Joint Beamforming and Trajectory Design for Aerial Intelligent Reflecting Surface-Aided Secure Transmission
Abstract
:1. Introduction
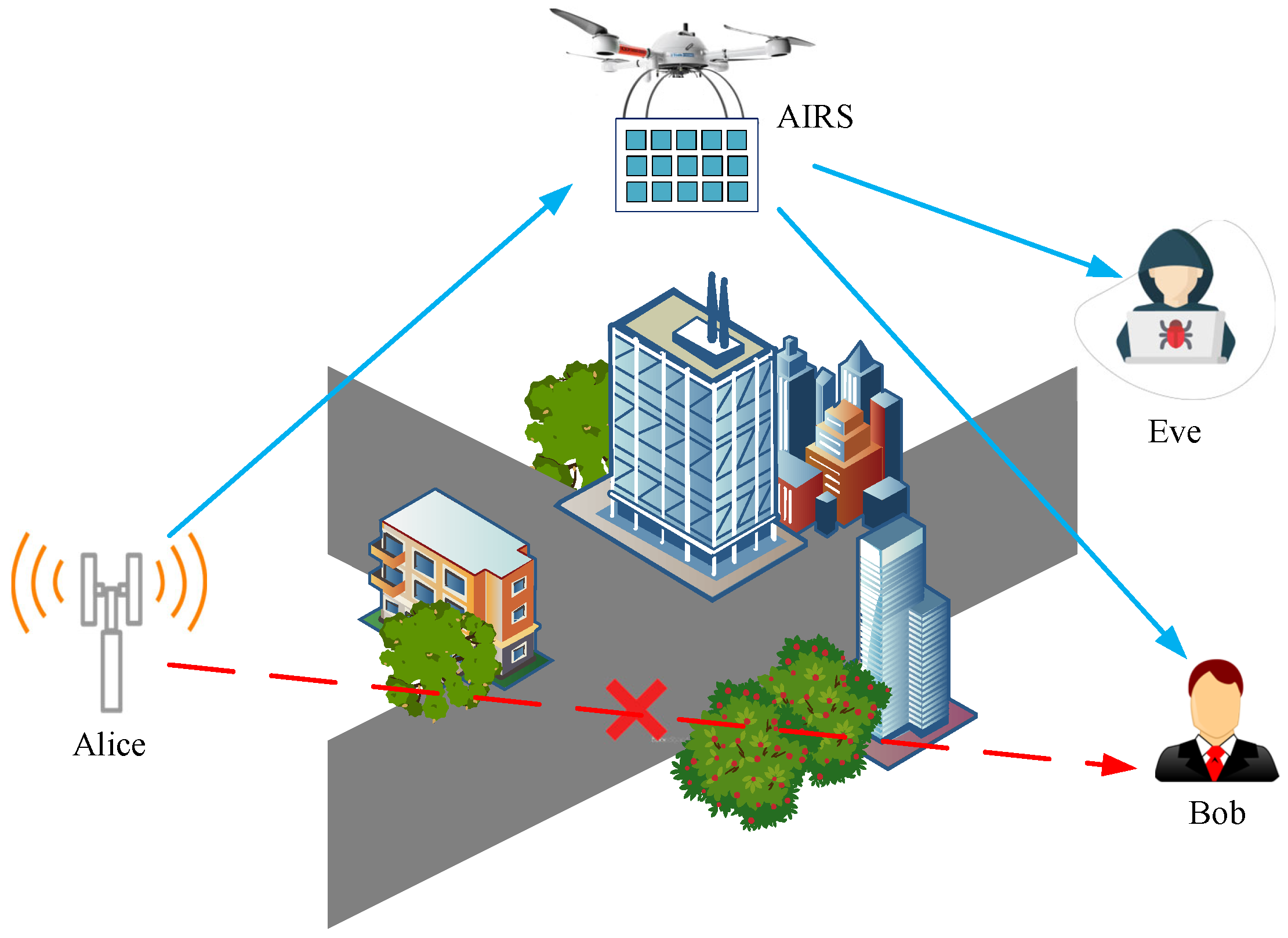
- A novel AIRS-assisted secure transmission scenario is investigated. With massive reflecting elements mounted on an aerial platform, AIRS facilitates the free-space LoS link transmission of confidential signals.
- Aiming to guarantee the information security, the average secrecy rate during the flight time is introduced as the secrecy performance metric. Then, we formulate the average secrecy rate maximization problem by jointly designing transmit beamforming, phase-shift matrix, and trajectory of AIRS.
- To cope with the non-convex problem that is formulated, we propose an iterative algorithm. The solutions are derived alternately by dividing the original problem into three sub-problems.
- For the AIRS, the Minorization-Maximization (MM) algorithm-based method is proposed to derive the closed-form solution of phase shifts. Additionally, the DDPG-based algorithm is proposed to design AIRS’s trajectory.
2. System Model
2.1. Channel Model
2.2. Signal Model
2.3. Problem Formulation
3. Average Secrecy Rate Maximization
3.1. Transmit Beamforming Design
3.2. Phase-Shift Design
3.3. AIRS Trajectory Design
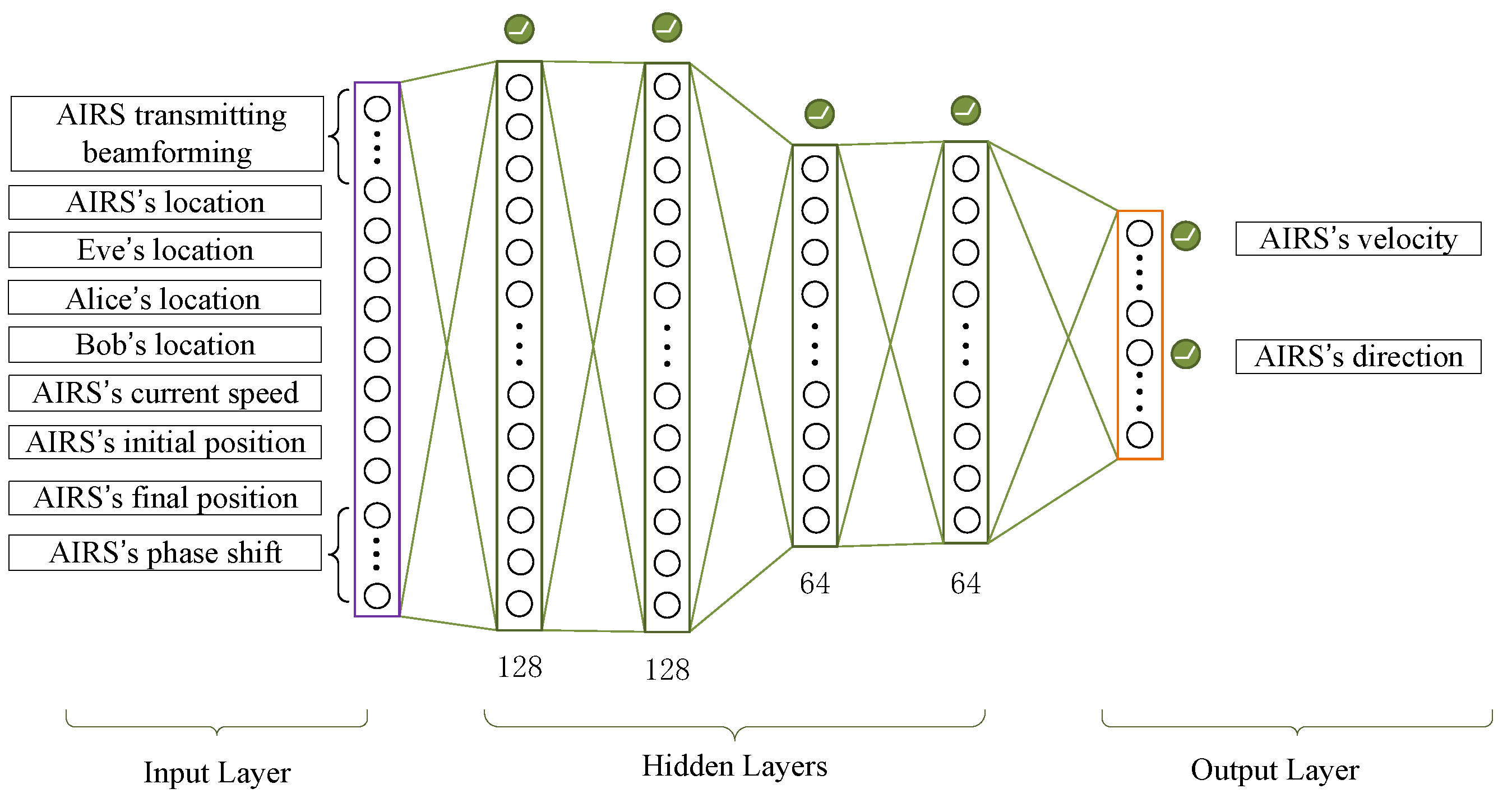
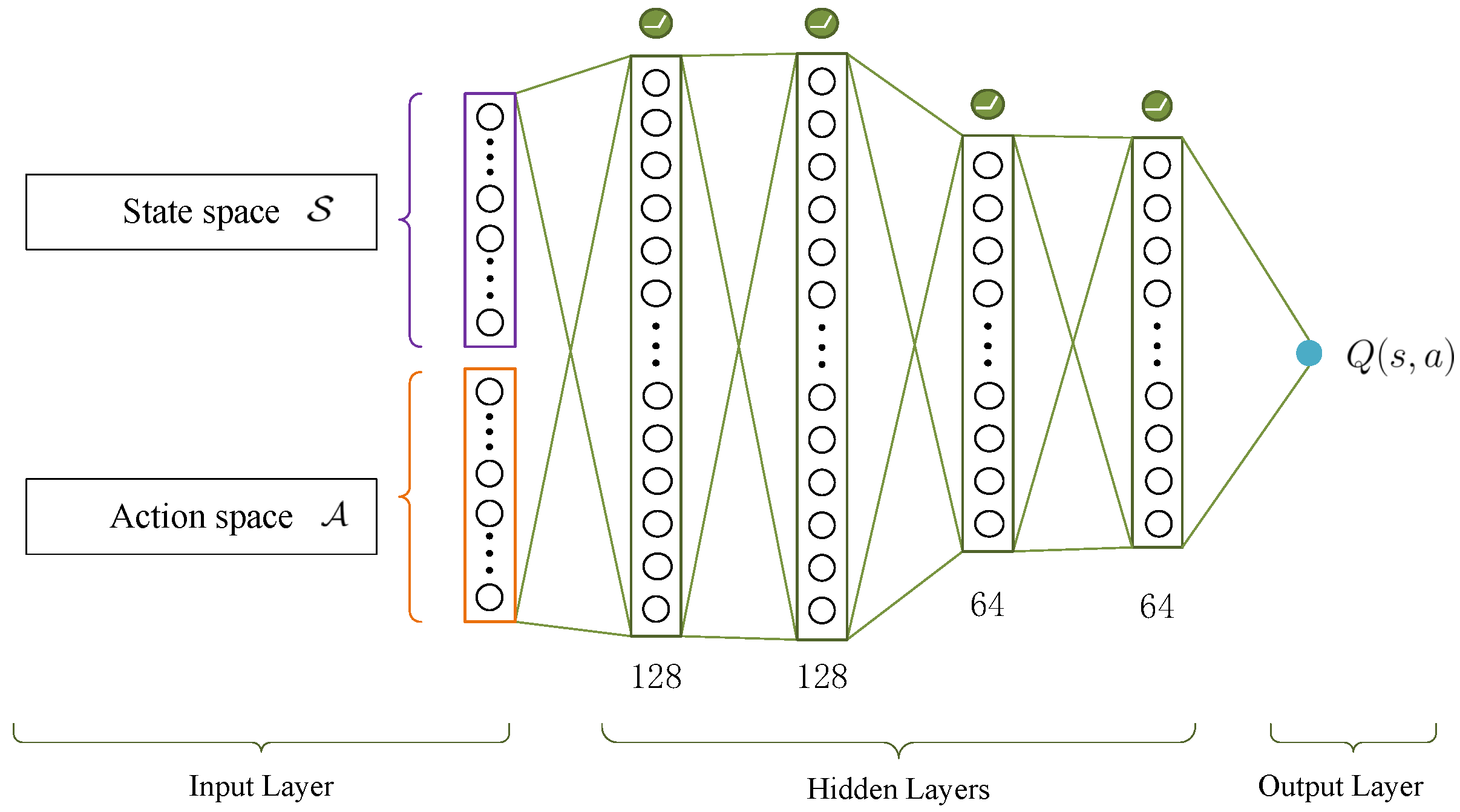
3.3.1. State, Action, and Reward
3.3.2. Loss Function
3.3.3. Neural Network
| Algorithm 1 DDPG Algorithm |
|
3.4. Iterative Algorithm Description
| Algorithm 2 Algorithm for Average Secrecy Rate Maximization |
|
3.5. Complexity Analysis
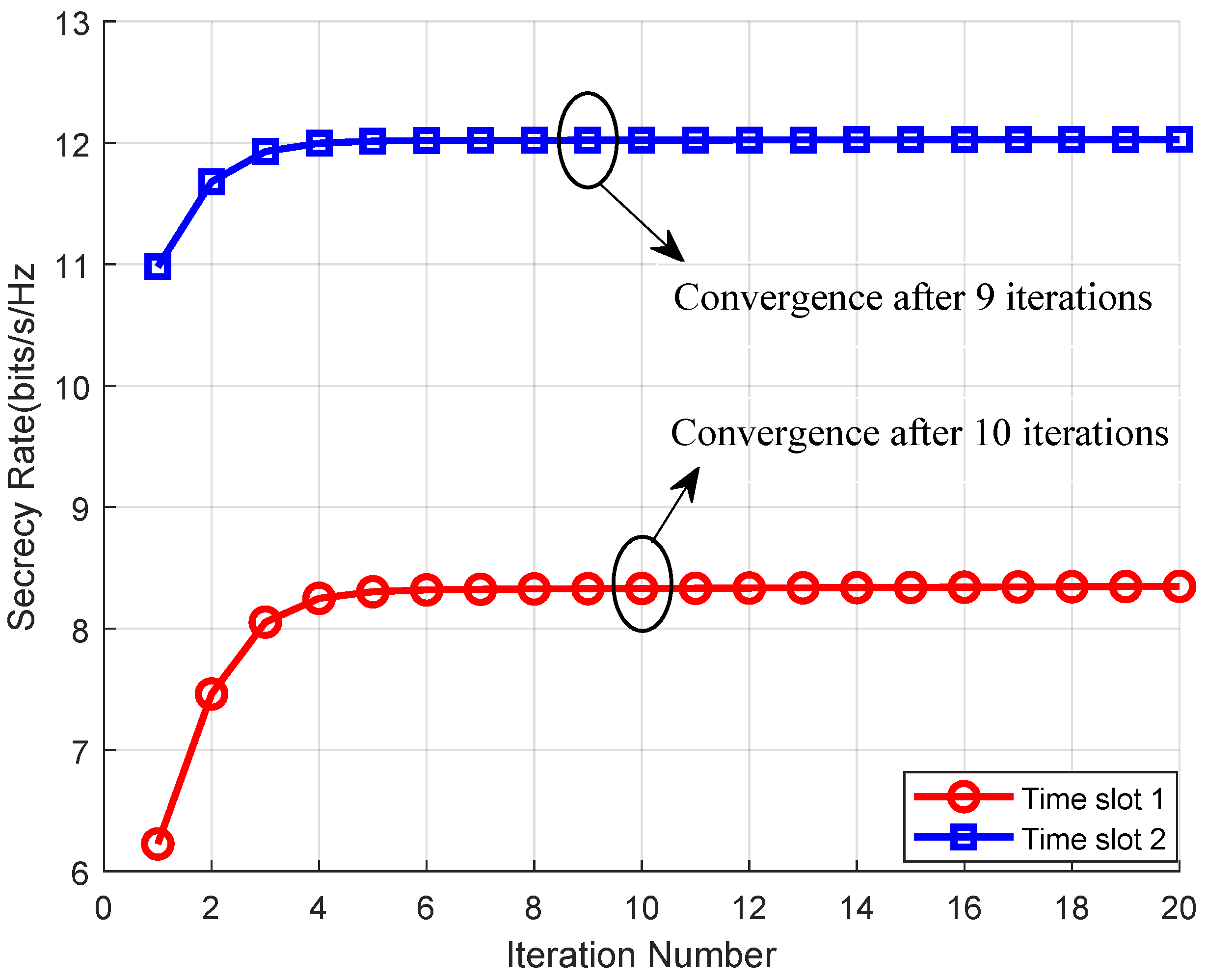
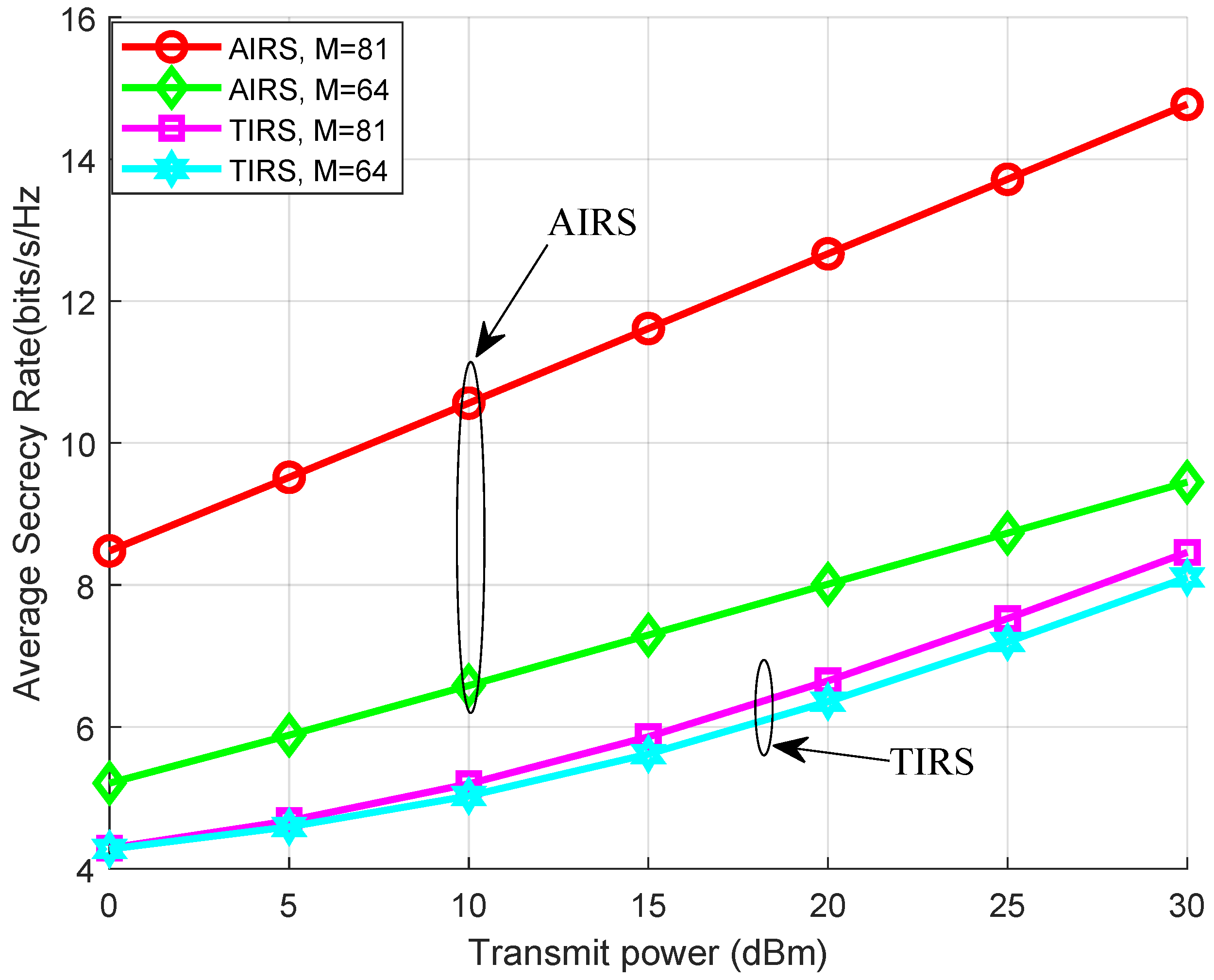
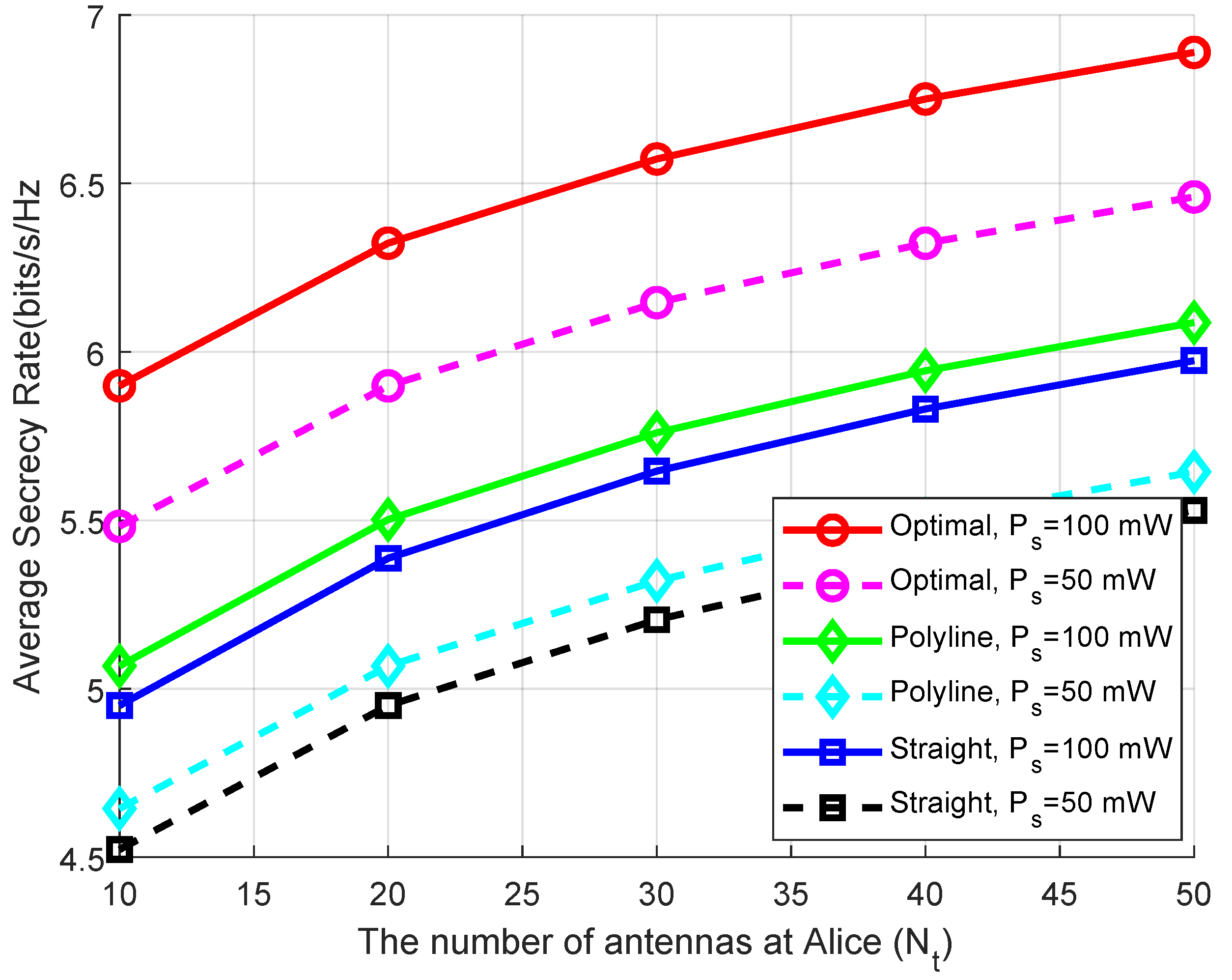
4. Simulation Results and Analysis
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Proof of Proposition 1
Appendix B. Proof of Proposition 2
References
- Chorti, A.; Barreto, A.N.; Köpsell, S.; Zoli, M.; Chafii, M.; Sehier, P.; Fettweis, G.; Poor, H.V. Context-Aware Security for 6G Wireless: The Role of Physical Layer Security. IEEE Commun. Stand. Mag. 2022, 6, 102–108. [Google Scholar] [CrossRef]
- Angueira, P.; Val, I.; Montalban, J.; Seijo, Ó.; Iradier, E.; Fontaneda, P.S.; Fanari, L.; Arriola, A. A Survey of Physical Layer Techniques for Secure Wireless Communications in Industry. IEEE Commun. Surv. Tutor. 2022, 24, 810–838. [Google Scholar] [CrossRef]
- Tang, Z.; Hou, T.; Liu, Y.; Zhang, J.; Hanzo, L. Physical Layer Security of Intelligent Reflective Surface aided NOMA Networks. IEEE Trans. Veh. Technol. 2022, 71, 7821–7834. [Google Scholar] [CrossRef]
- Li, G.; Yang, H.; Zhang, J.; Liu, H.; Hu, A. Fast and Secure Key Generation with Channel Obfuscation in Slowly Varying Environments. In Proceedings of the IEEE Conference on Computer Communications (IEEE INFOCOM), Online, 2–5 May 2022; pp. 1–10. [Google Scholar]
- Dong, L.; Han, Z.; Petropulu, A.P.; Poor, H.V. Improving Wireless Physical Layer Security via Cooperating Relays. IEEE Trans. Signal Process. 2010, 58, 1875–1888. [Google Scholar] [CrossRef]
- Qiao, J.; Zhang, H.; Zhao, F.; Yuan, D. Secure Transmission and Self-Energy Recycling With Partial Eavesdropper CSI. IEEE J. Sel. Areas Commun. 2018, 36, 1531–1543. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, R. Towards Smart and Reconfigurable Environment: Intelligent Reflecting Surface Aided Wireless Network. IEEE Commun. Mag. 2019, 58, 106–112. [Google Scholar] [CrossRef]
- Gong, S.; Lu, X.; Hoang, D.T.; Niyato, D.; Shu, L.; Kim, D.I.; Liang, Y.C. Toward Smart Wireless Communications via Intelligent Reflecting Surfaces: A Contemporary Survey. IEEE Commun. Surv. Tutor. 2020, 22, 2283–2314. [Google Scholar] [CrossRef]
- Yang, H.; Xiong, Z.; Zhao, J.; Niyato, D.; Xiao, L.; Wu, Q. Deep Reinforcement Learning-Based Intelligent Reflecting Surface for Secure Wireless Communications. IEEE Trans. Wirel. Commun. 2021, 20, 375–388. [Google Scholar] [CrossRef]
- Dong, L.; Wang, H.M. Enhancing Secure MIMO Transmission via Intelligent Reflecting Surface. IEEE Trans. Wirel. Commun. 2020, 19, 7543–7556. [Google Scholar] [CrossRef]
- Khan, W.U.; Lagunas, E.; Ali, Z.; Javed, M.A.; Ahmed, M.; Chatzinotas, S.; Ottersten, B.; Popovski, P. Opportunities for physical layer security in UAV communication enhanced with intelligent reflective surfaces. arXiv 2022, arXiv:2203.16907. [Google Scholar]
- Wu, Q.; Zhang, S.; Zheng, B.; You, C.; Zhang, R. Intelligent Reflecting Surface-Aided Wireless Communications: A Tutorial. IEEE Trans. Commun. 2021, 69, 3313–3351. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, X.; Mu, X.; Hou, T.; Xu, J.; Di Renzo, M.; Al-Dhahir, N. Reconfigurable Intelligent Surfaces: Principles and Opportunities. IEEE Commun. Surv. Tutor. 2021, 23, 1546–1577. [Google Scholar] [CrossRef]
- Huang, C.; Zappone, A.; Alexandropoulos, G.C.; Debbah, M.; Yuen, C. Reconfigurable Intelligent Surfaces for Energy Efficiency in Wireless Communication. IEEE Trans. Wirel. Commun. 2019, 18, 4157–4170. [Google Scholar] [CrossRef]
- Yu, X.; Xu, D.; Sun, Y.; Ng, D.W.K.; Schober, R. Robust and Secure Wireless Communications via Intelligent Reflecting Surfaces. IEEE J. Sel. Areas Commun. 2020, 38, 2637–2652. [Google Scholar] [CrossRef]
- Cui, M.; Zhang, G.; Zhang, R. Secure Wireless Communication via Intelligent Reflecting Surface. IEEE Wirel. Commun. Lett. 2019, 8, 1410–1414. [Google Scholar] [CrossRef]
- Dong, L.; Wang, H.M. Secure MIMO Transmission via Intelligent Reflecting Surface. IEEE Wirel. Commun. Lett. 2020, 9, 787–790. [Google Scholar] [CrossRef]
- Asaad, S.; Wu, Y.; Bereyhi, A.; Müller, R.R.; Schaefer, R.F.; Poor, H.V. Secure Active and Passive Beamforming in IRS-Aided MIMO Systems. IEEE Trans. Inf. Forensics Secur. 2022, 17, 1300–1315. [Google Scholar] [CrossRef]
- Qiao, J.; Alouini, M.S. Secure Transmission for Intelligent Reflecting Surface-Assisted mmWave and Terahertz Systems. IEEE Wirel. Commun. Lett. 2020, 9, 1743–1747. [Google Scholar] [CrossRef]
- Qiao, J.; Zhang, C.; Dong, A.; Bian, J.; Alouini, M.S. Securing Intelligent Reflecting Surface Assisted Terahertz Systems. IEEE Trans. Veh. Technol. 2022, 71, 8519–8533. [Google Scholar] [CrossRef]
- Ye, J.; Qiao, J.; Kammoun, A.; Alouini, M.S. Non-Terrestrial Communications Assisted by Reconfigurable Intelligent Surfaces. Proc. IEEE 2022. [Google Scholar] [CrossRef]
- Hashida, H.; Kawamoto, Y.; Kato, N. Intelligent Reflecting Surface Placement Optimization in Air-Ground Communication Networks Toward 6 G. IEEE Wirel. Commun. 2020, 27, 146–151. [Google Scholar] [CrossRef]
- Lu, H.; Zeng, Y.; Jin, S.; Zhang, R. Aerial Intelligent Reflecting Surface: Joint Placement and Passive Beamforming Design with 3D Beam Flattening. IEEE Trans. Wirel. Commun. 2021, 20, 4128–4143. [Google Scholar] [CrossRef]
- Lu, H.; Zeng, Y.; Jin, S.; Zhang, R. Enabling Panoramic Full-Angle Reflection via Aerial Intelligent Reflecting Surface. In Proceedings of the IEEE International Conference on Communications Workshops (ICC Workshops), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Pang, X.; Zhao, N.; Tang, J.; Wu, C.; Niyato, D.; Wong, K.K. IRS-Assisted Secure UAV Transmission via Joint Trajectory and Beamforming Design. IEEE Trans. Commun. 2021, 70, 1140–1152. [Google Scholar] [CrossRef]
- Guo, X.; Chen, Y.; Wang, Y. Learning-Based Robust and Secure Transmission for Reconfigurable Intelligent Surface Aided Millimeter Wave UAV Communications. IEEE Wirel. Commun. Lett. 2021, 10, 1795–1799. [Google Scholar] [CrossRef]
- Ge, L.; Dong, P.; Zhang, H.; Wang, J.B.; You, X. Joint beamforming and trajectory optimization for intelligent reflecting surfaces-assisted UAV communications. IEEE Access 2020, 8, 78702–78712. [Google Scholar] [CrossRef]
- AlJubayrin, S.; Al-Wesabi, F.N.; Alsolai, H.; Duhayyim, M.A.; Nour, M.K.; Khan, W.U.; Mahmood, A.; Rabie, K.; Shongwe, T. Energy Efficient Transmission Design for NOMA Backscatter-Aided UAV Networks with Imperfect CSI. Drones 2022, 6, 190. [Google Scholar] [CrossRef]
- Khan, W.U.; Jamshed, M.A.; Lagunas, E.; Chatzinotas, S.; Li, X.; Ottersten, B. Energy efficiency optimization for backscatter enhanced NOMA cooperative V2X communications under imperfect CSI. IEEE Trans. Intell. Transp. Syst. 2022. [Google Scholar] [CrossRef]
- Ihsan, A.; Chen, W.; Khan, W.U. Energy-efficient backscatter aided uplink NOMA roadside sensor communications under channel estimation errors. arXiv 2021, arXiv:2109.05341. [Google Scholar]
- Alfattani, S.; Jaafar, W.; Hmamouche, Y.; Yanikomeroglu, H.; Yongaçoglu, A.; Đào, N.D.; Zhu, P. Aerial platforms with reconfigurable smart surfaces for 5G and beyond. IEEE Commun. Mag. 2021, 59, 96–102. [Google Scholar] [CrossRef]
- Wyner, A.D. The wire-tap channel. Bell. Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Lange, K. Optimization (Chapter 8); Springer Science & Business Media: New York, NY, USA, 2013; Volume 95, pp. 185–219. [Google Scholar]
- Peng, Z.; Zhang, Z.; Pan, C.; Li, L.; Swindlehurst, A.L. Multiuser full-duplex two-way communications via intelligent reflecting surface. IEEE Trans. Signal Process. 2021, 69, 837–851. [Google Scholar] [CrossRef]
- Yu, X.; Xu, D.; Schober, R. Enabling Secure Wireless Communications via Intelligent Reflecting Surfaces. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]

| Reference | Scenario | Description | Design Objective |
|---|---|---|---|
| [15,16] | Secure communication in MISO system | TIRS-assisted secure communication between multi-antenna access point and a ground user | Maximize the secrecy rate of the legitimate communication link |
| [17,18] | Secure transmission in MIMO system | TIRS-aided secure transmission from BS to multi-users | Maximize the secrecy rate |
| [19,20] | Secure transmission in mmWave/THz systems | TIRS-aided secure transmission of terrestrial network in mmWave/THz bands | Maximize the system secrecy rate |
| [22] | AIRS-aided cellular network | AIRS-assisted communication between BS and aerial users | Maximize mean signal-to-interference-noise ratio (SINR) |
| [23,24] | AIRS-assisted communication system | AIRS-enhanced terrestrial communication within a given area | Maximize the worst-case signal-to-noise ratio |
| [25] | Secure UAV communication system | TIRS-aided secure transmission from UAV to a terrestrial user | Maximize the average secrecy rate |
| [26] | Robust secure UAV communication system | TRIS-aided secure transmission in mmWave UAV system with imperfect CSI | Maximize the sum secrecy rate of all users |
| [27] | TIRS-aided UAV communication system | Multi-TIRSs aided communication from UAV to ground user | Maximize the received power at the ground user |
| No. | State | Numeric Types | Dimension |
|---|---|---|---|
| 1 | transmit beamformer | complex vector | |
| 2 | phase-shift vector of AIRS | complex vector | M |
| 3 | AIRS’s current speed | real scalar | 1 |
| 4 | location of Alice | real vector | 3 |
| 5 | location of Bob | real vector | 3 |
| 6 | location of Eve | real vector | 3 |
| 7 | starting position of AIRS | real vector | 3 |
| 8 | target position of AIRS | real vector | 3 |
| 9 | current location of AIRS | real vector | 3 |
| Parameter | Description | Parameter | Description |
|---|---|---|---|
| action at n-th time slot | state at n-th time slot | ||
| current actor network | target actor network | ||
| current critic network | target critic network | ||
| distance from to target | reward function | ||
| binary penalty indicator on | discount factor | ||
| binary penalty indicator on | size of mini-batch |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Y.; Qiao, J.; Zhang, C. Joint Beamforming and Trajectory Design for Aerial Intelligent Reflecting Surface-Aided Secure Transmission. Electronics 2022, 11, 2802. https://doi.org/10.3390/electronics11182802
Wang Y, Qiao J, Zhang C. Joint Beamforming and Trajectory Design for Aerial Intelligent Reflecting Surface-Aided Secure Transmission. Electronics. 2022; 11(18):2802. https://doi.org/10.3390/electronics11182802
Chicago/Turabian StyleWang, Yanping, Jingping Qiao, and Chuanting Zhang. 2022. "Joint Beamforming and Trajectory Design for Aerial Intelligent Reflecting Surface-Aided Secure Transmission" Electronics 11, no. 18: 2802. https://doi.org/10.3390/electronics11182802






