1. Introduction
In 2019, AI and AI-related innovation, fifth-generation mobile networks (5G), cloud computing, and the IoT became important to the market. In 2022, Garter™ introduced the productivity revolution with AI [
1]. PCIe 5.0 is over 10% based on the PCIe 4.0 market [
2]. Market demand strategies can be developed with the T-plan analysis method [
3]. This analysis process tracks market demand, products, technologies, and strategies for products.
Market demand can be calculated based on data pertaining to 5G applications from the 3rd Generation Partnership Project (3GPP). Using 5G applications created with network slice layers, a PC system can focus on AI, IoT, high-performance computing, and cloud storage for security products. 5G applications are in demand for edge service in physical and virtual resources. In this study, we used the serial bus as the basic design model and reviewed the system topology. To evaluate application demand, we assessed suitable technologies and developed market-appropriate solutions. We used the PCI Express system for the processor, memory, storage, and USB devices for network slice services. We reviewed performance and power efficiency. Following the released PCI Express roadmap, product designs should be ready in around three years for each generation. Considering USB, PCI Express, CXL, and security risks, it will also take around three years to produce these product changes.
In this survey, we referenced system-related specifications and release schedules, and reviewed the products introduced to the market. Our methodology involved reviewing enhancements and features in USB, PCI Express, NVMe, and CXL. Based on these serial bus solutions and 5G application slices, we attempted to understand the need for AI, IoT, cloud computing, and storage.
Security algorithms were suggested for quantum computers to highlight some of the changes needed to provide more secure systems, and have been part of market demand since 2016 [
4]. Systems and devices using 5G applications require more secure products than those previously in use. Intel™ and Microsoft™ must commence security review processes and provide secure updates and solutions. The specifications of USB, PCIe, and NVMe also include more secure solutions during protocol transition with PCI Express. Products with secure hardware and software have been introduced to the market, while market demand for 5G secure cloud and 5G network usage has increased.
For the PC industry, Intel™, AMD™, and NVIDIA™ are the three major solution providers. The roadmaps for AI and deep learning produced by these three companies provide valuable product strategies. We reviewed these solutions for hardware and software in different product lines, including CPU- and GPU-based systems designed for application slicing in physical and virtual devices. As a result, devices with low power and low data throughput are designed for IoT, while devices with high power and high data throughput are designed for AI and deep learning. USB PDs provide appropriate power design for products as demanded. Cloud services are based on data throughput, storage, and performance. Deep learning uses CPU and GPU solutions for performance, as demanded.
Secure devices such as TPM can be combined with systems that protect data while moving it from the field to backup services. Risks in different network slicing layers in virtual and physical resources require more silicon and hardware security solutions.
1.1. Strategy for AI, IoT, Cloud Computing, and Storage
Physical infrastructure and edge cloud systems based on 5G application slicing could be the best system design strategy [
5,
6]. Based on AI and IoT product strategies, platforms consider power and security solutions in different 5G application slicing. This approach reduces data throughput from the infrastructure layer to the edge cloud. An infrastructure layer for 5G application slices would be a suitable solution for the IoT. For cloud computing, PCI Express and CXL with data protocol communications impact system performance. NVMe with PCI Express protocol transition could aid PCI Express in terms of increasing performance with storage. The strategy we used for cloud computing was based on PCI Express and CXL system designs, with secure data transition. Cloud storage was focused on edge cloud for PCI Express, NVMe, and security, as well as secure data in the 5G application slice.
Based on the PC industry, the product strategy for 5G relies on solution combinations, with some focus on technologies and on reviewing systems with respect to serial bus and solutions from standard specifications. The system has hardware solutions provided by industry vendors. A system designer may use these findings to define market demand.
1.2. Organization
In this paper, we discuss:
- 1.
Section 1: We review the market demand for 5G and the PCIe-based systems with components, based on Intel™, AMD™, and NVIDIA™ solutions for GPUs and CPUs for system design, as demanded.
- 2.
Section 2: We review PC industry capabilities and 5G application market demand for security, the IoT, AI, cloud computing, and storage.
- 3.
Section 3: Using a serial bus, we review PCIe base system technology with PCIe, NVMe with storage, and CXL. We review secure solutions with TPM.
- 4.
Section 4: We review PCI Express, CXL, USB, and a security technical roadmap. We review Intel™, AMD™, and NVIDIA™ product roadmaps for AI and deep learning.
- 5.
Section 5: Based on the product domain, we review the requirements for technical solutions.
- 6.
Section 6: We summarize system design solutions for AI, IoT, cloud computing, and storage.
- 7.
Section 7 and
Section 8: We describe the way in which system design using serial bus can simplify solutions for the problem of market demand.
2. Market Analysis of the PC Industry
Standard specifications for technology in the PC industry should reference information to identify a strategy for products entering the market. Solution providers have product roadmaps and suggestions regarding the market for each generation. Some designs drive the industry to focus on technologies related to products. In general, servers, desktops, and notebooks are the three main PC product lines. Solution providers have introduced roadmaps and updated technical solutions to help navigate the marketplace. The PC industry is based on this information and prioritizes each common design for the coming market in each segment. PCI Express was the main component for the system, and the component and features are the default configuration of the system for the market. The system reserves the interface for customized component usage for specific requirements. There is a reliance on multiple configurations and on extending feature capability to meet market demand.
2.1. Analysis of the Market for 5G Applications
When 5G was introduced to the market in 2019, various services led to the increase of the number of physical types of equipment and the number of virtual services in the cloud. Devices and systems related to the PC industry benefited from using these applications, requiring the development of products and strategies for such changeable markets [
7]. Gartner™ reviewed some technologies in 2021 that were already in the peak phase of inflated expectations. These technologies drove the market to generate expectations for the products and technologies [
1,
8]. With cutting-edge requirements being produced in AI, graphs, and storage, these applications increased market demand in the PC industry.
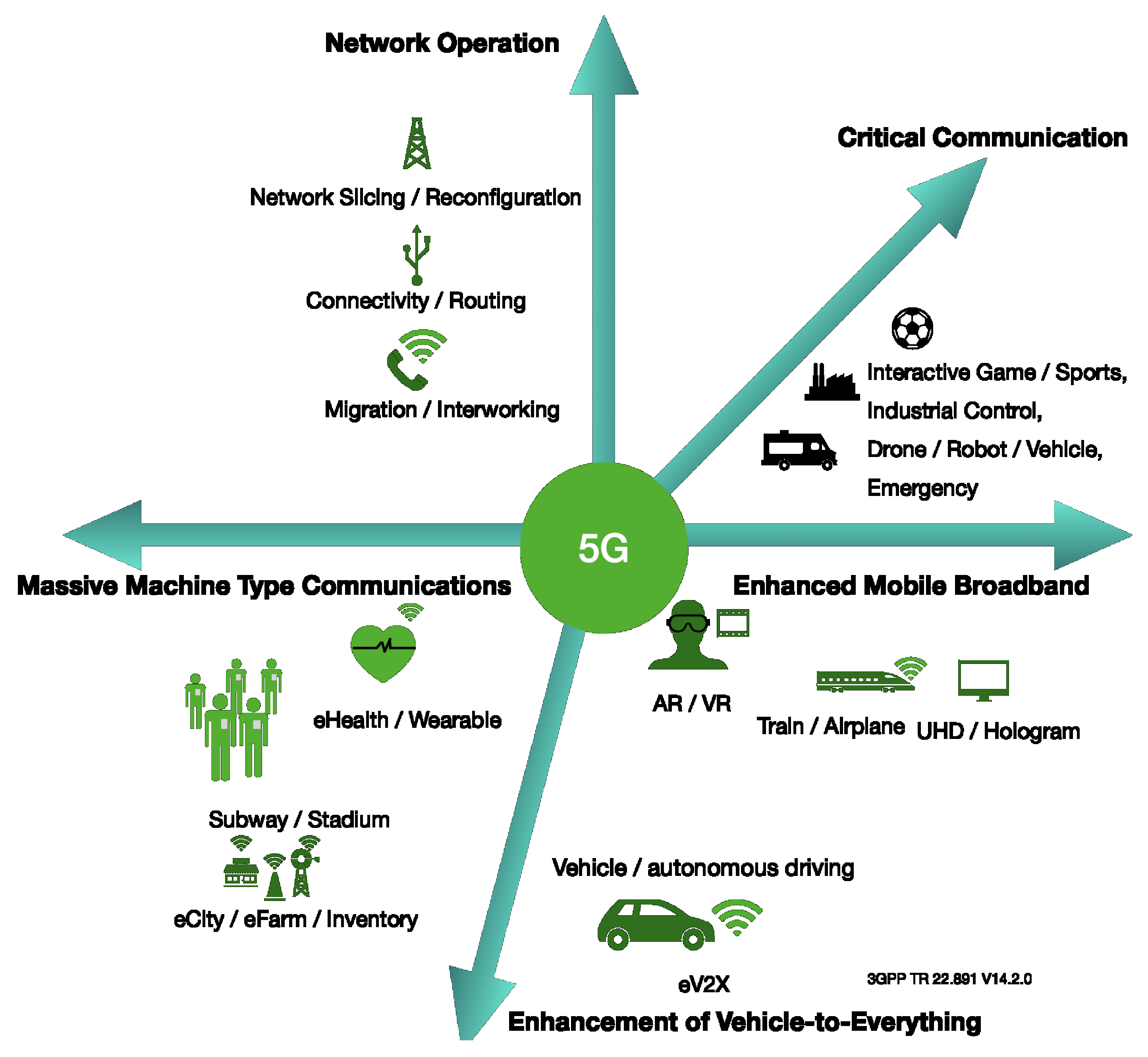
With respect to the FS_SMARTER service dimension, market perspectives and products involve five dimensions and related business scopes. These are enhanced mobile broadband, critical communications, network operations, massive machine-type communications, and enhancement of vehicle-to-everything, all of which have been deemed fit for service in the 5G environment, and involve high data throughput with high-performance computing systems in terms of AI, IoT, cloud computing, and storage. Each dimension has specific requirements for power and performance. Critical environments and processes specific to the service must deal with market demand for specific designs, as shown in
Figure 1 [
7,
9].
In 3GPP, “5G for industry 4.0” provides 5G applications for the industrial IoT (Vertical_LAN in Release 16). 5G time-sensitive communications, 5G non-public networks, and 5G LAN-type services were introduced in this version release, which also included enhanced support for the industrial IoT in Release 17 [
10]. It is expected that the global IoT market, with the growth of 5G and service solution applications in the market, will increase the demand for these applications.
For 5G applications, there should be a network environment to transition each network slice layer, which connects the infrastructure layer with the physical and virtual resources [
5,
6]. For massive machine-type communications, there should be a field sensor with an IoT edge from the network to the backend service. For enhanced mobile broadband, there should be field services with high data throughput through the internet for backend service with data. The enhancement of vehicle-to-everything requires quality of service (QoS) with a trust network slice in 5G application demands [
11].
Software and service requirements enhance IoT business model cross-platform design structures to manage the dedicated IoT market [
12]. AI features have produced three main market shares: computer vision, machine learning, and natural language processing. These technologies rely on cloud computing and cloud storage modules [
13]. 5G and IoT with edge requirements extend the AI market size. With these demands, various applications and solutions are increasing the edge computing requirements. Azure™, AWS™, HPE™, and Google™ deliver solutions for AI and IoT in cloud environments. Applications in edge services must consider data and the performance issues arising from communication [
14]. In terms of the next-generation data storage market, it should continue to grow in the cloud environment. AI and IoT with edge data storage applications will also grow the market.
Market Trends in the PC Industry in AI, IoT, Cloud Computing, and Storage
The PC market has been influenced by handheld systems, AI, and IoT system usage in recent years. 3GPP has classified these requirements into five categories: enhanced mobile broadband, critical communication, massive machine-type communications, network operation, and enhancement of vehicle-to-everything in TR 22.891 [
9]. The market in each category is multidimensional.
Over the last few years, there has been a dramatic increase in AI, IoT, and 5G applications, which has produced new markets [
12,
14,
15,
16].
2.2. Market Requirements in the PC Industry
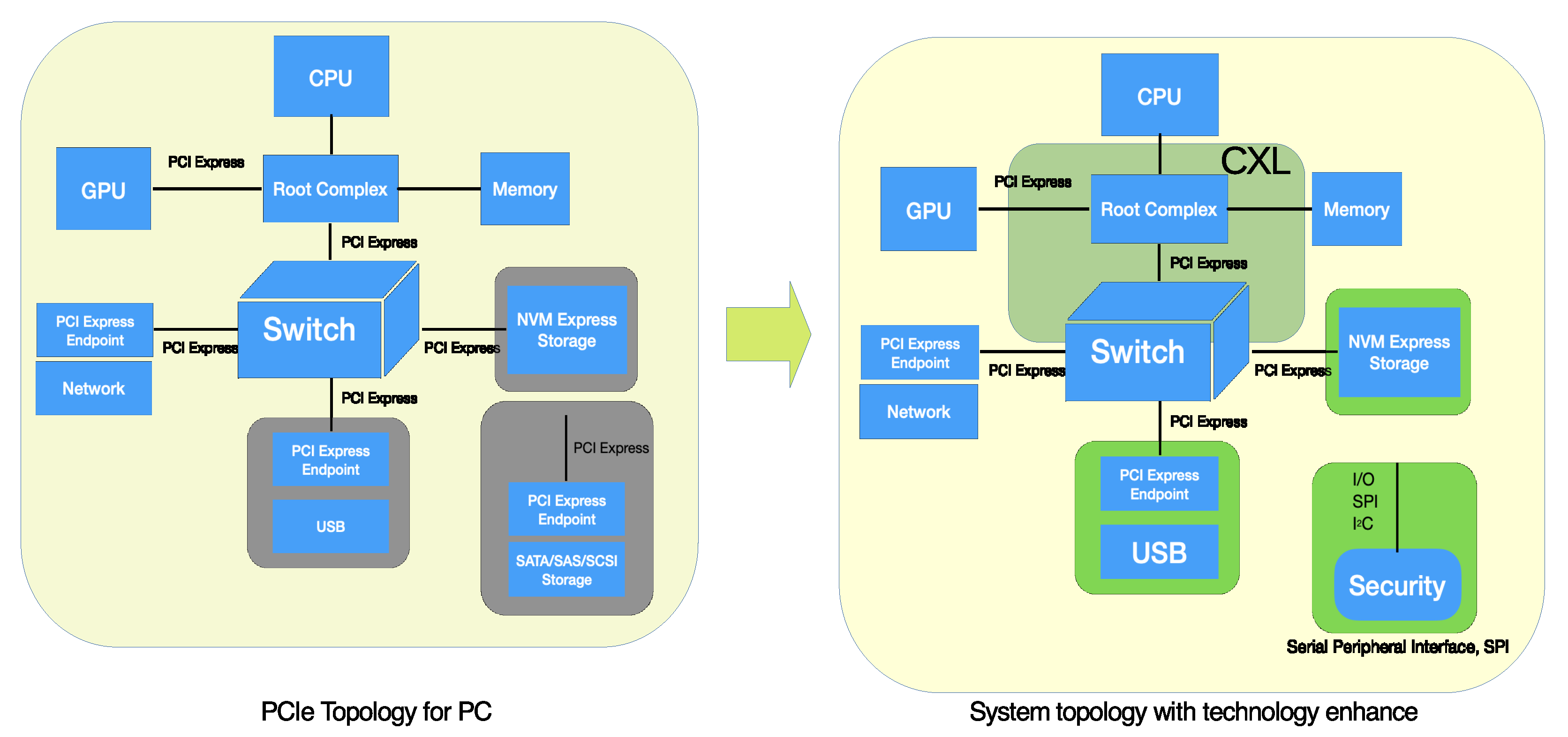
The PC industry has a design strategy to review solutions for products such as all-in-one silicon-on-chips (SoCs) and CPUs with chipsets combined with memory, as well as systems in regular design. As shown in
Figure 2, PC systems use PCI Express (PCIe) and PCIe topology to build a system for market demand [
17].
Cloud computing, cloud applications, and cloud storage reduce the requirement for personal equipment. Cloud market demand does not follow traditional market demand for notebooks, desktops, and servers.
Market Requirements for Security
More secure services and systems have been reviewed for network and cloud usage. The cloud base environment relies on servers and services through the internet. This process transfers data through different devices and across different routers, which means that servers face challenges such as security, reliability, and safety control processes [
18]. Data protection and data security requirements have increased in the past few years. In 2019, the US announced security concerns throughout various industries, which impacted businesses in the US. The reaction worldwide was to face these presented risks that year and continue to enhance security solutions in platforms and services [
4].
Data from Microsoft Azure has indicated there is a rapidly increasing market and consumer base for security. Customers are willing to pay more for security solutions, since cloud environment applications have grown in recent years [
19].
In 5G communication, Function Virtualization (NFV) and Software-Defined Networking (SDN) have faced Distributed Denial-of-Service (DDoS) security risks [
20,
21]. 5G applications with network slices featuring various layers face different security risks. There are infrastructure layers with physical devices, backend services with cloud computing, and storage, which create more security considerations. In terms of security considerations, personal data breaches, physical safety, and personal privacy were found to be concerns for 80% of respondents [
19].
3. Technology Analysis Using PCI Express, CXL, USB, NVMe, and Security
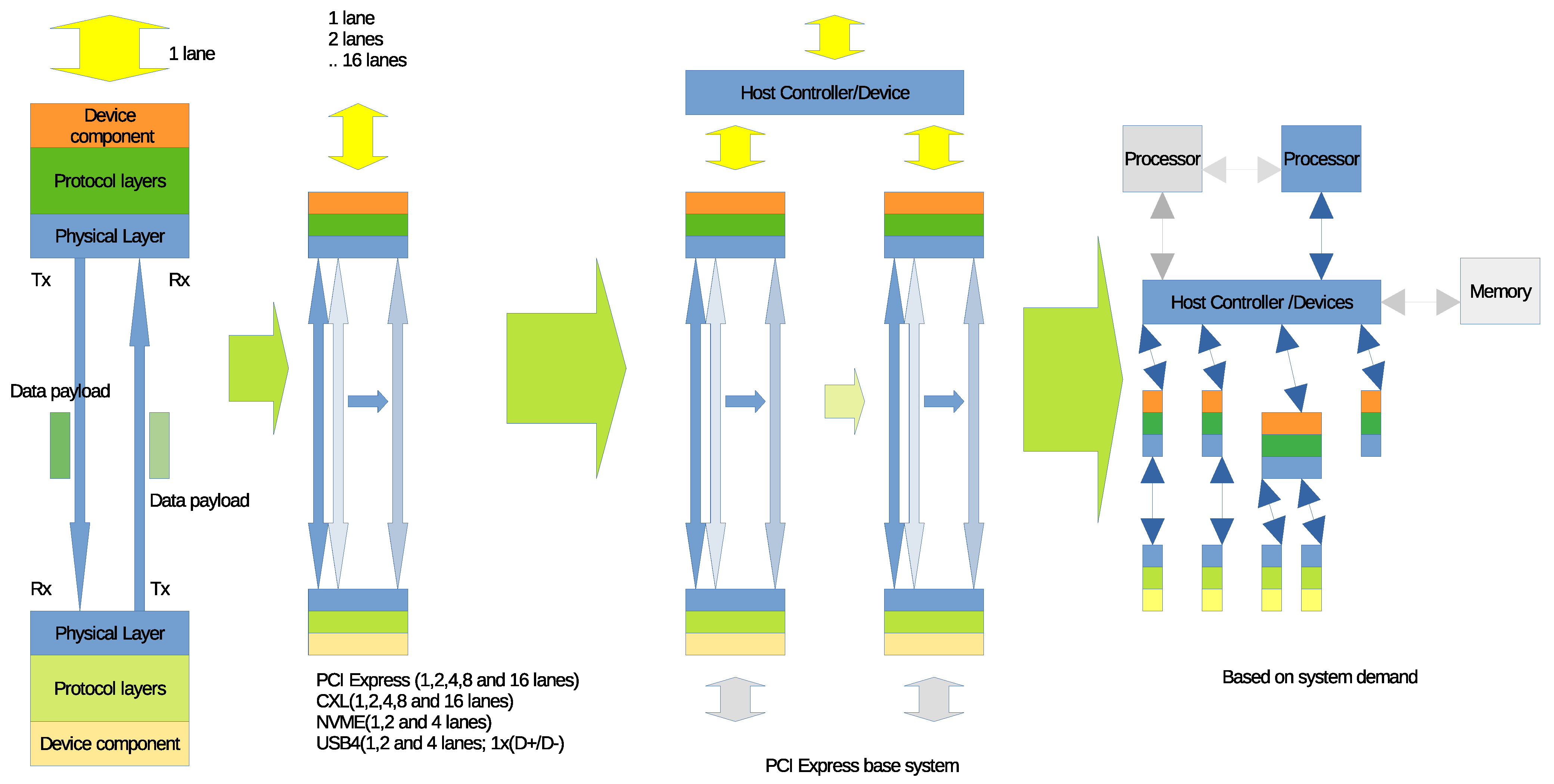
The topology of the PC structure involves PCI Express, and PCIe relies on a serial bus across the system, based on current system designs for PCIe-based systems. PCIe, NVMe, USB, and CXL use serial bus systems [
17,
22,
23,
24]. The serial bus base system was the basis for the analysis methods used to understand the PC system, as shown in
Figure 3.
In the PC system, a security system includes hardware and software solutions. Cloud usage increases the security requirements, which also drive the product and technology strategy. In
Figure 2, enhancements to the serial bus models in this topology are described. Secure devices in 5G application layers and cloud usage requirements drive demand for secure solutions.
3.1. PCI Express
According to the PCIe industry-standard roadmap, PCIe 5.0 will provide more efficiency in 5G, AI, and network computing requirements, since its bandwidth is increased to 32.0 Gb/s. The I/O bandwidth doubles every three years in PCI Express [
25,
26]. This drives PCIe fabric topology, as it is the main architecture in the current PC industry [
17,
27].
In 2021, PCIe 5.0 products were introduced to the market. Intel™ introduced PCIe 4.0 and PCIe 5.0 solutions to the PC industry, which can provide systems with better performance, as shown in
Figure 4 [
27]. The PCIe 5.0 and PCIe 6.0 technology roadmaps have been verified in other high-speed serial bus protocols [
17,
28].
3.2. Compute Express Link
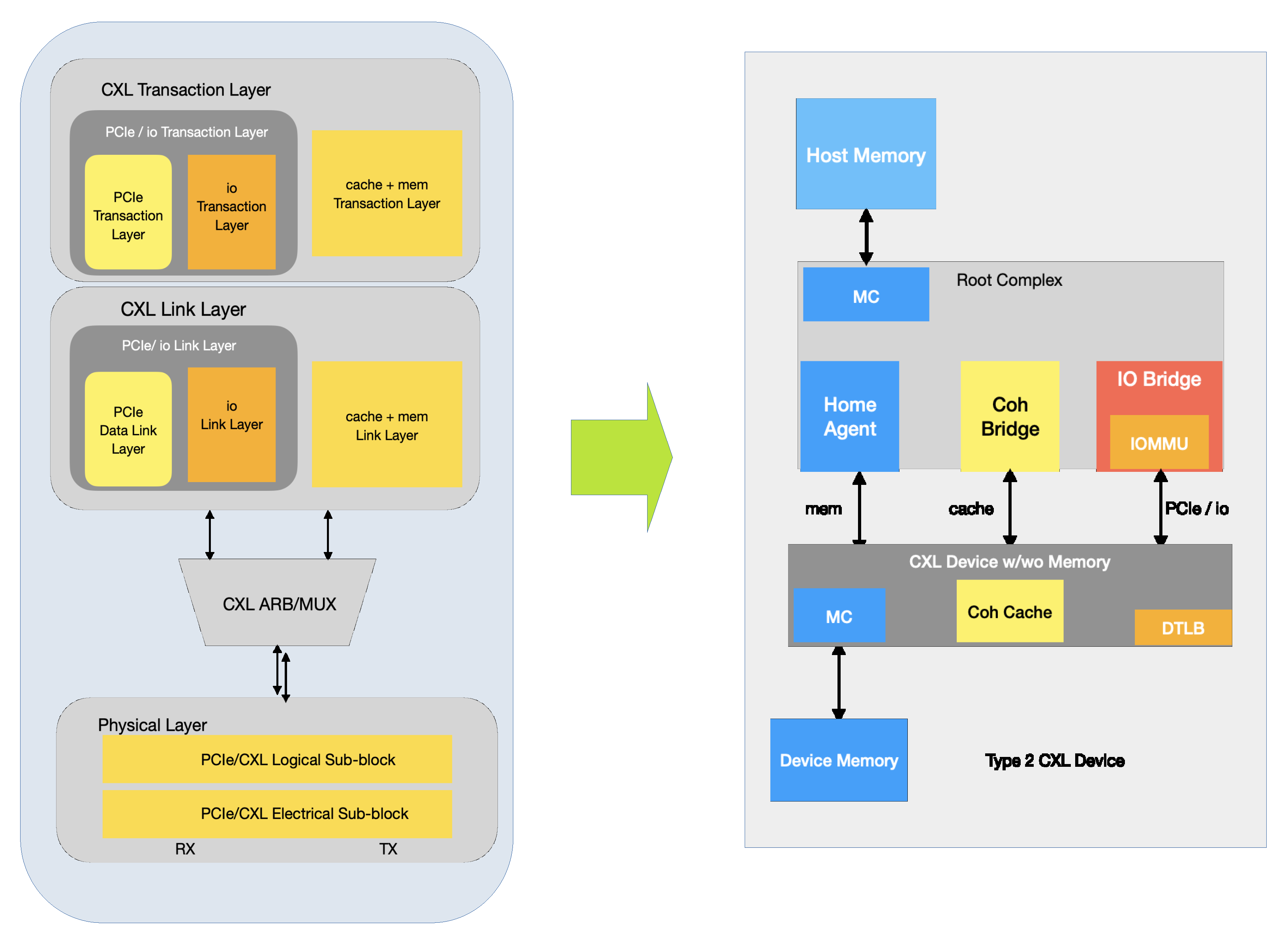
The Compute Express Link (CXL) is based on PCIe 5.0 and includes three types, as shown in
Figure 5: CXL.IO, CXL.Cache, and CXL.MEM. CXL redefines the root complex capability in three types, which can enhance system performance through CXL devices and root complex [
22]. The cache behavior defined in CXL enables remote memory component usage and allows cacheable resources to increase performance through communication across the system topology. CXL features a modified high-speed serial bus that extends the high-speed serial bus capability. This is included in the cache and memory method in CXL, and is backward compatible with PCIe, as seen in
Figure 5 [
22].
3.3. NVM Express
NVM Express follows the PCIe specification to design its products, which allows host software to communicate with a nonvolatile memory subsystem. NVMe reduces the storage access method to memory access and block access. NVMe status can replace traditional storage access methods, which can be implemented in different interconnects through data communication (NVMe over PCIe, NVMe over Fabrics, NVMe over Ethernet, NVMe over InfiniBand, RDMA offload) [
23,
29,
30,
31]. This is also based on high-speed Ethernet environments to access resources and storage through Ethernet (RDMA over Converged Ethernet (RoCE)) [
23].
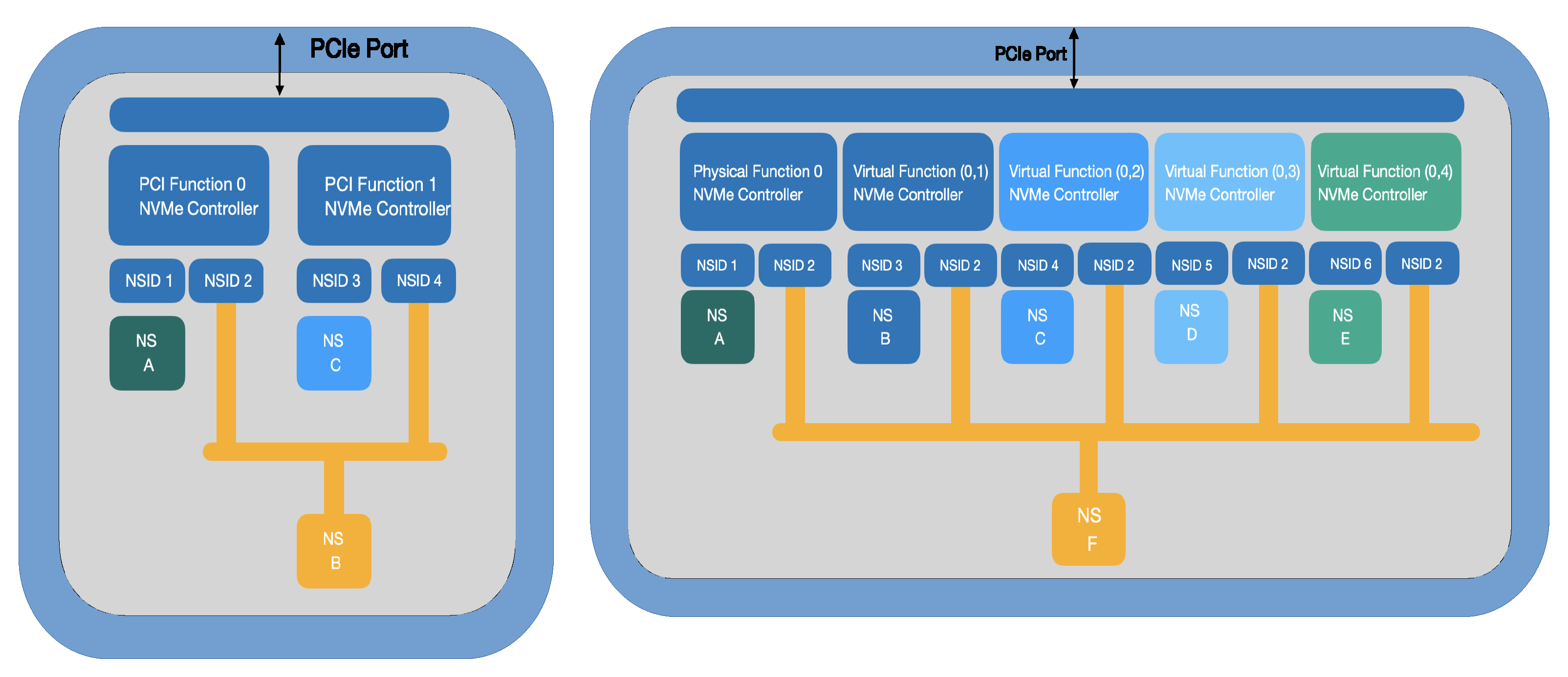
Figure 6 [
23] shows the topology with NVMe connected to a PCIe port. NVMe has two controllers with PCI functions, single root I/O virtualization, multi-path I/O, and namespace sharing [
32]. NVMe 1.3 enhanced security features and power management features. The secure storage access method with multiple access was enhanced in NVMe. NVMe 1.4 improves access methods and is cross-interconnected with industry standards to increase performance. NVMe 2.0 enhances NVMe over Fabrics and multiple usages in the subsystem.
3.4. Universal Serial Bus (USB)
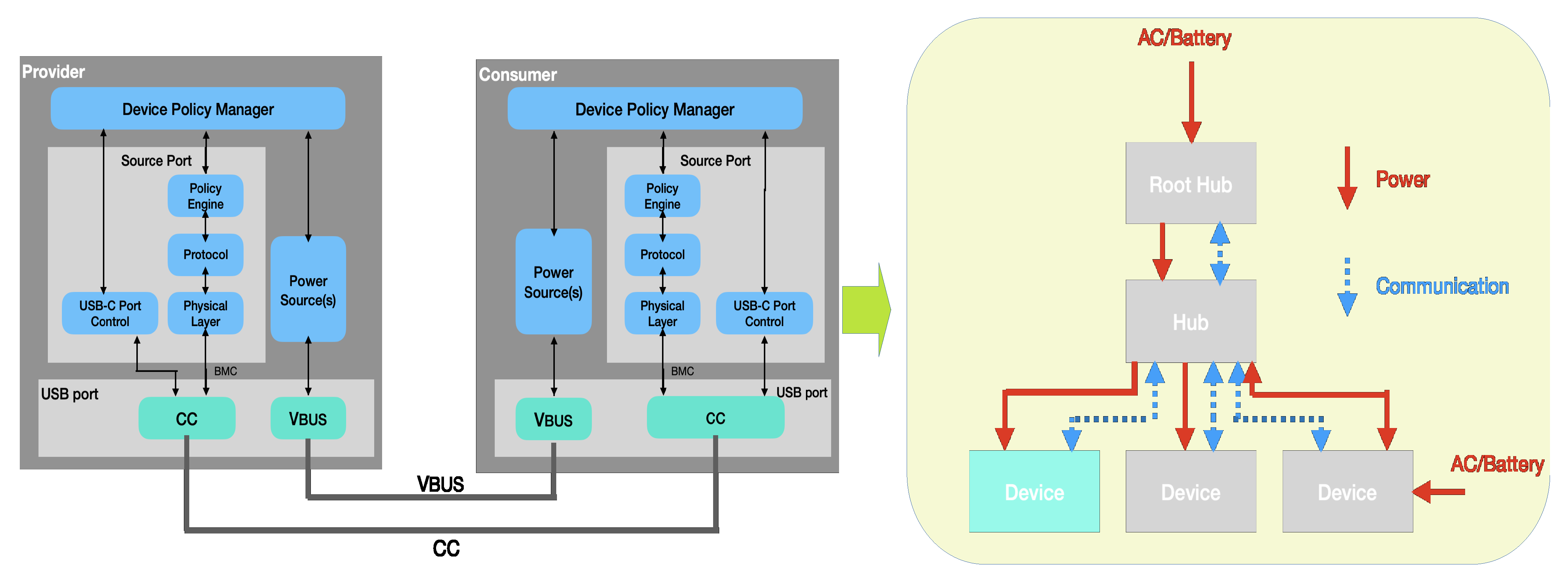
According to the USB industry standard roadmap, USB 4.0 with Thunderbolt 3 will provide more extended features across the USB topology. These include more combined features with USB, Display Port (DP), PCI Express (PCIe), and Power Delivery (PD) for power, as shown in
Figure 7 [
24,
33].
Although the USB 4.0 specifications are combined with Thunderbolt 3, Thunderbolt 4 still uses the PCIe4.0 16Gb/s per lane in a chipset with multiple serial GPIO design for the features combined within. USB uses lanes to transfer data through the UBS connector; the ideal speed to transfer data is from 2560 MB/s to 5120 MB/s [
24,
34,
35]. This bandwidth and data transfer rate should enhance the capability of the system to run other protocols through USB. The USB 4.0 topology is shown in
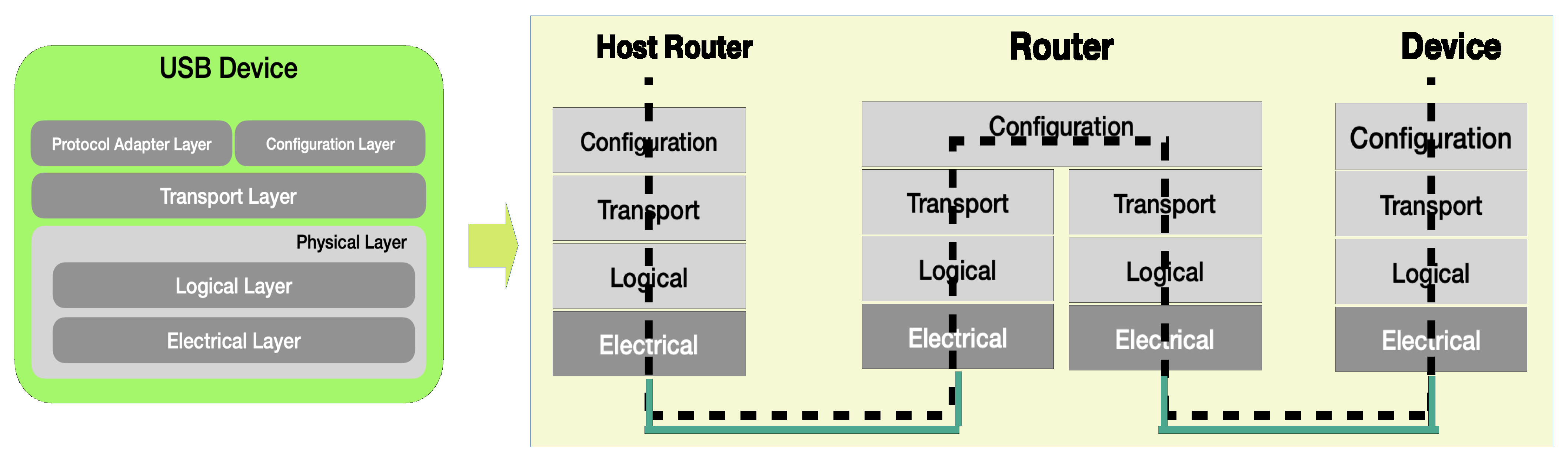
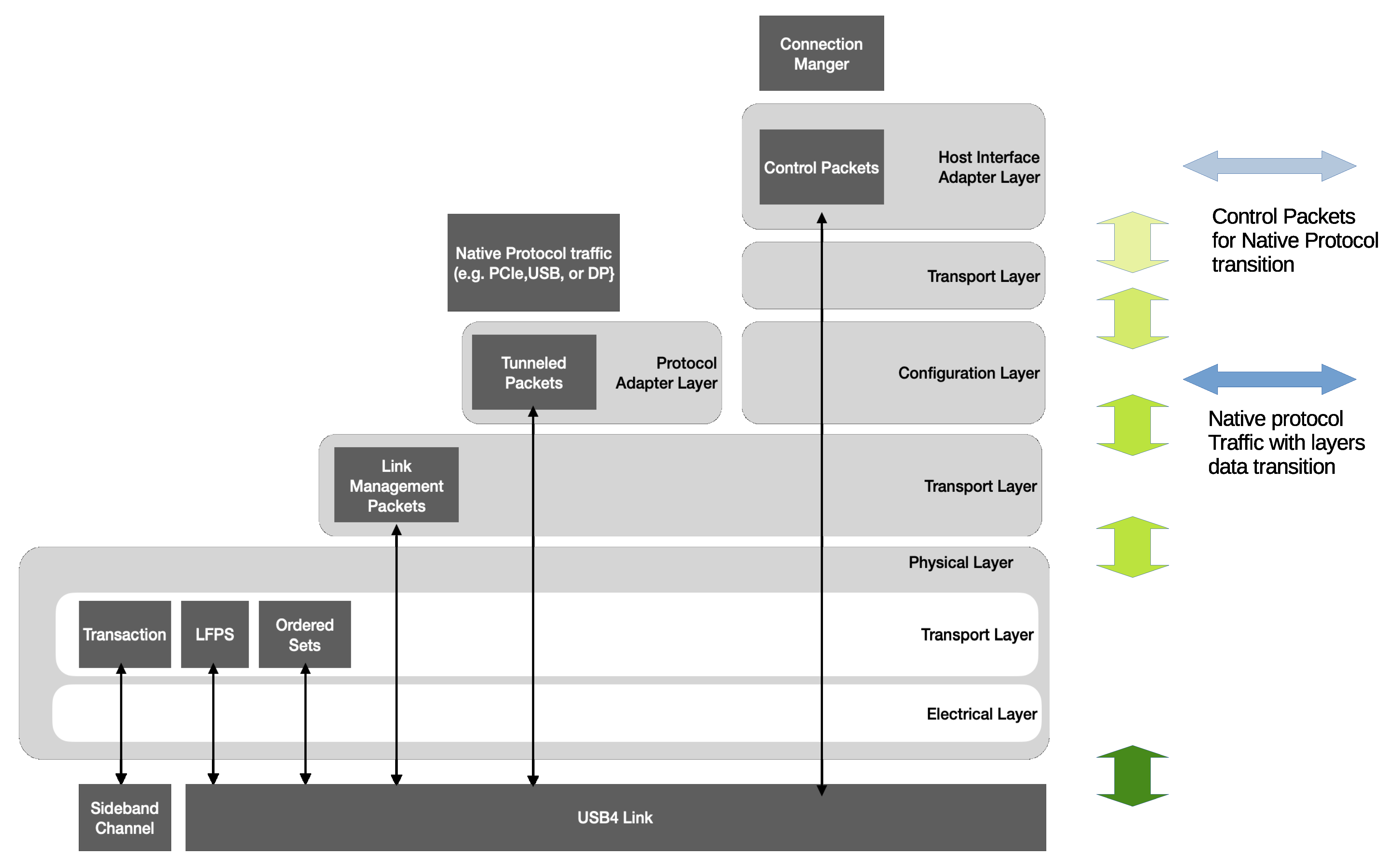
Figure 8 and
Figure 9 [
24], including the layers with routers, as the design structure for USB, PCIe, and Display Port (DP); these data protocols with layers transition through a high-speed serial bus.
Power is delivered through a PD protocol using the USB PD power source [
36]. This capability enhances the system design, allowing the capability to reduce the design in terms power scope, as shown in
Figure 10 [
37]. USB 3.1 is combined with power delivery specifications to change the AC-DC capability through the USB interface across the platform’s design.
Power is delivered on-demand through the PD, as shown in
Figure 10 [
37]. For a platform designed with a programmable power supply under 15 W up to 100 W, a PC system could use these mechanisms to design a power tolerance system, in order to identify the system as a performance-based system for power saving and to customize the system for specific products.
3.5. Security
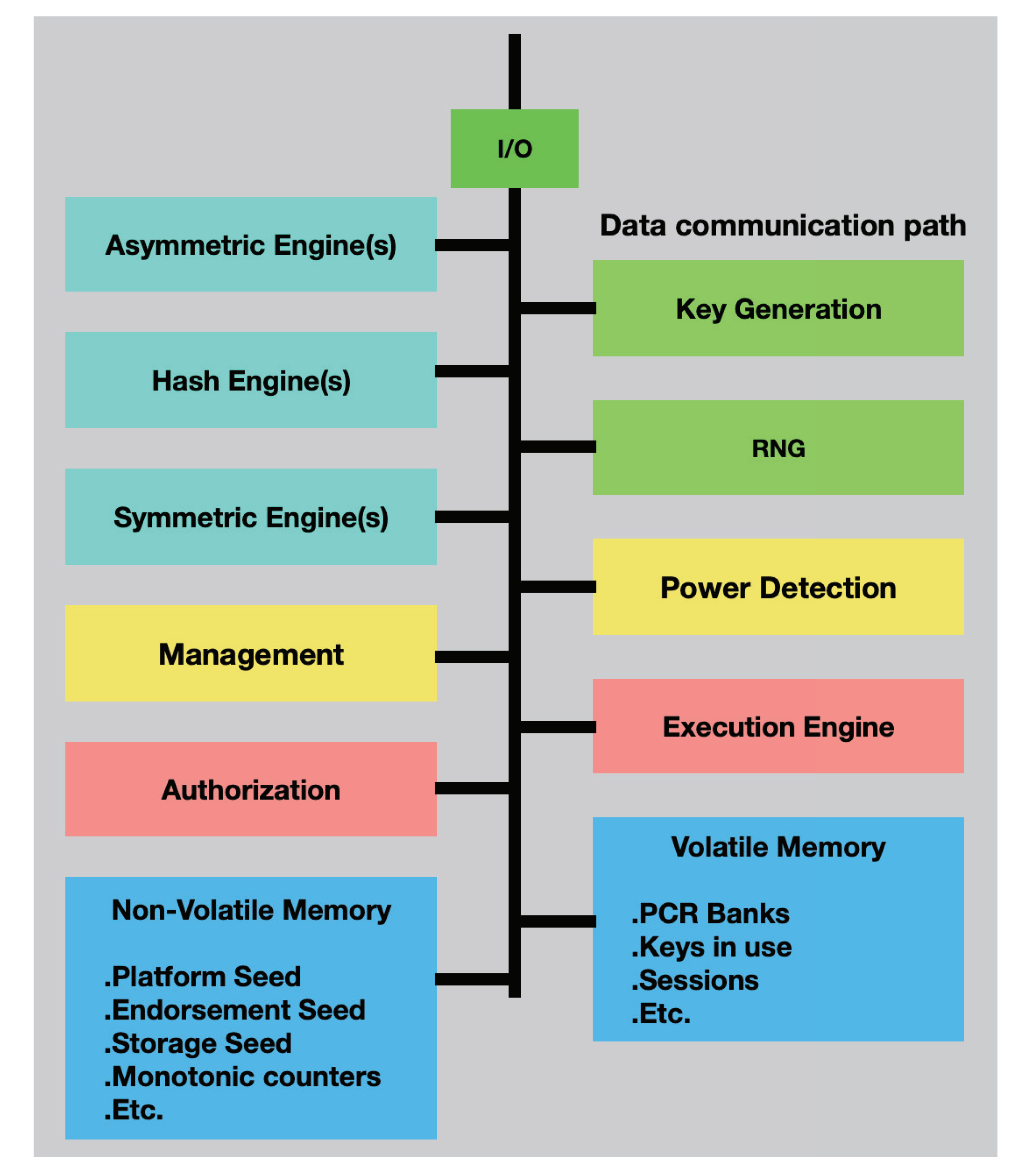
The Trust Platform Module (TPM) was released by the Trust Computing Group. The TCG defined the security system with security features in software and hardware.
Figure 11, shows the TPM with data communication through secure features. The system reference TPM has security features for hardware, software, and application usage to enhance platform security [
38]. Secure Hash Algorithms (SHA) function in SHA1 and SHA2 series, public-key cryptography, and PKCS, and are updated from sources including the Social Security Administration (SSA), etc. [
38,
39]. These security-based algorithms are combined in different software-defined phases and states to enable these security features to secure software and firmware. The system security solutions used as platform designs for Windows-based and Linux-based systems in the market have been reviewed [
40]. TPM 2.0 (SHA256, SHA384, and SM3-256 with RSA 2048 or larger) was the current common TCM from TPM 1.2 (RSA 2048 and SHA1) for hardware security key algorithms, combined with a platform that can let the firmware and OS enhance security for platform-specific designs based on the platform hardware security [
38,
39]. Similar to Microsoft with BitLocker, usage methods are combined, using the SHA algorithm to enhance security [
41]. Software TPM and hardware TPM are improved to construct TPM secure systems.
Intel™ and AMD™ system chipsets still combine software and hardware security solutions in the system chipset, which can use hardware resources to define a combination of security solutions in the system (such as the SHA2 series with RSA with hardware public security keys and OEM security). There are some security-blocked resources that can protect specific resources for access resource requirements, such as AMD™ Secure Memory Encryption (SME), and Secure Encrypted Virtualization (SEV); Intel™ TDT in Intel™ Software Guard Extension, and Intel™ SGX [
42,
43].
IC-based security solutions are based on a traditional interface to secure data during transfers in the platform and connections. These make the original data into secure data during storage access. Some platforms and endpoint devices such as those in the IoT could use IC security to improve their security environments. Multiple software security solutions can be combined in the system. As well as the operating system and the firmware, the execution system should be assessed for security risks to reduce security concerns during execution [
44]. To compare secure solutions, SHA-256 is the main option in the current product line, but SHA-384 is scheduled to deliver solutions in 2020. More secure solutions may be combined for 5G and the cloud environment [
4].
The secure system references the TPM architecture, as shown in
Figure 11 and enhances the security solutions that it contains. The interface across the TPM and the platform security algorithm reduces the security risks of a system. The TCG-defined methods rely on the root of trust. For a trusted platform, there are three items that need to be reviewed: Root of Trust Measurement (RTM), Root of Trust Storage (RTS), and Root of Trust for Reporting (PTR) [
45].
In
Figure 11, the TPM covers secure solutions and shows the root of trust and the process in the system. The TPM 2.0 is listed in the OS vendor’s support lists for Microsoft and Linux-based systems as a basic requirement for security [
41]. When an operating system runs on open source and virtual machines in the PC industry, security solutions use hardware and software to enhance security capabilities.
4. Technical Strategy Using PCI Express, CXL, USB, NVMe, and Security
With the analysis method through the serial bus, the system can be based on system topology to simplify the product strategy. The technical strategy involves a review of upcoming technologies and solutions. The strategy analysis process references the main platform interfaces, such as PCIe, CXL, USB, NVMe, and security, in order to understand the risks and benefits of changes in new technologies.
Subjects were divided into five main specification improvements. In order to clarify the relative contributions of these specifications, a multiple regression analysis for the changes was performed. Analyses of various items were used to detect and predict significant differences among varieties, as well as dependency across different specifications for systems.
4.1. Technical Strategy through PCIe
In 2021, PCIe 5.0 was introduced. Related products to PCIe 5.0 started on different product plans. PCIe 4.0 and PCIe 5.0 for NVMe/M.2 storage and graphic devices have promoted in the market since 2021.
4.2. Technical Strategy Using CXL
In 2020, CXL rev.2.0 was released, based on PCIe 5.0 and the native PCIe 5.0 protocol. CXL modifies PCIe layer protocols and behavior to extend the capability of the high-speed serial bus. The market for PCIe 4.0 devices in 2020 and 2021 took advantage of this demand. For the server market, PCIe 5.0 and CXL were introduced in 2021 and 2022. CXL replaces part of the CPU memory and cache behavior to achieve a root complex increase to cover memory resources. These changes address the root complex bottleneck in the PCIe topology with a high-speed serial bus such as PCIe 5.0. These changes in the PC topology for high-speed serial buses allow the release of the memory resource control method from the CPU root complex to the CXL root complex. System resources are managed through the CXL bus, which contains cache behavior, in order to realize the system as a component base through the CXL bus for usage. A virtual channel with multiple access methods allows CXL to work more efficiently.
4.3. Technical Strategy Using USB
Thunderbolt 3 was included in USB and became USB 4.0. Thunderbolt 3 with PCIe and DP is included in USB 4.0, which extends the USB pin device and protocols for some combined features through the USB connector. Based on the Type-C cable with different pin definitions, Thunderbolt enables more protocols: USB, Display Port, PCIe, and Thunderbolt. Power delivery methods were also enhanced [
24,
35].
4.4. Technical Strategy through Security
TPM with security IC has been a major feature of recent applications. Security solutions in PC systems focus on TPM and chipset security solutions using SHA 256 and RSA 2048 with Public Key Cryptography Standards (PKCS). We reviewed the security solutions that have entered the market since 2019. In software security, SHA256, SHA384, RSA 1024, 2048, and 3096 are included in the product plans. Silicon data security solutions were delivered in 2019. Chipset security is based on different strategies to work on multiple security solutions. Security solutions and strategies have undergone key changes since 2019 at different levels, which were based on risk analysis of current security systems in the environment of cloud computing and storage access and protection. For quantum computing, suggested solutions from the NSA have influenced security solutions. There are multiple algorithms, including RSA 3072-bit the larger SHA-384, AES-256, Diffie–Hellman (DH) 3072-bit, or the even larger ECDH with NIST P-384 and ECDSA with NIST P-384. The NSA also suggests enhancing some algorithms that have been used in previous designs [
4].
Secure solutions are based on the operating system, and the operating systems have a strategy using open-source kernels and virtual machine design architectures on CPU core design topology. These changes in the system rely on more secure solutions using hardware and software.
4.5. Technology Strategy Analysis from Intel, AMD, and nVIDIA
Intel™, AMD™, and Nvidia™ have different roadmaps to provide solutions for AI, IoT, edge computing, and cloud services.
Figure 12,
Figure 13 and
Figure 14 show solutions from Intel™, AMD™, and Nvidia™. Each product strategy is based on an individual vision to design the production line for different aspects of the market [
46]. AMD™ provides GPU and CPU solutions for software in the industry. NVIDIA™ provides GPU solutions for embedded, desktop, data center, and cloud settings with software solutions for market demand [
26,
47]. Intel provides CPU solutions for applications demand. The technical analysis is based on Intel™, AMD™, and Nvidia™ technologies. The product strategy is based on serial bus and security to review market requirements [
48,
49,
50]. Based on the roadmap for AI and deep learning solutions produced by Intel™and Nvidia™, hardware and software solutions have been combined for AI and the IoT. Nvidia™ provides market and application demand solutions with its hardware and software solutions. Intel™and AMD™ provide hardware solutions and software solutions for market demand. The demand for 5G applications has been met by products from Intel™, AMD™, and Nvidia™.
5. Strategies for Products Design in AI, IoT, Cloud Computing, and Storage
Based on Intel™, AMD™, and Nvidia™ solutions and 5G application demands, a PC system with serial bus standard solutions using PCI Express, NVMe, CXL, and USB is the main basic technology for system configuration. For high-performance cloud computing, PCIe 4.0, PCIe 5.0, and CXL-based systems that work with NVMe are be the suggested design structures for the system. SHA-384 and RSA-3096 with security features will be the system requirements system from 2020. For the IoT, security solutions from the secured IC will help IoT security solutions in a 5G environment [
51]. Power concerns in the IoT environment involve USB-based power delivery, which can reduce power consumption while the device is in an active state. For 5G, 3GPP TR 22.864, and high video solutions in a 5G environment setting with high data transfer rate, these service requirements probably rely on NVMe storage and network services [
7]. Data transfer through the cloud can also consume power and run-time system power management is a consideration.
For coming CXL changes, the PCIe bus with speeds up to 16/32G and upcoming 64G will enhance the chipset interface bandwidth for the platform design structure. The serial bus bandwidth with device usage methods could impact power and performance, and some direct resource usage methods for storage and memory could help to reduce the host control methods and the impact of the processor or controller.
USB 4.0 includes Thunderbolt, and USB enables the DP and PCIe through USB connections. This power with data transfer enhancement could enable new products based on USB 4.0. Power Delivery (PD) with various power ranges may enhance platform design for innovations.
Using these technical strategies with application demand, strategies for products could reference these solutions as suggestions.
5.1. Product Strategy for AI and the IoT
AI with IoT is a system that would have multiple components in the environment. Based on the access components of the AI and IoT environment for specific requirements, power and security enhancements for products must satisfy specific system needs [
4,
52]. A small system designed on modular lines could extend specific features through an interface. USB has released some capabilities for these market requirements. The combined security solutions are the basic component models of the IoT and AI market, which reduces the performance impact of the software security solutions. The strategy for software solutions moves from a hardware abstraction layer structure to an open-source kernel with a virtual machine in the operating system (OS) and software. To secure the system, more hardware security solutions will be combined in this market. USB with PD capability would provide some power-related solutions with NVMe storage or NVMe over Ethernet. Based on the technical strategy, AI, and IoT, low0power requirement for edge services could satisfy more 5G application demands. These considerations are based on low-data throughput in cloud usage and more power saving when the system task workload is at a low frequency.
5.2. Product Strategy for High-Performance Cloud Computing
For cloud computing in a high-performance market, product designs will be based on performance. In PC system architecture, there are a few main technical improvements in PCIe 4.0 16G and the upcoming PCIe 5.0 32G. CXL is based on PCIe 4.0 to enhance the high-speed component in this structure. Network slicing for cloud computing, Network Function Virtualization (NFV), and Software-Defined Networking (SDN) for edge services in 5G [
53] are also involved. With multiple access points with high performance for data processed with edge devices and systems, these demands will focus on system performance with response time. In high-performance requirements for PC systems, NVME for PCIe 4.0 and coming PCIe 5.0 are still in the product roadmap. In the next generation, the CXL structure design platform will be based on PCIe capabilities to enhance traditional PC structures. CXL enhancement will contain OS, driver, and storage access topology changes for the new PC system structure. High performance is based on serial buses with protocol data sent through each path. With serial bus design systems, the host behavior across PCI Express, USB, CXL, and NVMe would impact the performance as intended, reducing both host behavior and the path of protocol transition when there is a protocol data transition for system resource usage. Data transition could provide more data throughput with protocol layer transition and a higher data payload.
5.3. Product Strategy for Storage in the Cloud
Storage in the cloud has a market roadmap for physical storage and SSD. The coming market, which is based on the 5G market for edge computing requirements, will drive NVMe-based systems to facilitate market increments. NVMe provides data transition with secure features and is also based on PCI Express bandwidth to provide greater data throughput. A topology system is included in the coming CXL. NVMe increases data transfer through its data protocols and also reduces data layer transfer through hardware signals in the system. NVMe over Ethernet reduces data from stored data in an Ethernet environment. Cloud services rely on system security, chipset security with storage security, and data transferred to the network. TPM solutions enable data security with a number of SHA usage methods. Data security and environment security will include various solutions in the cloud environment.
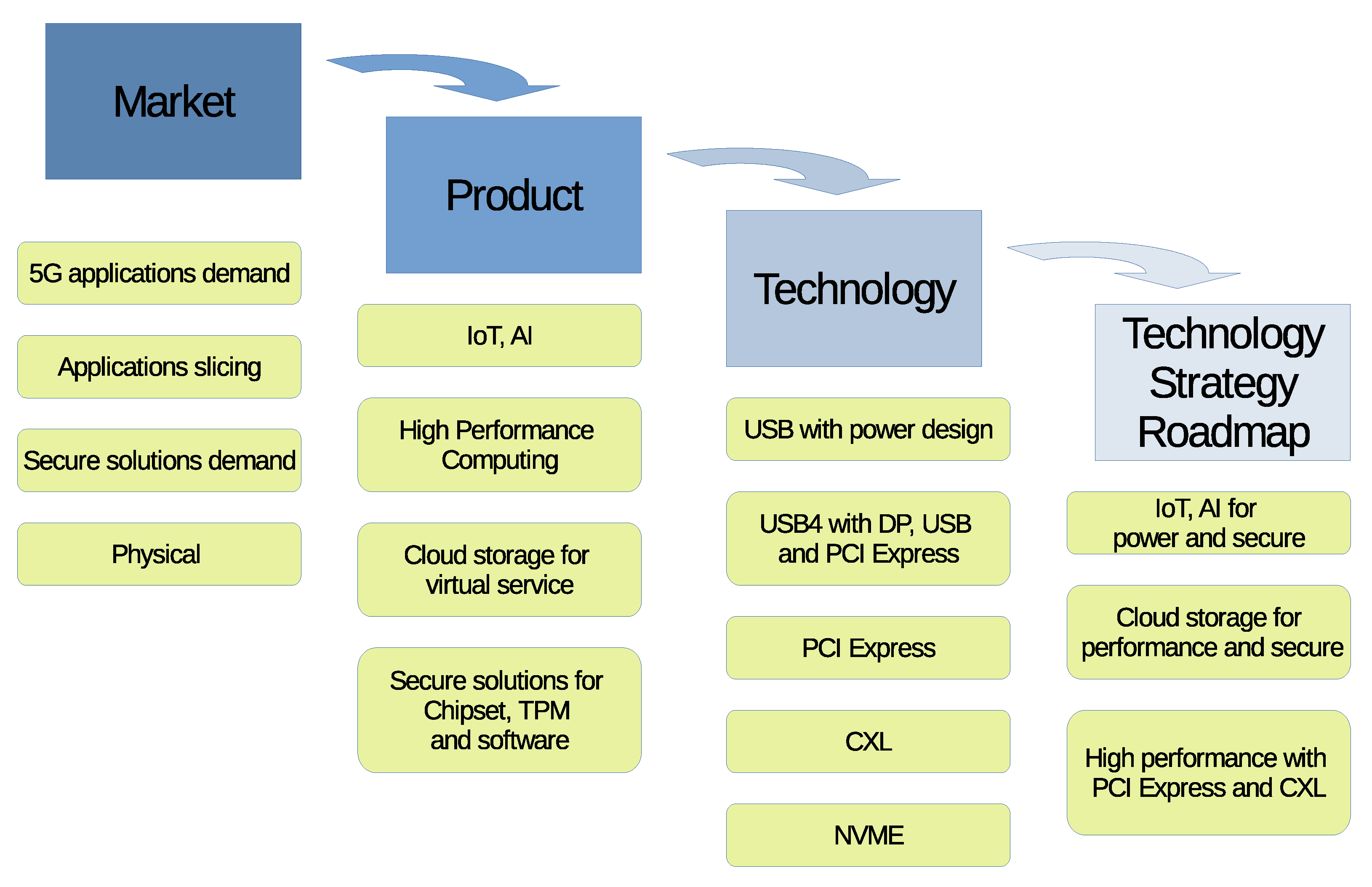
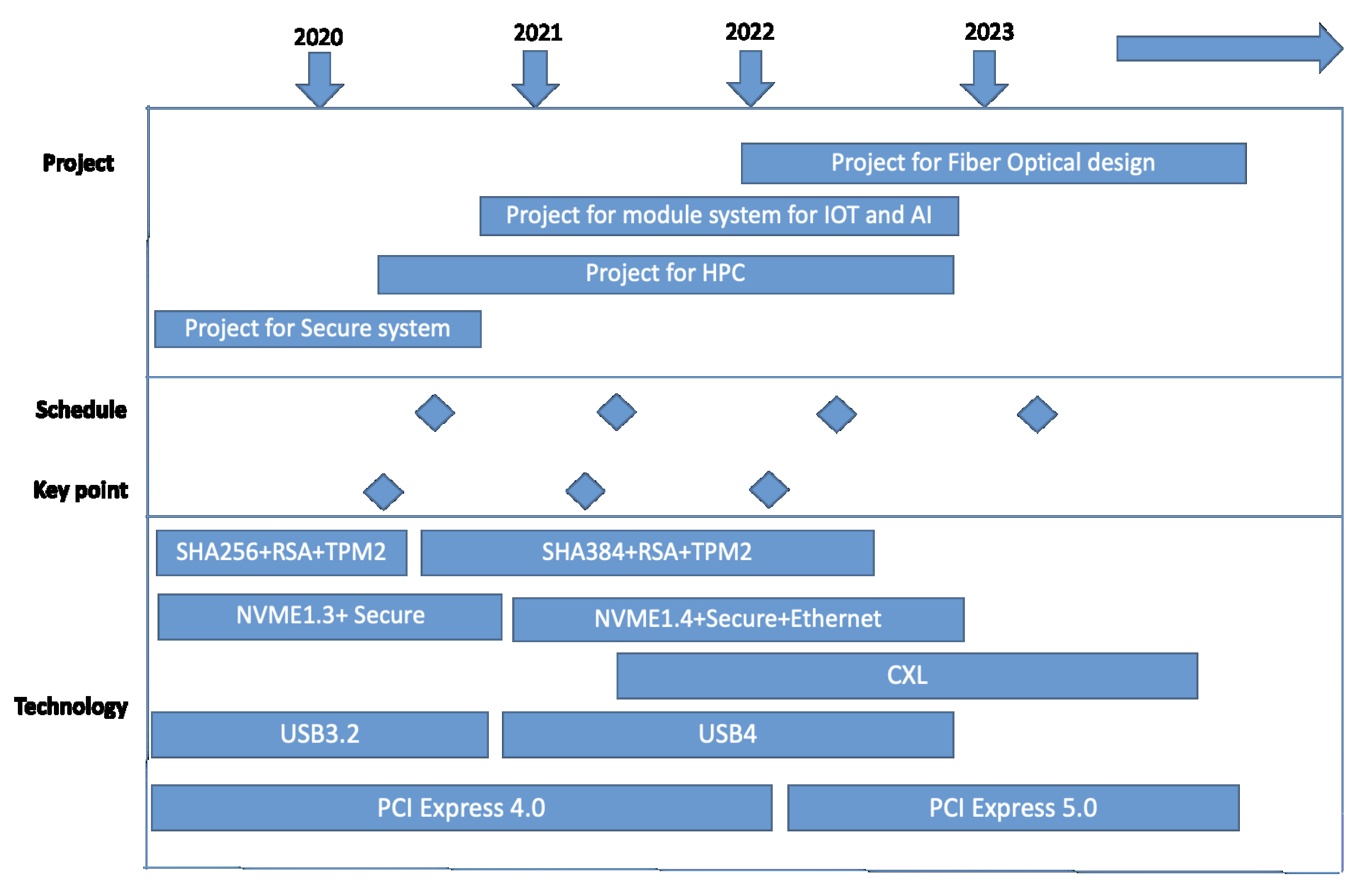
6. Technology Strategy Roadmap
The T-Plan goes through a process of assessing markets, products, and technology in PC system technology roadmaps. Based on these technology features, it seeks to deliver a product strategy roadmap, as shown in
Figure 15 [
3,
54].
In the PC industry, systems are designed for performance, and continual innovation increases speed and performance. Portable systems focus on power management. In current system designs, power consumption and performance work on different product lines. 5G applications demand the redefining of product design strategies for the 5G market. Enhanced mobile broadband, critical communication, network operation, massive machine-type communications, and enhancement of vehicle-to-everything incur specific requirements for systems. Systems will consider power resources, performance, and feature requirements. Intel™, AMD™, and Nvidia™ have deep learning roadmaps to meet market demand in terms of data throughput, power consumption, and secure communication, as seen in
Figure 16.
Secure solution enhancement involves SHA-384 with an RSA extension, chipset-based secure solutions, and software security for the cloud environment. Bandwidth with the cloud and 5G extends the cloud service. Product design following the new security solutions will facilitate market requirements for secure environments, which include AI, IoT, and cloud storage.
Advances in CXL will enhance system performance. These changes release host control through the CXL bus and will follow the PCIe high serial bus speed to PCIe 5.0. These changes involve both hardware and software. The software can be modified via Virtual Machines (VM) and multitasking processes in threads. Microsoft is following this system topology with a VM structure to take steps for the next generation of PC systems.
USB 4.0 combines PCIe and DP to extend USB applications in the market. These are technology enhancements for USB and Thunderbolt, which have been introduced in the market through Intel products. USB-IF combines these technologies, which have become industry standards since USB 4.0.
NVMe 1.4 performance follows PCIe. Interconnecting protocol communication support reduces data transfer layers through multiple root complexes, physically reducing loading for resource management across different devices. These path-reducing solutions will provide more efficient storage access in the cloud.
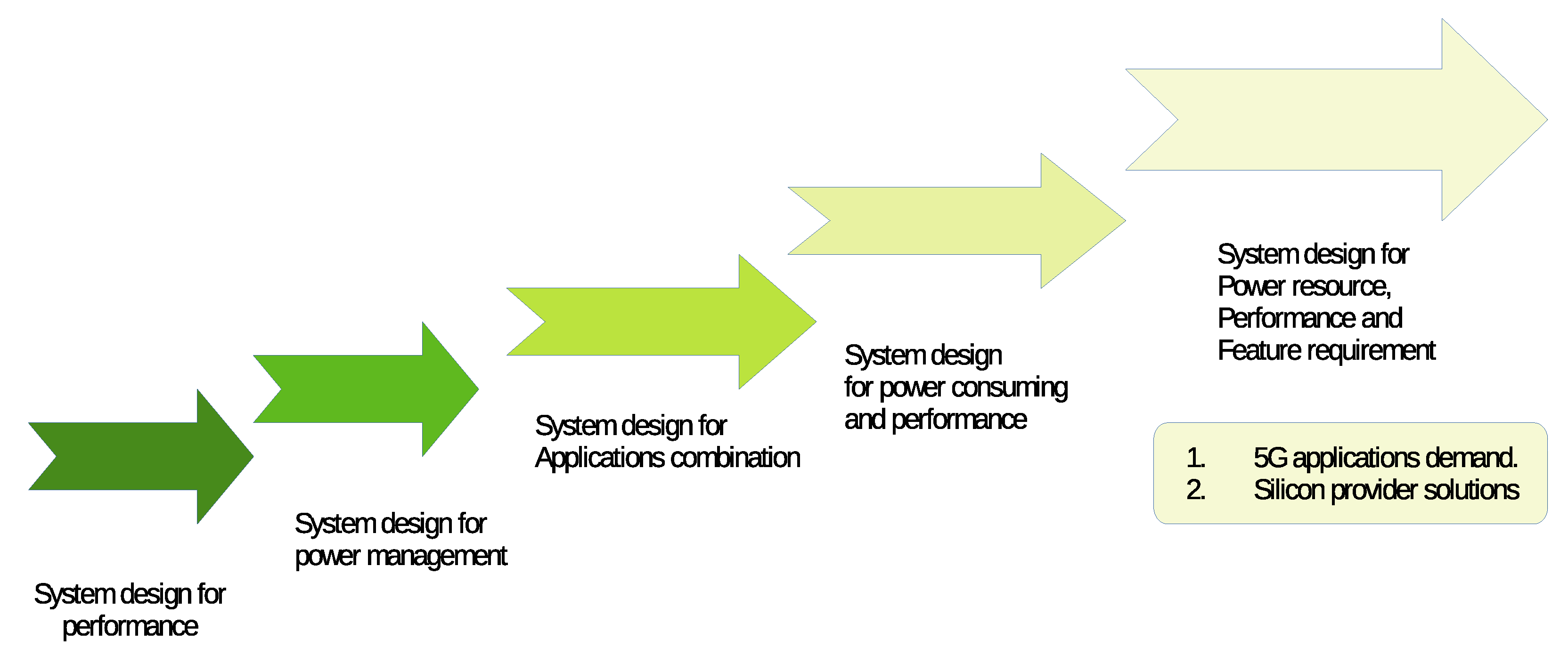
The PC industry has started to change its product strategy roadmap in terms of power source, performance, and feature requirements, as shown in
Figure 17.
6.1. Technology Strategy Roadmap for AI and IoT
For AI and IoT, the front-end side is served by environment sensors to an endpoint service. The environment varies according to the market. As shown in
Figure 12,
Figure 13 and
Figure 14, products such as cross-cloud, edge, and endpoint service provide strategies for these products.
A system in this environment face limits in terms of power and security. In a factory or outside environment, a system with low power and security would be appropriate. USB with low power design through PD and new security solutions, introduced to the market in 2020, will form the basis for technology strategy roadmaps for AI and IoT.
Changing security solution will enable secure system chains to deliver overall solutions in the security market. Original secure products in the market are relevant to security updates in various business models. Secure AI and secure IoT solutions are used in trusted platforms and trusted service chains, as shown in
Figure 18.
6.2. Technology Strategy Roadmap for High-Performance Cloud Computing
Cloud computing is focused on high-performance systems as a product design strategy. In the technology strategy roadmap for cloud computing, PCIe 4.0, PCIe 5.0, and CXL are key performance determinants of the system. PCIe 4.0 already has more design capabilities with 16 Gbs platform designs. When there is a high serial bus on the system, the new design material and design procedure is based on these changes, from the physical level to the driver level. These changes are the main risks with new technologies. CXL-based systems have been combined with PCIe for multiple support configurations. These capabilities will reduce the development cycle time for CXL systems. Software and operating systems could also follow previous design modifications for CXL platform support. The PC industry plans a safe product strategy by reviewing resources for market requirements. The CXL platform with a new system mindset would be used to allocate resources for technology strategies in this field. PCIe 5.0 and the upcoming PCIe specification use a new protocol for a new system structure. These changes will also lead to changes in the PC industry, pushing it to review the resources and capabilities of this new high-performance computing system for the market. The technology strategy roadmap in
Figure 19 reviews the main technology differences and indicates the technology base required for systems.
6.3. Technology Strategy Roadmap for Cloud Storage
The requirement for cloud storage increases each year. More data resources are updated in the cloud and there are more requirements in the market for storage. Traditional storage devices use SATA, SAS, and SCSI. AI, the IoT, and edge computing enable new storage, in line with the 5G market. The system can be redefined as a cloud or edge system. These environment-based systems have a certain technology roadmaps that focuses on PCIe, NVMe, and security. The technology roadmap is similar to the changes each year, which provide new solutions for cloud storage, as shown in
Figure 20.
6.4. Product Strategy Roadmap
Based on the technical strategy roadmap for AI, IoT, HPC, and cloud storage, there are a number of concerns in terms of market and technical resource management. In
Figure 19, HPC faces PCIe 5.0 and CXL technology changes in the coming years, which will be influenced by system enhancement changes. Technical coverage for skills and knowledge will face various challenges in different phases and layers. According to
Figure 18, the available products for the market will focus on edge requirements for AI, IoT, and security, which use efficient resources for 5G-enhanced business models. In
Figure 20, cloud storage for NVMe is also the product strategy in the roadmap. These changes will reduce product design resources and provide the product with enhanced performance.
With the T-plan method, we can review the technical coverage of the products, as shown in
Figure 17. The product strategy focuses on secure feature enhancement in 2021. The product strategy should focus on power dependency designs for the service chain and 5G environment segments for IoT. In 2022, NVMe over Ethernet solutions will provide more efficient and secure environments, which will allow storage replacement products. USB 4.0 will enhance product design in USB-based system modules.
In 2021, platform design includes a USB PD power range to identify products with power. This will enhance the product for specific markets in the edge cloud. In 2022, there will be a focus on NVMe 1.4 with Ethernet service. These products will enhance network storage. Systems will be based on NVMe features to enhance performance in a virtual environment.
According to the USB strategy, power tolerance for platform capability will go through USB 4.0 with PCIe and DP support scope to enhance platforms for more modular designs. Products from TPM 2.0 revision 1.16 (AES, ECC, ECDAA, ECDH, RSA, SHA-1, SHA256) are being updated to revision 1.38. The system will be based on TPM 2.0 revision 1.38 (enhancing AES, ECC-256, ECC-384, RSA, SHA-1, SHA-2, and SHA-3) to modify current product lines for the market. The FW version is based on TPM 2.0 to enable the feature matrix. Reselling products for security requirements with currently designed products has continued from 2020 to 2021.
7. Recommendation
With 5G applications layers, each layer defines the service chain and some specific usage area. The T-plan with PCIe-based technologies combined provides some suggestions for platform design for application demand. Edge devices with 5G applications, reliable devices, secure devices, and resource usage can follow the current study to develop more suitable products.
8. Conclusions
With respect to demand for 5G applications, the product strategy roadmap reviewed serial bus specifications with PCI Express, CXL, USB, and NVMe. System design is based on these serial bus enhancement and secure solutions to construct needs for the products. Based on these market analyses, in demand products and technologies were identified. There were some additional findings arising from this research:
- 1.
Infrastructure layers and backend services with physical and virtual secure solutions, along with more secure system design are in demand as 5G penetration rises;
- 2.
Based on the PCI Express system topology, some newly defined specifications in PCI Express, CXL, and NVMe might change in the next few years for cloud computing and storage through the Ethernet;
- 3.
With serial bus topology and the market demand for secure solutions in IoT, AI, HPC, and storage, these analysis methods have simplified the product strategy for market demand;
- 4.
This essay evaluated USB, PCIe, NVMe, CXL, and security change lists. System design structures will incorporate these changes and impact product plans in different product lines.
- 5.
We have analyzed 5G application slices in different layers. System design could be based on a logical topology with data workload and power requirements. Secure solutions using PCI Express, NVMe, USB, and TPM can provide hardware systems that can combine with software security solutions to meet market demand.
Based on this research, the PC market requires some changes for security and performance. Using a serial bus design system, the market could achieve more secure solutions. To address these changes, the strategy for system design should incorporate market demands. Using PCI Express, NVMe, USB, CXL, and security, solutions to meet 5G demand were analyzed and some appropriate solutions were provided. Based on USB PD power capability, we reviewed low-power system designs in edge service. High-performance systems based on PCIe 5.0, PCIe 6.0, and CXL to enable high-speed serial bus transitions. The analysis process followed in this research could provide a more reliable product strategy for 5G. Based on the five dimension requirements in 5G applications, we reviewed many specifications and research in AI, IoT, and cloud storage based on edge service. The analysis results provide suggested solutions for edge device products and product hardware design for PCIe-based systems with serial buses.