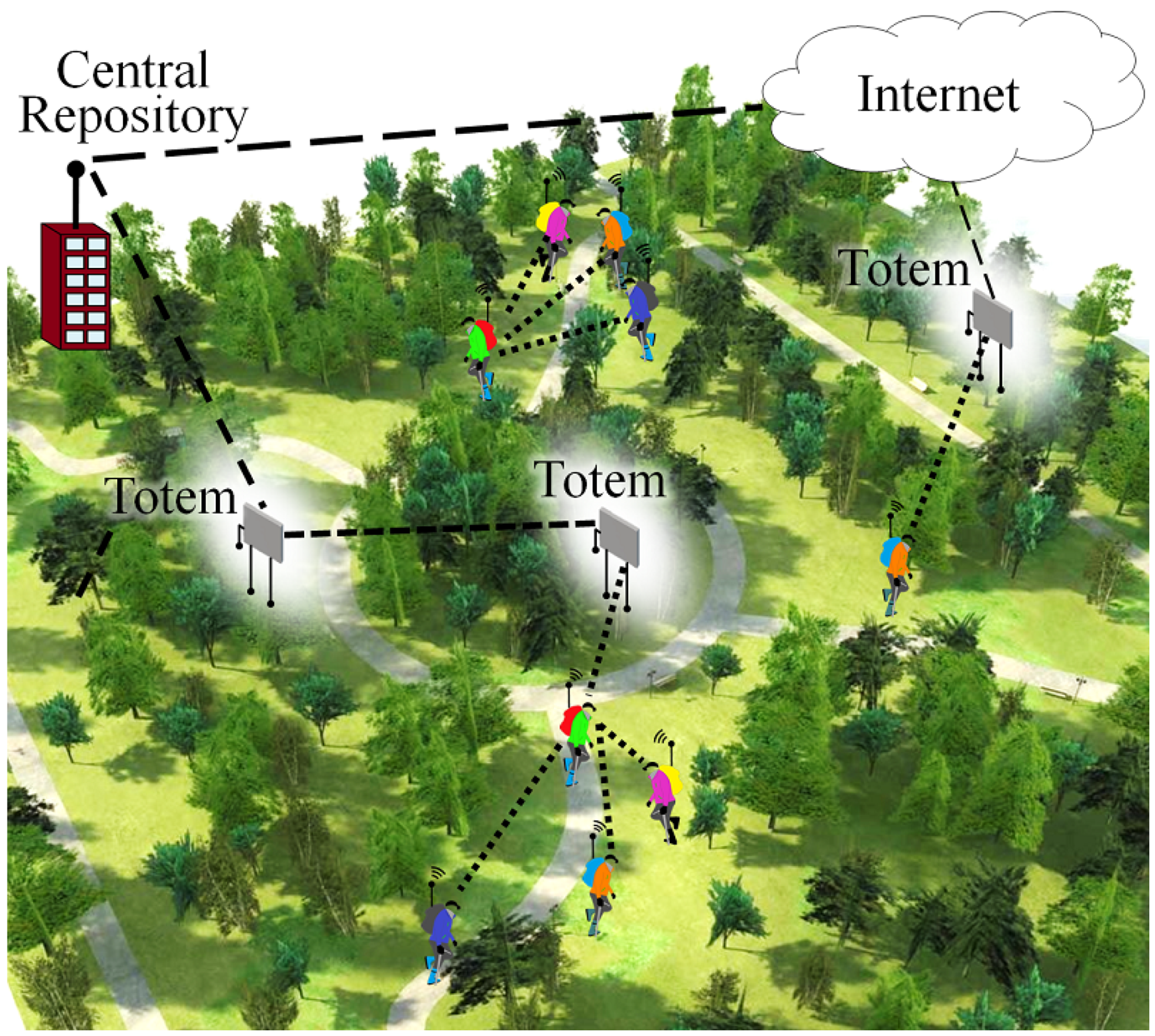
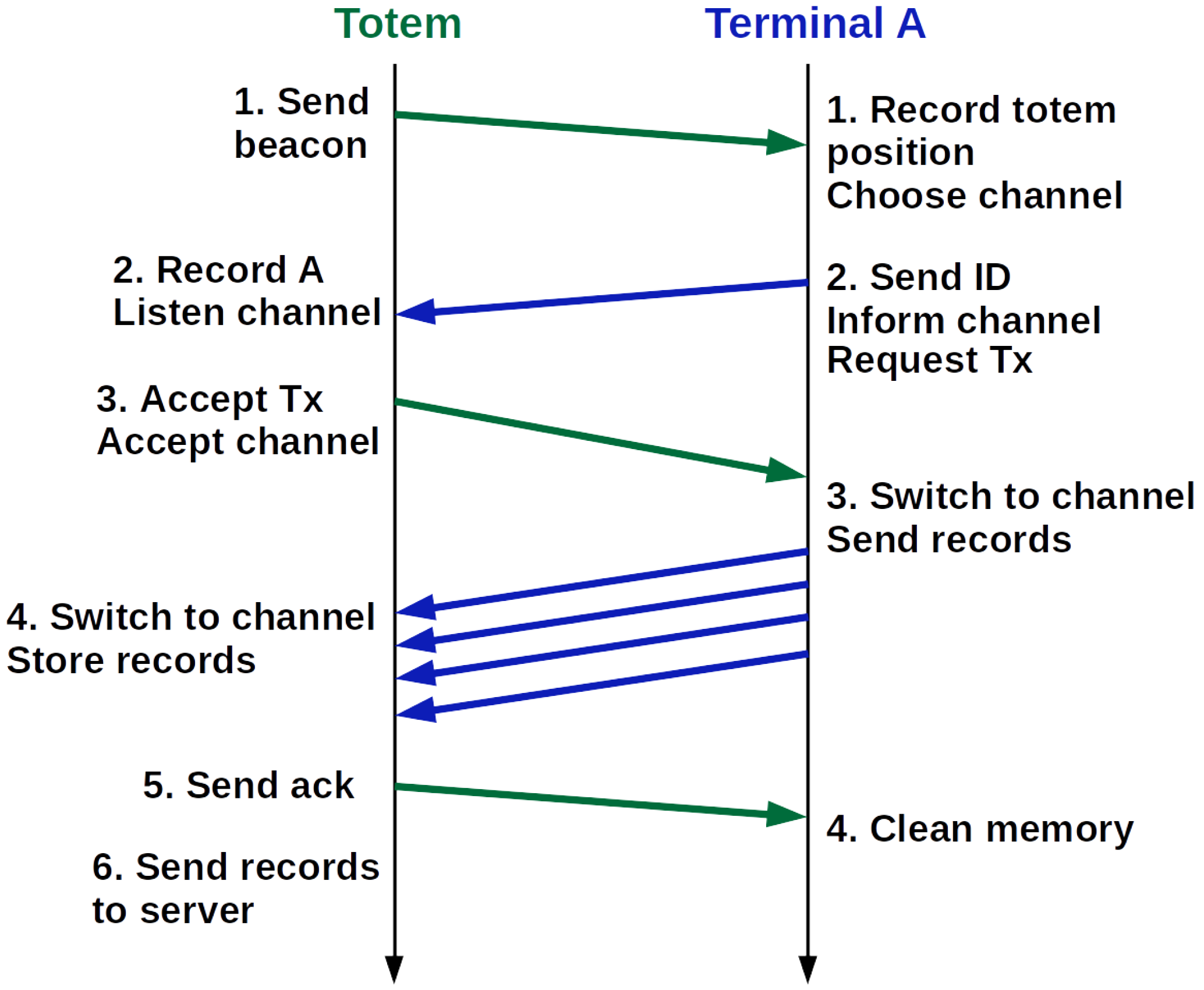
5.1. Infrastructure
5.2. Protocol and Application
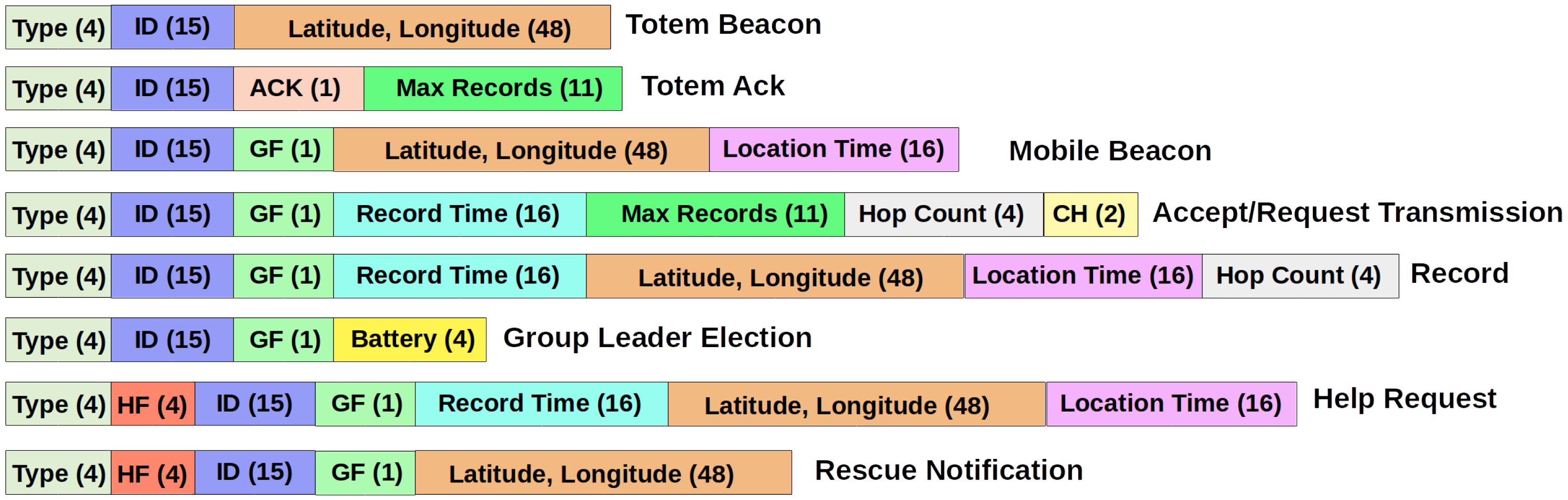
- Type (4 bits)—indicates the message type. Currently, eight messages are defined, leaving space for future extensions. The defined types are:
- help request—actively sent by the user at risk, requesting help, without the need to wait for processing other visitors’ records;
- rescue notification—reports that there is a rescue team on the way, send by paramedics at the park headquarters;
- totem beacon—announces the presence of a totem and its coordinates as a reference for the visitor;
- totem ack—confirms receipt of records sent by the terminal;
- terminal beacon—announces the presence of a mobile terminal, its most recent coordinates, obtained via GPS or received from a totem, and a timestamp associated to this last known position;
- request/acceptance of records transmission—used during the initial handshake, to request/accept the transmission of records, as well as to inform the parameters to be used in the transmission and avoid transmitting unwanted records;
- record—stores sighting data from another terminal or update position of the own terminal, used to estimate the displacement of each visitor;
- group leader election—message used for group leader election.
- Help Flag (HF, 4 bits)—informs if the visitor requested for help.
- ID (mobile or totem) (15 bits)—an integer that identifies the totem or the mobile terminal. The first addresses are fixed and assigned to totems; the others are assigned on demand to terminals. Terminal addresses should remain unique to allow ubiquitous identification of visitors throughout the area during the monitored interval, set to 24 h. If the terminal is not located within the time limit within this range, rescue will be sent even without request.
- Acknowledge (ACK, 1 bit)—indicates that it is a confirmation message for receiving records. If the records were received with errors or only partially, this field has a value of zero.
- Group Flag (GF, 1 bit)—indicates if the terminal issuing the message is a group leader. Together with the mobile ID of the leader forms the group ID.
- Record Time (16 bits)—records the moment of contact with another mobile terminal.
- Latitude and Longitude (24 bits each)—stores the last coordinate obtained, accurate to 2.4 m. Geographic coordinates can be obtained by GPS every minute, if the GPS signal is available, or received from a totem when the mobile terminal is within range. The GPS receiver used in the experiments has an accuracy of 2.5 m [31].
- Location Time (16 bits)—stores the moment the coordinates were obtained.
- Hop Count (4 bits)—contains the number of times the message was forwarded, incremented with each transmission.
- Max Records (11 bits)—reports the maximum number of sighting records that the terminal accepts to receive or received by a totem.
- Battery (4 bits)—reports an estimate of battery life.
- Channel (CH, 2 bits)—identifies the LoRa spreading factor to be used for record exchange.
5.3. Optimization
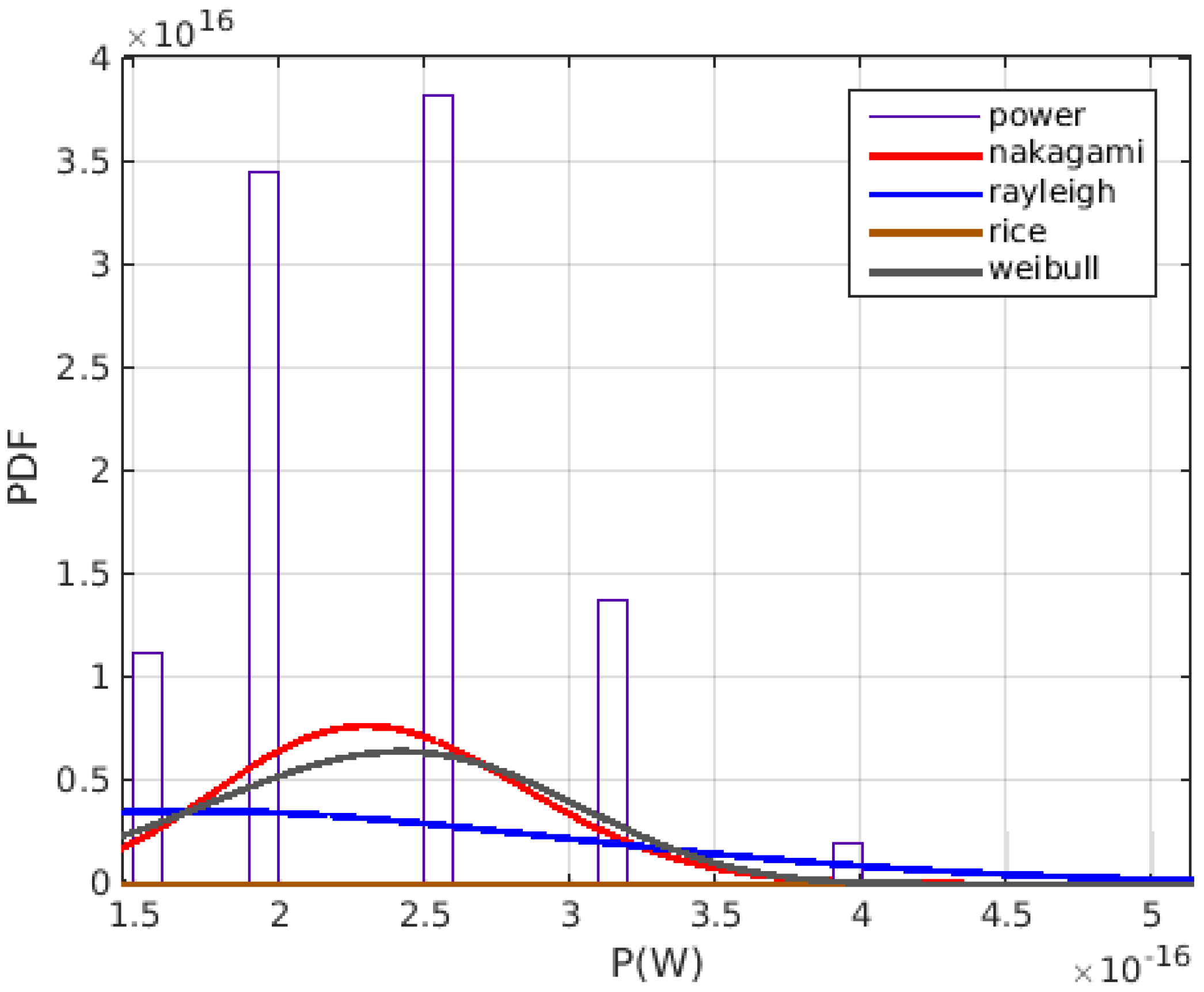
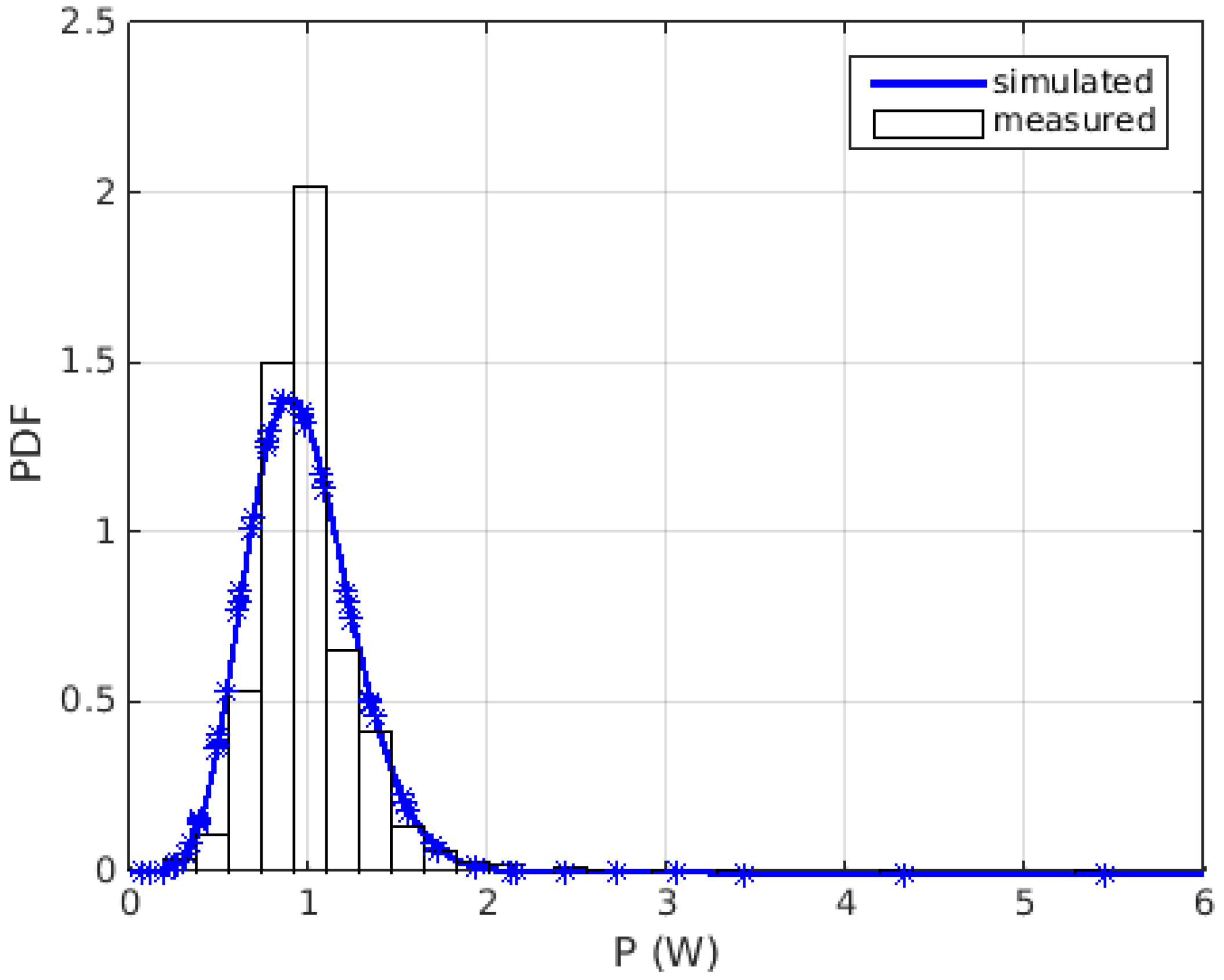
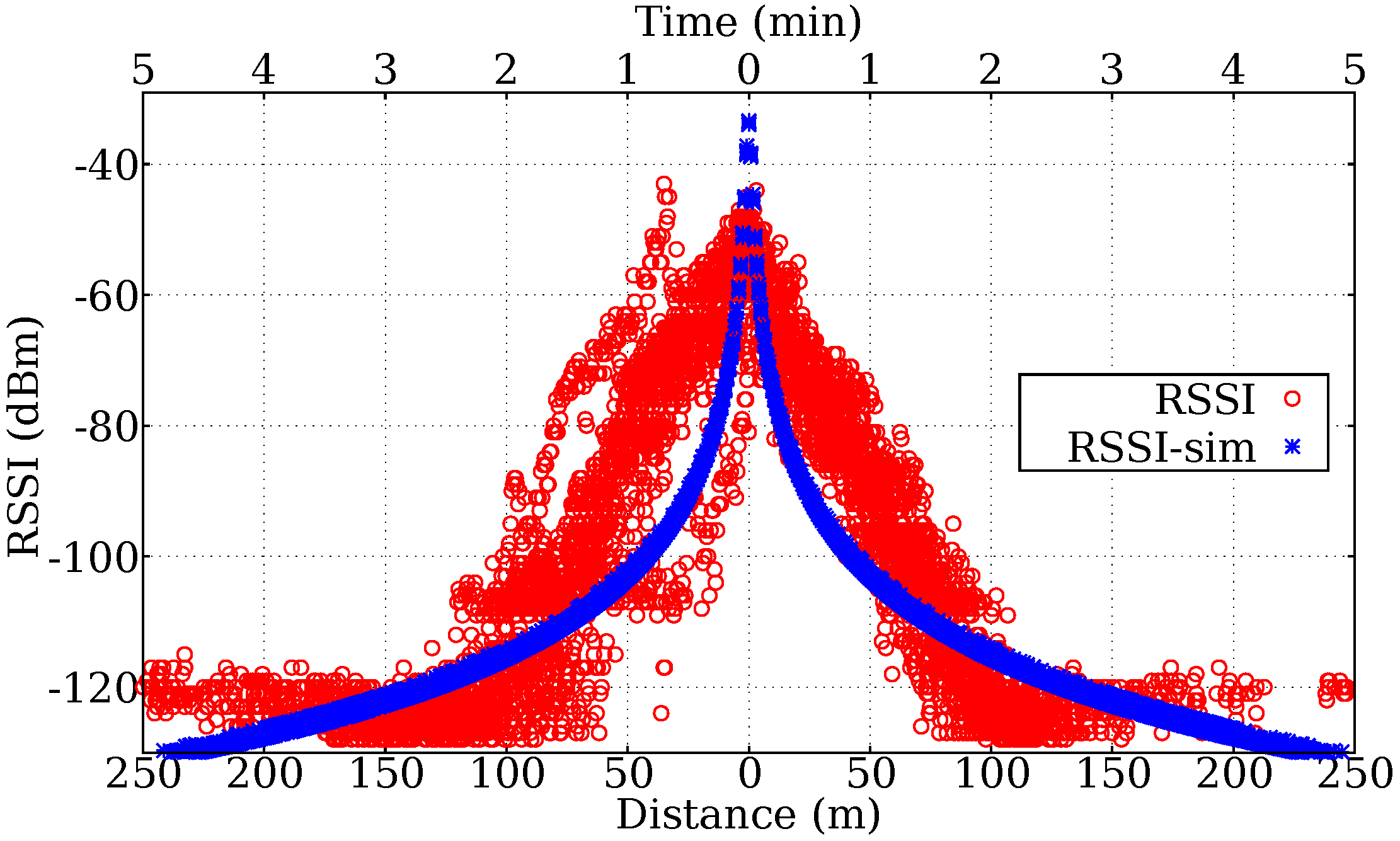
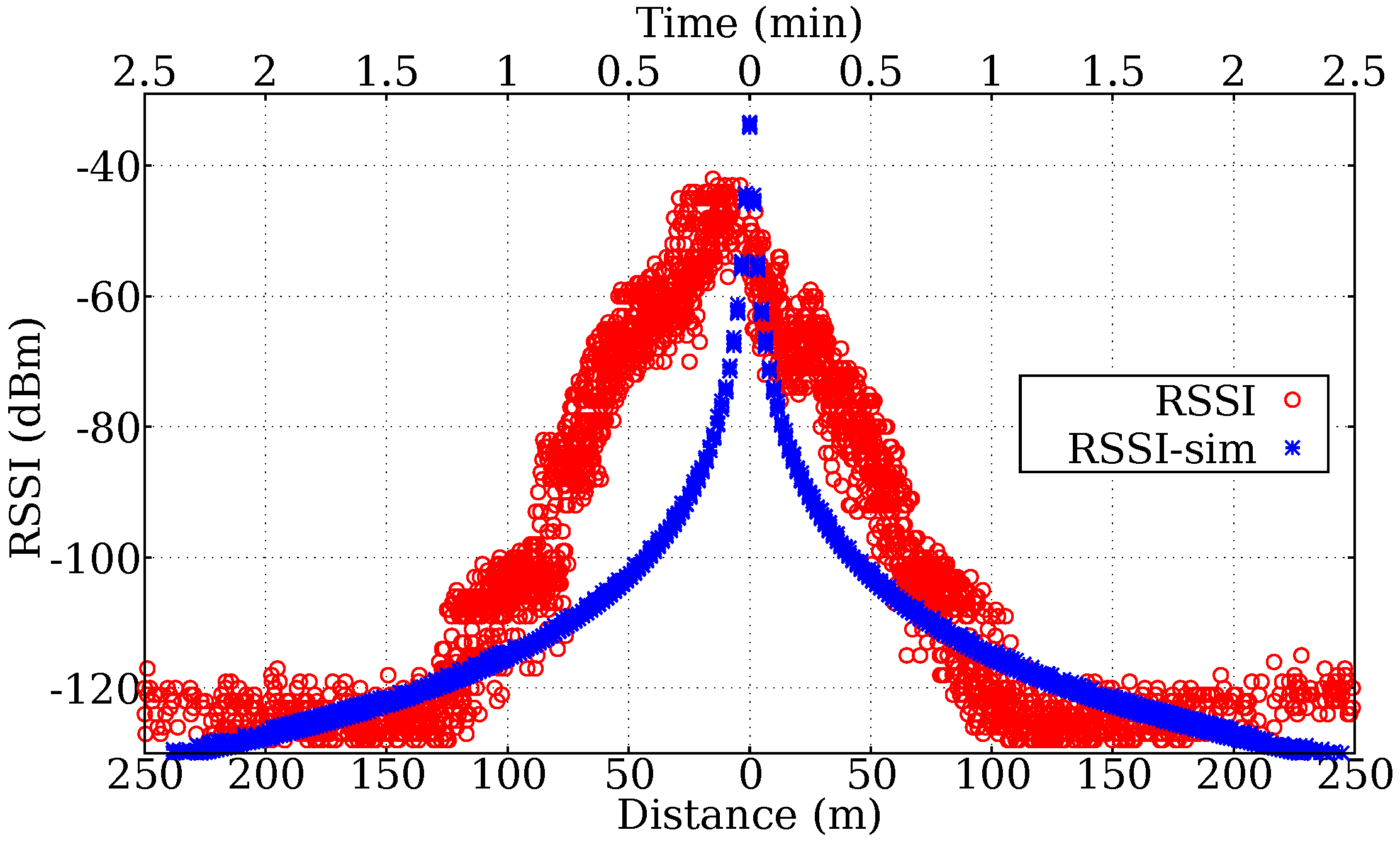
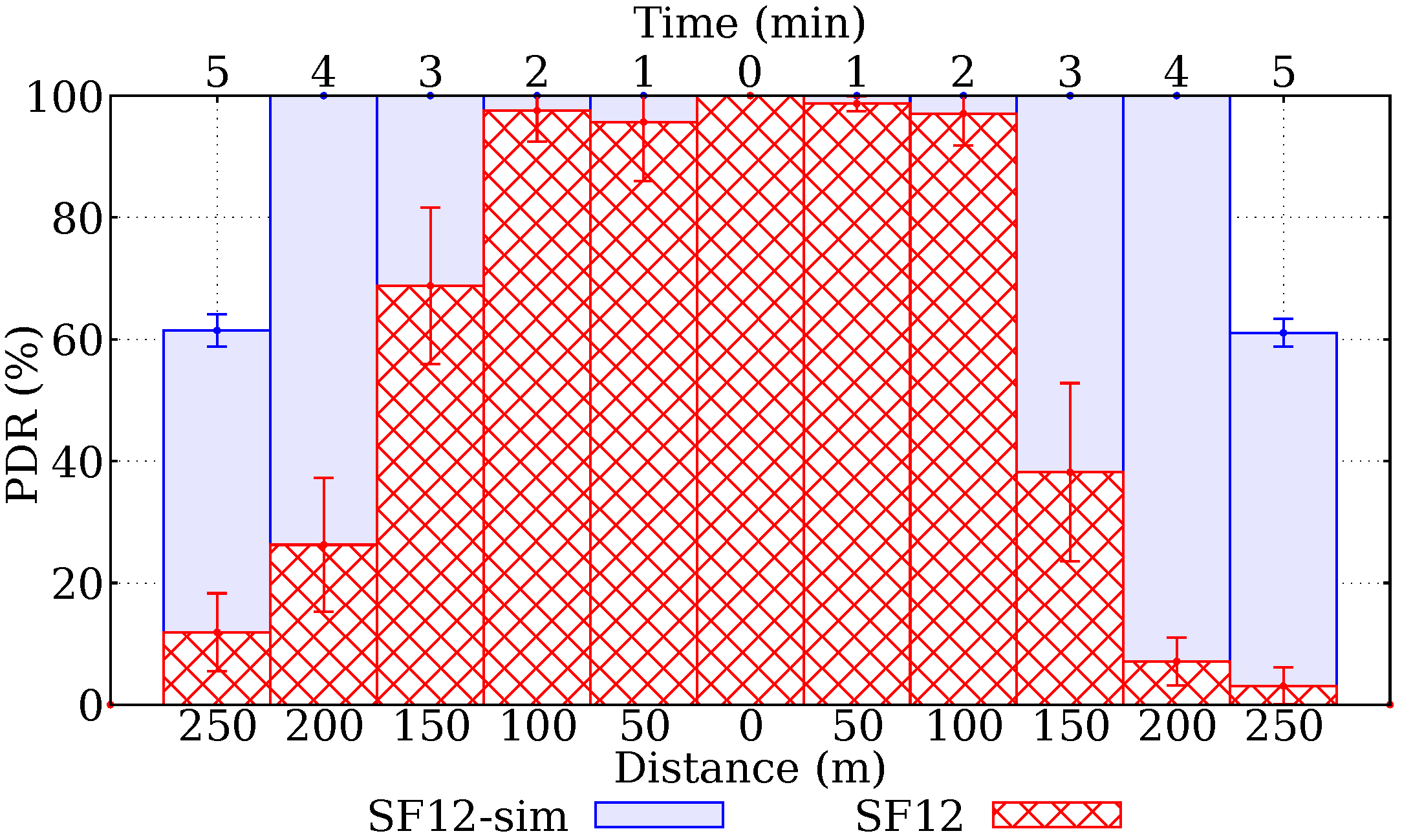
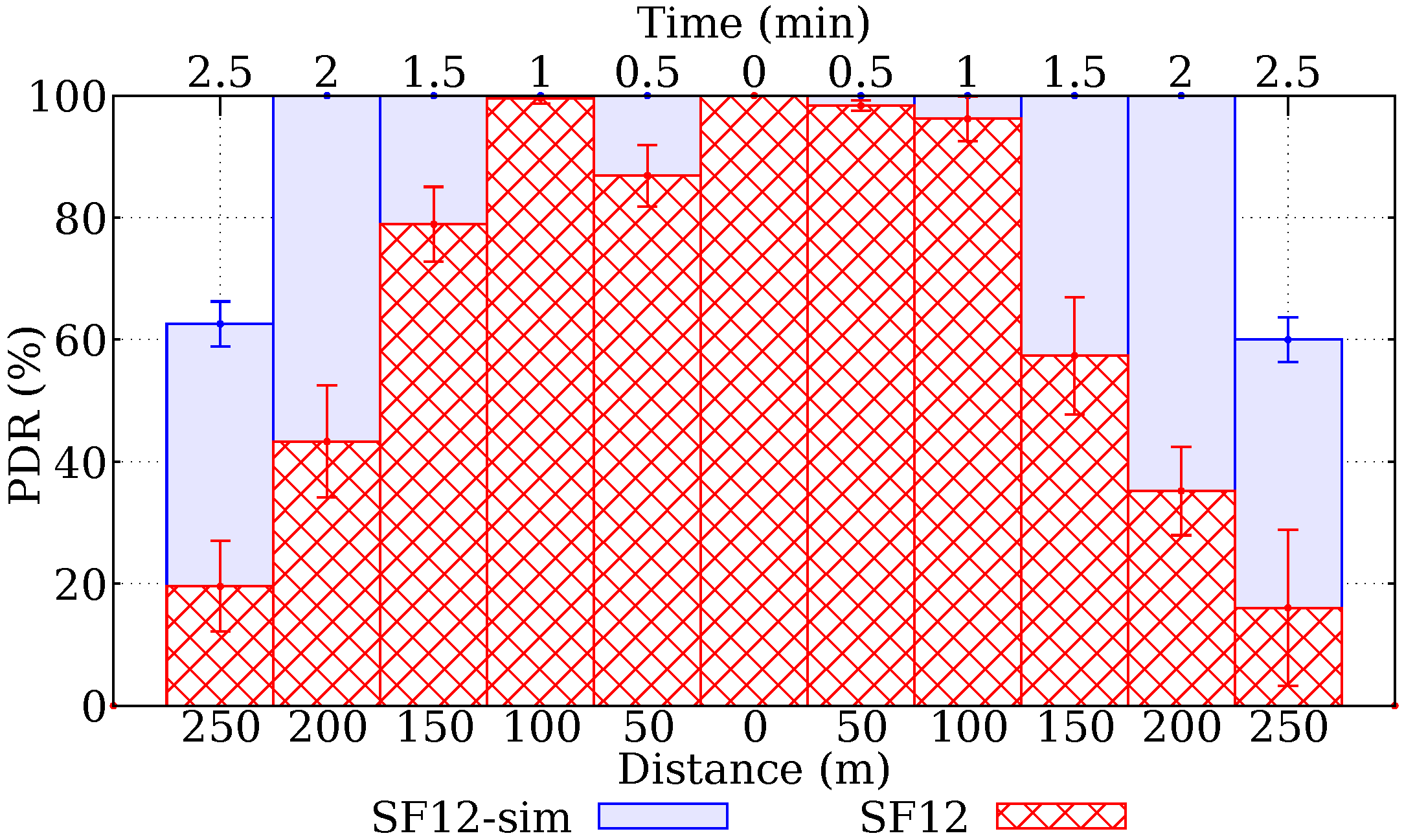
6. Simulation
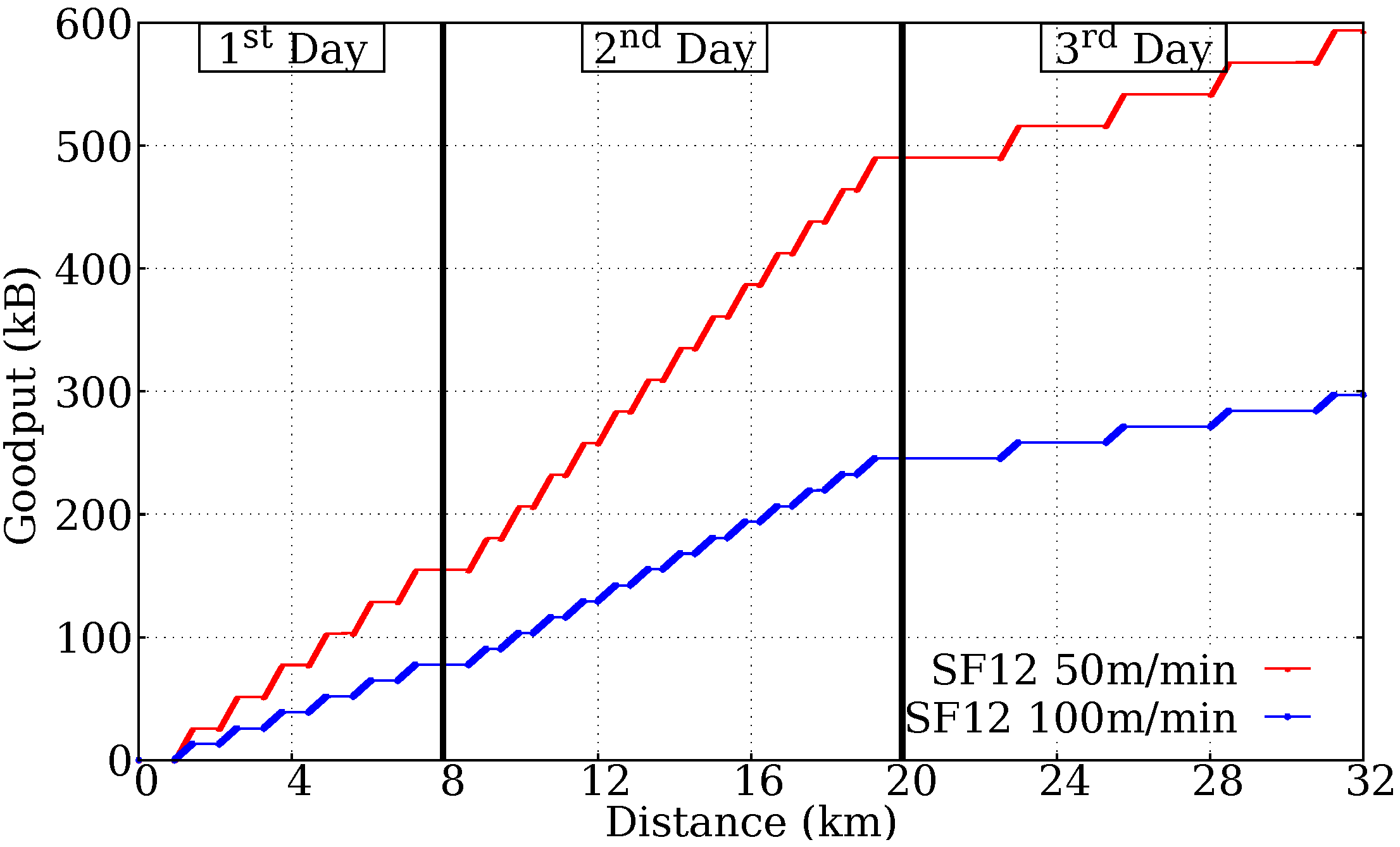
- 1st day: approximately 150 kB, below the worst-case load of 182 kB;
- 2nd day: approximately 500 kB − 150 kB = 350 kB. Above 182 kB;
- 3rd day: approximately 600 kB − 500 kB = 100 kB. Below 182 kB.
- 1st day: approximately 80 kB, below the worst-case load of 182 kB;
- 2nd day: approximately 250 kB − 80 kB = 170 kB. Below 182 kB;
- 3rd day: approximately 300 kB − 250 kB = 50 kB. Below 182 kB.
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Crotti, R.; Misrahi, T. The Travel & Tourism Competitiveness Report 2017. Paving the Way for a More Sustainable and Inclusive Future; World Economic Forum: Geneva, Switzerland, 2017. [Google Scholar]
- LoRa™-Alliance. LoRa™-Alliance Technology. 2016. Available online: https://www.lora-alliance.org/technology (accessed on 20 December 2019).
- Augustin, A.; Yi, J.; Clausen, T.; Townsley, W.M. A study of LoRa: Long range & low power networks for the Internet of things. Sensors 2016, 16, 1466. [Google Scholar]
- Bor, M.; Vidler, J.; Roedig, U. LoRa for the Internet of Things. In Proceedings of the International Conference on Embedded Wireless Systems and Networks (EWSN), Graz, Austria, 15 February 2016; pp. 361–366. [Google Scholar]
- Marais, J.M.; Malekian, R.; Abu-Mahfouz, A.M. LoRa and LoRaWAN testbeds: A review. In Proceedings of the IEEE AFRICON, Cape Town, South Africa, 20 September 2017; pp. 1496–1501. [Google Scholar]
- Semtech Corporation. LoRa™ Modulation Basics AN1200.22. 2015. Available online: https://www.semtech.com/uploads/documents/an1200.22.pdf (accessed on 20 December 2019).
- Huang, J.H.; Amjad, S.; Mishra, S. CenWits: A sensor-based loosely coupled search and rescue system using witnesses. In Proceedings of the 3rd International Conference on Embedded Networked Sensor Systems, San Diego, CA, USA, 2–4 November 2005; pp. 180–191. [Google Scholar]
- Miller, M.; Lieske, S.; Carter, R.; Walsh, S. Understanding the Interaction Between a Protected Destination System and Conservation Tourism Through Remote Sensing. In Comprehensive Remote Sensing; Elsevier: Amsterdam, The Netherlands, 2018; pp. 123–143. [Google Scholar]
- Carbonés Fargas, B. IoT and Tracking Capabilities in LPWANs. Master’s Thesis, Universitat Politècnica de Catalunya, Barcelona, Spain, 2017. [Google Scholar]
- Hunkeler, U.; Truong, H.L.; Stanford-Clark, A. MQTT-S—A publish/subscribe protocol for Wireless Sensor Networks. In Proceedings of the 3rd International Conference on Communication Systems Software and Middleware and Workshops (COMSWARE), Bangalore, India, 5–10 January 2008; pp. 791–798. [Google Scholar]
- Baharudin, A.M.; Yan, W. Long-range wireless sensor networks for geo-location tracking: Design and evaluation. In Proceedings of the International Electronics Symposium (IES), Bali, Indonesia, 21 September 2016; pp. 76–80. [Google Scholar]
- Bouras, C.; Gkamas, A.; Kokkinos, V.; Papachristos, N. Using LoRa technology for IoT monitoring systems. In Proceedings of the 10th International Conference on Networks of the Future (NoF), Rome, Italy, 1 October 2019; pp. 134–137. [Google Scholar]
- Sanchez-Iborra, R.; G Liaño, I.; Simoes, C.; Couñago, E.; Skarmeta, A.F. Tracking and monitoring system based on LoRa technology for lightweight boats. Electronics 2019, 8, 15. [Google Scholar] [CrossRef]
- Joshi, A.; VishnuKanth, I.N.; Samdaria, N.; Bagla, S.; Ranjan, P. GPS-less animal tracking system. In Proceedings of the 4th International Conference on Wireless Communication and Sensor Networks (WCSN), Wuhan, China, 17 December 2008; pp. 120–125. [Google Scholar]
- Jiang, L.; Huang, J.H.; Kamthe, A.; Liu, T.; Freeman, I.; Ledbetter, J.; Mishra, S.; Han, R.; Cerpa, A. SenSearch: GPS and witness assisted tracking for delay tolerant sensor networks. In Proceedings of the International Conference on Ad-Hoc Networks and Wireless, Luxembourg, 3 October 2009; pp. 255–269. [Google Scholar]
- Huang, Y.T.; Chen, Y.C.; Huang, J.H.; Chen, L.J.; Huang, P. YushanNet: A delay-tolerant wireless sensor network for hiker tracking in Yushan national park. In Proceedings of the 10th International Conference on Mobile Data Management: Systems, Services and Middleware, Taipei, Taiwan, 25 October 2009; pp. 379–380. [Google Scholar]
- Burghardt, D.; Edwardes, A.; Weibel, R. WebPark–Entwicklung eines mobilen Informationssystems für Erholungs-und Naturschutzgebiete. Kartographische Nachrichten 2003, 53, 58–64. (In German) [Google Scholar] [CrossRef]
- Gonçalves, A. Projecto Webpark-Informação Geográfica Relevante para Visitantes de Áreas Protegidas. In Actas do eSIG2004-VIII Encontro de Utilizadores de Informação Geográfica, Lisboa (Poster); LNEC/DHA/GTI-Relatorios Cientificos: Lisboa, Portugal, 2004. (In Portuguese) [Google Scholar]
- Krug, K.; Mountain, D.; Phan, D. Location-based services for mobile users in protected areas. GeoInformatics 2003, 6, 26–29. [Google Scholar]
- Lawson, S.R.; Manning, R.E.; Valliere, W.A.; Wang, B. Proactive monitoring and adaptive management of social carrying capacity in Arches National Park: An application of computer simulation modeling. J. Environ. Manag. 2003, 68, 305–313. [Google Scholar] [CrossRef]
- Son, B.; Her, Y.s.; Kim, J.G. A design and implementation of forest-fires surveillance system based on wireless sensor networks for South Korea mountains. Int. J. Comput. Sci. Network Secur. 2006, 6, 124–130. [Google Scholar]
- Rao, T.R.; Balachander, D.; Kiran, A.N.; Oscar, S. RF propagation measurements in forest & plantation environments for Wireless Sensor Networks. In Proceedings of the International Conference on Recent Trends in Information Technology, Chennai, Tamil Nadu, India, 19–21 April 2012; pp. 308–313. [Google Scholar]
- Tsai, M. Path-Loss and Shadowing (Large-Scale Fading); Technical Report; National Taiwan University: Taipei, Taiwan, 2011. [Google Scholar]
- Nakagami, M. The m-distribution—A general formula of intensity distribution of rapid fading. In Statistical Methods in Radio Wave Propagation; Pergamon: Oxford, UK, 1960; pp. 3–36. [Google Scholar]
- Abdi, A.; Kaveh, M. On the utility of gamma PDF in modeling shadow fading (slow fading). In Proceedings of the IEEE 49th Vehicular Technology Conference, Houston, TX, USA, 20 May 1999; Volume 3, pp. 2308–2312. [Google Scholar]
- Goursaud, C.; Gorce, J.M. Dedicated networks for IoT: PHY/MAC state of the art and challenges. EAI Endorsed Trans. Int. Things 2015, 15, 1–11. [Google Scholar] [CrossRef]
- Raza, U.; Kulkarni, P.; Sooriyabandara, M. Low Power Wide Area Networks: An Overview. IEEE Commun. Surveys Tutor. 2017, 19, 855–873. [Google Scholar] [CrossRef]
- Cerf, V.; Burleigh, S.; Hooke, A.; Torgerson, L.; Durst, R.; Scott, K.; Fall, K.; Weiss, H. Delay-Tolerant Networking Architecture. RFC 4838. 2007. Available online: https://tools.ietf.org/html/rfc4838 (accessed on 20 December 2019).
- Scott, K.; Burleigh, S.C. Bundle Protocol Specification. RFC 5050. 2007. Available online: https://tools.ietf.org/html/rfc5050 (accessed on 20 December 2019).
- Ferreira, A.E.; Ortiz, F.M.; Costa, L.H.M.K. Avaliação de Tecnologias de Comunicação Sem-Fio para Monitoramento em Ambientes de Floresta. In Proceedings of the Anais do XXXVII Simpósio Brasileiro de Redes de Computadores e Sistemas Distribuídos, Gramado, Brazil, 6 May 2019; pp. 116–129. (In Portuguese). [Google Scholar]
- AG, U.H. NEO-6: U-blox 6 GPS Modules Data Sheet. 2011. Available online: https://www.u-blox.com/sites/default/files/products/documents/NEO-6_DataSheet_(GPS.G6-HW-09005).pdf (accessed on 20 December 2019).
- De Queiroz, G.F.C.; Ferreira, A.E.; Ortiz, F.M.; Couto, R.S.; Costa, L.H.M.K. Posicionamento de Pontos de Acesso Sem-fio para Segurança de Visitantes em Parques Florestais. In Proceedings of the Anais do XXXVI Simpósio Brasileiro de Redes de Computadores e Sistemas Distribuídos, Campos do Jordão, Brazil, 6 May 2018. (In Portuguese). [Google Scholar]
- Stutzman, W.L.; Thiele, G.A. Antenna Theory and Design, 3rd ed.; John Wiley & Sons: Hoboken, NJ, USA, 2012. [Google Scholar]
- Henderson, T.R.; Lacage, M.; Riley, G.F.; Dowell, C.; Kopena, J. Network simulations with the ns-3 Simulator. In SIGCOMM Demonstration; Association for Computing Machinery: Seattle, WA, USA, 2008; Volume 14, p. 527. [Google Scholar]
- Hammersley, J. Monte Carlo Methods; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Magrin, D.; Centenaro, M.; Vangelista, L. Performance evaluation of LoRa networks in a smart city scenario. In Proceedings of the IEEE International Conference on Communications (ICC), Paris, France, 25 May 2017; pp. 1–7. [Google Scholar]
- Ferreira, A.E.; Ortiz, F.M.; Costa, L.H.M.K. Caracterização de Disrupções na Faixa ISM de 900 MHz em Ambiente de Floresta. In Proceedings of the XXXVII Simpósio Brasileiro de Telecomunicações e Processamento de Sinais (SBrT), Petrópolis, Brazil, 2 October 2019. (In Portuguese). [Google Scholar]
- Rappaport, T.S. Wireless Communications: Principles and Practice; Prentice Hall: Upper Saddle River, NJ, USA, 1996; Volume 2. [Google Scholar]







| Description | Value |
|---|---|
| Controller | Arduino Uno R3 |
| Wireless interface | Dragino RF96 |
| GPS Receiver | U-blox NEO-6M |
| Antenna | Monopole 7dBi |
| Transmission antenna height | 1.5 m |
| Supply Current in Receive Mode | 10.8 mA |
| Supply Current in Transmit Mode | 120 mA |
| Description | Value |
|---|---|
| Frequency | 915 MHz |
| Bandwidth | 500 kHz |
| Code Rate | 4/5 |
| Transmission Power | 14 dBm |
| Description | Value |
|---|---|
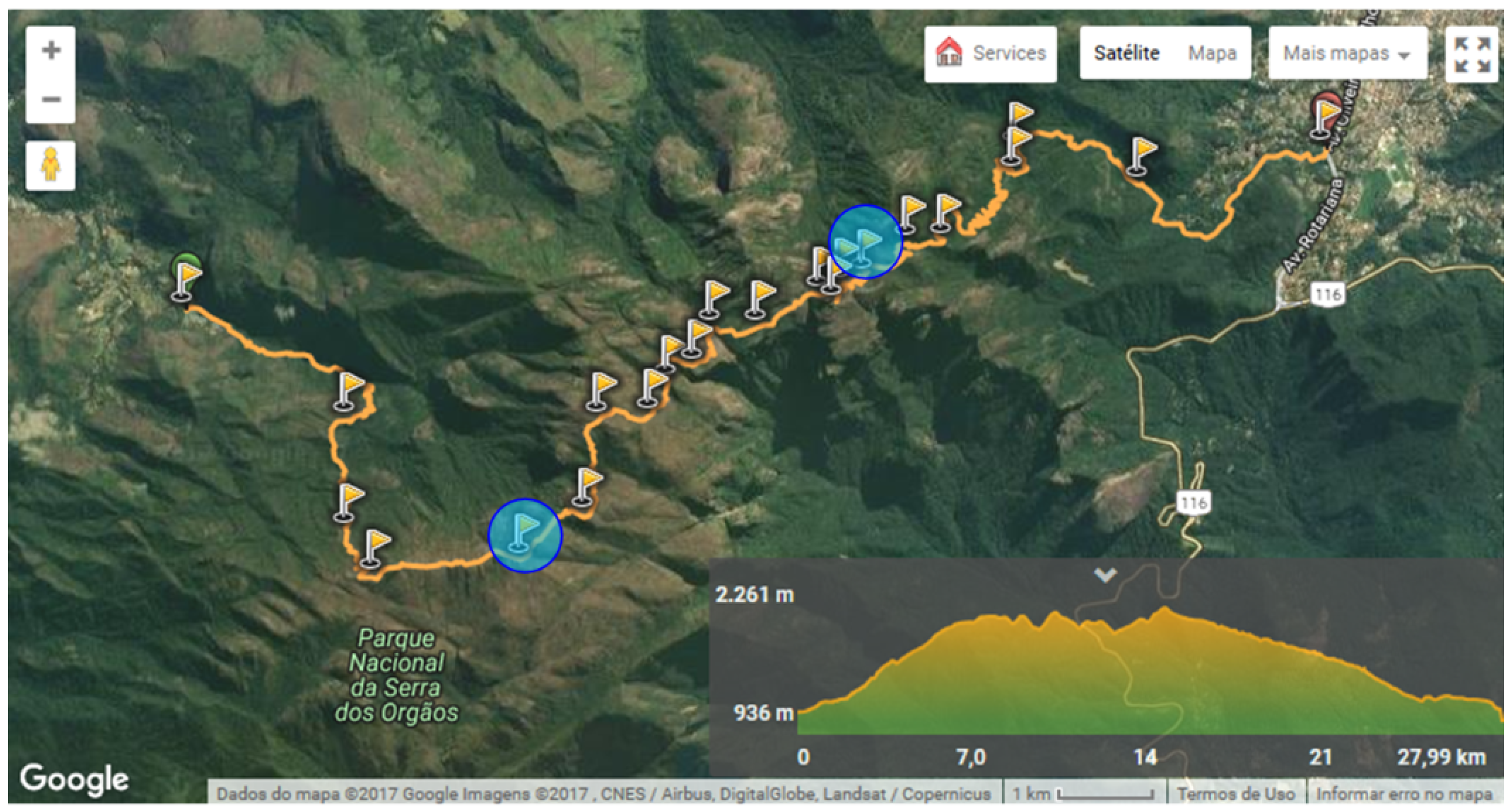
| Track length | 29 km |
| Number of receivers (totems) | 23 |
| Receiving antenna height | 2.5 m |
| PHY Protocol | LoRa |
| Spreading Factor | SF12 |
| Frequency | 915 MHz |
| Bandwidth | 500 kHz |
| Code Rate | 4/5 |
| Mobile speed | 50 m/min (3 km/h) |
| 100 m/min (6 km/h) | |
| Transmission antenna height | 1.5 m |
| Transmission power | 14 dBm |
| Packet size | 47 bytes |
| Number of executions | 10 rounds |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ferreira, A.E.; Ortiz, F.M.; Almeida, T.T.d.; Costa, L.H.M.K. A Visitor Assistance System Based on LoRa for Nature Forest Parks. Electronics 2020, 9, 696. https://doi.org/10.3390/electronics9040696
Ferreira AE, Ortiz FM, Almeida TTd, Costa LHMK. A Visitor Assistance System Based on LoRa for Nature Forest Parks. Electronics. 2020; 9(4):696. https://doi.org/10.3390/electronics9040696
Chicago/Turabian StyleFerreira, Ana Elisa, Fernando Molano Ortiz, Thales Teixeira de Almeida, and Luís Henrique M. K. Costa. 2020. "A Visitor Assistance System Based on LoRa for Nature Forest Parks" Electronics 9, no. 4: 696. https://doi.org/10.3390/electronics9040696
APA StyleFerreira, A. E., Ortiz, F. M., Almeida, T. T. d., & Costa, L. H. M. K. (2020). A Visitor Assistance System Based on LoRa for Nature Forest Parks. Electronics, 9(4), 696. https://doi.org/10.3390/electronics9040696





