Abstract
In a multimedia cloud computing system, suppose all cloud users outsource their own data sets to the cloud in the encrypted form. Each outsourced set is associated with an access structure such that a valid data user, Bob, with the credentials satisfying the access structure is able to conduct computing over outsourced encrypted set (e.g., decryption or other kinds of computing function). Suppose Bob needs to compute the set intersection over a data owner Alice’s and his own outsourced encrypted sets. Bob’s simple solution is to download Alice’s and Bob’s outsourced encrypted sets, perform set intersection operation, and decrypt the set intersection ciphertexts. A better solution is for Bob to delegate the cloud to calculate the set intersection, without giving the cloud any ability in breaching the secrecy of the sets. To solve this problem, this work introduces a novel primitive called ciphertext-policy attribute-based encryption with outsourced set intersection for multimedia cloud computing. It is the first cryptographic algorithm supporting a fully outsourced encrypted storage, computation delegation, fine-grained authorization security for ciphertext-policy model, without relying on an online trusted authority or data owners, and multi-elements set, simultaneously. We construct a scheme that provably satisfies the desirable security properties, and analyze its efficiency.
1. Introduction
The multimedia cloud computing has been a successful computing paradigm since it can offer mass data storage and elastic but powerful computing capabilities at an affordable price. Cloud users, e.g., data owners and data users, can outsource their multimedia data to the cloud, then access it and share it with other users at anytime from anywhere. However, since data outsourcing will undermine the control capability for data owners since the outsourced data resides in the cloud service providers’ scope, it inevitably raises the security concerns regarding the data confidentiality, data integrity, and data access control. While it is natural to encrypt data before outsourcing it to the cloud, it indeed raises another issue about how to facilitate the cloud to perform some specific function over outsourced encrypted data without compromising data privacy.
In this paper, we study the problem of set intersection over outsourced encrypted data sets, which is a variant of the private set intersection (PSI) problem [1] that has been extensively studied. In the traditional setting of PSI, two data users, holding their own data sets at local, joint compute the data sets’ intersection in a manner that they only obtain the information about the intersection but nothing else. PSI has been widely adopted to many practical applications, such as private data mining, private matching, credit information system, anti-epidemic information system, and educational resources sharing, etc.
Problem. For the multimedia cloud computing scenario, the cloud users (i.e., the data owners and the data users) no longer store their own data sets at local and calculate the set intersection by themselves. Instead, the cloud users expect to outsource them to the cloud in encrypted form and entrust the cloud to help them complete the set intersection operation. While several works have studied PSI over outsourced encrypted data in the cloud [2,3,4], it certainly raises a difficulty for the data owners on how to enforce that their encrypted data can be used to perform by only some specific users. That is, how can the data owners limit the ability for the data users on performing set intersection by complying with certain control policies.
Motivation. shi2021delegated. In their protocol, it restricts PSI operation permissions through access control policy, embedded in data users’ secret keys. However, in -, the access structure is associated with data users instead of outsourced data sets. So, it is not particularly suitable for achieving access control over cloud data. Recently, Ali et al. proposed a ciphertext-policy attribute-based set intersection solution [6] to realize fine-grained authorization for outsourced data sets of data owners. Unfortunately, in their protocol, the data sets of the data users must be in plaintext form and the data users should execute PSI operations at local. It is not applicable to the case where all cloud users outsourced their encrypted data sets to the cloud and delegate PSI computation to the cloud. To our knowledge (cf. Section 2), none of the existing schemes consider this problem how to achieve the following objectives simultaneously: (1) All cloud users should outsource their data sets in the ciphertext form to the cloud. (2) The cloud users should be able to preserve data privacy while allowing the set intersection delegation to the cloud. (3) The cloud users should be able to accomplish fine-grained access control to the set operation permissions over their outsourced encrypted data sets. (4) It should not rely on the always online trusted authority and the data owners.
Our Contributions. For solving the above problem, this work introduces a novel notion called ciphertext-policy attribute-based encryption with outsourced set intersection (-) for multimedia cloud computing. In -, all cloud users encrypt their own data sets by customizing an access structure before outsourcing. An authorized data user (Bob), whose attributes satisfy the access structure of the data owner’s (Alice) data set, can delegate the set intersection calculation between Alice’s and Bob’s data sets to the cloud by generating a token. This work presents the formal definition of - with security properties, then presents a specific scheme. There are five characteristic properties for our - scheme: (1) It supports fully outsourced encrypted data sets for all cloud users, including data owners and data users. (2) The cloud can be delegated to execute PSI operations and not acquire any additional information beyond the result of encrypted set intersection. (3) It combines PSI and CP-ABE to realize fine-grained authorization for outsourced set intersection operation. (4) The data owner and the trusted authority are not required to participate in the interaction. (5) It supports multi-elements data sets. It is suitable for multimedia cloud computing.
2. Related Work
Although PSI has been widely studied previously, all existing solutions did not resolve the problems considered in this work. We brief the relevant technologies below and compare them with our - as shown in Table 1.

Table 1.
Property summary for PSI schemes. “×” means not supported, “√” means supported, “CP” means ciphertext-policy and “KP” means key-policy. In the related work and our solution in this paper. Fully outsourced encrypted storage means that all cloud users, including data owners and data users, can outsource their data sets in encrypted form. Computation delegation means it supports delegating PSI operations to the cloud. Fine-grained authorization security (as defined in Definition 4) means that it supports fine-grained authorization security with key-policy or ciphertext-policy setting. Without always online trusted authority or data owner means that it is not required that the trusted authority or data owners are always online. Multi-elements set means it supports multiple elements data set.
Two-party Private Set Intersection. In this scenario, it only involves two participants, a client and a server, both of whom work interactively to accomplish the set intersection operation with their own data sets [7,8]. Unfortunately, these solutions cannot be adapted to cloud architecture; for that, both parties have to decrypt all of their outsourced encrypted data sets and do the heavy computations for PSI at local. Obviously, they cannot support fine-grained authorization and the data owner should be always online.
Three-party Private Set Intersection. In this model, it includes three participants, i.e., the cloud servers, the data owners, and data users, where the data owners and the data users wish to outsource set intersection operations to the server. For example, refs. [2,3,4,9] considered outsourcing set intersection operations to the cloud while preserving the privacy of the data sets. In addition, symmetric/asymmetric encryption with equality test, e.g., [10,11], is a specific solution for one-element data sets. Unfortunately, all of these solutions ask for the data owner to always be online or have no authorization mechanism. Thus, traditional three-party PSI protocols are impractical for the cloud system.
Attribute-based Encryption (). A reliable solution for realizing fine-grained authorization for outsourced data is , introduced by Sahai and Waters [15]. This technique allows the data users with appropriate attributes to decrypt the ciphertexts under an access structure. There are two types of : ciphertext-policy (-) in which the ciphertext is generated under an access structure (e.g., [16,17]) and key-policy (-) in which the private key is generated under an access structure (e.g., [18,19]). also can be combined with other techniques to provide fine-grained operation and computation, e.g., attribute-based keyword search (e.g., [20]) or attribute-based proxy re-encryption (e.g., [21]).
Attribute-based Set Intersection. The first attribute-based set intersection solution is attribute-based encryption with equality test (ABEET). ABEET supports access control and set intersection computation delegation, but only for one-element data sets. Zhu et al. and Wang et al., respectively, present the first KP-ABEET and CP-ABEET [12,13]. After that, Cui et al. presented a performance enhanced ciphertext-policy construction [14]. Unfortunately, in these schemes, the trapdoor is generated with the master secret key held by the trusted authority and the data owner is required to participate in the delegating phase to send its token to the cloud. So, the trusted authority and the data owners should be always online. Even worse, in existing ABEET schemes, the cloud server without can obtain set intersection with for and for . So, they actually cannot achieve fine-grained authorization security, which will be illustrated in Definition 4. It is impractical and secure enough for distributed cloud computing. The first attribute-based solution for multi-elements set intersection is proposed by Mohammad Ali et. al. It achieves fine-grained authorization security and is not dependent on an online trusted authority or data owners. However, in Ali’s scheme, data users must store the plaintext form of their set and execute PSI operations at local. It is not supporting fully outsourced encrypted storage and computation delegation, so it is not applied to our scenario where the data sets of all cloud users are encrypted in the cloud. Later, Shi et al. introduced a - scheme by combining - and PSI to achieve fully outsourced encrypted storage and computation delegation. However, it is still not applied to our scenario since it implements access control for cloud users instead of cloud data sets [5].
For that, in this work, we combine PSI and - to propose a novel primitive named ciphertext-policy attribute-based encryption with outsourced set intersection (-), implementing access control for ciphertext data sets. Compared with existing solutions, our - can support a fully outsourced encrypted storage, computation delegation, fine-grained authorization security for ciphertext-policy() model, without relying on an online trusted authority or data owners, and multi-elements set, simultaneously.
3. Problem Formulation
3.1. System Model
Figure 1 highlights the system model, which consists of three entities—a cloud server, a trusted attribute authority, and the cloud users, e.g., a data owner (named Alice), an authorized data user (named Bob), and an unauthorized data user (named Calos). The cloud affords for the cloud users computing and storing supporting. The trusted attribute authority issues data users’ secret keys in line with their attribute certificates. The data owner (i.e., Alice), which can be either individuals or organizations, encrypt their private data sets according to an access control policy and then outsource them to the cloud server. An authorized user (i.e., Bob), whose attributes satisfy Alice’s and his own access structures simultaneously, can delegate set intersection operations over Alice’s and his own encrypted data sets to the cloud. Whereas any unauthorized user, i.e., Calos, whose attributes do not satisfy the access structure of Alice, cannot outsource the set intersection operations to the cloud.
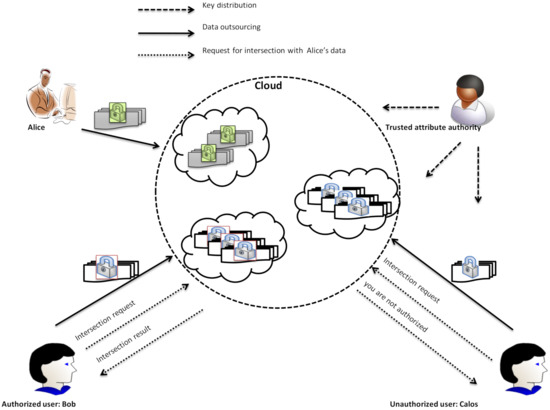
Figure 1.
System model of -.
Here, we suppose that the cloud is honest but curious, meaning that it runs the protocols honestly but attempts to obtain privacy information about the data sets.
A cloud user is malicious and might collude with the semi-trusted cloud.
3.2. Formal Definition
Here is shown the formal definition of - (ciphertext-policy attribute-based encryption with outsourced set intersection), in which ciphertexts are generated under an access structure. is denoted as an access policy and is denoted as an attribute set, respectively, in -. Let if and only if is satisfied by in -.
Definition. 1.
(-) A scheme for - has the following algorithms:
: The trusted attribute authority bootstraps the master private key and the public parameters as input a security parameter ℓ.
: The trusted attribute authority generates secret keys for a data user.
: Given , a cloud user (data owner or data user) encrypts their private data set . Then they outsource the ciphertexts to the cloud.
: A data user runs this algorithm to generate a token to delegate the set intersection operations between the data owner’s and his own encrypted data sets to the cloud, where the token will be sent to the cloud for this purpose.
: The cloud server runs this algorithm to calculate the set intersection , only if associated to meets both and , where and are specified by of the data owner and of the data user, respectively.
The correctness of - scheme can be defined as: With , , , for set and for set , if and , is the ciphertext of set intersection , where .
3.3. Security Definitions
It is said that the - scheme is secure if it satisfies the following security properties: selective security against chosen-plaintext attack, one-wayness under a chosen-plaintext attack, and fine-grained authorization security.
Selective security against chosen-plaintext attack: Intuitively, this property says that a probabilistic polynomial-time (PPT) adversary , modeling malicious unauthorized data users, cannot obtain any useful information about the encrypted sets without being given the corresponding tokens, where the term “selective” means that it asks for the adversary to choose which parties to compromise before initializing the public parameters. This security property can be formally defined by the game between and a challenger as follows.
Setup: chooses and sends it to the challenger. Then the challenger executes to bootstrap and , it sets as the master private key and sends to as a public key.
Phase 1: can make queries for polynomial-many times as follows:
- : If , the challenger aborts; else, it executes and sends back to .
- : If , then the challenger aborts the simulation; otherwise, it executes , and sends to .
Challenge: selects two data sets and where but , and sends them to the challenger. The challenger picks , executes and returns back to .
Phase 2: executes as in Phase 1.
Guess: A guess is replied by . wins the security game if .
Definition 2.
If the advantage that wins the selective security game is negligible, the - construction is selective secure.
One-wayness security: Intuitively, this property requires that any PPT adversary , modeling honest-but-curious cloud server, even with a token, is unable to acquire any useful information about the plaintexts corresponding to the ciphertexts in question. Note that, given a target ciphertext and the appropriate token, where the term “appropriate” means the credentials that generate the token satisfy the access control policy associated to the target ciphertext, can purposefully choose and encrypt a data set element with public parameters, and compare their chosen ciphertext with the target ciphertext. Obliviously, brute-force attack is inevitable, so it is just demanded that have no better strategy. The one-wayness security can be defined by the following game.
Setup: The challenger produces by executing , sets as the master secret key, and sends to as the public parameters.
Phase 1: can query following oracles for polynomial-many times, the challenger bookkeeps a list initially empty.
- : The challenger replies to and inserts to .
- : The challenger replies (where ) to .
Challenge: selects and sends to the challenger, where . The challenger chooses such that , selects uniformly at random, calculates and . Then return back to .
Phase 2: It is similar to Phase 1, except that when querying .
Guess: A guess d is replied by . wins the one-wayness security game if .
Definition 3.
If the advantage , in which is the domain size of set elements and m is the number of guess/brute-force attacks makes, that wins the one-wayness security game is negligible, the - construction is one-wayness secure.
Fine-grained authorization: The adversary , modeling the honest-but-curious cloud server, cannot use the known tokens to obtain set intersection if the credentials that generate the tokens do not satisfy the access control policies associated to two ciphertexts simultaneously. Intuitively, cannot use for and for to achieve set intersection , if and whose associated attribute sets do not satisfy A and C’s access structure simultaneously. This can be formalized via the following fine-grained authorization security game.
Setup: The challenger produces by executing , sets as the master private key, and returns back to .
Phase 1: can make polynomial-many oracle queries as follows, and the challenger bookkeeps two lists and initially empty.
- : The challenger replies back to and adds to .
- : The challenger replies (where ) to and insert into .
Challenge: selects and , and sends them to the challenger. The challenger chooses two sets , selects , replies and back to . It is required that
- , and cannot be 1 simultaneously.
- , and cannot be 1 simultaneously.
Phase 2: It is similar to Phase 1, except that:
- For any query for or , and cannot be 1 simultaneously.
Guess: A guess is replied by . wins the fine-grained authorization game if .
Definition 4.
If the advantage that wins fine-grained authorization security game is negligible, the - construction is fine-grained authorization secure.
4. Scheme Construction
4.1. - Construction
The - scheme is described as follows.
(): Given security parameter ℓ, it generates the public parameter and master key as follows:
- Set .
- Let and be two secure hash functions.
- Choose , then make the public parameter as and the master secret key as
: It picks , then calculates and . For each attribute , it selects , and computes and . It sets the private key as
: Given set where , it encrypts as follows: It picks and computes for each . It runs and computes for each . It sets the ciphertext as , where .
: It selects , computes for each , and sets . It sets the token as
: As input , and a token , it executes as follows:
- For , it arbitrarily chooses a subset satisfying . If there is no such S, 0 is returned. Else, it calculates , where . Then it runs , and computes and It sets .
- For , it arbitrarily chooses a subset satisfying . If there is no such , 0 is returned. Else, it calculates , where . Then it runs , and computes and It sets .
- It outputs the set intersection .
we can verify the correctness for - construction easily according to the protocols. Then its security properties will be analyzed.
4.2. Security Analysis
Theorem 1.
The - scheme is selective secure against chosen-plaintext attack in the generic bilinear group model as specified in Definition 2.
Proof.

It is first to show that the scheme is secure when , and then extend it to the case .
Since in the challenge phase of the game, ’s aim is to distinguish and , where and . The probabilities of distinguishing from and distinguishing from where are the same. Therefore, if distinguishes from with probability , then distinguishes between and with probability . We consider the following adjusted game, in which attempts to discriminate between and with .
Setup: The challenger randomly picks , sets public parameter as , and transfers them to . It bookkeeps two initially empty lists and . can query polynomially many times for and .
: If has not been queried before, it picks , replies to and inserts into ; Else, it retrieves from and replies to .
: If an element d was queried before, it searches from and sends back to ; else, it picks , inserts into , then sends back to .
Phase 1: can query the oracles polynomially many times as follows.
: The challenger selects . For each , it chooses , and sets
: The challenger chooses and calculates
Challenge: chooses and transfers an access policy to the challenger., which is not satisfied by any that was queried to . The challenger picks two equal length messages uniformly at random from the message space, selects and , and runs . If , then the challenger computes where . Otherwise, it calculates where . At last, it returns to .
Phase 2: queries the oracles as in Phase 1.
Guess: outputs a guess of .
In the generic model, if it is distinguishable between and for , it should build with certain . Then it will be shown that the probability that build for certain is negligible, possibly taking advantage of the oracles’ outputs. Table 2 lists all the possible queries to group oracle .

Table 2.
Possible group oracle queries in the selective security game.
Let us discuss the way building with certain . Since only the term has the element , the only way of building for is building , where . Obviously, to construct , needs to use , , , , and . However, only under the condition that the attribute set satisfies can be reconstructed.
Thus far, it is shown that can gain a negligible advantage in the modified game.
Intuitively, for the general case of , we can also prove that the scheme is selective secure against chosen-plaintext attack as in [5]. □
Theorem 2.
The - scheme is one-wayness secure if hash function is one-way.
Proof.
Suppose there is a PPT adversary winning the game for one-wayness with a non-negligible advantage , a challenger can be simulated to break one-wayness for .
Given , the challenger executes the following game.
Setup: It chooses , sets , and transfers to .
Phase 1: It keeps an initially empty list . is able to query the following oracles in polynomially many times:
: For an attribute set , it returns to and inserts into .
: For an attribute set , it replies .
Challenge: transfers to the challenger an access control policy , where , . The challenger selects and generates a data set , where are chosen from at random and is set as implicitly. It sets the ciphertext as follows:
- If , is the same with that in the real scheme;
- If , set , by choosing at random and setting implicitly. Then run and compute for each . At last it sets
The challenger chooses an attribute set such that , and forwards to the adversary and .
Phase 2: It is the same as that defined by the game.
Guess: The challenger wins if replies a guess d satisfying .
It is shown that if outputs with probability , then . Moreover, , where is the data set size. Therefore, if wins the game for one-wayness with a non-negligible advantage , the challenger can break the one-wayness for with a non-negligible probability that is at least . □
Theorem 3.
The - scheme is fine-grained authorization secure in the generic bilinear group model.
Proof.

We first show that the - construction is fine-grained authorization secure while .
Setup: The challenger picks and transfers to . The challenger bookkeeps lists and , which are empty initially, and can query and in polynomially many times as follows:
: Given the attribute , if has not been queried before, it picks , replies , and inserts into ; Else, it replies by searching from .
: If has been queried before, then it searches from and sends back to ; otherwise, it picks , replies to , and inserts into .
Phase 1: The challenger bookkeeps two initially empty lists and . can query the oracles polynomially many times.
: It picks . For each , it chooses , and sets It returns to A and adds to .
: The challenger selects , runs . For each , it chooses , and sets It sends to and inserts into .
Challenge: The adversary selects access control policies and sends them to the challenger. We require that (1) , and cannot output 1 simultaneously, and (2) , and cannot output 1 simultaneously. The challenger chooses two data sets of equal length.
For each , the challenger selects and runs . It computes , where .
It selects and for each it selects and runs . It calculates where .
At last, it returns to .
Phase 2: It is the same as that defined by the game.
Guess: A guess of is output by .
In this game, attempts to determine whether is equal to . Since each message in data sets is encrypted independently, needs to determine whether is equal to for . The only way is to judge whether or not is same as . Since in the generic model, the only way that can determine is equal to is that there are two queries and for some and into G or . We artificially add the query to ’s queries. Then, it will be shown that never makes any query for . We can see that only appears in the term and only appears in the term . So, needs to construct . Table 3 lists all the queries to group oracle .

Table 3.
Possible queries for group oracle in fine-grained authorization game.
In the above game, only appears in the term and only appears in the term . Let for some , and then needs to construct . Since is independent with , needs to construct and . The only way to construct needs to use (, ) and (, ,) related to key or token queries labeled with (). is ’s secret share associated to . So, or can be only reconstructed if . Let is a set of such that for or , where is known to , can be reconstructed. For any , or can be reconstructed only if the key or token query labeled with satisfies . However, there is no key or token query labeled with () satisfying not only but also . Therefore, there is no such that and can both be reconstructed.
Consequently, and for some can be constructed by with negligible probability, and it is fine-grained authorization secure for .
As with the evidence in Theorem 1, it can be shown that our solution is also fine-grained authorization secure for . This completes the proof. □
5. Efficiency Analysis
Here, we measure the performance of - and other related works about attribute-based set intersection by the asymptotic complexity. Pairing operation time is denoted by P, hash operation time is denoted by H, group exponentiation time in G is denoted by E, and group exponentiation time in is denoted by . The multiplication operation is ignored since it has much higher efficiency compared to the above operations.
For analyzing the performance of - clearly, firstly we compared it with - [5], as in Table 4, as follows:

Table 4.
Efficiency comparison between - and our -. Note that here, both sets are n in size, the number of a data user’s attributes is S, the number of attributes involved in the access tree is N.
It shows that in the - scheme is more expensive than that in the - scheme, while in the - scheme is more expensive than that in the - scheme. In both schemes, the algorithm and the algorithm incur almost the same cost. algorithm can be delegated to the cloud server. However, our - can specify the access structure over outsourced data sets directly, while - can only access control for users because of its key-policy setting.
Additionally, as we showed in Section 2, on one hand, Ali’s solution [6] requires the data user to store complete sets of big data and spend more time than nE + nH for PSI operation at local. This has a great burden on the computing and storage for the cloud users. On the other hand, ABEET solutions [12,13,14] cannot support multi-elements data sets and fine-grained authorization security. Even worse, they require the data owners and trusted authority to always be online. So, the communication cost is too high and they are not applicable to the distributed cloud scenario.
Thus, our - is the most practical and secure solution than existing attribute-based set intersection schemes for cloud computing.
6. Conclusions
We introduced a novel application of multimedia cloud computing: ciphertext-policy attribute-based encryption with outsourced set intersection. This application has five properties: (1) All cloud users outsource their encrypted data sets to a cloud, where each outsourced data set has an associated access control policy. (2) A data user who has the credentials that satisfy the data owner’s access control policy is able to delegate to the cloud the set intersection operation between his own and the data owner’s data sets. (3) The cloud helps data users calculate the set intersection without being capable of learning any additional useful information and without being given the data user’s credentials. (4) It is not required that the data owners and the trusted authority are always online. (5) It supports multi-elements data sets.
There are many interesting problems for future research in multimedia cloud computing. First, our schemes do not hide what credentials the data user possesses. How to hide such information is an open problem. Second, our main contribution is not for high performance, but for new cryptographic functions and security in this work. So, it is also interesting to design a high performance - scheme in future work.
Author Contributions
Conceptualization, Y.S.; methodology, Y.S.; formal analysis, S.Q.; writing—original draft preparation, Y.S.; writing—review and editing, Y.S. and S.Q. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Philosophy and Social Science Foundation of the Jiangsu Higher Education Institutions of China “Research on Blockchain-based Intelligent Credit Information System and its Privacy Preservation Mechanism” (Grants No. 2021SJA0448), the Natural Science Foundation of Jiangsu Province (Grants No. BK20210928), and the Scientific Research Foundation of Nanjing Institute of Technology (Grants No. YKJ201980), and the Higher Education Research Project of Nanjing Institute of Technology “Research on Security Sharing Mechanism of Compound Teaching Resources based on Blockchain” (Grants No. 2021ZC13).
Data Availability Statement
All data is available to the public.
Acknowledgments
This paper has benefited from the comments of the anonymous reviewers.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Freedman, M.J.; Nissim, K.; Pinkas, B. Efficient private matching and set intersection. In Advances in Cryptology-EUROCRYPT 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 1–19. [Google Scholar]
- Wang, Q.; Zhou, F.; Xu, J.; Peng, S. Tag-based Verifiable Delegated Set Intersection over Outsourced Private Datasets. In IEEE Transactions on Cloud Computing; IEEE: Piscataway, NJ, USA, 2020; p. 1. [Google Scholar] [CrossRef]
- Abadi, A.; Terzis, S.; Dong, C. VD-PSI: Verifiable delegated private set intersection on outsourced private datasets. In International Conference on Financial Cryptography and Data Security; Springer: Berlin/Heidelberg, Germany, 2016; pp. 149–168. [Google Scholar]
- Yang, X.; Luo, X.; Xu, A.W.; Zhang, S. Improved outsourced private set intersection protocol based on polynomial interpolation. Concurr. Comput. Pract. Exp. 2018, 30, e4329. [Google Scholar] [CrossRef] [Green Version]
- Shi, Y.; Qiu, S. Delegated Key-Policy Attribute-Based Set Intersection over Outsourced Encrypted Data Sets for CloudIoT. Secur. Commun. Netw. 2021, 2021, 5595243. [Google Scholar] [CrossRef]
- Ali, M.; Mohajeri, J.; Sadeghi, M.R.; Liu, X. Attribute-based fine-grained access control for outscored private set intersection computation. Inf. Sci. 2020, 536, 222–243. [Google Scholar] [CrossRef]
- Pinkas, B.; Rosulek, M.; Trieu, N.; Yanai, A. Psi from paxos: Fast, malicious private set intersection. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2020; pp. 739–767. [Google Scholar]
- Lv, S.; Ye, J.; Yin, S.; Cheng, X.; Feng, C.; Liu, X.; Li, R.; Li, Z.; Liu, Z.; Zhou, L. Unbalanced private set intersection cardinality protocol with low communication cost. Future Gener. Comput. Syst. 2020, 102, 1054–1061. [Google Scholar] [CrossRef]
- Zhu, H.; Chen, M.; Sun, M.; Liao, X.; Hu, L. Outsourcing Set Intersection Computation Based on Bloom Filter for Privacy Preservation in Multimedia Processing. Secur. Commun. Netw. 2018, 2018, 5841967. [Google Scholar] [CrossRef] [Green Version]
- Duong, D.H.; Fukushima, K.; Kiyomoto, S.; Roy, P.S.; Susilo, W. A lattice-based public key encryption with equality test in standard model. In Australasian Conference on Information Security and Privacy; Springer: Berlin/Heidelberg, Germany, 2019; pp. 138–155. [Google Scholar]
- Lee, H.T.; Ling, S.; Seo, J.H.; Wang, H. Public key encryption with equality test from generic assumptions in the random oracle model. Inf. Sci. 2019, 500, 15–33. [Google Scholar] [CrossRef]
- Zhu, H.; Wang, L.; Ahmad, H.; Niu, X. Key-policy attribute-based encryption with equality test in cloud computing. IEEE Access 2017, 5, 20428–20439. [Google Scholar] [CrossRef]
- Wang, Q.; Peng, L.; Xiong, H.; Sun, J.; Qin, Z. Ciphertext-policy attribute-based encryption with delegated equality test in cloud computing. IEEE Access 2017, 6, 760–771. [Google Scholar] [CrossRef]
- Cui, Y.; Huang, Q.; Huang, J.; Li, H.; Yang, G. Ciphertext-policy attribute-based encrypted data equality test and classification. Comput. J. 2019, 62, 1166–1177. [Google Scholar] [CrossRef]
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Advances in Cryptology–EUROCRYPT 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 457–473. [Google Scholar]
- Liu, Z.; Duan, S.; Zhou, P.; Wang, B. Traceable-then-revocable ciphertext-policy attribute-based encryption scheme. Future Gener. Comput. Syst. 2019, 93, 903–913. [Google Scholar] [CrossRef]
- Ma, H.; Wang, Z.; Guan, Z. Efficient Ciphertext-Policy Attribute-Based Online/Offline Encryption with User Revocation. Secur. Commun. Netw. 2019, 2019, 8093578. [Google Scholar] [CrossRef]
- Li, J.; Yu, Q.; Zhang, Y.; Shen, J. Key-policy attribute-based encryption against continual auxiliary input leakage. Inf. Sci. 2019, 470, 175–188. [Google Scholar] [CrossRef]
- Zhang, J.; Gao, H. A compact construction for non-monotonic key-policy attribute-based encryption. Int. J. High Perform. Comput. Netw. 2019, 13, 321–330. [Google Scholar] [CrossRef]
- Zheng, Q.; Xu, S.; Ateniese, G. VABKS: Verifiable attribute-based keyword search over outsourced encrypted data. In Proceedings of the IEEE INFOCOM 2014-IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 522–530. [Google Scholar]
- Li, Z.; Sharma, V.; Ma, C.; Ge, C.; Susilo, W. Ciphertext-policy attribute-based proxy re-encryption via constrained PRFs. Sci. China Inf. Sci. 2021, 64, 1–2. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).