Abstract
With the rapid development of cloud computing, it is playing an increasingly important role in data sharing. Meanwhile, attribute-based encryption (ABE) has been an effective way to share data securely in cloud computing. In real circumstances, there is often a mutual access sub-policy in different providers’ access policies, and the significance of each attribute is usual diverse. In this paper, a secure and efficient data-sharing scheme in cloud computing, which is called unified ciphertext-policy weighted attribute-based encryption (UCP-WABE), is proposed. The weighted attribute authority assigns weights to attributes depending on their importance. The mutual information extractor extracts the mutual access sub-policy and generates the mutual information. Thus, UCP-WABE lowers the total encryption time cost of multiple providers. We prove that UCP-WABE is selectively secure on the basis of the security of ciphertext-policy weighted attribute-based encryption (CP-WABE). Additionally, the results of the implementation shows that UCP-WABE is efficient in terms of time.
1. Introduction
As one of the most promising applications, cloud computing [1,2,3] provides a more efficient way for data sharing. It enables data providers to store their data remotely in a cloud, and once data consumers can access the cloud, they can access the data any time and anywhere. Despite cloud computing supplying great convenience for data sharing, it also brings the serious challenge of information security [4]. Massive data are stored in the cloud storage platforms, and the data often contain sensitive information, such as personal health records in the medical cloud [5,6,7] and banking transactions in the financial cloud [8,9,10]. An untrustworthy entity named the cloud service provider (CSP) runs the cloud storage platforms, and it may steal the sensitive information to make a profit. Therefore, how to enforce a secure and efficient data sharing in the cloud has attracted many scholars’ attention [11,12,13,14].
Attribute-based encryption (ABE) [15] is a widespread cryptographic technology to protect the security of data in cloud computing. Different from traditional public key encryption, ABE does not encrypt plaintexts for an explicit consumer. Consumers’ secret keys and ciphertexts are associated with a set of attributes or an access policy, respectively. A consumer can decrypt a ciphertext if and only if his/her secret key has a match with the ciphertext. Weighted attribute-based encryption [16,17,18,19,20,21] is a variant of ABE. It assigns different weights to attributes according to their importance. For example, we can give full professor and distinguished professor with weights one and two, denoted as “professor(1)” and “professor(2)”, respectively. This can avoid a very complicated access structure and improve the efficiency of the encryption in certain scenarios.
1.1. Problem Statement
In practical applications [7,22], different data providers share their own data with weighted access policies, and these policies may have a mutual sub-policy. A simple instance is given to elucidate this issue.
As illustrated in Figure 1, the data providers have data and to share separately. The weighted access policy of is {Attr3(3) AND (Attr1(2) AND Attr2(3))}. The weighted access policy of is {Attr4(2) AND (Attr1(2) AND Attr2(3))}. We notice that there is a mutual sub-policy {Attr1(2) AND Attr2(3)} between and , and this means that the encryptions of and have some processes of repetition. This provides the possibility of improving the efficiency of the data sharing.
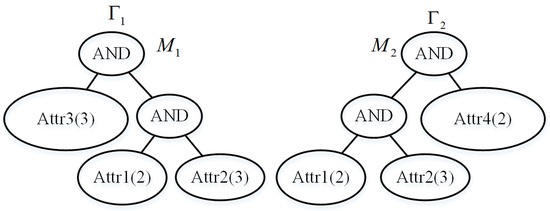
Figure 1.
Two data providers have data and to share separately. and are the weighted access policies of and .
1.2. Our Contributions
In this paper, we propose a new data-sharing scheme, which is called unified ciphertext-policy weighted attribute-based encryption (UCP-WABE), in cloud computing. UCP-WABE achieves both security and high performance. In this scheme, every attribute has its own weight depending on its importance defined in the system. The data providers share their data under their weighted access policies. When there is a mutual sub-policy among the weighted access policies, UCP-WABE optimizes the encryption of the data. UCP-WABE is proven to be selectively secure [23] on the basis of CP-WABE [16]. We carry out experiments for UCP-WABE, and the implementation results exhibit that UCP-WABE has better efficiency.
1.3. Organization
The rest of this paper is arranged as follows. Section 2 describes related work. Section 3 introduces preliminaries. In Section 4, we present the system model and security model of UCP-WABE. Section 5 proposes our data-sharing scheme. Section 6 represents the security analysis of UCP-WABE. The implementation results are presented in Section 7. Finally, the conclusions are stated in Section 8.
2. Related Work
As a popular cryptographic primitive used in cloud computing, ABE has two categories. One is ciphertext-policy ABE (CP-ABE) [24], and the other is key-policy ABE (KP-ABE) [25]. The major difference between CP-ABE and KP-ABE is the relationship of the ciphertext and secret key with the access policy and attributes. Specifically, for the former, a ciphertext is associated with an access policy that is expressed by threshold gates and attributes. A consumer’s secret key has attributes embedded. For the latter, a ciphertext is associated with attributes, and an access policy is embedded into a consumer’s secret key. CP-ABE enables data providers to construct its access policy freely; in other words, the providers describe who can get the shared data flexibly. Therefore, CP-ABE is more suitable for data sharing in the cloud.
In order to increase the efficiency and enlarge the use scope of ABE for data sharing, many researchers have made great efforts. Liu et al. [17] introduced the concept of weight into CP-ABE and proposed a ciphertext-policy weighted attribute-based encryption scheme. In this scheme, the authority transforms the attribute set into the weight attribute separation set, then the data provider encrypts the data with linear secret sharing methods [26]. Although the size of the ciphertext and private key increases, the scheme achieves fine-grained access control and reflects the significance of attributes. Therefore, the scheme is more suitable for the practical applications. However, the scheme only supports the linear secret sharing scheme (LSSS) [27] access structure. On the basis of [17], Liu et al. [18] proposed another ciphertext-policy weighted attribute-based encryption scheme that supports threshold access structure [28]. This structure can consist of a threshold and many attributes. Therefore, this scheme is more expressive and is more appropriate for the cloud computing environment. Meanwhile, the scheme is proven secure under the selective-weighted attribute model. Nevertheless, the scheme only supports the threshold access structure, which only contains one threshold gate in one structure, and this still limits the expression. Wang et al. [19] proposed a multi-authority-based weighted attribute encryption scheme, which introduced the concept of weight into multi-authority-based attribute encryption [29]. In this scheme, a central authority assigns a unique user identifier (UID) to each consumer. The UID is the global identity of a consumer in the system, and it is used to generate the attribute secret keys issued by multiple authorities. The attribute authorities assign different weights to attributes depending on their importance; whereas, the scheme only supports the threshold access structure. Liu et al. [16] proposed an improved ciphertext-policy weighted attribute-based encryption (CP-WABE) to improve the efficiency over the traditional CP-ABE scheme. In this scheme, every attribute has its own weight according to its importance. The data provider encrypts its data under a weighted access policy. The data consumer can decrypt the ciphertext only if his/her attributes satisfy the weighted access policy. The scheme supports the tree access structure, so it can encrypt data under a more complex access policy. The scheme is proven to be secure under the decision ℓ-Expanded bilinear Diffie–Hellmann exponent (ℓ-Expanded BDHE) assumption [30]. Ghosh et al. [21] proposed a secure and efficient data collaboration scheme, which is called blowfish hybridized weighted attribute-based encryption. In this scheme, The weight is assigned to each attribute based on its importance, and data are encrypted using access control policies. The consumers can access the data corresponding to their weight in order to reduce the computational overload. Nevertheless, when there is a mutual sub-policy among the access policies of providers, all above-mentioned schemes do not consider further optimization.
3. Preliminaries
In this section, we introduce the basic concepts of bilinear mapping [31] and the weighted access tree [16].
3.1. Bilinear Mapping
Let and be two cyclic groups of prime order p with the multiplication. Let g be a generator of and be a bilinear mapping. Let : be a bilinear mapping having the following properties:
- Bilinearity: For any and , is the set of integers . It has .
- Non-degeneracy: .
- Computability: For all , there is an efficient computation .
Note that is symmetric since .
3.2. Weighted Access Tree
A weighted access tree is an image representation of a weighted access policy. Let be a weighted access tree. Let be the nodes of and be the root of . There are two kinds of nodes in , non-leaf node and leaf node. The former represents a threshold gate, for example “AND”, “OR”, “a of b ”. and describe the threshold gate, where denotes the number of children of and denotes the threshold value, . When , the threshold gate is an AND gate, and when , it is an OR gate. A leaf node is described by a data consumer’s attribute with weight, and . We denote the parent of by and denote the index for in its parent’s children by , where .
In , every non-leaf node corresponds to a function . is a Boolean function, and it is TRUE if has at least child nodes whose Boolean functions are evaluated to be TRUE. We say that a data consumer’s attribute set satisfies if TRUE, which is defined as described below.
For any leaf node that is associated with an attribute , if its Boolean value is TRUE, the weight of from must be greater than or equal to the weight of . For any non-leaf node, its Boolean value is the value of its Boolean function. If and only if the tree’s root node’s Boolean value is TRUE, then = TRUE.
For instance, as shown in Figure 1, two weighted access trees correspond to two weighted access policies. : {Attr3(3) AND (Attr1(2) AND Attr2(3))}, : {Attr4(2) AND (Attr1(2) AND Attr2(3))}. Considering a data consumer whose attribute set is {Attr1(3), Attr2(3), Attr3(4), Attr4(1)}. We could calculate that = TRUE, = FALSE. Table 1 gives several outcomes of with different attribute sets .

Table 1.
Valuation of the weighted access trees in Figure 1.
4. System Model and Security Model of UCP-WABE
In this section, we describe the system model and security model of UCP-WABE. The system model shows how UCP-WABE enforces data sharing in cloud computing. The security model makes a foundation for the security analysis in Section 6.
4.1. System Model of UCP-WABE
Figure 2 displays the data-sharing system using UCP-WABE in the cloud environment. This system model is improved from the system model of CP-WABE [16]. The system model consists of five types of entities: a weighted attribute authority (WAA), a mutual information extractor (MIE), a cloud storage platform, numerous data providers, and data consumers. The cloud storage platform is managed by CSP and offers data storage service due to its massive storage ability. The provider’s data are encrypted with its weighted access policy and uploaded to the cloud. The data consumer downloads the ciphertexts and decrypts them with his/her secret key to recover the data. All providers and consumers are supervised by WAA. WAA is responsible for authenticating the attributes of every data consumer. WAA also assigns different weights to attributes according to their importance. The MIE assists the providers in encrypting their data. For illustration, we consider two providers in the system.
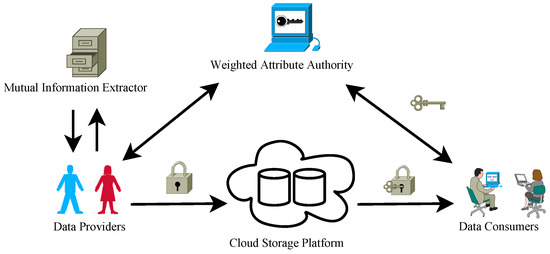
Figure 2.
System model of UCP-WABE.
In Figure 2, WAA is a trustworthy entity that is in charge of producing the data consumers’ secret keys. CSP is honest but curious. This means that the cloud implements the manipulations dutifully and gives true outcomes; whereas, it also tries its best to get sensitive information. A data consumer could be compromised by an adversary; thus, this consumer could make attempts at obtaining data beyond his/her access range. The communication channels among the providers, the consumers, as well as the cloud are unsafe. In other words, the data in these channels could be eavesdropped by the adversary.
4.2. Security Model of UCP-WABE
The security model of UCP-WABE is described by a selective security game between a challenger and an adversary. This game is borrowed from CP-WABE [16]. The phases of the game are the following:
Init: The adversary declares the challenge weighted access policy that he/she will try to attack and sends to the challenger.
Setup: Here, the challenger calls the Setup algorithm to generate and send the public parameters to the adversary.
Phase 1: In this phase, the adversary can adaptively query for secret keys for the weighted attribute sets to the challenger. The challenge weighted access policy must not be satisfied by any one of the queried attribute sets. The challenger responds by running the KeyGen algorithm to generate the corresponding secret keys .
Challenge: The adversary submits two messages of the same length . Then, the adversary makes a weighted access policy that there is a mutual access sub-policy between and . is sent to the challenger, as well. The challenger flips a random coin and encrypts under . The ciphertext is given to the adversary.
Phase 2: This phase is the same as Phase 1. The adversary asks for more secret keys, and the same restriction is that must not be satisfied by any one of the queried attribute sets.
Guess: The adversary outputs his/her guess on b.
Definition 1.
A UCP-WABE scheme is selectively secure if all polynomial time adversaries have at most a negligible advantage in the above security game, where the advantage of an adversary is defined as [32].
According to this definition, if we prove that there is no such polynomial time adversary who has a non-negligible advantage in the above security game, we can prove that UCP-WABE is selectively secure. The details of the proof will be described in Section 6.1.
5. Proposed Unified Ciphertext-Policy Weighted Attribute-Based Encryption
This section first gives an overview of our scheme. Then, we articulate the proposed UCP-WABE data-sharing scheme, which consists of five algorithms.
5.1. Overview of UCP-WABE
In UCP-WABE, different providers’ weighted access trees can be merged into one if and only if the trees meet two conditions. One is that there is a mutual sub-policy between the weighted access trees. The other is that the sub-trees’ roots of every weighted access tree locate in a trunk. A merging process is displayed in Figure 3. The two weighted access policies belong to different providers and have a mutual sub-policy: {Attr3(3) AND (Attr1(2) OR Attr2(3))}. All roots of the left weighted access tree are in the trunk: “AND”–“AND”–“OR”. All roots of the right weighted access tree are in the trunk: “OR”–“AND”–“OR”. Therefore, the two conditions are met, and the weighted access trees can be merged. The structure of the new weighted access tree is a multi-root tree.
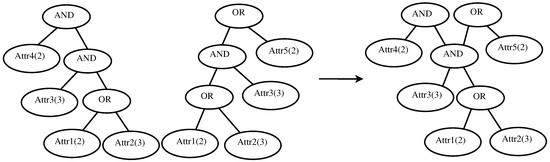
Figure 3.
The merging process of two weighted access trees.
5.2. The Design of UCP-WABE
UCP-WABE can be described as a collection of the following five algorithms:
Setup(). This algorithm generates the public parameters () and the master secret key (). WAA runs Setup, which takes a security parameter and the set of all attributes in the system as input. Each attribute has a weight depending on its importance in the system, and let be the maximum weight of attribute , where .
WAA chooses a group of prime order p with generator g and random group elements . WAA also chooses a random exponent and computes as:
The master key of the system MSK can be calculated as:
PP is released to all the data providers and data consumers.
MutualInfoGen(). In [24], the cpabe toolkit [33] can transform an access policy into a stylized expression. Therefore, MIE is able to extract the mutual sub-policy when providers’ access policies meet the two conditions. Then, MIE creates an access tree according to the mutual sub-policy. Let denote the set of the leaf nodes in . Each element of represents an attribute (denoted by ) with a weight (denoted by ). The number of leaf nodes is denoted by . . Let denote the jth part of , where . MIE chooses a polynomial for every node of . Let the polynomial degree , as follows:
where denotes the polynomial coefficient. Moreover, let denote the root of . MIE picks a random quantity and randomly chooses other points of to determine . MIE selects for the non-root node of , where:
MIE randomly picks the other points to determine . Therefore, it can get the polynomials for any .
MIE chooses random values , and creates the mutual information as follows:
, MIE first calculates:
Then, for to , MIE calculates:
When , let , where is the polynomial of the node whose attribute is . MIE calculates:
Then, MIE calculates:
Finally, MIE creates the mutual information :
Algorithm 1 shows the pseudocode of the MutualInfoGen algorithm.
| Algorithm 1 The mutual information generation algorithm (MutualInfoGen). |
| Input:: The public parameter. : The weighted access tree of Provider A. : The weighted access tree of Provider B. Output:: The mutual information. 1: Create according to the mutual sub-policy of and 2: Select a random ; set ; and randomly choose other points to determine 3: for ∀ non-root node do 4: Calculate , and randomly choose other points to determine 5: if then 6: Calculate 7: for to do 8: if then 9: Calculate 10: else 11: Set , and calculate 12: end if 13: end for 14: Calculate 15: end if 16: end for 17: |
Encrypt(). MIE sends to the providers. Then, they encrypt the messages , respectively. Consider Provider A as an instance. It runs Encrypt as follows. Provider A creates the access tree based on , which is a sub-tree of . For any trunk node above in , the polynomial is determined as follows.
where denotes the child node of along the trunk and is the index value of to its parent node. In order to calculate conveniently, when providers construct the access policies, it sets for each trunk node. For non-constant coefficients of (3), Provider A selects them randomly. Then, the constant term can be computed by (10). Taking a simple instance, let be the parent of . Provider A needs to determine:
Provider A selects coefficients randomly, and . Due to (10), Provider A knows that:
then it calculates the constant term with (3), as:
Similarly, MIE determines every trunk node’s polynomial. For any other node of , the method of determining is identical to the method of MIE creating .
Provider A obtains every polynomial of node in with (4) and (10), and is created completely. Provider B creates based on likewise.
Let denote the set of the leaf nodes in . The number of leaf nodes is denoted by . Provider A produces the ciphertext of message as follows:
Provider A first calculates , where is the polynomial of access tree ’s root node . For , Provider A chooses random values , and calculates:
Then, for to , MIE calculates:
When , let , where is the polynomial of the node whose attribute is . MIE calculates:
Then, MIE calculates:
Finally, Provider A creates the ciphertext :
Algorithm 2 represents the pseudocode of Encrypt algorithm.
KeyGen(). WAA calls this algorithm to produce on the basis of and the data consumer’s attributes. Particularly, , let denote the weight of , and let denote the jth part of , where . For each , WAA chooses and randomly. WAA also chooses random values . WAA generates components as follows:
| Algorithm 2 The encryption algorithm (Encrypt). |
| Input:: The public parameter. : The data that Provider A wants to share. : The weighted access tree of Provider A. : The mutual information. Output:: The ciphertext of . 1: Create based on 2: for ∀ trunk node above do 3: Calculate ; select non-constant coefficients randomly; and calculate 4: if then 5: Calculate 6: end if 7: end for 8: for ∀ non-trunk node do 9: Determine the same as MutualInfoGen 10: if then 11: Calculate 12: for to do 13: if then 14: Calculate 15: else 16: Set , and calculate 17: end if 18: end for 19: Calculate 20: end if 21: end for 22: |
Then, WAA outputs:
Decrypt(). Consider that the aforementioned consumer gets , and he/she wants to recover . The decryption process is defined as follows.
If is a leaf node of and is associated with attribute and , let ’s Boolean value be TRUE, and calculate:
Then, for to :
When to ,
When ,
Finally, the consumer computes:
is the attribute of leaf node , so , and:
Equations (22) and (24)–(26) are on the basis of bilinear mapping properties, which were introduced in Section 3.1. If or , then , and ⊥ is a termination signal.
For a non-leaf node of , let be the children of and be an arbitrary -size set of , where . If does not exist, set , or else, ’s Boolean value is TRUE, then compute:
where is the Lagrange coefficient polynomial.
Therefore, if the access tree is satisfied by , the decryption algorithm begins from the root node , and the consumer calculates:
Algorithm 3 displays the pseudocode of Decrypt algorithm.
Figure 4 shows the working process of UCP-WABE for unified encryption. Figure 5 displays the process flow of a consumer for decryption.
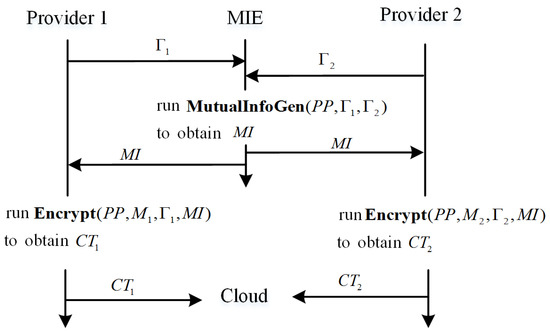
Figure 4.
The process flow of unified encryption.
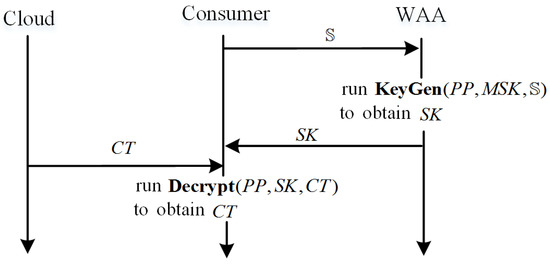
Figure 5.
The process flow of decryption.
| Algorithm 3 The decryption algorithm (Decrypt). |
| Input:: The public parameter. : The secret key of the consumer. : The ciphertext of . Output:: The plaintext of . 1: for ∀ leaf node do 2: if attribute of , and then 3: Set ’s Boolean value to be TRUE, and calculate 4: for to do 5: if then 6: Calculate 7: else 8: Calculate 9: end if 10: end for 11: Calculate 12: else 13: Set 14: end if 15: end for 16: for ∀ non-leaf node do 17: Set as the children of and as an arbitrary -size set of , where . 18: if then 19: Set 20: else 21: Set ’s Boolean value to be TRUE, and calculate 22: end if 23: end for 24: if ’s Boolean value is TRUE then 25: Calculate 26: end if 27: |
6. Security Analysis
6.1. Security Proof
Extended from CP-WABE, UCP-WABE is expected to have the same security property as CP-WABE, which has been proven to be selectively secure under a variant of the decision ℓ-bilinear Diffie-Hellmann exponent (BDHE) assumption [16]. Based on the selective security of CP-WABE, we prove UCP-WABE is selectively secure.
Theorem 1.
If no polynomial time adversary can selectively break CP-WABE with a weighted challenge access policy , no polynomial time adversary can selectively break UCP-WABE with .
Proof.
To prove the theorem, we assume that there exists a polynomial time adversary , which has a non-negligible advantage in selectively breaking UCP-WABE. Using , we will build a polynomial time adversary , which selectively breaks CP-WABE with a non-negligible advantage .
Init: declares a challenge weighted access policy and sends it to . sends to the CP-WABE challenger.
Setup: The public parameter of CP-WABE = is sent to , then sends to .
Phase 1: makes secret key queries to for attribute sets, and none of these sets satisfy the challenge access policy . Suppose asks for attribute set . gives to the CP-WABE challenger and gets . returns to to answer the query. This process would repeat until no longer queries.
Challenge: submits two messages of the same length . Then, constructs a weighted access policy that there is a mutual access sub-policy between and . is also sent to . sends to the CP-WABE challenger. The CP-WABE challenger flips a random coin and encrypts with . The ciphertext is , and the CP-WABE challenger sends it to . constructs challenge ciphertext as and returns it to .
Phase 2: asks for more secret keys, and the same restriction is that must not be satisfied by any one of the queried attribute sets. answers as in Phase 1.
Guess: outputs its guess , and outputs in its own game. has an advantage in breaking CP-WABE as
Thus, has a non-negligible advantage in selectively breaking CP-WABE, so the proof of the theorem is completed. □
6.2. Discussion
In UCP-WABE, CSP cannot know the details of the data because the data are stored in an encrypted form. The data are encrypted under a weighted access policy, so only the consumers who possess a set of weighted attributes satisfying the policy can decrypt the ciphertext. Hence, UCP-WABE achieves a fine-grained access control, and the confidentiality of the data can be guaranteed against unauthorized consumers. A data provider constructs the weighted access policy according to the data consumers’ attributes instead of the data consumers’ detailed information. The threshold gates are also used to construct the weighted access policy. Therefore, the providers are able to construct sophisticated weighted access policies, and there is no limit to the number of threshold gates and attributes. Thus, UCP-WABE can support an extremely large number of weighted access policies, and UCP-WABE can implement flexible access control.
7. Evaluation of the Encryption Efficiency
The theoretical efficiency analysis of UCP-WABE is first given, then we carry out the experiments, and the results show that UCP-WABE has better efficiency than other schemes.
7.1. Efficiency Analysis Based on Encryption Methodologies
denotes the operation in group . denotes the operation in . In order to analyse the efficiency conveniently, suppose the number of levels of is equal to ’s and each level has the same number of attributes. Thus, have the same number of attributes, i.e., . Let be the bit size of an element of ∗ and be the number of elements of ∗. Let denote the least node set that satisfies . The comprehensive comparison among CP-ABE [24], CP-WABE [16], and our proposed UCP-WABE is summarized in Table 2. Moreover, the hash computation cost does not have to be included because it is very small.

Table 2.
Comprehensive analysis.
As shown in Table 2, suppose the values of are given. When and are fixed, the encryption time cost declines with in UCP-WABE. In order to display the results more intuitively, we suppose all the attributes have the same weight in the access trees and all the maximum weights are the same in . Therefore, the time cost of encryption linearly declines with , and the rate of descent is in UCP-WABE. In CP-ABE and CP-WABE, the encryption time cost remains unchanged. When and are fixed, the encryption time cost linearly rises with , and the growth rate is in UCP-WABE. Although the growth rate of encryption time cost is also equal to in CP-WABE, it is always higher than that in UCP-WABE. The encryption time cost increases with exponentially in CP-ABE. When and are fixed, the encryption time cost linearly rises with , and the growth rate is in UCP-WABE. The encryption time cost also linearly rises with , and the growth rate is in CP-WABE. In spite of the encryption time cost declining with in CP-ABE, it still remains far higher than UCP-WABE. In Table 2, one noteworthy fact is that the encryption time cost is a summation of the two data providers’ encryption time.
7.2. Efficiency Analysis Based on Implementation
The implementation of UCP-WABE is on the basis of the cpabe toolkit [33] and the Pairing-Based Cryptography library [34]. The implementation uses a 160-bit elliptic curve group based on the supersingular curve over a 512-bit finite field. The experiments are conducted on a PC, in Intel Core2 Duo with 3.00-GHz CPU and 2GB RAM, running Ubuntu15.04. We compare UCP-WABE with CP-WABE and CP-ABE in the field of encryption time cost. For all experiments, we make all the weighted access policies’ threshold gates “AND” gates. This ensures that all of the ciphertext components could be calculated in Decrypt.
Figure 6 shows the encryption time cost with given experimental conditions , and . We do not suppose all the attributes have the same maximum weight in this case for the reason that the result of CP-ABE is too high. The number of mutual attributes used in the experiments is . As shown in Figure 6, the encryption time cost of UCP-WABE follows a linear decline with the number of the mutual access tree attributes. For CP-WABE and CP-ABE, the encryption time cost almost keeps unchanged.
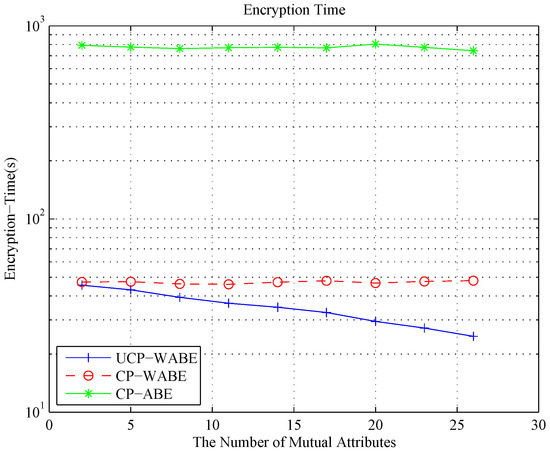
Figure 6.
Encryption time cost for the changed number of mutual access tree attributes.
Figure 7 displays the encryption time with and . In the experiments, the number of ’s attributes is . As shown in Figure 7, the encryption time cost follows a linear growth with the number of the access tree attributes in UCP-WABE and CP-WABE. Meanwhile, the former is lower than the latter. The result of CP-ABE increases exponentially with the number of access tree attributes.
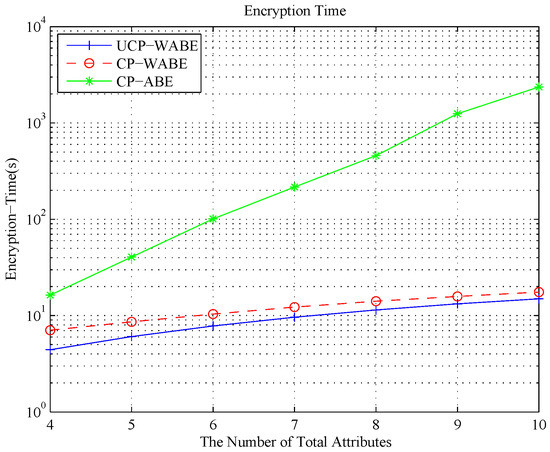
Figure 7.
Encryption time cost for the changed number of access tree attributes.
Figure 8 shows the encryption time cost with given experimental conditions , and . The weight of attributes in used in the experiments is . Figure 8 shows that the encryption time cost of UCP-WABE and CP-WABE is following a linear growth in the weight of attributes, and the former is lower than the latter. The result of CP-ABE is decreasing with the weight of attributes; however, it is still higher than UCP-WABE. Therefore, UCP-WABE improves the efficiency of encryption.
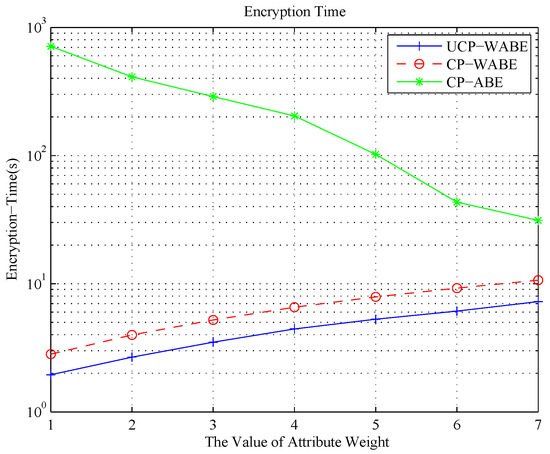
Figure 8.
Encryption time cost for the changed weight of attributes in the access tree.
8. Conclusions
In this paper, we have proposed a novel UCP-WABE scheme for sharing data in cloud computing environments. The scheme optimizes the encryption of data that are encrypted under the multi-providers’ access policies where these policies have a mutual sub-policy. UCP-WABE utilizes a mutual information extractor to extract the mutual sub-policy and produce mutual information, which assists in optimizing the encryption. UCP-WABE also takes advantage of weighted attribute-based encryption to avoid too complex of an access structure. We analyse the computational complexity of UCP-WABE theoretically and experimentally. The analyses indicate that UCP-WABE has a better efficiency of encryption. The security analysis shows that UCP-WABE is selectively secure. It should be noted that we only consider the case of two data providers. In practice, UCP-WABE will have a more efficient data sharing if the more providers’ access policies have a mutual sub-policy. In our future work, we will optimize the system implementation and conduct comprehensive experiments with real-life cases in cloud computing.
Author Contributions
W.L. proposed the main idea and conceptualization. He also performed experiments, results analysis, and scientific discussions and wrote the paper. W.N., D.L. and R.P.L. helped to revise the clarity of the work, as well as write and organize the paper. Finally, S.L. assisted in English corrections and submission of the article.
Funding
This work was supported in part by the National Key R&D Program of China under Grant 2017YFB0802300, in part by the National High-tech R&D Program of China (863 Program) under Grant 2015AA016005 and Grant 2015AA017201, in part by the Applied Sci-Tech R&D Special Fund Program of Guangdong Province under Grant 2015B010131007 and in part by the China Scholarship Council under Grant 201506470040.
Acknowledgments
The authors thank the reviewers for their valuable comments and suggestions, which improved the technical content and the presentation of the paper.
Conflicts of Interest
The authors declare that they have no conflict of interest.
Abbreviations and Notations
The following abbreviations and notations are used in this manuscript:
| UCP-WABE | unified ciphertext-policy weighted attribute-based encryption |
| the data that provider i wants to share | |
| the weighted access tree relates to | |
| a bilinear mapping | |
| ’s input group | |
| ’s output group | |
| p | ’s order, namely there are p elements in |
| the set of integers | |
| g | ’s generator. |
| the jth node in | |
| ’s children number | |
| ’s threshold value | |
| the attribute set of a data consumer | |
| the ith attribute of a data consumer | |
| WAA | weighted attribute authority |
| MIE | mutual information extractor |
| the public parameter and master secret key of UCP-WABE | |
| secret key of a data consumer, issued by WAA | |
| the set of all attributes in the system | |
| the ith attribute in | |
| the maximum weight of | |
| the weight of from | |
| the weight of from | |
| the number of leaf nodes in | |
| the root node of the mutual access tree | |
| the mutual information | |
| the hash function to hash an attribute | |
| the ciphertext of | |
| ⊥ | termination signal |
| the operation in | |
| the operation in | |
| the bit size of an element of ∗ | |
| the number of elements of ∗ |
References
- Yu, S.; Wang, C.; Ren, K.; Lou, W. Achieving secure, scalable, and fine-grained data access control in cloud computing. In Proceedings of the 2010 Proceedings IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–9. [Google Scholar] [CrossRef]
- Lee, Y.H.; Huang, K.C.; Wu, C.H.; Kuo, Y.H.; Lai, K.C. A Framework for Proactive Resource Provisioning in IaaS Clouds. Appl. Sci. 2017, 7, 777. [Google Scholar] [CrossRef]
- Chadwick, D.W.; Fatema, K. A privacy preserving authorisation system for the cloud. J. Comput. Syst. Sci. 2012, 78, 1359–1373. [Google Scholar] [CrossRef]
- Liu, X.; Zhang, Y.; Wang, B.; Yan, J. Mona: Secure multi-owner data sharing for dynamic groups in the cloud. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 1182–1191. [Google Scholar] [CrossRef]
- Abbas, A.; Khan, S.U. A Review on the State-of-the-Art Privacy-Preserving Approaches in the e-Health Clouds. IEEE J. Biomed. Health Inform. 2014, 18, 1431–1441. [Google Scholar] [CrossRef] [PubMed]
- Liu, L.; Lai, J.; Deng, R.H.; Li, Y. Ciphertext-policy attribute-based encryption with partially hidden access structure and its application to privacy-preserving electronic medical record system in cloud environment. Secur. Commun. Netw. 2016, 9, 4897–4913. [Google Scholar] [CrossRef]
- Li, W.; Liu, B.M.; Liu, D.; Liu, R.P.; Wang, P.; Luo, S.; Ni, W. Unified Fine-grained Access Control for Personal Health Records in Cloud Computing. IEEE J. Biomed. Health Inform. 2018. [Google Scholar] [CrossRef] [PubMed]
- Qiu, M.; Gai, K.; Thuraisingham, B.; Tao, L.; Zhao, H. Proactive user-centric secure data scheme using attribute-based semantic access controls for mobile clouds in financial industry. Future Gener. Comput. Syst. 2018, 80, 421–429. [Google Scholar] [CrossRef]
- Chang, V.; Ramachandran, M. Financial Modeling and Prediction as a Service. J. Grid Comput. 2017, 15, 177–195. [Google Scholar] [CrossRef]
- Gai, K.; Du, Z.; Qiu, M.; Zhao, H. Efficiency-Aware Workload Optimizations of Heterogeneous Cloud Computing for Capacity Planning in Financial Industry. In Proceedings of the IEEE International Conference on Cyber Security and Cloud Computing, New York, NY, USA, 3–5 November 2015; pp. 1–6. [Google Scholar]
- Wang, G.; Liu, Q.; Wu, J.; Guo, M. Hierarchical attribute-based encryption and scalable user revocation for sharing data in cloud servers. Comput. Secur. 2011, 30, 320–331. [Google Scholar] [CrossRef]
- Li, M.; Yu, S.; Zheng, Y.; Ren, K.; Lou, W. Scalable and secure sharing of personal health records in cloud computing using attribute-based encryption. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 131–143. [Google Scholar] [CrossRef]
- Hur, J. Improving security and efficiency in attribute-based data sharing. IEEE Trans. Knowl. Data Eng. 2013, 25, 2271–2282. [Google Scholar] [CrossRef]
- Li, J.; Zhang, Y.; Chen, X.; Xiang, Y. Secure attribute-based data sharing for resource-limited users in cloud computing. Comput. Secur. 2018, 72, 1–12. [Google Scholar] [CrossRef]
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Springer: Berlin, Germany, 2005; pp. 457–473. [Google Scholar] [CrossRef]
- Liu, X.; Ma, J.; Xiong, J.; Li, Q.; Ma, J. Ciphertext-Policy Weighted Attribute Based Encryption for Fine-Grained Access Control. In Proceedings of the International Conference on Intelligent NETWORKING and Collaborative Systems, Xi’an, China, 9–11 September 2013; pp. 51–57. [Google Scholar]
- Liu, X.; Ma, J.; Xiong, J.; Li, Q.; Zhang, T. Ciphertext-policy weighted attribute based encryption scheme. J. Xi’an Jiaotong Univ. 2013, 47, 44–48. [Google Scholar]
- Liu, X.; Ma, J.; Xiong, J.; Li, Q.; Zhang, T.; Zhu, H. ciphertext-policy weighted attribute-based encryption scheme in cloud computing. J. Sichuan Univ. (Eng. Sci. Ed.) 2013, 45, 21–26. [Google Scholar]
- Wang, Y.; Zhang, D.; Zhong, H. Multi-authority based weighted attribute encryption scheme in cloud computing. In Proceedings of the International Conference on Natural Computation, Xiamen, China, 19–21 August 2014; pp. 1033–1038. [Google Scholar]
- Liu, X.; Zhu, H.; Ma, J.; Ma, J.; Ma, S. Key-Policy Weighted Attribute based Encryption for fine-grained access control. In Proceedings of the 2014 IEEE International Conference on Communications Workshops (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 694–699. [Google Scholar] [CrossRef]
- Ghosh, S.; Karar, V. Blowfish Hybridized Weighted Attribute-Based Encryption for Secure and Efficient Data Collaboration in Cloud Computing. Appl. Sci. 2018, 8, 1119. [Google Scholar] [CrossRef]
- Li, W.; Ni, W.; Liu, D.; Liu, R.P.; Wang, P.; Luo, S. Fine-Grained Access Control for Personal Health Records in Cloud Computing. In Proceedings of the 2017 IEEE 85th Vehicular Technology Conference (VTC Spring), Sydney, NSW, Australia, 4–7 June 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Boneh, D.; Boyen, X. Efficient selective-ID secure identity-based encryption without random oracles. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Springer: Berlin, Germany, 2004; pp. 223–238. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar] [CrossRef]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; ACM: New York, NY, USA, 2006; pp. 89–98. [Google Scholar] [CrossRef]
- Waters, B. Ciphertext-Policy Attribute-Based Encryption: An Expressive, Efficient, and Provably Secure Realization; Springer: Berlin/Heidelberg, Germany, 2011; pp. 53–70. [Google Scholar]
- Beimel, A. Secure Schemes for Secret Sharing and Key Distribution. Ph.D. Thesis, Israel Institute of Technology Technion, Haifa, Israel, 1996. [Google Scholar]
- Beimel, A.; Tassa, T.; Weinreb, E. Characterizing ideal weighted threshold secret sharing. In Proceedings of the Theory of Cryptography Conference, Cambridge, MA, USA, 10–12 February 2005; Springer: New York, NY, USA, 2005; pp. 600–619. [Google Scholar]
- Chase, M. Multi-authority attribute based encryption. In Proceedings of the Conference on Theory of Cryptography, Amsterdam, The Netherlands, 21–24 February 2007; pp. 515–534. [Google Scholar]
- Liang, K.; Huang, X.; Guo, F.; Liu, J.K. Privacy-Preserving and Regular Language Search Over Encrypted Cloud Data. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2365–2376. [Google Scholar] [CrossRef]
- Cohen, H.; Frey, G.; Avanzi, R.; Doche, C.; Lange, T.; Nguyen, K.; Vercauteren, F. Handbook of Elliptic and Hyperelliptic Curve Cryptography; CRC Press: Boca Raton, FL, USA, 2005. [Google Scholar]
- Stinson, D.R. Cryptography: Theory and Practice; CRC Press: Boca Raton, FL, USA, 2005. [Google Scholar]
- The CPABE Toolkit. Available online: http://acsc.cs.utexas.edu/cpabe/ (accessed on 4 March 2018).
- Pairing-Based Cryptography Library. Available online: http://crypto.stanford.edu/pbc/ (accessed on 4 March 2018).
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).