Investigations of the Wireless M-Bus System Resilience under Challenging Propagation Conditions
Abstract
:1. Introduction
- Provide the minimum CNIR values (and, thus, sensitivity), separately for each throughput mode, which may lend themselves to serving as reference figures at a wireless sensor network (WSN) radio-planning stage, based on the WM-Bus technology.
- Allow us to select the most appropriate operational mode (in terms of the modulation and the throughput) to best-fit propagation conditions encountered on the WSN deployment site.
- Demonstrate Wireless M-Bus performance under propagation conditions of variable adversity at the two different frequency bands.
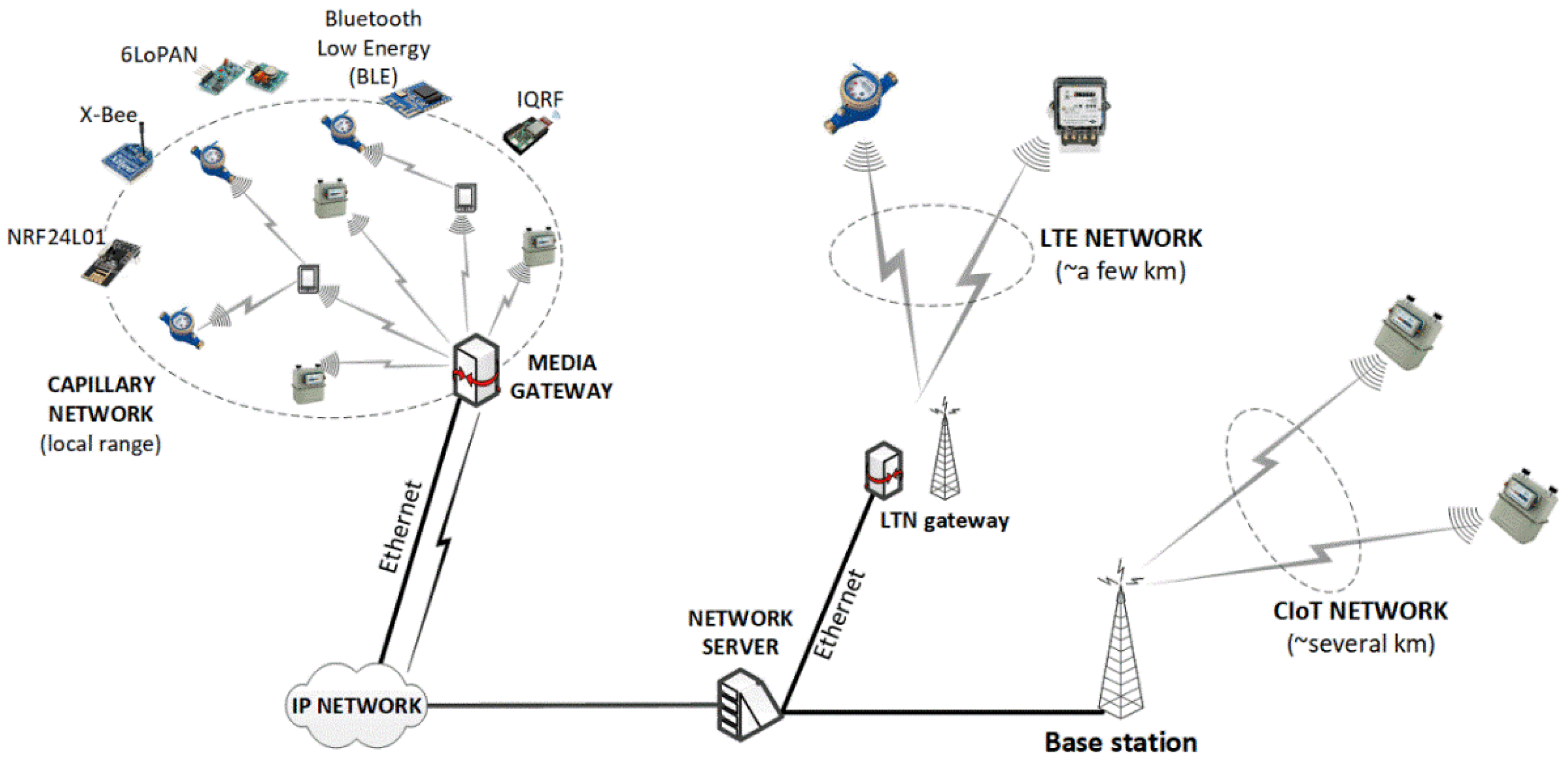
2. On the Internet of Things Systems and Capillary Networks
3. On Jamming in WSN and the Internet of Things Systems—A Review
4. The Purpose of the Investigations
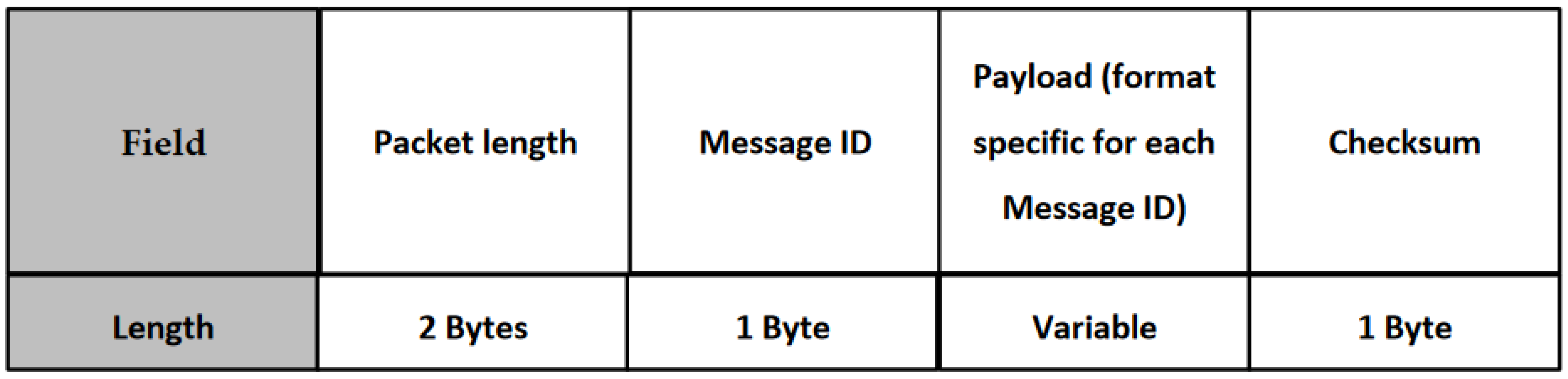
5. Measurements of Wireless M-Bus Resilience to Interference and Multipath
- ▪ Electromagnetic (EM) disturbances of variable power, with additive white gaussian characteristic (AWGN). For this purpose, investigations were carried out in an anechoic chamber, as shown in Section 6.
- ▪ Extremely multipath propagation, emulated with the use of a reverberation chamber, as shown in Section 7.
6. WMBus Performance under Controlled Radio Jamming
6.1. The Measurement Environment and Procedures
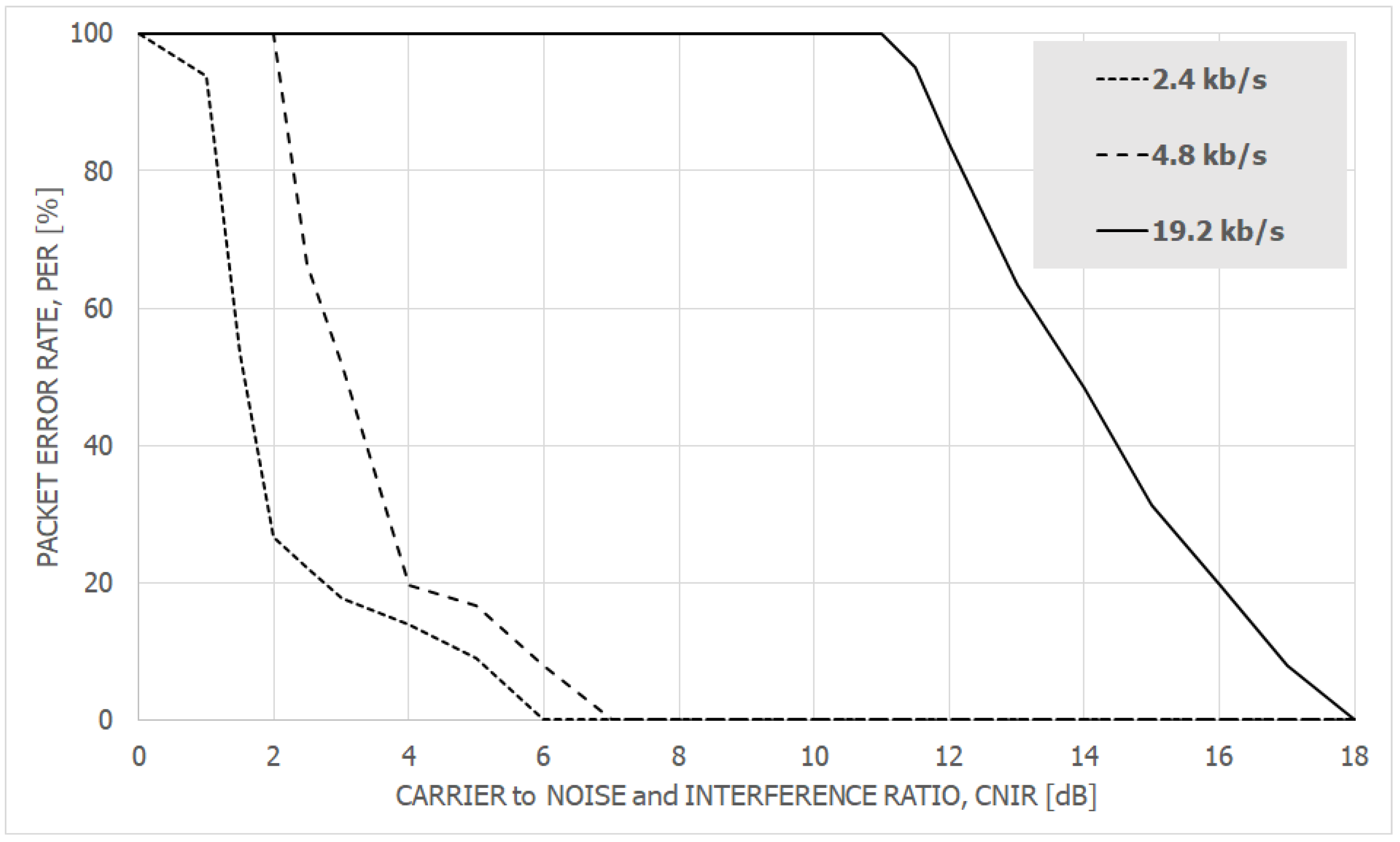
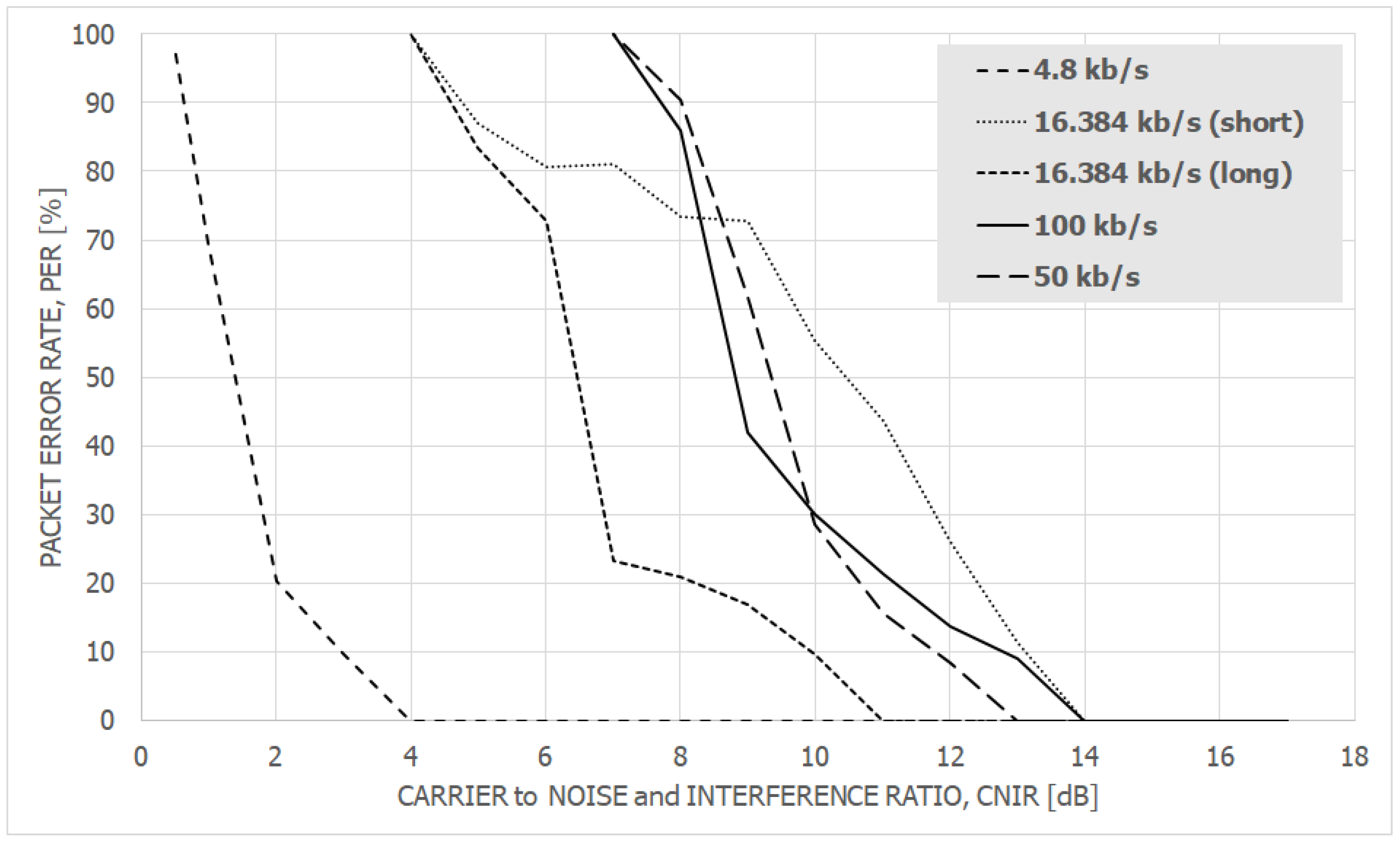
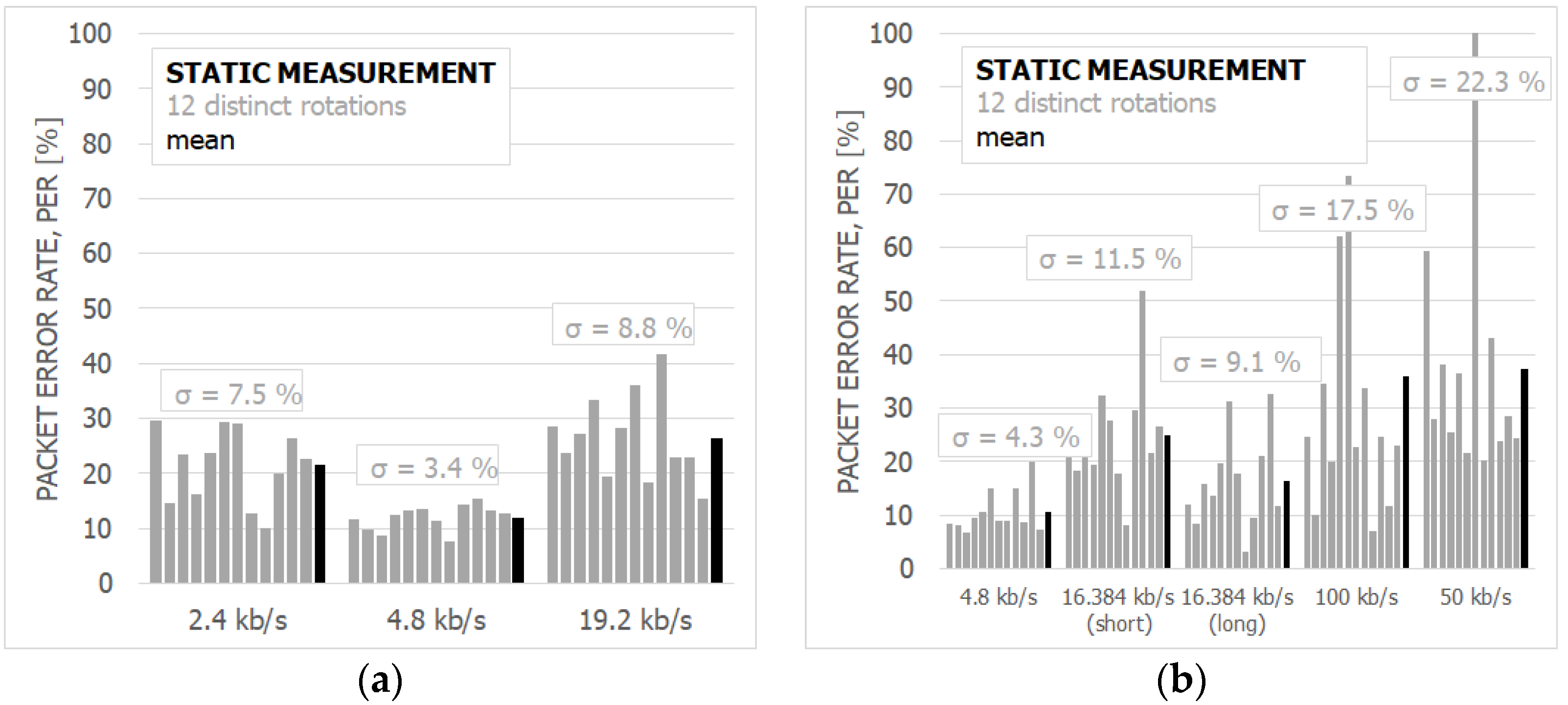
6.2. The Results and Discussion
7. Investigations of Wireless M-Bus Susceptibility to the Multipath Propagation
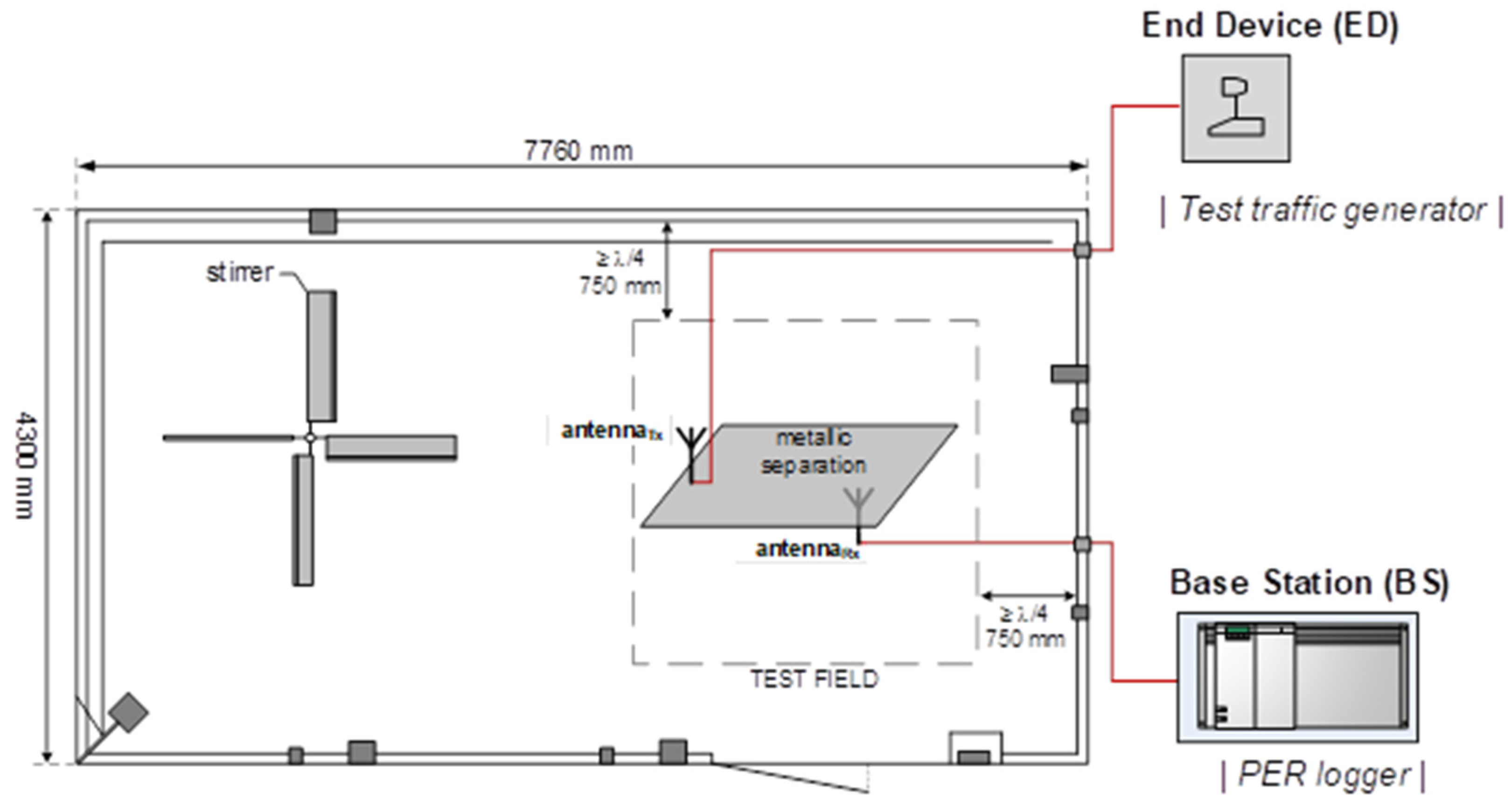
7.1. The Measurement Environment and Procedures
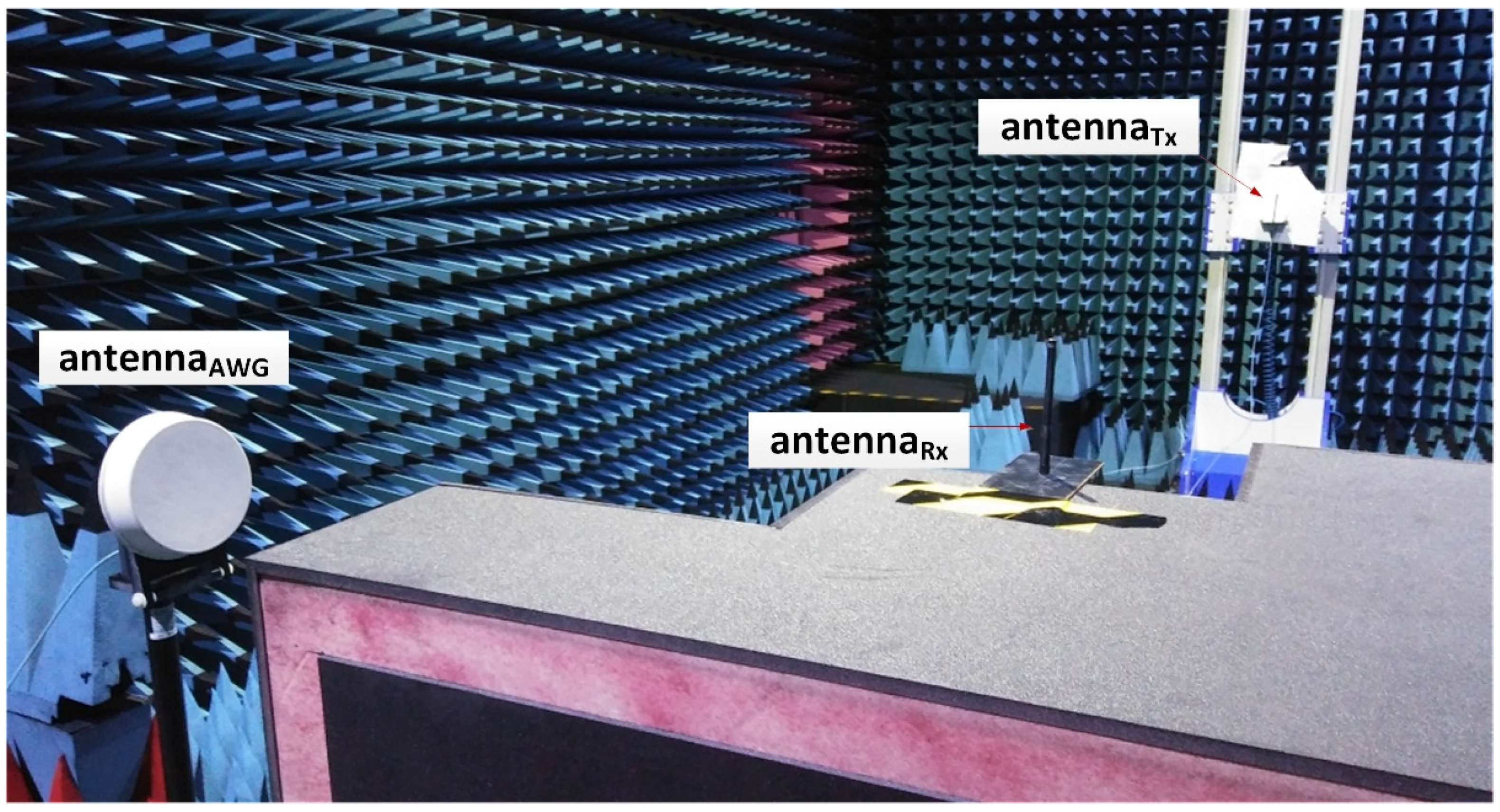
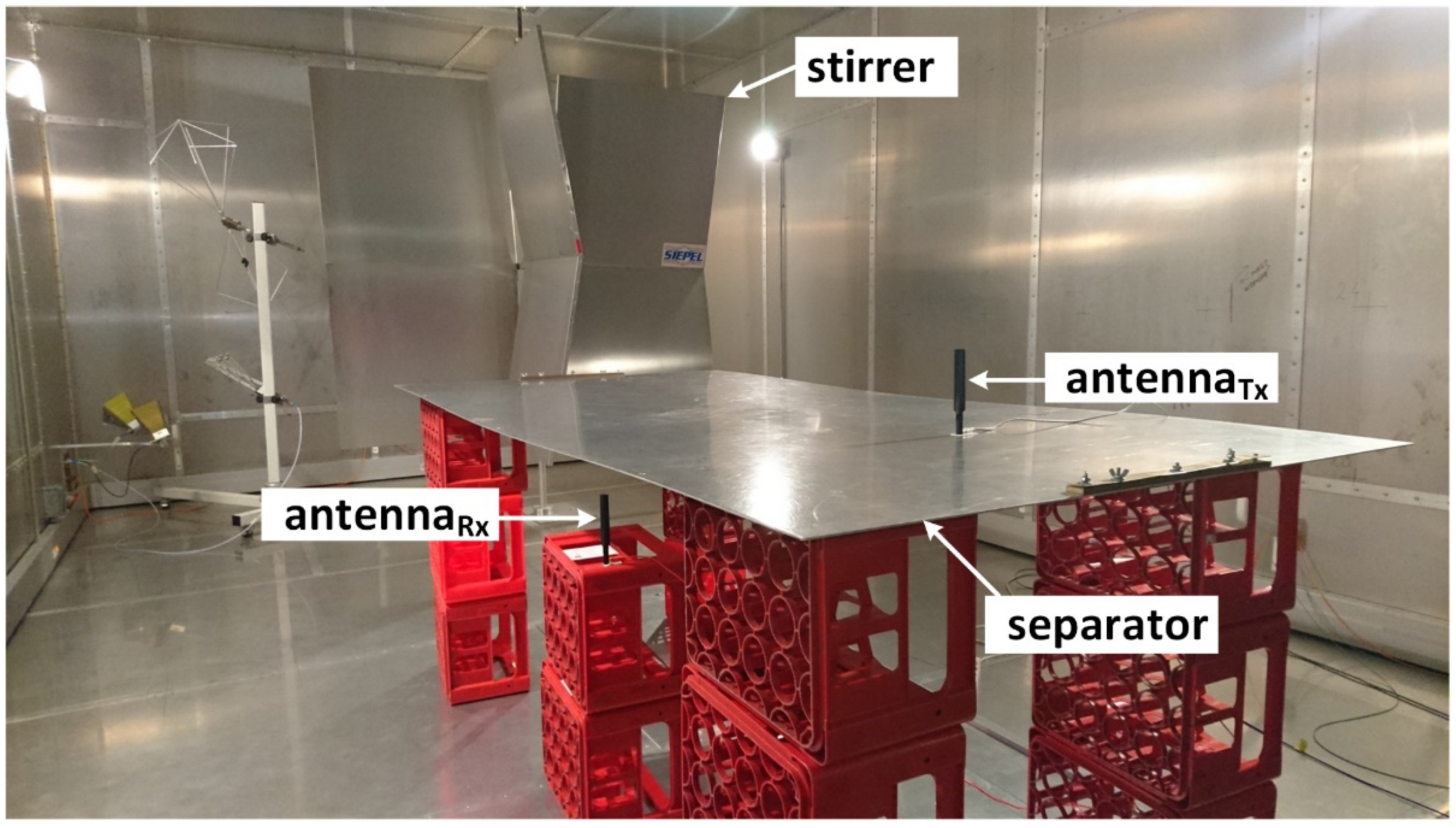
- In order to eliminate the influence of the tested DUT devices, e.g., by their undesirable energy radiation from on-board electronics, only antennas of these devices were placed in the chamber, marked in Figure 10 as ‘antennaTx’ and ‘antennaRx’, attached to their respective modems (placed outside the chamber) by means of low-loss cables with the minimum length required to operate the equipment outside the chamber during measurements. These cables were drawn outside the chamber through well-shielded feedthroughs in the chamber wall.
- In order to eliminate the direct component, both antennas during PER measurements were separated by a conductive separator (e.g., a metal plane), which created the signal reception conditions characteristic of the Rayleigh channel (desirable and typical for resonance cavities acc. to [39]), i.e., one in which the arriving components are solely due to reflections and diffractions.
- The reverberation chamber was equipped with a stirrer that facilitated a homogeneous distribution of the electric field in its interior during measurements.
- The chamber control system enabled the stirrer to work in both a fixed and continuous rotation mode, with a user-defined angular rotation speed (degrees/second).
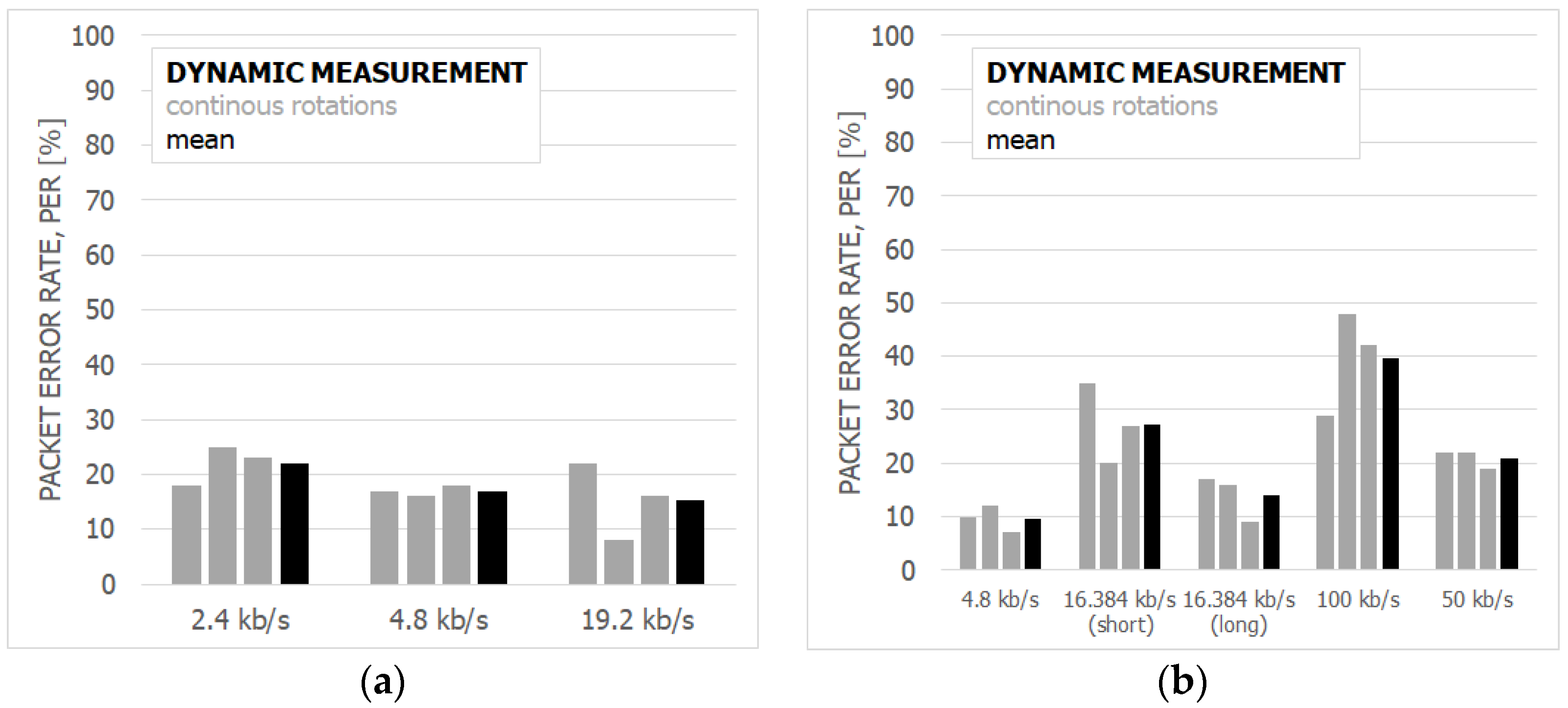
7.2. The Results and Discussion
8. General Conclusions and Further Research
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviation
| AWGN | Additive White Gaussian Noise |
| BBN | Broadband Noise |
| CIoT | Cellular IoT |
| CNIR | Carrier to Noise and Interference Ratio |
| DUT | Device Under Test |
| EM | Electromagnetic |
| FSK | Frequency-shift keying |
| GEV | Generalized Extreme Value Distribution |
| GFSK | Gaussian Frequency-shift keying |
| IDS | Intrusion Detection System |
| IoT | Internet of Things |
| ISM | Industrial, Scientific, Medical |
| LEC | Laboratory of Electromagnetic Compatibility (LEC) |
| LTN | Low Throughput Network |
| M2M | Machine-to-machine |
| MIMO | Multiple Input Multiple Output |
| ML | Machine Learning |
| MTC | Machine-type Communication) |
| MTD | Machine-type device |
| PDP | Power Delay Profile |
| PER | Packet Error Rate |
| RFID | Radio Frequency Identification |
| SNR | Signal to Noise Ratio |
| WM-Bus | Wireless M-Bus |
| WSN | Wireless Sensor Network |
References
- Ashton, K. That ‘Internet of Things’ Thing. In the real world, things matter more than ideas. RFiD J. 2009, 22, 97–114. [Google Scholar]
- Peter Day’s World of Business, BBC World Service (BBC). Available online: http://downloads.bbc.co.uk/podcasts/radio/worldbiz/worldbiz_20150319-0730a.mp3 (accessed on 25 June 2022).
- TR 45.820 V2.1.0; Cellular System Support for Ultra Low Complexity and Low Throughput Internet of Things; The 3rd Generation Partnership Project; 3GPP Organizational Partners: Valbonne, France, 2015.
- Huvio, E.; Grönvall, J.; Främling, K. Tracking and tracing parcels using a distributed computing approach. In Proceedings of the 14th Annual Conference for Nordic Researchers in Logistics (NOFOMA’2002), Trondheim, Norway, 12–14 June 2002; pp. 29–43. [Google Scholar]
- Magrassi, P. Why a Universal RFID Infrastructure Would Be a Good Thing. Technology 2002, 16, 0038. [Google Scholar]
- Magrassi, P.; Berg, T. A World of Smart Objects, Gartner Research Report R-17-2243. 2002. Available online: https://www.gartner.com/en/documents/366151 (accessed on 4 January 2023).
- Internet of Things—An Action Plan for Europe; COM(2009) 278 final; Commission of the European Communities: Brussels, Belgium, 2009.
- Wood, A. The Internet of Things Is Revolutionizing Our Lives, but Standards Are a Must. The Guardian. 2015. Available online: https://www.theguardian.com/media-network/2015/mar/31/the-internet-of-things-is-revolutionising-our-lives-but-standards-are-a-must (accessed on 4 January 2023).
- Evans, D. The Internet of Things: How the Next Evolution of the Internet Is Changing Everything. Cisco White Pap. 2011, 1, 1–11. [Google Scholar]
- Shafiq, M.; Tian, Z.; Bashir, A.K.; Du, X.; Guizani, M. CorrAUC: A Malicious Bot-IoT Traffic Detection Method in IoT Network Using Machine-Learning Techniques. IEEE Internet Things J. 2021, 8, 3242–3254. [Google Scholar] [CrossRef]
- Shafiq, M.; Tian, Z.; Bashir, A.K.; Du, X.; Guizani, M. IoT malicious traffic identification using wrapper-based feature selection mechanisms. Comput. Secur. 2020, 94, 101863. [Google Scholar] [CrossRef]
- Shafiq, M.; Tian, Z.; Bashir, A.K.; Jolfaei, A.; Yu, X. Data mining and machine learning methods for sustainable smart cities traffic classification: A survey. Sustain. Cities Soc. 2020, 60, 102177. [Google Scholar] [CrossRef]
- Shafiq, M.; Tian, Z.; Sun, Y.; Du, X.; Guizani, M. Selection of effective machine learning algorithm and Bot-IoT attacks traffic identification for internet of things in smart city. Future Gener. Comput. Syst. 2020, 107, 433–442. [Google Scholar] [CrossRef]
- Anani, W.; Ouda, A. Wireless Meter Bus: Secure Remote Metering within the IoT Smart Grid. In Proceedings of the 2022 International Symposium on Networks, Computers and Communications (ISNCC), Shenzhen, China, 19–22 July 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Machine-to-Machine Communications (M2M); Smart Metering Use Cases. ETSI TR 102 691 V1.1.1 (2010-05). Available online: https://www.etsi.org/deliver/etsi_tr/102600_102699/102691/01.01.01_60/tr_102691v010101p.pdf (accessed on 4 January 2023).
- Vejlgaard, B.; Lauridsen, M.; Nguyen, H.C.; Kovács, I.; Mogensen, P.E.; Sørensen, M. Interference Impact on Coverage and Capacity for Low Power Wide Area IoT Networks. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference, San Francisco, CA, USA, 19–22 March 2017. [Google Scholar]
- Lauridsen, M.; Vejlgaard, B.; Kovacs, I.Z.; Nguyen, H.; Mogensen, P. Interference Measurements in the European 868 MHz ISM Band with Focus on LoRa and SigFox. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Chi, Z.; Li, Y.; Liu, X.; Wang, W.; Yao, Y.; Zhu, T.; Zhang, Y. Countering cross-technology jamming attack. In Proceedings of the 13th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec ‘20), Association for Computing Machinery, New York, NY, USA, 8–10 July 2020; pp. 99–110. [Google Scholar] [CrossRef]
- Singh, J.; Woungang, I.; Dhurandher, S.K.; Khalid, K. A jamming attack detection technique for opportunistic networks. Internet Things 2022, 17, 100464. [Google Scholar] [CrossRef]
- Mbarek, B.; Ge, M.; Pitner, T. An adaptive anti-jamming system in HyperLedger-based wireless sensor networks. Wirel. Netw. 2022, 28, 691–703. [Google Scholar] [CrossRef]
- Navas, R.E.; Cuppens, F.; Cuppens, N.B.; Toutain, L.; Papadopoulos, G.Z. Physical resilience to insider attacks in IoT networks: Independent cryptographically secure sequences for DSSS anti-jamming. Comput. Netw. 2021, 187, 107751. [Google Scholar] [CrossRef]
- Sciancalepore, S.; Oligeri, G.; Di Pietro, R. Strength of Crowd (SOC)—Defeating a Reactive Jammer in IoT with Decoy Messages. Sensors 2018, 18, 3492. [Google Scholar] [CrossRef]
- Manikandan, C.; Alamelumangai, V. Performance Analysis of Nash Algorithm to Detect the Jamming Attack in IoT Network. Compliance Eng. J. 2020, 11, 7–13. [Google Scholar]
- Tang, X.; Ren, P.; Han, Z. Jamming Mitigation via Hierarchical Security Game for IoT Communications. IEEE Access 2018, 6, 5766–5779. [Google Scholar] [CrossRef]
- Zhang, P.; Sun, S. One Node to Guard All: Jamming-Resistant and Low-Latency Communication for IoT. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Pomianek, A.J.; Staniec, K.; Joskiewicz, Z. Practical remarks on measurement and simulation methods to emulate the wireless channel in the reverberation chamber. Prog. Electromagn. Res. PIER 2010, 105, 49–69. [Google Scholar] [CrossRef]
- Staniec, K.; Kowal, M. LoRa performance under variable interference and heavy-multipath conditions. Wirel. Commun. Mob. Comput. 2018, 2018, 6931083. [Google Scholar] [CrossRef]
- Staniec, K.; Kucharzak, M.; Jóskiewicz, Z.; Chowański, B. Measurement-Based Investigations of the NB-IoT Downlink Performance in Fading Channels. IEEE Wirel. Commun. Lett. 2021, 10, 1780–1784. [Google Scholar] [CrossRef]
- Embit EMB-WMB169PA, EMB-WMB868 Datasheet, Embit; Revision 1.9; Italy, 2014. Available online: http://www.embit.eu/wp-content/datasheets/EMB-WMB-datasheet-latest.pdf (accessed on 4 January 2023).
- Alobaidy, H.A.; Singh, M.J.; Behjati, M.; Nordin, R.; Abdullah, N.F. Wireless Transmissions, Propagation and Channel Modelling for IoT Technologies: Applications and Challenges. IEEE Access 2022, 10, 24095–24131. [Google Scholar] [CrossRef]
- European Telecommunications Standards Institute. LTE, 5G., Study on Channel Model for Frequency Spectrum above 6 GHz (3GPP TR 38.900 Version 14.3.1 Release 14). European Telecommunications Standards Institute, ETSI TR 138 900 V14.3.1 (2017-08). 2017. Available online: http://www.etsi.org. (accessed on 28 November 2022).
- Olasupo, T.O. Propagation Modeling of IoT Devices for Deployment in Multi-level Hilly Urban Environments. In Proceedings of the 2018 IEEE 9th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 1–3 November 2018; pp. 346–352. [Google Scholar] [CrossRef]
- Callebaut, G.; Van der Perre, L. Characterization of LoRa Point-to-Point Path Loss: Measurement Campaigns and Modeling Considering Censored Data. IEEE Internet Things J. 2020, 7, 1910–1918. [Google Scholar] [CrossRef]
- Callebaut, G.; Gunnarsson, S.; Guevara, A.P.; Johansson, A.J.; Van Der Perre, L.; Tufvesson, F. Experimental Exploration of Unlicensed Sub-GHz Massive MIMO for Massive Internet-of-Things. IEEE Open J. Commun. Soc. 2021, 2, 2195–2204. [Google Scholar] [CrossRef]
- Embit Binary Interface-WMBus Specific Documentation. Revision 2.2; Embit s.r.l.: Modena, Italy, 2014.
- Moher, M.; Haykin, S. Communication Systems, 5th ed.; Wiley: Hoboken, NJ, USA, 2009; p. 448. ISBN 9780471697909. [Google Scholar]
- ITU. ITU-R P.1407-1; Multipath Propagation and Parameterization of Its Characteristics. Available online: https://www.itu.int/rec/T-REC-X.1407-202201-I (accessed on 4 January 2023).
- Saunders, S.R.; Aragón-Zavala, A. Antennas and Propagation for Wireless Communications Systems, 2nd ed.; John Wiley & Sons Ltd.: New York, NY, USA, 2007. [Google Scholar]
- Hill, D.A. Electromagnetic Fields in Cavities: Deterministic and Statistical Theories. In The IEEE Press Series on Electromagnetic Wave Theory; John Wiley & Sons Inc.: Hoboken, NJ, USA, 2009. [Google Scholar]
- IEC 61000-4-21; Electromagnetic Compatibility (EMC) Part 4: Testing and Measurement Techniques Reverberation Chamber Test Methods; Section 21: Reverberation Chamber Test Methods. International Standard: Geneva, Switzerland, 2011.



| Min | Typ. | Max | Unit | Note | |
|---|---|---|---|---|---|
| RF Frequency Range | 169.400 | 169.475 | MHz | ||
| Frequency Tolerance | 3.5 | ppm | Excluding ageing typ. ±1 ppm/year | ||
| RF Data Rate | 0 | 200 | kbps | ||
| Programmable Output Power Range | −7 | +27 | dBm | Std. Conditions: 3.3 V 25 °C | |
| Rx Bandwidth (BW) | 8 | 200 | kHz | ||
| Receiver Sensitivity 4.8 kbps GFSK | −117 | dBm | |||
| RF Input Saturation | +10 | dBm | |||
| Blocking | As specified in EN 300 220 | ||||
| ±2 MHz | 78 | dB | |||
| ±10 MHz | 81 | dB |
| Min | Typ. | Max | Unit | Note | |
|---|---|---|---|---|---|
| RF Frequency Range | 868.000 | 869.650 | MHz | subband g1, g2, g3 | |
| Frequency Tolerance | 15 | ppm | ±15 ppm over temperature range | ||
| RF Data Rate | 0 | 200 | kbps | ||
| Programmable Output Power Range | −7 | +15 | dBm | Std. Conditions: 3.3 V 25 °C | |
| Rx Bandwidth (BW) | 8 | 200 | kHz | ||
| Receiver Sensitivity 4.8 kbps GFSK | −117 | dBm | |||
| RF Input Saturation | +10 | dBm | |||
| Blocking | As specified in ETSI EN 300 220 | ||||
| ±2 MHz | TBD | TBD | |||
| ±10 MHz | TBD | TBD |
| CH no. | WMBus Mode | WMBus ch. Name | Center Freq. [MHz] | Modulation | Data Rate [kbps] | FSK Deviation [kHz] |
|---|---|---|---|---|---|---|
| 3 | N | N1c, N2c (CEPT 2a) | 169.4313 | GFSK | 2.4 | ±2.4 |
| 1 | N | N1a, N2a (CEPT 1a) | 169.4063 | GFSK | 4.8 | ±2.4 |
| 7 | N | N2g (CEPT 0) | 169.4375 | 4-GFSK | 19.2 | −7.2, −2.4 +2.4, +7.2 |
| 18 | reserved | R2 | 868.33 | FSK | 4.8 | ±6 |
| 23 | S (short preamble) | S | 868.3 | FSK | 16.384 | ±50 |
| 24 | S (long preamble) | S | 868.3 | FSK | 16.384 | ±50 |
| 37 | C | Other channel | 868.95 | FSK | 100 | ±45 |
| 38 | C | Other channel | 869.525 | GFSK | 50 | ±25 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kowal, M.; Staniec, K. Investigations of the Wireless M-Bus System Resilience under Challenging Propagation Conditions. Electronics 2023, 12, 907. https://doi.org/10.3390/electronics12040907
Kowal M, Staniec K. Investigations of the Wireless M-Bus System Resilience under Challenging Propagation Conditions. Electronics. 2023; 12(4):907. https://doi.org/10.3390/electronics12040907
Chicago/Turabian StyleKowal, Michal, and Kamil Staniec. 2023. "Investigations of the Wireless M-Bus System Resilience under Challenging Propagation Conditions" Electronics 12, no. 4: 907. https://doi.org/10.3390/electronics12040907
APA StyleKowal, M., & Staniec, K. (2023). Investigations of the Wireless M-Bus System Resilience under Challenging Propagation Conditions. Electronics, 12(4), 907. https://doi.org/10.3390/electronics12040907







