Efficient Dynamic Integrity Verification for Big Data Supporting Users Revocability
Abstract
:1. Introduction
1.1. Related Work
1.2. Our Contributions
1.3. Paper Organization
2. Preliminaries
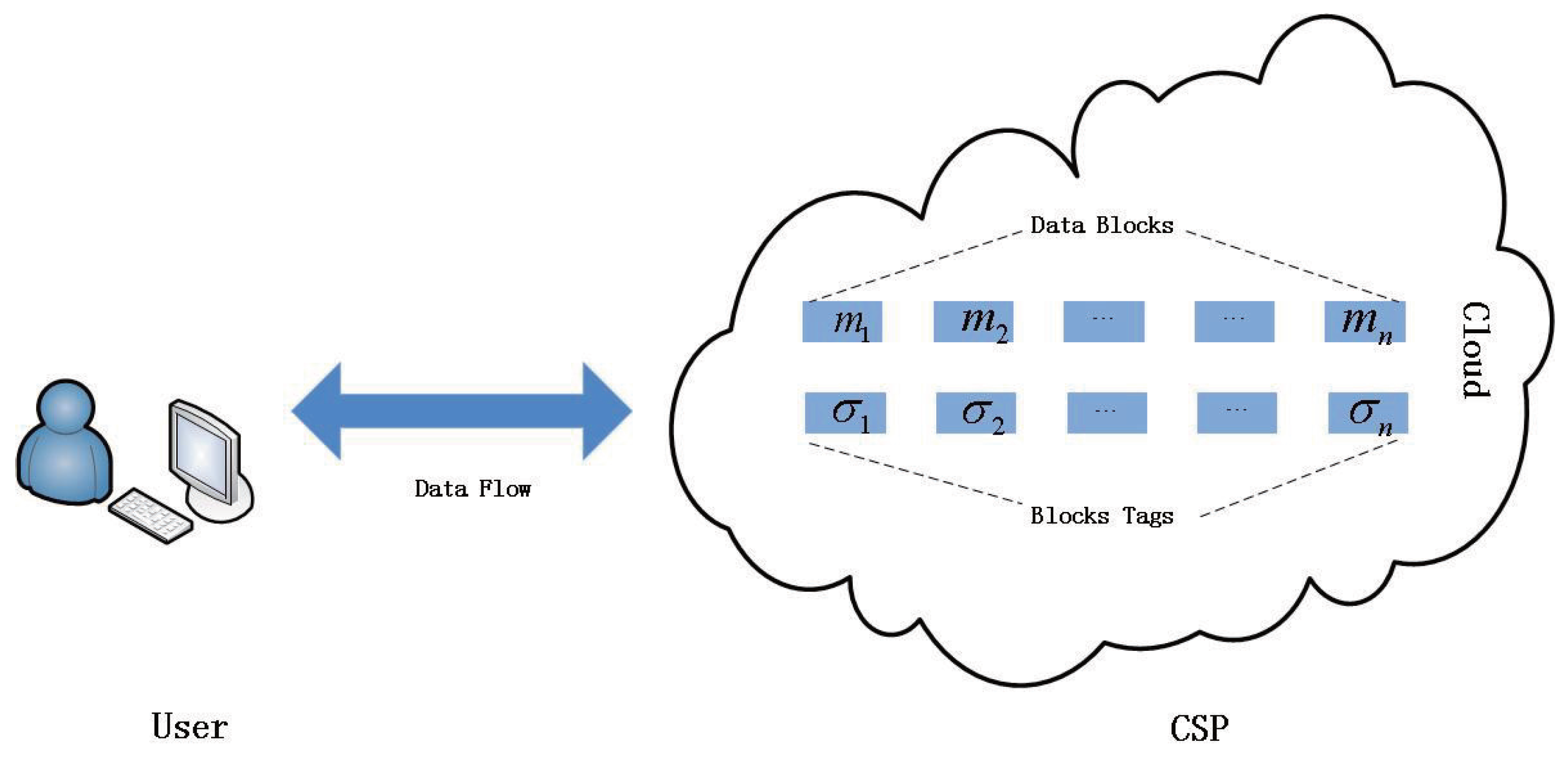
2.1. The User Data Stored in the Cloud
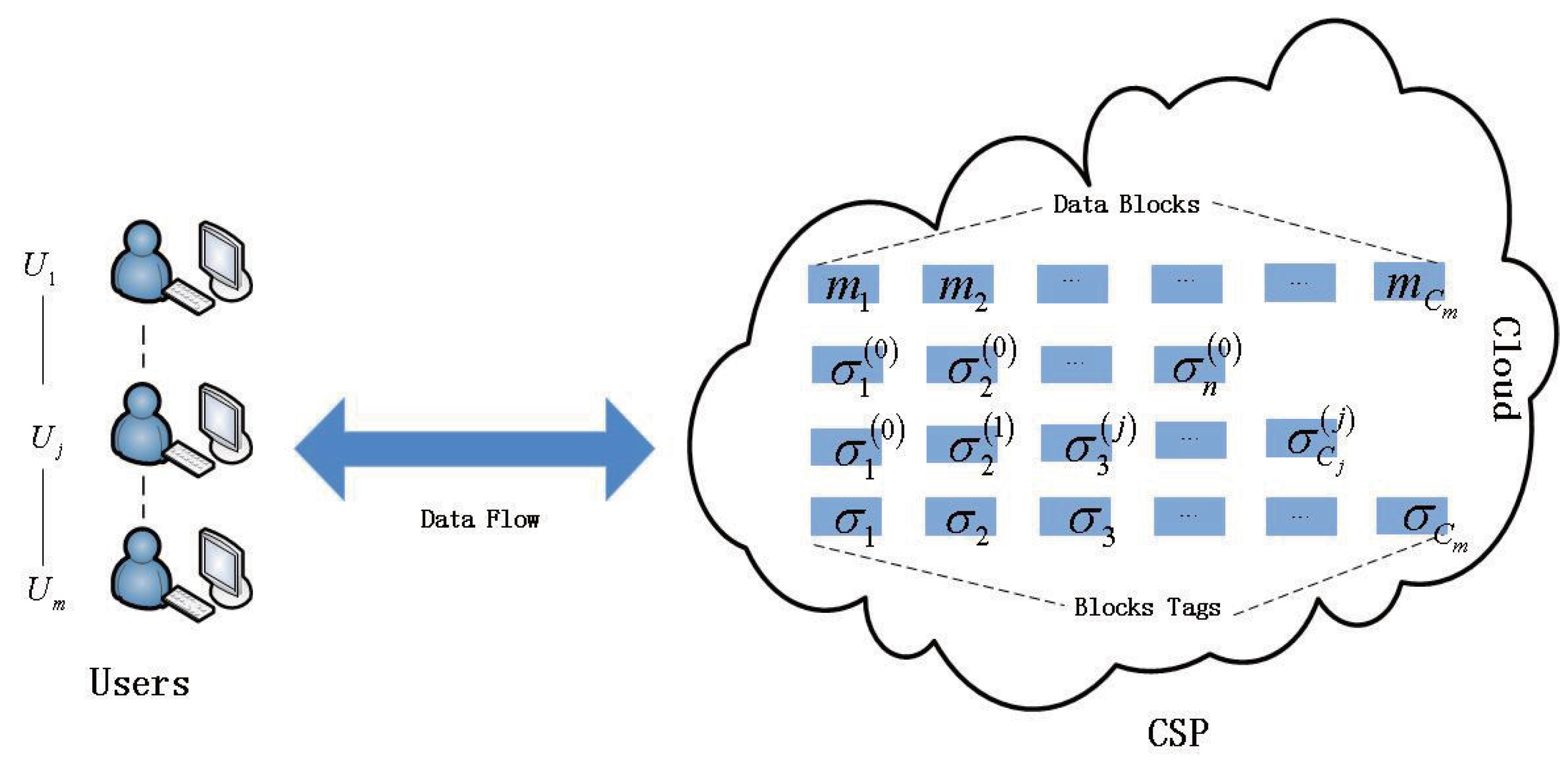
2.2. Multi-User Data Stored in the Cloud with the Revocable System
2.3. The Revocable Scheme Supported Third-Party Privacy-Preserving Auditing
3. Formalization and Definitions
3.1. Definition 1: Revocable Third-Party Privacy-Preserving Auditing Scheme for Cloud Storage
3.2. Definition 2: Security Model
- ;
- The data block m is not the original one.
3.3. Design Goals
- (i)
- TPA is allowed to verify the correctness of the cloud data. It executes data auditing without retrieving entire data and introduces none additional online burden to the user.
- (ii)
- Storage correctness: If the cloud indeed stores entire data, then it would always output valid proofs.
- (iii)
- Privacy-preserving: TPA learns no information of the stored data from information collected during the auditing process.
- (iv)
- Revocability: If a user is revoked, then its successor could establish a new auditing procedure efficiently.
- (v)
- Collusion resistance: If the data stored in the cloud is changed, then the auditing scheme should be able to detect it with high probability even though the cloud colludes with revoked users.
- (vi)
- Efficiency: the computation, communication and storage overhead should be as small as possible.
4. The Revocable Third-Party Privacy-Preserving Auditing Scheme for Cloud Storage
4.1. Bilinear Map
- 1.
- Bilinearity: For all , and , we have .
- 2.
- Non-degeneracy: .
- 3.
- Computability: There exists an efficient algorithm to compute the map e.
- 4.
- Exchangeability:
4.2. Hardness Assumptions
4.3. Specification
- 1.
- Select a random .
- 2.
- Compute its public key .
- 3.
- Output and .
- 1.
- The initial user encodes all the files and then splits them into n block such that each block is in , i.e., .
- 2.
- For all , compute the tag of data block as , , where u is a public parameter chosen randomly from G, and .
- 3.
- Send the initial verification metadata and the data blocks to the cloud and then deletes them locally.
- 1.
- The data blocks is processed as by current user , where is a positive integer. The increment of the data block by the operations denoted by , which user will add these data to the cloud in the period .
- 2.
- For all , compute the tag of data block as , , where u is a public parameter chosen randomly from G, and . Send the verification metadata and data blocks to the cloud and then deletes them locally.
- 1.
- When the current user wants to update the data in the previous period for some reason, the and should be retrieved firstly.
- 2.
- Then the user verified the with the previous user public key. If wrong the auditing scheme ends, if right the user deals with the data block as and replaced the tag by At the same time the user replaced the by .
- 3.
- At last the user sends verification metadata and the block to the cloud and then deletes them locally.
- 1.
- Set , .
- 2.
- For any , let the verification metadata of block data associated with user be .
5. Analysis of the Proposed Auditing Scheme
5.1. Correctness
5.2. Security Analysis
6. Performance Analysis
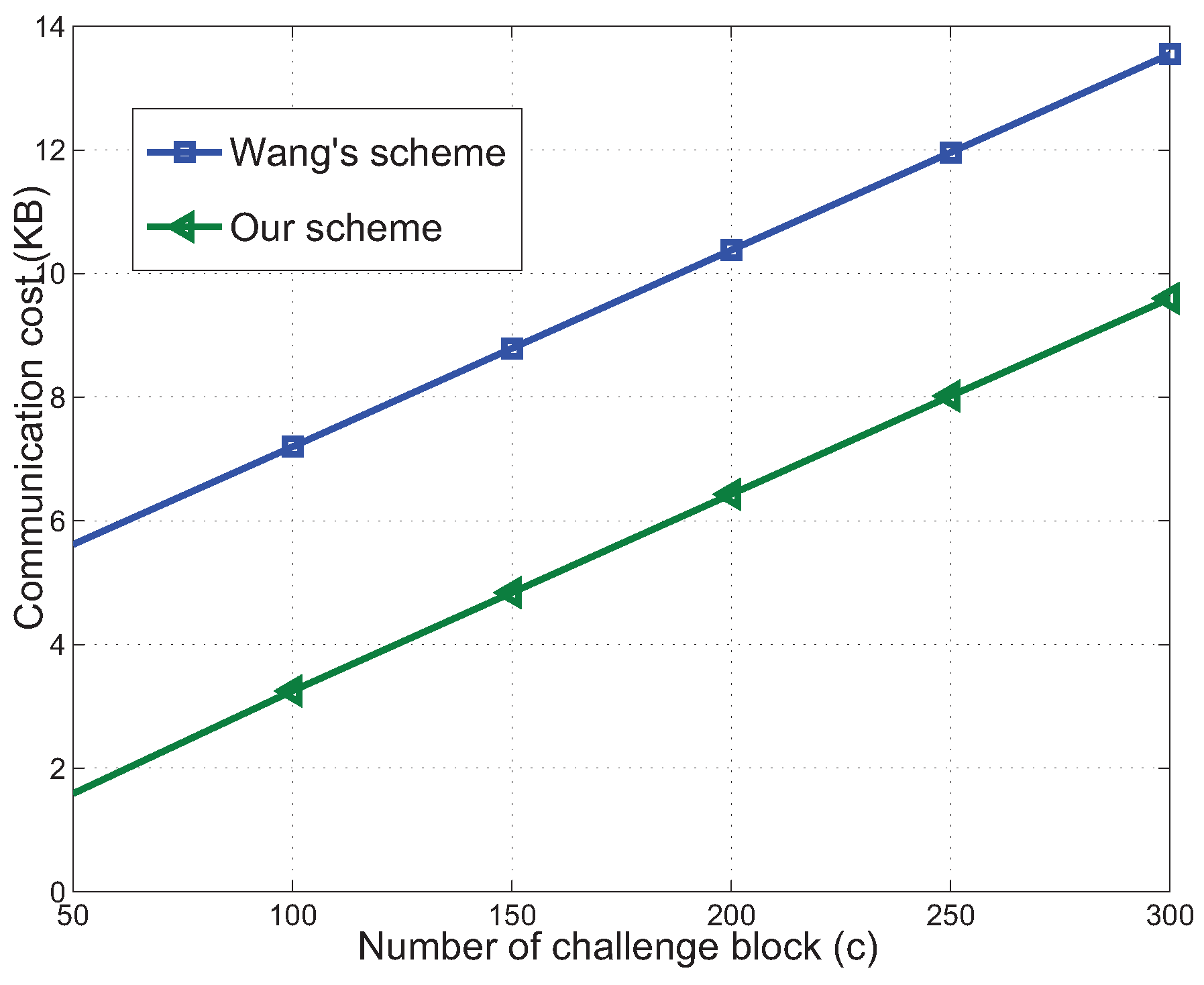
6.1. Communication Cost
6.2. Computation Cost
6.3. Experimental Results
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- 9 worst cloud security threats. Available online: http://www.informationweek.com/byte/cloud/infrastructure-as-a-service/9-worst-cloud-security-threats/d/d-id/1114085 (accessed on 25 May 2016).
- Cloud Security Alliance. Top Hreats to Cloud Computing. Available online: http://www.cloudsecurityalliance.org (accessed on 25 May 2016).
- Kincaid, J. Mediamax/Helinkup Close Its Doors. Available online: http://techcrunch.com/2008/07/10/mediamaxthelinkup-closes-its-doors/ (accessed on 25 May 2016).
- Cloud Computing Users Are Losing Data, Symantec Finds. Available online: http://news.investors.com/technology/011613-640851-cloud-computing-data-loss-high-in-symantec-study.htm (accessed on 25 May 2016).
- Kher, V.; Kim, Y. Securing distributed storage: Challenges, techniques, and systems. In Proceedings of the 2005 ACM Workshop on Storage Security and Survivability, Fairfax, VA, USA, 11 November 2005; pp. 9–25.
- Schroeder, B.; Gibson, G.A. Disk failures in the real world: What does an mttf of 1, 000, 000 hours mean to you? In Proceedings of the FAST ’07: 5th USENIX Conference on File and Storage Technologies, San Jose, CA, USA, 14–16 Februery 2007; Volume 7, pp. 1–16.
- Cloud Security Alliance. Cloud computing vulnerability incidents: a statistical overview. Available online: http://www.cert.uy/wps/wcm/connect/975494804fdf89eaabbdab1805790cc9/CloudComputing-Vulnerability-Incidents.pdf/?MOD=AJPERES (accessed on 25 May 2016).
- Yu, S.; Wang, C.; Ren, K.; Lou, W. Achieving secure, scalable, and fine-grained data access control in cloud computing. In Proceedings of the 2010 Proceedings IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–9.
- Wang, C.; Chow, S.S.M.; Wang, Q.; Ren, K.; Lou, W. Privacy-preserving public auditing for secure cloud storage. IEEE Trans. Comput. 2013, 62, 362–375. [Google Scholar] [CrossRef]
- Wang, Q.; Wang, C.; Li, J.; Ren, K.; Lou, W. Enabling public verifiability and data dynamics for storage security in cloud computing. In Computer Security—ESORICS 2009; Springer: Medford, MA, USA, 2009; pp. 355–370. [Google Scholar]
- Ateniese, G.; Burns, R.; Curtmola, R.; Herring, J.; Kissner, L.; Peterson, Z.; Song, D. Provable data possession at untrusted stores. In Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 29 October–2 November 2007; pp. 598–609.
- Juels, A.; Kaliski, B.S., Jr. Pors: Proofs of retrievability for large files. In Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 29 October–2 November 2007; pp. 584–597.
- Shacham, H.; Waters, B. Compact proofs of retrievability. In Advances in Cryptology-ASIACRYPT 2008; Springer: Medford, MA, USA, 2008; pp. 90–107. [Google Scholar]
- Li, M.; Yu, S.; Ren, K.; Lou, W. Securing personal health records in cloud computing: Patient-centric and fine-grained data access control in multi-owner settings. In Security and Privacy in Communication Networks; Springer: Medford, MA, USA, 2010; pp. 89–106. [Google Scholar]
- Zhang, X.; Xu, C.; Zhang, X. Efficient pairing-free privacy-preserving auditing scheme for cloud storage in distributed sensor networks. Int. J. Distrib. Sens. Netw. 2015, 501, 593759. [Google Scholar] [CrossRef]
- Wang, B.; Li, B.; Li, H. Panda: Public auditing for shared data with efficient user revocation in the cloud. IEEE Trans. Serv. Comput. 2015, 8, 92–106. [Google Scholar] [CrossRef]
- Wang, B.; Li, H.; Li, M. Privacy-preserving public auditing for shared cloud data supporting group dynamics. In Proceedings of the 2013 IEEE International Conference on Communications (ICC), Budapest, Hungary, 9–13 June 2013; pp. 1946–1950.
- Yuan, J.; Yu, S. Efficient public integrity checking for cloud data sharing with multi-user modification. In Proceedings of the IEEE Conference on Computer Communications (INFOCOM), Toronto, ON, Canada, 27 April–2 May 2014; pp. 2121–2129.
- Delerablée, C.; Paillier, P.; Pointcheval, D. Fully collusion secure dynamic broadcast encryption with constant-size ciphertexts or decryption keys. In Pairing-Based Cryptography—Pairing 2007; Springer: Medford, MA, USA, 2007; pp. 39–59. [Google Scholar]
- Chaum, D.; Van Heyst, E. Group signatures. In Advances in Cryptology EUROCRYPT 91; Springer: Medford, MA, USA, 1991; pp. 257–265. [Google Scholar]
- Wang, B.; Li, B.; Li, H. Knox: Privacy-preserving auditing for shared data with large groups in the cloud. In Applied Cryptography and Network Security; Springer: Medford, MA, USA, 2012; pp. 507–525. [Google Scholar]
- Ateniese, G.; Hohenberger, S. Proxy re-signatures: New definitions, algorithms, and applications. In Proceedings of the 12th ACM conference on Computer and Communications Security, Alexandria, VA, USA, 7–10 November 2005; pp. 310–319.
- Liu, Q.; Wang, G.; Wu, J. Efficient sharing of secure cloud storage services. In Proceedings of the 2010 IEEE 10th International Conference on Computer and Information Technology (CIT), Bradford, UK, 29 June–1 July 2010; pp. 922–929.
- Liu, Q.; Wang, G.; Wu, J. Time-based proxy re-encryption scheme for secure data sharing in a cloud environment. Inf. Sci. 2014, 258, 355–370. [Google Scholar] [CrossRef]



| Repression | |
|---|---|
| n | the number of the initial data block; |
| the period of data manager’s management; | |
| the current period is correspondence the current user ; | |
| C | the number of the total data blocks at the auditing time: |
| where ; | |
| the of blocks at the end of period ; | |
| the increment of the data block at the end of period ; | |
| the increment of the data block by the operation during the period ; | |
| the tag is generated by the and data block ; | |
| Q | the set of index-coefficient pairs, i.e., ; |
| t | it used to verify if the block i-th match the data block; |
| V | the response for the challenge Q; |
| Scheme | Communication Cost | Computation Cost | Collusion Resistance | |
|---|---|---|---|---|
| Update Time | Audit Time | |||
| [16] | NO | |||
| Our scheme | YES | |||
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, X.; Xu, C.; Zhang, X.; Gu, T.; Geng, Z.; Liu, G. Efficient Dynamic Integrity Verification for Big Data Supporting Users Revocability. Information 2016, 7, 31. https://doi.org/10.3390/info7020031
Zhang X, Xu C, Zhang X, Gu T, Geng Z, Liu G. Efficient Dynamic Integrity Verification for Big Data Supporting Users Revocability. Information. 2016; 7(2):31. https://doi.org/10.3390/info7020031
Chicago/Turabian StyleZhang, Xinpeng, Chunxiang Xu, Xiaojun Zhang, Taizong Gu, Zhi Geng, and Guoping Liu. 2016. "Efficient Dynamic Integrity Verification for Big Data Supporting Users Revocability" Information 7, no. 2: 31. https://doi.org/10.3390/info7020031





