Cybersecurity for Blockchain-Based IoT Systems: A Review
Abstract
:1. Introduction
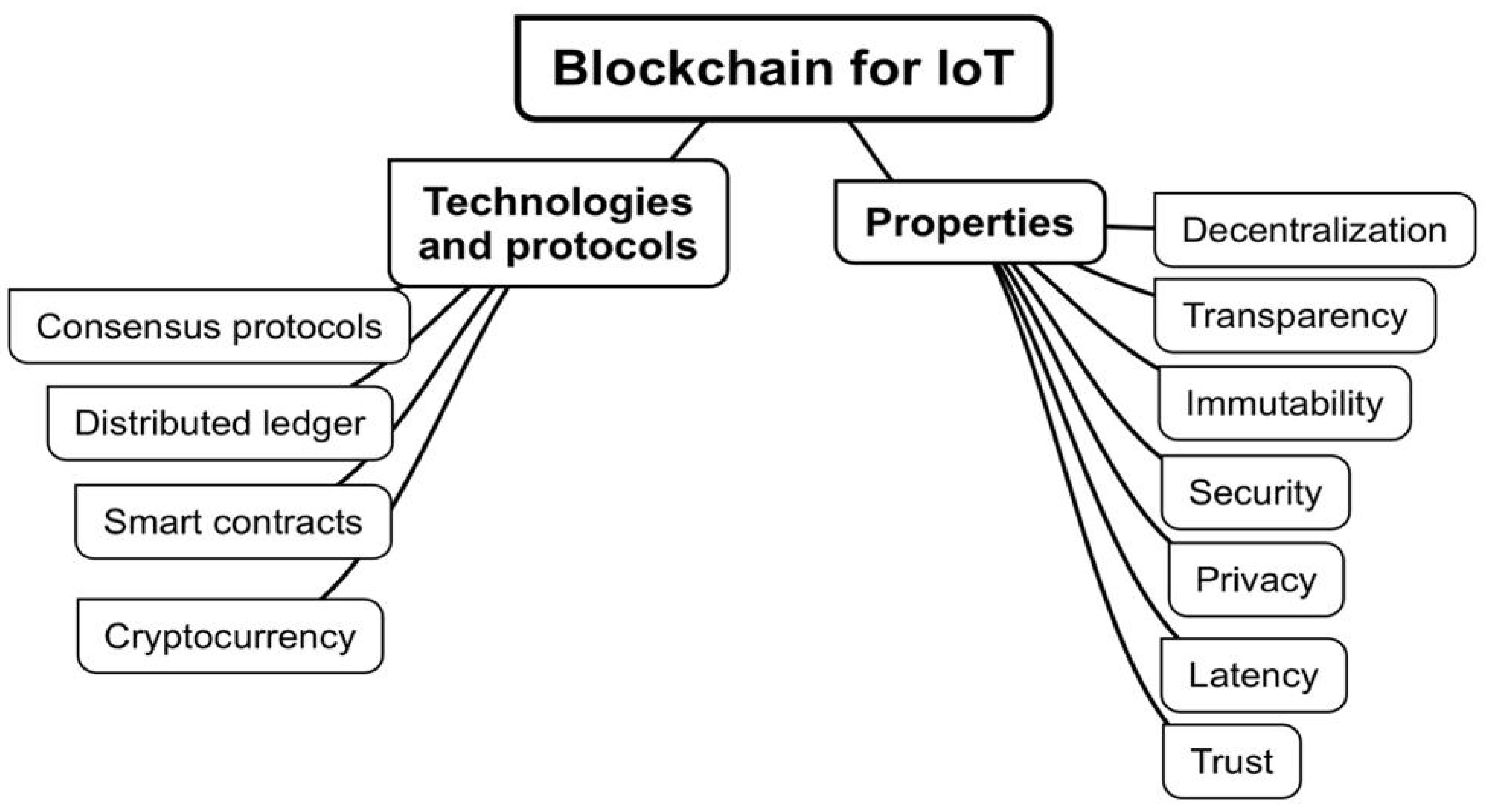
- Decentralization: Blockchain is a decentralized technology, which means that it is not controlled by any single entity [9]. This makes it difficult for hackers to target and attack. In a centralized system, all data is stored on a single server, making it a single point of failure. In a decentralized system, data is stored on multiple nodes, which makes it more difficult for hackers to gain access to all of the data.
- Transparency: Blockchain is a transparent technology, which means that all transactions are recorded on the blockchain and are visible to all participants [10]. This makes it difficult for hackers to commit fraud or tamper with data. In a centralized system, transactions are not always transparent, making it difficult to track down fraud or identify those responsible for tampering with data.
- Consensus Mechanisms: Blockchain uses consensus mechanisms to validate transactions. Consensus mechanisms are algorithms that ensure that all participants in the network agree on the validity of a transaction [11]. This makes it difficult for hackers to manipulate the network and approve fraudulent transactions. In a centralized system, a single entity is responsible for validating transactions, making it easier for hackers to manipulate the system.
- Cryptographic Techniques: Blockchain uses cryptographic techniques to secure data. Cryptographic techniques are algorithms that encrypt data and make it unreadable to unauthorized users [12]. This makes it difficult for hackers to steal data from the blockchain. In a centralized system, data is often stored in plain text, making it easier for hackers to steal data.
- Smart Contracts: Blockchain can be used to create smart contracts, which are self-executing contracts stored on the blockchain. Smart contracts are tamper-proof and irreversible, enabling automation and enforcement of agreements between parties [13]. This can improve the efficiency and security of IoT systems.
- Device Layer: This layer consists of the IoT devices themselves, such as sensors, actuators, and embedded systems. These devices collect and generate data, which is then transmitted to the blockchain network for processing and storage.
- Communication Layer: The communication layer facilitates the transmission of data between IoT devices and the blockchain network. It encompasses protocols, standards, and network infrastructure that enable secure and reliable communication.
- Blockchain Layer: The blockchain layer is the core component of the system and comprises the distributed ledger and associated consensus mechanisms. It records and validates transactions, ensuring the integrity and immutability of the data stored on the blockchain.
- Smart Contract Layer: This layer involves the implementation of smart contracts, which are self-executing contracts with predefined rules and conditions. Smart contracts enable automation, enforce business logic, and facilitate secure interactions between IoT devices and the blockchain network.
- Application Layer: The application layer includes the various applications and services built on top of the blockchain-based IoT system. These applications leverage the secure and transparent nature of the underlying blockchain to provide functionalities such as data analytics, supply chain management, and decentralized control.
2. Research Methodology
3. Literature Survey
4. Challenges of Using Blockchain for Securing IoT Networks
4.1. IoT Device Security
4.1.1. Device Authentication and Authorization
4.1.2. Device Integrity and Firmware Updates
4.1.3. Secure Communication and Data Privacy
4.1.4. Physical Security
4.2. Blockchain Security
4.2.1. Consensus Mechanisms
4.2.2. Scalability and Performance
4.2.3. Privacy and Confidentiality
4.2.4. Smart Contract Security
4.2.5. Governance and Consensus among Multiple Parties
4.2.6. Regulatory and Legal Challenges
4.3. Network Security
4.3.1. Distributed Denial of Service (DDoS) Attacks
4.3.2. Sybil Attacks:
4.3.3. Rogue Device Detection
4.3.4. Interoperability and Standardization
5. Discussion
5.1. IoT Security and Blockchain
- Data breaches: IoT devices often collect and store sensitive data, such as user personal information, location data, and financial data. If these data are compromised, they could be used for identity theft, fraud, or other malicious activities.
- Malware attacks: IoT devices are often poorly designed and maintained, making them vulnerable to malware attacks. Malware could be used to steal data, take control of devices, or disrupt operations.
- Physical attacks: IoT devices are often located in remote or unsecured locations, making them vulnerable to physical attacks. Attackers could steal or damage devices, or disrupt their operations.
- Encryption: Blockchain can be used to encrypt data stored on IoT devices, making it more difficult for unauthorized users to access.
- Authentication: Blockchain can be used to authenticate users and devices, ensuring that only authorized users have access to the system.
- Access control: Blockchain can be used to control who has access to data and devices, and what they can do with it.
- Vulnerability management: Blockchain can be used to identify and mitigate vulnerabilities in IoT systems, making them less susceptible to attack.
- XAI: XAI techniques aim to explain the inner workings, decisions, and outcomes of complex AI systems in an interpretable and transparent manner. This is particularly valuable for blockchain-based IoT systems due to several reasons [40]:
- –
- Enhancing accountability: By understanding how blockchain decisions are made, stakeholders can ensure the system is functioning correctly and accountable for its actions. This builds user trust.
- –
- Debugging issues: Interpretable explanations of the blockchain’s behavior can help debug any issues within the system and identify potential vulnerabilities.
- –
- Adapting to changes: Explanations provide insight into how the system is performing, which can guide necessary changes and updates over time.
- –
- Deterring attacks: Increased transparency into the blockchain network’s operations can act as a deterrent against potential attackers by making exploitation more difficult.
- Model summarization: This technique condenses complex models into simpler, interpretable representations. This can be done by using natural language descriptions, decision trees, or other techniques.
- Feature attribution: This technique assigns “importance scores” to features to indicate their relative impact on outcomes. This can be done by using techniques such as sensitivity analysis or local interpretable model-agnostic explanations (LIME).
- Counterfactual explanations: This technique indicates how outcomes would change under different conditions. This can be done by using techniques such as counterfactual regret minimization or counterfactual explanations.
- Causal modeling: This technique uses causal graphs to represent causal relationships within the system. This can be done by using techniques such as structural causal models or Bayesian networks.
- Lack of standardization: There is currently no standard for XAI, which can make it difficult to compare and evaluate different XAI techniques.
- Data privacy: XAI often requires access to sensitive data, which can raise privacy concerns.
- Computational complexity: XAI can be computationally expensive, which can limit its scalability.
5.2. Blockchain for IoT: Potential Applications for Smart Cities
5.2.1. Data Integrity and Security
5.2.2. Identity and Access Management
5.2.3. Smart Contracts and Automation
5.2.4. Supply Chain Management
5.2.5. Decentralized Infrastructure and Connectivity
5.2.6. Microtransactions and Tokenization
6. Open Issues and Future Directions
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Dorri, A.; Kanhere, S.S.; Jurdak, R. Blockchain in Internet of Things: Challenges and solutions. arXiv 2016, arXiv:1608.05187. [Google Scholar]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Future Gener. Comput. Syst. 2020, 107, 841–853. [Google Scholar] [CrossRef] [Green Version]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of blockchain technology: Architecture, consensus, and future trends. In Proceedings of the IEEE international congress on big data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar]
- Panarello, A.; Tapas, N.; Merlino, G.; Longo, F.; Puliafito, A. Blockchain and IoT integration: A systematic survey. Sensors 2018, 18, 2575. [Google Scholar] [CrossRef] [Green Version]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, 13–17 March 2017; pp. 618–623. [Google Scholar]
- Islam, M.R.; Rahman, M.M.; Mahmud, M.; Rahman, M.A.; Mohamad, M.H.S. A review on blockchain security issues and challenges. In Proceedings of the IEEE 12th Control and System Graduate Research Colloquium (ICSGRC), Shah Alam, Malaysia, 7 August 2021; pp. 227–232. [Google Scholar]
- Raju, M.C.; Paul, K.S. A Comprehensive Review of Cyber Security in Blockchain-Based IoT. Math. Stat. Eng. Appl. 2022, 71, 10646–10659. [Google Scholar]
- Mahmood, S.; Chadhar, M.; Firmin, S. Cybersecurity challenges in blockchain technology: A scoping review. Hum. Behav. Emerg. Technol. 2022, 2022, 7384000. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef] [Green Version]
- Maple, C. Security and privacy in the internet of things. J. Cyber Policy 2017, 2, 155–184. [Google Scholar] [CrossRef] [Green Version]
- Deep, S.; Zheng, X.; Jolfaei, A.; Yu, D.; Ostovari, P.; Kashif Bashir, A. A survey of security and privacy issues in the Internet of Things from the layered context. Trans. Emerg. Telecommun. Technol. 2022, 33, e3935. [Google Scholar] [CrossRef] [Green Version]
- Qian, Y.; Jiang, Y.; Chen, J.; Zhang, Y.; Song, J.; Zhou, M.; Pustišek, M. Towards decentralized IoT security enhancement: A blockchain approach. Comput. Electr. Eng. 2018, 72, 266–273. [Google Scholar] [CrossRef]
- Moin, S.; Karim, A.; Safdar, Z.; Safdar, K.; Ahmed, E.; Imran, M. Securing IoTs in distributed blockchain: Analysis, requirements and open issues. Future Gener. Comput. Syst. 2019, 100, 325–343. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K.; Imran, M. Blockchain-based secure and privacy-preserving framework for smart healthcare systems. IEEE Access 2019, 7, 116258–116273. [Google Scholar]
- Joshi, A.P.; Han, M.; Wang, Y. A survey on security and privacy issues of blockchain technology. Math. Found. Comput. 2018, 1, 121. [Google Scholar] [CrossRef] [Green Version]
- Deshmukh, A.; Sreenath, N.; Tyagi, A.K.; Abhichandan, U.V.E. Blockchain Enabled Cyber Security: A Comprehensive Survey. In Proceedings of the International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 25–27 January 2022; pp. 1–6. [Google Scholar]
- Algarni, S.; Eassa, F.; Almarhabi, K.; Almalaise, A.; Albassam, E.; Alsubhi, K.; Yamin, M. Blockchain-based secured access control in an IoT system. Appl. Sci. 2021, 11, 1772. [Google Scholar] [CrossRef]
- Rajawat, A.S.; Rawat, R.; Barhanpurkar, K.; Shaw, R.N.; Ghosh, A. Blockchain-based model for expanding IoT device data security. In Advances in Applications of Data-Driven Computing; Springer: Singapore, 2021; pp. 61–71. [Google Scholar]
- Haleem, A.; Javaid, M.; Singh, R.P.; Suman, R.; Rab, S. Blockchain technology applications in healthcare: An overview. Int. J. Intell. Netw. 2021, 2, 130–139. [Google Scholar] [CrossRef]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 Statement: An Updated Guideline for Reporting Systematic Reviews. Int. J. Surg. 2021, 88, 105906. [Google Scholar] [CrossRef]
- Le, T.V.; Hsu, C.L. A systematic literature review of blockchain technology: Security properties, applications and challenges. J. Internet Technol. 2021, 22, 789–802. [Google Scholar]
- Al-Farsi, S.; Rathore, M.M.; Bakiras, S. Security of blockchain-based supply chain management systems: Challenges and opportunities. Appl. Sci. 2021, 11, 5585. [Google Scholar] [CrossRef]
- Badri, S.; Ullah, J.S.; Alghazzawi, D.; Aldhaheri, S.; Pitropakis, N. BIoMT: A Blockchain-Enabled Healthcare Architecture for Information Security in the Internet of Medical Things. Comput. Syst. Sci. Eng. 2023, 46, 3667–3684. [Google Scholar] [CrossRef]
- Shafagh, H.; Burkhalter, L.; Hithnawi, A.; Duquennoy, S. Towards Blockchain-based Auditable Storage and Sharing of IoT Data. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 3 November 2017; pp. 45–50. [Google Scholar]
- Yli-Huumo, J.; Ko, D.; Choi, S.; Park, S.; Smolander, K. Where Is Current Research on Blockchain Technology?—A Systematic Review. PLoS ONE 2016, 11, e0163477. [Google Scholar] [CrossRef] [Green Version]
- Guo, H.; Yu, X. Survey on Blockchain Technology and Its Security. J. Softw. Eng. Appl. 2022, 3, 100067. [Google Scholar] [CrossRef]
- Lin, I.-C.; Liao, T.-C. A Survey of Blockchain Security Issues and Challenges. Int. J. Netw. Secur. Its Appl. 2018, 10, 25–42. [Google Scholar]
- Wylde, V.; Rawindaran, N.; Lawrence, J.; Balasubramanian, R.; Prakash, E.; Jayal, A.; Platts, J. Cybersecurity, Data Privacy and Blockchain: A Review. Comput. Sci. 2022, 3, 127. [Google Scholar] [CrossRef] [PubMed]
- Xu, X.; Weber, I.; Staples, M.; Zhu, L.; Bosch, J.; Bass, L.; Rimba, P. A Taxonomy of Blockchain-Based Systems for Architecture Design. In Proceedings of the 1st IEEE International Conference on Software Architecture (ICSA), Gothenburg, Sweden, 3–7 April 2017; pp. 243–252. [Google Scholar]
- Zou, Y.; Meng, T.; Zhang, P.; Zhang, W.; Li, H. Focus on Blockchain: A Comprehensive Survey on Academic and Application. J. Syst. Sci. Inf. 2018, 6, 238–268. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Patsakis, C. A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telemat. Inform. 2019, 36, 55–81. [Google Scholar] [CrossRef]
- Conoscenti, M.; Vetro, A.; De Martin, J.C. Blockchain for the Internet of Things: A systematic literature review. In Proceedings of the IEEE/ACS 13th International Conference of Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–2 December 2016; pp. 1–6. [Google Scholar]
- Kumar, N.M.; Mallick, P.K. Blockchain technology for security issues and challenges in IoT. Procedia Comput. Sci. 2018, 132, 1815–1823. [Google Scholar] [CrossRef]
- Alam, T. Blockchain-Based Internet of Things: Review, Current Trends, Applications, and Future Challenges. Computers 2022, 12, 6. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Dwivedi, A.D.; Srivastava, G.; Dhar, S.; Singh, R. A decentralized privacy-preserving healthcare blockchain for IoT. Sensors 2019, 19, 326. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Christidis, K.; Devetsikiotis, M. Blockchains and Smart Contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Awan, S.M.; Azad, M.A.; Arshad, J.; Waheed, U.; Sharif, T. A Blockchain-Inspired Attribute-Based Zero-Trust Access Control Model for IoT. Information 2023, 14, 129. [Google Scholar] [CrossRef]
- Jagatheesaperumal, S.K.; Pham, Q.V.; Ruby, R.; Yang, Z.; Xu, C.; Zhang, Z. Explainable AI Over the Internet of Things (IoT): Overview, State-of-the-Art and Future Directions. IEEE Open J. Commun. Soc. 2022, 3, 2106–2136. [Google Scholar] [CrossRef]
- Mendes, C.; Rios, T.N. Explainable Artificial Intelligence and Cybersecurity: A Systematic Literature Review. arXiv 2023, arXiv:2303.01259. [Google Scholar]
- Arrieta, A.B.; Díaz-Rodríguez, N.; Del Ser, J.; Bennetot, A.; Tabik, S.; Barbado, A.; García, S.; Gil-López, S.; Molina, D.; Benjamins, R.; et al. Explainable Artificial Intelligence (XAI): Concepts, taxonomies, opportunities and challenges toward responsible AI. Inf. Fusion 2020, 58, 82–115. [Google Scholar] [CrossRef] [Green Version]
- Bosri, R.; Rahman, M.S.; Bhuiyan, M.Z.A.; Al Omar, A. Integrating blockchain with artificial intelligence for privacy-preserving recommender systems. IEEE Trans. Netw. Sci. Eng. 2020, 8, 1009–1018. [Google Scholar] [CrossRef]
- Ahmad, A.; Bailey, K. Blockchain in food traceability: A systematic literature review. In Proceedings of the 32nd Irish Signals and Systems Conference (ISSC), Athlone, Ireland, 10–11 June 2021; pp. 1–6. [Google Scholar]
- Patil, A.S.; Tama, B.A.; Park, Y.; Rhee, K.H. A framework for blockchain-based secure smart green house farming. Adv. Comput. Sci. Ubiquitous Comput.-Springer Singap. 2018, 17, 1162–1167. [Google Scholar]
- Chen, Z.; Shen, Y.; Zhang, X.; Chen, S. A blockchain-based privacy-preserving framework for secure data sharing in healthcare IoT. IEEE Access 2020, 8, 44820–44832. [Google Scholar]
- Zhang, Y.; Liu, J.; Zhang, Y.; Yang, L. A blockchain-based secure framework for data sharing in smart agriculture. IEEE Internet Things J. 2021, 8, 10280–10291. [Google Scholar]
- Košťál, K.; Helebrandt, P.; Belluš, M.; Ries, M.; Kotuliak, I. Management and monitoring of IoT devices using blockchain. Sensors 2019, 19, 856. [Google Scholar] [CrossRef] [Green Version]
- Hakak, S.; Khan, W.Z.; Gilkar, G.A.; Imran, M.; Guizani, N. Securing smart cities through blockchain technology: Architecture, requirements, and challenges. IEEE Netw. 2020, 34, 8–14. [Google Scholar] [CrossRef]
- Georgiou, I.; Nell, J.G.; Kokkinaki, A.I. Blockchain for Smart Cities: A Systematic Literature Review. In Information Systems, Proceedings of the 17th European, Mediterranean, and Middle Eastern Conference, EMCIS 2020, Dubai, United Arab Emirates, 25–26 November 2020; Springer International Publishing: Berlin/Heidelberg, Germany, 2020; Volume 17, pp. 169–187. [Google Scholar]
- Durneva, P.; Cousins, K.; Chen, M. The current state of research, challenges, and future research directions of blockchain technology in patient care: Systematic review. J. Med. Internet Res. 2020, 22, e18619. [Google Scholar] [CrossRef]
- Khalid, U.; Asim, M.; Baker, T.; Hung, P.C.; Tariq, M.A.; Rafferty, L. A decentralized lightweight blockchain-based authentication mechanism for IoT systems. Cluster Comput. 2020, 23, 2067–2087. [Google Scholar] [CrossRef]
- Abbassi, Y.; Benlahmer, H. IoT and Blockchain combined: For decentralized security. Procedia Comput. Sci. 2021, 191, 337–342. [Google Scholar] [CrossRef]
- Issa, W.; Moustafa, N.; Turnbull, B.; Sohrabi, N.; Tari, Z. Blockchain-based federated learning for securing Internet of Things: A comprehensive survey. ACM Comput. Surv. 2023, 55, 1–43. [Google Scholar] [CrossRef]
- Rehman, M.; Javaid, N.; Awais, M.; Imran, M.; Naseer, N. Cloud-based secure service providing for IoTs using blockchain. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–7. [Google Scholar]
- Sengupta, J.; Ruj, S.; Bit, S.D. A comprehensive survey on attacks, security issues and blockchain solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481. [Google Scholar] [CrossRef]
- Zorzo, A.F.; Nunes, H.C.; Lunardi, R.C.; Michelin, R.A.; Kanhere, S.S. Dependable IoT using blockchain-based technology. In Proceedings of the Eighth Latin-American Symposium on Dependable Computing (LADC), Foz do Iguacu, Brazil, 8–10 October 2018; pp. 1–9. [Google Scholar]




| Ref. | Category | Challenge | Proposed Solution |
|---|---|---|---|
| [2] | Blockchain security |
|
|
| [3] | Blockchain architecture |
|
|
| [4] | Blockchain and IoT integration |
|
|
| [5] | Blockchain and Internet of Things (IoT) |
|
|
| [6] | Blockchain security |
|
|
| [7] | Blockchain-based IoT |
|
|
| [8] | Blockchain security |
|
|
| [15] | Blockchain security |
|
|
| [21] | Blockchain security |
|
|
| [22] | Blockchain-based supply chain management |
|
|
| [23,24,36] | Blockchain-based healthcare architecture |
|
|
| [25] | Blockchain-based IoT |
|
|
| [27,28] | Blockchain security |
|
|
| [29] | Blockchain security |
|
|
| [30] | Blockchain security |
|
|
| [31] | Blockchain security |
|
|
| [32] | Blockchain and IoT integration |
|
|
| [33] | Blockchain and Internet of Things (IoT) |
|
|
| [34] | Blockchain and Internet of Things (IoT) |
|
|
| [35] | Internet of Things (IoT) security |
|
|
| Layer | Security Challenges | Security Solutions |
|---|---|---|
| Device Layer |
|
|
| Communication Layer |
|
|
| Blockchain Layer |
|
|
| Smart Contract Layer |
|
|
| Application Layer |
|
|
| Technique | Limitations | Possible Solution |
|---|---|---|
| Public key identification | Could potentially compromise the privacy of the data being stored on the blockchain. | Use pseudonymous or anonymous identities on the blockchain. |
| Single consensus algorithm | Could make the blockchain more vulnerable to attack. | Use multiple consensus algorithms. |
| A single blockchain for all IoT devices | Could make it difficult to scale the blockchain to a large number of users. | Use multiple blockchains for different types of IoT devices. |
| Proof-of-work consensus algorithm | Could make it difficult to process transactions quickly. | Use a more efficient consensus algorithm. |
| Blockchain standards | Blockchains are still in their early stages of development, so there is a risk of security vulnerabilities. | Work to develop standards for blockchain interoperability. |
| Blockchain complexity | Blockchains are a complex technology, so there is a risk that they will be difficult to use for some applications. | Develop user-friendly interfaces for blockchains. |
| Benefits of Integrating Blockchain and XAI in IoT Systems | Challenges | Future Research Directions |
|---|---|---|
| Enhanced transparency | Computational and storage requirements | Explore XAI techniques specifically tailored for blockchain-based IoT systems |
| Trust and accountability | Complexity and interpretability | Develop mechanisms for interpretability and explainability in decentralized settings |
| Compliance and regulation | Privacy and data protection | Investigate privacy-preserving techniques for blockchain and XAI integration |
| - | Scalability and performance | Address scalability challenges in consensus mechanisms and AI algorithm performance |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alajlan, R.; Alhumam, N.; Frikha, M. Cybersecurity for Blockchain-Based IoT Systems: A Review. Appl. Sci. 2023, 13, 7432. https://doi.org/10.3390/app13137432
Alajlan R, Alhumam N, Frikha M. Cybersecurity for Blockchain-Based IoT Systems: A Review. Applied Sciences. 2023; 13(13):7432. https://doi.org/10.3390/app13137432
Chicago/Turabian StyleAlajlan, Razan, Norah Alhumam, and Mounir Frikha. 2023. "Cybersecurity for Blockchain-Based IoT Systems: A Review" Applied Sciences 13, no. 13: 7432. https://doi.org/10.3390/app13137432
APA StyleAlajlan, R., Alhumam, N., & Frikha, M. (2023). Cybersecurity for Blockchain-Based IoT Systems: A Review. Applied Sciences, 13(13), 7432. https://doi.org/10.3390/app13137432






