An Integrated Testbed for Power System Cyber-Physical Operations Training
Abstract
:1. Introduction
1.1. Problem Statement
1.2. Related Works
1.3. Contribution
- Develop a HIL co-simulation testbed that boasts the integration of a real-time simulator, industry-grade protection, automation equipment, and a SCADA system;
- Show an integration of protection studies in a CPS testbed;
- Analyze different cyber threats at a granular level with network packet analysis;
- Demonstrate the interoperability of the testbed at the communication protocol level with the use of DNP3, C37.118, and IEC 61850 for use cases;
- Hands-on experiments to train students and industry professionals in cybersecurity.
1.4. Limitations
1.5. Outline of the Paper
2. Cyber–Physical Systems
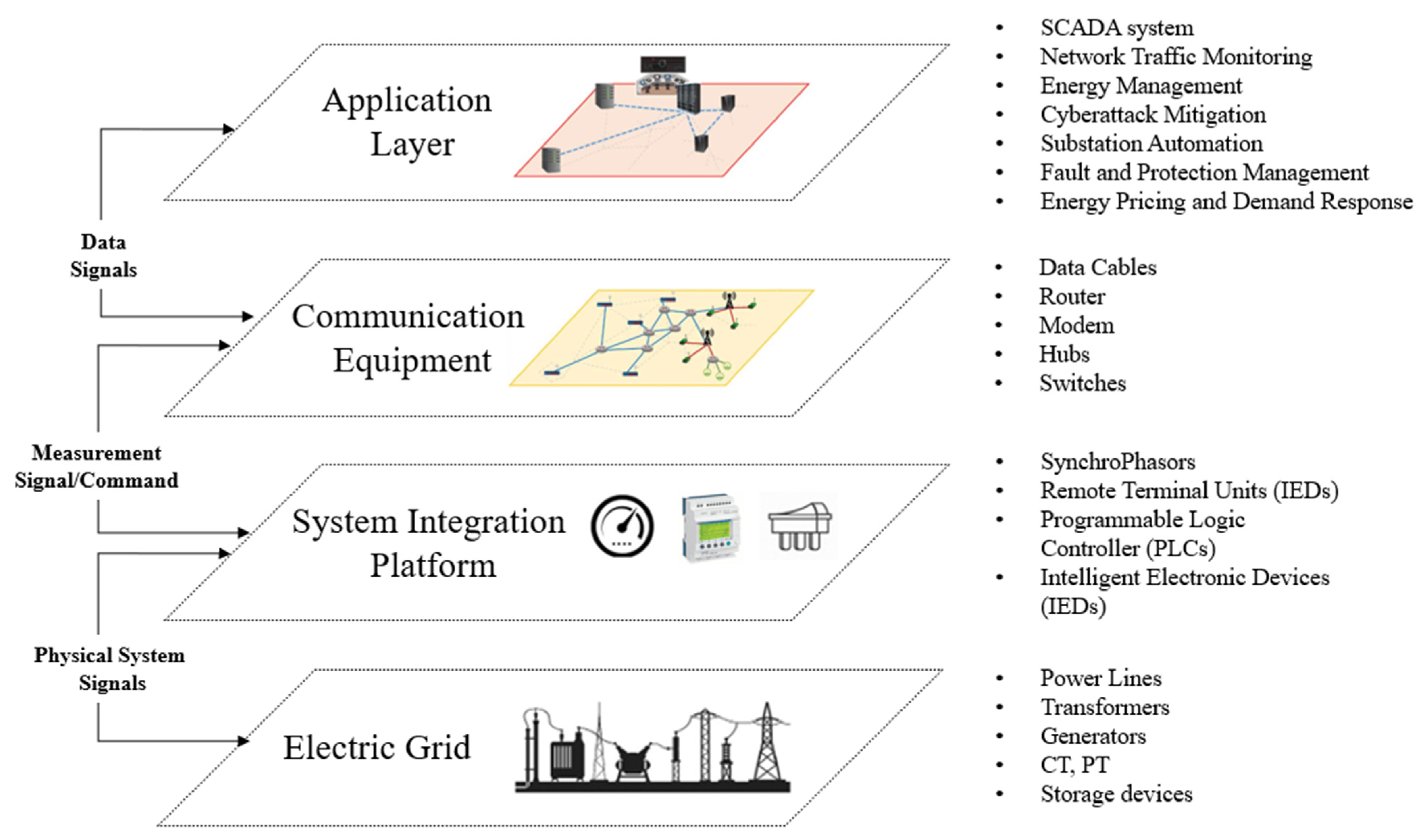
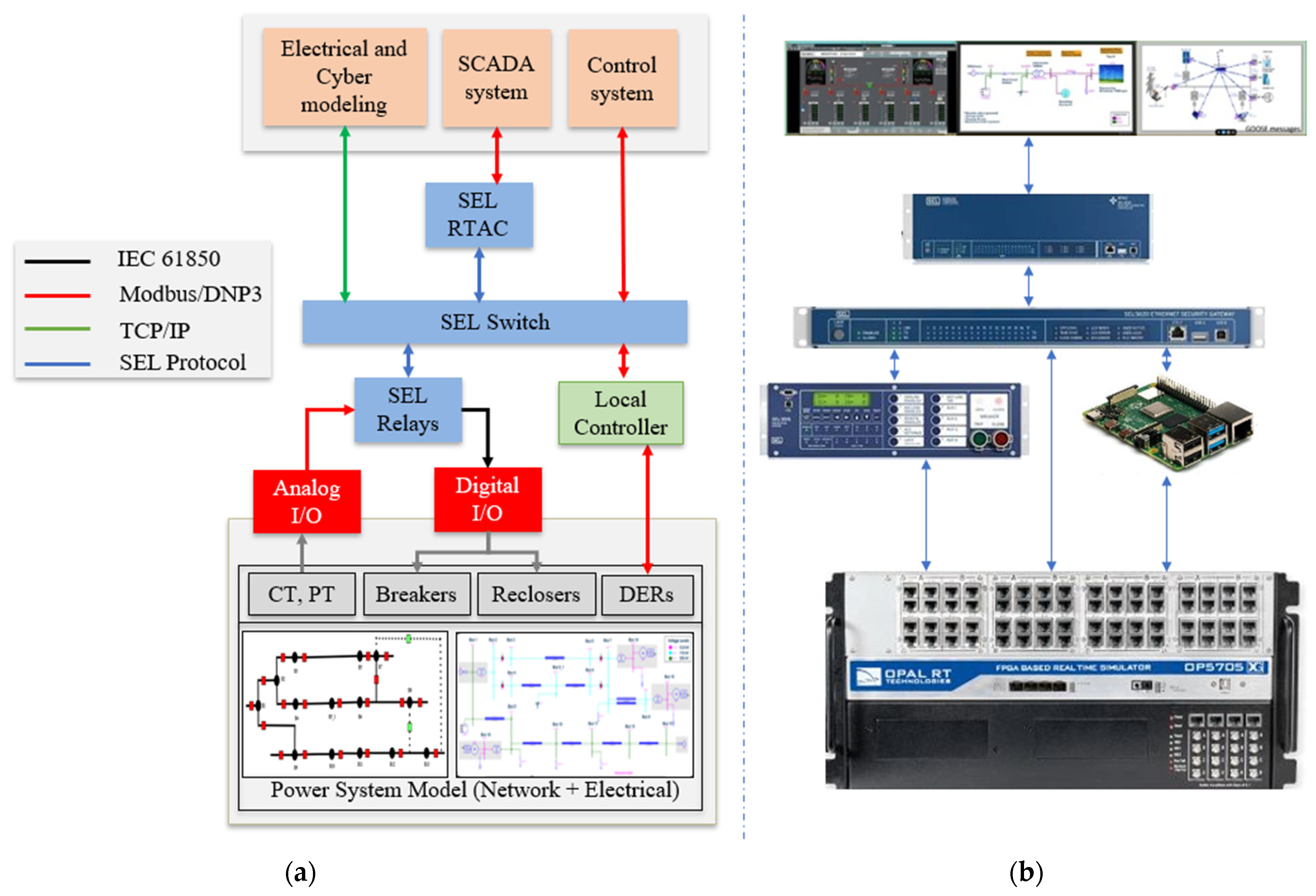
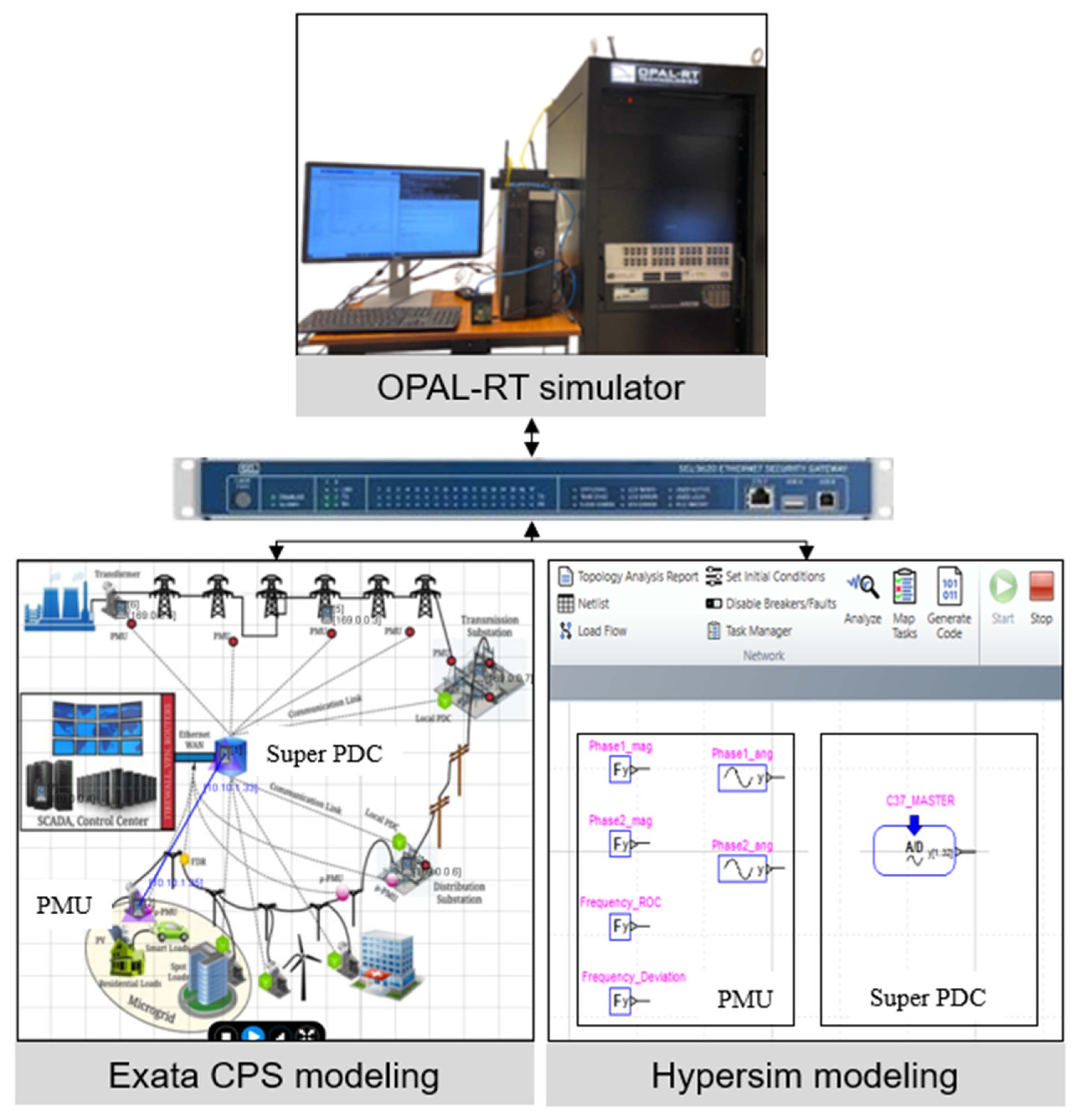
3. CPS Testbed Architecture
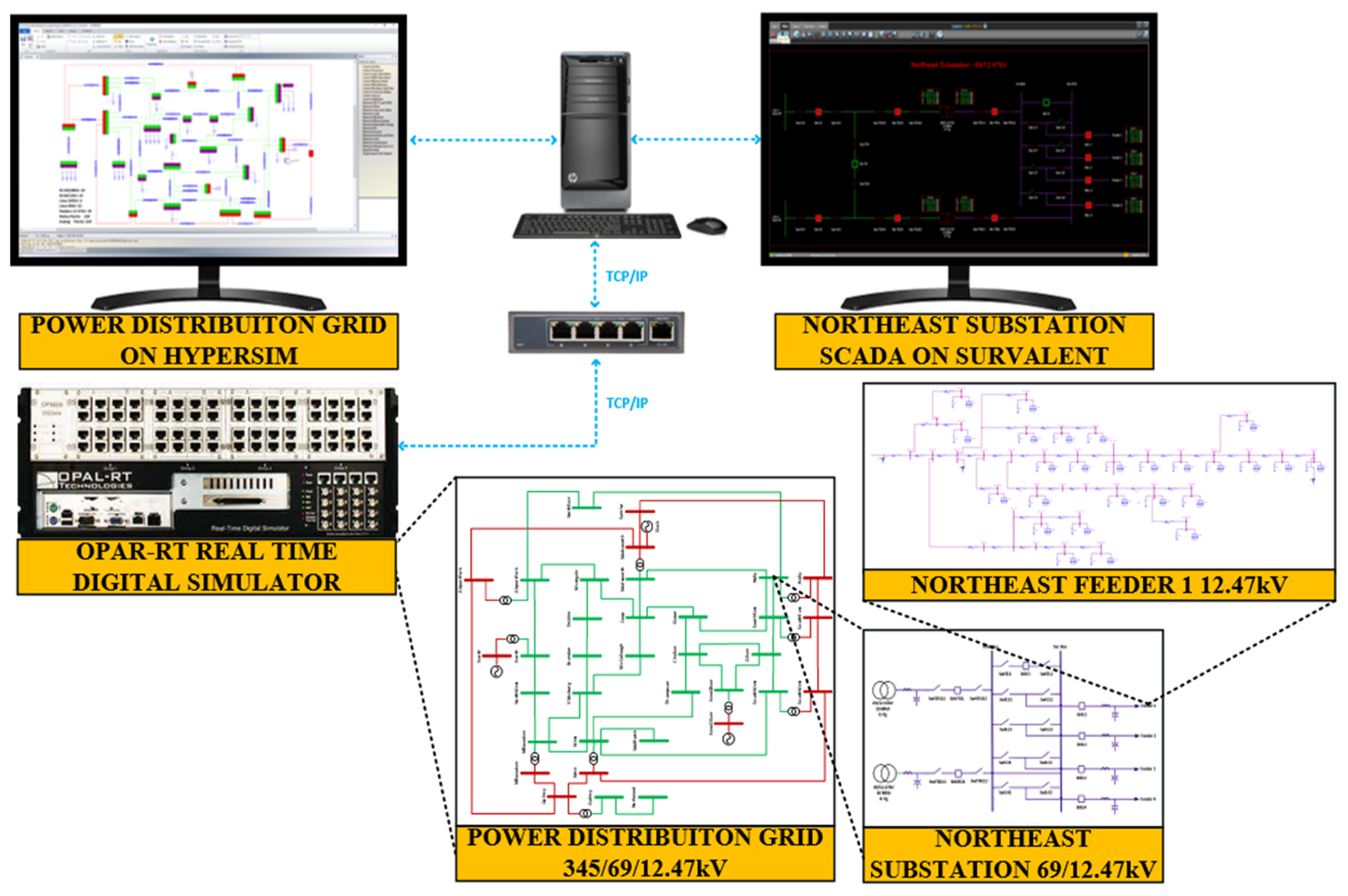
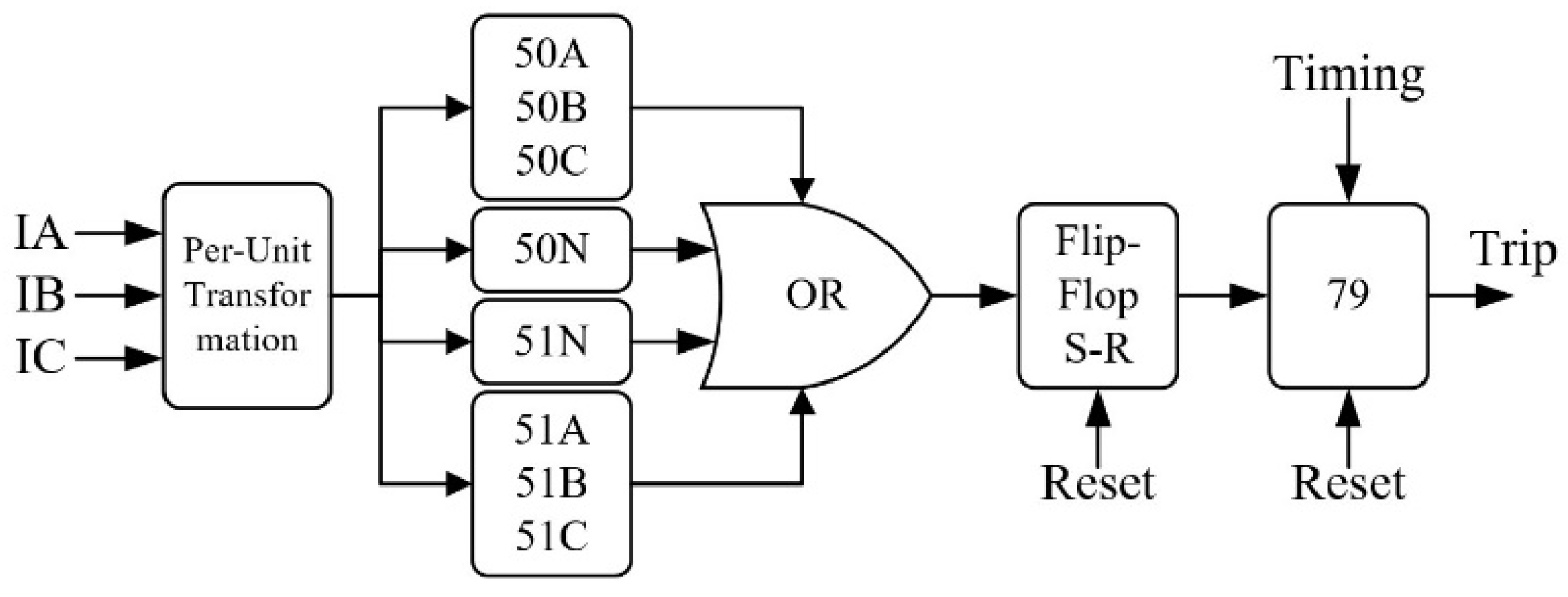
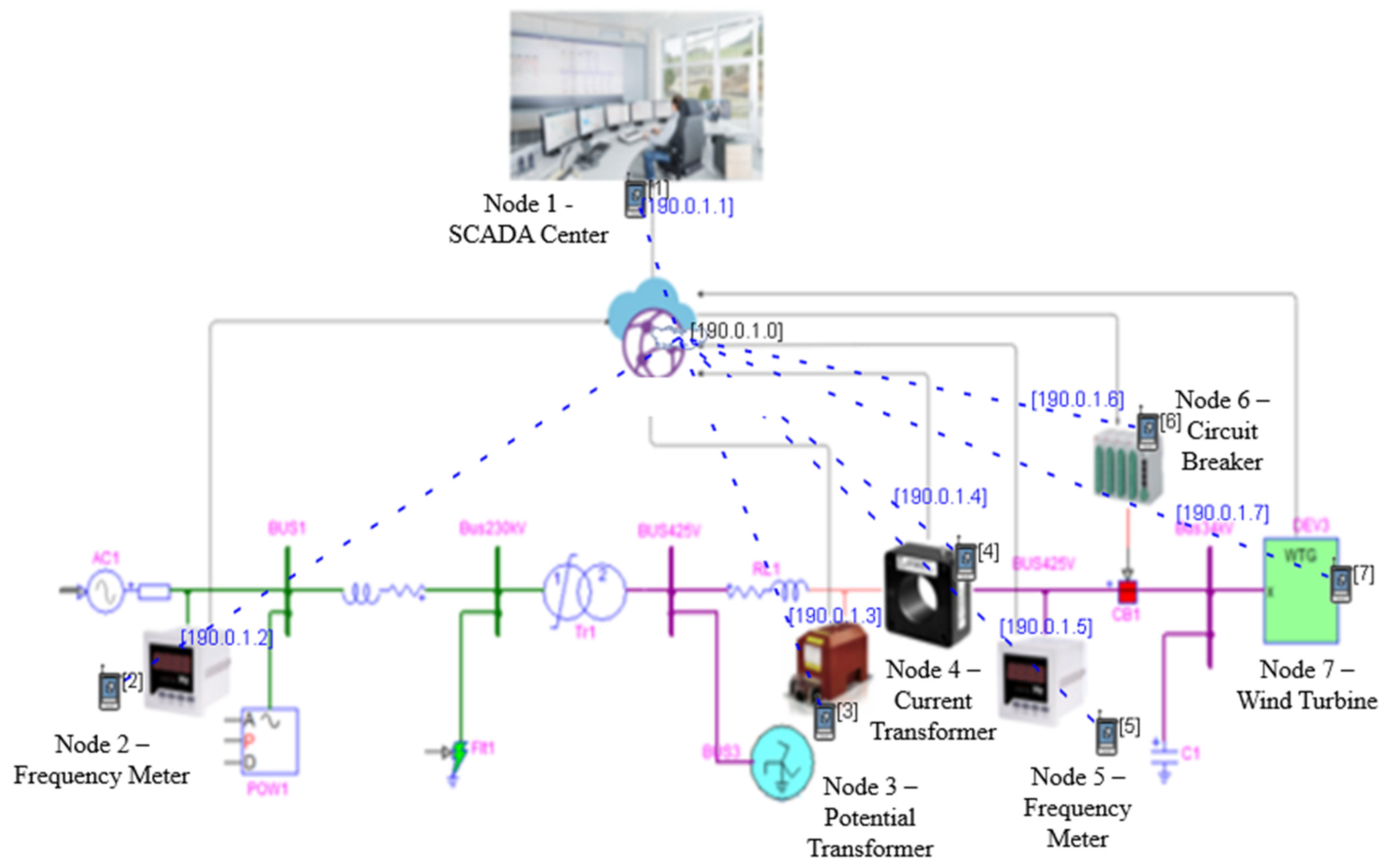
3.1. Power System Layer
3.2. Hardware Layer
3.3. Communication Layer
3.4. Application Layer
4. CPS Testbed Applications
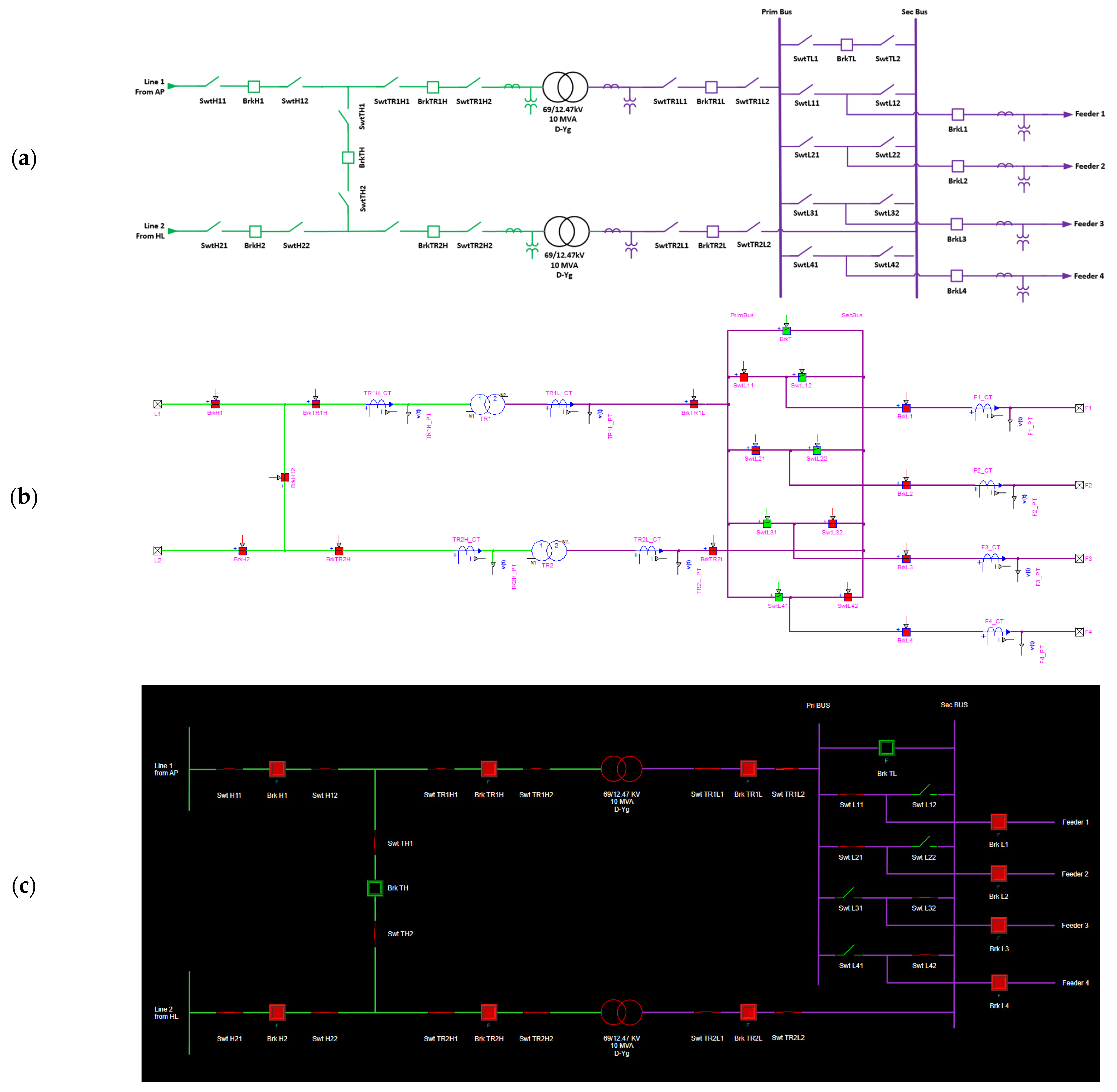
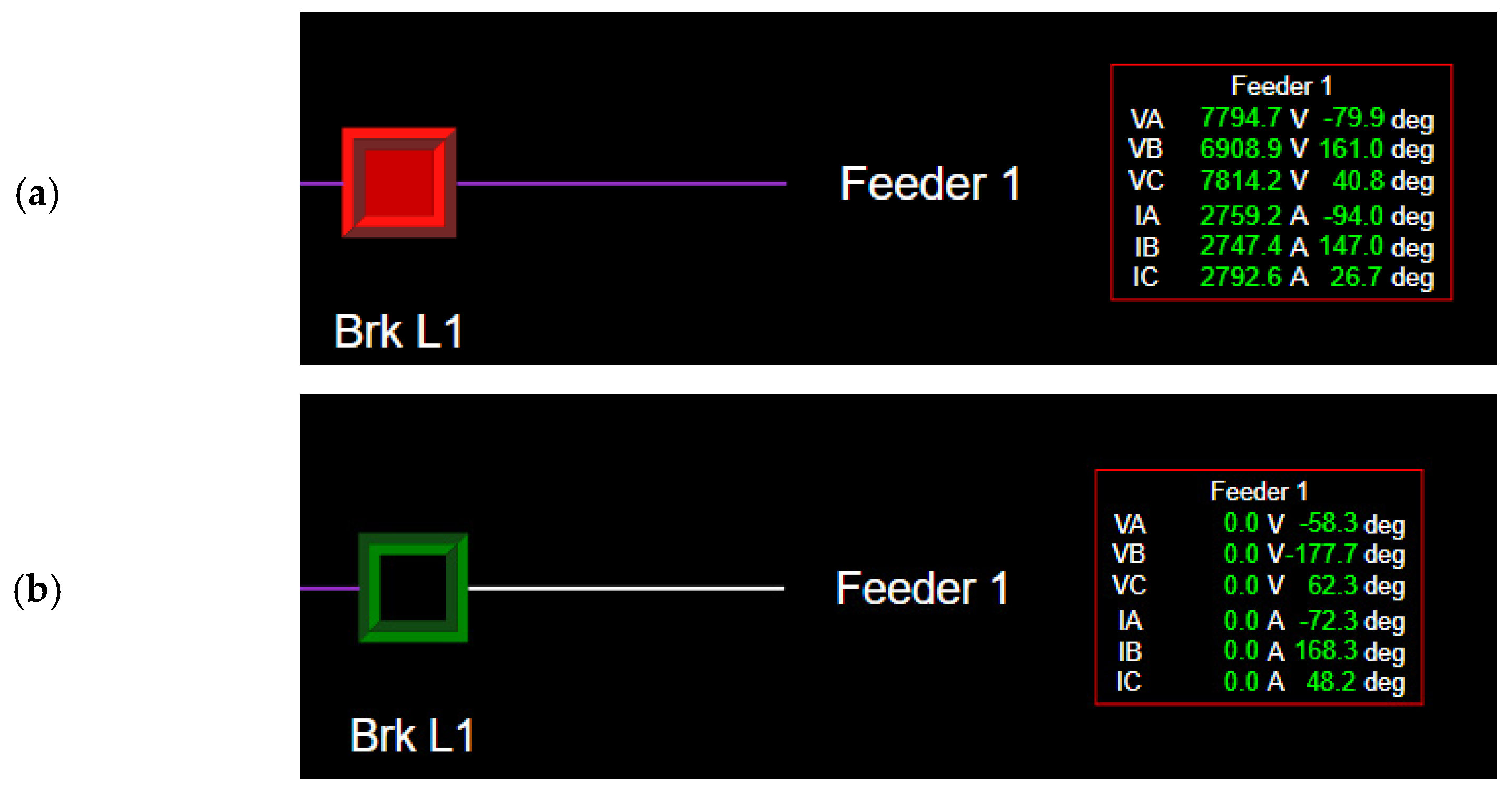
4.1. Module 1: Power Distribution System SCADA Operator Training
4.2. Module 2: General Power System CPS Operator Training
4.2.1. Denial-of-Service Attack
4.2.2. Jammer Attack
4.3. Module 3: Wide-Area Monitoring System (WAMS) CPS Training
4.4. Module 4: Wind Turbine CPS Operator Training
5. Discussion and Future Perspectives
- Module 4.1 can be expanded to include dynamic reconfiguration and self-healing capabilities during faults and/or power blackout events.
- Module 4.2 can incorporate multiple cyberattack scenarios, such as man-in-the-middle (MitM) attacks; false data injection attacks; vulnerability attacks; software-based attacks; passive attacks such as eavesdropping, port scanning, and network scanning; and signal intelligence attacks.
- Module 4.3 can add wide-area synchro-phasor monitoring, protection, and control to simulate the loss of generation or load due to cyberattacks on power system frequency and/or voltages.
- Module 4.4 can be further studied to develop simulation-aided risk assessments, real-time intrusion detection systems, and cyber defense mechanisms on DER-integrated smart grids.
6. Conclusions
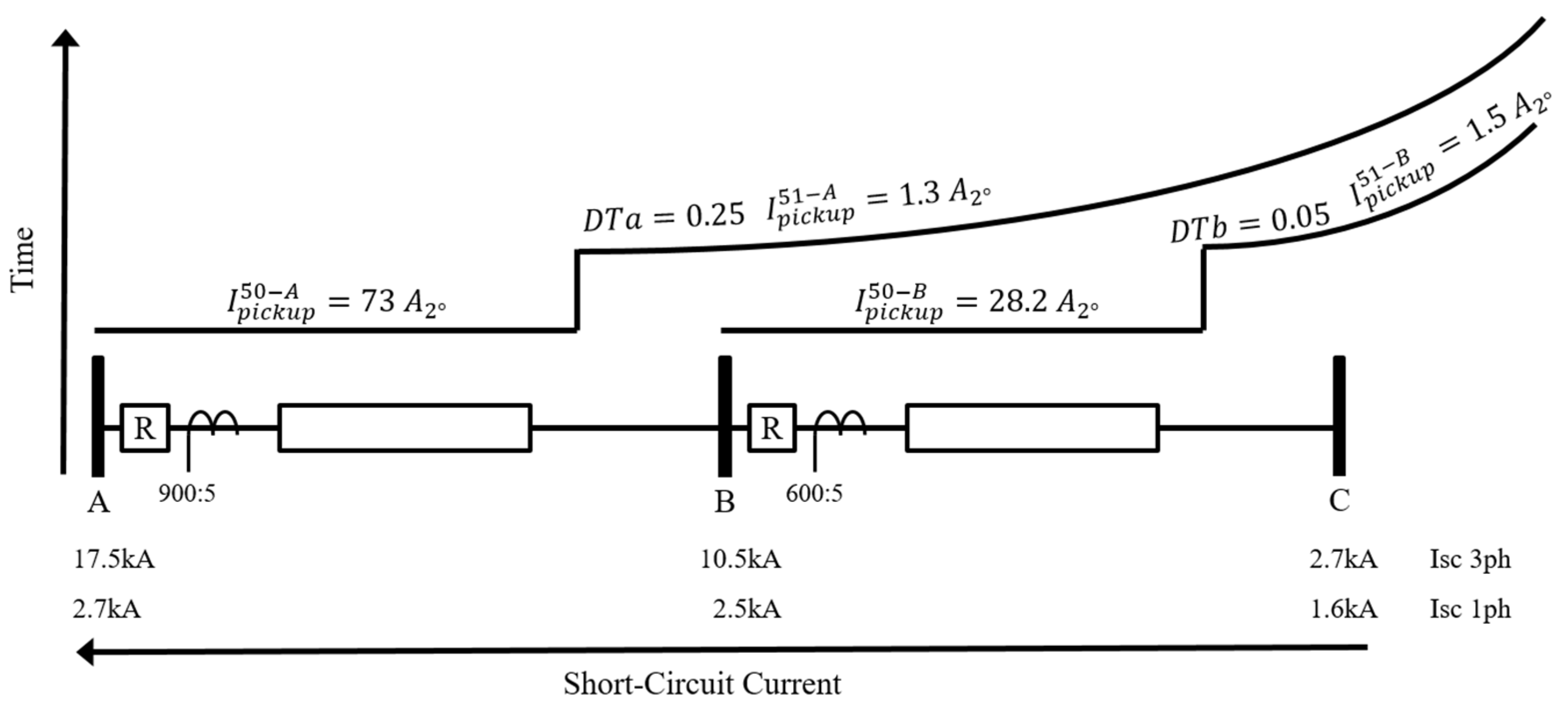
- A protection study on the distribution system was carried out to demonstrate the operation of protection devices and the SCADA system.
- A DOS attack for a wired network and the jammer attack for a wide-area wireless network on a wind farm SCADA operation with the demonstration of node failure and missing packets was carried out.
- The manipulation of phasor signals showed how data from PMUs at remote locations can be manipulated to interrupt wide-area system monitoring.
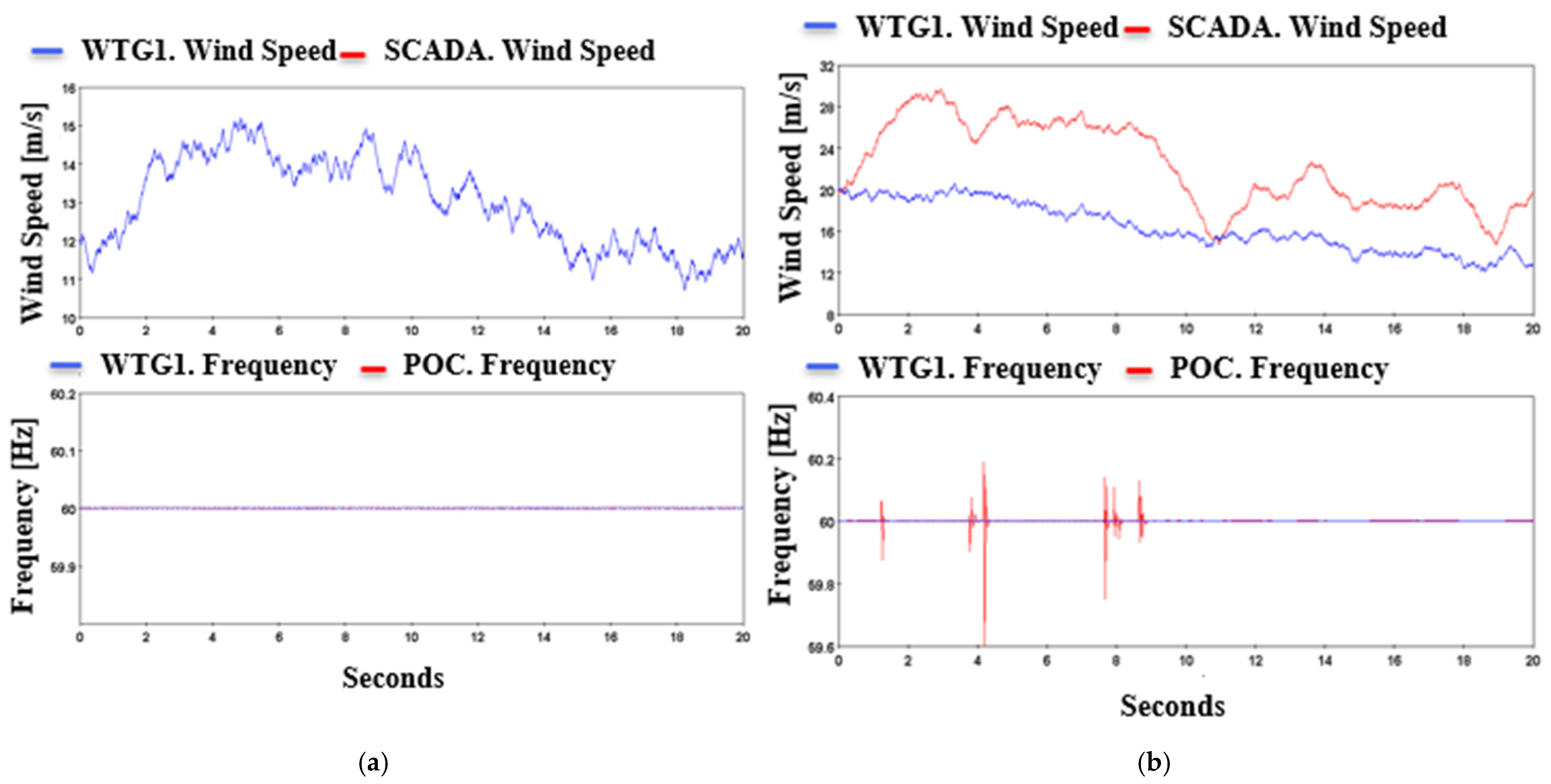
- The final module on wind power plant operation showed the impact of false data injection in control variables and a DOS attack on wind turbine actuators. Results were observed as the misguided SCADA operation was reflected by loss of generation at a larger scale.
- Using secured broadcasting capable of detecting DoS and jamming mechanisms will aid in the design of highly resilient SCADA systems for emerging smart grids that can mitigate cyberattacks while achieving high-level availability.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Li, Z.; Shahidehpour, M.; Aminifar, F.; Alabdulwahab, A.; Al-Turki, Y. Networked Microgrids for Enhancing the Power System Resilience. Proc. IEEE 2017, 105, 1289–1310. [Google Scholar] [CrossRef]
- Ton, D.T.; Smith, M.A. The U.S. Department of Energy′s Microgrid Initiative. Electr. J. 2012, 25, 84–94. [Google Scholar] [CrossRef]
- Reliability Considerations from the Integration of Smart Grid. 2010. Available online: www.nerc.com (accessed on 25 June 2023).
- Palmintier, B.; Krishnamurthy, D.; Top, P.; Smith, S.; Daily, J.; Fuller, J. Design of the HELICS High Performance Transmission Distribution Communication Market. In Proceedings of the 2017 Workshop on Modeling and Simulation of Cyber-Physical Energy Systems (MSCPES), Pittsburgh, PA, USA, 21 April 2017. [Google Scholar]
- Bryson, J.; Gallagher, P.D. NIST Special Publication 1108R2 NIST Framework and Roadmap for Smart Grid Interoperability Standards, Release 2.0; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2012.
- Qi, J.; Hahn, A.; Lu, X.; Wang, J.; Liu, C.-C. Cybersecurity for distributed energy resources and smart inverters. IET Cyber-Physical Syst. Theory Appl. 2016, 1, 28–39. [Google Scholar] [CrossRef]
- Electric Power System Resiliency Challenges and Opportunities Power System Transformation. Available online: https://www.naseo.org/Data/Sites/1/resiliency-white-paper.pdf (accessed on 25 June 2023).
- Zheng, X.; Julien, C.; Podorozhny, R.; Cassez, F. BraceAssertion: Runtime Verification of Cyber-Physical Systems. In Proceedings of the 2015 IEEE 12th International Conference on Mobile Ad Hoc and Sensor Systems, Dallas, TX, USA, 9–22 October 2015; pp. 298–306. [Google Scholar]
- Oyewumi, I.A.; Jillepalli, A.A.; Richardson, P.; Ashrafuzzaman, M.; Johnson, B.K.; Chakhchoukh, Y.; Haney, M.A.; Sheldon, F.T.; de Leon, D.C. ISAAC: The Idaho CPS Smart Grid Cybersecurity Testbed. In Proceedings of the 2019 IEEE Texas Power and Energy Conference (TPEC), College Station, TX, USA, 7–8 February 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Marashi, K.; Sarvestani, S.S.; Hurson, A.R. Consideration of Cyber-Physical Interdependencies in Reliability Modeling of Smart Grids. IEEE Trans. Sustain. Comput. 2017, 3, 73–83. [Google Scholar] [CrossRef]
- Liu, R.; Vellaithurai, C.; Biswas, S.S.; Gamage, T.T.; Srivastava, A.K. Analyzing the Cyber-Physical Impact of Cyber Events on the Power Grid. IEEE Trans. Smart Grid 2015, 6, 2444–2453. [Google Scholar] [CrossRef]
- Konstantinou, C. Cyber-Physical Systems Security Education Through Hands-on Lab Exercises. IEEE Des. Test 2020, 37, 47–55. [Google Scholar] [CrossRef]
- Hahn, A.; Ashok, A.; Sridhar, S.; Govindarasu, M. Cyber-Physical Security Testbeds: Architecture, Application, and Evaluation for Smart Grid. IEEE Trans. Smart Grid 2013, 4, 847–855. [Google Scholar] [CrossRef]
- Cui, H.; Li, F.; Tomsovic, K. Cyber-physical system testbed for power system monitoring and wide-area control verification. IET Energy Syst. Integr. 2020, 2, 32–39. [Google Scholar] [CrossRef]
- Zhou, X.; Gou, X.; Huang, T.; Yang, S. Review on Testing of Cyber Physical Systems: Methods and Testbeds. IEEE Access 2018, 6, 52179–52194. [Google Scholar] [CrossRef]
- Tong, H.; Ni, M.; Zhao, L.; Li, M. Flexible hardware-in-the-loop testbed for cyber physical power system simulation. IET Cyber-Physical Syst. Theory Appl. 2019, 4, 374–381. [Google Scholar] [CrossRef]
- Cintuglu, M.H.; Mohammed, O.A.; Akkaya, K.; Uluagac, A.S. A Survey on Smart Grid Cyber-Physical System Testbeds. IEEE Commun. Surv. Tutorials 2016, 19, 446–464. [Google Scholar] [CrossRef]
- McLaughlin, S.; Konstantinou, C.; Wang, X.; Davi, L.; Sadeghi, A.-R.; Maniatakos, M.; Karri, R. The Cybersecurity Landscape in Industrial Control Systems. Proc. IEEE 2016, 104, 1039–1057. [Google Scholar] [CrossRef]
- Xie, J.; Bedoya, J.C.; Liu, C.-C.; Hahn, A.; Kaur, K.J.; Singh, R. New Educational Modules Using a Cyber-Distribution System Testbed. IEEE Trans. Power Syst. 2018, 33, 5759–5769. [Google Scholar] [CrossRef]
- Marwedel, P.; Mitra, T.; Grimheden, M.E.; Andrade, H.A. Survey on Education for Cyber-Physical Systems. IEEE Des. Test 2020, 37, 56–70. [Google Scholar] [CrossRef]
- Poudel, S.; Ni, Z.; Malla, N. Real-time cyber physical system testbed for power system security and control. Int. J. Electr. Power Energy Syst. 2017, 90, 124–133. [Google Scholar] [CrossRef]
- Gao, H.; Peng, Y.; Jia, K.; Wen, Z.; Li, H. Cyber-Physical Systems Testbed Based on Cloud Computing and Software Defined Network. In Proceedings of the 2015 International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), Adelaide, Australia, 23–25 September 2015; pp. 337–340. [Google Scholar] [CrossRef]
- National Scada Test Bed: Fact Sheet. Available online: https://www.energy.gov (accessed on 25 June 2023).
- Wlazlo, P.; Sahu, A.; Mao, Z.; Huang, H.; Goulart, A.; Davis, K.; Zonouz, S. Man-in-the-middle attacks and defence in a power system cyber-physical testbed. IET Cyber-Physical Syst. Theory Appl. 2021, 6, 164–177. [Google Scholar] [CrossRef]
- Chen, B.; Butler-Purry, K.L.; Goulart, A.; Kundur, D. Implementing a real-time cyber-physical system test bed in RTDS and OPNET. In Proceedings of the 2014 North American Power Symposium (NAPS), Pullman, WA, USA, 7–9 September 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Georg, H.; Muller, S.C.; Dorsch, N.; Rehtanz, C.; Wietfeld, C. INSPIRE: Integrated Co-Simulation of Power and ICT Systems for Real-Time Evaluation. In Proceedings of the 2013 IEEE International Conference on Smart Grid Communications (SmartGridComm), Vancouver, BC, Canada, 21–24 October 2013; pp. 576–581. [Google Scholar] [CrossRef]
- HELICS. Tools With HELICS Support. 2020. Available online: https://docs.helics.org/en/latest/Tools_using_HELICS.html (accessed on 25 June 2023).
- Sridhar, S.; Ashok, A.; Mylrea, M.; Pal, S.; Rice, M.; Gourisetti, S.N.G. A Testbed Environment for Buildings-to-Grid Cyber Resilience Research and Development. In Proceedings of the 2017 Resilience Week (RWS), Wilmington, DE, USA, 18–22 September 2017; pp. 12–17. [Google Scholar] [CrossRef]
- Mo, Y.; Kim, T.H.-J.; Brancik, K.; Dickinson, D.; Lee, H.; Perrig, A.; Sinopoli, B. Cyber–Physical Security of a Smart Grid Infrastructure. Proc. IEEE 2012, 100, 195–209. [Google Scholar] [CrossRef]
- Dondossola, G.; Terruggia, R. Cyber Security of Smart Grid Communications: Risk Analysis and Experimental Testing. Power Syst. 2015, 79, 169–193. [Google Scholar] [CrossRef]
- Mohagheghi, S.; Stoupis, J.; Wang, Z. Communication Protocols and Networks for Power Systems-Current Status and Future Trends. In Proceedings of the 2009 IEEE/PES Power Systems Conference and Exposition, Seattle, WA, USA, 15–18 March 2009; pp. 1–9. [Google Scholar] [CrossRef]
- SCALABLE Network Technologies. SCALABLE Network Technologies Cyber Security Solutions for Critical Infrastructure. Available online: https://www.keysight.com/us/en/assets/3122-1399/technical-overviews/Cyber-Security-Solutions-for-Critical-Infrastructure.pdf (accessed on 25 June 2023).
- Hong, J.; Chen, Y.; Liu, C.-C.; Govindarasu, M. Cyber-Physical Security Testbed for Substations in a Power Grid. Power Syst. 2015, 79, 261–301. [Google Scholar] [CrossRef]
- Vellaithurai, C.B.; Biswas, S.S.; Liu, R.; Srivastava, A. Real Time Modeling and Simulation of Cyber-Power System. Power Syst. 2015, 79, 43–74. [Google Scholar] [CrossRef]
- Yamashita, K.; Ten, C.-W.; Rho, Y.; Wang, L.; Wei, W.; Ginter, A. Measuring Systemic Risk of Switching Attacks Based on Cybersecurity Technologies in Substations. IEEE Trans. Power Syst. 2020, 35, 4206–4219. [Google Scholar] [CrossRef]
- Hong, J.; Nuqui, R.F.; Kondabathini, A.; Ishchenko, D.; Martin, A. Cyber Attack Resilient Distance Protection and Circuit Breaker Control for Digital Substations. IEEE Trans. Ind. Inform. 2019, 15, 4332–4341. [Google Scholar] [CrossRef]
- MITRE Enterprise Engineering. Crown Jewels Analysis. Available online: https://www.mitre.org/publications/systems-engineering-guide/enterprise-engineering/systems-engineering-for-mission-assurance/crown-jewels-analysis (accessed on 10 October 2020).
- Salunkhe, O.; Gopalakrishnan, M.; Skoogh, A.; Fasth-Berglund, A. Cyber-Physical Production Testbed: Literature Review and Concept Development. Procedia Manuf. 2018, 25, 2–9. [Google Scholar] [CrossRef]
- Vellaithurai, C.B.; Biswas, S.S.; Srivastava, A.K. Development and Application of a Real-Time Test Bed for Cyber–Physical System. IEEE Syst. J. 2015, 11, 1–12. [Google Scholar] [CrossRef]
- Kurt, M.N.; Yilmaz, Y.; Wang, X. Real-Time Detection of Hybrid and Stealthy Cyber-Attacks in Smart Grid. IEEE Trans. Inf. Forensics Secur. 2018, 14, 498–513. [Google Scholar] [CrossRef]
- Gambier, A. Real-time Control and Hardware-in-the-loop Simulation for Educational Purposes of Wind Energy Systems. IFAC-PapersOnLine 2020, 53, 17344–17349. [Google Scholar] [CrossRef]
- Yang, Y.; Pranggono, B.; Littler, T.; Yao, Z.; Im, E.G.; McLaughlin, K.; Wang, H.; Sezer, S. Man-in-the-middle attack test-bed investigating cyber-security vulnerabilities in smart grid SCADA systems. In Proceedings of the International Conference on Sustainable Power Generation and Supply (SUPERGEN 2012), Hangzhou, China, 8–9 September 2012. [Google Scholar] [CrossRef]
- Gupta, K.; Sahoo, S.; Panigrahi, B.K.; Blaabjerg, F.; Popovski, P. On the Assessment of Cyber Risks and Attack Surfaces in a Real-Time Co-Simulation Cybersecurity Testbed for Inverter-Based Microgrids. Energies 2021, 14, 4941. [Google Scholar] [CrossRef]
- Zhang, L.; Li, S.; Wihl, L.; Kazemtabrizi, M.; Ali, S.O.; Paquin, J.; Labbé, S. Cybersecurity Study of Power System Utilizing Advanced CPS Simulation Tools. Available online: http://conference-americas.pacw.org/ (accessed on 25 June 2023).
- REAL-TIME SIMULATION. Available online: https://www.opal-rt.com/ (accessed on 10 March 2022).
- Bian, D.; Kuzlu, M.; Pipattanasomporn, M.; Rahman, S.; Wu, Y. Real-time co-simulation platform using OPAL-RT and OPNET for analyzing smart grid performance. In Proceedings of the IEEE Power and Energy Society General Meeting, Denver, CO, USA, 26–30 July 2015; pp. 1–5. [Google Scholar] [CrossRef]
- Keysight. EXata Network Modeling—Critical Infrastructure. Keysight. Available online: https://www.keysight.com/us/en/product/SN050ECPA/exata-network-modeling-critical-infrastructure.html (accessed on 25 June 2023).
- SCADA SurvalentONE. Available online: https://www.survalent.com/adms-platform-overview/ (accessed on 10 March 2022).
- Padullaparti, H.; Pratt, A.; Mendoza, I.; Tiwari, S.; Baggu, M.; Bilby, C.; Ngo, Y. Peak Load Management in Distribution Systems Using Legacy Utility Equipment and Distributed Energy Resources Preprint. 2021. Available online: www.nrel.gov/publications (accessed on 25 June 2023).
- University of Nebraska—Lincoln, IEEE Region 4, IEEE Computer Society, IEEE Communications Society, IEEE Power & Energy Society, and Institute of Electrical and Electronics Engineers. In Proceedings of the 2017 IEEE International Conference on Electro Information Technology (EIT), Lincoln, NE, USA, 14–17 May 2017.
- Ritchie, J.; Robertson, C.F.R. A Comparison of Phasor Communication Protocols and the Streaming Telemetry Transport Protocol (STTP) for the Transfer of Synchrophasor and Other Streaming Data. 2019. Available online: https://gridprotectionalliance.org (accessed on 25 June 2023).
- Kite, D.; Jenkins, R. Automating Protection System Monitoring and Verification With the SEL RTAC. pp. 1–16. Available online: https://selinc.com/api/download/112761/?lang=en (accessed on 25 June 2023).
- Paithankar, V.G.; Bhide, S.R. Fundamentals of Power System Protection, 2nd ed.; PHI Learning Pvt. Ltd.: Delhi, India, 2022. [Google Scholar]
- IEEE Std C37.2-2008; IEEE Standard For Electrical Power System Device Function Numbers, Acronyms, And Contact Designations. Available online: https://www.academia.edu/9761872/IEEE_Standard_for_Electrical_Power_System_Device_Function_Numbers_IEEE_Std_C37_2_2008 (accessed on 25 June 2023).
- Ahmad, A.; AbuHour, Y.; Alghanim, F. A Novel Model for Distributed Denial of Service Attack Analysis and Interactivity. Symmetry 2021, 13, 2443. [Google Scholar] [CrossRef]
- Cortés-Leal, A.; Del-Valle-Soto, C.; Cardenas, C.; Valdivia, L.J.; Del Puerto-Flores, J.A. Performance Metric Analysis for a Jamming Detection Mechanism under Collaborative and Cooperative Schemes in Industrial Wireless Sensor Networks. Sensors 2022, 22, 178. [Google Scholar] [CrossRef]
- Zhao, J.; Netto, M.; Mili, L. A Robust Iterated Extended Kalman Filter for Power System Dynamic State Estimation. IEEE Trans. Power Syst. 2017, 32, 3205–3216. [Google Scholar] [CrossRef]
- Hojabri, M.; Dersch, U.; Papaemmanouil, A.; Bosshart, P. A Comprehensive Survey on Phasor Measurement Unit Applications in Distribution Systems. Energies 2019, 12, 4552. [Google Scholar] [CrossRef]
- Bhamare, Y. Utilization of IEC 61850 GOOSE Messaging in Protection Applications in Distribution Network. Available online: https://api.semanticscholar.org/CorpusID:8309387 (accessed on 25 June 2023).
- Katsigiannis, Y.A.; Stavrakakis, G.S. Estimation of wind energy production in various sites in Australia for different wind turbine classes: A comparative technical and economic assessment. Renew. Energy 2014, 67, 230–236. [Google Scholar] [CrossRef]
- Jayachandran, M.; Reddy, C.R.; Padmanaban, S.; Milyani, A.H. Operational planning steps in smart electric power delivery system. Sci. Rep. 2021, 11, 17250. [Google Scholar] [CrossRef] [PubMed]




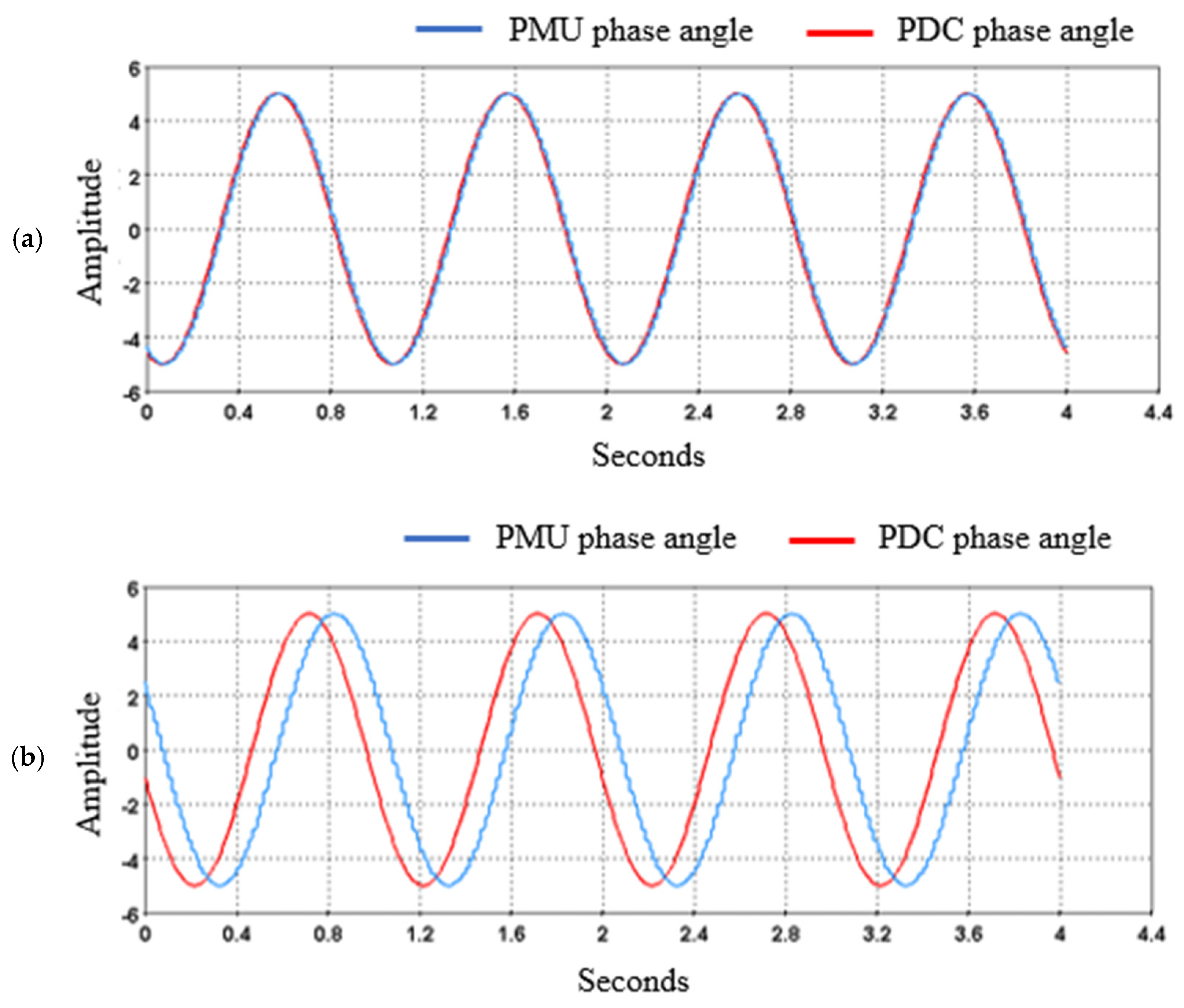
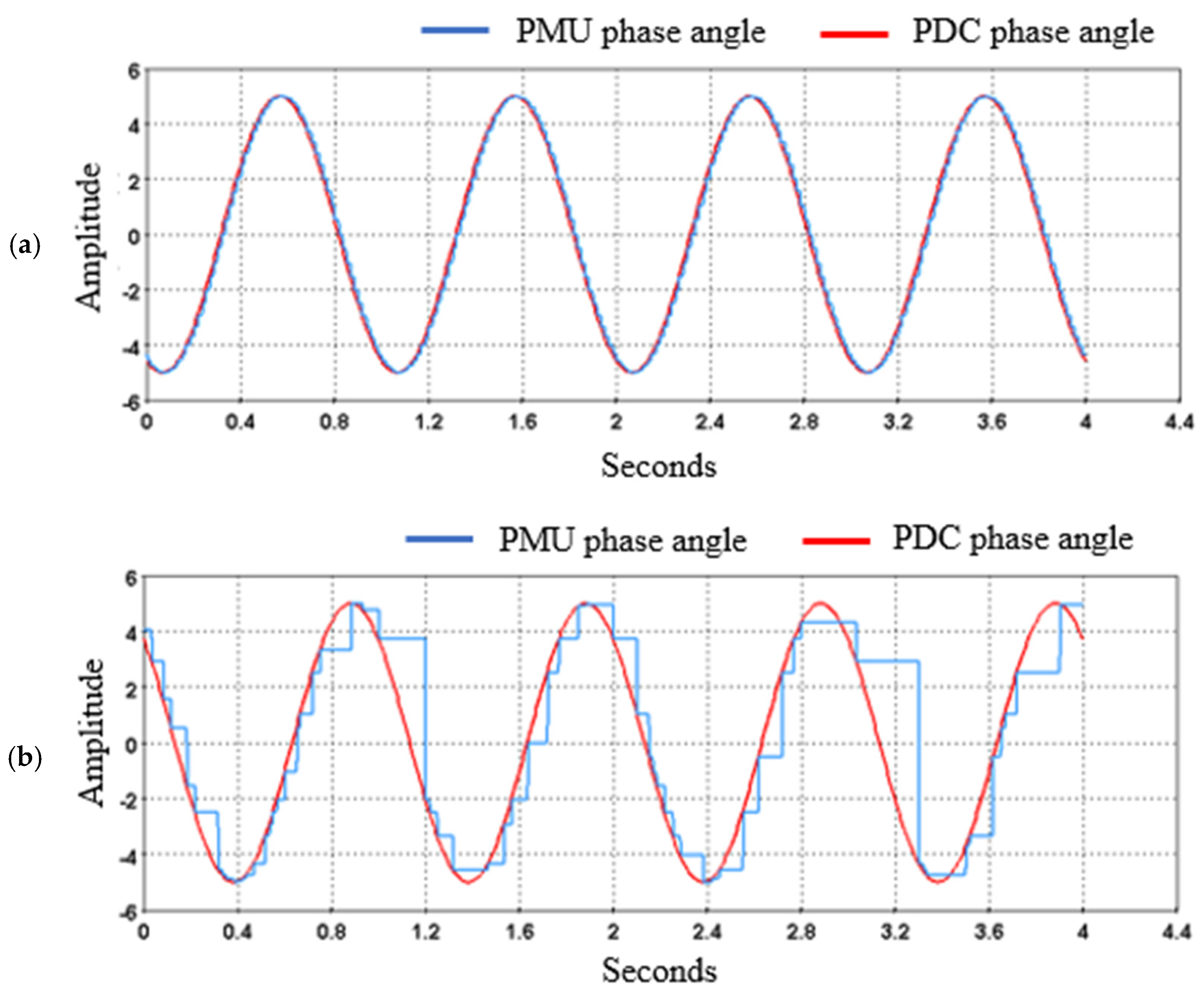


| Literature | Year | Research Topic | Novelty | Co-Simulation | Real Time | IDS |
|---|---|---|---|---|---|---|
| [11] | 2015 | The impact of cyberattacks on power grids was studied in a simulated power network and an emulated communication network. | Reconfigurable testbed | No | No | No |
| [39] | 2015 | Development and application of real-time testbed for CPS | Real-time simulation | No | Yes | No |
| [18] | 2016 | ICS for the deployment of cybersecurity methods was studied using different attack scenarios. | Emphasizes the optimal distribution of security protection in large legacy ICSs | No | No | No |
| [40] | 2018 | Detection of stealthy cyberattacks in the smart grid | Study of hybrid and stealthy attacks in a power system | No | Yes | Yes |
| [41] | 2020 | CPS testbed for wind energy systems | HIL simulation | Yes | Yes | No |
| [42] | 2021 | CPS testbed studying MITM attack detection and defense | FDIA and MITM attacks simulated in the data link layer | No | No | Yes |
| [43] | 2021 | Real-time co-simulation testbed for inverter-based microgrids | Use of SEL-3530 with OPAL-RT | Yes | Yes | No |
| [44] | 2021 | A real-time CPS testbed to study cyber threats and risk assessments | Use of EXata CPS for attack simulation in real time | Yes | Yes | No |
| Bus | [A] | [kA] | [kA] |
|---|---|---|---|
| A | 115 | 17.5 | 2.7 |
| B | 90 | 10.5 | 2.5 |
| C | 43 | 2.7 | 1.6 |
| Property | Value | Property | Value |
|---|---|---|---|
| Attack type | DOS | Attack type | Jammer |
| Victim node | Node 2 | Jammer node | Node 15 |
| Victim IP | 10.10.1.33 | Start time | 1 |
| DOS attack type | Basic attack | End time | 25 |
| Victim port | 7200 | Scanner index | 0 |
| Configure | Interval | Jamming power | Power (dBm) |
| Interval | 0.1 s | Power | 100 dBm |
| Duration | 30 s | Silent jammer | Yes |
| Ramp-up time | 0 s | Ramp-up time | 0 s |
| Data rate | 1 Mbps |
| Property | Attack 1 | Attack 2 |
|---|---|---|
| Attack type | Packet multiply attack | Delay attack |
| Attacker node | Node 2 (PDC node) | Node 2 (PDC node) |
| Layer type | Network | Network |
| Destination port | 7200 | 7200 |
| MODP attack type | Multiply | Delay |
| Value | 2 | 100 ms |
| Number of bytes | 2 | - |
| Start byte | 112 | - |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chamana, M.; Bhatta, R.; Schmitt, K.; Shrestha, R.; Bayne, S. An Integrated Testbed for Power System Cyber-Physical Operations Training. Appl. Sci. 2023, 13, 9451. https://doi.org/10.3390/app13169451
Chamana M, Bhatta R, Schmitt K, Shrestha R, Bayne S. An Integrated Testbed for Power System Cyber-Physical Operations Training. Applied Sciences. 2023; 13(16):9451. https://doi.org/10.3390/app13169451
Chicago/Turabian StyleChamana, Manohar, Rabindra Bhatta, Konrad Schmitt, Rajendra Shrestha, and Stephen Bayne. 2023. "An Integrated Testbed for Power System Cyber-Physical Operations Training" Applied Sciences 13, no. 16: 9451. https://doi.org/10.3390/app13169451






