IIoT Malware Detection Using Edge Computing and Deep Learning for Cybersecurity in Smart Factories
Abstract
:1. Introduction
- (i)
- An edge computing and malware detection system is proposed for the distributed IIoT environments of smart factories.
- (ii)
- A convolutional neural network (CNN) model using image visualization techniques is incorporated for malware classification.
- (iii)
- The proposed malware detection system is validated on the Malimg dataset.
- (iv)
- A detection accuracy of 98.93% is achieved for 25 different malware types in experiments conducted.
2. Literature Review
2.1. Security Threats for Smart Factories
- Stealing personal data of end customers: Criminals use integrated customer relationship management (CRM) systems, e.g., operating system access through heating and air conditioning vendors.
- Entire system down: This can cause dramatic losses associated with hacker attacks.
- Industrial espionage and sabotage: This involves extortion of duties by exploiting technical vulnerabilities to gain a competitive advantage over competitors by stealing intellectual property and trade secrets.
2.1.1. Cyberattacks
2.1.2. Common Cyberattacks
2.2. Smart Factory Cyberattack Structure Diagram
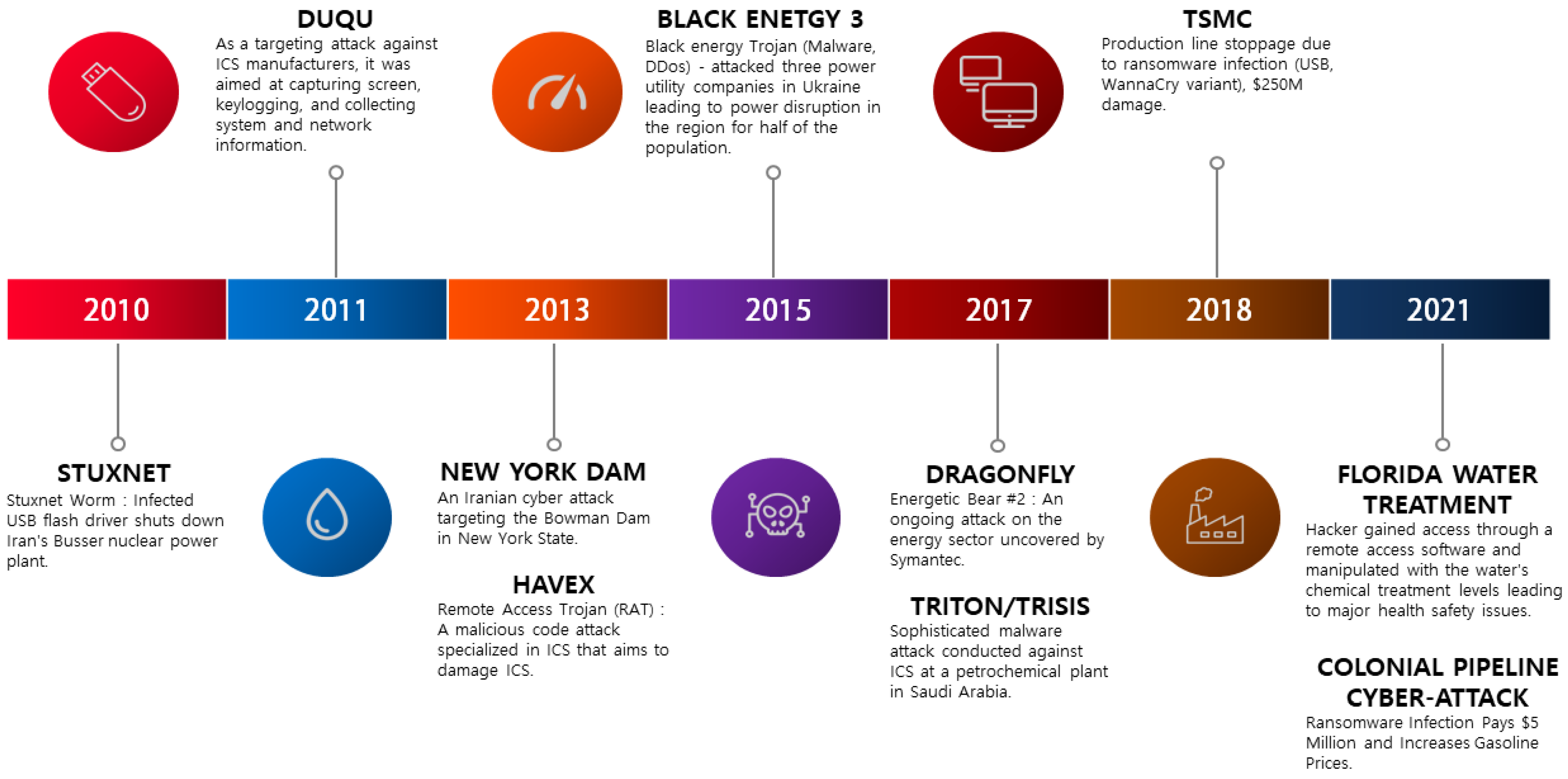
2.3. Smart Factory Cyberattack Cases
3. Edge Computing and Deep Learning-Based Malware Detection Method
3.1. Deep Learning for Malware Detection
3.2. Deep Learning for Malware Detection in Smart Factory
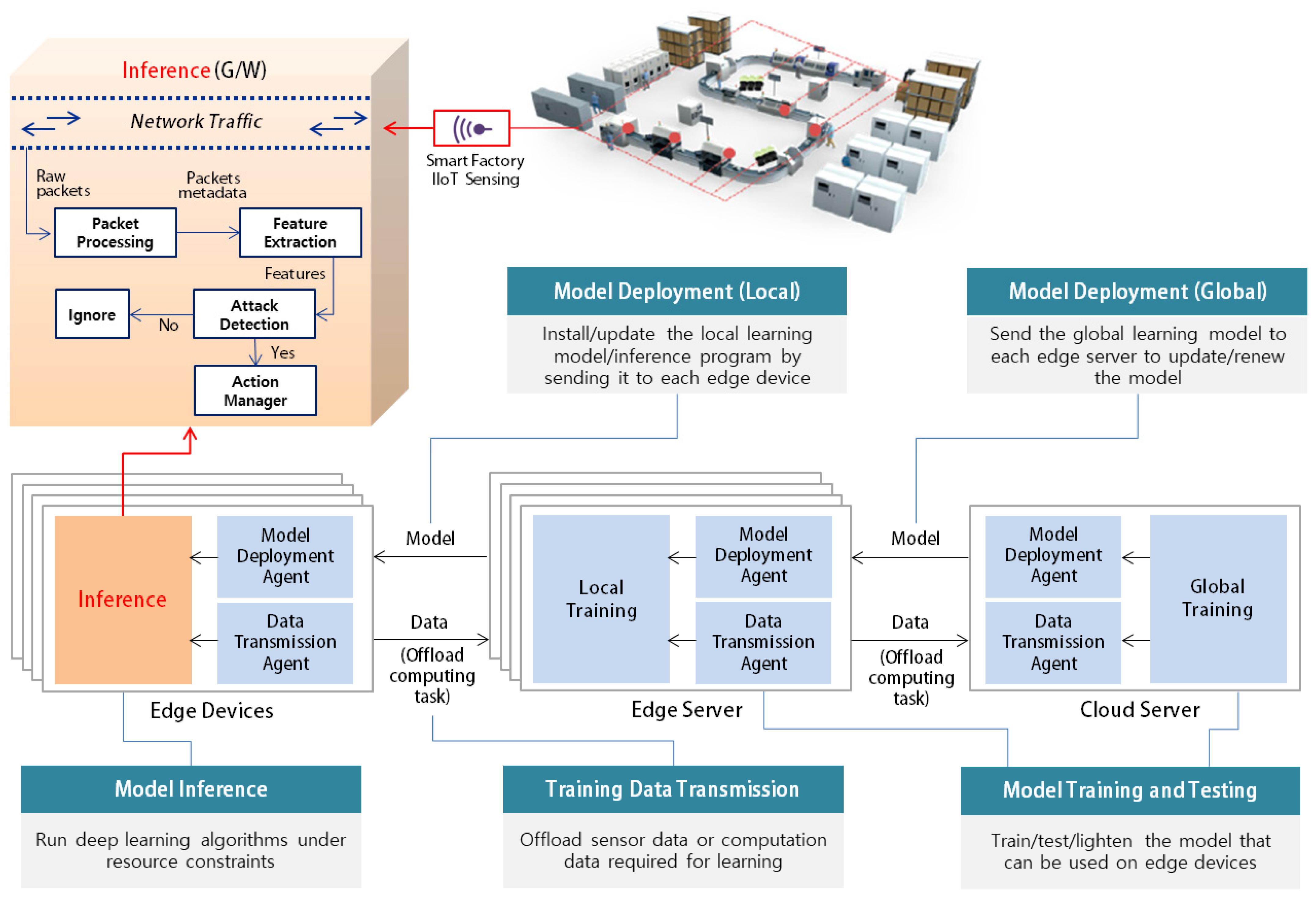
3.3. Edge Computing and Deep Learning-Based Malware Detection System
3.4. Main Functions of the Edge Computing Deep Learning-Based Malware Detection System
3.4.1. Model Training and Testing
3.4.2. Model Deployment
3.4.3. Model Inference
3.4.4. Training Data Transmission
3.5. Convolutional Neural Network (CNN) for Malware Detection
4. Experimental Evaluation
4.1. Dataset and Experiment Setup
4.2. Evaluation Metrics
5. Results and Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Hussain, Z.; Akhunzada, A.; Iqbal, J.; Bibi, I.; Gani, A. Secure IIoT-enabled industry 4.0. Sustainability 2021, 13, 12384. [Google Scholar] [CrossRef]
- Kim, H.L.; Nguyen, M.H.; Tran, T.D.; Tran, N.D. IMIDS: An Intelligent Intrusion Detection System against Cyber Threats in IoT. Electronics 2022, 11, 524. [Google Scholar]
- Zorić, P.; Musa, M.; Mijo Kuljanić, T. Smart Factory Environment: Review of Security Threats and Risks. In Proceedings of the International Conference on Future Access Enablers of Ubiquitous and Intelligent Infrastructures, FABULOUS 2021, Virtual Event, 6–7 May 2021; pp. 203–214. [Google Scholar]
- Wu, Y.; Dai, H.N.; Wang, H. Convergence of Blockchain and Edge Computing for Secure and Scalable IIoT Critical Infrastructures in Industry 4.0. IEEE Internet Things J. 2020, 8, 2300–2317. [Google Scholar] [CrossRef]
- Dorobantu, O.G.; Halunga, S. Security threats in IoT. In Proceedings of the 2020 International Symposium on Electronics and Telecommunications (ISETC), Timisoara, Romania, 5–6 November 2020; pp. 1–4. [Google Scholar]
- Falco, G.; Caldera, C.; Shrobe, H. IIoT Cybersecurity Risk Modeling for SCADA Systems. IEEE Internet Things J. 2018, 5, 4486–4495. [Google Scholar] [CrossRef]
- Stellios, I.; Kotzanikolaou, P.; Psarakis, M.; Alcaraz, C.; Lopez, J. A Survey of IoT-Enabled Cyberattacks: Assessing Attack Paths to Critical Infrastructures and Services. IEEE Commun. Surv. Tutor. 2018, 20, 3453–3495. [Google Scholar] [CrossRef]
- Paes, R.; Mazur, D.C.; Venne, B.K.; Ostrzenski, J. A Guide to Securing Industrial Control Networks: Integrating IT and OT Systems. IEEE Ind. Appl. Mag. 2020, 26, 47–53. [Google Scholar] [CrossRef]
- Pan, F.; Pang, Z.; Luvisotto, M.; Xiao, M.; Wen, H. Physical layer security for industrial wireless control systems: Basics and future directions. IEEE Ind. Electron. Mag. 2018, 12, 18–27. [Google Scholar] [CrossRef]
- Lee, K.T. Smart Factory Industrial R & D Strategy. Open Standards and ICT Association, Korea Internet Conference. 2015. Available online: http://past.krnet.or.kr/board/include/download.php?no=1924&db=dprogram&fileno=2 (accessed on 20 May 2022).
- Georgakopoulos, D.; Jayaraman, P.P.; Fazia, M.; Villari, M.; Ranjan, R. Internet of Things and Edge Cloud Computing Roadmap for Manufacturing. IEEE Cloud Comput. 2016, 4, 66–73. [Google Scholar] [CrossRef]
- Yang, H.; Alphones, A.; Zhong, W.D.; Chen, C.; Xie, X. Learning-Based Energy-Efficient Resource Management by Heterogeneous RF/VLC for Ultra-Reliable Low-Latency Industrial IoT Networks. IEEE Trans. Ind. Inform. 2020, 16, 5565–5576. [Google Scholar] [CrossRef]
- Wen, S.; Jiajia, L.; Yanlin, Y. AI-Enhanced Offloading in Edge Computing: When Machine Learning Meets Industrial IoT. IEEE Netw. 2019, 33, 68–74. [Google Scholar]
- GE Report. Everything you Need Know About Industrial Internet of Things. GE. 2017. Available online: https://www.gereports.kr/everything-you-need-know-about-industrial-internet-of-things/ (accessed on 20 May 2022).
- Wu, Y.; Huang, H.; Wang, C.X.; Pan, Y. 5G-Enabled Internet of Things; CRC Press: Boca Raton, FL, USA, 2019. [Google Scholar]
- Zhang, J.; Chen, H.; Gong, L.; Cao, J.; Gu, Z. The Current Research of IoT Security. In Proceedings of the 2019 IEEE Fourth International Conference on Data Science in Cyberspace (DSC), Hangzhou, China, 23–25 June 2019; pp. 346–353. [Google Scholar]
- Libri, A.; Bartolini, A.; Benini, L. pAElla: Edge AI-Based Real-Time Malware Detection in Data Centers. IEEE Internet Things J. 2020, 7, 9589–9599. [Google Scholar] [CrossRef] [Green Version]
- Chen, J.; Ran, X. Deep Learning with Edge Computing: A Review. Proc. IEEE 2019, 107, 1655–1674. [Google Scholar] [CrossRef]
- Li, H.; Ota, K.; Dong, M. Learning IoT in Edge: Deep Learning for the Internet of Things with Edge Computing. IEEE Netw. 2018, 32, 96–101. [Google Scholar] [CrossRef] [Green Version]
- Wang, Z.; Tian, J.; Fang, H.; Chen, L.; Qin, J. LightLog: A lightweight temporal convolutional network for log anomaly detection on the edge. Comput. Netw. 2022, 203, 108616. [Google Scholar] [CrossRef]
- Häckel, B.; Hänsch, F.; Hertel, M.; Übelhör, J. Assessing IT availability risks in smart factory networks. Bus. Res. 2018, 12, 523–558. [Google Scholar] [CrossRef] [Green Version]
- Davis, J. Cybersecurity for Manufacturers: Securing the Digitized and Connected Factory; MForesight, Computing Community Consortium. 2017. Available online: https://cra.org/ccc/wp-content/uploads/sites/2/2017/10/MForesight-Cybersecurity-Report.pdf (accessed on 20 May 2022).
- Tuptuk, N.; Hailes, S. Security of smart manufacturing systems. J. Manuf. Syst. 2018, 47, 93–106. [Google Scholar] [CrossRef]
- Burke, R.; Mussomeli, A.; Laaper, S.; Hartigan, M.; Sniderman, B. The Smart Factory; Deloitte University Press: Westlake, TX, USA, 2017. [Google Scholar]
- FTP Software. 5 Ways to Mitigate Cybersecurity Risks in Smart Manufacturing. Available online: https://www.fpt-software.com/5-ways-to-mitigate-cybersecurity-risks-in-smart-manufacturing/ (accessed on 20 May 2022).
- The European Union Agency for Cybersecurity. Good Practices for Security of Internet of Things in the Context of Smart Manufacturing; ENISA: Athens, Greece, 2018; Available online: https://www.enisa.europa.eu/publications/good-practices-for-security-of-iot (accessed on 20 May 2022).
- Dhirani, L.L.; Newe, T.; Armstrong, E. Industrial IoT, Cyber Threats, and Standards Landscape: Evaluation and Roadmap. Sensors 2021, 21, 3901. [Google Scholar] [CrossRef]
- KISA. Security Model for Smart Factory; Korea Internet & Security Agency: Seoul, Korea, 2020; Available online: https://www.kisa.or.kr/post/fileDownload?menuSeq=2060205&postSeq=11&attachSeq=2&lang_type=KO (accessed on 20 May 2022).
- Yu, W.; Liang, F.; He, X.; Hatcher, W.G.; Lu, C.; Lin, J.; Yang, X. A Survey on the Edge Computing for the Internet of Things. IEEE Access 2017, 6, 6900–6919. [Google Scholar] [CrossRef]
- Lu, Y.; Morris, K.; Frechette, S. Current Standards Landscape for Smart Manufacturing Systems; NISTIR-8107; NIST. 2016. Available online: https://nvlpubs.nist.gov/nistpubs/ir/2016/NIST.IR.8107.pdf (accessed on 20 May 2022).
- Paharia, B.; Bhushan, K. A comprehensive review of distributed denial of service (DDoS) attacks in fog computing environment. In Handbook of Computer Networks and Cyber Security; Springer: Cham, Switzerland, 2020; pp. 493–524. [Google Scholar] [CrossRef]
- Tu, S.; Waqas, M.; Rehman, S.U.; Aamir, M.; Rehman, O.U.; Zhang, J.; Chang, C.C. Security in fog computing: A novel technique to tackle an impersonation attack. IEEE Access 2018, 6, 74993–75001. [Google Scholar] [CrossRef]
- Rajendran, G.; Nivash, R.S.R.; Parthy, P.P.; Balamurugan, S. Modern security threats in the Internet of Things (IoT): Attacks and Countermeasures. In Proceedings of the 2019 International Carnahan Conference on Security Technology (ICCST), Chennai, India, 1–3 October 2019. [Google Scholar]
- Conti, M.; Dragoni, N.; Lesyk, V. A survey of man in the middle attacks. IEEE Commun. Surv. Tutor. 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Abbas, N.; Asim, M.; Tariq, N.; Baker, T.; Abbas, S. A Mechanism for Securing IoT-enabled Applications at the Fog Layer. J. Sens. Actuator Netw. 2019, 8, 16. [Google Scholar] [CrossRef] [Green Version]
- Aslan, O.; Yilmaz, A.A. A New Malware Classification Framework Based on Deep Learning Algorithms. IEEE Access 2021, 9, 87936–87951. [Google Scholar] [CrossRef]
- Pedreira, V.; Barros, D.; Pinto, P. A Review of Attacks, Vulnerabilities, and Defenses in Industry 4.0 with New Challenges on Data Sovereignty Ahead. Sensors 2021, 21, 5189. [Google Scholar] [CrossRef] [PubMed]
- Bakić, B.; Milić, M.; Antović, I.; Savić, D.; Stojanović, T. 10 years since Stuxnet: What have we learned from this mysterious computer software worm? In Proceedings of the 2021 25th International Conference on Information Technology (IT), Zabljak, Montenegro, 16–20 February 2021.
- Tang, M.; Luo, M.; Zhou, J.; Yang, Z.; Guo, Z.; Yan, F.; Liu, L. Side-Channel Attacks in a Real Scenario. Tsinghua Sci. Technol. 2018, 23, 586–598. [Google Scholar] [CrossRef]
- Liang, J.; Zhang, M.; Leung, V.C.M. A Reliable Trust Computing Mechanism Based on Multisource Feedback and Fog Computing in Social Sensor Cloud. IEEE Internet Things J. 2020, 7, 5481–5490. [Google Scholar] [CrossRef]
- Khalid, A.; Zainal, A.; Maarof, M.A.; Ghaleb, F.A. Advanced Persistent Threat Detection: A Survey. In Proceedings of the 2021 3rd International Cyber Resilience Conference (CRC), Langkawi Island, Malaysia, 29–31 January 2021. [Google Scholar]
- Javed, S.H.; Ahmad, M.B.; Asif, M.; Almotiri, S.H.; Masood, K.; Ghamdi, M.A.A. An Intelligent System to Detect Advanced Persistent Threats in Industrial Internet of Things (I-IoT). Electronics 2022, 11, 742. [Google Scholar] [CrossRef]
- Li, S.; Zhang, Q.; Wu, X.; Han, W.; Tian, Z. Attribution Classification Method of APT Malware in IoT Using Machine Learning Techniques. Secur. Commun. Netw. 2021, 2021, 9396141. [Google Scholar] [CrossRef]
- Bilge, L.; Dumitras, T. Before We Knew It: An Empirical Study of Zero-Day Attacks in the Real World. In Proceedings of the 2012 ACM conference on Computer and Communications Security, Raleigh, NC, USA, 16–18 October 2012; pp. 833–844. [Google Scholar]
- Zhang, W.; Guo, W.; Liu, X.; Liu, Y.; Zhou, J.; Li, B.; Lu, Q.; Yang, S. LSTM-Based Analysis of Industrial IoT Equipment. IEEE Access 2018, 6, 23551–23560. [Google Scholar] [CrossRef]
- Baracaldo, N.; Chen, B.; Ludwig, H.; Safavi, A.; Zhang, R. Detecting Poisoning Attacks on Machine Learning in IoT Environments. In Proceedings of the 2018 IEEE International Congress on Internet of Things (ICIOT), San Francisco, CA, USA, 2–7 July 2018. [Google Scholar]
- Papernot, N.; McDaniel, P.; Goodfellow, I.; Jha, S.; Celik, Z.B.; Swami, A. Practical Black-Box Attacks against Machine Learning. In Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security, Abu Dhabi, United Arab Emirates, 2–6 April 2017. [Google Scholar]
- Alam, M.N.; Sarma, D.; Lima, F.F.; Saha, I.; Ulfath, R.E.; Hossain, S. Phishing attacks detection using machine learning approach. In Proceedings of the 2020 Third International Conference on Smart Systems and Inventive Technology (ICSSIT), Tirunelveli, India, 20–22 August 2020. [Google Scholar]
- Trend Micro. What Is Phishing? Trend Micro. Available online: https://www.trendmicro.com/en_us/what-is/phishing.html (accessed on 20 May 2022).
- Hernandez, G.; Arias, O.; Buentello, D.; Jin, Y. Smart Nest Thermostat: A Smart Spy in Your Home; Black Hat USA: San Francisco, CA, USA, 2014. [Google Scholar]
- Mrabet, H.; Belguith, S.; Alhomoud, A.; Jemai, A. A Survey of IoT Security Based on a Layered Architecture of Sensing and Data Analysis. Sensors 2020, 20, 3625. [Google Scholar] [CrossRef]
- Jang, J.; Kim, Y.; Park, J. Current Status of Cyber Attacks and Response System in Smart Factory Environment. IITP Weekly Technology Trends. 2022. Available online: https://www.itfind.or.kr/publication/regular/weeklytrend/weekly/view.do?boardParam1=8265&boardParam2=8265 (accessed on 20 May 2022).
- Kisielius, J. Breaking Down the SolarWinds Supply Chain Attack. Available online: https://spycloud.com/solarwinds-attack-breakdown/ (accessed on 20 May 2022).
- Tsvetanov, T.; Slaria, S. The effect of the Colonial Pipeline shutdown on gasoline prices. Econ. Lett. 2021, 209, 110122. [Google Scholar] [CrossRef]
- Nguyen, L. Cybersecurity and Defending Critical Infrastructure. In Proceedings of the Harvard Model Congress 2022, Boston, MA, USA, 23–26 February 2022. [Google Scholar]
- Hajda, J.; Jakuszewski, R.; Ogonowski, S. Security Challenges in Industry 4.0 PLC Systems. Appl. Sci. 2021, 11, 9785. [Google Scholar] [CrossRef]
- Oueslati, N.E.; Mrabet, H.; Jemai, A.; Alhomoud, A. Comparative Study of the Common Cyber-physical Attacks in Industry 4.0. In Proceedings of the 2019 International Conference on Internet of Things, Embedded Systems and Communications (IINTEC), Tunis, Tunisia, 20–22 December 2019. [Google Scholar]
- Alazab, M. Proling and classifying the behavior of malicious codes. J. Syst. Softw. 2015, 100, 91–102. [Google Scholar] [CrossRef]
- Liu, Y.; Pi, D. A novel kernel SVM algorithm with game theory for network intrusion detection. KSII Trans. Internet Inf. Syst. 2017, 11, 4043–4060. [Google Scholar]
- Mohamed Amine, F.; Maglaras, L.; Ahmim, A.; Derdour, M.; Janicke, H. RDTIDS: Rules and decision tree-based intrusion detection system for internet-of-things networks. Future Internet 2020, 12, 44. [Google Scholar]
- Madhawa, S.; Balakrishnan, P.; Arumugam, U. Roll forward validation based decision tree classification for detecting data integrity attacks in industrial internet of things. J. Intell. Fuzzy Syst. 2019, 36, 2355–2366. [Google Scholar] [CrossRef]
- Prabavathy, S.; Sundarakantham, K.; Shalinie, S. Design of cognitive fog computing for intrusion detection in Internet of Things. J. Commun. Netw. 2018, 20, 291–298. [Google Scholar] [CrossRef]
- Liu, Y.S.; Lai, Y.K.; Wang, Z.H.; Yan, H.B. A new learning approach to malware classification using discriminative feature extraction. IEEE Access 2019, 7, 13015–13023. [Google Scholar] [CrossRef]
- Hasan, M.; Islam, M.M.; Zarif, M.I.I.; Hashem, M. Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches. Internet Things 2019, 7, 100059. [Google Scholar] [CrossRef]
- Li, J.; Zhao, Z.; Li, R.; Zhang, H. AI-Based Two-Stage Intrusion Detection for Software Defined IoT Networks. IEEE Internet Things J. 2019, 6, 2093–2102. [Google Scholar] [CrossRef] [Green Version]
- Mehmood, A.; Mukherjee, M.; Ahmed, S.H.; Song, H.; Malik, K.M. NBC-MAIDS: Naïve Bayesian classification technique in multi-agent system-enriched IDS for securing IoT against DDoS attacks. J. Supercomput. 2018, 74, 5156–5170. [Google Scholar] [CrossRef]
- Hodo, E.; Bellekens, X.; Hamilton, A.; Dubouilh, P.L.; Iorkyase, E.; Tachtatzis, C.; Atkinson, R. Threat analysis of IoT networks Using Artificial Neural Network Intrusion Detection System. In Proceedings of the 2016 International Symposium on Networks, Computers and Communications (ISNCC), Yasmine Hammamet, Tunisia, 11–13 May 2016; pp. 1–6. [Google Scholar]
- Kulkarni, R.; Venayagamoorthy, G. Neural network based secure media access control protocol for wireless sensor networks. In Proceedings of the 2009 International Joint Conference on Neural Networks(IJCNN), Atlanta, GA, USA, 14–19 June 2009; pp. 1680–1687. [Google Scholar]
- Tuncer, T.; Ertam, F.; Dogan, S. Automated malware recognition method based on local neighborhood binary pattern. Multimed. Tools Appl. 2020, 79, 27815–27832. [Google Scholar] [CrossRef]
- Kan, Z.; Wang, H.; Xu, G.; Guo, Y.; Chen, X. Towards Light-Weight Deep Learning Based Malware Detection. In Proceedings of the 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), Tokyo, Japan, 23–27 July 2018. [Google Scholar]
- Raff, E.; Barker, J.; Sylvester, J.; Brandon, R.; Catanzaro, B.; Nicholas, C. Malware Detection by Eating a Whole EXE. Comput. Sci. 2017. [Google Scholar]
- AL-Hawawreh, M.; Moustafa, N.; Sitnikova, E. Identification of malicious activities in industrial internet of things based on deep learning models. J. Inf. Secur. Appl. 2018, 41, 1–11. [Google Scholar] [CrossRef]
- LeCun, Y.; Bengio, Y.; Hinton, G. Deep learning. Nature 2015, 521, 436–444. [Google Scholar] [CrossRef] [PubMed]
- Nataraj, L. A Signal Processing Approach to Malware Analysis; University of California: Santa Barbara, CA, USA, 2015. [Google Scholar]
- Nataraja, L.; Jacobb, G.; Manjunatha, B. Detecting Packed Executables Based on Raw Binary Data; Technical Report; University of California: Santa Barbara, CA, USA, 2010. [Google Scholar]
- Nataraj, L.; Yegneswaran, V.; Porras, P.; Zhang, J. A comparative assessment of malware classication using binary texture analysis and dynamic analysis. In Proceedings of the 4th ACM workshop on Security and artificial intelligence, New York, NY, USA, 21 October 2011; pp. 21–30. [Google Scholar]
- Nataraj, L.; Kirat, D.; Manjunath, B.S.; Vigna, G. Sarvam: Search and retrieVAL of malware. In Proceedings of the Annual Computer Security Applications Conference (ACSAC) Workshop on Next Generation Malware Attacks and Defense (NGMAD), New Orleans, LA, USA, 9–13 December 2013. [Google Scholar]
- Nguyen, X.H.; Nguyen, X.D.; Huynh, H.H.; Le, K.H. Realguard: A Lightweight Network Intrusion Detection System for IoT Gateways. Sensors 2022, 22, 432. [Google Scholar] [CrossRef]
- Falana, O.J.; Sodiya, A.S.; Onashoga, S.A.; Badmus, B.S. Mal-Detect An intelligent visualization approach for malware detection. J. King Saud Univ. Comput. Inf. Sci. 2022, 34, 1968–1983. [Google Scholar] [CrossRef]
- Althubiti, S.A.; Jones, E.M.; Roy, K. LSTM for Anomaly-Based Network Intrusion Detection. In Proceedings of the 2018 28th International Telecommunication Networks and Applications Conference (ITNAC), Sydney, NSW, Australia, 21–23 November 2018. [Google Scholar]
- Diro, A.; Chilamkurti, N. Leveraging LSTM Networks for Attack Detection in Fog-to-Things Communications. IEEE Commun. Mag. 2018, 56, 124–130. [Google Scholar] [CrossRef]
- Wu, D.; Jiang, Z.; Xie, X.; Wei, X.; Yu, W.; Li, R. LSTM Learning with Bayesian and Gaussian Processing for Anomaly Detection in Industrial IoT. IEEE Trans. Ind. Inform. 2020, 16, 5244–5253. [Google Scholar] [CrossRef] [Green Version]
- Vasan, D.; Alazab, M.; Wassan, S.; Safaei, B.; Zheng, Q. Image-based malware classification using ensemble of CNN architectures (IMCEC). Comput. Secur. 2020, 92, 101748. [Google Scholar] [CrossRef]
- Jo, W.; Kim, S.; Lee, C.; Shon, T. Packet Preprocessing in CNN-Based Network Intrusion Detection System. Electronics 2020, 9, 1151. [Google Scholar] [CrossRef]
- Wang, C.; Zhao, Z.; Wang, F.; Li, Q. A novel malware detection and family classification scheme for IoT based on DEAM and densenet. Secur. Commun. Netw. 2021, 2021, 6658842. [Google Scholar] [CrossRef]
- Catak, F.O.; Ahmed, J.; Sahinbas, K.; Khand, Z.H. Data augmentation based malware detection using convolutional neural networks. PeerJ Comput. Sci. 2021, 7, 1–26. [Google Scholar] [CrossRef] [PubMed]
- Yang, H.; Chengy, L.; Chuahz, M.C. Deep-Learning-Based Network Intrusion Detection for SCADA Systems. In Proceedings of the 2019 IEEE Conference on Communications and Network Security (CNS), Washington, DC, USA, 10–12 June 2019. [Google Scholar]
- Perales Gómez, Á.L.; Fernández Maimó, L.; Huertas Celdrán, A.; García Clemente, F.J.; Gil Pérez, M.; Martínez Pérez, G. SafeMan: A unified framework to manage cybersecurity and safety in manufacturing industry. Softw.-Pract. Exp. 2021, 51, 607–627. [Google Scholar] [CrossRef]
- Abeshu, A.; Chilamkurti, N. Deep Learning: The Frontier for Distributed Attack Detection in Fog-to-Things Computing. IEEE Commun. Mag. 2018, 56, 169–175. [Google Scholar] [CrossRef]
- HaddadPajouh, H.; Khayami, R.; Dehghantanha, A.; Choo, K.K.R.; Parizi, R.M. AI4SAFE-IoT: An AI-powered secure architecture for edge layer of Internet of thing. Neural Comput. Appl. 2020, 32, 16119–16133. [Google Scholar] [CrossRef]
- Alshahrani, H.M. Coll-iot: A collaborative intruder detection system for internet of things devices. Electronics 2021, 10, 848. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Cui, L.; Su, D.; Zhou, Y.; Zhang, L.; Wu, Y.; Chen, S. Edge Learning for Surveillance Video Uploading Sharing in Public Transport Systems. IEEE Trans. Intell. Transp. Syst. 2021, 22, 2274–2285. [Google Scholar] [CrossRef]
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A survey on mobile edge computing: The communication perspective. IEEE Commun. Surv. Tuts. 2017, 19, 2322–2358. [Google Scholar] [CrossRef] [Green Version]
- The Asimov Institute. The Neural Network Zoo. 2022. Available online: https://www.asimovinstitute.org/neural-network-zoo/ (accessed on 20 May 2022).
- Akarsh, S.; Simran, K.; Poornachandran, P.; Menon, V.K.; Soman, K.P. Deep Learning Framework and Visualization for Malware Classification. In Proceedings of the 2019 5th International Conference on Advanced Computing & Communication Systems (ICACCS), Coimbatore, India, 15–16 March 2019. [Google Scholar]
- Vasan, D.; Alazab, M.; Wassan, S.; Naeem, H.; Safaei, B.; Zheng, Q. IMCFN: Image-based malware classification using fine-tuned convolutional neural network architecture. Comput. Netw. 2020, 171, 107138. [Google Scholar] [CrossRef]
- Demirezen, M.U. Image Based Malware Classification with Multimodal Deep Learning. Int. J. Inf. Secur. Sci. 2021, 10, 42–59. [Google Scholar]
- Vinayakumar, R.; Alazab, M.; Soman, K.; Poornachandran, P.; Venkatraman, S. Robust intelligent malware detection using deep learning. IEEE Access 2019, 7, 46717–46738. [Google Scholar] [CrossRef]
- Zhong, F.; Chen, Z.; Xu, M.; Zhang, G.; Yu, D.; Cheng, X. Malware-on-the-Brain: Illuminating Malware Byte Codes with Images for Malware Classification. IEEE Trans. Comput. 2022. [Google Scholar] [CrossRef]
- Krithika, V.; Vijaya, M. Malware Detection Using Gist Features and Deep Neural Network. In Proceedings of the 2020 6th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, India, 6–7 March 2020. [Google Scholar]
- Nataraj, L.; Karthikeyan, S.; Jacob, G.; Manjunath, B. Malware images: Visualization and automatic classification. In Proceedings of the 2011 International Symposium on Visualization for Cyber Security, Pittsburgh, PA, USA, 20 July 2011. [Google Scholar]
- Jian, Y.; Kuang, H.; Ren, C.; Ma, Z.; Wang, H. A novel framework for image-based malware detection with a deep neural network. Comput. Secur. 2021, 109, 102400. [Google Scholar] [CrossRef]
- Saridou, B.; Rose, J.R.; Shiaeles, S.; Papadopoulos, B. SAGMAD-A Signature Agnostic Malware Detection System Based on Binary Visualisation and Fuzzy Sets. Electronics 2022, 11, 1044. [Google Scholar] [CrossRef]
- Awan, M.J.; Masood, O.A.; Mohammed, M.A.; Yasin, A.; Zain, A.M.; Damaševičius, R.; Abdulkareem, K.H. Image-Based Malware Classification Using VGG19 Network and Spatial Convolutional Attention. Electronics 2021, 10, 2444. [Google Scholar] [CrossRef]
- Liu, H.; Kamata, S.I.; Li, Y. Hybrid Featured based Pyramid Structured CNN for Texture Classification. In Proceedings of the 2019 IEEE International Conference on Signal and Image Processing Applications (ICSIPA), Kuala Lumpur, Malaysia, 17–19 September 2019. [Google Scholar]








| Security Item | Manufacturing Systems | IT Systems |
|---|---|---|
| System | ‣ HMI, PLC, sensor, actuator, etc. ‣ Mechanical control | ‣ ERP, SCM, MES, WMS, etc. ‣ Data or corporate resource management |
| OS | ‣ Use of dedicated OS/real-time OS | ‣ Use of general-purpose OS (Windows, Linux) |
| Components | ‣ Heterogeneous | ‣ Homogenous |
| Lifecycle | ‣ Long (5–20 years) | ‣ Short (3–5 years) |
| Communication | ‣ Mixing industrial protocols and standard communication protocols | ‣ Standard communication protocols |
| Network requirements | ‣ Emphasis on robustness and real-time requirements ‣ Response time is important and communication delay is not allowed | ‣ Focus on non-real time and overall throughput ‣ Reliability of response is important, and some communication delay is allowed |
| Availability | ‣ Critical, 24 × 7, planned downtime | ‣ Not always available, outages, rebooting tolerable |
| Time dependency | ‣ Delays accepted | ‣ Critical |
| Resources | ‣ Limited | ‣ Enough resources for security |
| Patch (including security patch) | ‣ Difficult maintenance such as patching | ‣ Easy maintenance such as patching |
| Security priority | ‣ Availability > Integrity > Confidentiality | ‣ Confidentiality > Integrity > Availability |
| Security awareness | ‣ Not familiar with security in general | ‣ Awareness of the importance of security |
| Prevention | ‣ Physical protection for field devices | ‣ In-depth defense |
| Forensics | ‣ Limited | ‣ Available |
| Antivirus | ‣ Non-general with difficulty applying to general IT products | ‣ General for wide use |
| Impact of accident | ‣ Fatal damage and large-scale physical and economic damage due to industrial site operation disruption | ‣ Relatively insignificant economic damage such as work inconvenience and delay |
| Threat Vector | Threat Classification | Risk Impact |
|---|---|---|
| Work area | ‣ Malicious activities (stealing, misuse, alteration, theft, destruction of information about business ICT systems, networks, and infrastructure) ‣ Business network failure through malware infection | Medium to High |
| Process control network | ‣ Malfunctions and interruptions due to denial of service (DoS) attacks ‣ PLC malfunction and interruption through control command modulation ‣ Obtaining and leaking recipes and control device account/password through eavesdropping ‣ Intrusion of a Wi-Fi wireless network via public SSID | High |
| Supply chain | ‣ Modulation of normal operating setpoints through maintenance channels ‣ Ransomware infection through external public services and ports ‣ DoS attack using remote access vulnerability | High |
| External Internet | ‣ DoS attack using server OS and software vulnerabilities ‣ Infection with malware, such as phishing, spyware, and Trojans, via email | High |
| Physical attacks | ‣ Damage to devices and supporting facilities ‣ Normal operation setpoint and firmware modification ‣ Ransomware infection via USB port ‣ Malfunctions and interruptions through arbitrary process manipulation | High |
| Others | ‣ Disasters (accidents, force majeure, etc.) ‣ Unintentional/accidental failure (malfunction and downtime due to user error) ‣ Laws (laws relating to third-party subcontractors, GDPR issues, etc.) | Medium to High |
| Attack | Description | Attack by (Packets, etc.) |
|---|---|---|
| Flooding | An attack in which the server receives many connection requests but does not respond to complete the handshake. | TCP, UDP, ICMP |
| Smurf | Network layer DoS attack due to misconfiguration of network equipment | IP, ICMP |
| Ping of Death | Attacks that use ping to make large ICMP packets and create a load to process all the fragmented packets. | ICMP |
| Teardrop | An attack in which numerous Internet protocol (IP) data fragments are transmitted over a network and cannot be reassembled into the original packet, resulting in an overflow. | Variants such as Bonk, Boink, etc. |
| Jamming | Attacks that disrupt normal communication through illegal wireless communication disturbance [32]. | Mobile communication network, GPS, radio wave (RF) |
| Attack | Description | Attack by (Packets, etc.) |
|---|---|---|
| Sniffing | Eavesdropping on network traffic (e.g., data packets of other people) between systems connected to the network. | Sniffer |
| Spoofing | Attacks that trick hostnames, IPs, MACs, email addresses, etc. [34]. | IP/ARP/DNS/DHCP/Email Spoofing |
| Session Hijacking | Attacks that control communication by intercepting a session in which the connection between two systems is active (e.g., logged in) [35]. | TCP, RDP |
| Packet Injection | Attacks that inject malicious data along with normal data. | |
| Replay | Attacks that copy and retransmit messages and packets that have the same effect even if reused. |
| Malware | Description |
|---|---|
| Worms | They are not parasitic on other programs. They exist and run independently and self-replicate. |
| Viruses | It is possible to self-replicate while infecting and parasitizing other programs, but they cannot spread independently. |
| Trojans | They hide their original purpose without self-replication and perform malicious actions by disguising as normal programs. |
| Spyware | They are installed secretly without the consent of users and operate in a manner to collect and steal information from users. |
| Ransomware | They encrypt sensitive data of users and operate in a manner requiring money in exchange for decryption. |
| Backdoor | They operate in a manner that allows bypass access through the communication connection path installed secretly without a normal authentication procedure. |
| Attack | Description | Citation |
|---|---|---|
| Side-Channel | Using technology to collect and analyze various types of information leaking from the hardware and software of industrial equipment, such as analysis of power consumption, electromagnetic waves, optical signals, traffic flow (e.g., network), etc., secret information is decrypted to carry out an attack. | [39] |
| Eavesdropping | By monitoring network traffic, attackers can obtain sensitive information, such as how a particular system or production process operates, which can be used for further attacks in the future. | [28] |
| Data tampering | Data tampering attacks are those in which data (e.g., industrial control data) are stored or transmitted without permission for malicious purposes. | [40] |
| False Data Injection | Industrial control systems without an authentication mechanism can use this attack to inject malicious code and malformed commands. | [23] |
| Advanced Persistent Threats (APT) | APTs are highly intelligent attacks that set clear targets, collect information over the long term, and perform more sophisticated attacks by combining new technologies and various attack methods. | [38,41,42,43] |
| Zero-Day | These attacks exploit a security vulnerability that has not yet been disclosed, and it is difficult to defend and develop a patch as only a small number of people are aware of such a vulnerability until it is disclosed to the public. | [44] |
| Attacks against AI (machine learning and data analytics) | These attacks change the input data supplied to the system causing the AI system to malfunction, damaging the learning process by tampering with the measurement values of IIoT sensors and manipulating training data, and stealing information about the training model by extracting the data used to train the AI model. | [45,46,47] |
| Phishing | As the most common cyberthreat, phishing refers to the act of stealing useful information or attempting theft through a connected device (a link to a fake bank website, an email infected with malware, etc.) disguised as a legitimate message. | [48,49] |
| Physical | This refers to the illegal manipulation, changing, or causing of physical damage to accessible devices (e.g., sensors, industrial IoT terminals, production facilities) by an attacker with physical access. | [50] |
| Step | Description |
|---|---|
| 1 | The raw malware binary files are converted into images. A one-dimensional array of malware raw binary files is converted to grayscale image pixels with values ranging from 0 (black) to 255 (white) and reconstructed into a two-dimensional array. |
| 2 | The image is normalized to the size of 112 × 112 pixels. During the dimensionality reduction stage, certain important features may be omitted, but most of the malware images in the Malimg dataset maintain their texture properties in the normalization stage. |
| 3 | The dataset is split into a training set (70%) and a test set (30%). |
| 4 | The data converted into images are applied to the CNN. |
| 5 | CNN is converted to flatten. As the last layer of the CNN is in the form of an n-dimensional matrix, it is flattened. Flattening refers to the conversion of an n-dimensional matrix into a one-dimensional column matrix. |
| 6 | The malware family is classified by the CNN model and Softmax is used for multiclass classification. |
| Parameter | Value |
|---|---|
| Input shape | 112 × 112 × 3 |
| Epochs | 40 |
| Dropout | 0.45 |
| Learning rate | 0.0001 |
| Batch size | 32 |
| Loss function | Categorical cross entropy |
| Optimizer | Adam |
| Trainable parameters | 1,009,761 |
| Non-trainable parameters | 800 |
| Parameter | Description |
|---|---|
| True Positive (TP) | Number of malware correctly identified as malware |
| True Negative (TN) | Number of non-malware correctly identified as non-malware |
| False Positive (FP) | Number of non-malware incorrectly identified as malware |
| False Negative (FN) | Number of malware incorrectly identified as non-malware |
| No. | Image Size | Dropout | Learning Rate | Accuracy (%) | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|---|---|---|
| ① | 64 × 64 | 0.45 | 0.0001 | 97.93 | 98.02 | 97.91 | 97.96 |
| ② | 112 × 112 | 0.45 | 0.0001 | 98.93 | 98.93 | 98.93 | 98.92 |
| ③ | 192 × 192 | 0.45 | 0.0001 | 98.36 | 98.47 | 98.30 | 98.38 |
| ④ | 112 × 112 | 0.45 | 0.0005 | 95.54 | 95.60 | 95.56 | 95.58 |
| ⑤ | 112 × 112 | 0.45 | 0.0010 | 97.86 | 97.87 | 97.87 | 97.87 |
| ⑥ | 112 × 112 | 0.35 | 0.0001 | 98.04 | 98.05 | 98.01 | 98.03 |
| ⑦ | 112 × 112 | 0.55 | 0.0001 | 98.32 | 98.44 | 98.20 | 98.32 |
| ID | Class Name | Malware Type | Precision | Recall | F1-Score | Support |
|---|---|---|---|---|---|---|
| 0 | Adialer.C | Dialer | 1.00 | 1.00 | 1.00 | 37 |
| 1 | Agent.FYI | Backdoor | 1.00 | 1.00 | 1.00 | 35 |
| 2 | Allaple.A | Worm | 0.99 | 1.00 | 1.00 | 885 |
| 3 | Allaple.L | Worm | 1.00 | 1.00 | 1.00 | 477 |
| 4 | Alueron.gen!J | Worm | 0.98 | 1.00 | 0.99 | 59 |
| 5 | Autorun.K | Worm: AutoIT | 1.00 | 1.00 | 1.00 | 32 |
| 6 | C2LOP.P | Trojan | 0.95 | 0.86 | 0.90 | 44 |
| 7 | C2LOP.gen!g | Trojan | 0.92 | 0.97 | 0.94 | 60 |
| 8 | Dialplatform.B | Dialer | 1.00 | 1.00 | 1.00 | 53 |
| 9 | Dontovo.A | Trojan Downloader | 1.00 | 1.00 | 1.00 | 49 |
| 10 | Fakerean | Rogue | 1.00 | 0.98 | 0.99 | 114 |
| 11 | Instantaccess | Dialer | 1.00 | 1.00 | 1.00 | 129 |
| 12 | Lolyda.AA1 | PWS | 1.00 | 1.00 | 1.00 | 64 |
| 13 | Lolyda.AA2 | PWS | 1.00 | 1.00 | 1.00 | 55 |
| 14 | Lolyda.AA3 | PWS | 1.00 | 1.00 | 1.00 | 37 |
| 15 | Lolyda.AT | PWS | 1.00 | 0.98 | 0.99 | 48 |
| 16 | Malex.gen!J | Trojan | 1.00 | 0.95 | 0.97 | 41 |
| 17 | Obfuscator.AD | Trojan Downloader | 1.00 | 1.00 | 1.00 | 43 |
| 18 | Rbot!gen | Backdoor | 1.00 | 1.00 | 1.00 | 47 |
| 19 | Skintrim.N | Trojan | 1.00 | 1.00 | 1.00 | 24 |
| 20 | Swizzor.gen!E | Trojan Downloader | 0.83 | 0.76 | 0.79 | 38 |
| 21 | Swizzor.gen!I | Trojan Downloader | 0.81 | 0.85 | 0.83 | 40 |
| 22 | VB.AT | Worm | 1.00 | 1.00 | 1.00 | 122 |
| 23 | Wintrim.BX | Trojan Downloader | 0.90 | 0.97 | 0.93 | 29 |
| 24 | Yuner.A | Worm | 1.00 | 1.00 | 1.00 | 240 |
| accuracy | 0.99 | 2802 | ||||
| macro avg | 0.98 | 0.97 | 0.97 | 2802 | ||
| weighted avg | 0.99 | 0.99 | 0.99 | 2802 |
| Citation | Year | Proposed Methods | Accuracy (%) | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|---|---|
| [96] | 2019 | CNN, LSTM + gray | 95.50 | 95.50 | 95.50 | 95.50 |
| [99] | 2019 | CNN(2), LSTM + gray | 96.30 | 96.30 | 96.20 | 96.20 |
| [69] | 2020 | LNBP + LDA + gray | 89.40 | 91.00 | 89.00 | 90.00 |
| [97] | 2020 | CNN + Color | 98.82 | 98.85 | 98.81 | 98.75 |
| [105] | 2021 | CNN(VGG19) + gray | 97.62 | 97.68 | 97.50 | 97.20 |
| [98] | 2021 | CNN(VGG16) + Color | 99.72 | 99.72 | 99.60 | 99.66 |
| [79] | 2022 | CNN + gray | 95.63 | 95.34 | 95.30 | 94.98 |
| [100] | 2022 | CNN + gray | 96.00 | 95.30 | 96.00 | 95.20 |
| Our model | 2022 | CNN + gray | 98.93 | 98.93 | 98.93 | 98.92 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, H.-m.; Lee, K.-h. IIoT Malware Detection Using Edge Computing and Deep Learning for Cybersecurity in Smart Factories. Appl. Sci. 2022, 12, 7679. https://doi.org/10.3390/app12157679
Kim H-m, Lee K-h. IIoT Malware Detection Using Edge Computing and Deep Learning for Cybersecurity in Smart Factories. Applied Sciences. 2022; 12(15):7679. https://doi.org/10.3390/app12157679
Chicago/Turabian StyleKim, Ho-myung, and Kyung-ho Lee. 2022. "IIoT Malware Detection Using Edge Computing and Deep Learning for Cybersecurity in Smart Factories" Applied Sciences 12, no. 15: 7679. https://doi.org/10.3390/app12157679






