Distributed K-Anonymous Location Privacy Protection Algorithm Based on Interest Points and User Social Behavior
Abstract
1. Introduction
- A comprehensive user similarity is constructed by user point of interest similarity and user social behavior similarity, so that the requesting user can find the undifferentiated collaborating user when the collaborating user constructs an anonymous zone. This approach makes it impossible for an attacker to infer the location of the real user through background knowledge.
- The real location of the collaborating user is used to form the anonymity set, avoiding the problem of uncontrollable virtual locations. The requesting user can construct the anonymity zone independently of the collaborating user without the help of a centralized anonymizer.
- By homogenizing the collaborative user set, the homogeneity of the anonymous location points within the anonymous region is improved while the range of the anonymous region is guaranteed to be constant, resulting in a higher quality of the anonymous region.
2. Related Works
2.1. Virtual Collaboration Location-Based Solutions
2.2. Real Collaboration Location-Based Solutions
3. Preparatory Knowledge
3.1. System Architecture
3.2. Attack Model
3.3. Collaborative User Similarity
3.3.1. Semantic Similarity of Interest Points
- means delete ;
- means insert ;
- means replace .
3.3.2. Distance Similarity of Interest Points
3.3.3. Similarity of Social Behavior of Collaborating Users
4. K-Anonymous Location Privacy-Protection Algorithm Based on User Similarity
4.1. Collaborative User Similarity Calculation Algorithm
| Algorithm 1: User similarity calculation algorithm. |
Input: user’s POI name, POI coordinates Output: user’s similarity set :
|
4.2. Collaborative User Selection Algorithm
| Algorithm 2: Collaborative anonymous user selection algorithm. |
Input: user similarity set, user real location loc, location K, anonymous parameter K Output: optimal collaborative anonymous set:
|
5. Privacy Analysis and Experimentation
5.1. Privacy Analysis
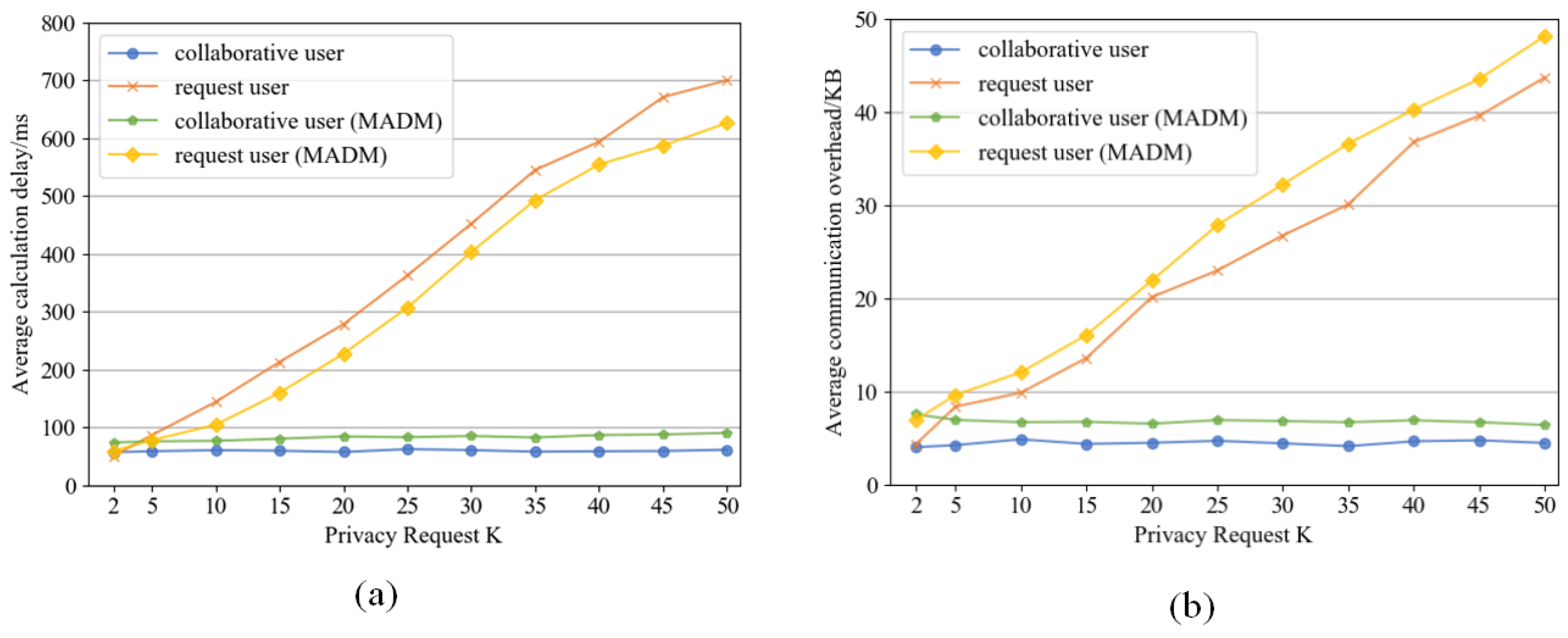
5.2. Performance Verification
5.3. Privacy Verification
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Zhang, T.; Li, X.; Zhang, Q. Location privacy protection: A power allocation approach. IEEE Trans. Commun. 2018, 67, 748–761. [Google Scholar] [CrossRef]
- Ni, W.; Gu, M.; Chen, X. Location privacy-preserving k nearest neighbor query under user’s preference. Knowl.-Based Syst. 2016, 103, 19–27. [Google Scholar] [CrossRef]
- Ghinita, G.; Nguyen, K.; Maruseac, M. A secure location-based alert system with tunable privacy-performance trade-off. GeoInformatica 2020, 24, 951–985. [Google Scholar] [CrossRef] [PubMed]
- Li, W.; Li, C.; Geng, Y. APS: Attribute-aware privacy-preserving scheme in location-based services. Inf. Sci. 2020, 527, 460–476. [Google Scholar] [CrossRef]
- Albelaihy, A.; Thayananthan, V. BL0K: A New Stage of Privacy-Preserving Scope for Location-Based Services. Inf. Sci. 2019, 19, 696. [Google Scholar] [CrossRef]
- Luo, H.; Zhang, H.; Long, S.; Lin, Y. Enhancing frequent location privacy-preserving strategy based on geo-Indistinguishability. Multimed. Tools Appl. 2021, 80, 21823–21841. [Google Scholar] [CrossRef]
- Zhao, P.; Huang, Y.; Gao, J.; Xing, L.; Wu, H.; Ma, H. Federated learning-based collaborative authentication protocol for shared data in social IoV. IEEE Sens. J. 2022, 22, 7385–7398. [Google Scholar] [CrossRef]
- Zhao, X.; Pi, D.; Chen, J. Novel trajectory privacy-preserving method based on prefix tree using differential privacy. Knowl.-Based Syst. 2020, 198, 105940. [Google Scholar] [CrossRef]
- Andrés, M.E.; Bordenabe, N.E.; Chatzikokolakis, K.; Palamidessi, C. Geo-indistinguishability: Differential privacy for location-based systems. In Proceedings of the 2013 ACM SIGSAC Conference on Computer, Berlin, Germany, 4–8 November 2013; pp. 901–914. [Google Scholar]
- Farouk, F.; Alkady, Y.; Rizk, R. Efficient privacy-preserving scheme for location based services in VANET system. IEEE Access 2020, 8, 60101–60116. [Google Scholar] [CrossRef]
- Li, M.; Salinas, S.; Thapa, A.; Li, P. n-CD: A geometric approach to preserving location privacy in location-based services. In Proceedings of the 2013 IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 3012–3020. [Google Scholar]
- Andrew, J.; Eunice, R.J.; Karthikeyan, J. An anonymization-based privacy-preserving data collection protocol for digital health data. Front. Public Health 2023, 11. [Google Scholar] [CrossRef]
- Jia, X.; Xing, L.; Gao, J.; Wu, H. A survey of location privacy preservation in social internet of vehicles. IEEE Access 2020, 8, 201966–201984. [Google Scholar] [CrossRef]
- Wu, Z.; Wang, R.; Li, Q.; Lian, X.; Xu, G.; Chen, E.; Liu, X. A location privacy-preserving system based on query range cover-up or location-based services. IEEE Trans. Veh. Technol. 2020, 69, 5244–5254. [Google Scholar] [CrossRef]
- Gruteser, M.; Grunwald, D. Anonymous usage of location-based services through spatial and temporal cloaking. In Proceedings of the 1st International Conference on Mobile Systems, Applications and Services, San Francisco, CA, USA, 5–8 May 2003; pp. 31–42. [Google Scholar]
- Niu, B.; Li, Q.; Zhu, X.; Cao, G.; Li, H. Achieving k-anonymity in privacy-aware location-based services. In Proceedings of the IEEE INFOCOM 2014—IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April 2014–2 May 2014; pp. 754–762. [Google Scholar]
- Niu, B.; Zhu, X.; Li, W.; Li, H. Epcloak: An efficient and privacy-preserving spatial cloaking scheme for lbss. In Proceedings of the 2014 IEEE 11th International Conference on Mobile Ad Hoc and Sensor Systems, Philadelphia, PA, USA, 28–30 October 2014; pp. 398–406. [Google Scholar]
- Yang, D.; Ye, B.; Zhang, W.; Zhou, H.; Qian, X. KLPPS: A k-Anonymous Location Privacy Protection Scheme via Dummies and Stackelberg Game. Secur. Commun. Netw. 2021, 2021, 9635411. [Google Scholar] [CrossRef]
- Niu, B.; Zhu, X.; Li, W.; Li, H.; Wang, Y.; Lu, Z. A personalized two-tier cloaking scheme for privacy-aware location-based services. In Proceedings of the 2015 International Conference on Computing, Networking and Communications (ICNC), Garden Grove, CA, USA, 16–19 February 2015; pp. 94–98. [Google Scholar]
- Yu, H.; Zhang, H.; Yu, X. Trajectory similarity calculation method for privacy protection. J. Commun. 2022, 43, 1–13. [Google Scholar]
- Ji, Y.; Zhang, J.; Ma, J.; Yang, C.; Yao, X. BMPLS: Blockchain-based multi-level privacy-preserving location sharing scheme for telecare medical information systems. J. Med. Syst. 2018, 42, 147. [Google Scholar] [CrossRef] [PubMed]
- Liu, H.; Li, X.; Luo, B. Blockchain-based Distributed K Anonymous Location Privacy Protection Solution. J. Comput. Sci. 2019, 42, 19. [Google Scholar]
- Yang, M.; Ye, B.; Chen, Y. A trusted de-swinging k-anonymity scheme for location privacy protection. J. Cloud Comput. 2022, 11, 2. [Google Scholar] [CrossRef]
- Parmar, D.; Rao, U.P. Privacy-preserving enhanced dummy-generation technique for location-based services. Concurr. Comput. Pract. Exp. 2023, 35, e7501. [Google Scholar] [CrossRef]
- Zhang, S.; Li, X.; Tan, Z.; Peng, T.; Wang, G. A caching and spatial K-anonymity driven privacy enhancement scheme in continuous location-based services. Future Gener. Comput. Syst. 2019, 40–50. [Google Scholar] [CrossRef]
- Zhu, L.; Liu, X.; Jing, Z.; Yu, L.; Cai, Z.; Zhang, J. Knowledge-Driven Location Privacy Preserving Scheme for Location-Based Social Networks. Electronics 2023, 70. [Google Scholar] [CrossRef]
- Sei, Y.; Andrew, J.; Okumura, H.; Ohsuga, A. Privacy-preserving collaborative data collection and analysis with many missing values. IEEE Trans. Dependable Secur. Comput. 2022, 20, 2158–2173. [Google Scholar] [CrossRef]
- Liu, H.; Li, X.; Li, H.; Ma, J.; Ma, X. Spatiotemporal correlation-aware dummy-based privacy protection scheme for location-based services. In Proceedings of the IEEE INFOCOM 2017—IEEE Conference on Computer Communications, Atlanta, GA, USA, 1–4 May 2017; pp. 1–9. [Google Scholar]
- Wang, H.; Wang, C.; Shen, Z.; Liu, K.; Liu, P.; Lin, D. A MADM location privacy protection method based on blockchain. IEEE Access 2021, 9, 27802–27812. [Google Scholar] [CrossRef]
- Levenshtein, V.I. Binary codes capable of correcting deletions, insertions, and reversals. Soviet Phys. Doklady 1966, 10, 707–710. [Google Scholar]



| Virtual Location Solutions | Real Location Solutions | |||||||
|---|---|---|---|---|---|---|---|---|
| [15] | [16,17] | [18] | [19] | [20] | [21] | [22] | [23] | |
| Privacy protection degree | Low | Medium | High | High | High | Medium | High | High |
| Calculated overhead | Low | Medium | Low | Low | Medium | Low | Low | Medium |
| Communication overhead | Low | Low | Medium | High | High | Low | Medium | High |
| Service quality | Medium | High | Medium | Medium | High | Medium | High | High |
| Point Type | Point Type |
|---|---|
| Entrance/Exit | Finance |
| Real Estate | Hotel |
| Enterprises | Beauty |
| Shopping | Attractions |
| Transportation | Gourmet |
| Education | Car Service |
| Life Services | Media |
| Leisure | Medical |
| Sports | Government |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xing, L.; Zhang, D.; Wu, H.; Ma, H.; Zhang, X. Distributed K-Anonymous Location Privacy Protection Algorithm Based on Interest Points and User Social Behavior. Electronics 2023, 12, 2446. https://doi.org/10.3390/electronics12112446
Xing L, Zhang D, Wu H, Ma H, Zhang X. Distributed K-Anonymous Location Privacy Protection Algorithm Based on Interest Points and User Social Behavior. Electronics. 2023; 12(11):2446. https://doi.org/10.3390/electronics12112446
Chicago/Turabian StyleXing, Ling, Dexin Zhang, Honghai Wu, Huahong Ma, and Xiaohui Zhang. 2023. "Distributed K-Anonymous Location Privacy Protection Algorithm Based on Interest Points and User Social Behavior" Electronics 12, no. 11: 2446. https://doi.org/10.3390/electronics12112446
APA StyleXing, L., Zhang, D., Wu, H., Ma, H., & Zhang, X. (2023). Distributed K-Anonymous Location Privacy Protection Algorithm Based on Interest Points and User Social Behavior. Electronics, 12(11), 2446. https://doi.org/10.3390/electronics12112446







