1. Introduction
This work proposes lightweight solutions on the basis of standardized resources for the secure connection of IoT devices. This ensures a secure communication between the constrained environment devices and typical Internet hosts, using a lightweight yet standard compliant Internet security anomaly intrusion detection system.
Fog Computing offers a platform that addresses issues linked with the security as well as the privacy of IoT, since the IoT devices have very limited computational resources and those devices might not be able to perform the required computational tasks. Consequently, more development will occur in the area of intrusion detection because computer networks encounter new attacks daily. In the past decades, critical attacks have hit the Internet, leading to appalling consequences for computer users of different levels, such as companies, end-users, and governments [
1,
2]. The main challenge is to design reliable, secure IoT devices, including the Fog nodes that are located near the network edge. Fog Computing refers to a paradigm that deals with an extension of Cloud Computing as well as network edge services for the purpose of addressing the Cloud’s in-built glitches, such as the absence of support for mobility, latency, and awareness of location. The Fog system refers to a medium that is decentralized and has the ability to operate as well as process local data, which can be further installed in a heterogenic hardware, thus ensuring it is suitable for IoT applications. Importantly, Intrusion Detection Systems (IDSs) comprise a vital segment of the security configuration for any IoT or Fog related network, with the aim of ensuring top-notch service quality. Moreover, a lightweight IDS is more reliable, as there is a lack of resources for IoT and Fog related devices. There has been extensive research on Anomaly-based IDSs as protective techniques used in addressing the detection of attacks that are not known, known as zero-day attacks. Dissimilar to the types of IDS that are signature-based, they detect attacks based on pre-determined signature and known attacks. An IDS that is anomaly-based is more concerned with detecting novel kinds of attacks, unknown to the system [
3,
4]. However, this process is achieved via variation detection in the way the system behaves with regards to a previously defined profile of a normal system. The prediction of the anomalous behavior of a process in execution via the trace of a system call is a normal act among the security-based community and remains an active area of research. In addition, it is a distinctive problem in the recognizing of patterns, and it can be solved through algorithms in machine learning.
Machine Learning Based IDS for IoT Applications, within the computer network security domain, can be described as activities entailing the attempt of outer entities infiltrating a network’s ability to access a device so as to steal its information [
5]. In previous times, IDS has been employed; however, due to the contemporary challenges associated with IoT new age, most of the IoT devices possess very minimal resources which run difficult security solutions, thus leading to the non-effectivity of the systems. According to Jan and his companions [
6], a lightweight IDS probably provides a beneficiary solution for IoT devices; it makes use of machine learning algorithms for the detection of attempts, thus injecting irrelevant data to a network [
7] and placing more focus on securing medical devices. Due to the nature of IoT systems, comprising different devices that produce a massive volume of data for overworking IDS, there is a need to combine different machine learning algorithms for the improvement of the detection rate [
8].
According to the characteristics of Fog Computing, this article investigates and evaluates a general scheme: the IDS in an IoT environment based on machine learning. Furthermore, the proposed system employs a feature extraction technique based on Perceptron, thus evaluating the performance of the Modified Vector Space Representation (MVSR) technique, referred to as N-gram, which serves as templates for the training phase. In the pre-processing phase of this research, the feature selection process is added innovatively. The reason behind this design is to ensure improvement of the classifier algorithm to enable it to be lightweight during task performances hosted by Fog Computing. Furthermore, in this study, there is a comparison of the performance of some feature selection principal component analysis (PCA) with Mutual Information (MI) using Filter Methods. A simulation study made use of different algorithms for classification. The findings from the experiment revealed that their approach performed well, and it aided an accurate distinctive process behavior via system calls. This research therefore presents the design and performance evaluation of the technique used to represent the Modified Vector Space (MVS) based on raw ADFA-LD system call trace data, which is called N-gram. This is in conjunction with comparing other classifier designs, based on the majority of the classifiers, such as Decision Tree (DT), Random Forest (RF), Support Vector Machine (SVM)—Linear, Support Vector Machine (SVM)—Radial Basis Function (RBF), K-Nearest Neighbor (KNN), and Naive Bayes as intrusion detection classifiers, as well as verifying MLP superiority. Furthermore, the model’s performance is evaluated using Raspberry Pi, a popular IoT device. On this note, this research is considered to solve issues related to the Evaluation Performance (Recall, F1-Masure, Accuracy, False Positive Rate (FPR), Receiver Operating Characteristic (ROC), and Area Under the Curve (AUC)) and evaluate CPU Usage Testing Time and Energy Consumption. Finally, from the evaluated metrics, the research proposes the best lightweight IDS based on vector space representation (1-gram, 2-gram) as well as compare the presented IDS against the ADFA-LD.
1.1. Motivation
The focus of this research is the build-up of a lightweight security solution for IoT systems. This enhances the security of the Fog devices and reduces the overhead at the cloud side.
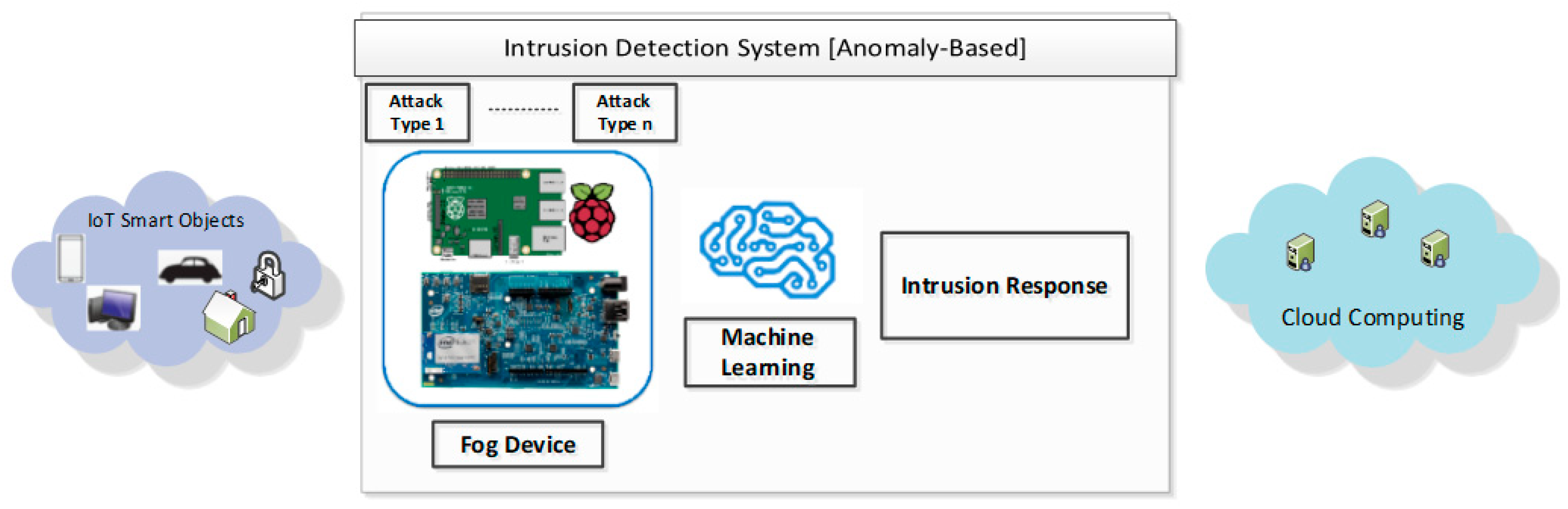
Figure 1 shows the structure of the lightweight IDS for a Fog Computing environment.
The Main Motivations of This Research
Reducing and mitigating the security challenges in IoT—this work would serve as a general scheme of the Intrusion Detection System, in accordance with the Fog Computing Environment’s features.
Improving and examining different feature extraction and selection methodologies compatible with the constrained resources of Fog Computing.
Evaluating the performance of different machine learning models based on time, energy consumption, and space complexity.
1.2. The Work Contribution
Regarding the security of IoT systems, issues such as suitability of high-end traditional security solutions exist due to the challenge of low storage capacity as well as low power for processing the IoT devices. Additionally, connectivity between IoT devices lasts for long periods of time without any human intervention [
9,
10,
11]; the hosting of a Fog node could be done via a large group of devices comprising video surveillance cameras, routers, embedded servers, switches, and industry-based controllers. Most of the aforementioned devices might have insufficient performing computational power; for instance, there is a need for efficient performance as well as the provision of real-time feedback and responses by intrusion detection algorithms, data analysis, and protocols used in cryptography. Thus, lightweight protocols and algorithms that do not require high-end computing resources are needed. An, Zhou, Lü, Lin and Yang [
12], with the aim of overcoming the issue of space limitation among Fog nodes, proposed a lightweight IDS, which they referred to as Sample Selected Extreme Learning Machine (SS-ELM). The dataset employed by the researchers was the KDD Cup 99, coupled with SS-ELM, which outperformed the classical Back Propagation (BP) algorithm with regard to the time spent in training and the accuracy of detection. Consequently, Hosseinpour, Vahdani Amoli, Plosila, Hämäläinen and Tenhunen [
13] proposed an Artificial Immune System [
14] that was lightweight and distributed IDS, with a detection accuracy reaching 98%. Furthermore, as a means of detecting the behavior of attacks on ADFA-LD, and with an FPR achievement of less than 20%, Xie, Hu, Yu and Chang [
15] employed frequency-based models. Invariably, the work was proceeded by Xie, Hu and Slay [
16], who implemented a single class SVM model on short sequences. Overall, a better performance was achieved; however, the research encountered a low positive rate of about 20%. In countering these challenge, another researcher [
17] implemented a vector space representation and used several classifiers in attaining a detection accuracy above 95%. Among the primary lapses in the work with lightweight IDS are the use of outdated datasets. In addition, IDS models that make use of contemporary datasets are specially designed for cloud-related platforms. The aforementioned challenges reveal the need to develop lightweight smart security solutions that are easily distributed and possess the ability to last long in service. Instead of ensuring individual security for many IoT devices, it is more reasonable to ensure the implementation of network data security solutions. The artificial intelligence theories, like Machine Learning, have already proven their significance when dealing with heterogeneous data of various sizes [
18,
19]. Thus, in this study, a lightweight IDS via the use of a suitable host dataset was developed. Hence, the core contributions of this work are as follows:
To review security challenges in IoT. Based on the review, a general architecture of lightweight IDS based on the machine learning method is put forward. We also review the specific aspects and look at the advantages, limitations, and key challenges.
To explore Intrusion Detection Systems (IDSs) using limited resources, such as a Fog node (Raspberry Pi 3), using a contemporary dataset, ADFA-LD, rather than the outdated KDD Cup 99 dataset.
To propose a lightweight technique for Intrusion Detection Systems in a Fog Computing environment, which reduces and mitigates the overheads in the Cloud security challenges.
To examine and improve different feature extraction and selection methodologies that are compatible with the constrained resources of Fog Computing.
To evaluate the performance of different machine learning models based on time, energy consumption, and space complexity and to evaluate the performance of MLP and its different parameters via a single hidden layer perceptron for practical detection time and energy, deference’s number of nodes, and reduced computational complexity for the selection and extraction of features.
The rest of the paper is structured as follows:
Section 2 discusses the related works and analyzes the requirements of IoT security events and IDS in Fog Computing. It also presents a brief review of the IDS literature for a foundation of the presented work. It specifies the evolution and history of lightweight IDS based machine learning in the components of the IoT and their drawbacks.
Section 3 is an overview of the methodology and the technical background of this work.
Section 4 provides the analysis of the benchmark ADFA-LD dataset and details of an experiment in terms of the software and hardware used. We discuss the evaluation of the results in
Section 5.
Section 6 is a summary of the conclusion, and future work is presented in
Section 7.
4. Experimental Setup
This work was based on evaluating the results of benchmark datasets. Nevertheless, currently available datasets lack real-life properties, thus explaining why the majority of systems for detecting anomalies in the intrusion are not applicable in the production environment [
154]. Consequently, this leads to an inability to adapt to non-stop variances within networks, such as changes in topology, new nodes, and variations in traffic loads, among others. Therefore, to ensure the evaluation of the proposed framework and algorithm based on their level of effectiveness for detecting attacks in IoT, this research utilized an intrusion detection dataset. According to the literature, the most preferred datasets for intrusion detection are NSLKDD and KDDCUP’99 [
154,
155,
156]. Furthermore, in this work, a more suitable and modern dataset, the Australian Defence Force Academy Linux Dataset (ADFA-LD) [
157,
158], was employed to train and evaluate the performance of the system.
4.1. ADFA-LD Dataset
The collection and generation of traces in system call based on a large scale for the purposes of research for simplistic tasks, as well as the number of available datasets for evaluating IDS, are quite limited. Recently, some researchers proposed ADFA-LD datasets as a novel alternative for outdated datasets [
157,
159]. From their proposal, it was revealed that there exists a higher level of complexity in ADFA-LD as compared to other contemporary datasets. A preliminary performance analysis was conducted on ADFA-LD by some scholars [
160,
161], which revealed the ineffectiveness of Euclidean distance as a medium for separating normal behaviors from those that are instigated by attacks.
Table 9 presents the distribution between system call traces, splitting them into normal and different types of attacks under three ADFA-LD groups.
Python workbench was employed for evaluating the demonstration of the modified vector space on the dataset of ADFA-LD. This workbench has the ability to host concurrent algorithms of machine learning, which also are used for the selected datasets, under different sizes of terms. A total of nine algorithms for classification were selected out of six diverse groups [
17]. Furthermore, the datasets were gathered and converted to representations of modified vector space for diverse sizes of terms. The term sizes one and two were chosen for this experiment. The experiment on the ADFA-LD dataset was executed in favor of the classification of binary. Out of the two labels, one was used for each trace, either attack or normal. Additionally, each of the selected algorithms was run independently according to the chosen options for data conversion.
Table 9 gives a description of a number of extracted features from the ADFA-LD dataset for the size terming, via a representation of modified spaces within the vector.
In comparison with aforementioned dataset benchmarks, ADFA-LD is seen to have the most representative nature for handling present-day cyber-attacks. In addition, it offers a well-organized framework for evaluating performance and developing intrusion detection systems (IDSs). Furthermore, many system call traces are contained in ADFA-LD, some of which are retrieved based on diverse situations for the purpose of simulating real-life scenarios. Additionally, they comprise a quite concise collection of system call traces, which represents present-day vulnerabilities on system levels as well as attacks. Thus, the generating of ADFA-LD is from a local Linux server (having a Linux kernel of 2.6.38), offering advanced as well as popularly used computer systems. ADFA-LD generated attacks comprise Webshell, Adduser, Hydra-FTP, Meterpreter, and Java-Meterpreter. Each of these attacks is capable of generating up to 8–20 traces of attack.
Table 10 presents the number of retrieved traces according to individual attack type. Additional information with regard to the technical aspects of the dataset is available in the literature [
157].
4.2. Software and Platform
The experiments are implemented using Python 2.7 softwar; Scipy and Numpy are used for experiments and the reprocessing phase. In addition, for the aspect of visualization, the Matplotlib library was used, while the ScikitLearn library was used for machine learning [
162,
163,
164,
165].
In this work, Python programming language is used to implement machine learning techniques. Python is a great language for machine learning for numerous reasons. First, it has a clear syntax; second, with python, the manipulation of text is very easy. Thus, the majority of researchers, including those associated with private and public organizations, make use of Python, therefore leading to its rapid documentation and development. Additionally, the compilation of scientific libraries, such as Scikit Learn, an open-source library for machine learning, developed as part of a project for the Google summer code, established around 2007 by David Cournapeau [
166,
167]. The language used in writing this code is Python, which incorporates both the scientific and numerical libraries of python, such as NumPy, SciPy, Panda, and matplotlib. Furthermore, it also makes available provisions for effective machine learning tools, such as regression algorithms, classification, and clustering. Furthermore, it supports feature extraction approaches and offers tutorials for understanding the respective concepts [
19,
164].
The testing aspect of the experiment was done via Raspberry Pi 3, a small, low-powered single board computer made by the UK Raspberry Pi Foundation. The Raspberry Pi has gained popularity among computer enthusiasts and has been employed for diverse projects on robotics and IoT, thus making it a perfect choice for IoT-device-related applications. Among a lot of applications for IoT, Raspberry Pi has been deployed in the form of a Fog node, referred to in [
168,
169,
170]. Thus, this experiment makes use of Raspberry Pi 3, the third generation of Raspberry Pi.
Raspberry Pi 3 comes with a low-powered yet high-speed CPU, named BCM2835 (1.2 GHz 64-bit quad-core ARMv8 CPU), with approximately 40 General Purpose Input Output (GPIO) pins, which are used in connecting sensors, 1 GB of RAM, SD card 16 GB class 10, four USB ports, Video Core IV 3D graphics core, full HDMI port, and Ethernet port.
Figure 5 presents the hardware components’ location on the Model B of Raspberry Pi 3. Correspondingly, Raspberry Pi is installed with Debian Linux based OS, referred to as Raspbian, which serves as an optimization for the Raspberry Pi hardware. Furthermore, Raspberry Pi helps in evaluating the time taken in response by a classifier, based on specific IoT hardware [
4]. Thus, the consumption of energy by Raspberry Pi is calculated via a commonly used technique, not significantly different from a conventional computer system. The voltage value of Raspberry Pi model 3 B is around +5.1 V. With regards to the requirements for current, a keyboard and HDMI port were connected to the Raspberry Pi, resulting in a 400 mA electrical current requirement. The power consumption is yielded by the combination of the products of both the Voltage (
V) and the Current (
I), which is then multiplied by the CPU time (
t) to calculate the consumed energy [
21,
171].
5. Results and Discussion
The experiment conducted in this paper was aimed at addressing the need for the development of an HIDS anomaly based on light weight, which is responsive to most recent attacks via the usage of ADFA-LD datasets, to employ in IoT-based Fog computing. Thus, the research tries to address the following issues:
What techniques that support HIDS anomaly based on light weight can be developed in IoT-based Fog Computing?
What Machine Learning computable devices with limited resources can help create lightweight HIDS in Fog Computing?
What feature extraction and selection approaches for pre-processing data can produce high performance?
Which classifiers can give high accuracy?
Which classifiers can give low CPU usage and energy consumption in testing data?
Many algorithms were employed for the purpose of achieving adequate results using these techniques. Thus, the study proposes a general viewpoint for the detection of anomalies via machine learning techniques. The conducted experiments also proved that supervised learning approaches perform far better than unsupervised approaches, provided there are no unknown attacks in the test data. Previous studies revealed that out of numerous supervised approaches, the best performance can be achieved by RF, SVM-RBF, and MLP; however, there are differences with regard to their individual capabilities to detect attack class effectively. In order to compare with other machine learning methods, contrast experiments are designed at the same time. This is done in the binary classification experiments, for using more loading instances for lightweight evaluation.
The first step in this experiment involves the computation of 1-gram and 2-gram, for the system call traces, whereby selections for the top 60 and 80 features for 1-gram, followed by the top 80 and 120 features for the 2-gram, were made on the basis of the value of their information using MI, which were combined to train the model. Comprehensively, the numerals 60, 80, and 120 were selected for the reduction of the data size as well as data representation [
21].
Furthermore, the classifiers were compared with regard to their accuracy, recall, F1-measure, FPR, ROC Curve, and AUC. In addition, a comparison was made of the testing time for CPU usage and energy consumption between the different classifiers using 1-gram and 2-gram, which are the maximum features on the Raspberry Pi platform.
This work did not focus on memory usage testing time, because after the collection of results and analysis, it was discovered that consumers for each classifier did not exceed 350 Bytes, as shown in
Figure 6, for the KNN classifier. Therefore, it is not considered important in the Raspberry Pi platform.
5.1. Performance of the Feature Extraction and Feature Selection
In this section, the performance of the feature extraction and feature selection methods are explored in terms of CPU time and memory usage. The 1-gram and 2-gram transformation modified vector spaces (feature extraction) are tested with two feature selection methods: Principle Component Analysis (PCA) and Mutual Information (MI) (filter method). Based on the test, the best feature selection method in term of its “light weight” was selected for implementation with the MLP classification method.
Figure 7a,b show the CPU time and memory usage, respectively. Based on this figure, we can notice that (MI) outperforms PCA, which on the contrary has a lesser performance for CPU time with the consumption of less memory.
The following stage, traces in the system call, makes use of a sparse matrix formatting technique from Python to ensure reduction in the size of the memory. This approach to formatting is of much relevance, as it was able to reduce a reasonable amount of data in the matrix, as 98.2% of the 2-gram matrix entries were zero values.
Figure 8 depicts the matrix’s compressed form, which is around 4% of the initial dense matrix memory space.
5.2. Performance of the Classification Methods
Subsequent to the normalization of the processed data for more suitable performance,
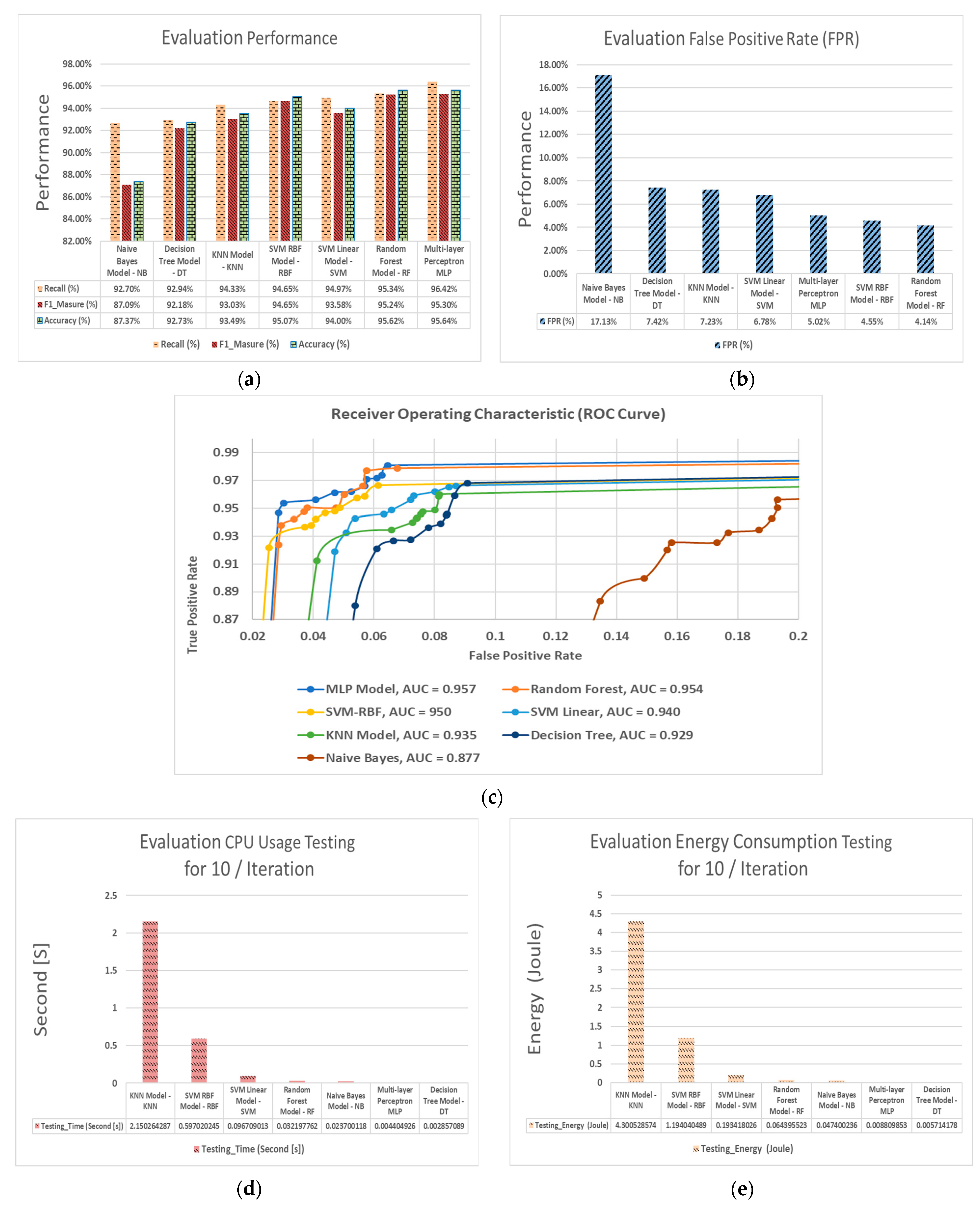
Figure 9a presents a comparison of recall, F1-measure, and accuracy between the different classifiers, using 80 features for 1-gram and 120 features for 2-gram, thus selecting the highest number of features to provide more efficiency and to help in determining the classifiers of good performance as well those fit for lightweight techniques.
Based on
Figure 9a, it is noticeable that MLP outperforms the other classifiers, in accordance with their accuracy, recall, and F1-measure. Correspondingly, the Naive Bayes and Decision Tree Models achieved the worst results for these metrics.
In terms of FPR,
Figure 9b reveals that RF, SVM-RBF, and MLP models outperform by approximately 5% compared to others, which achieved 17.13%. It is also noticeable that RF and SVM-RBF models achieved higher FPR than MLP, up to a difference of nearly 0.08% FPR. This value is meaningful with reference to the rate of detection; however, it is observed in
Figure 9c, which shows a comparison between ROC curves, that it is a graph of true positive rate against FPR. It is also noticeable that MLP outperforms the other classifiers, as it has the highest range over curve. In addition, the AUC value is equivalent to the probability that a classifier will rank a randomly chosen positive instance higher than a randomly chosen negative one. MLP showed the highest value (95.7%), and this represents that it was able to achieve a higher performance than the other classifiers.
Furthermore,
Figure 9d shows a comparison of CPU usage for the testing time between the different classifiers. Based on this figure, it is noticeable that Decision Tree (DT) and MLP outperform the other classifiers in terms of the testing time. However, SVM-RBF, RF, and KNN models had the worst values for CPU usage for the testing time.
In terms of energy consumption,
Figure 9e depicts the Decision Tree (DT), whereby MLP models outperformed by up to around (0.008) Joules the others models, including the KNN model (4.3 Joules). In other words, the MLP outperforms the other classifiers in terms of accuracy, recall, F1-measure, and FPR and achieved low values for CPU usage and energy consumption.
According to the above results, the best performance is given by the MLP model. Furthermore, MLP also did well with regard to the amount of CPU time and consumption of energy achieved for all instances during the testing phase, as compared to other classifiers. There were only a few cases where simple performances were provided by these techniques. However, observing the MLP model, it is obvious that it achieved a good performance and is also compatible with lightweight devices.
5.3. Performance on the Raspberry Pi
Raspberry Pi has a significantly slower speed as compared to other regularly used computers; thus its limited resources for computing makes it an appropriate platform to test the performance of the model. The model’s performance for this experiment was evaluated via a Raspberry Pi 3 of the Model Type B. The performance showed the median for each of the 10 iterations tested. Further observation showed that there were 350 instances (i.e., “normal” = 200, “attack” = 150) for the experimental testing of the test set.
Furthermore, the optimization of the CPU’s energy and time could be achieved via the utilization of Fog Computing’s distributive nature. It was observed that the average time used in testing was around 0.004 s, thus indicating a reasonable delay, as applicable to many IoT-inclined applications, and the energy consumption rate was 0.008 Joules.
Based on the benchmark, using the ADFA-LD training set and testing set, the experimental results show that for binary classification, the intrusion detection model of MLP-IDS through the training set and testing set has higher accuracy than other machine learning methods and maintains a high recall, F1-measure, and accuracy rate as well as the highest ROC curve with a high value of AUC, even in the case of FPR. The FPR rate was low for the other models, such as SVM-RBF and RF; however, though they outperformed, they had higher CPU time and energy consumption for the testing process and thus were inappropriate for the lightweight model. Consequently, the DT model outperformed the MLP model with respect to CPU time and energy consumption for the testing process, but maintained a lower rate of recall, F1-measure, and accuracy as well as a low ROC curve and low value of AUC; however, it also achieved a high value of FPR as compared to the other machine learning methods. Of course, the model proposed from this experiment will reduce the time and energy consumption for the testing process more effectively, as it boasts a higher accuracy than the other machine learning methods.
5.4. Performance of the MLP Methods (Parameter)
This work employed an ANN approach to serve as the computational model. This is due to its influence on biological neural network characteristics for incorporating intelligence into the proposed methods. Thus, a particular type of ANN is represented in the form of a direct graph, for the purpose of transmitting diverse information from the system over the edge and across nodes, without the formation of a cycle. To achieve this, a MLP model was adopted. However, in order to achieve an outstanding performance, it is important to find an optimal parameter when modeling an MLP [
162,
165].
Fully connected layer: This layer is referred to as a layer that is fully connected due to the connectivity of the layer’s unit with all other units around the succeeding layer. From a general perspective, high dimension mapping can be easily achieved via layers that are fully connected. This will result in more accuracy of the output. The function for non-linear activation used in this experiment is ReLU.
Batch Normalization and Regularization: Dropout (0.01) and Batch Normalization were employed amidst layers that were fully connected, for the purpose of over-fitting obviation as well as to ensure a speed-up of the model training of the Deep Neural Network (DNN). Regarding the alternative architectures, it was discovered that DNNs were able to over-fit the data used for training very easily, without the need for regularization, including situations where training was conducted for a large number samples.
Classification: This is the last layer, and it is fully connected as it makes use of the activation function from sigmoid for the classification of binary, as well as the activation function from softmax for the classification of multi-classes. Thus, the definition of the function for prediction loss in sigmoid is achieved via binary cross entropy; moreover, the definition for the prediction loss of softmax is achieved via categorical cross entropy as follows:
The estimation for the prediction loss of Binary classification is achieved via binary cross entropy, given by
where
pd denotes a vector of the predicted probability for all the testing dataset samples;
ed denotes a vector of expected class label, for which the values lie between 0 and 1
The prediction loss for Multi-class classification is estimated using categorical cross entropy, given by
where
ed represents the true probability distribution;
pd denotes the predicted probability distribution. Furthermore, in this research, adam was used as an optimizer for ensuring the minimization of the loss of categorical cross entropy as well as binary cross entropy [
129,
172].
As MLPs are parameterized, as shown in
Table 11, the performance is dependent on the optimized parameters. Determining the parameter that is optimized for both MLP network topologies and network parameters was achieved via the ADF-LD dataset. For identifying which parameter is suitable for MLP, this research employed the use of an architecture of medium size, for the experimentations within specific hidden units, rate of learning, and the functions of activation, as follows: default (Activation = ‘relu’, Solver = ‘adam’, Alpha = 0.0001), a small node size, and a single hidden layer. The architecture of MLP contains three layers. The first is the input layer, the second is the hidden layer or fully connected layer, and the third is the output later.
The advantages of Multi-layer Perceptron (MLP) are that it is able to (1) learn non-linear models and (2) learn models in real-time (online learning) via partial fit.
The disadvantages of Multi-Layer Perceptron (MLP) include the following: (1) MLP has hidden layers consisting of a non-convex loss function and comprising the existence of more than a single local minimum. Thus, accuracy of diverse validations can occur due to the initialization of various random weights. (2) MLP requires the tuning of several hyperparameters, including numerous hidden neurons, iterations, and layers. (1) MLP has a sensitivity to feature scaling [
129].
The evaluation performance for MLP parameters (Recall, F1-Measure, Accuracy, FPR) is illustrated in
Figure 10. The evaluation of light weight is based on the following parameters, as illustrated in
Figure 11: Evaluation of CPU Usage MLP Parameter; Evaluation of Memory Usage MLP Parameter; Evaluation of Energy (Consumption). This process includes exploring all factors that help to reach the goals of achieving a light weight. This study obtained performance under the default values of the MLP model that were deemed the most appropriate; however, some parameters were used to help provide the light weight. The performance from comparing both alpha values at an equal point of 10.0 shows that there is an improvement in both the processor usage and energy consumption. in addition, when using activation “identity”, it contributes to the support of light weight, while the performance of both “identity” and the alpha 10.0 is poor.
5.5. Performance of the MLP Methods (N-gram)
The experiment is performed via combining the top 60 and 80 for the 1-gram, whereas for the 2-gram, it combined the top 80 and 120, with several numbers of nodes at the hidden layer, after which the results underwent evaluation.
Figure 12a illustrates the model performance based on accuracy, via the use of combining four top features and their N-grams, accordingly. From the results, the best accuracy value was achieved for 4 nodes at the hidden layer, which used 80 1-gram and 120 2-gram.
With regards to the recall values, as depicted in
Figure 12b, the best value achieved around 97%, which was possible under three cases, namely the 2 node model via 80 1-gram and 80 2-gram; the 4 node model via 60 1-gram and 120 2-gram; the 6 node model via 60 1-gram, and 120 2-gram. The F1 measure values for total combinations of 1-gram as well as 2-gram are illustrated in
Figure 12c. The best value for the F1-measure was achieved on the 6 node model via 80 1-gram and 80 2-gram.
In terms of FPR,
Figure 12d shows that when increasing the number of nodes and the number of combinations of 1-gram and 2-gram, the models outperform.
Figure 12e shows that the best Area Under Curve (AUC) value achieved during the experiment was for 6 nodes at the hidden layer, with 80 1-gram and 120 2-gram, which achieve a value of 94.95%.
In terms of CPU usage and energy consumption,
Figure 12f,g depicts the low values. When using a small number of nodes and small numbers for all combinations of 1-gram and 2-gram, high values of CPU usage and energy consumption result. When increasing the number of nodes and the number of combinations of 1-gram and 2-gram, the best consumption value is achieved on the 2 node model using 60 1-gram and 80 2-gram, which outperformed by up to around (0.0025) seconds and by a (0.005) Joule energy consumption rate.
Furthermore, comparisons were made among all performances, such as for accuracy, recall, F1-measure, FPR, AUC, CPU usage, and energy consumption of the models via diverse nodes. These comparisons revealed that the overall outstanding performance was attained at the point where 2 or 4 nodes were used at the hidden layer. However, it is worth noting that the 5 and 6 node models also produced good values for the recall rate, similar to that of the 4 node model. Thus, conclusions can be drawn from the above analysis as to the fact that the model can perform well, provided the hidden layer contains a minute number of nodes. The use of 4 nodes at the hidden layer is adequate for the majority of applications. Overall, it can be postulated that the 4 node model of a hidden layer performs far better than models with a greater number of nodes, working on a mix of several 1-gram and 2-gram. The implication of this is that the addition of more nodes will yield an insignificant improvement in the performance of the model.
6. Conclusions
In this article, a novel and intelligent architecture of an IDS is presented. To address the aforementioned limitations of current systems, the IDS presented here includes the main function, type, and normal behavior profile of each IoT device connected to the network; the type of attack deployed is classified. Evaluation of the performance of applying a supervised machine learning approach to automate each function demonstrates that the proposed architecture can successfully distinguish between IoT devices on the network and whether network activity is malicious or benign, and it can detect which attack was deployed on which device connected to the network automatically. In addition to the experimental results, this study provides resources that can further support research into automating IoT-based cyber-attack detection.
In this work, a methodology was presented to develop a lightweight IDS-based machine learning model that can be used to identify potential attacks against IoT security, considering their impacts and the ways of mitigating as well as recovering from these attacks. In this work, the Fog Computing concepts and its security challenges were discussed.
The proposed method is tested using the ADFA-LD dataset for anomaly HIDS.
Spares Matrix (Memory Usage)—the compressed form of the matrix is around 4% of memory space of the original dense matrix.
Based on these results, we can notice that Mutual Information (MI) outperforms PCA, with less CPU time and with less memory consumption.
The research found that MLP outperforms the other classifiers in terms of 96% accuracy, 97% recall, 96% F1-Measure, 5% False Positive Rate (FPR), the highest curve of ROC, and 96% Area Under The Curve (AUC). It also achieved low CPU time usage of 4.404 ms and a low energy consumption of 8.809 mj.
This study obtained performance under the default values of the MLP model that were deemed the most appropriate; however, some parameters were used to help provide the light weight. The performance from comparing both alpha values at an equal point of 10.0 shows that there is an improvement in both the processor usage and energy consumption. in addition, when using activation “identity”, it contributes to the support of light weight, while the performance of both “identity” and the alpha 10.0 is poor.
The test is executed with 2, 3, 4, 5, and 6 nodes of the MLP single hidden layer. From the experiment, we found that 2 nodes of the MLP single hidden layer with 80 1-gram and 80 2-gram were able to achieve 95% accuracy, 97% recall rate, 94% F1-measure, and FPR of 7%, and an AUC of 95%. This is comparable to the higher number of nodes (i.e., 3 nodes to 6 nodes), which give similar results. Since the 2 node model has lower complexity, and there is no significant advantage when a higher number of nodes is implemented, the 2 node implementation is suggested for the Fog device.
Raspberry Pi, which acts as the Fog device with its limited computational resources, is a suitable platform for testing the model performance. The performance that shows the median for the CPU time usage is approximately 5 ms, and the energy consumption is approximatively 9 mj. The testing time could be optimized by utilizing the distributed nature of Fog Computing.
IoT end devices need novel solutions to protect their privacy. The current paper employed the application of the concepts of “A Lightweight Perceptron-based Intrusion Detection System” using Fog Computing to build a distributed lightweight security solution with high lifespan for IoT security.