1. Introduction
With the rapid development of computer science and telecommunication, users can now enjoy various services via the Internet such as online shopping, remote medical monitoring, etc. These services produce massive data, which may contain a great amount of sensitive data like cellphone numbers, accommodation addresses, etc. Thus, the confidentiality of these data should be highly protected [
1]. Encryption is a promising method to provide security protection for these sensitive data. Through encryption, these data are transformed into ciphertexts and stored securely in data clusters. However, traditional encryption techniques will prevent some common operations on ciphertexts—especially in terms of searching. For instance, a data owner wants to share some important data with some receivers in the multi-tenant data center, but data receivers do not know the exact location where these data have been stored. Since these data have been transferred into ciphertexts, it is inconvenient for them to search these encrypted data and determine the exact file they want. Thus, how to enable data owners to encrypt their data and make them searchable is a challenging and practical problem. The key word search mechanism is a promising tool to satisfy this demand. A keyword search protocol usually involves the participation of three parties: uploader, storage server, and receiver. The interaction process of a keyword search usually involves three steps:
Firstly, the uploader generates the search index for the corresponding keywords and uploads them with the ciphertexts to the storage server.
Secondly, the receiver computes the trapdoor for the desired keywords and sends the trapdoor to the storage server.
Thirdly, the storage server checks if the trapdoor generated by the receiver corresponds with the search index. The ciphertexts are returned to the receiver on the condition that the trapdoor and the search index are matched.
The first keyword search scheme based on PKC (Public Key Cryptography) was presented by Boneh et al. [
2] in 2004. Afterwards, many studies [
3,
4,
5] have been presented to provide better performances, higher security level, and more advanced functions. Aside from these properties, fine-grained access managements are also important because an uploader can take this advantage to make self-centric access policies on their private data [
6,
7,
8,
9]. To better satisfy this demand, Sahai et al. presented attribute-based encryption (ABE) [
10,
11,
12] which efficiently brings flexible access control. Researchers have also taken the advantages of ABE [
13,
14] and keyword search to present attribute-based keyword search schemes [
15,
16,
17,
18]. Until now, several schemes have achieved keyword search based on ABE, but the performance can still be further optimized. To begin with, although the proposed scheme can provide flexible revocation, they cannot minimize the damage when key exposure occurs. In multi-tenant architecture environments, the number of users is very large and key exposure seems inevitable. If key leakage happens, the confidentiality of the whole system will no longer exist. Further, in most of the existing schemes, there exist additional transmission overheads of key updating. Consequently, an attribute-based keyword search with key exposure protection mechanism and efficient key refreshing [
8] urgently needs to be proposed.
In this paper, we aim to tackle the above problems and present a key insulated attribute-based data retrieval with key word search (KI-ABDR-KS) scheme for multi-tenant architecture. We achieve flexible self-centric search management by utilizing a CP-ABE (Ciphertext Policy Attribute Based Encryption) [
12] mechanism. The data owner generates the index for ciphertext using a self-centric access policy, indicating what kinds of receivers are given the privileges to gain access to these encrypted data. The receiver generates the trapdoor for the desired keyword using the private key she owns [
19,
20]. The cloud server checks if the trapdoor generated by receiver corresponds with the search index. The ciphertexts are returned to the receiver on the condition that the trapdoor and the search index are matched. A key insulation mechanism [
21] is introduced to guarantee full security if key leakage occurs and helps to realize highly efficient key updating [
22].
The detailed contributions established in the article are as follows:
- (1)
We present a novel keyword search based on ABE with key exposure protection. In our scheme, a data owner can make self-centric access policy of the encrypted data. Only if the possessing attributes match with the policy can a receiver generate a valid trapdoor and search the ciphertext.
- (2)
The proposed scheme provides secure key exposure protection as well as both backward and forward security.
- (3)
In our scheme, the system lifespan is split up into several time periods. The public parameters of the cryptosystem remain unvaried during the whole lifespan, and users’ private keys are refreshed termly. When key leakage occurs, a user’s private keys shall be updated in a timely fashion to minimize the damage brought by key exposure.
- (4)
Our scheme achieves keyword semantic security under chosen keyword attack. Meanwhile, it is shown to be superior in terms of computation efficiency compared to existing works.
2. Related Works
2.1. Attribute-Based Cryptosystem
In a classical PKC mechanism, a user is given the right to make secure data shared with others in a private way based on their identities. However, it is not fully practical when data sharing is conducted via a more expressive access policy. In some scenarios (e.g., cloud computing), the amount of users and private data may be enormous. Assuming that a data owner wants to share some sensitive data with certain users using traditional encryption methods, she may run encrypt algorithms many times, since each user’s public key is unique and the encryption is inefficient.
ABE is a cryptographic notion supporting flexible data access control, and is equipped with many advantages. In ABE, the concept of “access policy” is introduced; only if the user’s attributes suit with the policy can she complete decryption. A file owner may set a data-centric access policy without concern about the specific identity of each user in the system (note that the amount of users in the system may be very large). Consequently, ABE is a more effective tool for data protection in large data outsource platforms. Existing literatures related to ABE have achieved many results in terms of fine-grained access control [
7,
13], revocation [
6], key abuse protection [
9], etc. Researchers have also implemented ABE in several practical scenarios such as wireless communications, cloud computing [
14], etc.
2.2. Attribute-Based Keyword Search
Attribute-based keyword search (ABKS) combines the advantages of ABE and searchable encryption and has been given attention from researchers all over the world. Han et al. in [
15] proposed an attribute-based searchable encryption with key policy. Their scheme achieves flexible access control on the search indexes of ciphertext. However, the proposed scheme directly sends the users’ private keys to the file server as the trapdoor. This results in key exposure to the file server. If the server becomes dishonest or is being attacked, all of the legal private keys will be obtained by the attackers, which will bring huge damage to the whole cryptosystem. Yang in [
16] designed a keyword search scheme based on ABE and applied it to an electronic health system. The proposed scheme supports fine-grained authorization and flexible revocation in the semi-trusted cloud server. However, the scheme generates a unique additional key pair for each user in the system. The generation of a search index also involves the public key of each user; this will bring a considerable computation burden when the amount of users is large. Sun et al. in [
17] presented a novel searchable encryption for cloud computing based on CP-ABE. Their scheme provides self-centric search authorization as well as authenticity check over the encrypted data. The proposed scheme also achieves selective confidentiality under chosen keyword attack and secure revocation. Zheng et al. in [
18] proposed a verifiable keyword search scheme. Their scheme permits users with promising credentials to search the ciphertext using the generated trapdoor. Their scheme can also distinguish if a server has honestly carried out the tasks which are sent by users. Miao et al. in [
23] applied ABKS to modern medical systems and demonstrated the high efficiency and security of their scheme. Zhou et al. in [
24] presented a novel type of ABKS which supports both online and offline decryption; thus, it was equipped with better flexibility. Wang et al. in [
25] did some path breaking work in terms of introducing the attribute and keywords vector to optimize the decryption efficiency. Dong et al. in [
26] proposed a lightweight ABKS scheme, the application of which is very appropriate to networks with constrained computation resources (e.g., mobile networks). Li et al. in [
27] tackled the search authorization issue in the cloud and designed a secure ABKS scheme which not only achieves trapdoor unlinkability and confidentiality, but also resists collusion attack. Vahid et al. in [
28] combined attribute-based cryptography with fuzzy search token techniques and presented a novel ABKS scheme. They also proved it to be secure under keyword guessing attack.
The existing works mentioned above have achieved significant progress in attribute-based cryptosystems and keyword search mechanisms. However, these schemes lack the security protection mechanism when key exposure happens. In a large data outsourcing system with multiple users, key exposure seems unavoidable. Once it is leaked, any user obtaining the private key can generate a legal trapdoor and the confidentiality of the whole system will no longer exist. Thus, it is essential to carryout key exposure protection for attribute-based keyword search schemes.
3. Models and Definitions
3.1. Framework of KI-ABDR-KS
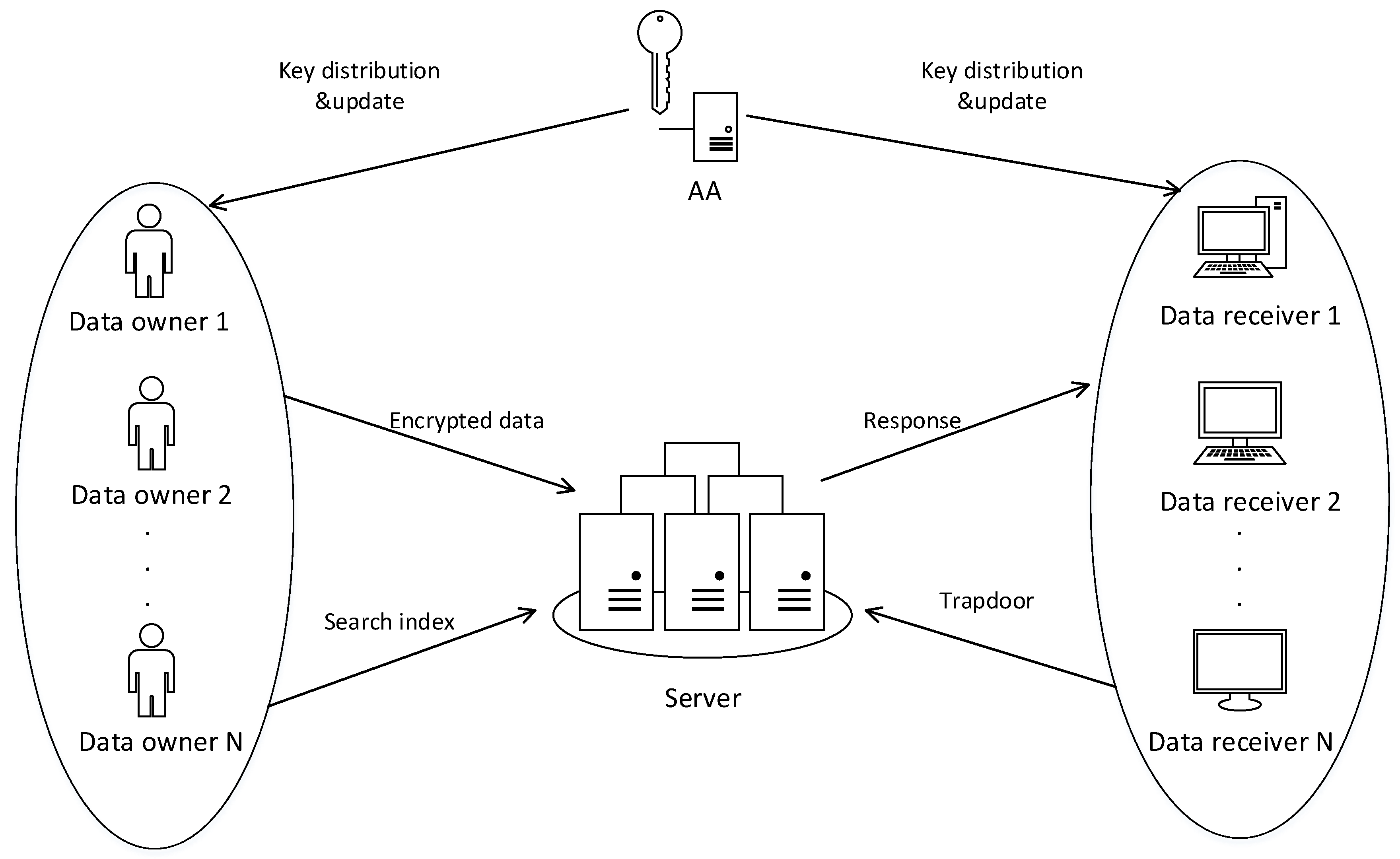
The system framework of our scheme is illustrated in
Figure 1. It contains four entities: attribute authority (AA), multi-tenant server, data owner, and data receiver. AA manages universal attributes and distributes users’ private keys. It is also responsible for updating users’ temporal private keys when the cryptosystem enters into a new time period. The data owner generates a secure index for each ciphertext using a self-centric policy, while the data receiver generates a trapdoor for the required ciphertext according to the desired keywords. The multi-tenant server provides secure storage services for the encrypted data and responses to receivers’ requests if the trapdoors are valid.
3.2. Formulized Definitions of KI-ABDR-KS
In this section, we will give the interactions between entitites illustrated in
Figure 1 and the formulized definitions of the algorithms. The proposed scheme contains seven algorithms, as below:
: This algorithm is run by AA. It takes a security number as input and outputs system public parameters as well as master keys.
: This algorithm is run by AA. It takes system parameters, the initial time period, and the attribute set a user owns as input; it outputs the master key of key helper and the initial private key for a user.
: This algorithm is run by AA. It takes system parameters and the newest time period as input. It outputs the key updating component for a user.
: This algorithm is run by the users. It takes the temporal private key of the previous period and key updating component as input, and it outputs the temporal private key at the latest version.
This algorithm is run by the data owner. It takes system parameters, an access structure, and key words as input; it outputs an index for a ciphertext.
This algorithm is run by the users. It takes users’ private keys and key word as input; it outputs a trapdoor.
This algorithm is run by the server. It takes users’ trapdoor as input and outputs the corresponding ciphertext.
3.3. Security Requirements
(1) Keyword semantic security: This security property guarantees that an cannot obtain the ciphertext without the valid trapdoor. In this paper, the requirement of key semantic security can be proved by a game described as follows:
Step 1
runs to obtain the related parameters in the game.
claims an access structure and is the attribute set involved.
Step 2
query: can obtain the trapdoor of several keywords for attribute set by running algorithm and sends the results back to Note that
Note that the trapdoor queries contain the implication of private key generation query.
Step 3
At the current time period , picks and , which have not been queried before. picks and runs algorithm to obtain .
outputs as a guess of . If , then wins the game.
The advantage of can be denoted by .
(2) Backward and forward security: This security property guarantees the system’s security and confidentiality when key exposure happens.
4. Concrete Constructions
In this section, we will provide the concrete algorithms from the system level viewpoint. These algorithms are the concrete and detailed expansions of the formulized definitions in
Section 3.2 based on the above defined algorithms.
Define two
order groups
. Let
be a bilinear pairing and
is a generator of
. Define a global attribute set
. Define hash functions:
,
. AA randomly chooses secret numbers
and computes
. The system masker keys are
while system public parameters are
.
At the initial time period , for a user possessing attribute set , AA picks and calculates . The initial private key of a user is denoted by . Note that remains unchanged throughout the whole system lifetime, while updates when system enters a new time period.
When the system arrives in a new period from to , AA computes the key updating component and sends the result to the user. Then, a user updates her temporal private key by calculating ( remains unchanged).
Data owner picks
and chooses a polynomial
for each node
in the access control structure
. Let the threshold value of the node be one more than the degree of
. For the root node, the data owner sets
. For others, let
Denote
to be the leaf nodes in
, then the search index
is constructed as:
For the desired keyword
, the data receiver picks a random number
and calculates the trapdoor
as Equation (2):
Then, the data receiver sends to the cloud server.
The cloud server tests:
If Equation (3) is set up, the cloud server sends the corresponding ciphertext to the data receiver.
5. Discussion
5.1. Keyword Semantic Security
Before giving our proof, we first give the hardness assumption [
17] that our scheme relies on:
Decision bilinear Diffie–Hellman assumption (DBDH): Picks random numbers
, assuming that the value of (
) are given, no probabilistic polynomial-time algorithm can distinguish the tuples (
) and (
) with a non-negligible probability.
Theorem 1. Our KI-ABDR-KS is keyword semantic secure if the DBDH hardness assumption holds.
Proof. If our scheme can be broken by an with advantage of , then a simulator can be constructed to break the DBDH hardness assumption with an advantage of . The challenge game is described as follows:
Let
and
be two cyclic groups with prime order
. Denote g as the generator of
. Let
be a bilinear pairing. Define a global attribute set
. Define hash functions
,
.
picks
,
and sets:
The aim of the simulator is to guess the value of
claims a challenging access structure (containing attribute set ) and plays the game on it.
When makes a trapdoor query for keyword on attribute set , the simulator responds as follows:
Simulator picks
, sets:
Then, the trapdoor is constructed as:
Note that the trapdoor queries contain the implication of private key generation query.
:
picks key words , . Simulator chooses , picks , and calculates the following information:
Simulator sends the above indexes to .
Let
, so we have:
outputs a value If , wins the game.
Next, we will analyze the simulator’s advantage in distinguishing the tuples in DBDH assumption.
If
is an invalid search index and
guesses randomly,
If
is a valid index. According to the definition,
has an advantage
From what has been discussed, the simulator’s advantage can be denoted by:
☐
5.2. Users’ Privacy and Trapdoor Unlinkability
In our scheme, the users’ privacy can be highly protected. According to the algorithm in our KI-ABDR-KS, a secret component is embedded into the trapdoor. Thus, the service provider cannot obtain any sensitive information of the private key. Besides, since the secret component is chosen by different users at random, it is computationally infeasible for cloud severs to distinguish different trapdoors containing the same key words, which meets the security demand of trapdoor unlinkability.
5.3. Forward and Backward Security
Our scheme can provide protection when key exposure happens. When key exposure happens at period , the system can still maintain its security by updating users’ temporal private keys to version. A user’s private key leakage during will not harm the security in the rest time periods. Our scheme also supports random access key updating, since attribute authority is capable of updating users’ temporal private keys from any previous time periods (denote these time periods by) to the last version in just one step by calculating .
5.4. Efficient Key Updating with Constant Size of Parameters
The process of key updating in the proposed KI-ABDR-KS is very efficient because when a new time period arrives, only partial key components have to be refreshed. According to the algorithm, the calculation of key updating component only takes one exponentiation. More importantly, though users’ private keys are updated periodically, the system public parameters remain the same throughout the whole lifetime. This will reduce the considerable computation cost which parameter synchronization brings about.
5.5. Performance Evaluation
We compare our scheme with schemes in [
17,
23,
28], which also implement attribute-based cryptosystem to achieve flexible key word search. The comparison is conducted with regard to the computation cost of each algorithm. Denote “Pair”, “Exp” to be the bilinear pairing and exponential operations, respectively, and “
n” is the amount of attributes involved. The results are listed in
Table 1.
From comparison, it can be seen that efficiency of
,
,
, and
are higher in our scheme. The
algorithm takes more exponential operations in our scheme, but it is run by the cloud server which has large computation capacity. Thus, this will not add a computation burden on the user side. In the scheme found in Reference [
17], the access structure only supports AND gate, but our scheme provides a more flexible access structure which supports AND along with OR gate; thus, the
algorithm in our scheme takes more exponential operations. Furthermore, unlike [
23,
28], our scheme is equipped with the function of highly efficient key updating. The system public parameters remain constant regardless of the number of attributes in the system and do not need to be changed during the process of key updating; this will reduce the considerable overheads brought by parameters synchronization. Consequently, our scheme has a better performance from the prospective of the overall efficiency.
6. Conclusions
In this paper, we propose a novel key insulated attribute-based data retrieval with keyword search mechanism. The proposed scheme can provide self-centric search indexes for the encrypted data. The proposed scheme also provides secure key exposure protection and full security when key exposure happens. By performance analysis, our scheme is of high-level security and is superior with respect to computation efficiency.