1. Introduction
Petri nets (PNs) present an effective tool to model and analyze Discrete Event Systems [
1]. They have compact structures and can be represented in the form of matrices. Indeed, PNs can be analyzed by linear algebras. They play an important role in addressing the deadlock problems and analyzing the behavior of flexible manufacturing system [
2,
3,
4,
5]; a flexible manufacturing system can be defined as a computer controlled production system capable of processing a variety of part types. The flexibility of the system gives manufacturing firms an advantage in a quickly changing manufacturing environment [
6].
In the framework of PNs, several approaches, such as the theory of regions, have been conducted for synthesizing PN controllers. The objective is to determine a convenient set of places and arcs connecting them to the transitions that, once added to a given PN plant model, will prevent the whole system from reaching forbidden states This PN controller is a designed subpart of the PN added to the controlled model. The theory of regions (TR) was initially proposed by Badouel and Darondeau [
7] to design a bounded PN from a given reachability graph. Indeed, the set of all possible markings reachable from the initial marking with their all possible firing transitions is denoted a reachability graph (RG) [
1] A PN is said bounded if it is
-bounded for
, i.e., the number of tokens in all places of the PN does not exceed
. Nevertheless, TR has been newly interpreted for control synthesis problem by Ghaffari et al. to calculate an optimal PN supervisor. This PN controller is capable of satisfying a given control specification [
8,
9]. Indeed, this theory can be presented by a linear system composed of three classes of conditions: the reachability conditions, the Marking/transition separation instances (MTSI) conditions and basic cycle equations. The resolution of this linear system leads to the design of a PN controller which is a set of control places.
However, the steps of generating and analyzing the reachability graph present difficult tasks that weigh down heavily on the process of calculating PN controllers. Moreover, the combinatorial explosion of states in the RG complicates the calculation of PN controllers. Since computing time costs money, the objective of this work is to apply the TR for supervisory control without computing the RG in order to ease the supervisor calculation and eventually reduce the production cost.
In an industrial context, different products can be performed at the same time which can increase the control constraints and incite the monitor to make the necessary adjustments in order to control the system and maximize the production with less time.
In fact, many studies have been conducted on reachability graph analysis which represents a significant technique for synthesizing optimal/near-optimal PN controllers [
10,
11,
12,
13]. In [
13], a RG based method is developed to calculate an optimal PN supervisor with the fewest control places for FMS modeled by PN. The RG is divided into a live zone and deadlock zone. The states in live zone are legal ones for a Flexible manufacturing system (FMS), and those in deadlock zone are deadlock or will lead to deadlocks. In [
10], a vector covering method is used to reduce the number of markings to consider in the synthesis of PN controllers. An optimal supervisor with the fewest control places can be designed by solving a Minimal number of control places problem (MCCP). The PN controller obtained is optimal and structurally minimal in terms of the number of control places. However, it has a limitation: the computational burden is extremely hard, mainly for large models.
In addition, in Zhao et al. [
14], a new method for supervisory control is developed using a divide-and-conquer strategy. Compared with most of traditional global-conquer methods of Uzam and Zhou [
15,
16], the computational efficiency of PN supervisors is improved. Nevertheless, as the number of shared resources in uncontrolled systems has increased, too many subsystems should be disposed. Thereby, as the net system size becomes larger, the improvement of this divide-and-conquer method will be impeded.
Our new control policy is based on the researches addressed on the use of the theory of regions. Up until now, the TR is recognized as one of the powerful method for deadlock prevention and supervisory control policies for obtaining maximally permissive PN controllers [
8,
9] which bans the set of forbidden states MI; unlike a legal marking, any state that does not comply with a control constraint is a non-legal state in the graph and will be denoted a forbidden marking
. In fact, many research works sought to lower the computational burden of the theory of regions; in [
17], the authors used the siphons-approach before using the TR to synthesize PN controllers. Besides, in [
18], a new method is developed for deadlocks prevention to decrease the number of reachability conditions of TR in order to facilitate the supervisor calculation. Their experimental results seems to be the most effective approach in deadlock prevention policy compared with existing works of [
15,
19,
20]. Unfortunately, the computation of RG and its analysis to determine the basic cycles and the legal/forbidden markings for this method are still heavy.
However, the methods able to apply the theory of regions for control synthesis without computing the reachability graph have not been investigated. This paper sheds new light on TR simplification by eliminating the RG calculation and avoiding the combinatorial explosion of states which is a meaningful step for RG-based method. In addition, this work is only focused on bounded PNs.
In our previous works [
21,
22,
23,
24,
25], a new method of minimal cuts in RG is developed using the theory of regions. Through this approach, we have also minimized the computational cost of PN supervisor using the TR on specific areas of the graph and not on the whole RG. Nonetheless, the graph generation step and its analysis are inevitable.
Accordingly, to reduce the computational burden of the TR, the RG generation step should be abandoned. In fact, based on PN properties and mathematical theories, one can speed up the synthesis process of PN controller. Consequently, the criterion of computation time of PN controllers will be a key factor in the comparison of this work with the previous ones [
8,
23].
The rest of this paper is structured as follows.
Section 2 depicts the background of the theory of regions and PN tools.
Section 3 introduces the concept of our new methodology for control synthesis. Next, three case studies will be given in
Section 4 in order to illustrate the contribution of the proposed approach.
Section 5 presents the results of comparison with previous works. Finally, conclusions are drawn in the
Section 6.
2. Background
A Petri net is a directed graph consisting of places, transitions and valued arcs connecting them. Formally, a PN is a bipartite graph
.
is a finite set of places.
is a finite set of transitions [
1].
is the pre-incidence function that specify weighted arcs from
to
.
is the set of nonnegative integers. In addition,
is the post-incidence function that specify weighted arcs from
to
. The transitions of a PN can be partitioned into two disjoint subsets:
the set of uncontrollable transitions and
the set of controllable transitions. Controllable transitions can be disabled by the PN controller, while uncontrollable transitions cannot. Let
(respectively,
) be the set of output transitions (respectively, input transitions) of the place
. A PN can be represented by the so-called incidence matrix
defined as
. Let
(respectively,
) the set of output places (respectively, input places) of transition
. Besides, let
be the reachability graph constructed from the initial marking
of a given PN. Ϻ represents the set of markings
. A transition
is enabled from a marking
(denoted by
) if and only if
if an enabled transition
is fired, it leads to a new marking
such that:
. This can be denoted by
. A marking
is accessible from a given marking
if there exists a firing sequence
transforming
into
. By firing a sequence
any marking
reachable from
satisfies the following state equation of Petri nets:
is a vector of nonnegative integers is the occurrence of transition in .
Let be the incidence matrix of marked PN. if , if , else 0. Where is a valuation function of arcs. : Finite set of arcs. A Petri net is k-bounded if the number of tokens in each place does not exceed k. If k = 1, then the PN is said safe. A PN is live if all transitions are live; a transition is said live if it can always be made enabled starting from any reachable marking. A PN is reversible if from any reachable state there is an enabled sequence to return to the initial marking .
Let us consider a set of legal markings; such admissible states correspond to a set of general mutual exclusion constraints GMECs. A constraint
defines a set of legal markings [
26]:
A new type of control specification constraint based on sequence transitions is developed in our previous work. This method is called admissible paths constraints APC
which defines a set of legal sequences of transitions [
27]:
The theory of regions in control synthesis was proposed by Ghaffari et al. [
8,
9] using the properties of PN for adding a controller
to the initial PN model. The PN controller is characterized by its initial marking
and incidence vector
. The TR is expressed by a linear system composed of three classes of conditions:
Reachability conditions:
: Is the path between
and
.
MTSI condition:
.
is the set of prohibited state transitions. The transition
may lead to a forbidden marking
.
is the set of markings which do not comply with a GMEC:
Basic cycle equations:
is the algebraic sum of occurrences of t in
, and R is the desired behavior of the controlled system.
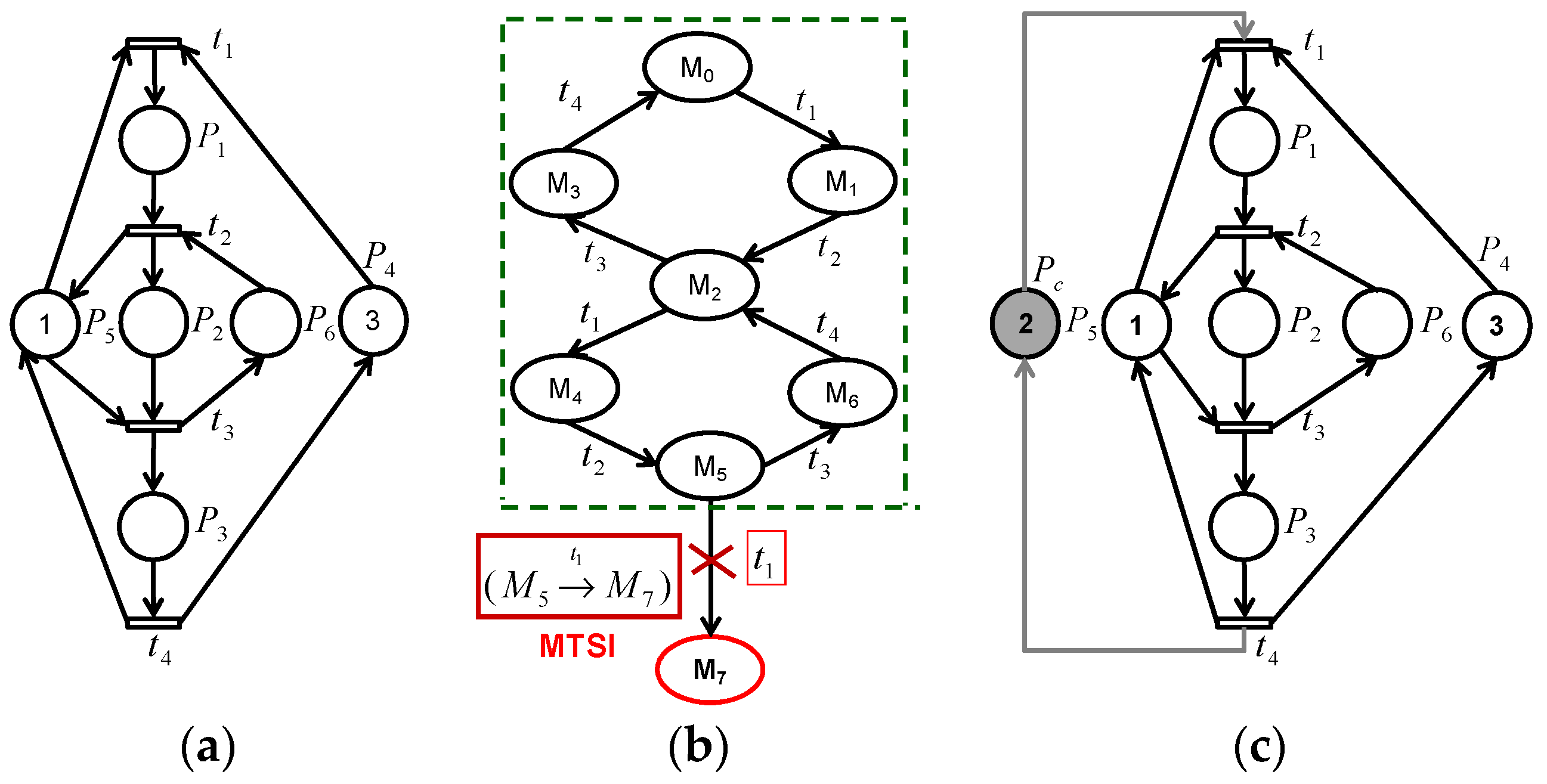
The application of the classical approach of the theory of regions [
9] is given in the following example (i.e., see
Figure 1). For a given PN (
Figure 1a) [
23], we firstly generate the reachability graph (
Figure 1b). Next, one can analyze the RG to determine existing basic cycles, the legal markings and the forbidden ones (marking
). The linear system of TR is given as follows:
The resolution of this linear system generates the following PN controller
. The addition of this PN controller gives the controlled PN model shown in the
Figure 1c.
In the following section, an effective method to avoid the combinatorial explosion of states in the presumed reachability graph will be introduced, where the generation step of RG is overlooked.
3. Design of PN Controller
3.1. Problem Setting
This work is focused on the minimization of the computational cost of the theory of regions by reducing the computation time for the synthesis of PN controllers. For this purpose, a new method based on PN tools and mathematical concepts, is proposed to design a PN supervisor without calculating the reachability graph.
Definition 1. (Combinations without repetition) A k-combination without repetition of a set A with n elements is an arbitrary subset of A having k elements. If we take k objects among n without repetition and regardless of the appearance order, one can represent the k objects by a part of k-elements from a set with n elements. To determine the number of these provisions, one can determine the number of arrangements of k objects, and divide them by the number of provisions obtained from each other by a permutation: .
Definition 2. (Combination with repetition) A k-combination with repetition of the set A is an arbitrary k-element multi-set of elements from A. If we take k objects among n without repetition and regardless of the appearance order, these objects can appear several times and we cannot represent them either with a part of k elements or with a k-tuple as their placement order is not involved. However, it is possible to represent such provisions with applications called combinations with repetition. The number of k-combinations with repetition of a set with n elements is denoted by and formally: .
Definition 3. (Usable sequence)
A sequence is said to be a usable sequence if it leads to a reachable state that may exist in the presumed reachability graph. Let be the set of usable sequences:
Definition 4. (Unusable sequence)
A sequence is said to be an unusable sequence if it leads to a state that does not exist in the presumed reachability graph. Let be the set of unusable sequences:
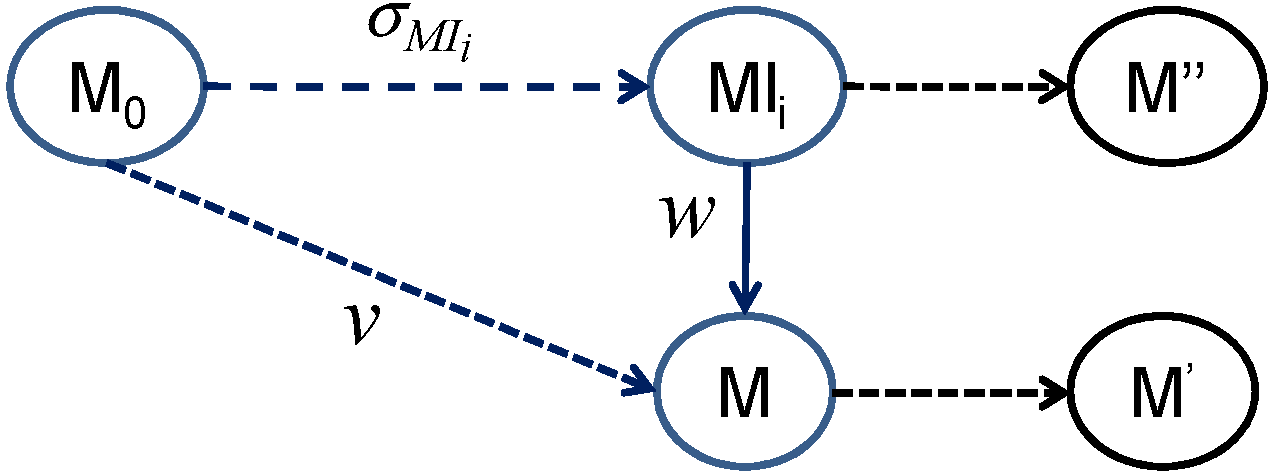
Definition 5. (Prefix of a sequence)
Let be the set of forbidden markings that does not fulfill a given GMEC and let be the set of events. A firing sequence of a given forbidden marking is a prefix of a sequence ,
if there is another sequence such that .
That is, is the concatenation of and (
see Figure 2). If is a physically possible sequence in the system, then naturally any prefix of is also a possible sequence in this system.
The key idea of the proposed method is to focus on the determination of the linear system of the theory of regions. Once the three classes of conditions of the TR, i.e., Equations (4)–(6), are defined, one can obtain the PN supervisor by adopting the interpretation of the theory of regions.
3.2. Basic Cycle Equations
Let
be a PN with its incidence matrix
, and let
be a nonnegative vector of n integers, solution of the equation
. Let
be the firing sequence for a legal marking
with
. The sequence
is called transition invariant [
28]:
The resolution of this system generates the transition invariants that identify the basic cycle equations:
Definition 6. Let be the set of existing transitions in the basic cycle equations such that:
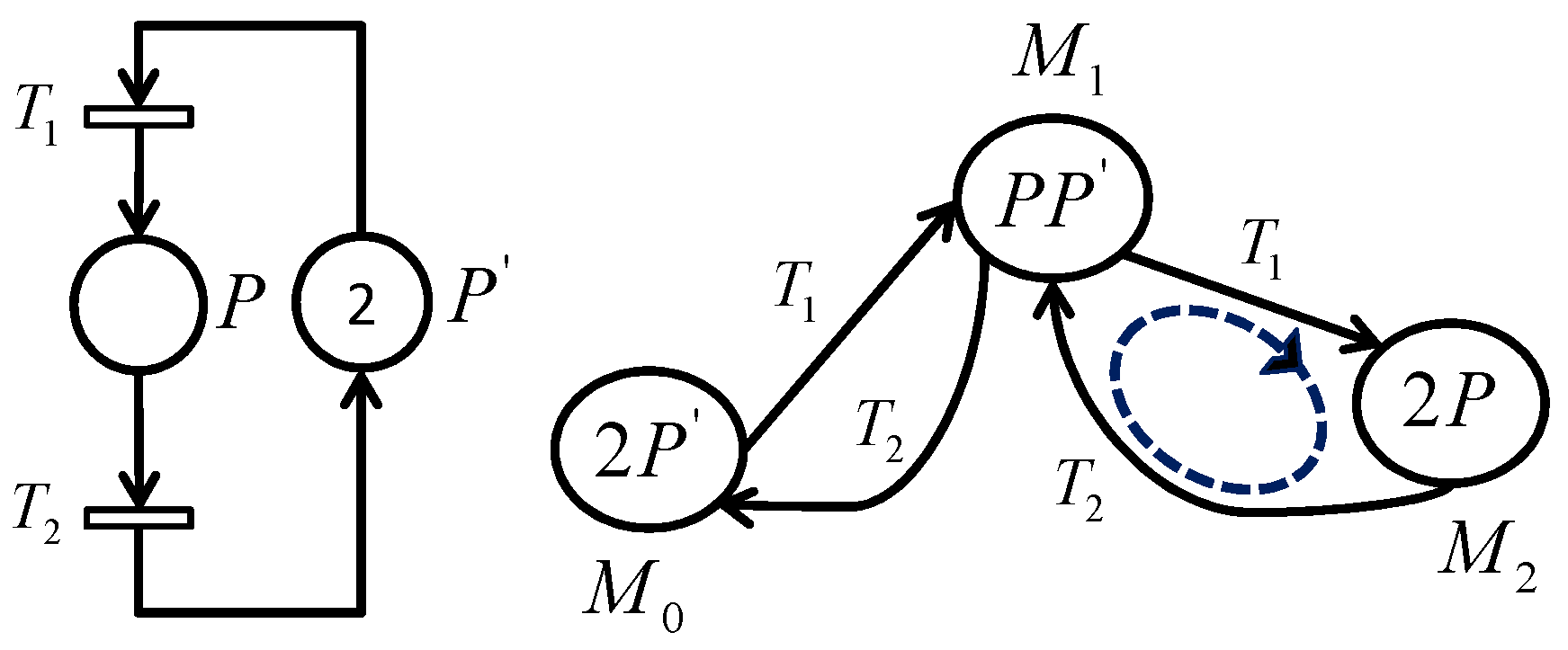
As shown in the example of PN given in
Figure 3, the application of the transition invariant method generates the cycle equation of the theory of regions:
.
Remark 1. The determination of the reachability conditions/MTSI conditions is equivalent to the identification of paths connecting the initial marking and the legal/forbidden markings . Thereby, to deduct this path, it is necessary to identify the corresponding sequence of transitions .
3.3. Reachability Conditions
Let
be the control place to determine. Each marking
that satisfies a given GMEC must be reachable by the controlled PN model. As matter of fact, the reachability condition translates the state equation of Petri nets (1). The difference is that the equation is positively assigned and the reachable marking is legal:
In order to determine all the firing sequences, the combinatorial analysis methods were introduced in our work (i.e., see Definitions 1 and 2).
Proposition 1. For a safe PN, the set of firing sequences of transitions denoted by S corresponds mathematically to combinations without repetition where i transitions are chosen among :
Proposition 2. For a k-bounded PN with ,
the set of firing sequences of transitions denoted by S corresponds mathematically to combinations with repetition where i transitions are chosen among :
A safe PN is a 1-bounded PN (k = 1). Each transition is fired no more than once in a given sequence . Similarly, is a collection of i transitions among and the transition can be collected at most once. Therefore, the sum of transition combinations corresponds to all firing sequences of transitions ).
3.4. MTSI Conditions
Up to here, the reachability conditions and the basic cycle equations are known. Furthermore, the initial marking of PN model is given. Through these data and our previous work, one can calculate the MTSI conditions.
Corollary 1. If the control specification is expressed as GMEC ,
then the identification of the set of forbidden states MI is possible without generating reachability graph using the canonic markings method [
25].
Remark 2. The firing sequences of transitions are generated from the set and not from since the cycle equations exist in the desired behavior of the controlled system and not in the whole graph .
Since the set MI of forbidden markings is known, one can determine the set of forbidden sequences
. Moreover, the calculation of
can be done in two ways:
Consequently, one can determine the MTSI condition:
By summarizing, a new interpretation of the theory of regions is developed in this work to determine the linear system formed of Equations (10)–(12).
3.5. Filtering of Sequences S
The filtering step of sequences S is necessary in our work in order to specify the correct linear system of the theory of regions. Indeed, the generation of the set of sequences S with/without repetition gives unusable sequences and usable sequences (i.e., see Definitions 3 and 4). Therefore, the usable sequences and the basic cycle equations allow us to accurately determine the linear system of the theory of regions.
The filtering of sequences S is performed using the state equation of Petri nets:
where
is the new marking to determine by testing all sequences of the set S.
Thus, the unusable sequences to reject are:
Sequences having prefixes (i.e., see Definition 5);
Sequences leading to null markings; and
Sequences leading to negative markings (A negative marking is a vector containing at least one negative component).
The synthesis method of PN controllers using the new interpretation of the theory of regions is described in the following Algorithm 1.
| Algorithm 1. Algorithm of the synthesis method |
| Given a PN with its initial marking and the set of forbidden markings MI, let S be the set of firing transitions sequences. |
| (1) | Determine the basic cycle equations using the transitions invariants method and let be the set of transitions in cycle equations. |
| (2) | If the PN is safe, then determine S with
If the PN is k-bounded with k > 1, then determine S with |
| (3) | Identify from S the set of forbidden firing sequences of transitions . |
| (4) | Filter the firing sequences of transitions S to get the set of usable sequences |
| (5) | While do: |
| (5.1) | For each forbidden sequences of transitions , write the linear system of the theory of regions composed of:
The MTSI condition of the eventual forbidden sequence
The reachabiliy conditions of the remaining sequences
The basic cycle equations |
| (5.2) | Solve the linear system of TR and let be the solution sought. |
| (6) | Remove redundant control places to obtain the controlled Petri net. |
In the first three steps, the cycle equations and the sequences S are generated. Thus, one can filter the firing sequences to form the linear system of the theory of regions by using only the usable sequences and the cycle equations. In the following steps, the theory of regions is applied and the PN supervisor is synthesized.
In the next section, three case studies are provided to show that the Algorithm 1 can find an optimal PN supervisor using the theory of regions without computing reachability graph.
4. Case Studies
In this section, three case studies of bounded PNs are solved using CPLEX software with a C program to evaluate our control policy. Notably, the three cases include two subclasses of PN (i.e., safe PNs and k-bounded PNs with k > 0) in order to apply and test the propositions of
Section 3.3. Owing to the limitation of paper space, the reachability conditions are not listed in these case studies.
Indeed, in Example 1, the resources are shared and the PN is safe which allow us to calculate the firing sequences using combinations without repetition (i.e., Proposition 1). Then, we can better assess the effectiveness of our method since safe PNs are special cases of PNs.
Next, Examples 2 and 3 model three stations of the FMS installed in our laboratory with k-bounded PNs. Consequently, the sequences of firing transitions will be determined employing combinations with repetition. In fact, Example 2 deals with two assembly stations with a production constraint, while Example 3 models a control quality station with another general mutual exclusion constraint. These two examples represent two real cases of production constraints, which allow us to tackle two real situations of industry.
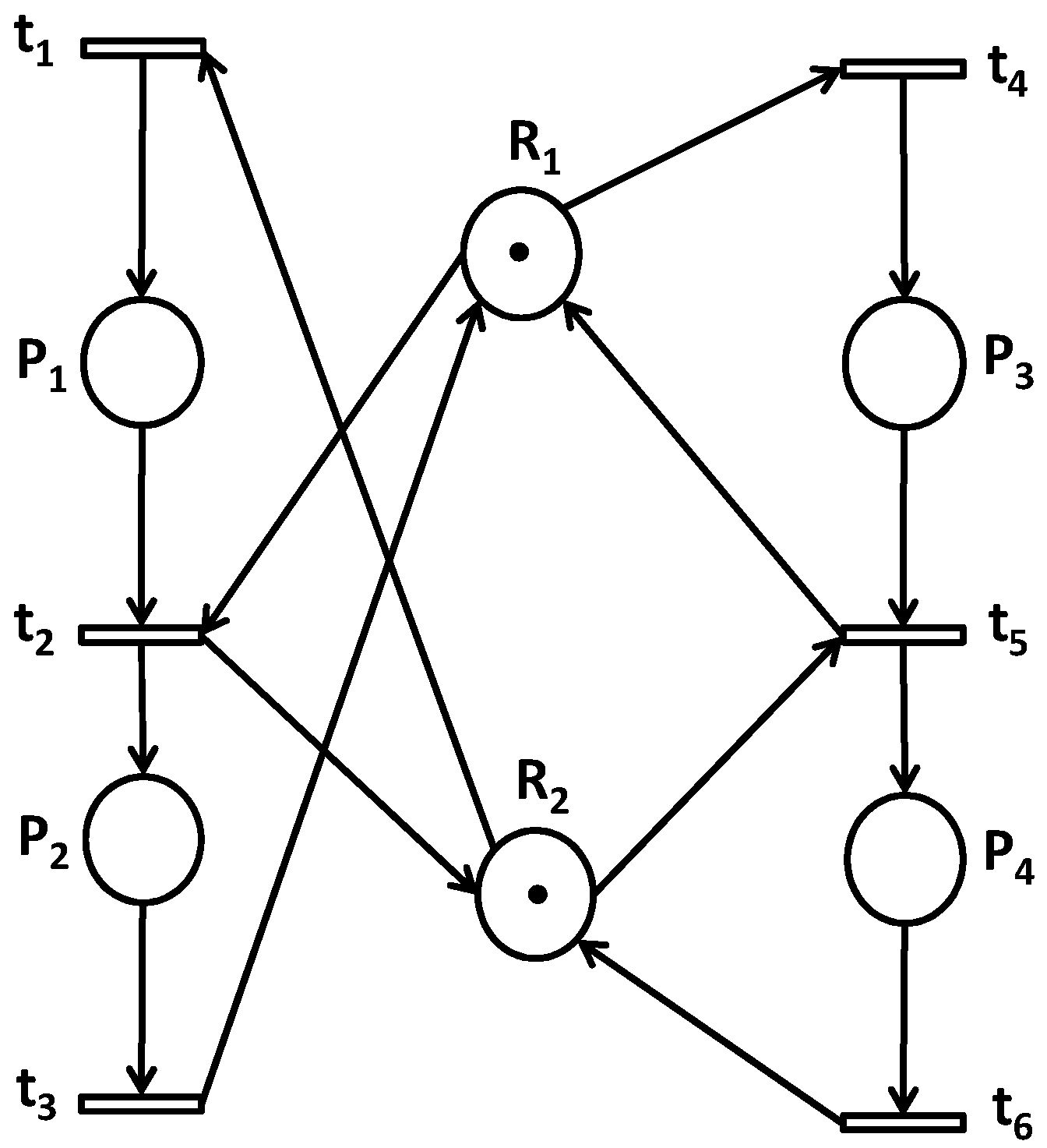
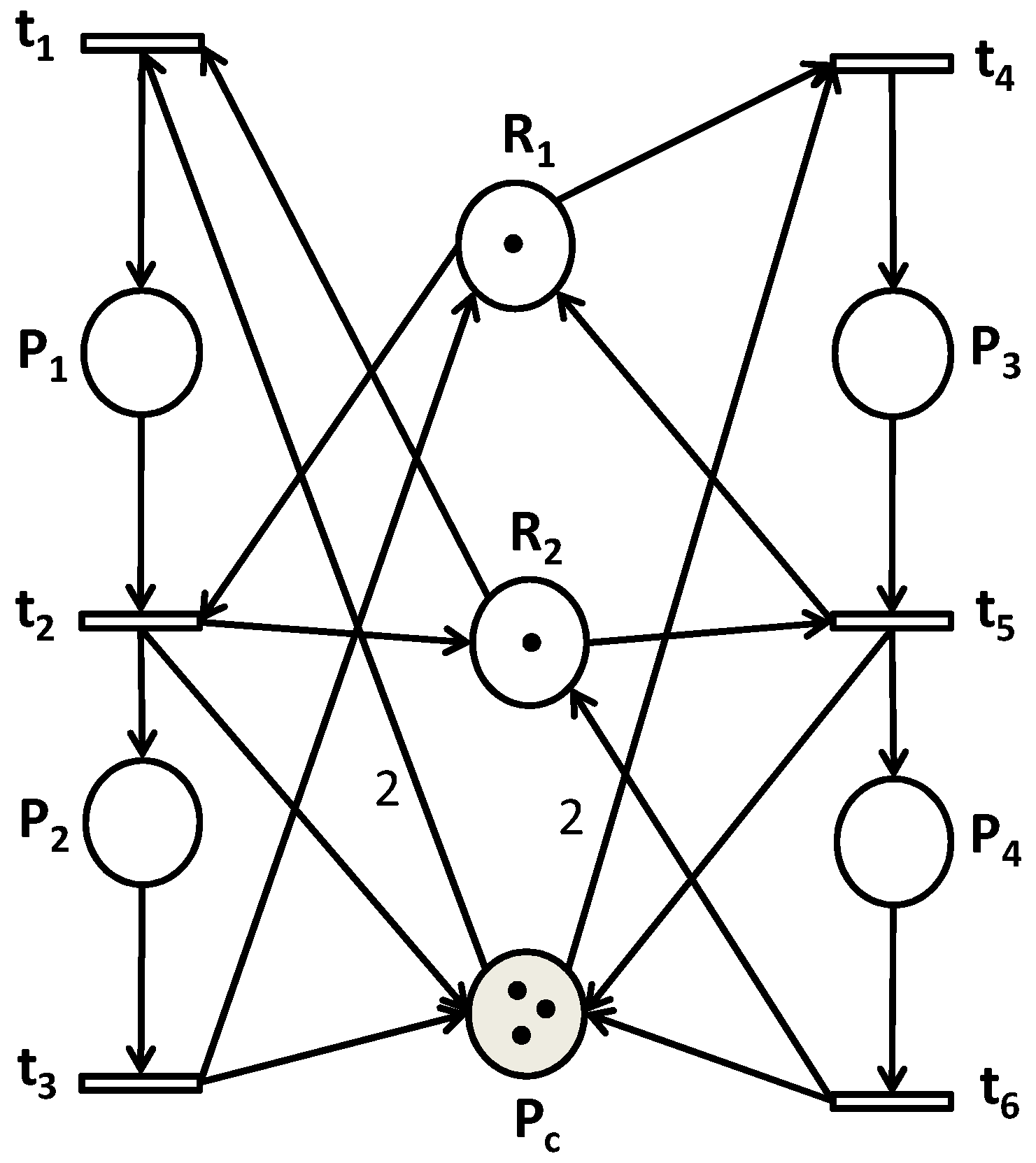
4.1. Case Study 1
This first case study addresses a PN model with two machines sharing two resources
and
shown in
Figure 4. The places
and
materialize two operations. To deal with the organizational and synchronization problem between two processes in parallel which is a current problem, we have to satisfy the following control specification:
.
The resolution of the equation:
gives the basic cycle Equation (10).
The corresponding sequences of the basic cycle equations are:
and
. Thus, the basic cycle Equation (10) can be listed as follows:
According to the Definition 6, the set
contains six transitions, i.e.,
6:
The PN is safe (k = 1). Then, conforming to the Proposition 1 the set S of firing sequences of transitions is generated through combinations without repetition.
Afterwards, the sequences S will be filtered conforming to the criteria mentioned in
Section 3.4 in order to obtain the usable sequences listed in
Table 1.
Finally, by identifying the usable sequences 8, one can obtain the reachability conditions (11).
The set of forbidden markings that do not fulfill the control specification are listed in
Table 2. In agreement with Corollary 1, the forbidden sequences σ
MI can be obtained using the canonic markings method and are listed in the
Table 3. Then, the MTSI condition can be obtained as follows:
Furthermore, by applying our algorithm, there is one control place
obtained when Equations (10)–(12) are solved. The PN controller information is listed in
Table 4. Therefore, the controlled PN model is given in
Figure 5.
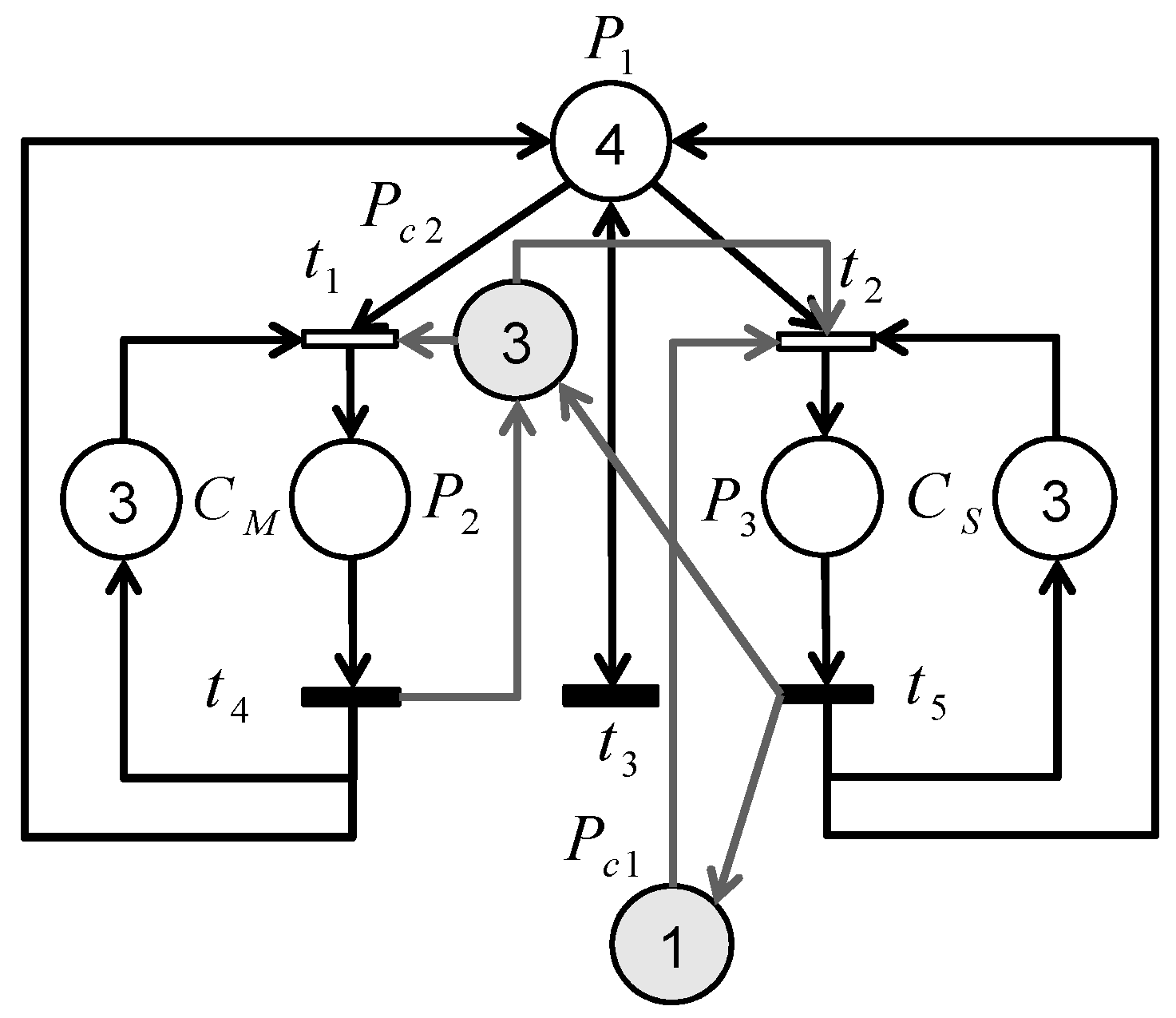
4.2. Case Study 2
A flexible manufacturing system in the Lorraine University contains two assembly stations in which engraved glass pieces are assembled with stands. The physical system and the PN model are presented in
Figure 6a,b. The place
models our production machine, while the place
represents a subcontractor production. The capacities of three pieces of the machine and the subcontractor are modeled by
and
, respectively. In addition, the place
represents our stock production. Moreover, the entry and exit events of the pallets in annex conveyors are modeled by transitions
and
, respectively. Alternatively, the pallet continues its way in the main conveyor by
. Note that
and
are uncontrollable.
The following scenario is employed: If and represent the subcontractor and the machine, the subcontractor production should be minimized to increase our profits. This control specification can be expressed by the following GMEC: .
Consequently, the basic cycle equations can be calculated as follows:
Reachability conditions: The set contains four transitions, i.e.,
The PN is k-bounded with k > 1. Thus, one can calculate the firing sequences of transitions using combinations with repetition (i.e., see Proposition 2):
Next, the set S is filtered in order to calculate the usable sequences listed in
Table 5, and then one can determine the reachability conditions.
The MTSI conditions are calculated using the forbidden sequences
. The sets of forbidden markings and sequences are listed in
Table 6 and
Table 7. MTSI conditions are:
According to our new method, two control places
and
can be obtained. The detailed information of the PN controllers is shown in
Table 8. Consequently, the controlled PN model is given in
Figure 7.
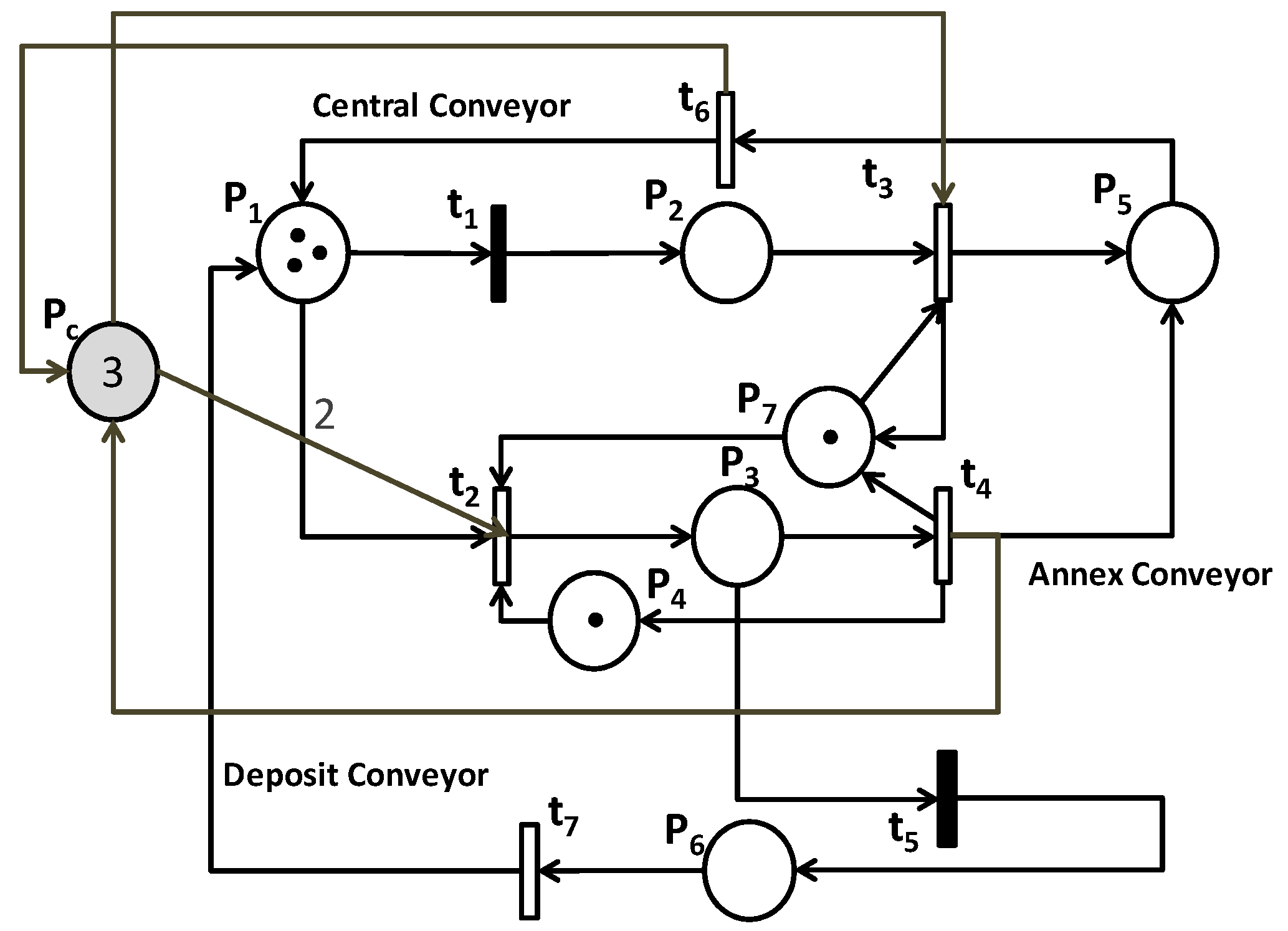
4.3. Case Study 3
A bounded PN modeling a quality control station of the FMS is shown in
Figure 8a,b. It is the final step in the production process of Lorraine University FMS. The places
,
and
represent the central conveyor, while the annex conveyor is modeled by
. Its capacity is modeled by
. If the piece to manufacture is not in compliance with recommended standard, it will be placed in the waste conveyor represented by the place
. Moreover,
models the priority of a treated piece compared to another untested piece. Note that the transitions
and
are uncontrollable.
In order to maximize manufacturing output, we propose to satisfy the following GMEC; the marking of plus twice the marking of must be less than three tokens. This control specification is expressed as follows: .
and
. Then, the basic cycle equations can be listed as follows:
The set of existing transitions in the basic cycles is
. The PN is k-bounded with k > 1, therefore:
After filtering the sequences S, the usable sequences are given in
Table 9 (
27).
The GMEC is
, then the forbidden markings that do not respect the control specification can be calculated (i.e., see
Table 10). Using the canonic markings method, the set of forbidden sequences
can be listed in
Table 11. Therefore, the MTSI condition is determined as follows:
Nevertheless, the transition
is uncontrollable. Then, a back chaining must be performed to determine the dangerous marking:
. Consequently, the MTSI condition to be considered is:
Finally, the synthesized PN controller
(i.e., see
Table 12) is added to the initial PN to obtain the controlled model shown below (
Figure 9).
5. Comparison with Previous Methods
This section presents three tables for comparing our new method with previous works. For convenience, the policy of this work is called
, our prior work [
23] is called
and the related research of Ghaffari et al. [
8] is called
.
Table 13 lists the comparison results of the first case study with three approaches of supervisory control. Since the RG is generated and contains eight states, one can know that
uses eight markings to design the PN monitor. Then,
improves
by introducing minimal cuts in RG and uses three markings to synthesize the PN controller. However, both of these efficient methods must pay for time consuming. Here, our proposed approach (i.e.,
) that does not generate RG reduced the technology and the theory of regions to obtain the same number of PN monitors. It enhances the computation efficiency of
. Based on the experimental results in
Table 13, 3018 ms are needed if one uses
in this example against 6015 ms and 3226 ms for
and
, respectively. As a result, we can infer that
is the most efficient among
and
.
Example 2 is a k-bounded PN model. Based on
Table 14, 13 states and five forbidden state transitions are needed to be processed if
or
is used, respectively. Besides,
still needs 7190 ms to design two PN monitors even though the computation time is reduced compared with
which needs 10,593 ms to calculate the same number of control places. Nonetheless, 0 markings and three forbidden state transitions are needed in our policy. Furthermore,
only takes 6216 ms to control the system, which shows that
is faster than
and
. This time difference can be significantly increased if bigger models are analyzed.
Based on the comparison results (i.e.,
Table 15), 27 markings and 12,120 ms are needed to obtain one PN monitor in
. However, under the minimal cuts policy (i.e.,
), only six markings are handled to calculate the supervisor. It does not seem to be efficient enough since it requires 6110 ms to supervise the quality control station of the FMS. Nevertheless, for the same number of forbidden state transitions and monitors, only 5930 ms are required in our new method that is able to control the FMS without computing any marking. To summarize,
is the best computationally improved optimal control algorithm among existing literatures that use the theory of regions.
6. Conclusions and Future Works
The proposed control synthesis method can be implemented for FMSs and generally for bounded PNs. The underlying notion of the previous work is that the TR must be solved by handling a number of markings which may increase according to the structural size of the system. For this purpose, one must generate the RG and all MTSI in the graph such that they have to pay for the high computation cost. However, PN properties and mathematical concepts are merged in our proposed method to reduce efficiently the computational burden of the TR.
As mentioned above, three case studies are solved using the CPLEX software with a C program in order to compare our new method with the existing optimal policies; as input, one can give the PN model and the GMEC, then one can obtain all information concerning the controlled system in the program output (computing time, control places, incidence vector, etc.). In fact, our control method determines all equations of the linear system of the TR without generating the RG, thus one can avoid the combinatorial explosion of states if bigger models are analyzed. Additionally, PN controllers can be determined with a drastically reduced time. Consequently, this achievement will positively impact the performance of the production systems since the production constraints require immediate actions through rapid adjustments in order to maximize the production. Furthermore, any efficient supervision of any system has a high cost; if a constraint is not satisfied in a timely manner, the production or the security can be directly affected. There are numerous examples, such as the change over time with different constraints, the generation of a new flight plan to face with disruptions in air traffic networks, etc.
Finally, this work provides scientific novelty to control bounded PNs (such as FMS, telecommunication systems, safety systems, air traffic management, rail traffic, etc.) since most previous studies on computing optimal supervisor depend on a complete state enumeration and mixed programming problem. In addition, since the RG-generation step is skipped, our program can handle any bounded PN model, even the biggest.
Hence, in the near future, how to deal with deadlock prevention policy without generating RG is to become an important issue.