An Integral Model to Provide Reactive and Proactive Services in an Academic CSIRT Based on Business Intelligence
Abstract
:1. Introduction
2. Related Work
3. Materials and Methods
3.1. Project Planning
3.2. Definition of Requirements
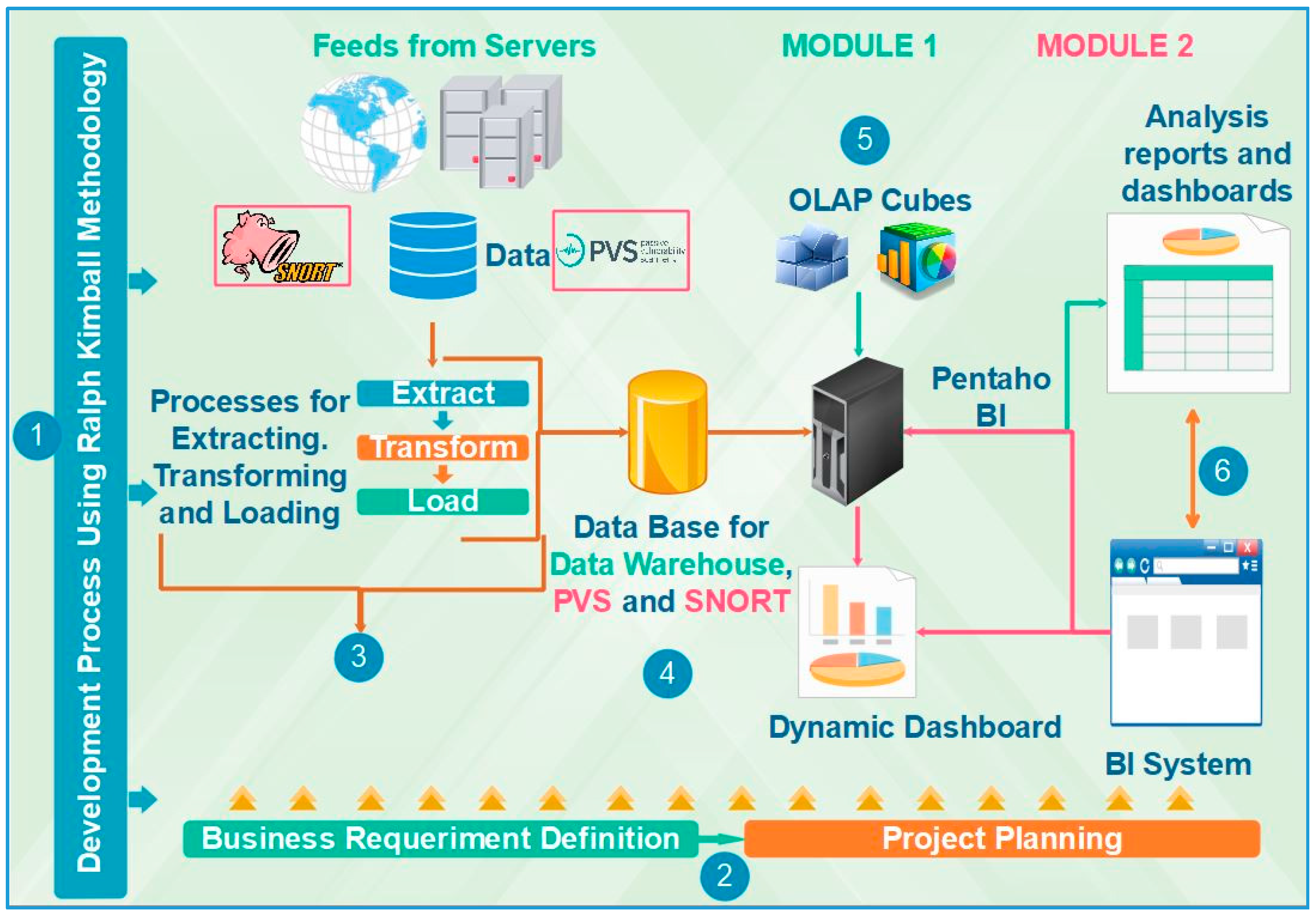
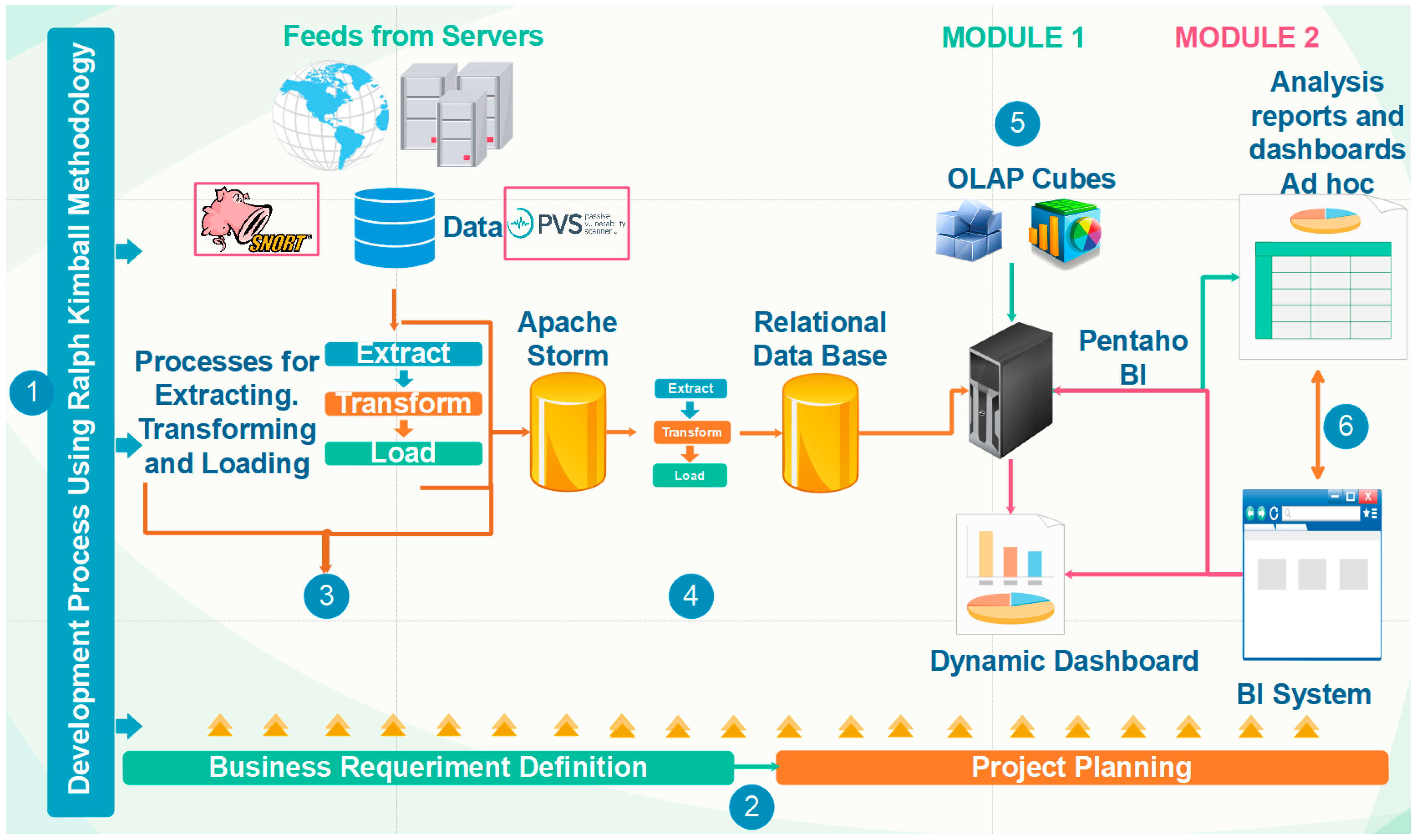
3.3. Design and Implementation of the Solution
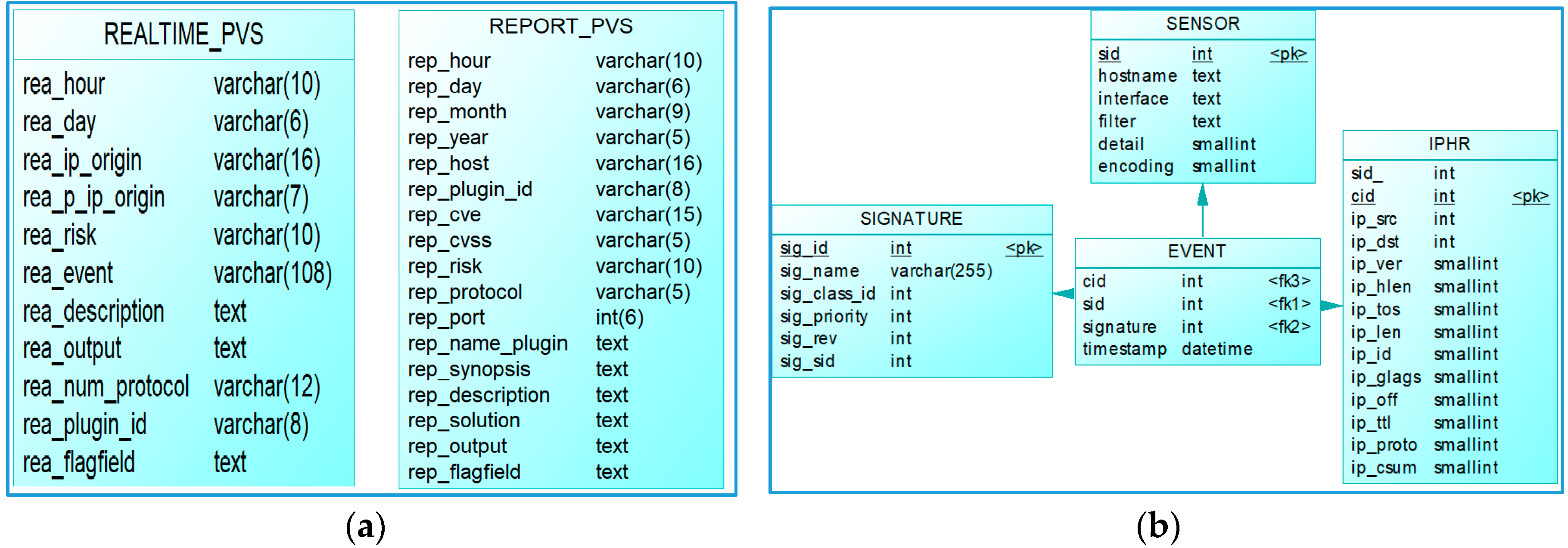
3.3.1. Data Sources
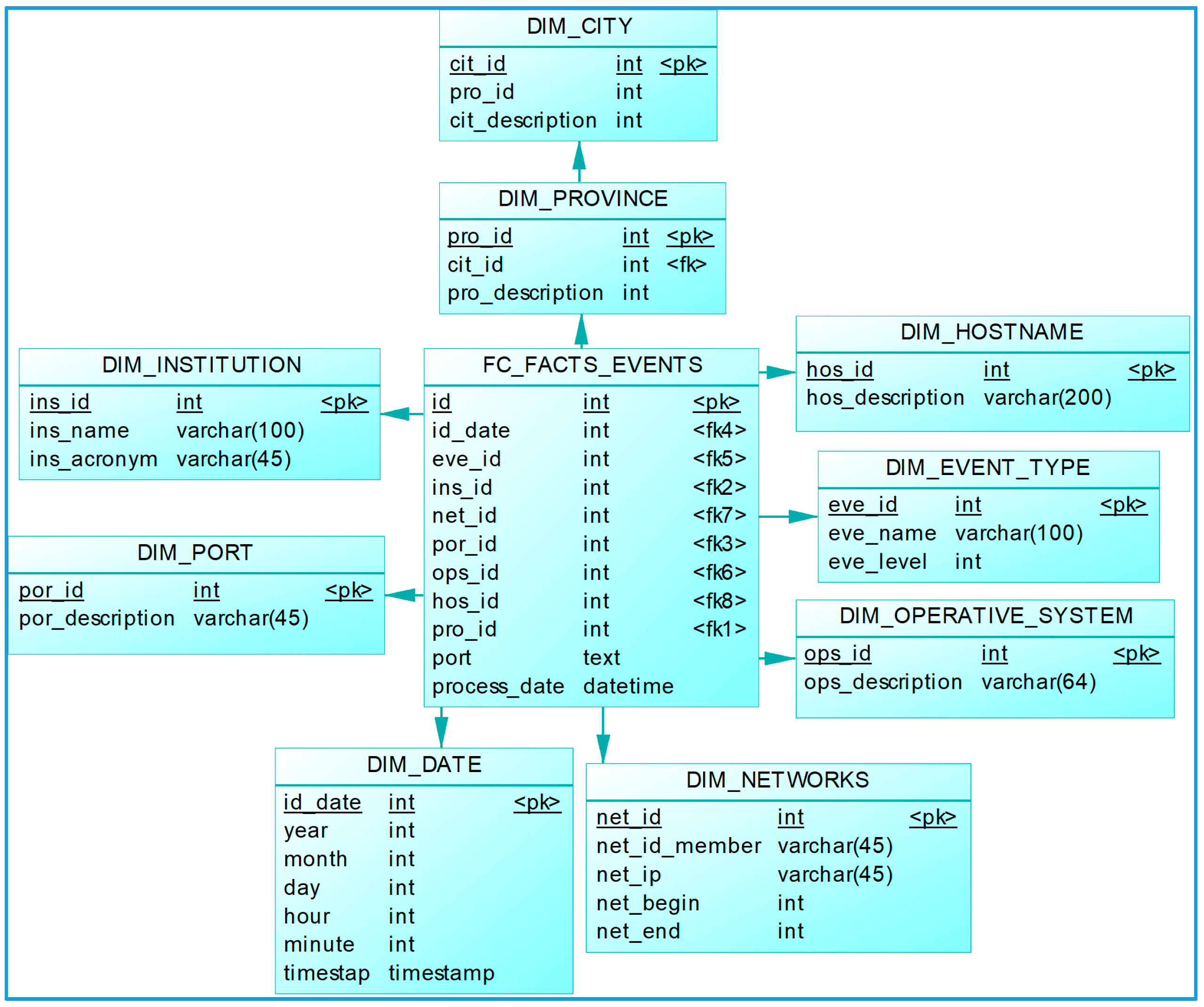
3.3.2. Dimensional Data Modeling
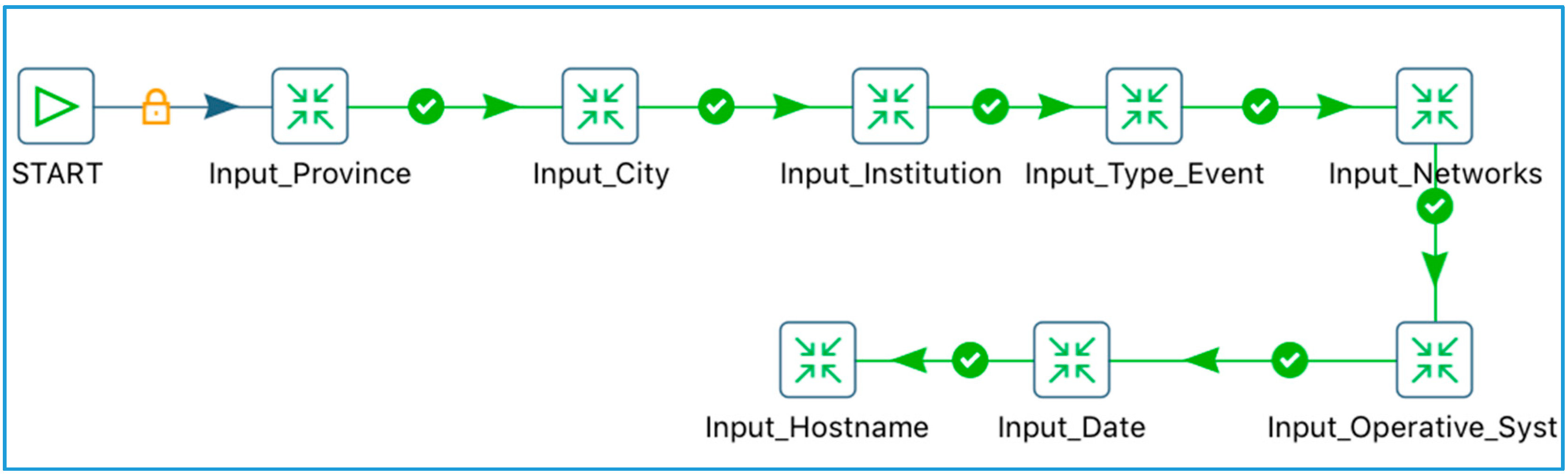
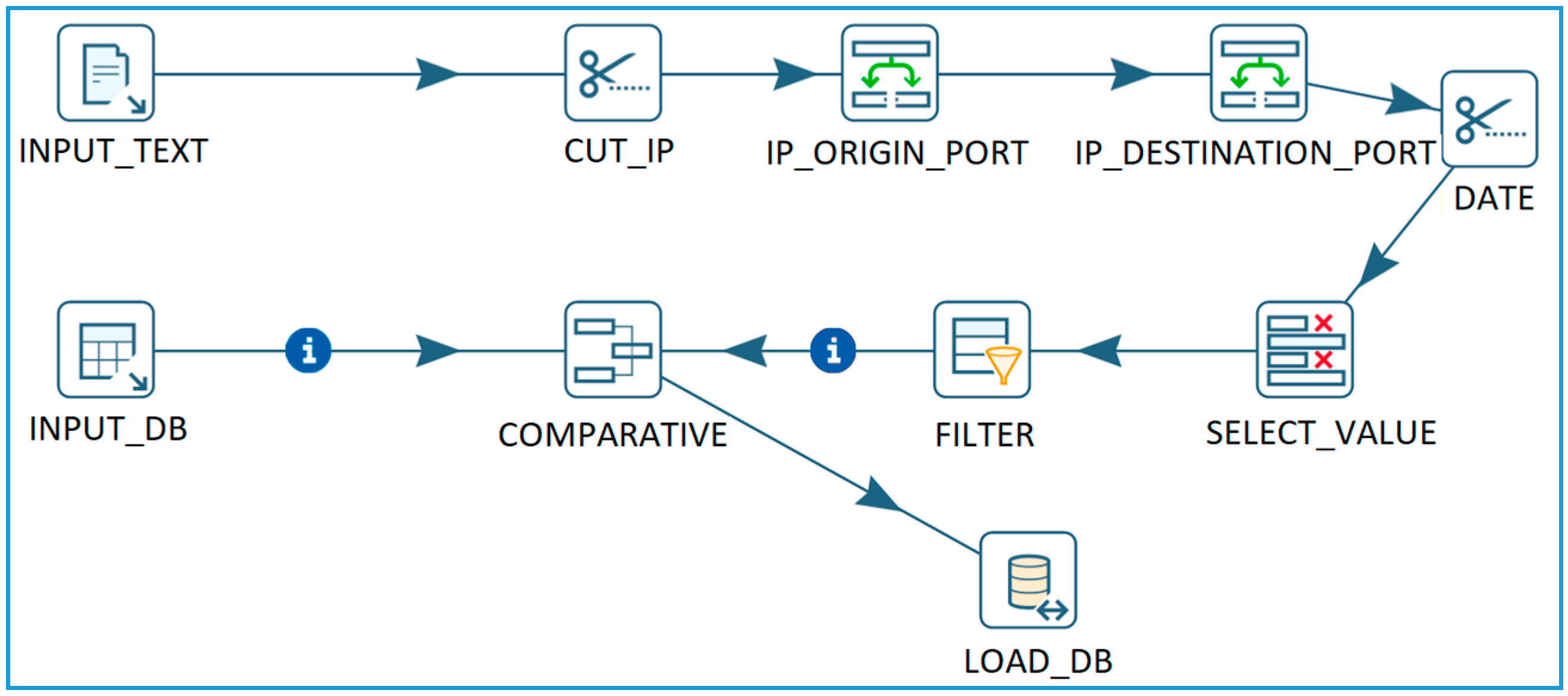
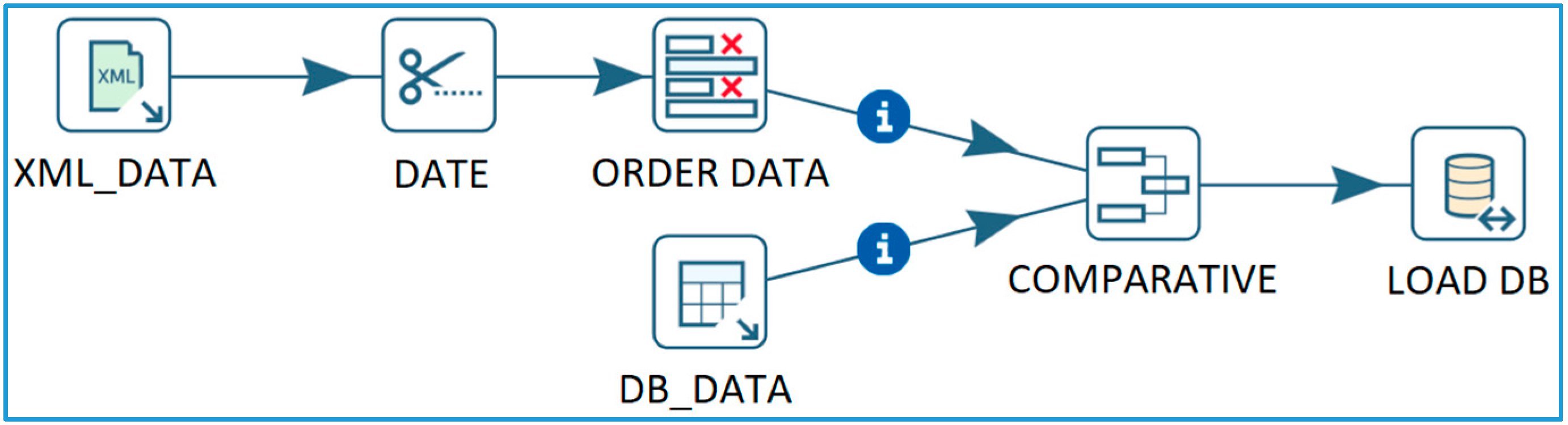
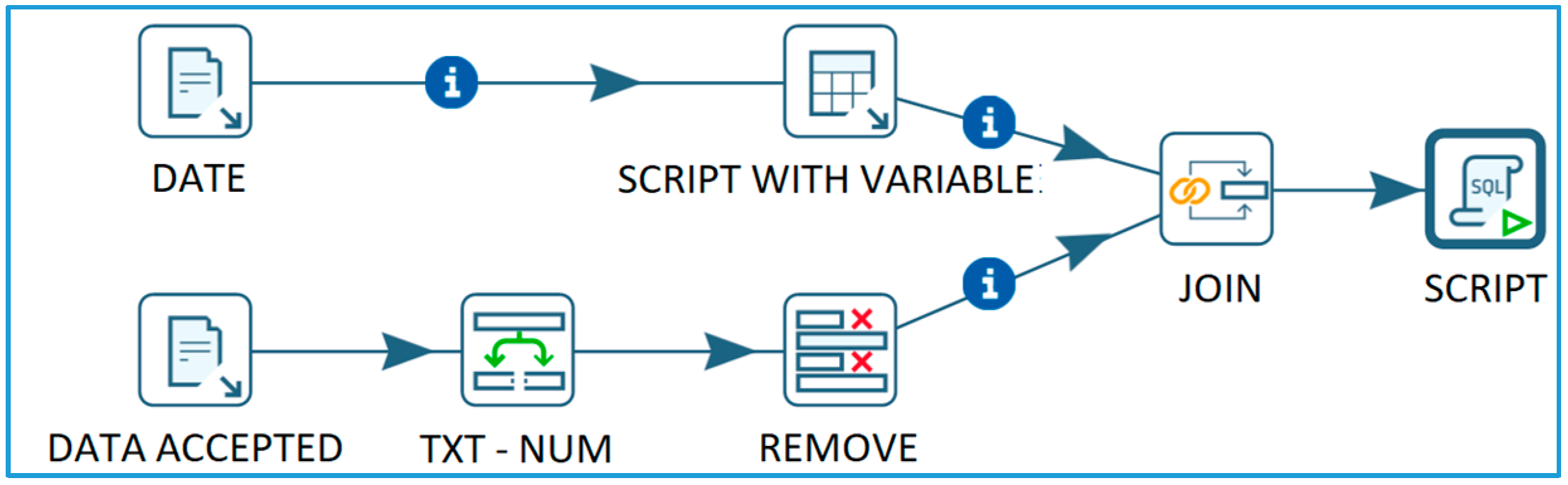
3.3.3. ETL Processes for Capturing and Data Filtering
3.3.4. Development of OLAP Cubes and Reports
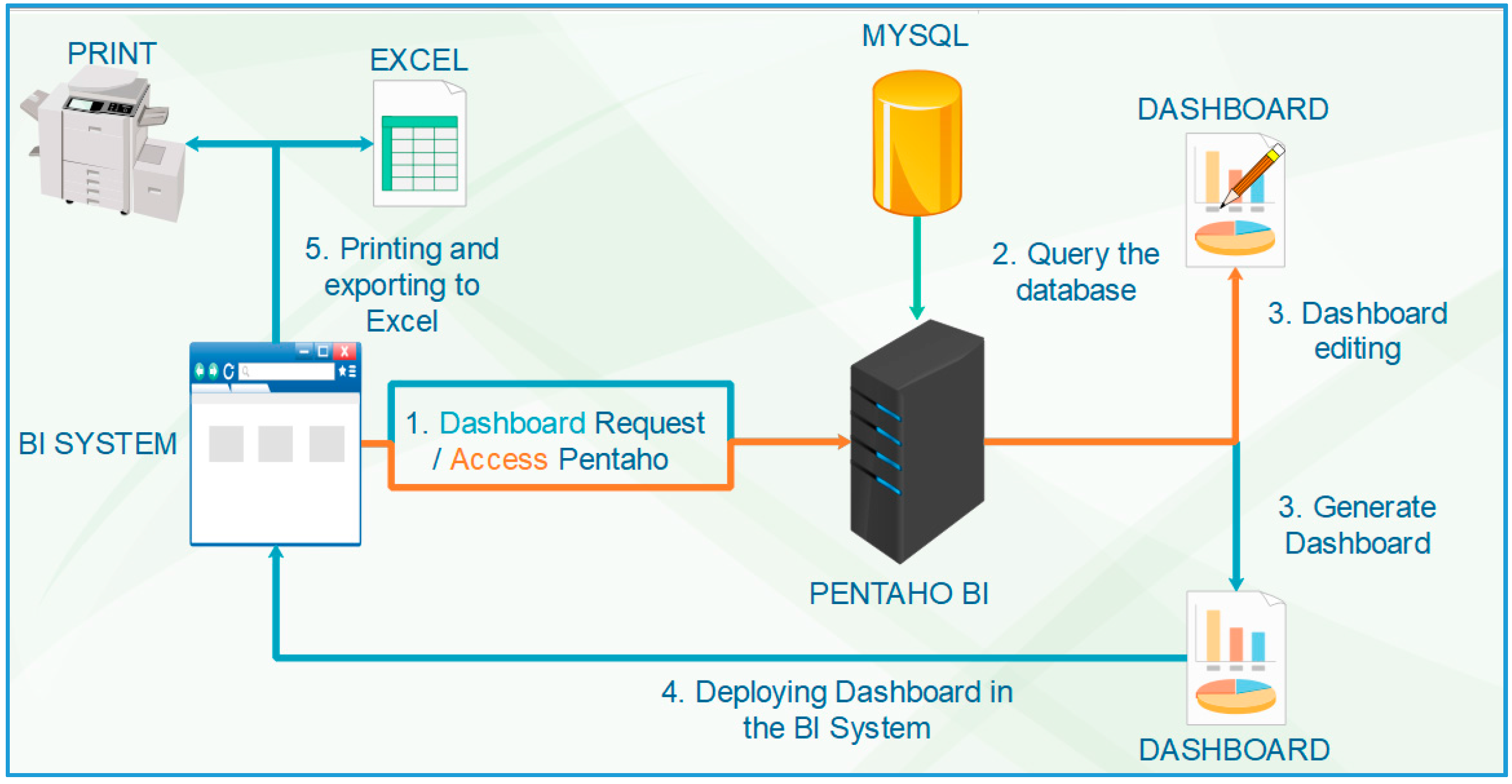
3.3.5. Custom BI Dashboards Development
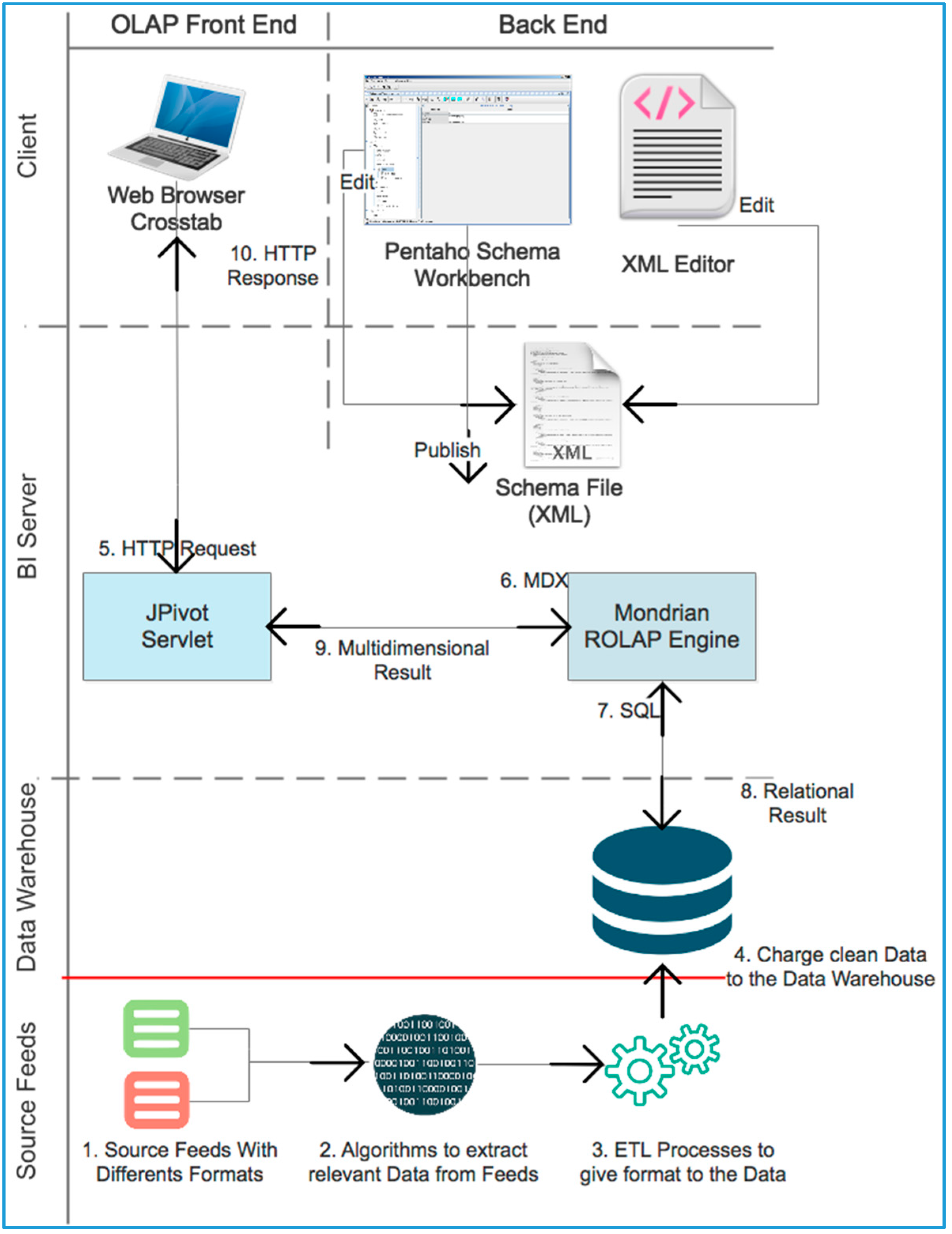
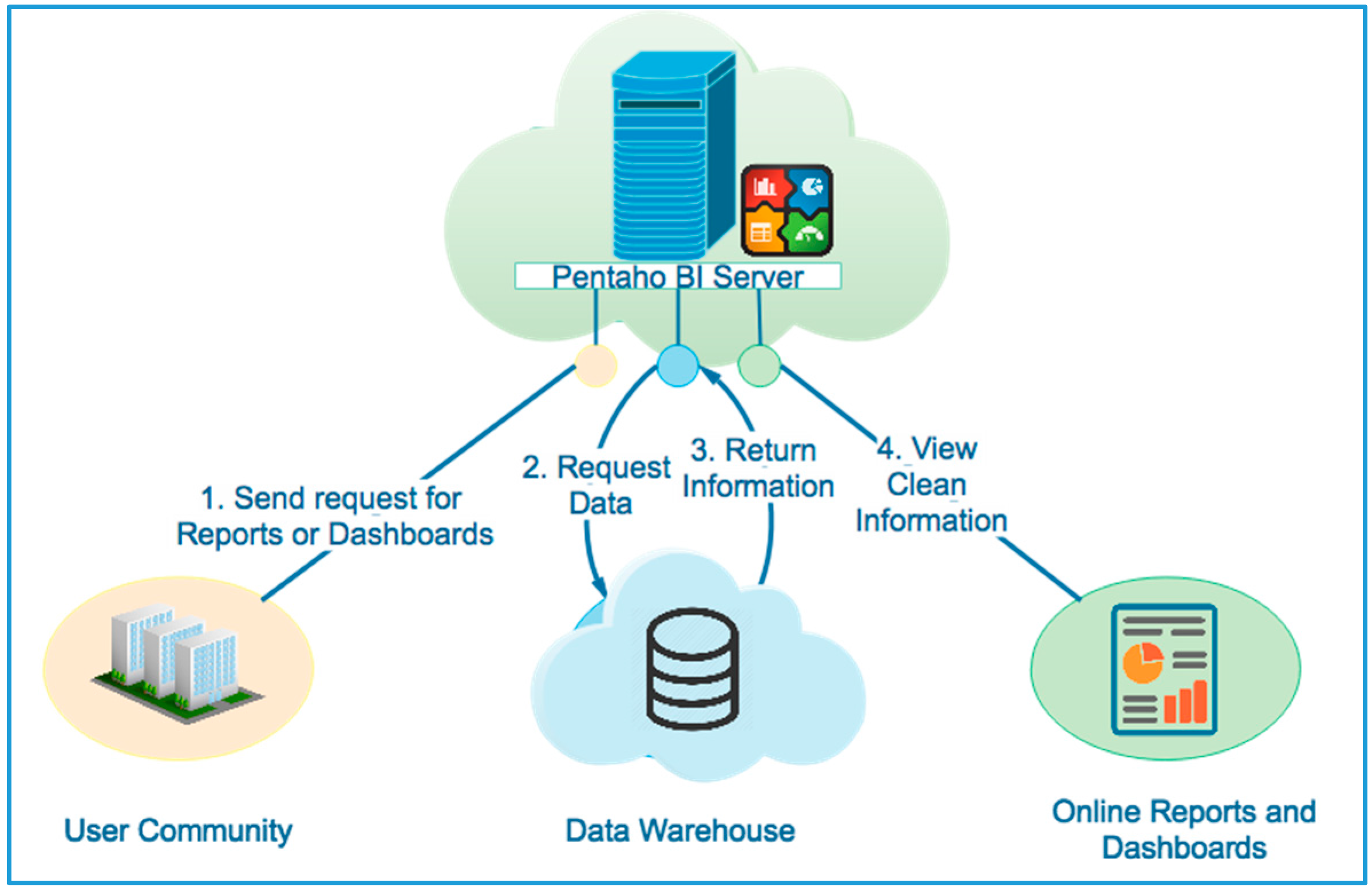
3.3.6. Development of the BI System
3.3.7. Preliminary Discussion
3.3.8. Proposal to Permit Scalability in a Scenario of Significant Data Growth
4. Results
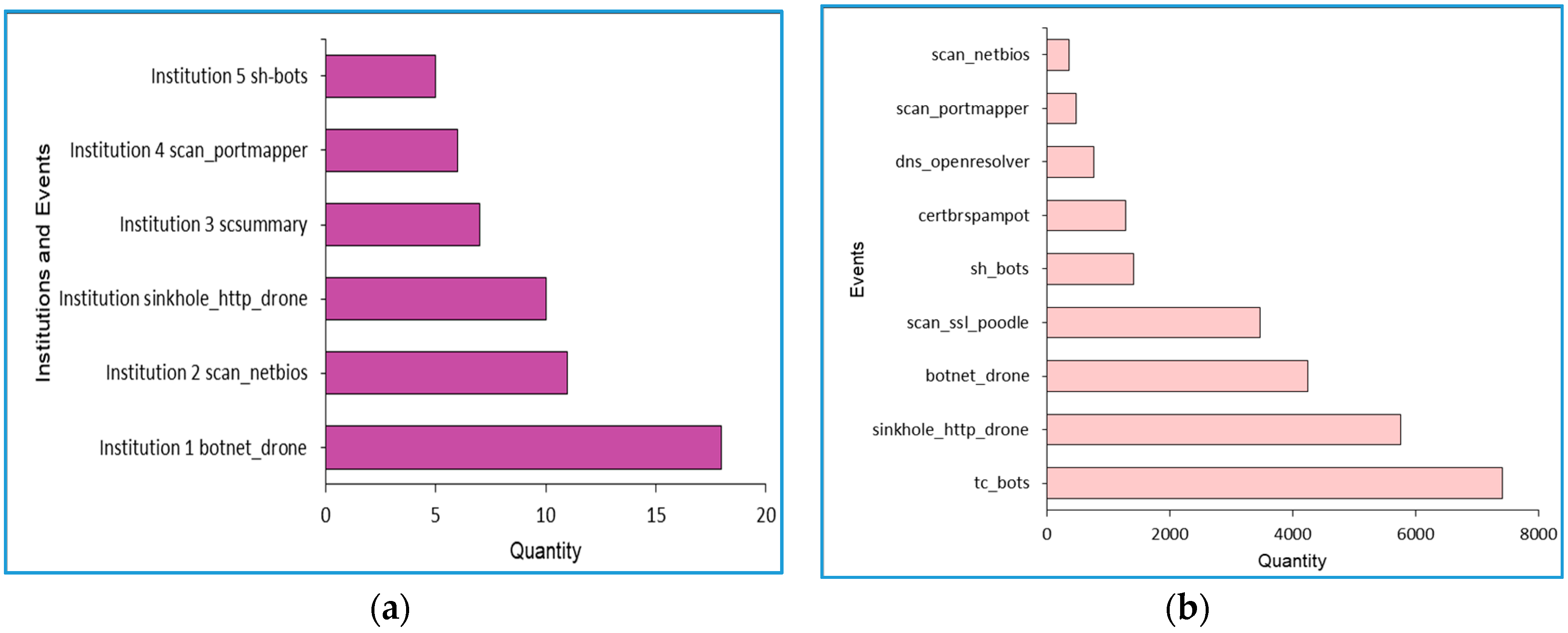
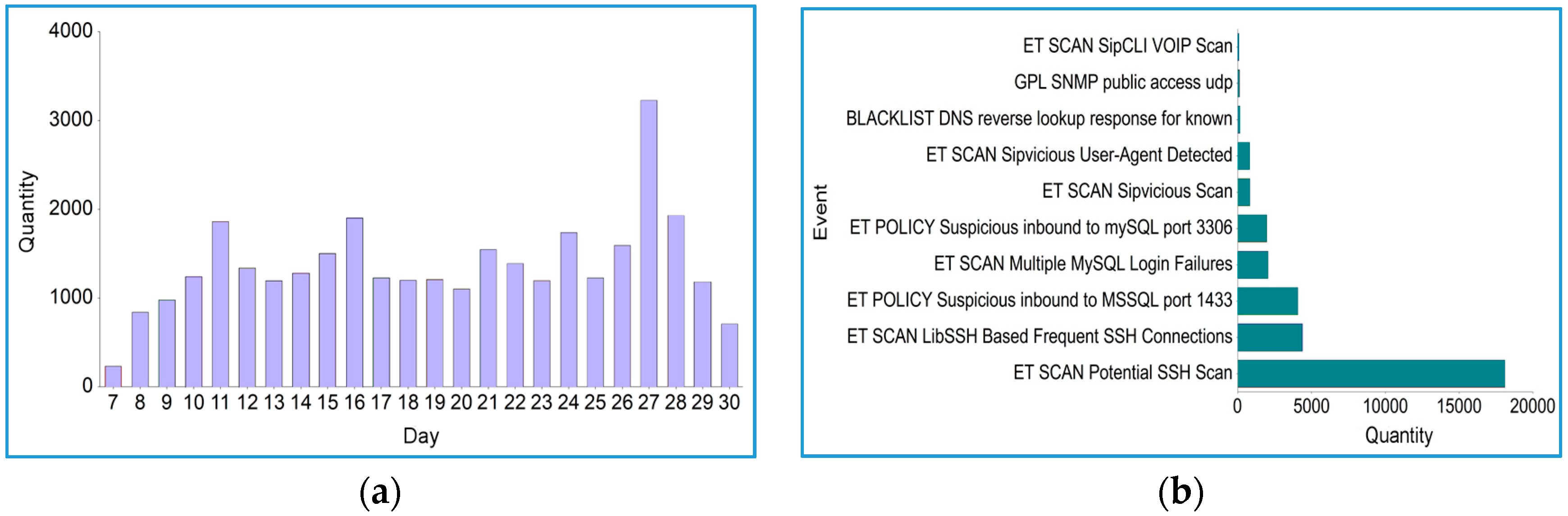
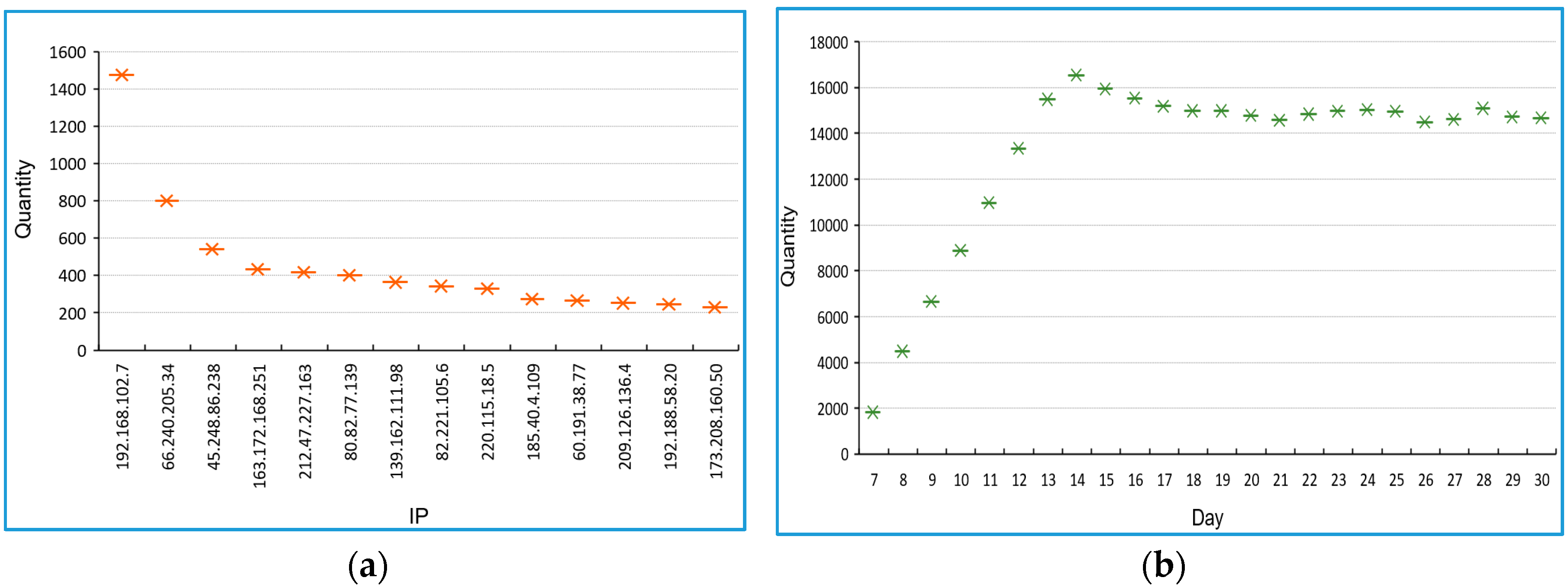
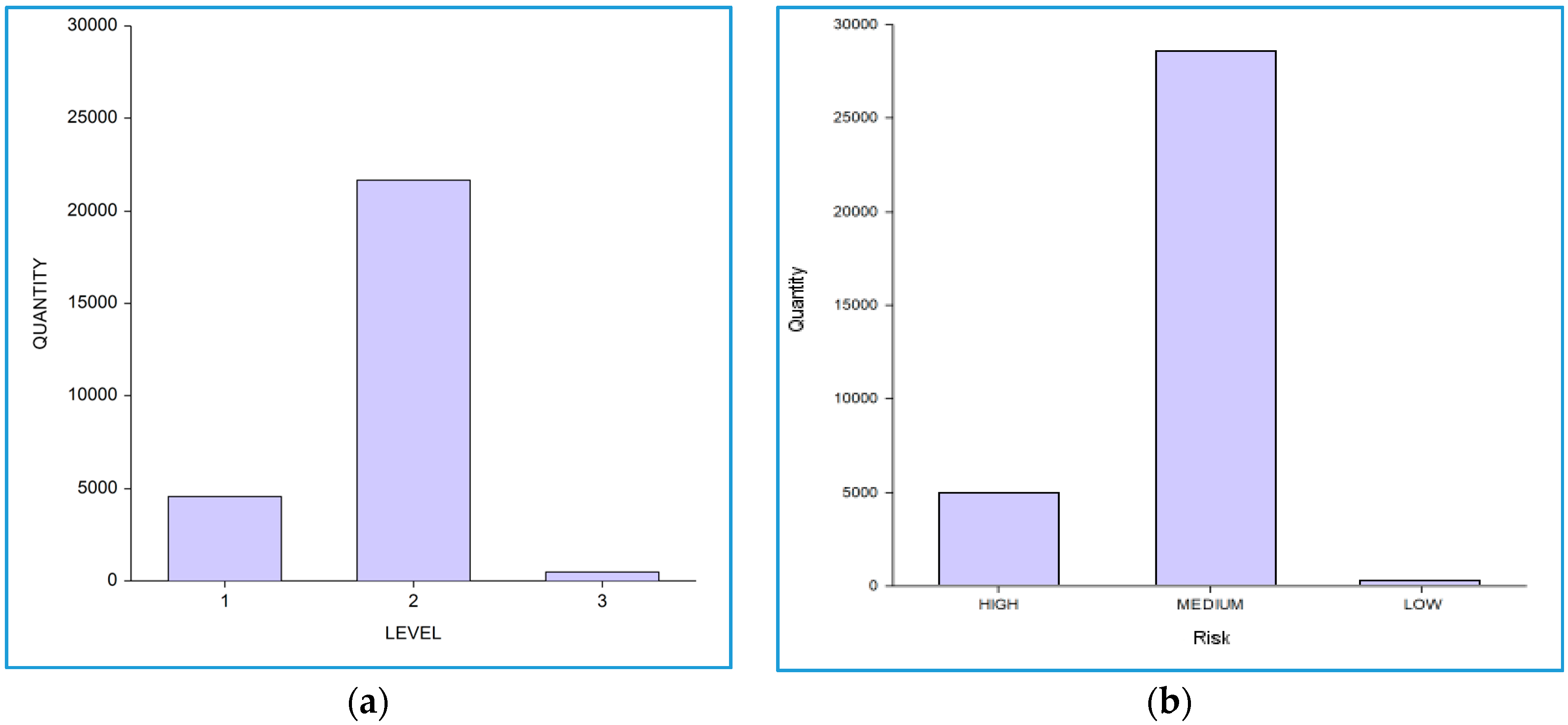
4.1. Proof of Concept
4.2. Evaluation Results
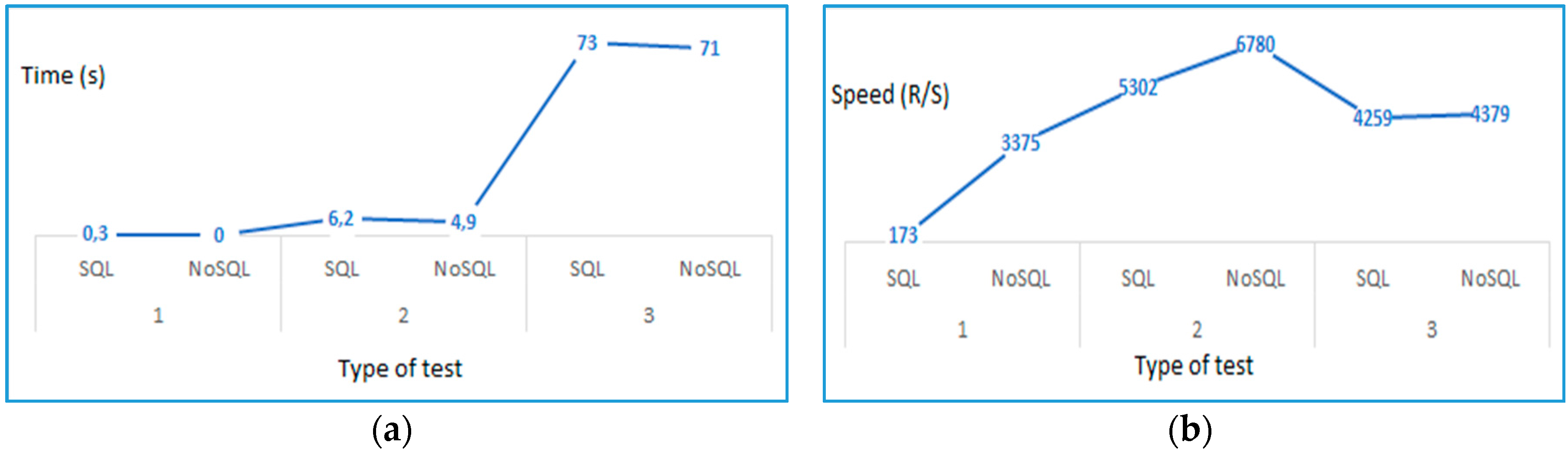
4.3. Comparison of Results Using MySQL against a NoSQL Environment
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Wamala, F. ITU National Cybersecurity Strategy Guide; International Telecommunications Union: Geneva, Switzerland, 2011. [Google Scholar]
- Ruefle, R.; Dorofee, A.; Mundie, D.; Householder, A.D.; Murray, M.; Perl, S.J. Computer security incident response team development and evolution. IEEE Secur. Priv. 2014, 12, 16–26. [Google Scholar] [CrossRef]
- Cichonski, P.; Millar, T.; Grance, T.; Scarfone, K. Computer security incident handling guide. NIST Spec. Publ. 2012, 800, 61. [Google Scholar]
- Johnson, C.; Badger, L.; Waltermire, D.; Snyder, J.; Skorupka, C. Guide to cyber threat information sharing. NIST Spec. Publ. 2016, 800, 150. [Google Scholar]
- Watkins, B. The Impact of Cyber-Attacks on the Private Sector. Available online: http://www.amo.cz/wp-content/uploads/2015/11/amocz-BP-2014-3.pdf (accessed on 22 September 2017).
- Sandberg, A.B.; Crnkovic, I. Meeting industry: Academia research collaboration challenges with agile methodologies. In Proceedings of the 39th International Conference on Software Engineering, Buenos Aires, Argentina, 20–28 May 2017. [Google Scholar]
- Freet, D.; Agrawal, R. A virtual machine platform and methodology for network data analysis with IDS and security visualization. In Proceedings of the Southeast Con, Charlotte, NC, USA, 30 March–2 April 2017. [Google Scholar]
- Wedgbury, A.; Jones, K. Automated asset discovery in industrial control systems: Exploring the problem. In Proceedings of the 3rd International Symposium for ICS & SCADA Cyber Security Research, British Computer Society, Ingolstadt, Germany, 17–18 September 2015. [Google Scholar]
- Kimball, R.; Ross, M.; Becker, B.; Mundy, J.; Thornthwaite, W. The Kimball Group Reader: Relentlessly Practical Tools for Data Warehousing and Business Intelligence Remastered Collection; John Wiley & Sons: Hoboken, NJ, USA, 2015. [Google Scholar]
- Power, D.J.; Sharda, R. Decision Support Systems. In Springer Handbook of Automation; Springer: Berlin/Heidelberg, Germany, 2009; pp. 1539–1548. [Google Scholar]
- Lim, E.; Chen, H.; Chen, G. Business intelligence and analytics: Research directions. ACM Trans. Manag. Inf. Syst. 2013, 3, 17. [Google Scholar] [CrossRef]
- Pipyros, K.; Thraskias, C.; Mitrou, L.; Gritzalis, D.; Apostolopoulos, T. A new strategy for improving cyber-attacks evaluation in the context of Tallinn Manual. Comput. Secur. 2017. [Google Scholar] [CrossRef]
- Rajasekharaiah, K.M.; Dule, C.S.; Srimani, P.K. CRSA cryptosystem based secure data mining model for business intelligence applications. In Proceedings of the International Conference on Electrical, Electronics and Optimization Techniques (ICEEOT), Chennai, India, 3–5 March 2016. [Google Scholar]
- Valladares, P.; Fuertes, W.; Tapia, F.; Toulkeridis, T.; Pérez, E. Dimensional data model for early alerts of malicious activities in a CSIRT. In Proceedings of the 2017 International Symposium on Performance Evaluation of Computer and Telecommunication Systems (SPECTS), Seattle, WA, USA, 9–12 July 2017. [Google Scholar]
- Yang, J.; Ryu, D.; Baik, J. Improving vulnerability prediction accuracy with secure coding standard violation measures. In Proceedings of the 2016 International Conference on Big Data and Smart Computing (BigComp), Hong Kong, China, 18–20 January 2016. [Google Scholar]
- Macas, M.; Lagla, L.; Fuertes, W.; Guerrero, G.; Toulkeridis, T. Data Mining model in the discovery of trends and patterns of intruder attacks on the data network as a public-sector innovation. In Proceedings of the 2017 Fourth International Conference on eDemocracy & eGovernment (ICEDEG), Quito, Ecuador, 19–21 April 2017. [Google Scholar]
- Manuel, J.; Cordeiro, R.; Silva, C. Between Data Mining and Predictive Analytics Techniques to Cybersecurity Protection on eLearning Environments. Available online: https://link.springer.com/chapter/10.1007/978-3-319-67621-0_17 (accessed on 5 September 2017).
- Tisdale, S.M. Cybersecurity: Challenges from a Systems, Complexity, Knowledge Management and Business Intelligence Perspective. Issues Inf. Syst. 2015, 16, 191–198. [Google Scholar]
- Gabriel, R.; Hoppe, T.; Pastwa, A.; Sowa, S. Analyzing malware log data to support security information and event management: Some research results. In Proceedings of the First International Conference on Advances in Databases, Knowledge and Data Applications, DBKDA’09, Gosier, Guadeloupe, 1–6 March 2009. [Google Scholar]
- Harang, R.; Guarino, P. Clustering of Snort alerts to identify patterns and reduce analyst workload. In Proceedings of the Military Communications Conference, 2012-MILCOM 2012, Orlando, FL, USA, 29 October–1 November 2012. [Google Scholar]
- Hellwig, O.; Quirchmayr, G.; Huber, E.; Goluch, G.; Vock, F.; Pospisil, B. Major Challenges in Structuring and Institutionalizing CERT-Communication. In Proceedings of the 2016 11th International Conference on Availability, Reliability and Security (ARES), Salzburg, Austria, 31 August–2 September 2016; pp. 661–667. [Google Scholar]
- Bollinger, J.; Enright, B.; Valites, M. Crafting the InfoSec Playbook: Security Monitoring and Incident Response Master Plan; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2015; ISBN 9781491913598. [Google Scholar]
- Kruidhof, O. Evolution of National and Corporate CERTs-Trust, the Key Factor; IOS Press: Washington, DC, USA, 2014; pp. 81–96. [Google Scholar]
- Bhatt, S.; Manadhata, P.K.; Zomlot, L. The operational role of security information and event management systems. IEEE Secur. Priv. 2014, 12, 35–41. [Google Scholar] [CrossRef]
- Osorno, M.; Millar, T.; Rager, D. Coordinated Cybersecurity Incident Handling: Roles, Processes and Coordination Networks for Crosscutting Incidents; Laurel Md Applied Physics Lab.: Laurel, MD, USA, 2011. [Google Scholar]
- Qian, Y.; Fang, Y.; Jaatun, M.G.; Johnsen, S.O.; Gonzalez, J.J. Managing emerging information security risks during transitions to Integrated Operations. In Proceedings of the 2010 43rd Hawaii International Conference on System Sciences (HICSS), Honolulu, HI, USA, 5–8 January 2010; pp. 1–11. [Google Scholar]
- Belsis, M.A.; Simitsis, A.; Gritzalis, S. Workflow Based Security Incident Management. In Panhellenic Conference on Informatics; Springer: Berlin/Heidelberg, Germany, 2005; pp. 684–694. [Google Scholar]
- Elmellas, J. Knowledge is power: The evolution of threat intelligence. Comput. Fraud Secur. 2016, 7, 5–9. [Google Scholar] [CrossRef]
- Grobler, M.; Jacobs, P.; van Niekerk, B. Cyber Security Centres for Threat Detection and Mitigation. In Threat Mitigation and Detection of Cyber Warfare and Terrorism Activities; AISPE Book Series; IGI Global: Hershey, PA, USA, 2016; p. 21. [Google Scholar]
- Sharkov, G. From Cybersecurity to Collaborative Resiliency. In Proceedings of the 2016 ACM Workshop on Automated Decision Making for Active Cyber Defense, Vienna, Austria, 24–28 October 2016; pp. 3–9. [Google Scholar]
- Mejía, J.; Muñoz, M.; Ramírez, H.; Peña, A. Proposal of Content and Security Controls for a CSIRT Website. In New Advances in Information Systems and Technologies; Springer International Publishing: Basel, Switzerland, 2016; pp. 421–430. [Google Scholar]
- Wu, D.; Chen, S.H.; Olson, D.L. Business intelligence in risk management: Some recent progresses. Inf. Sci. 2014, 256, 1–7. [Google Scholar] [CrossRef]
- Gahi, Y.; Guennoun, M.; Mouftah, H.T. Big Data Analytics: Security and privacy challenges. In Proceedings of the 2016 IEEE Symposium on Computers and Communication (ISCC), Messina, Italy, 27–30 June 2016; pp. 952–957. [Google Scholar]
- Zuech, R.; Khoshgoftaar, T.M.; Wald, R. Intrusion detection and big heterogeneous data: A survey. J. Big Data 2015, 2, 3. [Google Scholar] [CrossRef]
- Mahmood, T.; Afzal, U. Security analytics: Big data analytics for cybersecurity: A review of trends, techniques and tools. In Proceedings of the Information Assurance (NCIA), Rawalpindi, Pakistan, 11–12 December 2013; pp. 129–134. [Google Scholar]
- Jaramillo, E.; Munier, M.; Aniorté, P. Information Security in Business Intelligence based on Cloud: A Survey of Key Issues and the Premises of a Proposal. In Proceedings of the 10th International Workshop on Security in Information Systems, Angers, France, 5 July 2013. [Google Scholar]
- Ahmad, A.; Hadgkiss, J.; Ruighaver, A.B. Incident response teams—Challenges in supporting the organizational security function. Comput. Secur. 2012, 31, 643–652. [Google Scholar] [CrossRef]
- Kimball, R.; Caserta, J. The Data Warehouse? ETL Toolkit: Practical Techniques for Extracting, Cleaning, Conforming, and Delivering Data. John Wiley & Sons: Indianapolis, IN, USA, 2011. [Google Scholar]
- Mohd, N.; Yunos, Z.; Ariffin, A.; Nor, A. CSIRT Management Workflow: Practical Guide for Critical Infrastructure Organizations. In Proceedings of the 10th European Conference on Information Systems Management, ECISM 2016, Evora, Portugal, 8–9 September 2016. [Google Scholar]
- Kimball, R.; Ross, M. The Data Warehouse Toolkit: The Definitive Guide to Dimensional Modeling; John Wiley & Sons: Hoboken, NJ, USA, 2013. [Google Scholar]
- Schieber, D.; Reid, G. CSIRT Case Classification (Example for Enterprise CSIRT); Technical Report; FIRST: Manchester, NH, USA, 2004. [Google Scholar]
- Roberts, L.D.; Howell, J.A.; Seaman, K. Give me a customizable dashboard: Personalized learning analytics dashboards in higher education. Technol. Knowl. Learn. 2017, 22, 317–333. [Google Scholar] [CrossRef]
- Bouman, R.; van Dongen, J. Pentaho Solutions: Business Intelligence and Data Warehousing with Pentaho and MySQL; Wiley Publishing: Hoboken, NJ, USA, 2009. [Google Scholar]
- Sugumaran, V.; Sangaiah, A.K.; Thangavelu, A. (Eds.) Computational Intelligence Applications in Business Intelligence and Big Data Analytics; CRC Press: Boca Raton, FL, USA, 2017. [Google Scholar]
- Mulder, S. An Action Research Study on the Use of SCRUM to Provide Agility in Data Warehouse Development. Ph.D. Thesis, University of Pretoria, Pretoria, South Africa, 2011. [Google Scholar]
- Goede, R. Agile Data Warehousing: The Suitability of SCRUM as Development Methodology. In Proceedings of the 5th IADIS Multi Conference on Computer Science and Information Systems, Rome, Italy, 24–26 July 2011; pp. 51–58. [Google Scholar]
- Scholtz, I.I. Inmon versus Kimball: The Agile Development of a Data Warehouse. Ph.D. Thesis, North-West University, Potchefstroom, 2016. [Google Scholar]
- Highsmith, J.; Alistair, C. Agile software development: The business of innovation. IEEE Comput. 2001, 34, 120–127. [Google Scholar] [CrossRef]
- Iqbal, M.H.; Soomro, T.R. Big data analysis: Apache storm perspective. Int. J. Comput. Trends Technol. 2015, 9–14. [Google Scholar] [CrossRef]
- Dayarathna, M.; Malshan, M.; Perera, S.; Jayasinghe, M. Scalable Complex Event Processing on a Notebook. In Proceedings of the 11th ACM International Conference on Distributed and Event-Based Systems, Barcelona, Spain, 19–23 June 2017; pp. 327–330. [Google Scholar]
- Gessert, F.; Wingerath, W.; Friedrich, S.; Ritter, N. NoSQL database systems: a survey and decision guidance. Comput. Sci. Res. Dev. 2017, 32, 353–365. [Google Scholar] [CrossRef]





© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fuertes, W.; Reyes, F.; Valladares, P.; Tapia, F.; Toulkeridis, T.; Pérez, E. An Integral Model to Provide Reactive and Proactive Services in an Academic CSIRT Based on Business Intelligence. Systems 2017, 5, 52. https://doi.org/10.3390/systems5040052
Fuertes W, Reyes F, Valladares P, Tapia F, Toulkeridis T, Pérez E. An Integral Model to Provide Reactive and Proactive Services in an Academic CSIRT Based on Business Intelligence. Systems. 2017; 5(4):52. https://doi.org/10.3390/systems5040052
Chicago/Turabian StyleFuertes, Walter, Francisco Reyes, Paúl Valladares, Freddy Tapia, Theofilos Toulkeridis, and Ernesto Pérez. 2017. "An Integral Model to Provide Reactive and Proactive Services in an Academic CSIRT Based on Business Intelligence" Systems 5, no. 4: 52. https://doi.org/10.3390/systems5040052





