Robust and Fast Converging Cross-Layer Failure Correction in Segment-Routed Networks
Abstract
1. Introduction
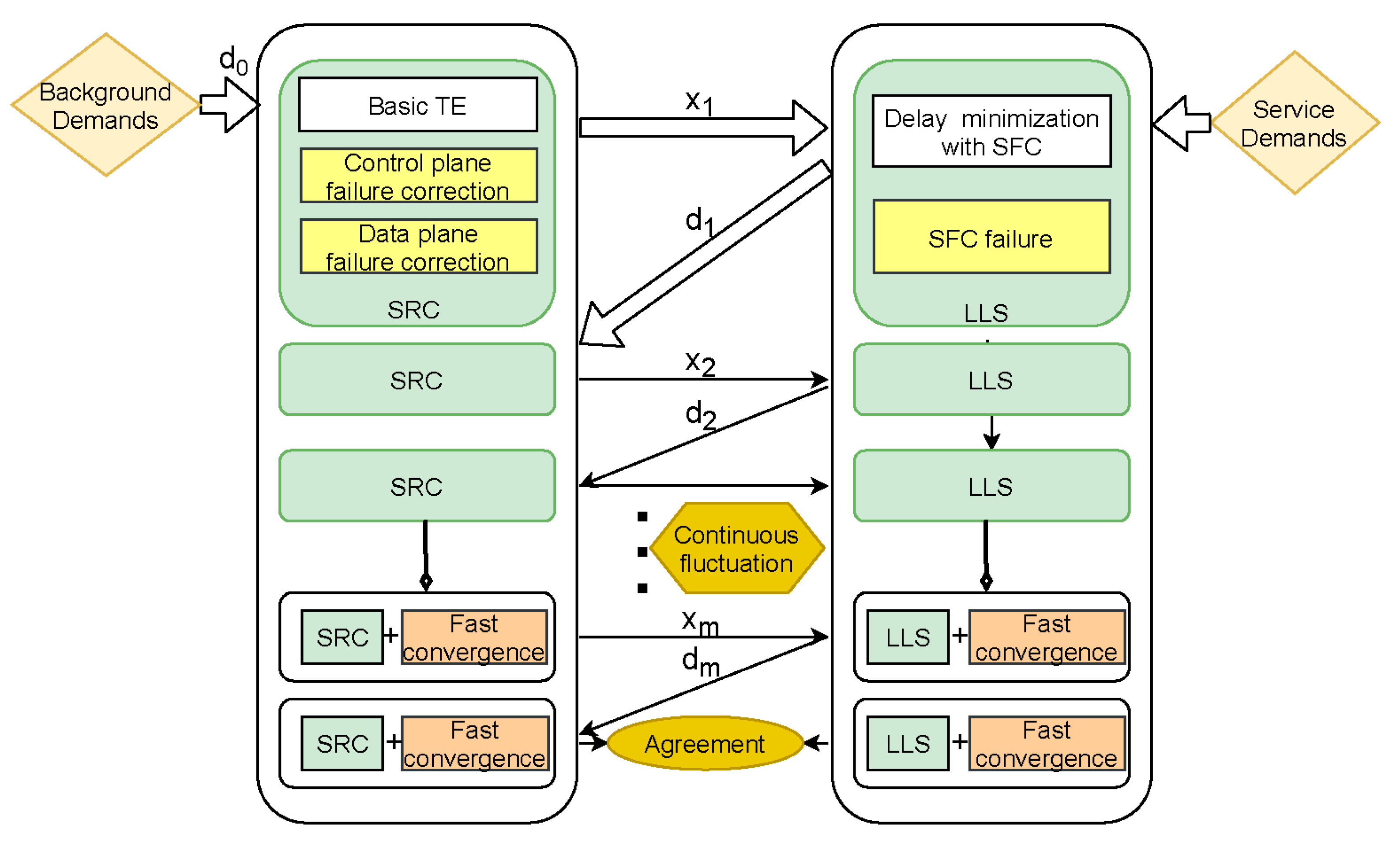
- In order to achieve better performance for time-sensitive applications, we combine NFV and cross-layer network models and propose SRC and LLS methods as the basic framework of this paper.
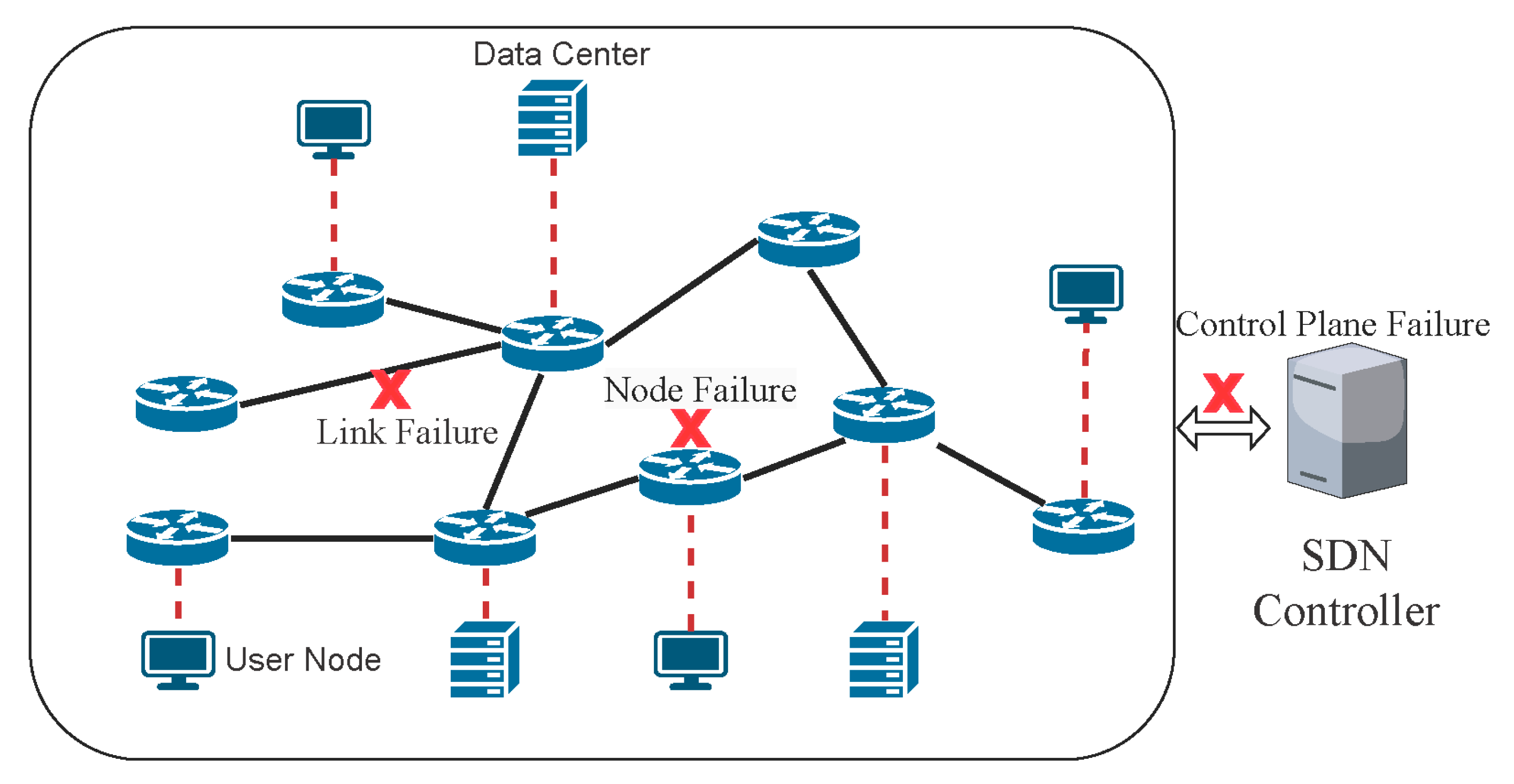
- To deal with the network failures in the underlay, we propose a failure correction mechanism for SRC. Our method can handle both data plane failures and control plane failures.
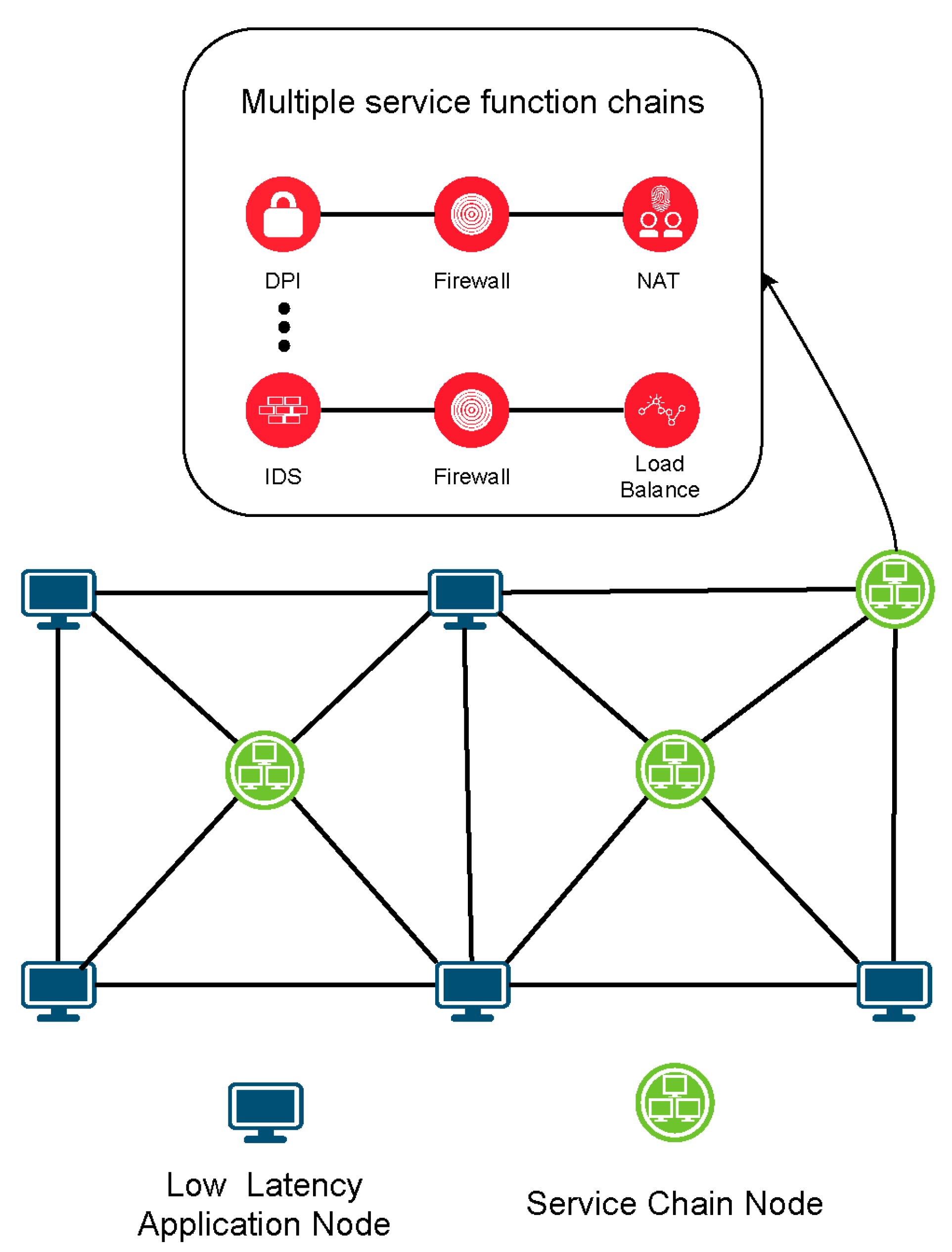
- In order to handle the unique failure types of the logic layer, we add an SFC failure handling mechanism to the LLS to ensure uninterrupted network transmission and ensure the performance of time-sensitive applications.
- We build a cross-layer interaction model regarding LLS and SRC. We treat the interaction as a repeated game [8]. SRC and LLS alternately and selfishly propose conditions until they reach a consensus. We design two strategies in our cross-layer model to accelerate network convergence to reduce the performance degradation caused by fluctuations in networks where errors may occur.
- In the course of our comparative experiment, we gradually add the mechanisms we introduced to the basic version of the framework, observing the impact of different mechanisms on the cross-layer interaction process, proving the effectiveness of our strategy, and the entire framework can guarantee the performance of time-sensitive applications.
2. Related Work
2.1. SFC
2.2. Network Failure Correction
2.3. Cross-Layer Model
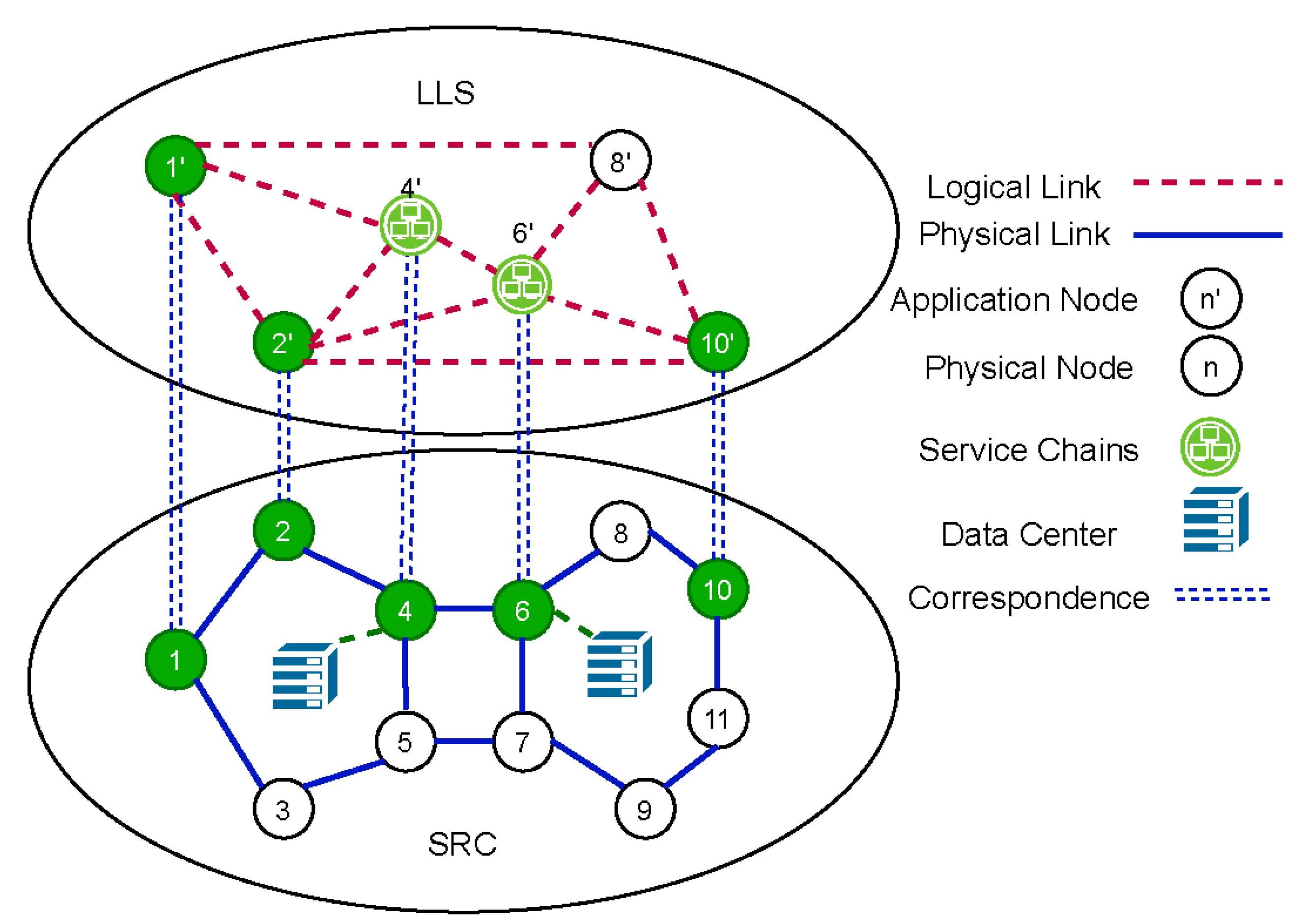
3. System Model
3.1. SRC Model
3.2. LLS Model
3.3. Cross-Layer Model
| Algorithm 1 Cross-Layer Model Iterative Algorithm |
| Input: , , , , , |
| Output: |
| 1: |
| 2: |
| 3: |
| 4: while () do |
| 5: |
| 6: |
| 7: |
| 8: |
| 9: end |
| 10: return |
4. Failure Correction in a Cross-Layer Architecture
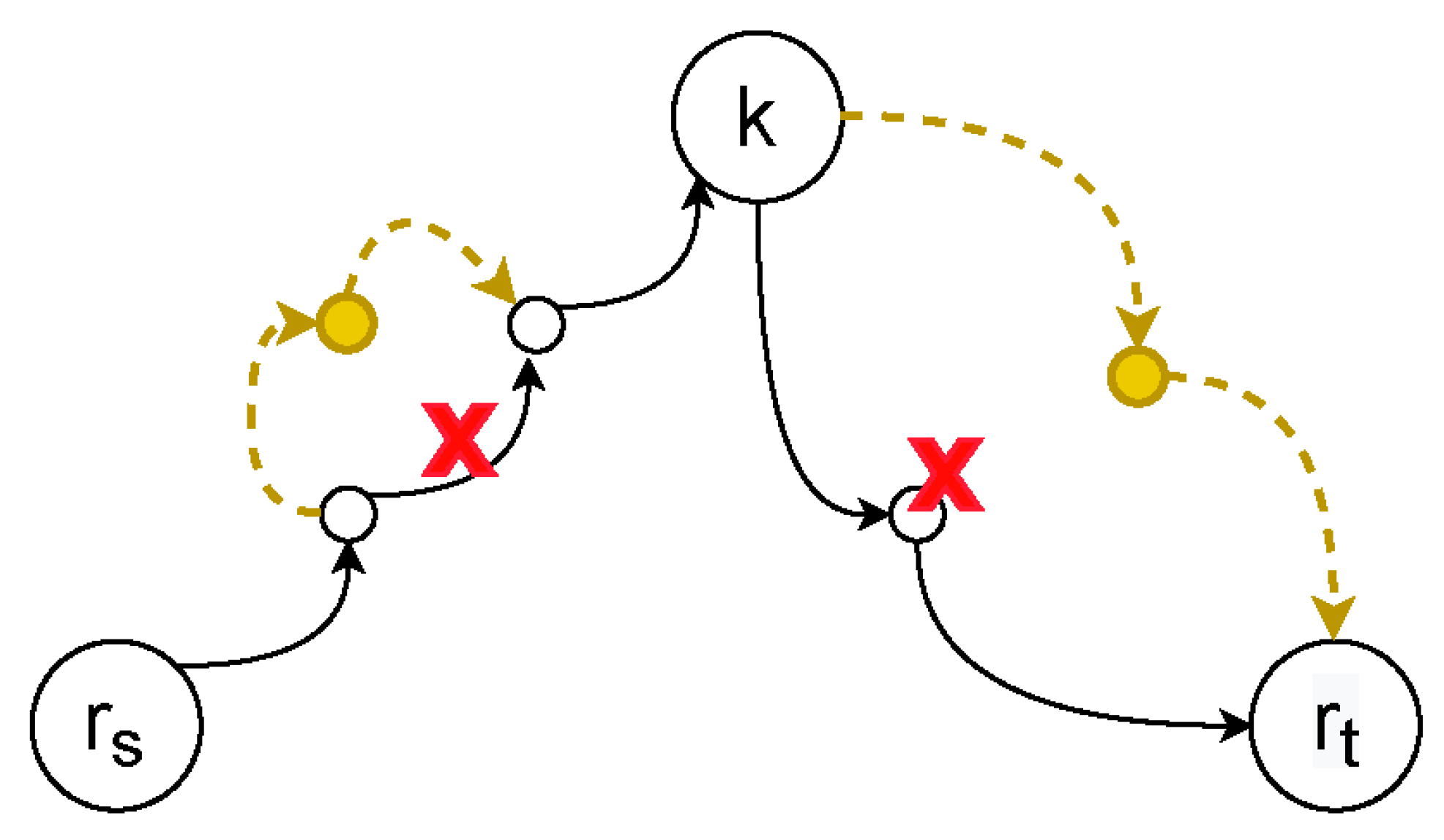
4.1. Failure Correction in SRC
4.1.1. Correction of Data Plane Failures
4.1.2. Correction of Control Plane Failures
4.2. Failure Correction in LLS
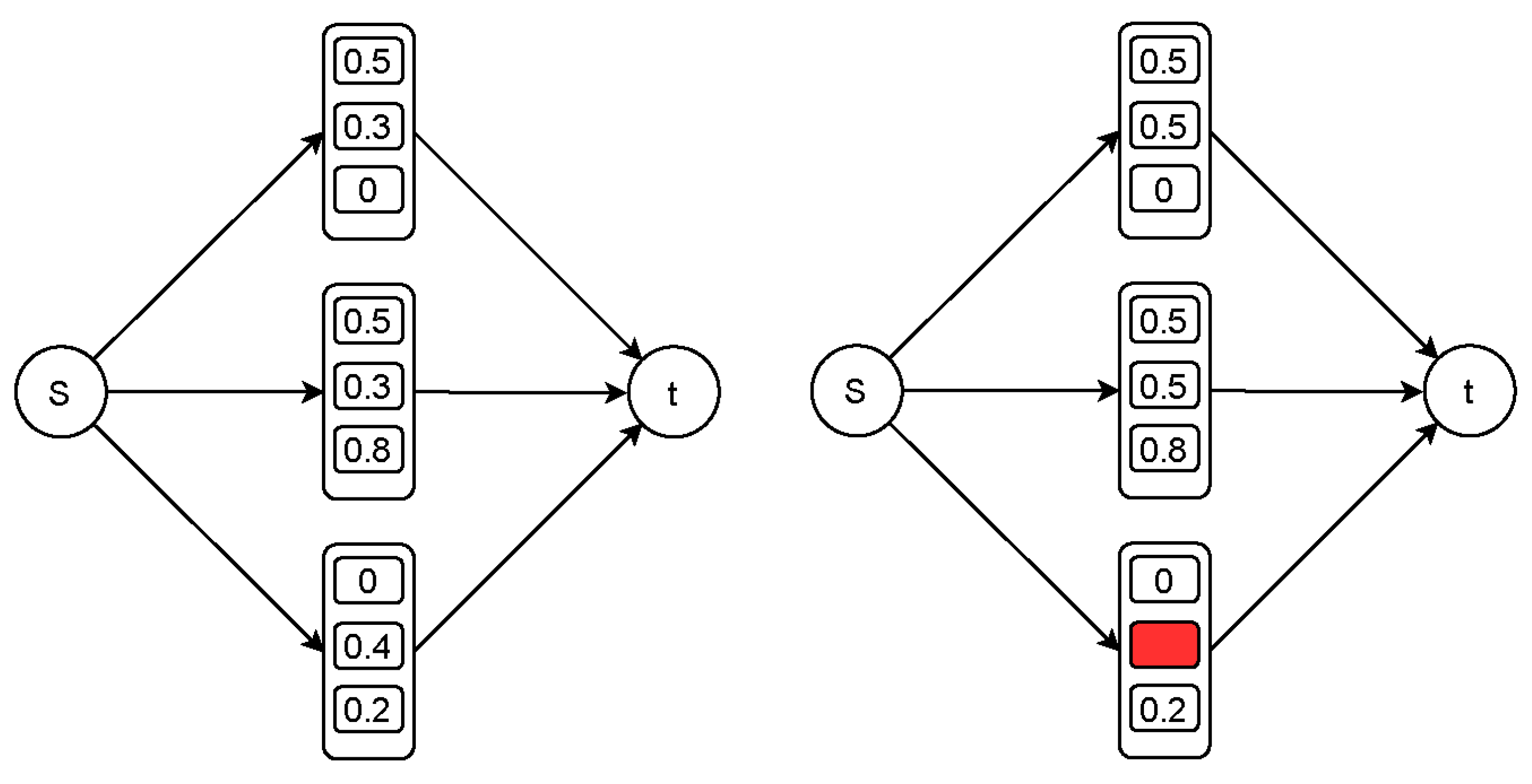
5. Fast Convergence in the Interaction
5.1. SRC Strategy for Fast Convergence
5.2. LLS Strategy for Fast Convergence
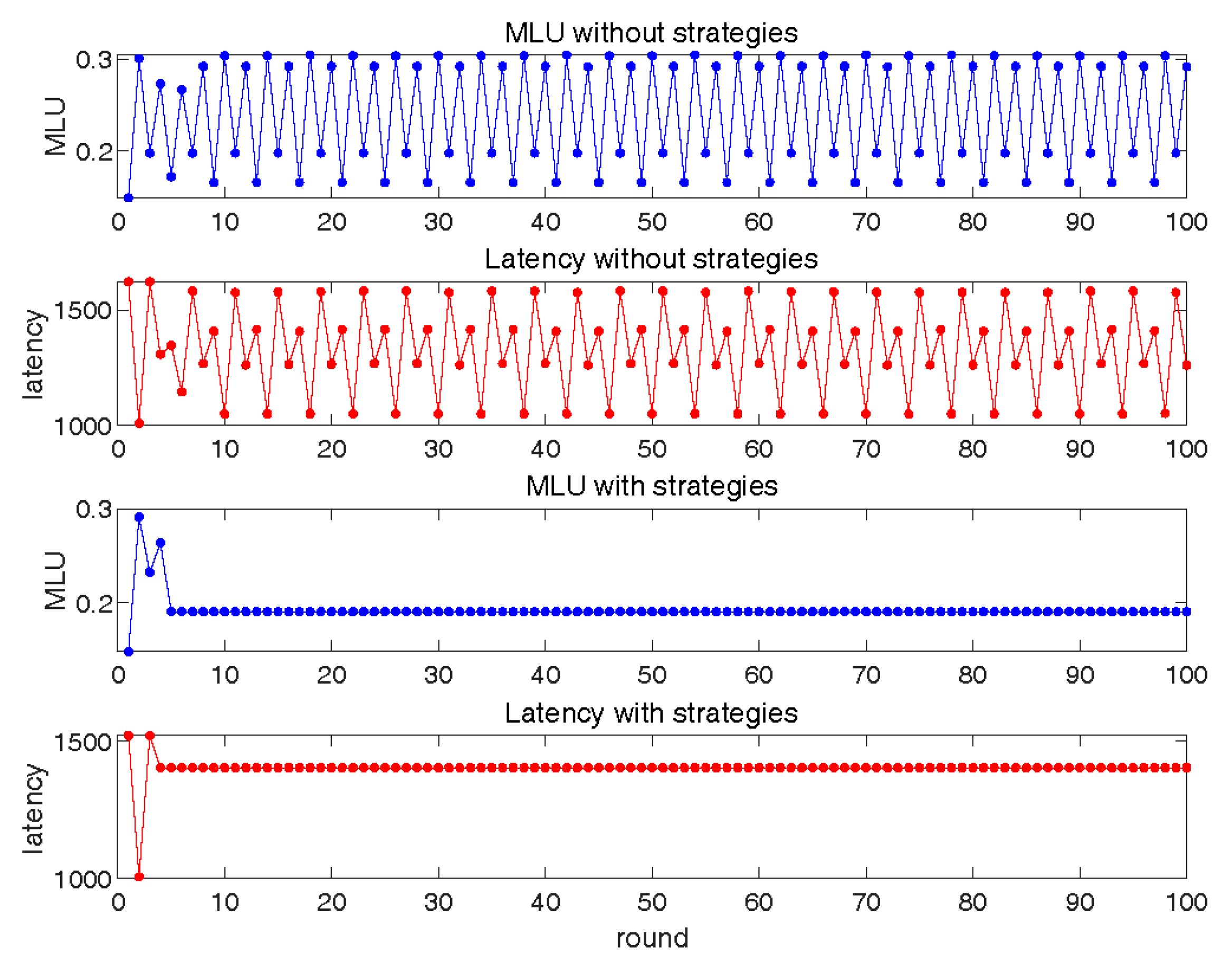
6. Performance Evaluation
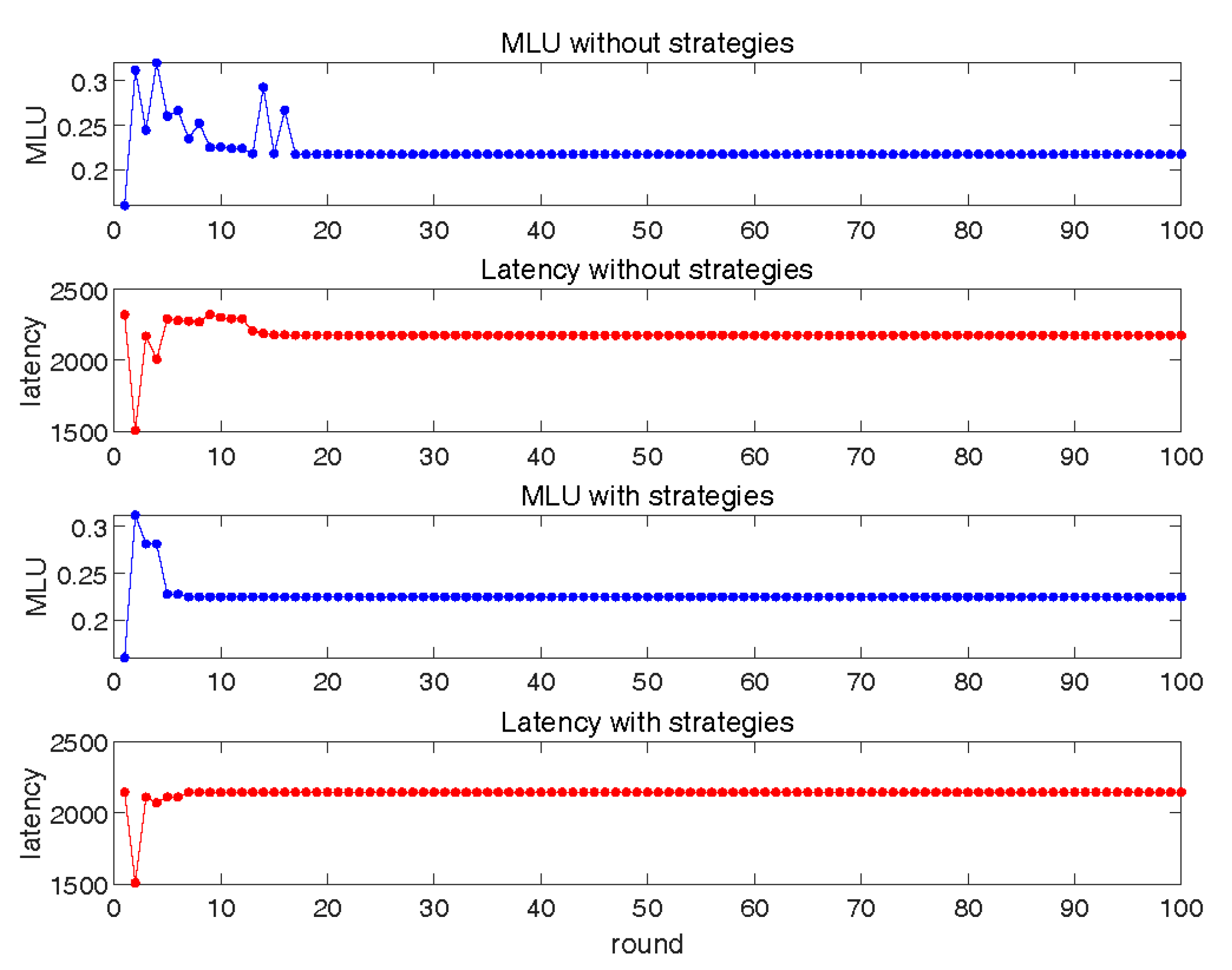
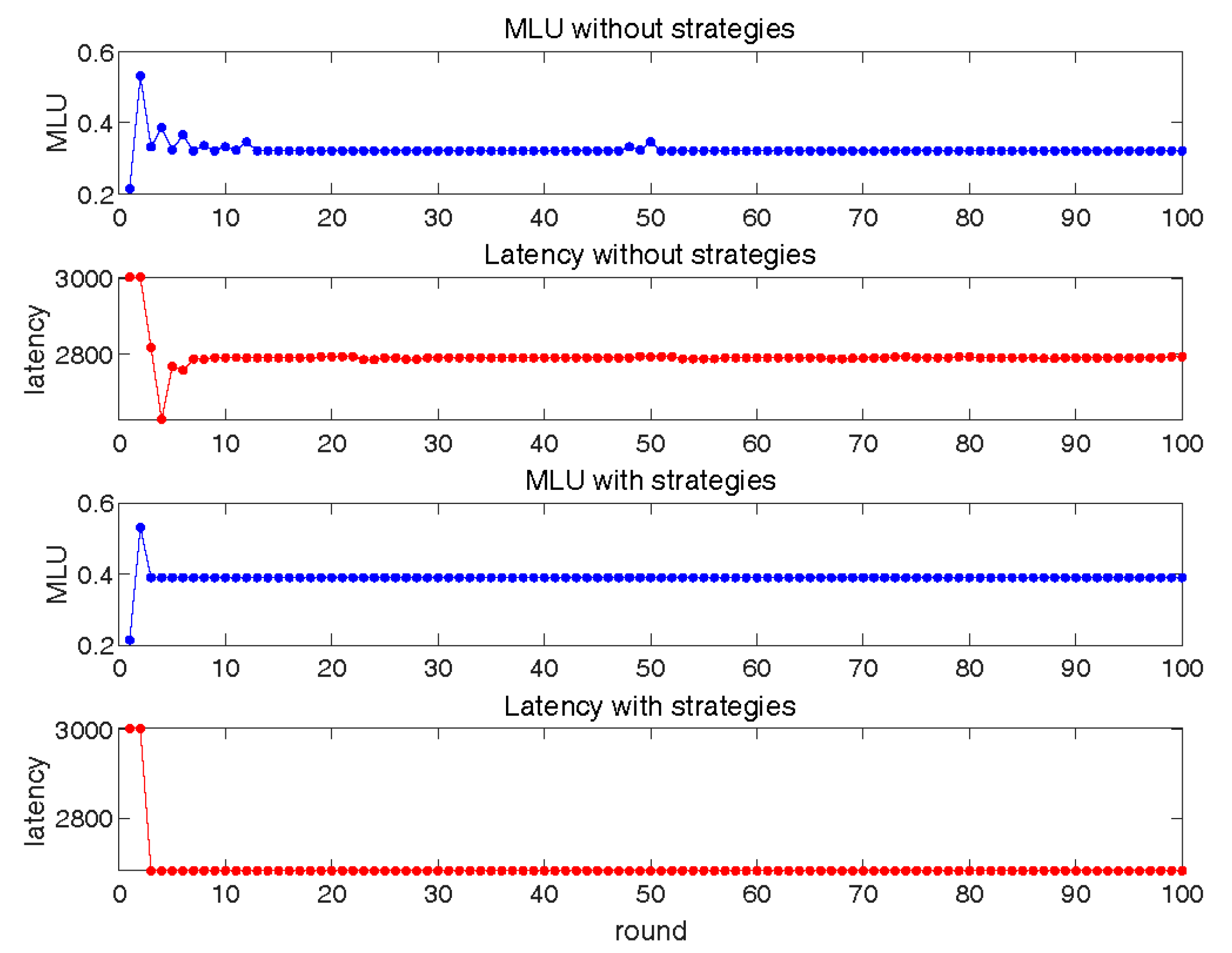
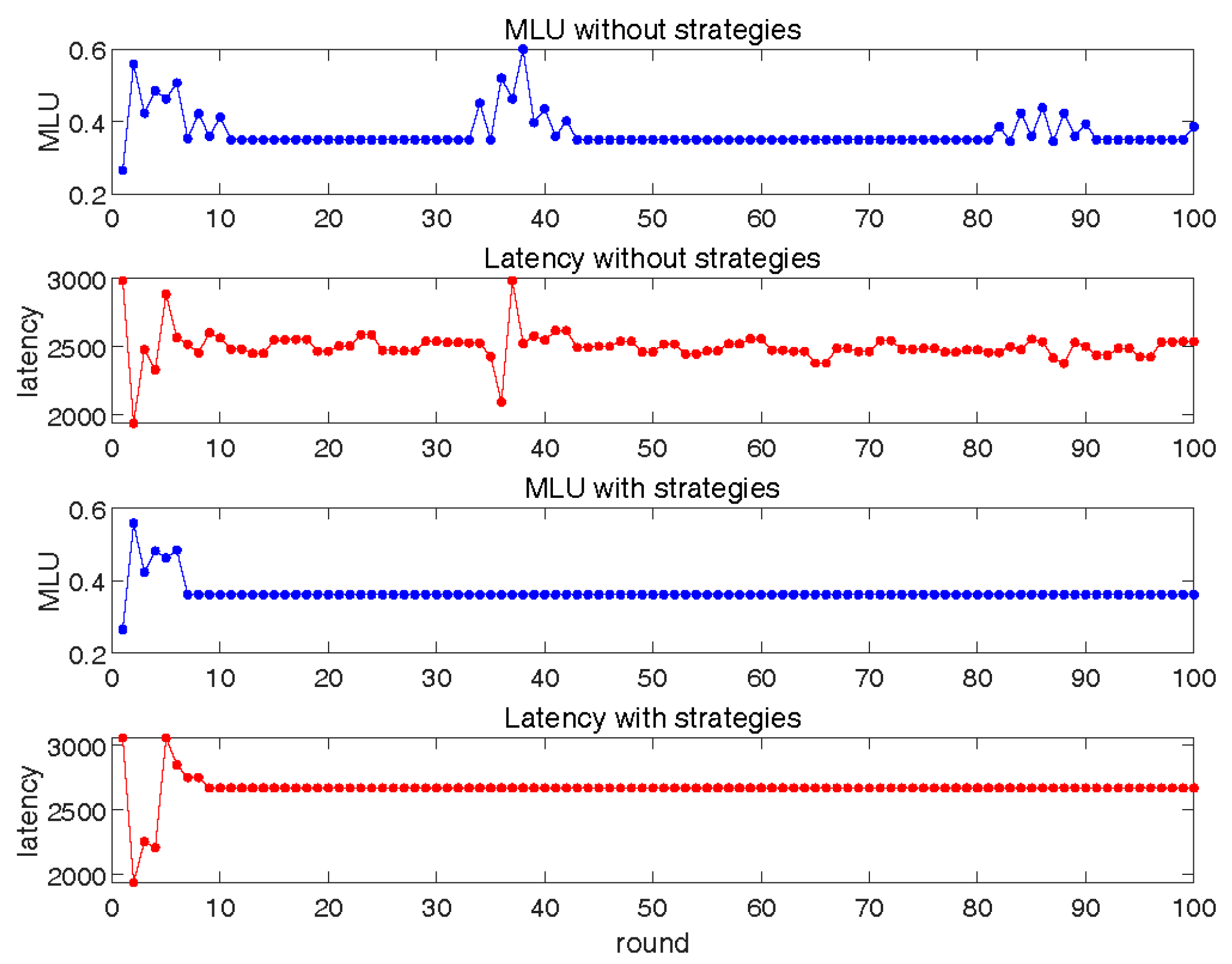
6.1. Interaction between Basic SRC and LLS
6.2. Interaction between SRC with Restoration and Basic LLS
6.3. Interaction between Basic SRC and LLS with Service Correction
6.4. Interaction between SRC and LLS
6.5. Convergence Time Varies with Network Size
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Aceto, G.; Botta, A.; Marchetta, P.; Persico, V.; Pescapé, A. A comprehensive survey on internet outages. J. Netw. Comput. Appl. 2018, 113, 36–63. [Google Scholar] [CrossRef]
- Budhkar, S.; Tamarapalli, V. An overlay management strategy to improve QoS in CDN-P2P live streaming systems. Peer-Peer Netw. Appl. 2019, 13, 190–206. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, X.; Fan, L.; Yu, S.; Lin, R. Segment Routing Optimization for VNF Chaining. In Proceedings of the ICC 2019-2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–7. [Google Scholar]
- Li, X.; Yeung, K.L. Traffic Engineering in Segment Routing Networks Using MILP. IEEE Trans. Netw. Serv. Manag. 2020, 17, 1941–1953. [Google Scholar] [CrossRef]
- Zheng, Z.; Zhao, C.; Zhang, J. Time-Sensitive Overlay Routing via Segment Routing with Failure Correction. In Proceedings of the 2021 IEEE International Conference on Communications Workshops (ICC Workshops), Montreal, QC, Canada, 14–23 June 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–6. [Google Scholar]
- Wang, J.; Qi, Q.; Gong, J.; Liao, J. Mitigating the Oscillations between Service Routing and SDN Traffic Engineering. IEEE Syst. J. 2018, 12, 3426–3437. [Google Scholar] [CrossRef]
- Ijaz, H.; Welzl, M.; Jamil, B. A survey and comparison on overlay-underlay mapping techniques in peer-to-peer overlay networks. Int. J. Commun. Syst. 2019, 32, e3872. [Google Scholar] [CrossRef]
- Seetharaman, S.; Hilt, V.; Hofmann, M.; Ammar, M. Resolving Cross-Layer Conflict between Overlay Routing and Traffic Engineering. IEEE/ACM Trans. Netw. 2009, 17, 1964–1977. [Google Scholar] [CrossRef]
- Abdelquoddouss, L.; Tarik, T. A survey on the placement of virtual resources and virtual network functions. IEEE Commun. Surv. Tutor. 2019, 21, 1409–1434. [Google Scholar]
- Sang, Y.; Ji, B.; Gupta, G.R.; Du, X.; Ye, L. Provably efficient algorithms for joint placement and allocation of virtual network functions. In Proceedings of the IEEE INFOCOM 2017-IEEE Conference on Computer Communications, Atlanta, GA, USA, 1–4 May 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–9. [Google Scholar]
- Sallam, G.; Gupta, G.R.; Li, B.; Ji, B. Shortest Path and Maximum Flow Problems under Service Function Chaining Constraints. In Proceedings of the IEEE INFOCOM 2018-IEEE Conference on Computer Communications, Honolulu, HI, USA, 16–19 April 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 2132–2140. [Google Scholar]
- Cziva, R.; Anagnostopoulos, C.; Pezaros, D.P. Dynamic, Latency-Optimal vNF Placement at the Network Edge. In Proceedings of the IEEE INFOCOM 2018-IEEE Conference on Computer Communications, Honolulu, HI, USA, 16–19 April 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 693–701. [Google Scholar]
- Fan, J.; Guan, C.; Zhao, Y.; Qiao, C. Availability-aware mapping of service function chains. In Proceedings of the IEEE INFOCOM 2017-IEEE Conference on Computer Communications, Atlanta, GA, USA, 1–4 May 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–9. [Google Scholar]
- Fei, X.; Liu, F.; Xu, H.; Jin, H. Adaptive VNF Scaling and Flow Routing with Proactive Demand Prediction. In Proceedings of the IEEE INFOCOM 2018-IEEE Conference on Computer Communications, Honolulu, HI, USA, 16–19 April 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 486–494. [Google Scholar]
- Hao, F.; Kodialam, M.; Lakshman, T.V. Optimizing restoration with segment routing. In Proceedings of the IEEE INFOCOM 2016-The 35th Annual IEEE International Conference on Computer Communications, San Francisco, CA, USA, 10–14 April 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–9. [Google Scholar]
- Pereira, V.; Rocha, M.; Sousa, P. Traffic Engineering with Three-Segments Routing. IEEE Trans. Netw. Serv. Manag. 2020, 17, 1896–1909. [Google Scholar] [CrossRef]
- Aubry, F.; Vissicchio, S.; Bonaventure, O.; Deville, Y. Robustly disjoint paths with segment routing. In Proceedings of the 14th International Conference on emerging Networking EXperiments and Technologies; ACM Press: New York, NY, USA, 2018; pp. 204–216. [Google Scholar]
- Foerster, K.-T.; Pignolet, Y.-A.; Schmid, S.; Tredan, G. CASA: Congestion and Stretch Aware Static Fast Rerouting. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 469–477. [Google Scholar]
- Bogle, J.; Bhatia, N.; Ghobadi, M. TEAVAR: Striking the right utilization-availability balance in WAN traffic engineering. In Proceedings of the ACM SIGCOMM, Beijing, China, 19–23 August 2019; pp. 29–43. [Google Scholar]
- Savage, S.; Collins, A.; Hoffman, E.; Snell, J.; Anderson, T. The end-to-end effects of Internet path selection. ACM SIGCOMM Comput. Commun. Rev. 1999, 29, 289–299. [Google Scholar] [CrossRef]
- Xiao, J.; Boutaba, R. Reconciling the Overlay and Underlay Tussle. IEEE/ACM Trans. Netw. 2013, 22, 1489–1502. [Google Scholar] [CrossRef]
- Guck, J.W.; Reisslein, M.; Kellerer, W. Function Split between Delay-Constrained Routing and Resource Allocation for Centrally Managed QoS in Industrial Networks. IEEE Trans. Ind. Inform. 2016, 12, 2050–2061. [Google Scholar] [CrossRef]
- Wang, J.; Liao, J.; Li, T. On the collaborations of multiple selfish overlays using multi-path resources. Peer-Peer Netw. Appl. 2015, 8, 203–215. [Google Scholar] [CrossRef]
- Xu, C.; Li, Z.; Li, J.; Zhang, H.; Muntean, G.-M. Cross-Layer Fairness-Driven Concurrent Multipath Video Delivery over Heterogeneous Wireless Networks. IEEE Trans. Circuits Syst. Video Technol. 2014, 25, 1175–1189. [Google Scholar] [CrossRef]
- Chen, J.; Liu, H.; Jia, H. Cross-Layer Resource Allocation in Wireless-Enabled NFV. IEEE Wirel. Commun. Lett. 2020, 9, 879–883. [Google Scholar] [CrossRef]
- Bhatia, R.; Hao, F.; Kodialam, M.; Lakshman, T. Optimized network traffic engineering using segment routing. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April–1 May 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 657–665. [Google Scholar]
- Xu, Z.; Liang, W.; Galis, A.; Ma, Y.; Xia, Q.; Xu, W. Throughput optimization for admitting NFV-enabled requests in cloud networks. Comput. Netw. 2018, 143, 15–29. [Google Scholar] [CrossRef]
- Jadin, M.; Aubry, F.; Schaus, P.; Bonaventure, O. CG4SR: Near Optimal Traffic Engineering for Segment Routing with Column Generation. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1333–1341. [Google Scholar]
- Ye, J.-L.; Chen, C.; Chu, Y.H. A Weighted ECMP Load Balancing Scheme for Data Centers Using P4 Switches. In Proceedings of the 2018 IEEE 7th International Conference on Cloud Networking (CloudNet), Tokyo, Japan, 22–24 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–4. [Google Scholar]
- Fernandez, J.C.; Taleb, T.; Guizani, M.; Kato, N. Bandwidth Aggregation-Aware Dynamic QoS Negotiation for Real-Time Video Streaming in Next-Generation Wireless Networks. IEEE Trans. Multimed. 2009, 11, 1082–1093. [Google Scholar] [CrossRef]
- Martin, R.; Menth, M.; Hemmkeppler, M. Accuracy and Dynamics of Hash-Based Load Balancing Algorithms for Multipath Internet Routing. In Proceedings of the 2006 3rd International Conference on Broadband Communications, Networks and Systems, San Jose, CA, USA, 1–5 October 2006; IEEE: Piscataway, NJ, USA, 2006; pp. 1–10. [Google Scholar]
- Chim, T.W.; Yeung, K.L.; Lui, K.S. Traffic distribution over equal-cost-multi-paths. Comput. Netw. 2005, 49, 465–475. [Google Scholar] [CrossRef][Green Version]
- Liu, Y.; Zhang, H.; Gong, W.; Towsley, D. On the interaction between overlay routing and underlay routing. In Proceedings of the IEEE 24th Annual Joint Conference of the IEEE Computer and Communications Societies, Miami, FL, USA, 13–17 March 2005; IEEE: Piscataway, NJ, USA, 2005; Volume 4, pp. 2543–2553. [Google Scholar]
- Gong, J.; Liao, J.; Wang, J.; Qi, Q.; Zhang, L. Reducing the oscillations between overlay routing and traffic engineering by repeated game theory. In Proceedings of the 2013 19th Asia-Pacific Conference on Communications (APCC), Denpasar, Indonesia, 29–31 August 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 591–596. [Google Scholar]
- Bu, Y.; Guo, H.; Hu, H.; Wang, B. A Traffic Splitting Algorithm Based on Dual Hash Table for Multi-path Internet Routing. In Proceedings of the 2010 International Conference on Machine Vision and Human-machine Interface, Kaifeng, China, 24–25 April 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 397–400. [Google Scholar]
- Lee, B.-S.; Kanagavelu, R.; Aung, K.M.M. An efficient flow cache algorithm with improved fairness in Software-Defined Data Center Networks. In Proceedings of the 2013 IEEE 2nd International Conference on Cloud Networking (CloudNet), San Francisco, CA, USA, 11–13 November 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 18–24. [Google Scholar]
- Kandula, S.; Katabi, D.; Sinha, S.; Berger, A. Dynamic load balancing without packet reordering. ACM SIGCOMM Comput. Commun. Rev. 2007, 37, 51–62. [Google Scholar] [CrossRef]
- Fortz, B.; Thorup, M. Internet traffic engineering by optimizing OSPF weights. In Proceedings of the IEEE INFOCOM 2000. Conference on Computer Communications. Nineteenth Annual Joint Conference of the IEEE Computer and Communications Societies (Cat. No.00CH37064), Tel Aviv, Israel, 26–30 March 2000; IEEE: Piscataway, NJ, USA, 2002; Volume 2, pp. 519–528. [Google Scholar]
- Gouareb, R.; Friderikos, V.; Aghvami, A.H. Delay Sensitive Virtual Network Function Placement and Routing. In Proceedings of the 2018 25th International Conference on Telecommunications (ICT), Saint-Malo, France, 26–28 June 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 394–398. [Google Scholar]
- Liu, H.H.; Kandula, S.; Mahajan, R.; Zhang, M.; Gelernter, D. Traffic engineering with forward fault correction. In Proceedings of the 2014 ACM Conference on SIGCOMM, Chicago, IL, USA, 17–22 August 2014; Association for Computing Machinery: New York, NY, USA, 2014; Volume 44, pp. 527–538. [Google Scholar] [CrossRef]
- Gay, S.; Schaus, P.; Vissicchio, S. REPETITA: Repeatable experiments for performance evaluation of traffic-engineering algorithms. arXiv 2017, arXiv:1710.08665. [Google Scholar]
- Yang, Q.; Li, W.; De Souza, J.; Zomaya, A.Y. Resilient virtual communication networks using multi-commodity flow based local optimal mapping. J. Netw. Comput. Appl. 2018, 110, 43–51. [Google Scholar] [CrossRef]
- Zhang, H.; Liu, Y.; Gong, W.; Towsley, D. Understanding the Interaction between Overlay Routing and Traffic Engineering; Technical Report; University of Massachusetts CMPSCI: Amherst, MA, USA, 2004. [Google Scholar]

| Symbols | Description |
|---|---|
| Symbols in SRC | |
| Underlay network graph with nodes and links . | |
| The bandwidth capacity of link e. | |
| The maximum link utilization. | |
| An intermediate node for segment routing. | |
| Flows aggregated by ingress and egress switches. | |
| The source switch of flow . | |
| The end switch of flow . | |
| A tunnel consisting of two shortest segments. | |
| Underlay demand on flow arising from the logical link . | |
| Underlay demand on flow arising from background traffic applications. | |
| The sum of and . | |
| The number of times the tunnel passes through physical link . | |
| Maximum number of link errors that occur simultaneously. | |
| Maximum number of switch errors that occur simultaneously. | |
| Maximum number of control plane errors that occur simultaneously. | |
| A scenario expressing node failures and link failures at the same time. | |
| A vector expressing control failures at the same time. | |
| The total traffic aggregating at link from flows starting at if no configuration failure happens. | |
| The total traffic aggregating at link from flows starting at if there exist configuration failures. | |
| The traffic volume on tunnel . | |
| The in the failure case . | |
| The splitting weight of the current period. | |
| The splitting weight of the last period. | |
| The total hop count of each flow after the operation of SRC in the last round. | |
| Symbols in LLS | |
| Overlay network graph with nodes , data center , and links . | |
| A data center in . | |
| Flows aggregated by ingress and egress switches. | |
| Flows that require a type- service chain aggregated by ingress and egress switches. | |
| The source switch of flow . | |
| The end switch of flow . | |
| The delay of flow . | |
| The link delay of overlay link . | |
| The bandwidth demand of flow . | |
| The bandwidth demand of flow that requires instances of type- service chains. | |
| The decision variable to represent the fraction of on link . | |
| A type of service chain. | |
| Type- service chains. | |
| The set of instances of type- service chains at data center . | |
| The computing resource capacity of . | |
| The bandwidth splitting weight of flow on . | |
| The number of times the tunnel passes through local link . | |
| Maximum number of SFC failures that occur simultaneously. | |
| A vector expressing ns SFC failures at the same time. | |
| The amount of overlay traffic on each link after the operation of overlay routing in the last round. | |
| Topology | Nodes | Links | SRC | LLS | Convergence |
|---|---|---|---|---|---|
| Eunetworks | 14 | 42 | 0.2633 s | 1.0651 s | 5 rounds |
| Agis | 17 | 44 | 0.6656 s | 2.4879 s | 5 rounds |
| EliBackone | 20 | 60 | 1.8755 s | 5.1245 s | 5 rounds |
| Integra | 23 | 64 | 3.6163 s | 9.3239 s | 5 rounds |
| Darkstrand | 26 | 56 | 5.7526 s | 17.1196 s | 4 rounds |
| Cesnet | 29 | 66 | 10.8048 s | 28.2829 s | 4 rounds |
| Canerie | 32 | 82 | 19.1414 s | 126.8002 s | 5 rounds |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zheng, Z.; Zhao, C.; Zhang, J. Robust and Fast Converging Cross-Layer Failure Correction in Segment-Routed Networks. Electronics 2021, 10, 2874. https://doi.org/10.3390/electronics10222874
Zheng Z, Zhao C, Zhang J. Robust and Fast Converging Cross-Layer Failure Correction in Segment-Routed Networks. Electronics. 2021; 10(22):2874. https://doi.org/10.3390/electronics10222874
Chicago/Turabian StyleZheng, Zengwei, Chenwei Zhao, and Jianwei Zhang. 2021. "Robust and Fast Converging Cross-Layer Failure Correction in Segment-Routed Networks" Electronics 10, no. 22: 2874. https://doi.org/10.3390/electronics10222874
APA StyleZheng, Z., Zhao, C., & Zhang, J. (2021). Robust and Fast Converging Cross-Layer Failure Correction in Segment-Routed Networks. Electronics, 10(22), 2874. https://doi.org/10.3390/electronics10222874







