Abstract
The Internet of things (IoT) is on the rise, and it is increasingly becoming a ubiquitous computing service that requires large data storage and processing. Due to the limited capabilities of most IoT devices, they always rely on cloud services for storage and computing, posing security and privacy risks. Due to its significant aspects, such as data security and privacy, Blockchain (BC) has drawn significant interest in alleviating these concerns. Despite its potential benefits, Blockchain’s high complexity and limited scalability make it computationally expensive and incompatible with IoT devices requiring lightweight solutions. Although several models have been proposed for this purpose, the issue is still far from being resolved. These models have significant constraints, such as resource optimization during operation. By presenting a scalable lightweight Blockchain integrated model (LightBlock), the primary objective of this work is to enable the usage of BC in the IoT environment. LightBlock is implemented by optimizing the components of a lightweight, scalable Blockchain. Lastly, the study’s findings should provide IoT users with a high level of security and privacy by ensuring applicability and offering end-to-end security.
1. Introduction
There have been incidents that have made it challenging to trust IoT devices. For instance, a few smart appliances and money machines have been compromised, reducing trust between consumers and businesses. Regardless of how IoT devices based on smart things offer different advantages, these technologies are not believed to be perfect in the communication network. It has been reported by a number of studies that researchers are concerned about security issues [1,2,3,4]. Several challenges are encountered by IoT devices such as data storage, memory constraints, lower power sources and capacity, limited infrastructure resources, and varying security measures and requirements.
The use of IoT is rapidly increasing and demanding massive volumes of data storage and processing. Due to the limited capability of IoT devices, they always tend to utilize cloud services from outsourced storage and computation, which has led to a series of potential threats to security and privacy. According to MyCERT, in 2018, more than 10,000 cyberattacks were recorded on corporations and individuals. Another report shockingly exposed that malicious attacks on IoT devices increased by 600% from 2016 to 2017. By 2020, analysts have estimated more than 50 billion devices will be connected globally, enormously increasing the security and privacy threats. To mitigate these fears, Blockchain has received extensive attention due to its prominent characteristics including data security and privacy. Despite the potential benefits, the high complexity and limited scalability of Blockchain make it computationally expensive, which cannot meet the requirements of IoT devices with lightweight solutions.
Although several models such as ELIB [5], Thinkey [6], LHBA [7], LSB [8], SH-BlockCC [9], ASAM [10], and OptChain [11] have been proposed to address the aforementioned limitations, the provided solutions are in an early stage, and major investigations need to be conducted. These models suffer from significant issues, such as resource optimization during operation, which significantly impact the models’ lightweight and scalable characteristics such as low overheads, sufficient bandwidth, and affordable memory usage and energy consumption by IoT devices. However, their findings can be used to propose a more effective model for addressing IoT challenges. ELIB [5] and LSB [8] focused on the consensus algorithm and throughput management to improve scalability and produce a lightweight Blockchain. In contrast, Thinkey [6], SH-BlockCC [9], and ASAM [10] concentrated on Blockchain architecture by proposing an efficient network topology and lightweight cryptographic approach. Lastly, LHBA [7] stressed the development of an adaptable cryptographic algorithm to assure the security and lightweight nature of Blockchain transactions. Only LSB [8] has investigated incorporating protection measures against existing Blockchain attacks to ensure that this lightweight nature does not compromise the security level. However, LSB [8] has a significant drawback in that the impact of network topology and cryptography methods on the lightweight and scalable qualities were not examined.
This study aims to propose a scalable lightweight Blockchain integrated model (LightBlock) to enable the use of Blockchain in the context of the IoT. LightBlock is carried out by optimizing the components that constitute a scalable lightweight Blockchain, strengthening the security by undertaking a qualitative analysis against all existing attacks, verifying the applicability onto IoT applications through a case study, and finally evaluating performance and security level through simulation scenarios. Results from the study should be able to bring a high level of security and privacy for IoT users by ensuring the applicability and providing end-to-end security. To do so, several potential solutions are proposed to optimize the components, such as scalable Blockchain architecture (SBA), lightweight consensus algorithm (LCA), changeable cryptographic function (CCF), and throughput management scheme (TMS) to integrate them into a single model. A list of Blockchain attacks is identified, and countermeasures are incorporated into the model to strengthen its security and privacy.
This paper consists of eight sections. Section 2 reviews the literature. Section 3 explores Blockchain’s scalability challenges. In Section 4, we introduce the research methodology of this paper. Section 5 and Section 6 discuss the conceptual model and the model development, respectively. Section 7 presents the results and discussion, and Section 8 concludes the paper.
2. Literature Review
By connecting billions of electronic sensors and control components to interconnected frameworks, the Internet of things (IoT) can be coordinated to improve efficiency, increase crucial convenience, and advance ways of living for every person on Earth. The effect will be felt across all IoT domains [12]. However, incidents have made it difficult to trust IoT devices. Investigations have demonstrated that security issues are the main concern as the volume of information supplied by many sensors grows steadily [13,14]. Sensors typically have limited storage, memory, and power management capabilities. Information security and protection are the main issues. Analysts have suggested potential future endeavors to overcome the obstacles by developing a lightweight security solution for IoT devices. The phrase lightweight does not imply a weak implementation but rather coherent algorithms with minimal overhead needs [2,15,16].
Although addressing security for IoT can be performed in different ways such as using physical layer security [17,18,19], Blockchain (BC) is more popular in the context of IoT [20,21]. BC is a digital ledger of transactions used for data storage and networked data sharing. The data potential consists of currencies (such as bitcoin), contracts (such as Ethereum), and personal data. Due to its high security and privacy, BC has attracted the attention of academics and practitioners in recent years. It is utilized in over 27 industries and distributes a digital ledger of transactions to all network nodes. To establish a new block, all nodes must confirm and accept it, eliminating the need for a central controlling node; this attribute is crucial in BC. Adding new blocks requires solving puzzles (hard to solve), which is easy to verify. Multiple consensus algorithms solve this puzzle by mining and adding a new block to the chain. The mining process happens in all nodes on the network. Therefore, BC can be utilized in numerous fields to ensure high security and privacy. BC can be used to provide high security and privacy for devices connected to the Internet (IoT devices). These devices are still using conventional cryptography due to many challenges:
- (a)
- Consumption of resources: Most IoT devices have limited resources, processes, bandwidth, and storage. These restrictions are inconvenient for complex security.
- (b)
- Centralization: Most devices rely on centralized communication models in which all devices are identified, authenticated, and linked via cloud servers. Consequently, any malfunction at this stage can bring the network to a halt.
- (c)
- Lack of privacy: The devices and communications are secured using conventional privacy measures.
On the other hand, there are several challenges to implementing BC in IoT:
- (a)
- Complex consensus algorithms: The algorithms utilized in BC (POW and POS) require significant computation.
- (b)
- Scalability and overhead: In BC, all new blocks are delivered to all nodes for verification, which boosts network scalability and overload.
- (c)
- Latency: It often takes time for nodes to confirm and add a new block. However, in IoT, there should be no waiting or delay for sent information.
- (d)
- Throughput: The number of transactions to be implemented and stored. In BC, transactions are limited (e.g., seven per second for Bitcoin), which is inconvenient for IoT because it involves swift transactions.
In the past several years, numerous attempts have been made to mitigate the complexity of BC and investigate the viability of implementing it on IoT/Smart devices; these studies are summarized in Table 1.

Table 1.
Findings of previous studies.
In addition to the studies presented in Table 2, several models, including ELIB [5], Thinkey [6], LHBA [7], LSB [8], SH-BlockCC [9], ASAM [10], and OptChain [11], have mainly worked to develop a lightweight Blockchain for IoT devices. These models have addressed various ways for components of a system to be lightweight and scalable. For example, scalable Blockchain architecture (SBA), lightweight consensus algorithm (LCA), variable cryptographic function (CCF), and throughput management scheme (TMS) are the constituents of TMS. Table 2 outlines various models’ utilized components and evaluation methodologies for developing a scalable, lightweight Blockchain. Although these models provided new ideas, the problem is far from being resolved; however, their insights can be used to suggest a superior solution that can effectively fulfill IoT requirements.

Table 2.
Comparison between literature models.
To recap, security and energy efficiency are considered basic needs for any networking-based system such as the IoT, and satellite communications [19]. Thus, this study targets lightweight Blockchain to achieve efficiency and security.
3. Scalability Challenges
This section comprehensively investigates the potential scalability outcomes of Blockchain-based innovation. The investigation examines the limitations of various Blockchain stages and system elements such as throughput, latency, block size, and network impacts on a peer-to-peer system’s effectiveness, security, and energy consumption. Blockchain has become well known for facilitating third-party involvement in exchanges and transactions. Blockchain is the technology that enables the use of digital currencies. It attracts the attention of specialists, academics, and various Blockchain highlights. The adaptability issue can be categorized as throughput, cost, limit, and systems networking. Scalability is affected by variables such as block size and block interval duration, which can also weaken the system’s security. If the framework’s scalability is changed indiscriminately, it may become vulnerable to numerous types of attacks
3.1. Blockchain Scalability
Blockchain was created to develop a system without a central point where each hub has equal rights. However, in any case, is there a central government? In this system, how does everything happen? Each hub confirms the payment and incorporates nearly all data into its circulated log. As a result, the specific number of hubs grows, making the approval procedure increasingly complicated and slow. Many believe that Blockchain’s scalability difficulties should be resolved because a decentralized society is constantly evolving and equipped to serve various areas by replacing the fiat payment structure.
Furthermore, a Blockchain-based payment architecture saves clients time and money while providing security. Unfortunately, this is not a straightforward problem to tackle. Instead, many people from the crypto network, including engineers, miners, partners, and others, should support each decision. It will take time and effort to modify the entire framework. This is why, by all accounts, many elective options appear to address this problematic issue.
3.2. Scalability Bottlenecks
Before defining and identifying the bottleneck variables affecting scalability, it is essential to understand that scalability is not a specific concept. Instead, it is a collection of several parameters and measures. For example, linking a single variable to many variables influencing execution and scalability is difficult.
Currently, the Blockchain protocol restricts the block size to a maximum of 1 MB. The best method to achieve this is by increasing the Bitcoin block size limit. To comply with current payment processors, researchers anticipate a piece size of approximately 8 GB, contrary to the 1 MB piece size estimated. This would involve around 400 terabytes of data. The increase of the block size may affect scalability measures within the Bitcoin-based Blockchain protocol system [31,32] as follows:
- Throughput—If the block size is increased, the number of transactions processed per second will increase. The throughput of the entire bitcoin Blockchain protocol infrastructure will also be enhanced.
- Massive capacity—Rendering the block size within the Blockchain protocol would pave the way for transferring and managing enormous data amounts. For instance, experts anticipate that an increase in block size to 8 GB would facilitate the management of approximately 400 TB of data.
- Lower transaction charges—Increasing the block size would free up a massive amount of space for additional transactions to be included in each block. Moreover, all Bitcoin competitors will be required to reduce their exchange fees.
- Scalability enhancement—The increase in block size will considerably improve the scalability of the Bitcoin-based Blockchain organization due to the increased throughput and productivity caused by the development of the system’s number of exchanges.
There are two distinct approaches to layer 1 scalability to handle the increasing workload:
- Horizontal scalability: The process of adding more hubs to a system.
- Vertical scalability: Adding extra capacity to the system’s machines.
Improving scalability via improved blocks has disadvantages. First, it takes more work from the system’s hubs, which prevents less capable PCs (the majority of close-to-home devices) from functioning in the network. Therefore, vertical scaling results in fewer authorized hubs, which suggests increasingly centralized mining and more potent hub operators. Initial vertical scalability layer: Scalability arrangements compromise two of Blockchain technology’s three key tenants: speed, security, and decentralization. It is unimaginable to expect to scale the primary layer and do all three tasks simultaneously. The increase in block size raises the hardware requirements for full hubs. This indicates that fewer PCs will be innovative enough to be interested in the system. A Blockchain becomes increasingly decentralized and safe when there are more validator hubs. A lower number of validator hubs leads to greater centralization and instability.
Layer 2 solutions are another scaling option. On top of the layer, these are based on a secure Blockchain foundation layer. They can achieve high throughput without compromising security. However, level 1 scaling methods reduce security and increase system centralization by limiting the number of system nodes. Instead, layer 2 solutions ignore the foundational layer (such as the Bitcoin and Ethereum Glockchains) and build protocols. These are only slightly less secure and provide increased throughput. Therefore, maintaining a secure foundation layer is essential for layer two solutions to function. On top of a dependable base layer, an unreliable or protected layer can be created. However, a secure layer cannot be constructed on a weak foundation. These solutions make the Blockchain more useful for a broader range of applications while preserving its core ideals of decentralization and security.
3.3. Example Scenario of Blockchain Top layer: Overlay Network
An overlay network is a computer network built on top of another network. The nodes in the overlay network can be thought of as being linked by virtual or consistent links. Each node corresponds to a path in the hidden network, sometimes via several physical connections. Peer-to-peer networks and other distributed frameworks are overlaid on top of their Internet hubs. Consequently, the Internet was initially implemented as an overlay on the phone network, whereas the phone network is gradually transitioning into an Internet-based overlay network via voice over IP (VoIP).
Blockchain’s virtual network comprises ITS foundation and service provisioning layer components. The use of overlay ensures that the current information communicates while the inheritance service remains unaffected. On the basis of the capabilities of hubs in the ITS framework and service provisioning layer, as well as their varied tiered topological associations, two types of Blockchain hubs comprising three types of interoperable chains are provided. Encryption and decryption of the information in the blocks are also performed at the Blockchain’s vehicular level to maintain the security and confidentiality of data. Below is an illustration of how the network layer operates.
4. Methodology
As depicted in Figure 1, the development methodology consists of distinct phases comparable to the approach [27].
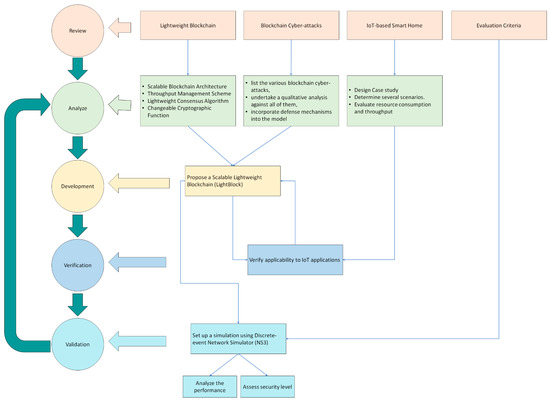
Figure 1.
Development methodology.
- A.
- Review Phase
We conduct a comprehensive review of existing IoT applications and Blockchain studies to (a) identify the lightweight Blockchain requirements that meet IoT devices’ capability, (b) study and analyze existing models, highlight strengths and weaknesses, and adopt useful elements to build a scalable, lightweight Blockchain, and (c) survey existing Blockchain cyberattacks and determine possible defense mechanisms.
- B.
- Analysis Phase
A complete assessment of existing IoT applications and Blockchain research is conducted to (a) determine the Blockchain needs for lightweight IoT devices, (b) examine and assess existing models, highlighting their merits and limitations and adopting beneficial components to create a scalable, lightweight Blockchain, and (c) examine existing Blockchain-based cyberattacks and identify potential defense solutions.
- C.
- Development Phase
We propose a scalable lightweight Blockchain integrated model (LightBlock). Four optimizations, namely, the scalable Blockchain architecture (SBA), lightweight consensus algorithm (LCA), and throughput management scheme (TMS), are applied to the development of LightBlock. Each component is examined independently.
- (a)
- Scalable Blockchain architecture (SBA): The implementation includes network topologies such as the star topology, bus topology, ring topology, and mesh topology. The combination of various topologies is to see which is best to support high scalability, low overhead, and fast processing time. The multiple star topology architecture may be a viable approach in which each star topology network consists of numerous nodes connected to a hub that can communicate with a hub connected to another node. In turn, this decreases the direct interaction between nodes, which causes latency and overhead. This architecture generates a decentralized process that supports the Blockchain’s nature.
- (b)
- Lightweight consensus algorithm (LCA): Several consensus algorithms have been identified, such as PoW, PoS, BFT, TCON, and DTC. The distributed time-based consensus (DTC) provides a more lightweight solution than others but with fewer than 100 transactions per second. Meanwhile, proof-of-work (PoW) provides nine transactions per second. In addition, a thorough analysis of DTC was conducted to increase the number of transactions by simplifying the mining process validation of transactions and new blocks.
- (c)
- Changeable cryptographic function (CCF): An examination of Blockchain’s existing hash functions, including QUARK, PHOTON, and SPONGENT to propose a new changeable hash-based CCF. A cryptographic function that can adjust the hash algorithm used for mining network traffic based on the security level of each transaction. High-security hashes increase the algorithm’s complexity, and, since not all transactions require high security, the hash function can be altered to optimize the operation. This optimization can significantly improve throughput.
- (d)
- Throughput management scheme (TMS): When the number of transactions exceeds the limit, it will be placed in a queue. However, some transactions cannot wait since they must be completed immediately. In this case, we must prioritize the transactions to control the throughput.
- D.
- Verification Phase
- (a)
- Improve LightBlock security resilience: Incorporate the potential defense mechanisms into the LightBlock model to provide security resilience.
- (b)
- Verify applicability to IoT applications by evaluating resource consumption and throughput: We undertake a case study on smart houses to demonstrate the efficiency and usability of LightBlock for IoT applications. Several scenarios will be analyzed to demonstrate the primary characteristics, such as minimal resource utilization and high throughput. We presume that the smart house is equipped with various Internet of things devices, such as smart sensors, smart locks, and smart lights. In addition, IoT devices with significantly varying capacities are now commercially available, such as Amazon Echo, which has abundant resources, and motion sensors with limited resources.
- E.
- Validation Phase
- (a)
- A simulation using a discrete-event network simulator (NS3) is conducted to analyze performance and assess the security level.
- (b)
- The performance of LightBlock is analyzed with respect to several predefined evaluation characteristics, including latency, processing time, bandwidth overhead, and scalability.
- (c)
- LightBlock’s security levels are evaluated.
5. The Conceptual Model
The lightweight Blockchain study aims to design and standardize robust procedures and practices for the contexts in which they operate. According to Table 2, no model meets all criteria. Thus, we propose a methodology to optimize and integrate the four components, SBA, LCA, GCCF, and TMS, while including defenses against known Blockchain threats. Once the model is complete, the applicability to IoT applications is validated by evaluating resource consumption and throughput using a smart home case study. In this case study, the Smart devices connected over the Internet as an IoT representative to ensure a low applicability of resource consumption and high throughput. The discrete-event network simulator is used to conduct simulation research to evaluate performance (by analyzing latency, processing time, bandwidth overhead, and scalability) and security level (through evaluating denial of service, dropping attack, and Blockchain attack). A conceptual model that highlights the four essential topics of this paper is depicted in Figure 2.
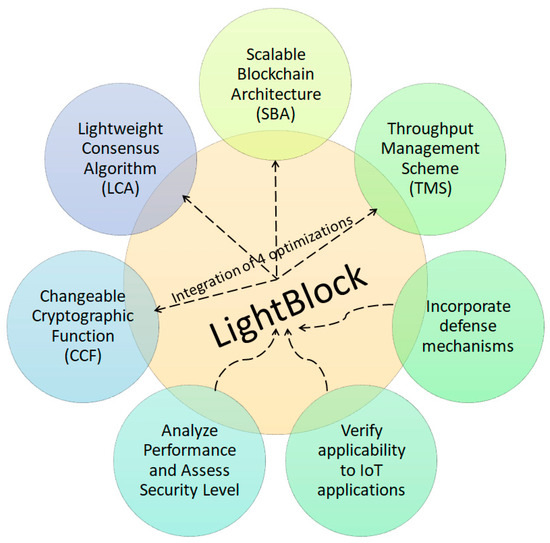
Figure 2.
Conceptual model.
6. Model Development
The critical components of the hash-based blockchain network architecture are the storage and cell nodes, which are executed between the control layer and field layer. During the block mining process, it creates a block utilizing data acquired from smart devices, which is sent to other Blockchain nodes for Blockchain authentication. After the authentication process, each node participating in the block authentication process will send a return message to the storage node containing the authenticated results. The block update is then processed according to the system’s specifications. The hash function has so many safety and security aspects. For instance, the process storage node is accountable for the authenticated block during the block update. The hash function is selected primarily by examining a threshold or a varying number of transactions. Here, throughput is defined as the number of completed Blockchain transactions per second. In any consensus method, Blockchain mining transactions cause system latency. Therefore, it is difficult for authenticators to execute the consensus process and satisfy the present Blockchain technology need.
Initially, we generate a hash list using LW hash manager, which mainly employs hash functions to prevent mining. The Purdue model is provided for this design, in which the field layer corresponds to levels 0 and 1. In this case, the control layer corresponds to level 2, and the cell node forms a block to authenticate data collected from connected devices. After validation, data are returned to the storage node, and the block is subsequently modified. The storage node is primarily responsible for managing block changes and the ledger.
In the simulation, different hash modules are executed by hardware, and their processing times are compared. If the hash function is implemented differently, the processing time is proportional to the number of modules executed in parallel. For example, when the hash module is invoked, the stimulated processing time is around 2 s. The execution of the parallel hash function incurs additional expenses due to the increase in necessary storage space. When the hash function is executed in parallel, its module simultaneously calculates the hash value, satisfying the mining process’s constraints. Each hash module requires equal processing power. To lessen the computational overhead of the consensus mechanism, we choose a lightweight hash function. These hash functions are carried out in a confined space. For instance, if the rate of transaction grows as the network traffic increases. The cell nodes replace the hash function with one with higher throughput, decreasing its security level. This also lessens the delay associated with mining and updating.
Figure 3 depicts the suggested architecture and a general grasp of the architecture. In the simulation, smart contract modules are executed by hardware, and their processing times are compared. The smart contract is programmed as the Blockchain layer. A Python script delivers data from things with relevant information, such as chain ID, nonce, gas, user ID, and receiver ID once the node negotiates with the smart contract. A gas fee is a Blockchain transaction fee, which the Blockchain network validators receive for their services to the Blockchain as part of each transaction. The Ethereum Blockchain uses computational resources to process every transaction. Data are signed by the server using the private key to assure data accuracy. If the hash function is implemented differently, the processing time is proportional to the number of modules executed in parallel. For example, when the hash module is invoked, the stimulated processing time is around 2 s. The execution of the parallel hash function incurs additional expenses due to the increase in necessary storage space. When the hash function is executed in parallel, its module simultaneously calculates the hash value, satisfying the mining process’s constraints. Each hash module requires equal processing power. To lessen the computational overhead of the consensus mechanism, we choose a lightweight hash function. These hash functions are carried out in a confined space. For instance, if the rate of the transaction grows as network traffic increases, the cell nodes replace the hash function with one with higher throughput, decreasing its security level. This also lessens the delay associated with mining and updating.
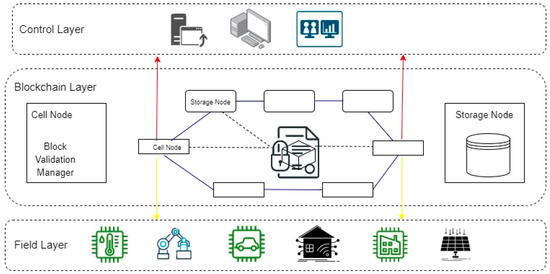
Figure 3.
Hash-based Blockchain architecture.
Using this framework facilitates network traffic monitoring. As a result of the simulation, the dataset with the highest throughput value for each DoS may be simply determined. This large dataset includes network traffic and attack datasets. Therefore, using the Message Queuing Telemetry Transport (MQTT) protocol, machine-to-machine interaction can be accomplished with a simple data transmission. Because MQTT’s 2 byte fixed header can handle applications with low bandwidths, limited computational power, minimal memory, and low batteries, which are frequent in IoT applications, it is suitable for IoT applications.
The IoT device, the device owner, the MQTT broker, and the clients are shown in Figure 4 as the major system participants. The system is made up of contract code written in Solidity language and stored on the Ethereum Blockchain, which enables a device owner to specify the criteria and guidelines for automating the sale of the IoT device’s data. Without requiring the assistance of a reliable third party to handle the exchange of payments, an interested client can engage with and contact the contract to access and utilize the data in real time.
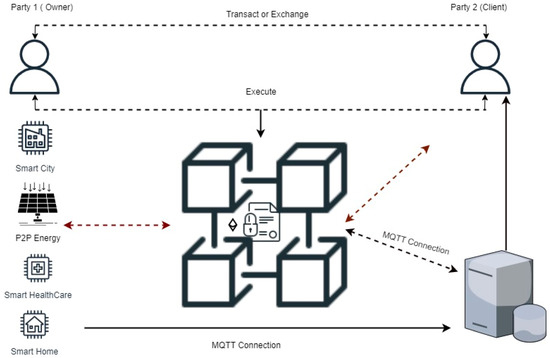
Figure 4.
IoT topology overview of using smart contract.
An MQTT broker housed in the cloud compiles and gathers the data produced by the Internet of things device. According to the figure, the MQTT broker is ideally housed in a cloud environment to ensure its dependability, scalability, availability, and low-latency accessibility to all clients globally. A publish/subscribe protocol is used by MQTT broker to gather and access the data. IoT devices frequently employ the highly lightweight communications protocol MQTT.
Using this framework facilitates network traffic monitoring. As a result of the simulation, the dataset with the highest throughput value for each DoS may be simply determined. This large dataset includes network traffic and attack datasets. Figure 5 depicts the hash function-related cell node and storage node presented in the process flow.
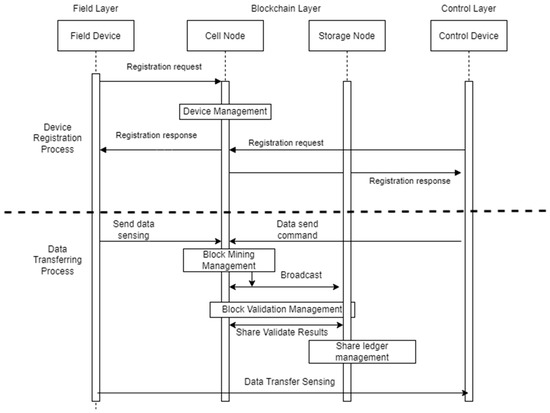
Figure 5.
Proposed architecture interaction process.
The record protocol of the hash work Blockchain system is applied primarily to secure the session’s data. The alert protocol, on the other hand, warns the user and system networks when threats arise across other protocols. The authentication process of arbitrary users results in a security vulnerability, whereby threats can present a fake server certificate and obtain all sensitive data from the end-user and network system. Blockchain with hash computation reduces hardware costs and electricity maintenance. In addition, it prevents the inefficient utilization of CPU resources. The hardware independence and encapsulation properties of virtualization enhance business continuity and availability. For example, IoT Blockchain enables using several operating systems and application types on the same hardware, for instance. All nodes inside the Blockchain infrastructure share the same hardware resources, and the performance parameters are monitored to ensure the system’s operation. Table 3 displays various functionalities with brief explanations and the corresponding functional component.

Table 3.
Function and related components of cell node.
7. Results and Discussion
In the proposed Blockchain architecture, a scenario where the smart contract function is redundantly constructed for parallel computing was simulated. In terms of CPU and memory usage, this section offers the performance evaluation of the suggested architecture for the various consensus methods, including PoW and PoS. To check if Ethereum is compatible with IoT and to decide which consensus algorithm is better suited for the situation when things have limited resources. In terms of tamper-free confidentiality, integrity, and availability, the suggested architecture meets the security requirements. The user is able to safeguard their private keys so that they can only transmit and manage data over a network.
The beginning shows the layers of testing for a new device: inquiry, block mining, block validation, block update, and exit. This is the initial step in device registration. The block update management task is carried out at the storage node following block validation. The storage node examines its capacity to see if there is enough space to attach the validated block. The validated block will be added to the ledger.
Each user request generates a check block. A distributed control authenticator validates the checking block. The completion of the authentication enables joining the Blockchain network. The decentralized Blockchain technology distributed ledger allows all hash functions with details. The availability of resources and authentication with new hash-based block functions make new block authorization possible. The availability of resources is maintained for newly permitted blocks. Figure 6 depicts the simulation testing procedure before and after fault tolerance.
Figure 6.
The process of simulation testing fault tolerance.
The first block is known as the header block and contains the hash value of the following block. The second block includes the IoT device ID, the detected value, the data, and the block’s hash value. If this is the final block, the hash value remains undefined or 0.
However, the NS-3 simulator was used for the simulation, which can accurately represent the real environment. React.JS is an open-source tool used to build user interfaces for web apps, which has Ganache GUI and MetaMask integrated. The smart contract was deployed on the local Ethereum Blockchain.
An overview of the Ganache GUI, a local Ethereum Blockchain that was used in this research, is shown in Figure 7. Each account’s digital address is illustrated with 100 ETHs in each account. Additionally, each account is linked to a distinct private key that guarantees the security of the wallet. Furthermore, 16 blocks are created in response to various trading actions carried out employing the web interface. The address where the smart contract is deployed is shown in the block 16 information (Figure 8).
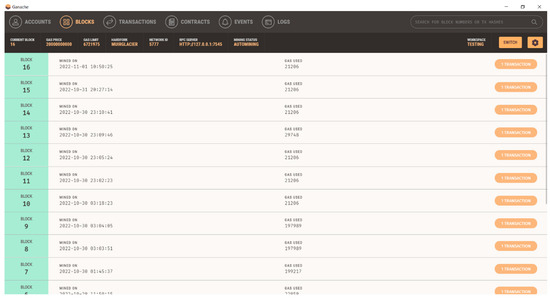
Figure 7.
Blockchain transaction status on the server.
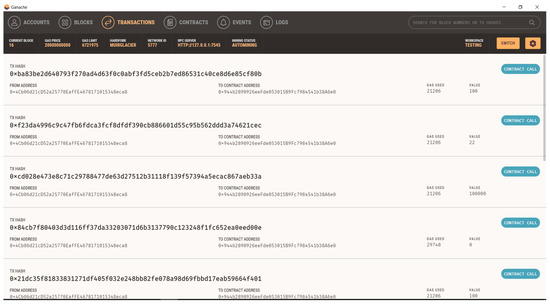
Figure 8.
Details of block 16 on the Blockchain server.
In Figure 9, only a few transactions per block might have negatively affected throughput. However, when there were 10 transactions per block, the throughput increased quickly and the performance boost started to decrease. With this network configuration, the maximum throughput of 350 tps resulted in approximately 100 transactions per block.
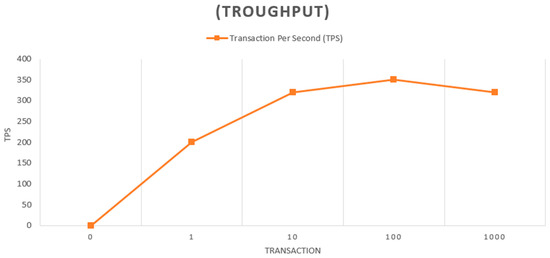
Figure 9.
Throughput.
Figure 10 displays the results, plotted using Excel, of the variance in the size of the Blockchain’s state database in megabytes (real size, sstorage, in blue), and size on disc, dsstorage, in orange). The results indicate that the size rise of the state database was almost linear for a range of 5–600 product record simulations. These outcomes are within the anticipated range while taking into account the constant size of the simulated product records. The number of transactions created in the database, which consists of blocks, is probably much higher than what would happen in a full Ethereum Blockchain node. This is most likely because ganache-cli mines a block for every transaction. The disc space utilized by the state database in an actual Blockchain node with proper mining should be significantly closer to the actual data size values.
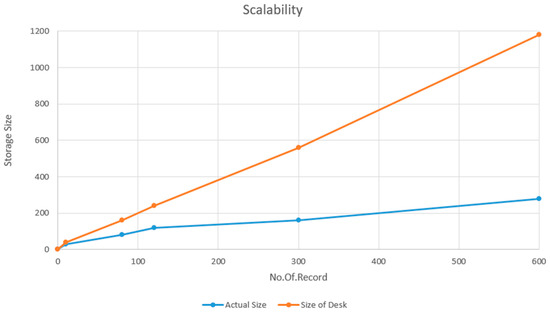
Figure 10.
Scalability.
Figure 11 indicates that, due to duplicate mining operations and the expense of distributing blocks between nodes, PoW uses the CPU and memory at its highest rates. Because of the lightweight nature of IoT devices, PoW is not practicable. Since PoS does not depend on high computing capacity, it generates significantly fewer results than PoW. The block confirmation time is considerably shortened in PoS, which results in a lower amount of energy used. However, it was discovered that, as traffic grows, PoW becomes overloaded and packet loss rises. In this regard, PoS may be a more beneficial and compact alternative than PoW for IoT applications due to its constrained resources.
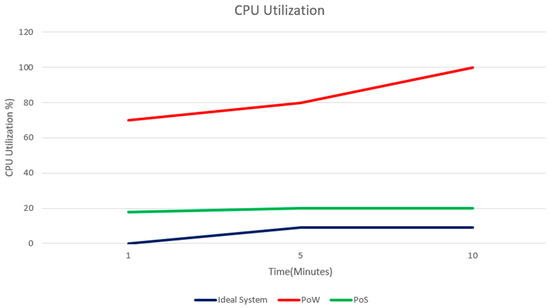
Figure 11.
CPU utilization.
8. Conclusions
This paper proposed a scalable lightweight Blockchain (LightBlock); this model can attract those who provide IoT services over the public cloud, e.g., managing smart homes remotely by offering a solid security and privacy solution for their customers to convene these services. Results from this study can bring a high level of security and privacy for IoT users, especially those who utilize cloud-based services. Thus, this study can support the realization of the national Internet of things (IoT) by providing end-to-end security over the Internet/public cloud and can meet IoT devices’ limited capability.
The proposed Blockchain architecture can modify the Blockchain’s hash function on the basis of the volume of transactions, thereby enhancing the availability of Blockchain networks. The hash function is better regarding implementation, power consumption, and throughput. This hash function assures cryptographic security and is executed in a minimal amount of space on IoT devices. Due to the hash function, every data block is linked by a flexible hash chain, which decreases the latency of the computational burden. This strategy can increase the network’s scalability when generating a more lightweight hash function. In addition, the proposed architecture can be implemented on devices with less than 1 s latency. Our proposed model achieves a high usage level and optimizes energy consumption by utilizing a hash-based lightweight Blockchain, which lowers data redundancy and storage issues.
Author Contributions
Conceptualization, M.G. and M.A.M.; methodology, M.G. and M.A.M.; formal analysis, M.G.; resources, R.R.; writing—original draft preparation, M.G. and F.H.F.; writing—review and editing, M.A.M., K.A.B. and R.R.; supervision, M.A.M.; project administration, M.A.M.; funding acquisition, R.R. All authors have read and agreed to the published version of the manuscript.
Funding
Authors wish to thank the Ministry of Education of Malaysia (MOE) for providing the research grant with code FRGS/1/2020/ICT07/UNITEN/02/1 to support this research.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Biswas, J.; Wai, A.A.P.; Tolstikov, A.; Hong, K.L.J.; Shankar, S.J.; Fook, V.F.S.; Yen, L.V.; Phua, C.; Jiaqi, Z.; Hoa, H.T.; et al. From context to micro-context–issues and challenges in sensorizing smart spaces for assistive living. Procedia Comput. Sci. 2015, 5, 288–295. [Google Scholar] [CrossRef]
- Sanchez, I.; Satta, R.; Fovino, I.N.; Baldini, G.; Steri, G.; Shaw, D.; Ciardulli, A. Privacy leakages in smart home wireless technologies. In Proceedings of the 2014 International Carnahan Conference on Security Technology (ICCST), Rome, Italy, 13–16 October 2014; pp. 1–6. [Google Scholar]
- Ukil, A.; Bandyopadhyay, S.; Pal, A. Privacy for IoT: Involuntary privacy enablement for smart energy systems. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 536–541. [Google Scholar]
- Kim, Y.-P.; Yoo, S.; Yoo, C. DAoT: Dynamic and energy-aware authentication for smart home appliances in internet of things. In Proceedings of the 2015 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 9–12 January 2015; pp. 196–197. [Google Scholar]
- Mohanty, S.N.; Ramya, K.; Rani, S.S.; Gupta, D.; Shankar, K.; Lakshmanaprabu, S.; Khanna, A. An efficient Lightweight integrated Blockchain (ELIB) model for IoT security and privacy. Futur. Gener. Comput. Syst. 2019, 102, 1027–1037. [Google Scholar] [CrossRef]
- Chen, S.; Dai, W.; Dai, Y.; Fu, H.; Gao, Y.; Guo, J.; He, H.; Liu, Y. A Scalable Blockchain Architecture. arXiv 2019, arXiv:1904.04560. [Google Scholar]
- Seok, B.; Park, J.; Park, J.H. A lightweight hash-based blockchain architecture for industrial IoT. Appl. Sci. 2018, 9, 3740. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. LSB: A Lightweight Scalable Blockchain for IoT security and anonymity. J. Parallel Distrib. Comput. 2019, 134, 180–197. [Google Scholar] [CrossRef]
- Singh, S.; Ra, I.H.; Meng, W.; Kaur, M.; Cho, G.H. SH-BlockCC: A secure and efficient Internet of things smart home architecture based on cloud computing and blockchain technology. Int. J. Distrib. Sens. Netw. 2019, 15, 155014771984415. [Google Scholar] [CrossRef]
- Novo, O. Blockchain Meets IoT: An Architecture for Scalable Access Management in IoT. IEEE Internet Things J. 2018, 5, 1184–1195. [Google Scholar] [CrossRef]
- Nguyen, L.N.; Nguyen, T.D.; Dinh, T.N.; Thai, M.T. OptChain: Optimal transactions placement for scalable blockchain sharding. In Proceedings of the 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–9 July 2019; pp. 525–535. [Google Scholar]
- Dohr, G.S.A.; Modre-opsrian, R.; Drobics, M.; Hayn, D. The Internet of Things for ambient assisted living. In Proceedings of the 2010 Seventh International Conference on Information Technology: New Generations, Las Vegas, NV, USA, 12–14 April 2010; Volume 29, pp. 133–140. [Google Scholar]
- Wahdain, E.A.; Baharudin, A.S. Big Data Analytics in the Malaysian Public Sector: The Determinants of Value Creation; Springer International Publishing: Berlin/Heidelberg, Germany, 2018; Volume 2. [Google Scholar]
- Giuffrida, N.; Fajardo-Calderin, J.; Masegosa, A.D.; Werner, F.; Steudter, M.; Pilla, F. Optimization and Machine Learning Applied to Last-Mile Logistics: A Review. Sustainability 2022, 14(9), 5329. [Google Scholar] [CrossRef]
- Yang, C.; Yuan, B.; Tian, Y.; Feng, Z.; Mao, W. A smart home architecture based on resource name service. In Proceedings of the 2014 IEEE 17th International Conference on Computational Science and Engineering, Chengdu, China, 19–21 December 2014. [Google Scholar]
- Bhide, V.H.; Wagh, S. I-learningIoT: An intelligent self learning system for home automation using IoT. In Proceedings of the Communications and Signal Processing (ICCSP), Chengdu, China, 10–11 October 2015; pp. 1763–1767. [Google Scholar]
- Lin, Z.; Niu, H.; An, K.; Wang, Y.; Zheng, G.; Chatzinotas, S.; Hu, Y. Refracting RIS-Aided Hybrid Satellite-Terrestrial Relay Networks: Joint Beamforming Design and Optimization. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 3717–3724. [Google Scholar] [CrossRef]
- An, K.; Lin, M.; Ouyang, J.; Zhu, W.-P. Secure Transmission in Cognitive Satellite Terrestrial Networks. IEEE J. Sel. Areas Commun. 2016, 34, 3025–3037. [Google Scholar] [CrossRef]
- Lin, Z.; An, K.; Niu, H.; Hu, Y.; Chatzinotas, S.; Zheng, G.; Wang, J. SLNR-based Secure Energy Efficient Beamforming in Multibeam Satellite Systems. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 1–4. [Google Scholar] [CrossRef]
- Gurunathan, M.; Mahmoud, M.A.; Mahdi, M.N. A Systematic Review on the Challenges of Adopting Advanced Security Solutions onto IoT-Based Smart Devices. J. Theor. Appl. Inf. Technol. 2022, 100, 4117. [Google Scholar]
- Gurunathan, M.; Mahmoud, M.A. A review and development methodology of a lightweight security model for IoT-based smart devices. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 110217. [Google Scholar] [CrossRef]
- Fitwi, A.; Chen, Y.; Zhu, S. A lightweight blockchain-based privacy protection for smart surveillance at the edge. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 552–555. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, 13–17 March 2017; pp. 618–623. [Google Scholar]
- Frikha, T.; Chaabane, F.; Aouinti, N.; Cheikhrouhou, O.; Ben Amor, N.; Kerrouche, A. Implementation of Blockchain Consensus Algorithm on Embedded Architecture. Secur. Commun. Networks 2021, 2021, 1–11. [Google Scholar] [CrossRef]
- Aruna Reddy, H.; Kavya Raveendra Bhat Pavithra, M.; Mandara, N.; Ramya, S. Blockchain for financial application using ioT. Int. Res. J. Comput. Sci. (IRJCS) 2019, 106, 369. [Google Scholar]
- Guruprakash, J.; Koppu, S. EC-ElGamal and Genetic algorithm-based enhancement for lightweight scalable Blockchain in IoT domain. IEEE Access 2020, 8, 141269–141281. [Google Scholar] [CrossRef]
- Xu, L.; Chen, L.; Gao, Z.; Xu, S.; Shi, W. EPBC: Efficient public blockchain client for lightweight users. In Proceedings of the 1st Workshop on Scalable and Resilient Infrastructures for Distributed Ledgers, Las Vegas, NV, USA, 11–15 December 2017; pp. 1–6. [Google Scholar]
- Shahid, A.R.; Pissinou, N.; Staier, C.; Kwan, R. Sensor-chain: A lightweight scalable blockchain framework for Internet of things. In Proceedings of the 2019 International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Atlanta, GA, USA, 14–17 July 2019; pp. 1154–1161. [Google Scholar]
- Abdulkader, O.; Bamhdi, A.M.; Thayananthan, V.; Elbouraey, F.; Al-Ghamdi, B. A lightweight blockchain based cybersecurity for IoT environments. In Proceedings of the 2019 6th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2019 5th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), Paris, France, 21–23 June 2019; pp. 139–144. [Google Scholar]
- Khan, S.; Lee, W.-K.; Hwang, S.O. AEchain: A Lightweight Blockchain for IoT Applications. IEEE Consum. Electron. Mag. 2021, 11, 64–76. [Google Scholar] [CrossRef]
- Goswami, S. Scalability Analysis of Blockchains through Blockchain Simulation; University of Nevada: Las Vegas, NV, USA, 2017. [Google Scholar]
- Shahsavari, Y.; Zhang, K.; Talhi, C. A Theoretical Model for Block Propagation Analysis in Bitcoin Network. IEEE Trans. Eng. Manag. 2022, 69, 1459–1476. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).