Intelligent Trust-Based Utility and Reusability Model: Enhanced Security Using Unmanned Aerial Vehicles on Sensor Nodes
Abstract
:1. Introduction
- UAV recharges nodes from the entire network using the energy utilization and re-usability method from the detected compromised node by using the intelligent trust evaluation system and external energy.
- UAV recharges only the lowest-powered nodes in the network and utilizes the static method of choosing a sink, with the next sink consequently only utilizing the power from the energy utility model.
- UAV renews the sink node by recharging energy from the network with a different sink selection algorithm and provides the best sink node selection algorithm and performance measures of each algorithm with network scalability.
2. Literature Review
3. Research Statement
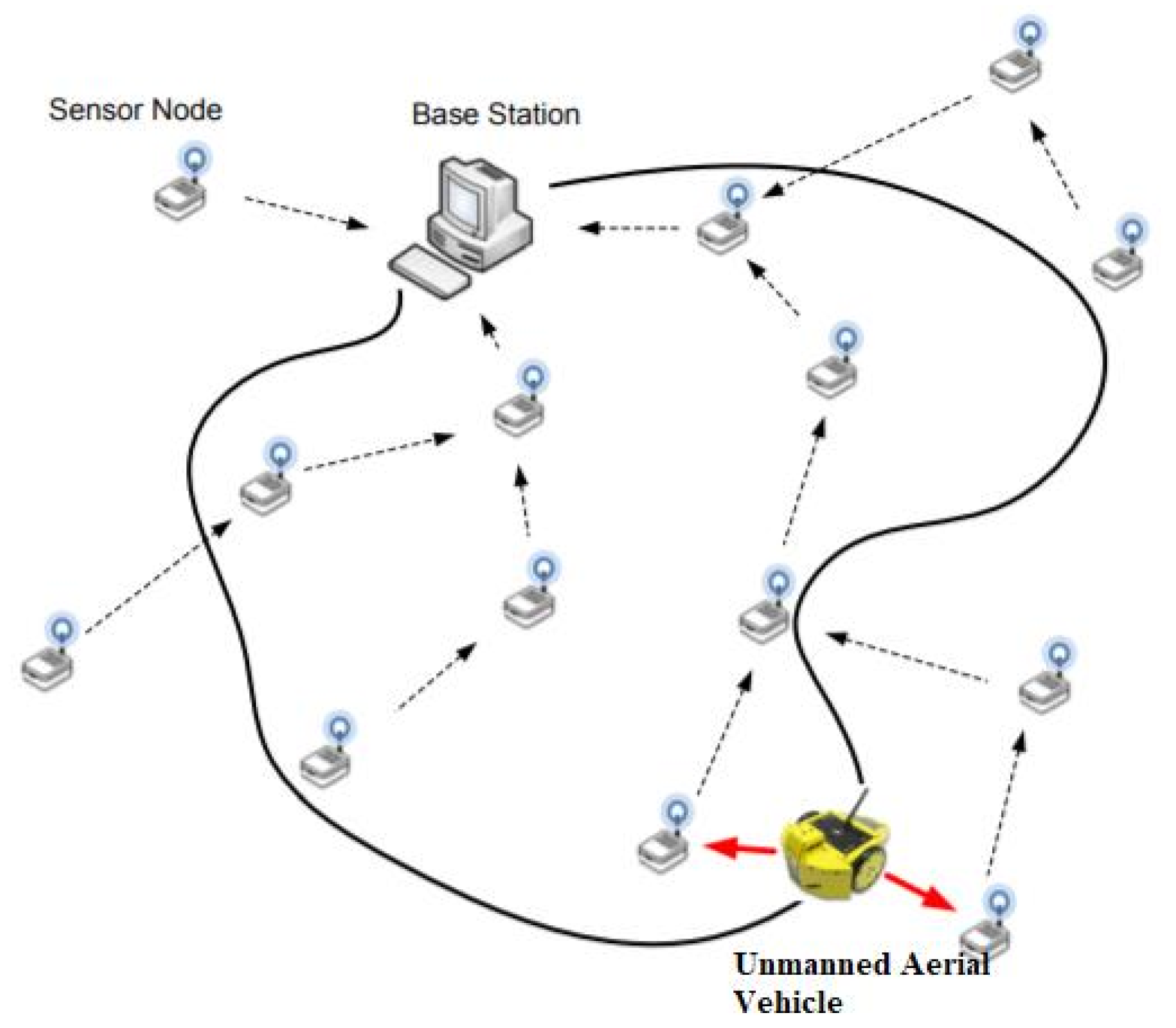
4. Energy Transfer through UAV
- It begins and finish with the same level of energy with a time and
- It does not go below
Gain in Energy at Sensor Node in the First Cycle
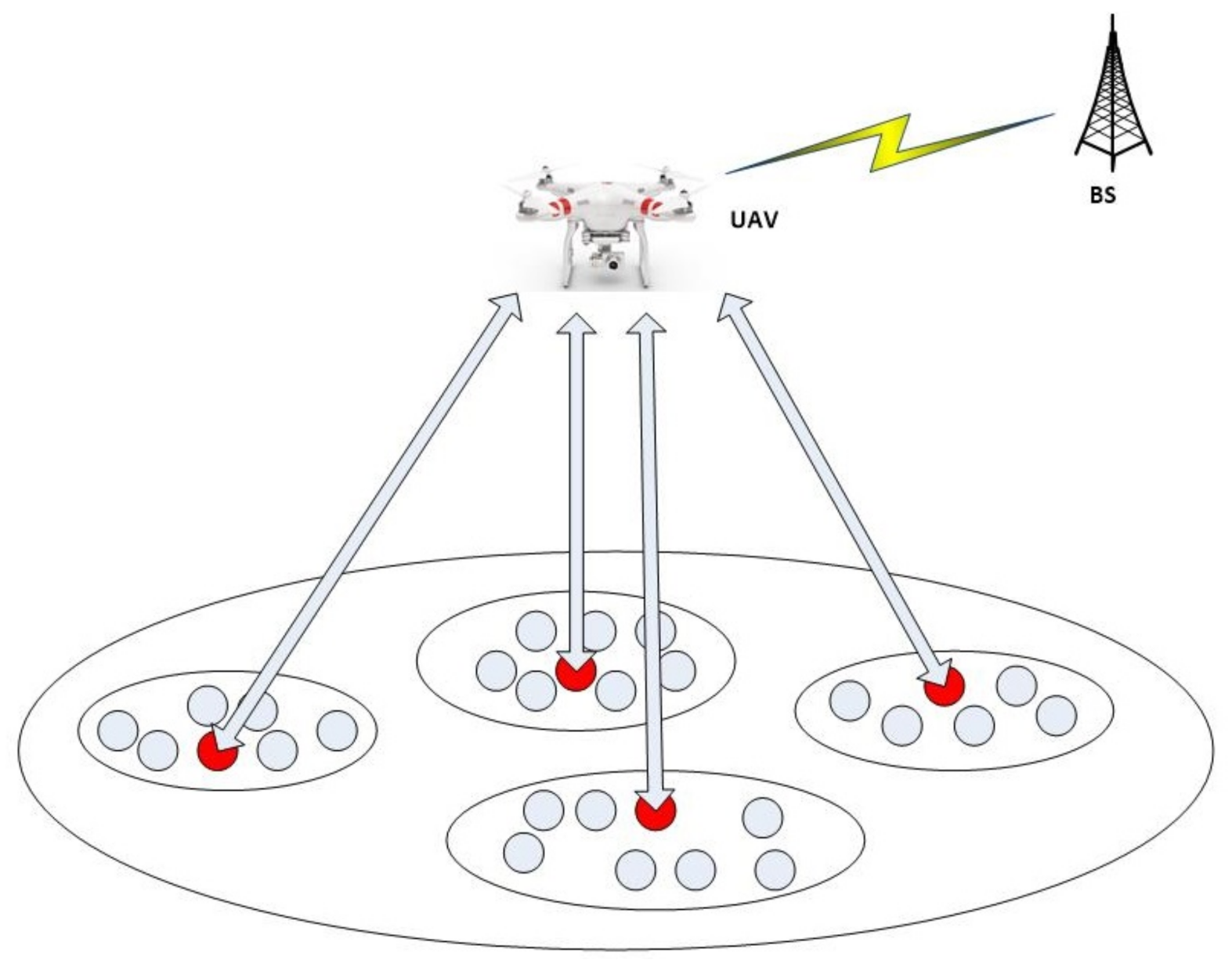
5. Energy Utility and Re-Usability Model through UAV
Remaining Energy
6. Optimization of Energy Distribution
6.1. Optimization Proof
6.2. Gain in Energy
6.3. Optimal Travel Path
7. Results and Discussion
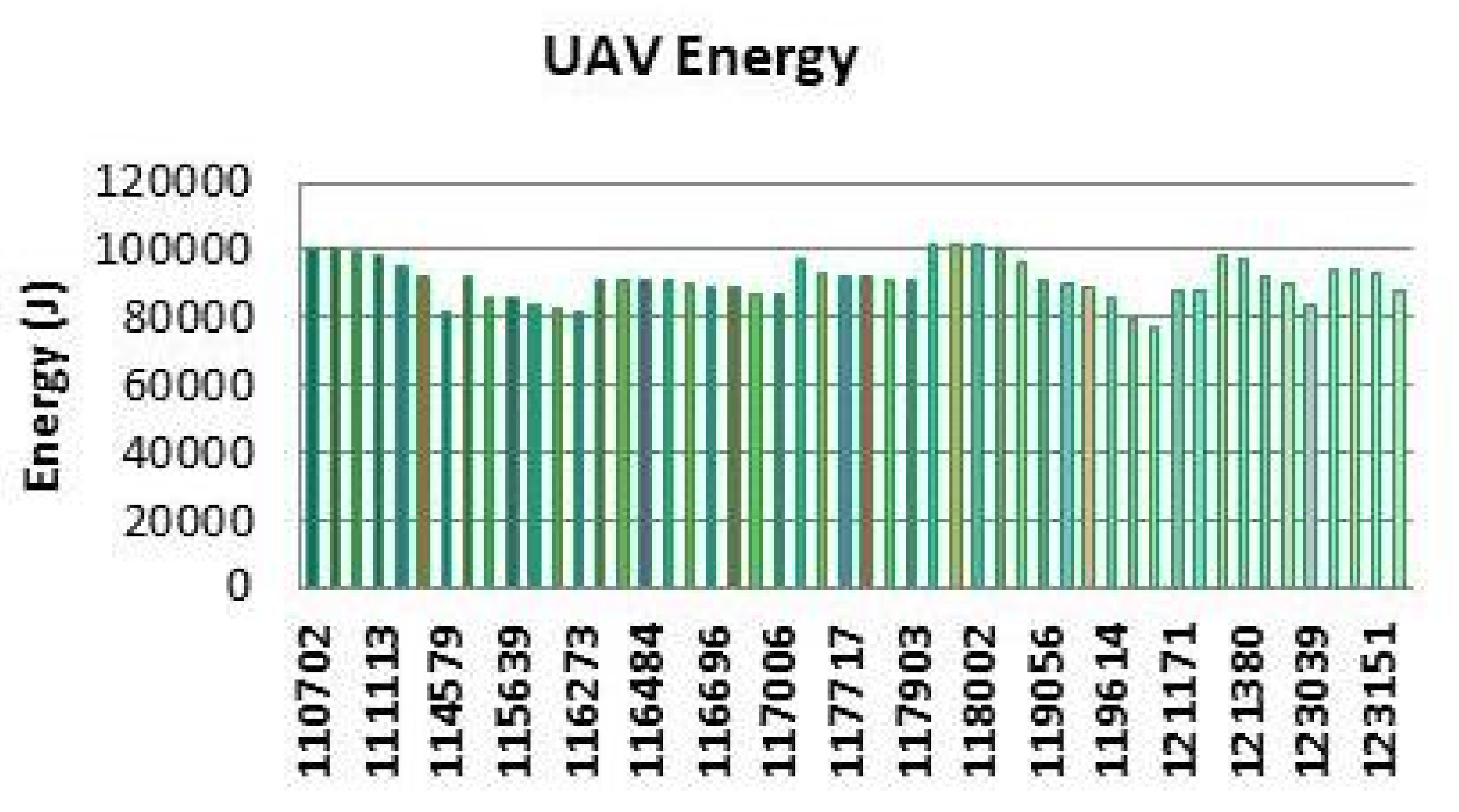
7.1. Simulation Settings
7.2. Results
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Xie, H.; Yan, Z.; Yao, Z.; Atiquzzaman, M. Data Collection for Security Measurement in Wireless Sensor Networks: A Survey. IEEE Internet Things J. 2019, 6, 2205–2224. [Google Scholar] [CrossRef] [Green Version]
- Al-Mekhlafi, Z.G.; Hanapi, Z.M.; Saleh, A.M.S. Firefly-Inspired Time Synchronization Mechanism for Self-Organizing Energy-Efficient Wireless Sensor Networks: A Survey. IEEE Access 2019, 7, 115229–115248. [Google Scholar] [CrossRef]
- Islam, T.; Park, S.-H. A Comprehensive Survey of the Recently Proposed Localization Protocols for Underwater Sensor Networks. IEEE Access 2020, 8, 179224–179243. [Google Scholar] [CrossRef]
- Saeed, N.; Nam, H.; Al-Naffouri, T.Y.; Alouini, M. A State-of-the-Art Survey on Multidimensional Scaling-Based Localization Techniques. IEEE Commun. Surv. Tutor. 2019, 21, 3565–3583. [Google Scholar] [CrossRef] [Green Version]
- Du, R.; Santi, P.; Xiao, M.; Vasilakos, A.V.; Fischione, C. The Sensable City: A Survey on the Deployment and Management for Smart City Monitoring. IEEE Commun. Surv. Tutor. 2019, 21, 1533–1560. [Google Scholar] [CrossRef]
- Chen, X.; Yu, L.; Wang, T.; Liu, A.; Wu, X.; Zhang, B.; Lv, Z.; Sun, Z. Artificial Intelligence-Empowered Path Selection: A Survey of Ant Colony Optimization for Static and Mobile Sensor Networks. IEEE Access 2020, 8, 71497–71511. [Google Scholar] [CrossRef]
- Basha, E.; Eiskamp, M.; Johnson, J.; Detweiler, C. UAV recharging opportunities and policies for sensor networks. Int. J. Distrib. Sens. Netw. 2015, 11, 824260. [Google Scholar] [CrossRef]
- Isolani, P.H.; Claeys, M.; Donato, C.; Granville, L.Z.; Latré, S. A Survey on the Programmability of Wireless MAC Protocols. IEEE Commun. Surv. Tutor. 2019, 21, 1064–1092. [Google Scholar] [CrossRef]
- Jiang, S.; Zhao, J.; Xu, X. SLGBM: An Intrusion Detection Mechanism for Wireless Sensor Networks in Smart Environments. IEEE Access 2020, 8, 169548–169558. [Google Scholar] [CrossRef]
- Otoum, S.; Kantarci, B.; Mouftah, H.T. On the Feasibility of Deep Learning in Sensor Network Intrusion Detection. IEEE Netw. Lett. 2019, 1, 68–71. [Google Scholar] [CrossRef]
- Pundir, S.; Wazid, M.; Singh, D.P.; Das, A.K.; Rodrigues, J.J.P.C.; Park, Y. Intrusion Detection Protocols in Wireless Sensor Networks Integrated to Internet of Things Deployment: Survey and Future Challenges. IEEE Access 2020, 8, 3343–3363. [Google Scholar] [CrossRef]
- Vinayakumar, R.; Alazab, M.; Soman, K.P.; Poornachandran, P.; Al-Nemrat, A.; Venkatraman, S. Deep Learning Approach for Intelligent Intrusion Detection System. IEEE Access 2019, 7, 41525–41550. [Google Scholar] [CrossRef]
- Chen, H.; Meng, C.; Shan, Z.; Fu, Z.; Bhargava, B.K. A Novel Low-Rate Denial of Service Attack Detection Approach in ZigBee Wireless Sensor Network by Combining Hilbert-Huang Transformation and Trust Evaluation. IEEE Access 2019, 7, 32853–32866. [Google Scholar] [CrossRef]
- O’Mahony, G.D.; Curran, J.T.; Harris, P.J.; Murphy, C.C. Interference and Intrusion in Wireless Sensor Networks. IEEE Aerosp. Electron. Syst. Mag. 2020, 35, 4–16. [Google Scholar] [CrossRef]
- Butun, I.; Österberg, P.; Song, H. Security of the Internet of Things: Vulnerabilities, Attacks, and Countermeasures. IEEE Commun. Surv. Tutor. 2020, 22, 616–644. [Google Scholar] [CrossRef] [Green Version]
- Khan, T.; Singh, K.; Abdel-Basset, M.; Long, H.V.; Singh, S.P.; Manjul, M. A Novel and Comprehensive Trust Estimation Clustering Based Approach for Large Scale Wireless Sensor Networks. IEEE Access 2019, 7, 58221–58240. [Google Scholar] [CrossRef]
- Poongodi, M.; Bose, S. Stochastic model: ReCAPTCHA controller based co-variance matrix analysis on frequency distribution using trust evaluation and re-eval by Aumann agreement theorem against DDoS attack in MANET. Clust. Comput. 2015, 18, 1549–1559. [Google Scholar] [CrossRef]
- Poongodi, M.; Bose, S. The COLLID based intrusion detection system for detection against DDOS attacks using trust evaluation. Adv. Nat. Appl. Sci. 2015, 9, 574–580. [Google Scholar]
- Poongodi, M.; Malviya, M.; Kumar, C.; Hamdi, M.; Vijayakumar, V.; Nebhen, J.; Alyamani, H. New York City taxi trip duration prediction using MLP and XGBoost. Int. J. Syst. Assur. Eng. Manag. 2021, 1–12. [Google Scholar] [CrossRef]
- Hu, J.; Luo, J.; Zheng, Y.; Li, K. Graphene-Grid Deployment in Energy Harvesting Cooperative Wireless Sensor Networks for Green IoT. IEEE Trans. Ind. Inform. 2019, 15, 1820–1829. [Google Scholar] [CrossRef]
- Poongodi, M.; Malviya, M.; Hamdi, M.; Vijayakumar, V.; Mohammed, M.A.; Rauf, H.T.; Al-Dhlan, K.A. 5G based Blockchain network for authentic and ethical keyword search engine. IET Commun. 2021, 1–7. [Google Scholar] [CrossRef]
- Kurs, A.; Karalis, A.; Moffatt, R.; Joannopoulos, J.D.; Fisher, P.; Soljacic, M. Wireless energy transfer via strongly coupled magnetic resonances. Science 2007, 317, 83–86. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Poongodi, M.; Bose, S. Detection and Prevention system towards the truth of convergence on decision using Aumann agreement theorem. Procedia Comput. Sci. 2015, 50, 244–251. [Google Scholar] [CrossRef] [Green Version]
- Pon, L.L.; Leow, C.Y.; Rahim, S.K.A.; Eteng, A.A.; Kamarudin, M.R. Printed Spiral Resonator for Displacement-Tolerant Near-Field Wireless Energy Transfer. IEEE Access 2019, 7, 172055–172064. [Google Scholar] [CrossRef]
- Poongodi, M.; Al-Shaikhli, I.F.; Vijayakumar, V. The probabilistic approach of energy utility and reusability model with enhanced security from the compromised nodes through wireless energy transfer in WSN. Int. J. Pure Appl. Math. 2017, 116, 233–250. [Google Scholar]
- Poongodi, M.; Bose, S. A firegroup mechanism to provide intrusion detection and prevention system against DDoS attack in collaborative clustered networks. Int. J. Inf. Secur. Priv. (IJISP) 2014, 8, 1–18. [Google Scholar] [CrossRef] [Green Version]
- Pon, L.L.; Abdul-rahim, S.K.; Leow, C.Y.; Himdi, M.; Khalily, M. Displacement-Tolerant Printed Spiral Resonator With Capacitive Compensated-Plates for Non-Radiative Wireless Energy Transfer. IEEE Access 2019, 7, 10037–10044. [Google Scholar] [CrossRef]
- Shi, Y.; Xie, L.; Hou, Y.T.; Sherali, H.D. On renewable sensor networks with wireless energy transfer. In Proceedings of the 2011 Proceedings IEEE INFOCOM, Shanghai, China, 10–15 April 2011; pp. 1350–1358. [Google Scholar] [CrossRef]
- Wu, P.; Xiao, F.; Huang, H.; Sha, C.; Yu, S. Adaptive and Extensible Energy Supply Mechanism for UAVs-Aided Wireless-Powered Internet of Things. IEEE Internet Things J. 2020, 7, 9201–9213. [Google Scholar] [CrossRef]
- Wang, M.; Lin, Y.; Tian, Q.; Si, G. Transfer Learning Promotes 6G Wireless Communications: Recent Advances and Future Challenges. IEEE Trans. Reliab. 2021, 70, 790–807. [Google Scholar] [CrossRef]
- Muniyappan, A.; Sundarappan, B.; Manoharan, P.; Hamdi, M.; Raahemifar, K.; Bourouis, S.; Varadarajan, V. Stability and Numerical Solutions of Second Wave Mathematical Modeling on COVID-19 and Omicron Outbreak Strategy of Pandemic: Analytical and Error Analysis of Approximate Series Solutions by Using HPM. Mathematics 2022, 10, 343. [Google Scholar] [CrossRef]
- Ko, H.; Pack, S.; Leung, V.C.M. Energy Utilization-Aware Operation Control Algorithm in Energy Harvesting Base Stations. IEEE Internet Things J. 2019, 6, 10824–10833. [Google Scholar] [CrossRef]
- Sun, R.; Wang, Y.; Su, R.; Cheng, N.; Shen, X.S. A Destination-Aided Wireless Energy Transfer Scheme in Multi-Antenna Relay Sensor Networks. IEEE Wirel. Commun. Lett. 2019, 8, 689–692. [Google Scholar] [CrossRef]
- Zhang, H.; Huang, Y.; Wang, J.; Wang, B.; Yang, L. Multiobjective Precoder Design for Coexisting Wireless Energy Transfer and Information Transmission Systems. IEEE Syst. J. 2020, 14, 445–456. [Google Scholar] [CrossRef]
- Li, Y.; Zhao, J.; Yang, Q.; Liu, L.; Ma, J.; Zhang, X. A Novel Coil With High Misalignment Tolerance for Wireless Power Transfer. IEEE Trans. Magn. 2019, 55, 1–4. [Google Scholar] [CrossRef]
- Poongodi, M.; Bose, S. A novel intrusion detection system based on trust evaluation to defend against DDoS attack in MANET. Arab. J. Sci. Eng. 2015, 40, 3583–3594. [Google Scholar] [CrossRef]
- Cetinkaya, O.; Dinc, E.; Koca, C.; Merrett, G.V.; Akan, O.B. Energy-Neutral Wireless-Powered Networks. IEEE Wirel. Commun. Lett. 2019, 8, 1373–1376. [Google Scholar] [CrossRef]
- Bayguzina, E.; Clerckx, B. Asymmetric Modulation Design for Wireless Information and Power Transfer With Nonlinear Energy Harvesting. IEEE Trans. Wirel. Commun. 2019, 18, 5529–5541. [Google Scholar] [CrossRef] [Green Version]
- Wang, L.; Wu, K.; Xiao, J.; Hamdi, M. Harnessing Frequency Domain for Cooperative Sensing and Multi-channel Contention in CRAHNs. IEEE Trans. Wirel. Commun. 2014, 13, 440–449. [Google Scholar] [CrossRef]
- Mhamdi, L.; Hamdi, M. Scheduling multicast traffic in internally buffered crossbar switches. In Proceedings of the 2004 IEEE International Conference on Communications (IEEE Cat. No.04CH37577), Paris, France, 20–24 June 2004; Volume 2, pp. 1103–1107. [Google Scholar] [CrossRef]
- Pun, K.; Hamdi, M. Distro: A distributed static round-robin scheduling algorithm for bufferless Clos-Network switches. In Proceedings of the Global Telecommunications Conference, Taipei, Taiwan, 17–21 November 2002; Volume 3, pp. 2298–2302. [Google Scholar] [CrossRef]








Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sahoo, S.K.; Mudligiriyappa, N.; Algethami, A.A.; Manoharan, P.; Hamdi, M.; Raahemifar, K. Intelligent Trust-Based Utility and Reusability Model: Enhanced Security Using Unmanned Aerial Vehicles on Sensor Nodes. Appl. Sci. 2022, 12, 1317. https://doi.org/10.3390/app12031317
Sahoo SK, Mudligiriyappa N, Algethami AA, Manoharan P, Hamdi M, Raahemifar K. Intelligent Trust-Based Utility and Reusability Model: Enhanced Security Using Unmanned Aerial Vehicles on Sensor Nodes. Applied Sciences. 2022; 12(3):1317. https://doi.org/10.3390/app12031317
Chicago/Turabian StyleSahoo, Santosh Kumar, Niranjanamurthy Mudligiriyappa, Abdullah A. Algethami, Poongodi Manoharan, Mounir Hamdi, and Kaamran Raahemifar. 2022. "Intelligent Trust-Based Utility and Reusability Model: Enhanced Security Using Unmanned Aerial Vehicles on Sensor Nodes" Applied Sciences 12, no. 3: 1317. https://doi.org/10.3390/app12031317






