Store-Carry and Forward-Type M2M Communication Protocol Enabling Guide Robots to Work together and the Method of Identifying Malfunctioning Robots Using the Byzantine Algorithm
Abstract
:1. Introduction
2. Related Work
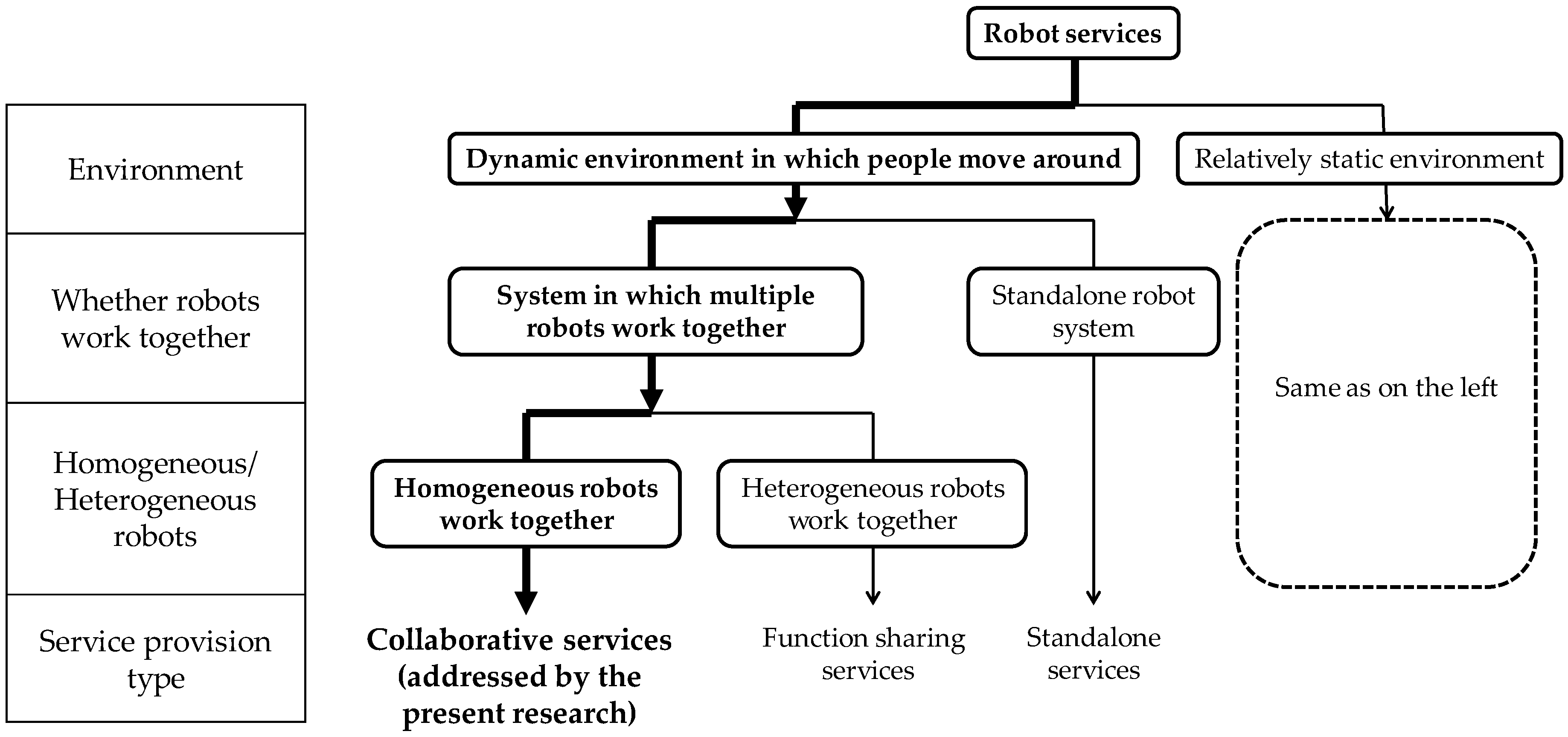
2.1. Network Robot Services
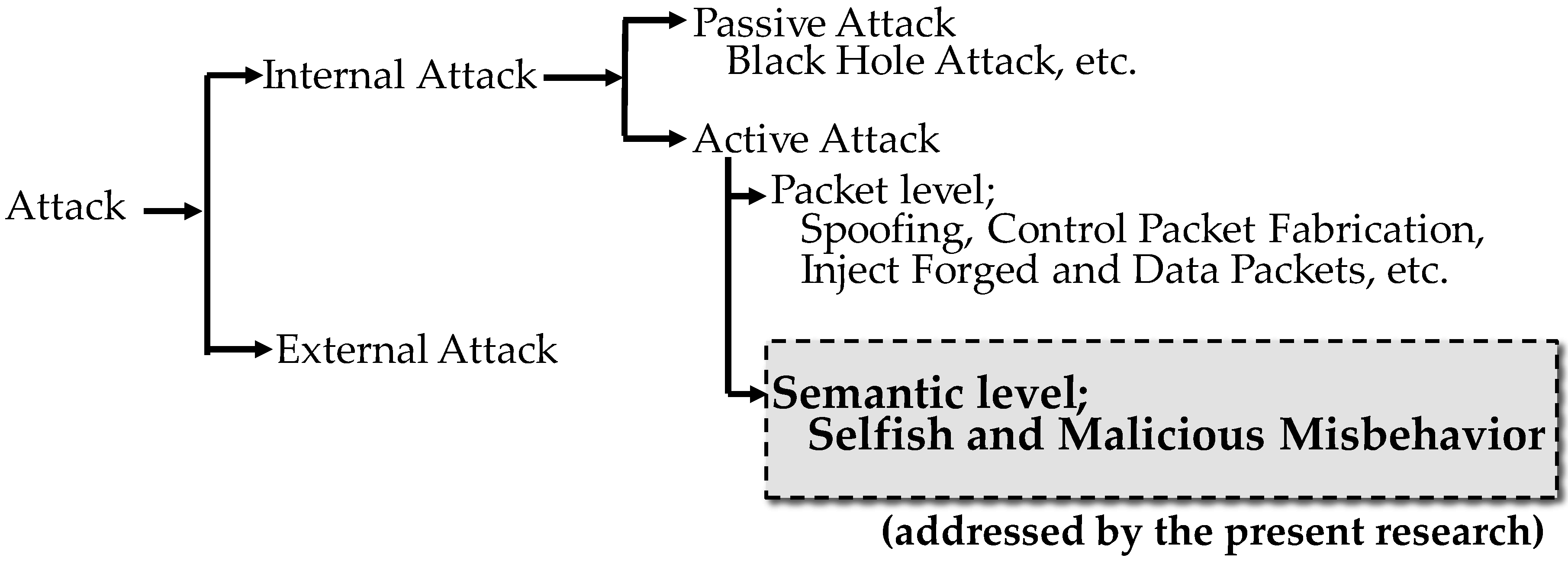
2.2. M2M Systems and Security
2.2.1. M2M Area Network
2.2.2. Security of M2M Area Networks
3. Architecture for Enabling Robots to Work Together
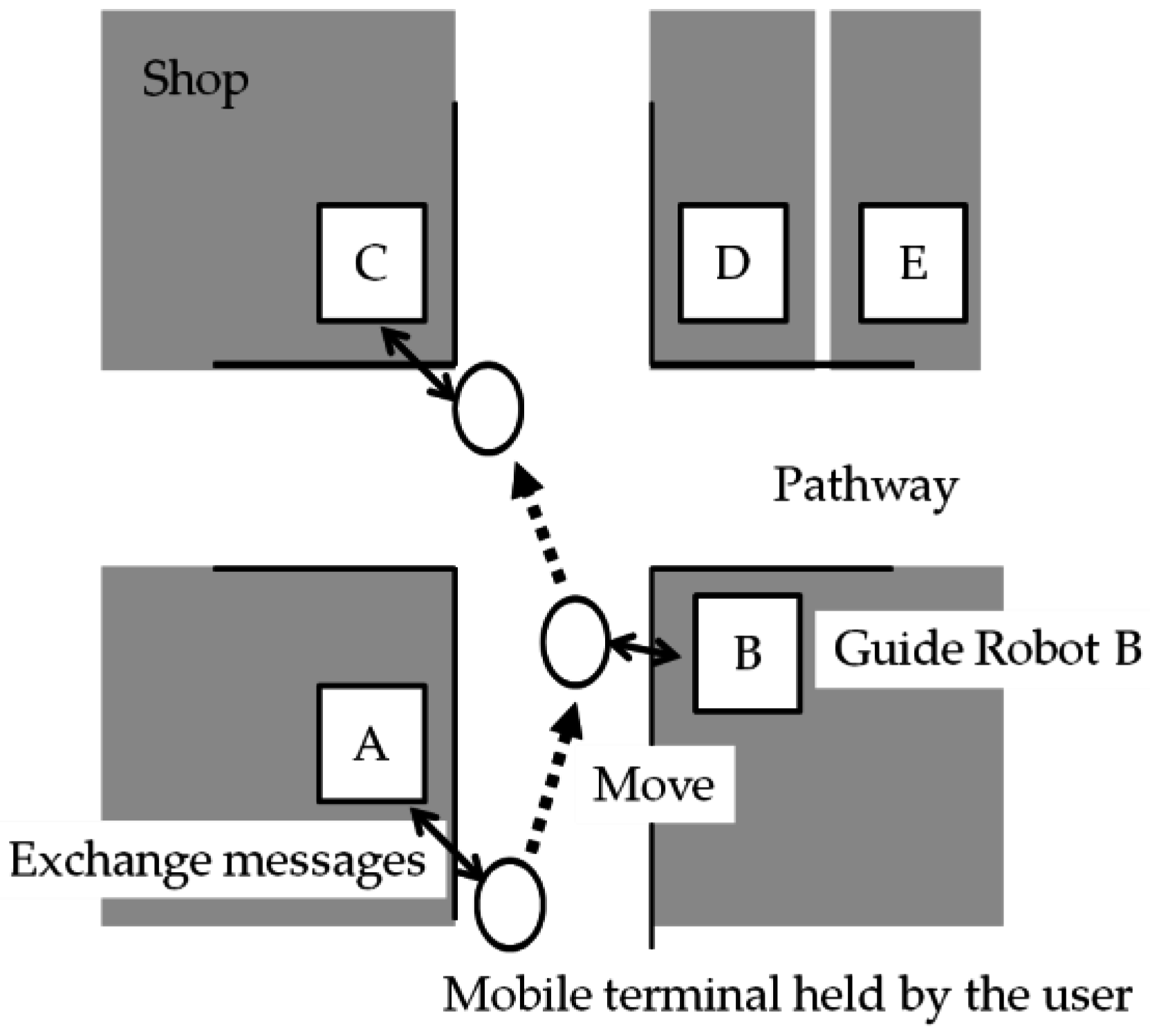
3.1. Overview of Direction Guidance and the Functional Structure
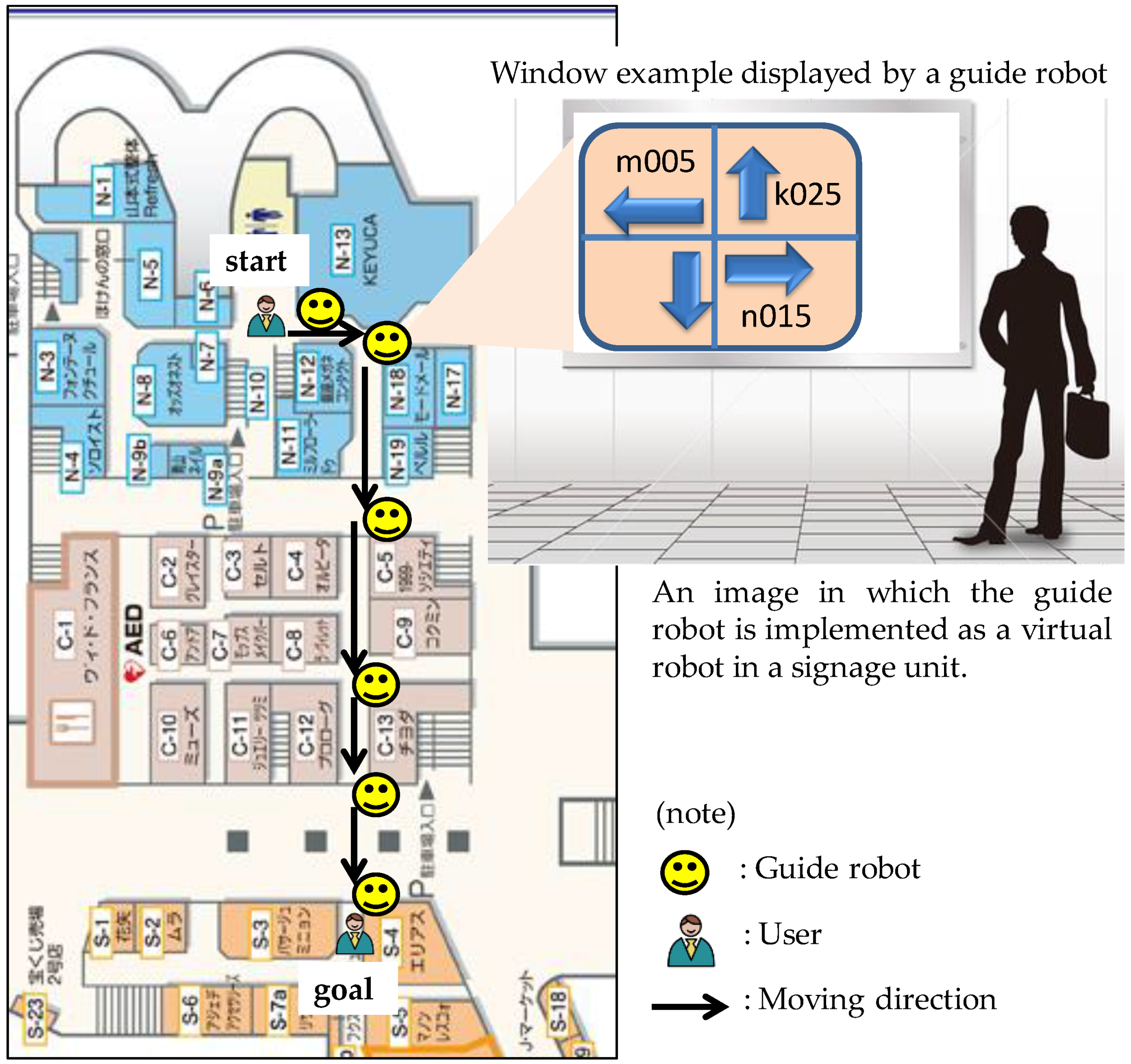
3.1.1. Overview of Direction Guidance
3.1.2. Functional Structure of a Robot
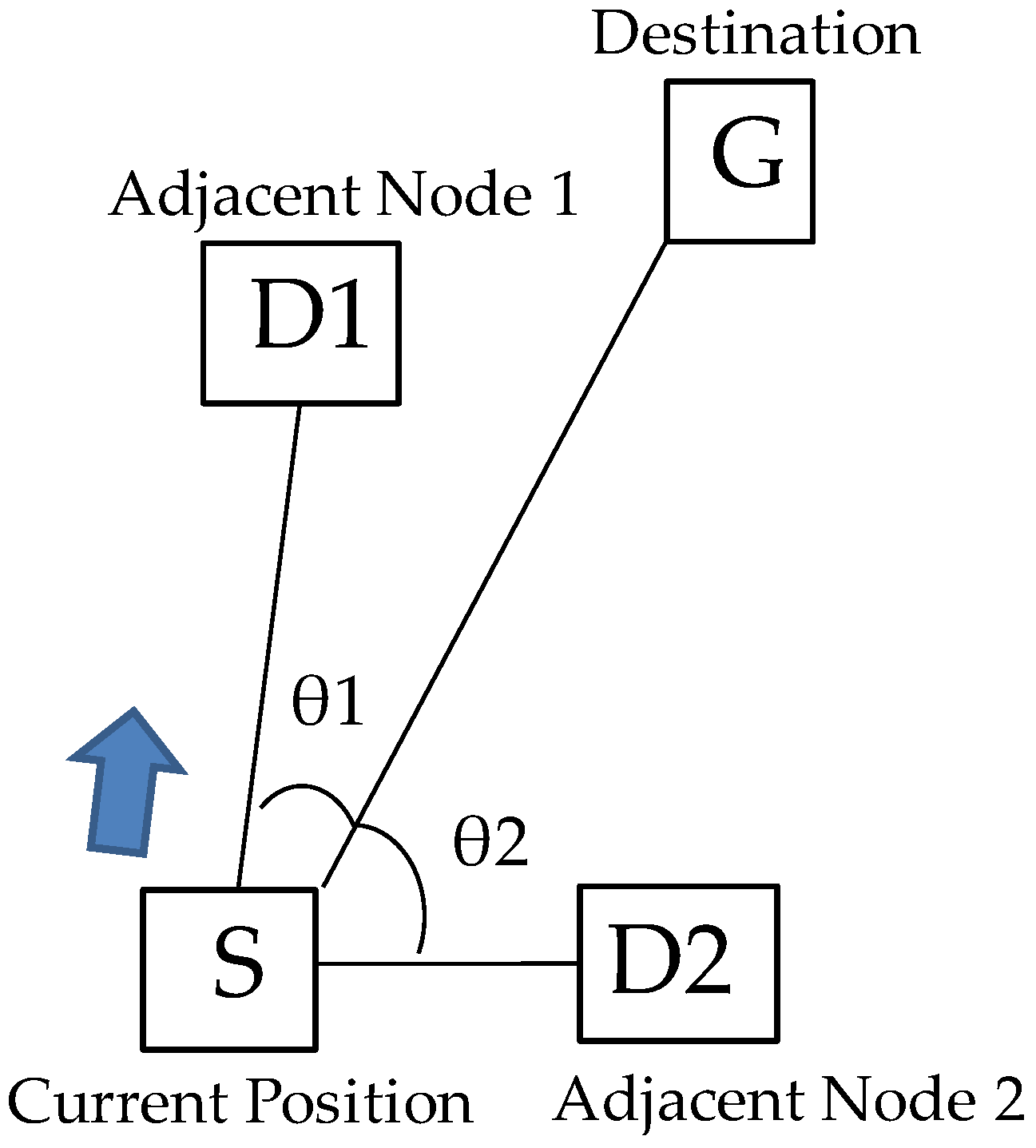
3.2. Guidance Based on the Angle-Based Algorithm
4. Method of Identifying Malfunctioning Robots Using the Byzantine Algorithm
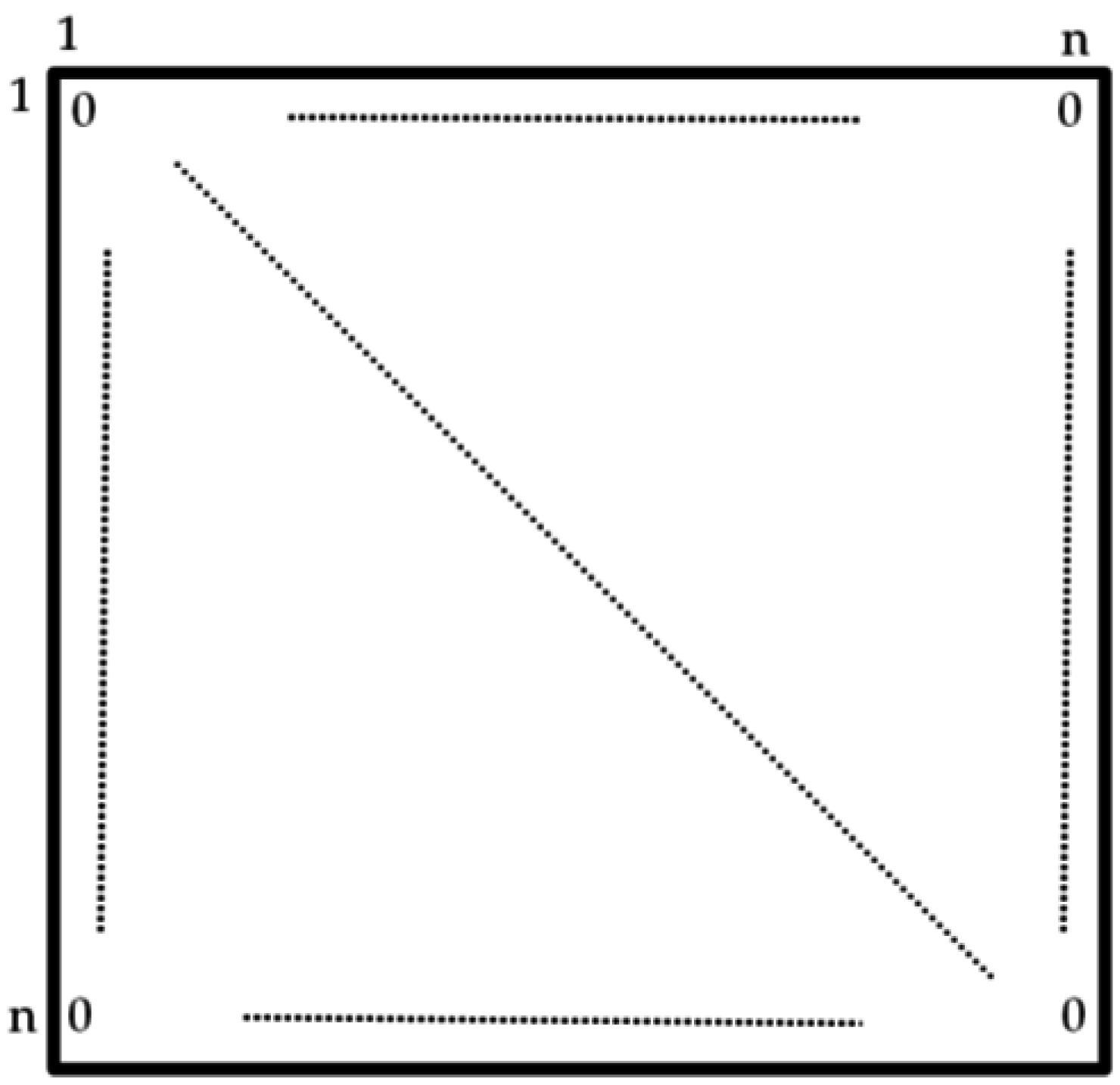
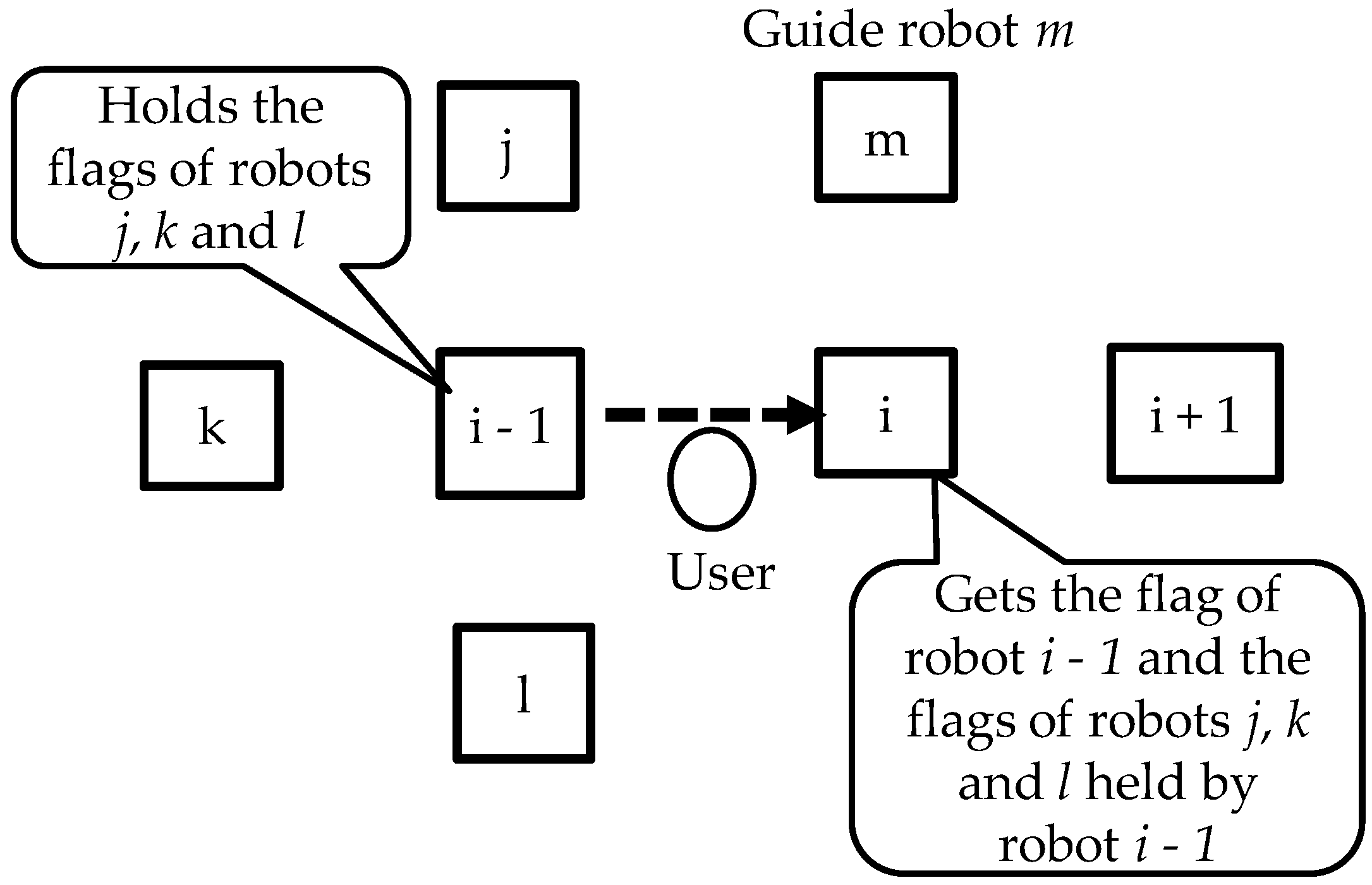
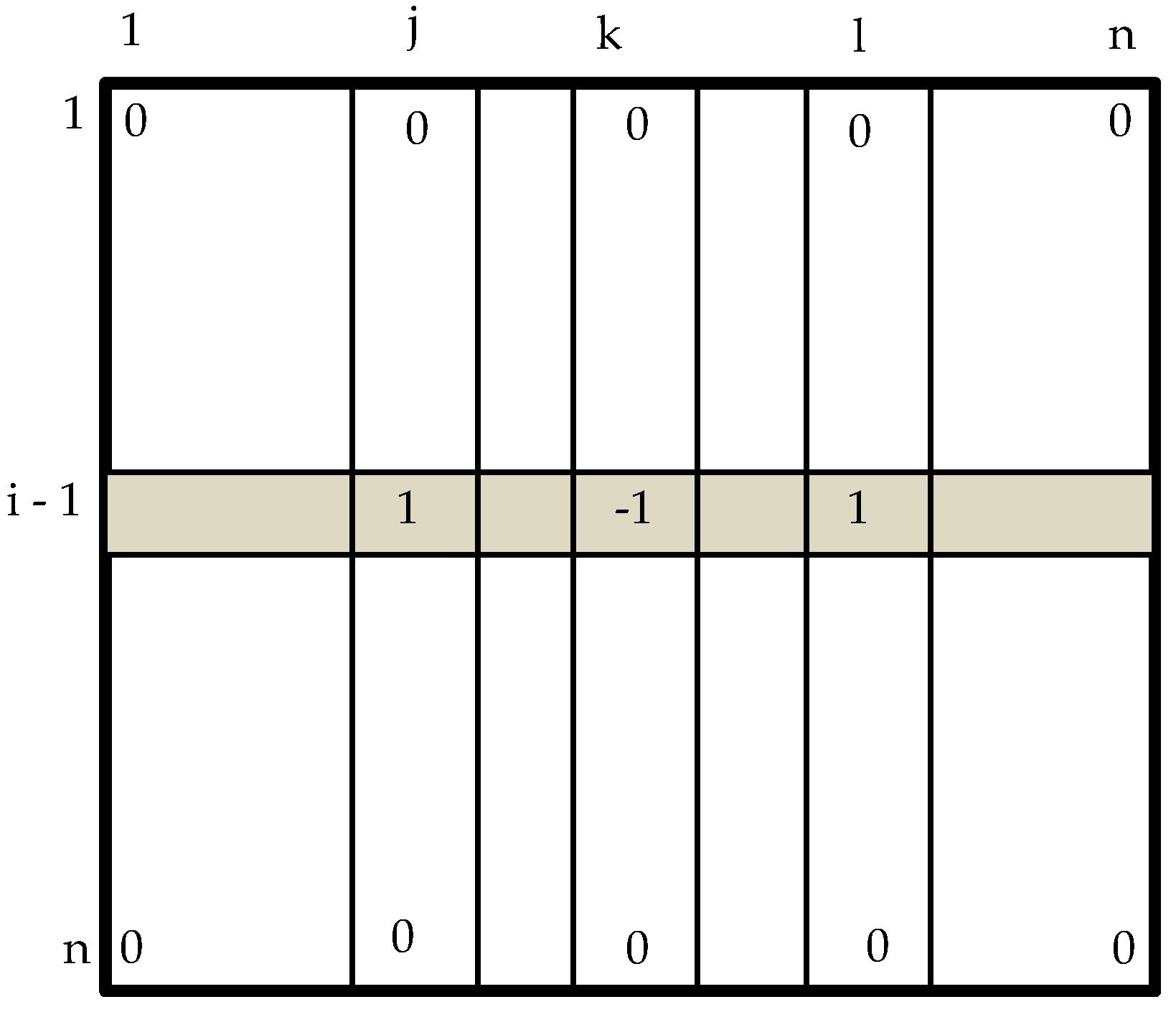
4.1. Distributed Cooperative Protocol for Store-Carry and Forward-Type M2M Communication
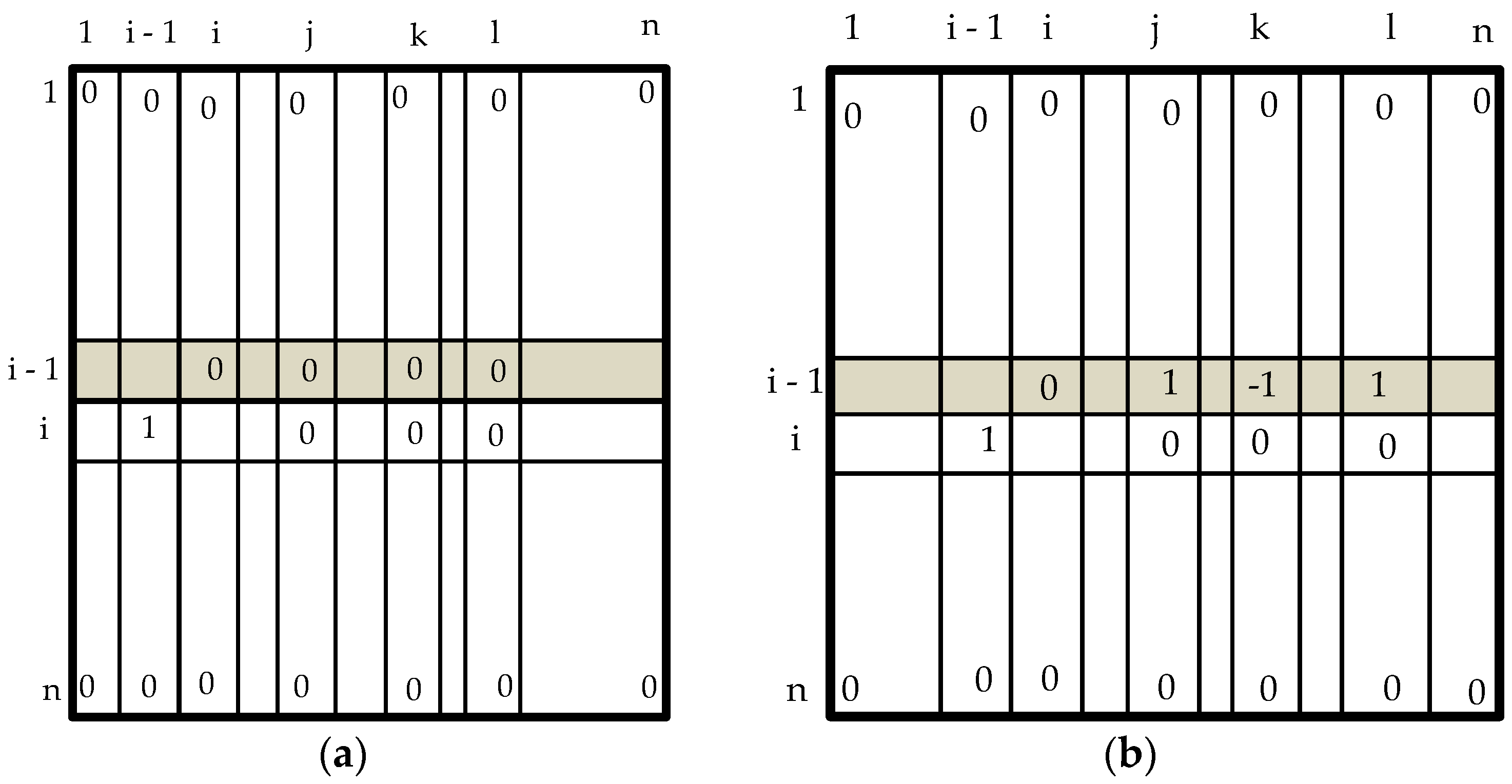
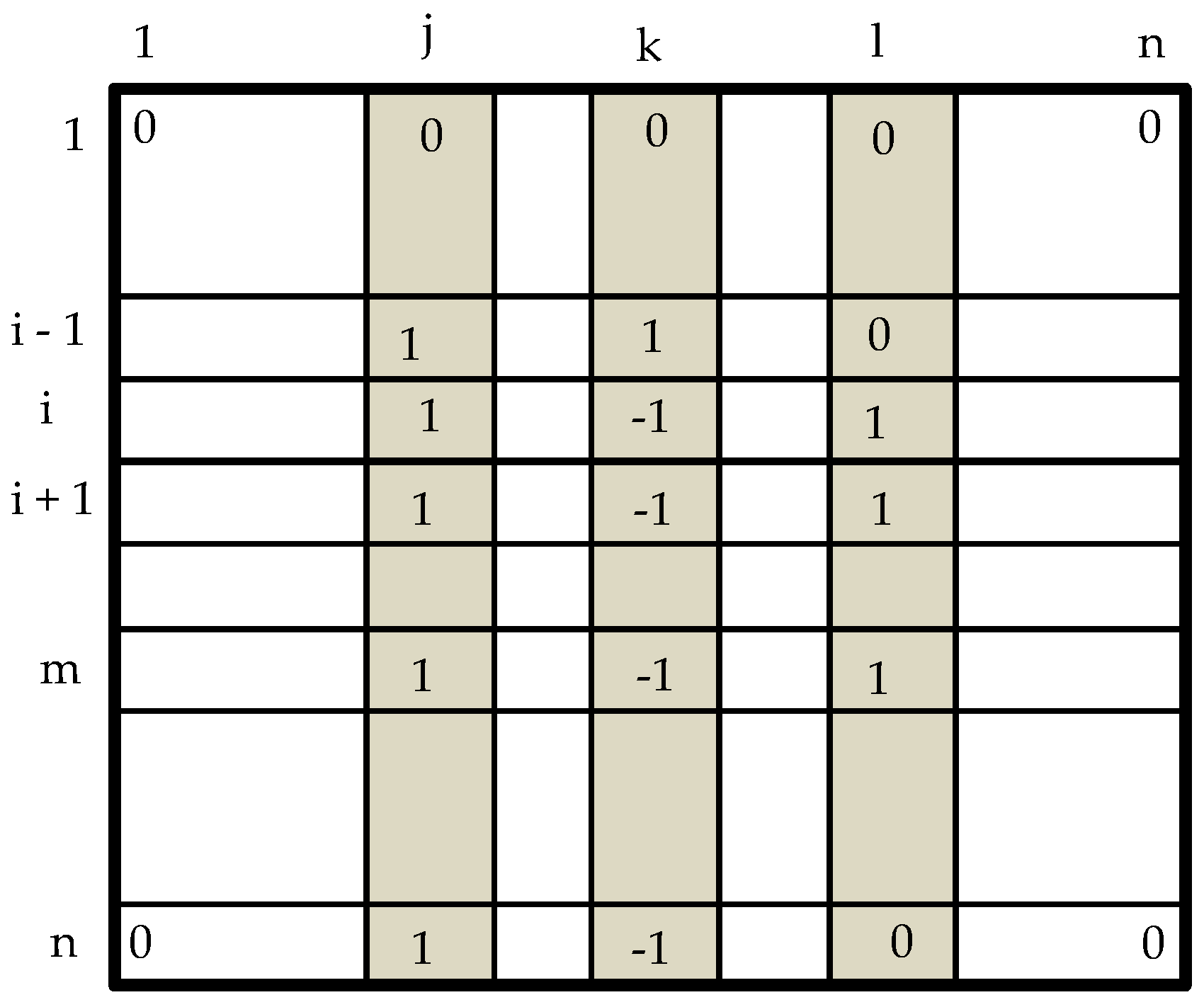
4.2. Algorithm for Identifying Malfunctioning Robots
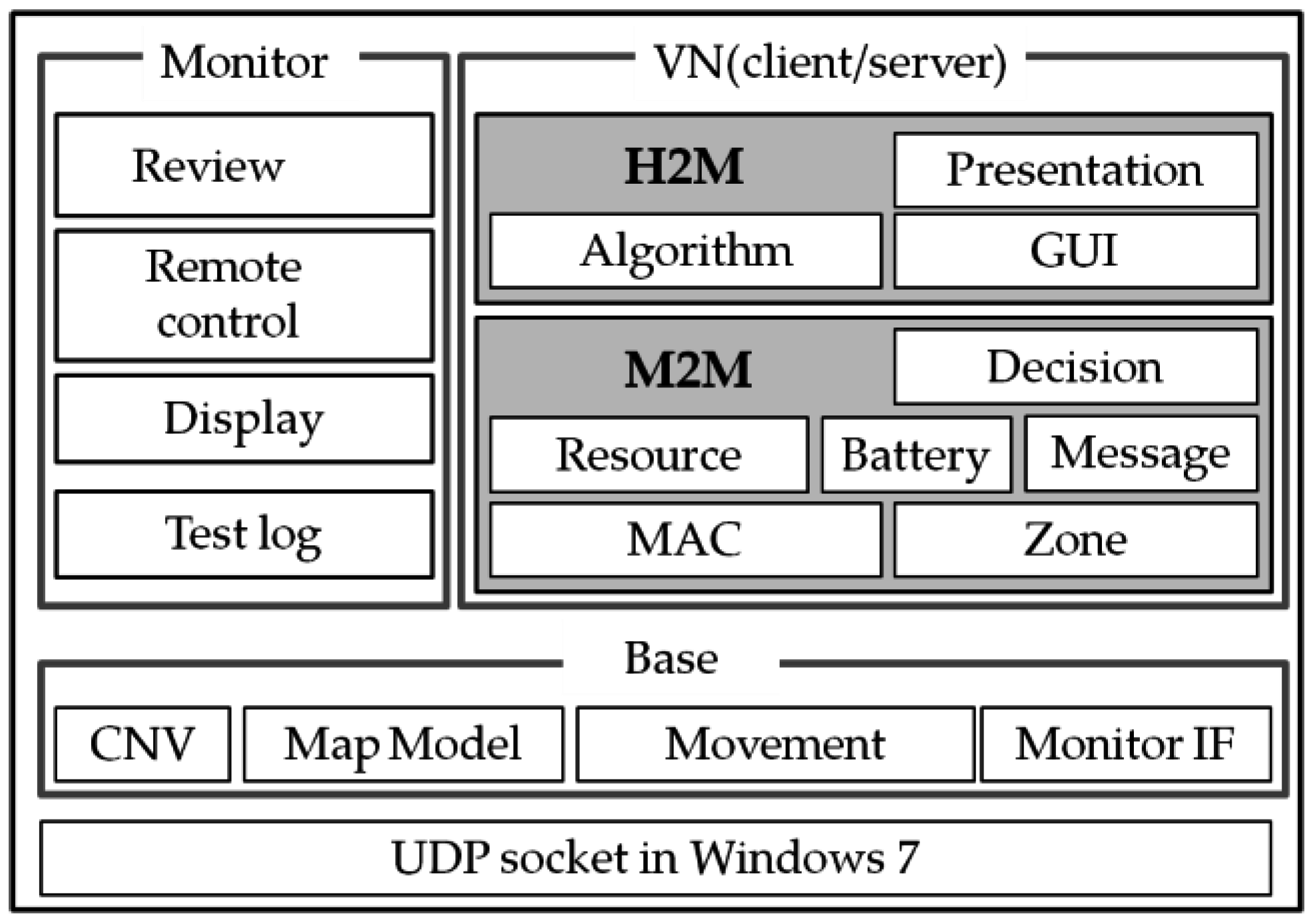
5. Evaluation System
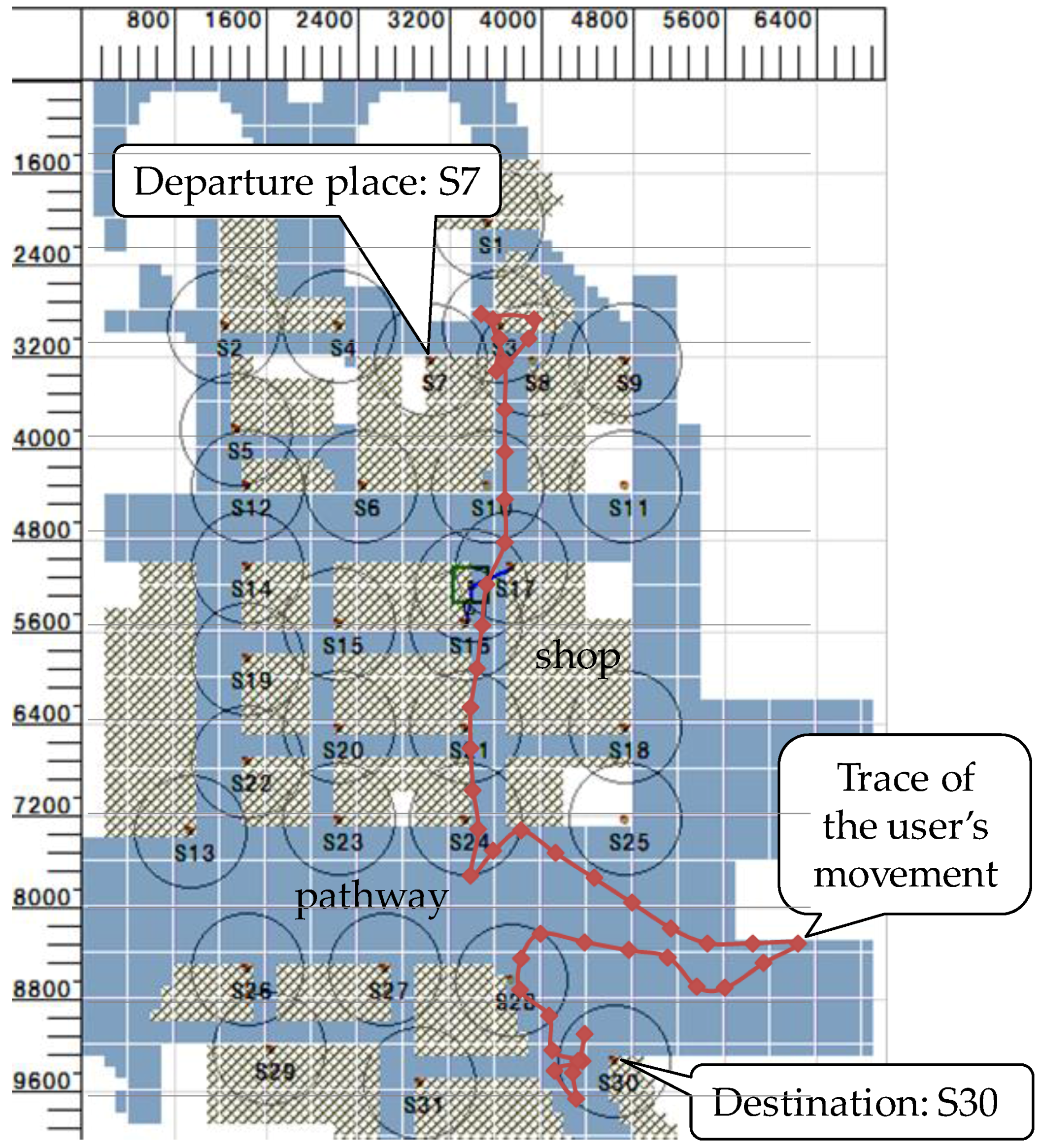
6. Evaluation Results
6.1. Simulation Conditions
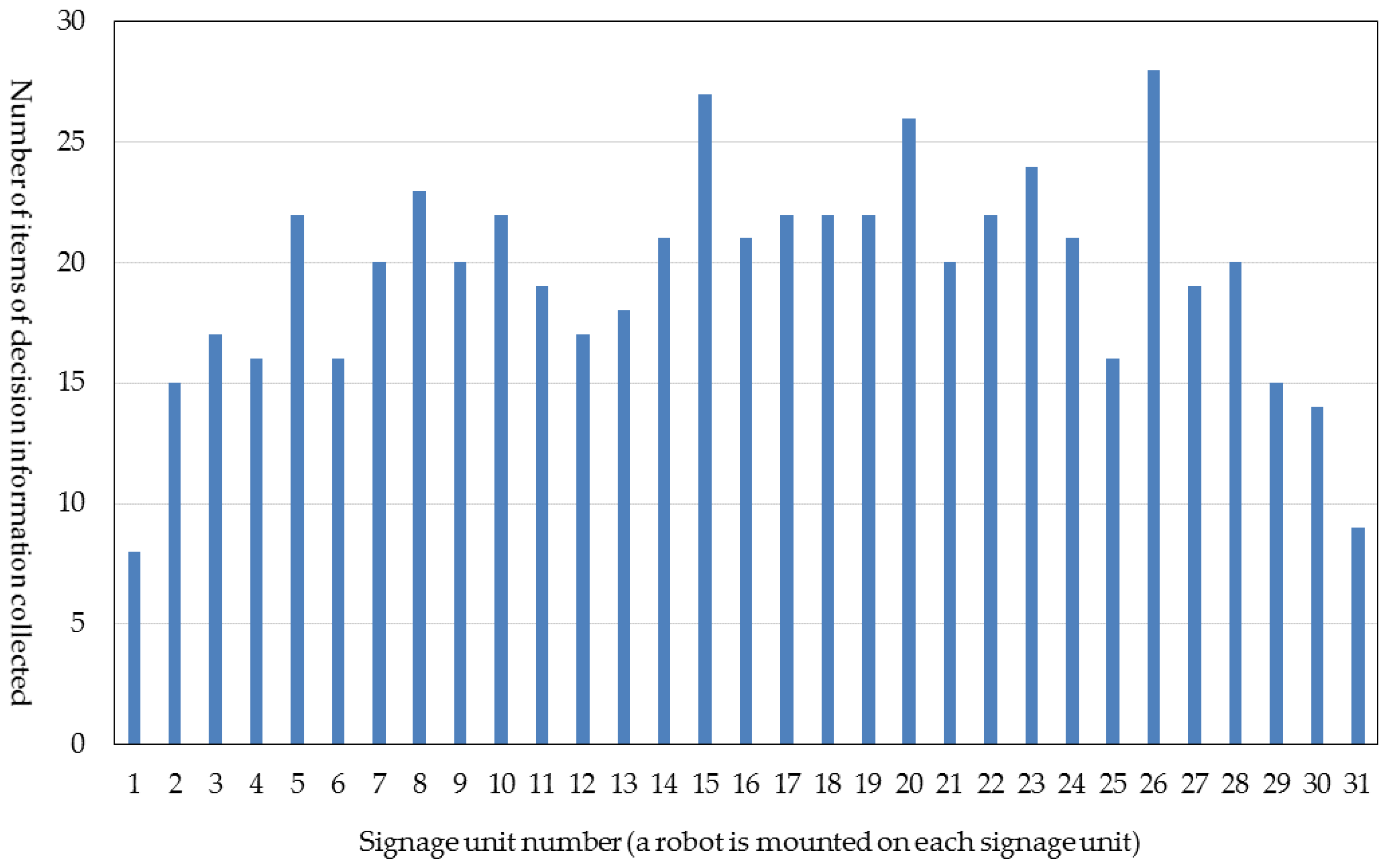
6.2. Number of Robots for Which Decision Information (Flag Value) Is Collected and the Pseudo-Synchronization Number
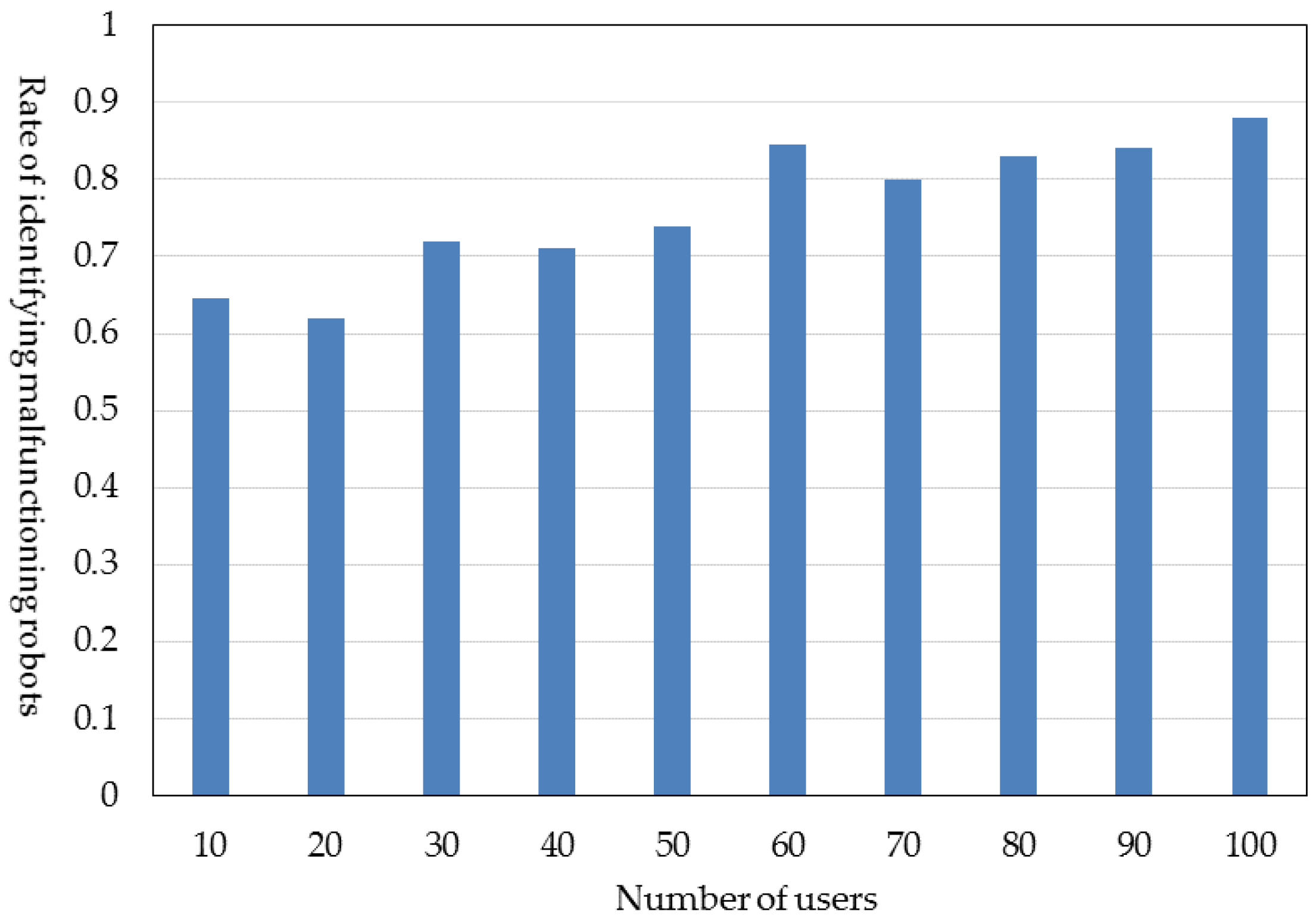
6.3. Rate of Identifying Malfunctioning Robots
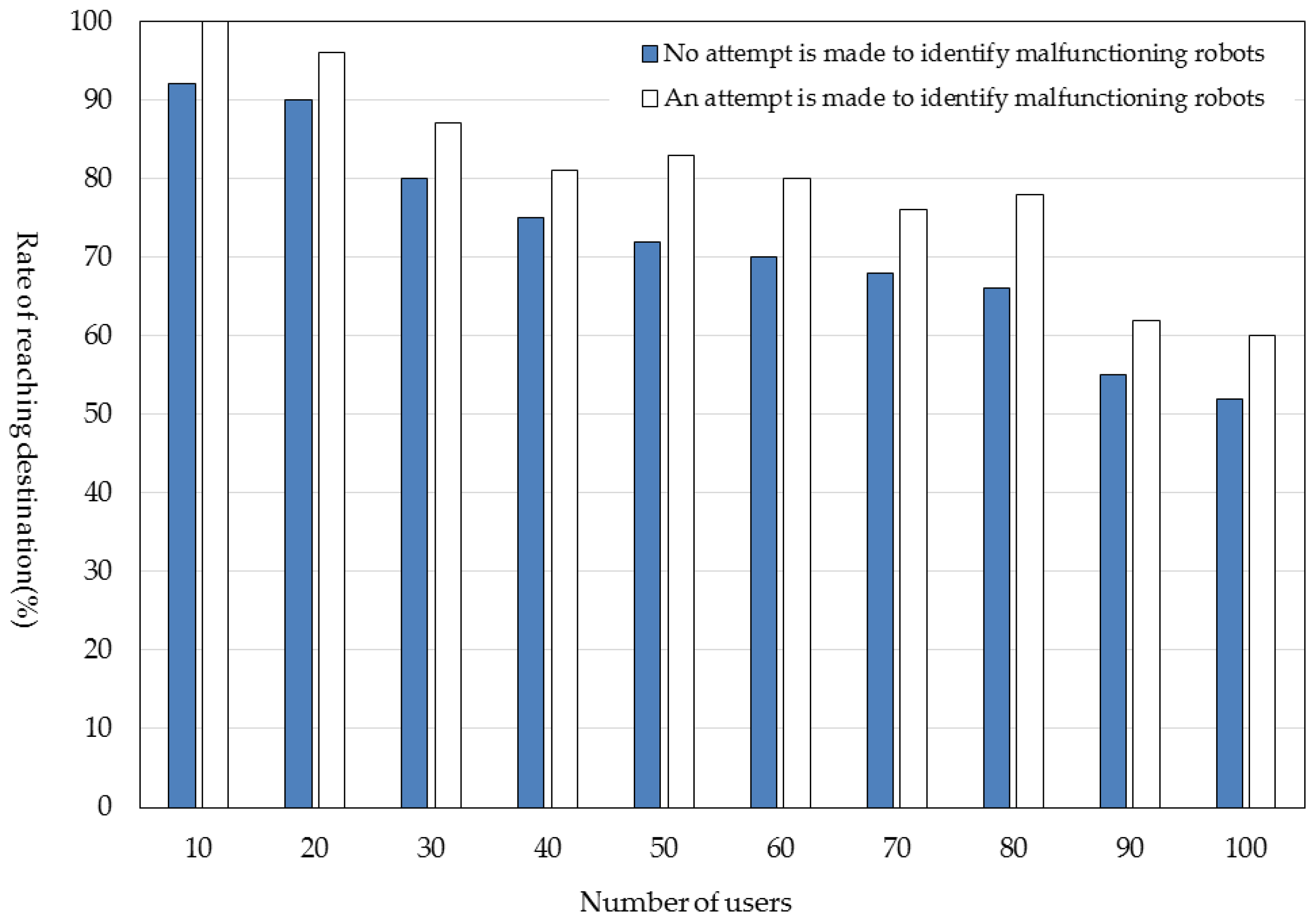
6.4. Rate of Reaching Destination
6.5. Average Length of Time to Reach Destination
7. Conclusions
Author Contributions
Conflicts of Interest
References
- Chandrasekaran, B.; Conrad, J.M. Human-robot Collaboration: A Survey. In Proceedings of the Annual IEEE SoutheastCon Conferences (SoutheastCon 2015), Fort Lauderdale, FL, USA, 9–12 April 2015.
- Siegwart, R.; Arras, K.O.; Bouabdallah, S.; Burnier, D.; Froidevaux, G.; Greppin, X.; Jensen, B.; Lorotte, A.; Mayor, L.; Meisser, M.; et al. Robox at Expo.02: A Large Scale Installation of Personal Robots. Robot. Auton. Syst. 2003, 42, 203–222. [Google Scholar] [CrossRef]
- Shiomi, M.; Kanda, T.; Ishiguro, H.; Hagita, N. Interactive Humanoid Robots for a Science Museum. IEEE Intell. Syst. 2007, 22, 25–32. [Google Scholar] [CrossRef]
- Gockley, R.; Forlizzi, J.; Simmons, R. Interactions with a Moody Robot. In Proceedings of the 1st ACM SIGCHI/SIGART Conference on Human-Robot Interaction (HRI2006), Salt Lake City, UT, USA, 2–4 March 2006; pp. 186–193.
- Kanda, T.; Hirano, T.; Eaton, D.; Ishiguro, H. Interactive Robots as Social Partners and Peer Tutors for Children: A Field Trial. J. Hum. Comput. Interact. 2004, 19, 61–84. [Google Scholar]
- Tanaka, F.; Cicourel, A.; Movellan, J.R. Socialization between Toddlers and Robots at an early Childhood Education Center. Proc. Natl. Acad. Sci. USA 2007, 104, 17954–17958. [Google Scholar] [CrossRef] [PubMed]
- Tezuka, H.; Katafuchi, N.; Nakamura, Y.; Machino, T.; Nanjo, Y.; Iwaki, S.; Shimokura, K. Robot Platform Architecture for Information Sharing and Collaboration Among Multiple Networked Robots. J. Robot. Mechatron. 2006, 18, 325–332. [Google Scholar]
- Nakamura, Y.; Machino, T.; Motegi, M.; Iwata, Y.; Miyamoto, T.; Iwaki, S.; Muto, S.; Shimokura, K. Framework and Service Allocation for Network Robot Platform and Execution of Interdependent Services. Robot. Auton. Syst. 2008, 56, 831–843. [Google Scholar] [CrossRef]
- Liu, Y.; Yang, J. A Ubiquitous and Cooperative Service Framework for Network Robot System. In Proceedings of the 2nd International Conference on Intelligent Robotics and Applications (ICIRA 2009), Singapore, 16–18 December 2009.
- Shiomi, M.; Kanda, T.; Glas, D.F.; Satake, S.; Ishiguro, H.; Hagita, N. A Network Robot System for Cooperative Guide Service in a Shopping Mall. J. Robot. Soc. Jpn. 2011, 29, 544–553. [Google Scholar] [CrossRef]
- Murakami, Y.; Nakanishi, H. Proposing GUI for Remotely Controlling Guide Robots. IPSJ SIG Technical Reports 2008, 11(2008-HCI-127), 79–86. Available online: http://id.nii.ac.jp/1001/00036580/ (accessed on 14 August 2016).
- Gross, H.M.; Boehme, H.; Schroeter, Ch.; Mueller, S.; Koenig, A.; Einhorn, E.; Martin, Ch.; Merten, M.; Bley, A. TOOMAS: Interactive Shopping Guide Robots in Everyday Use-Final Implementation and Experiences from Long-Term Field Trials. In Proceedings of the 2009 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS’09), St. Louis, MO, USA, 10–15 October 2009; pp. 2005–2012.
- Kemmotsu, K.; Koketsu, Y.; Iehara, M. Human Behavior Recognition Using Unconscious Cameras and a Visible Robot in a Network Robot System. J. Robot. Auton. Syst. 2008, 56, 857–864. [Google Scholar] [CrossRef]
- Boswarthick, D.; Elloumi, O.; Hersent, O. M2M Communications: A Systems Approach; Wiley: Chichester, UK, 2012. [Google Scholar]
- Bojic, I.; Granjal, J.; Monteiro, E.; Katusic, D.; Skocir, P.; Kusek, M.; Jezic, G. Communication and Security in Machine-to-Machine Systems. Wirel. Netw.r Mov. Objects 2014, 8611, 255–281. [Google Scholar]
- Ren, Y.; Chuah, M.C.; Yang, J.; Chen, Y. Detecting Blackhole Attacks in Disruption-Tolerant Networks through Packet Exchange Recording. In Proceedings of the IEEE International Symposium on a World of Wireless Mobile and Multimedia Networks (WoWMoM), Montreal, QC, Canada, 14–17 June 2010; pp. 1–6.
- Djenouri, D.; Khelladi, L.; Badache, A.N. A Survey of Security Issues in Mobile Ad Hoc and Sensor Networks. IEEE Commun. Surv. Tutor. 2005, 7, 2–28. [Google Scholar] [CrossRef]
- Yang, H.; Luo, H.Y.; Ye, F.; Lu, S.W.; Zhang, L. Security in Mobile Ad Hoc Networks: Challenges and Solutions. IEEE Wirel. Commun. 2004, 11, 38–47. [Google Scholar] [CrossRef]
- Tobu Hope Center. Available online: http://www.tobu-hope.co.jp/ (accessed on 15 August 2016).
- Suga, Y.; Takahashi, D.; Takami, K. Guiding Users to Shops Using the Near-Field Communication between Signages and Mobile Terminals. In Proceedings of the 2nd International Conference on Mobile and Wireless Technology (ICMWT2015), Bangkok, Thailand, 23–25 June 2015.
- Lamport, L.; Shostak, R.; Pease, M. The Byzantine Generals Problem. ACM Trans. Program. Lang. Syst. 1982, 4, 382–401. [Google Scholar] [CrossRef]
- Yamaguchi, T.; Takami, K. A Reference Point Construction Method Using Mobile Terminals and the Indoor Localization Evaluation in the Centroid Method. Computers 2015, 4, 155–175. [Google Scholar] [CrossRef]





| Item | Value |
|---|---|
| Number of signage units | 31 |
| Number of users (number of mobile terminals) | Varied from 10 to 100 |
| Behavior model | Random walk |
| Moving speed | 3.6 km/h |
| Maximum number of simultaneous connections allowed: NL | 8 |
| Display duration: TD | 30 s |
| Size of the underground shopping mall | 105 m × 70 m |
| Reach of wireless communication | 10 m |
| Simulation time | 10 min |
| Processing interval | 1 s |
| Number of simulation attempts | 5 |
| Pseudo-synchronization number: Nps | Varied from 5, 10 to 15 |
| Guidance algorithm | Correctly operating robots: angle-based algorithm |
| Malfunctioning robot: random | |
| Number of malfunctioning robots | 3 (S5, S10, and S15) |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Suga, Y.; Takami, K. Store-Carry and Forward-Type M2M Communication Protocol Enabling Guide Robots to Work together and the Method of Identifying Malfunctioning Robots Using the Byzantine Algorithm. Computers 2016, 5, 30. https://doi.org/10.3390/computers5040030
Suga Y, Takami K. Store-Carry and Forward-Type M2M Communication Protocol Enabling Guide Robots to Work together and the Method of Identifying Malfunctioning Robots Using the Byzantine Algorithm. Computers. 2016; 5(4):30. https://doi.org/10.3390/computers5040030
Chicago/Turabian StyleSuga, Yoshio, and Kazumasa Takami. 2016. "Store-Carry and Forward-Type M2M Communication Protocol Enabling Guide Robots to Work together and the Method of Identifying Malfunctioning Robots Using the Byzantine Algorithm" Computers 5, no. 4: 30. https://doi.org/10.3390/computers5040030
APA StyleSuga, Y., & Takami, K. (2016). Store-Carry and Forward-Type M2M Communication Protocol Enabling Guide Robots to Work together and the Method of Identifying Malfunctioning Robots Using the Byzantine Algorithm. Computers, 5(4), 30. https://doi.org/10.3390/computers5040030





