Sustainable and Practical Firmware Upgrade for Wireless Access Point Using Password-Based Authentication
Abstract
:1. Introduction
2. Related Works
3. Firmware Upgrade Using Password-Based Authentication
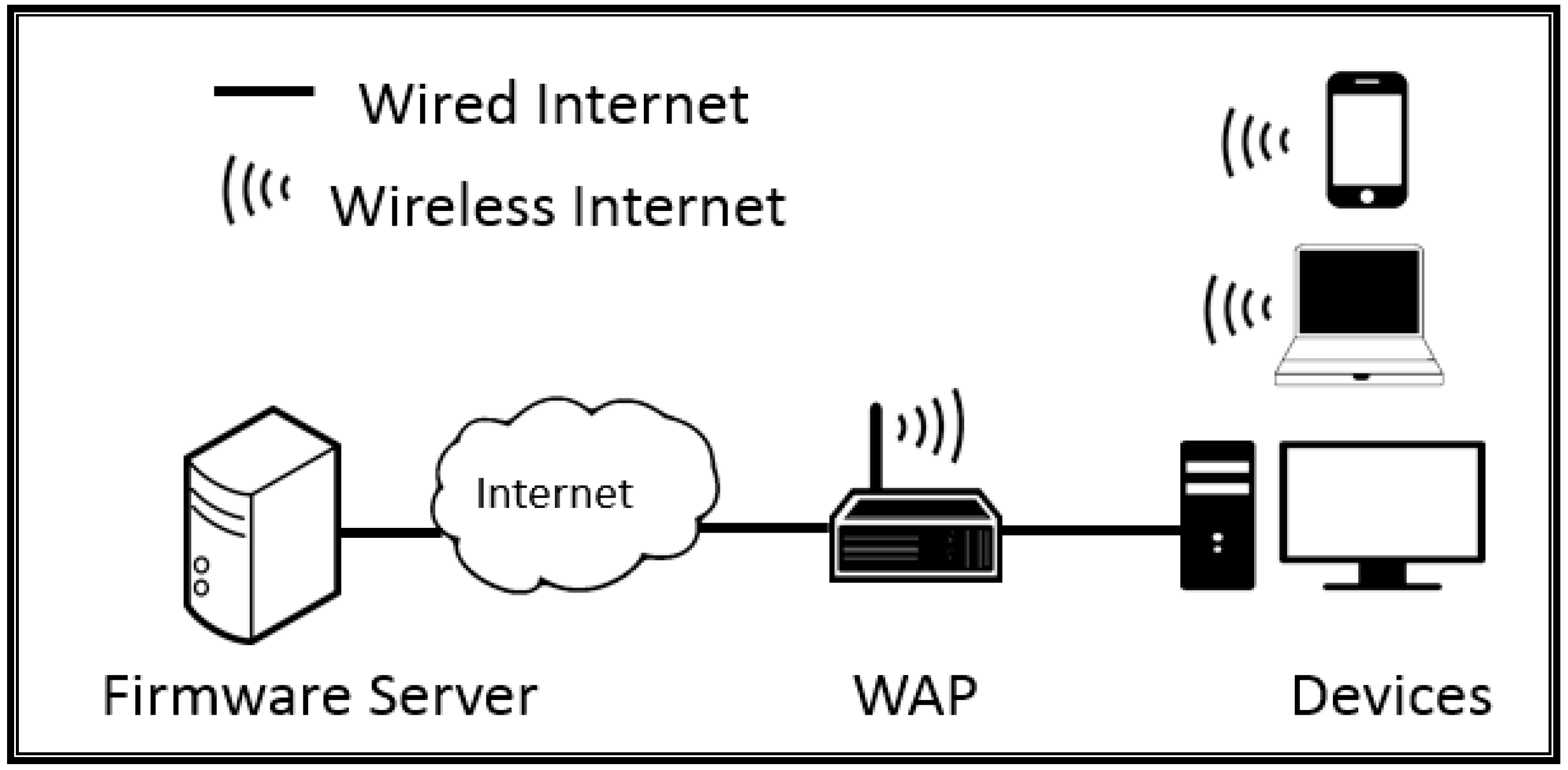
3.1. Network Architecture of the Firmware Upgrade Protocol
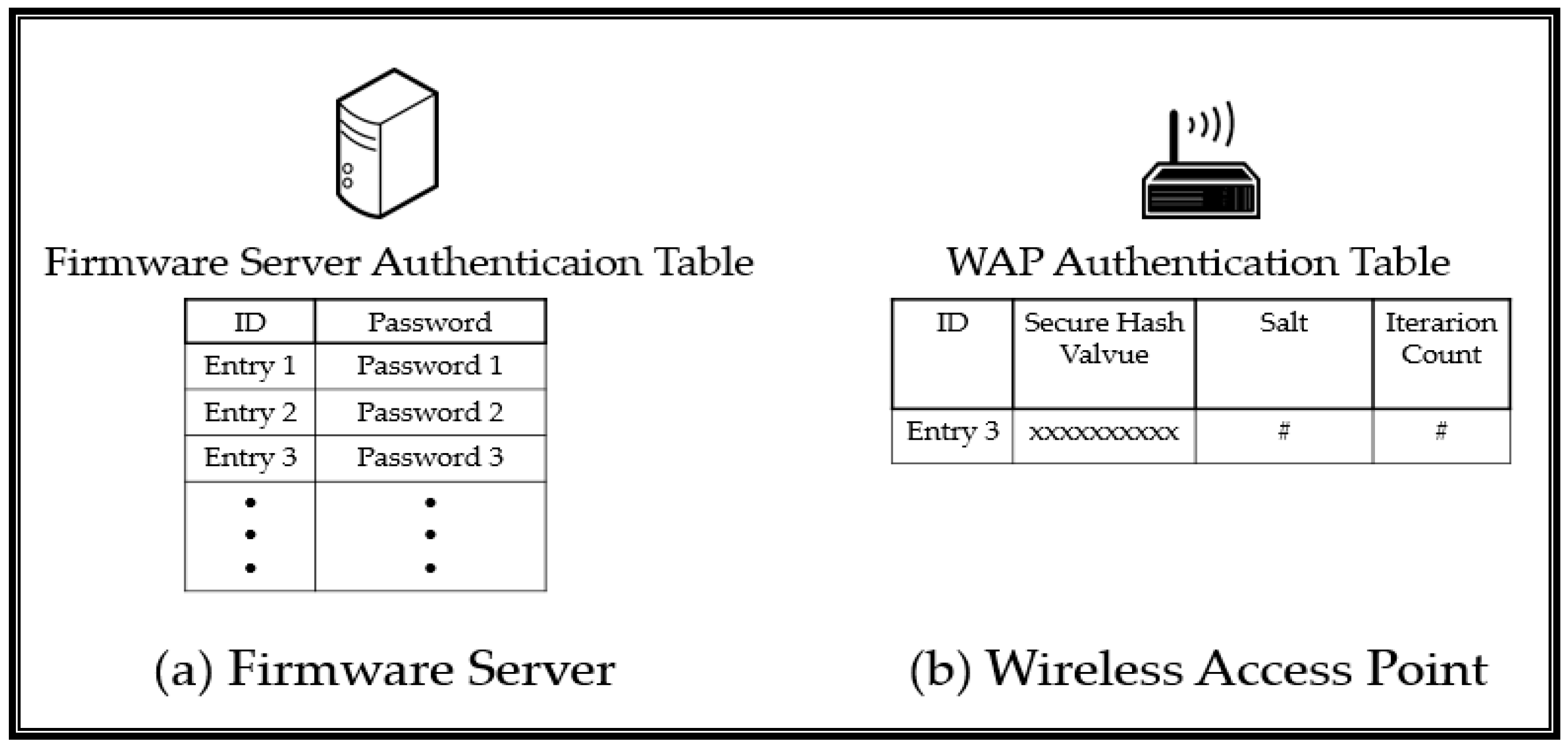
3.2. Practical Assumptions
3.3. Proposed Firmware Upgrade Protocol
4. Implementation and Experiments
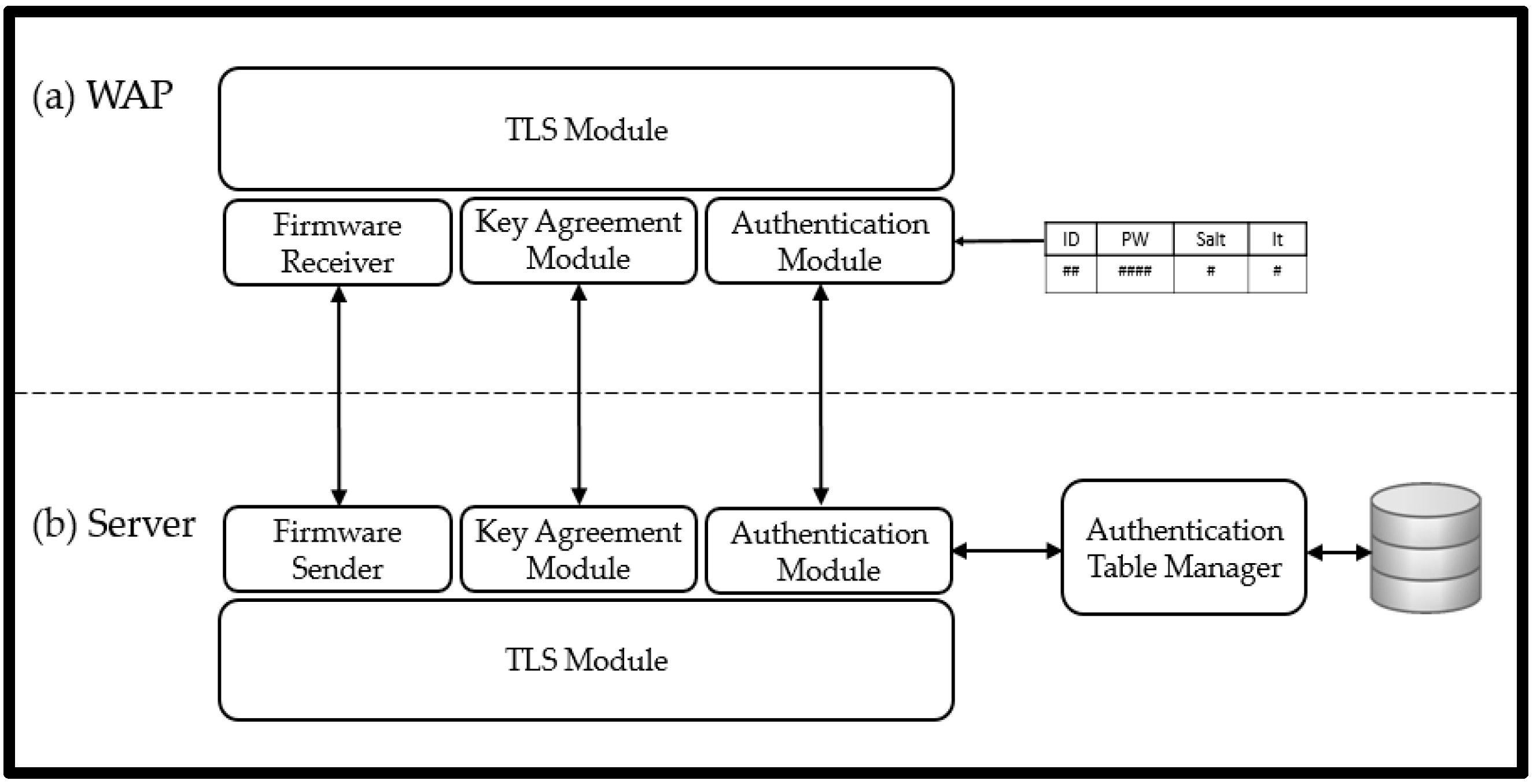
4.1. Prototype Implementation
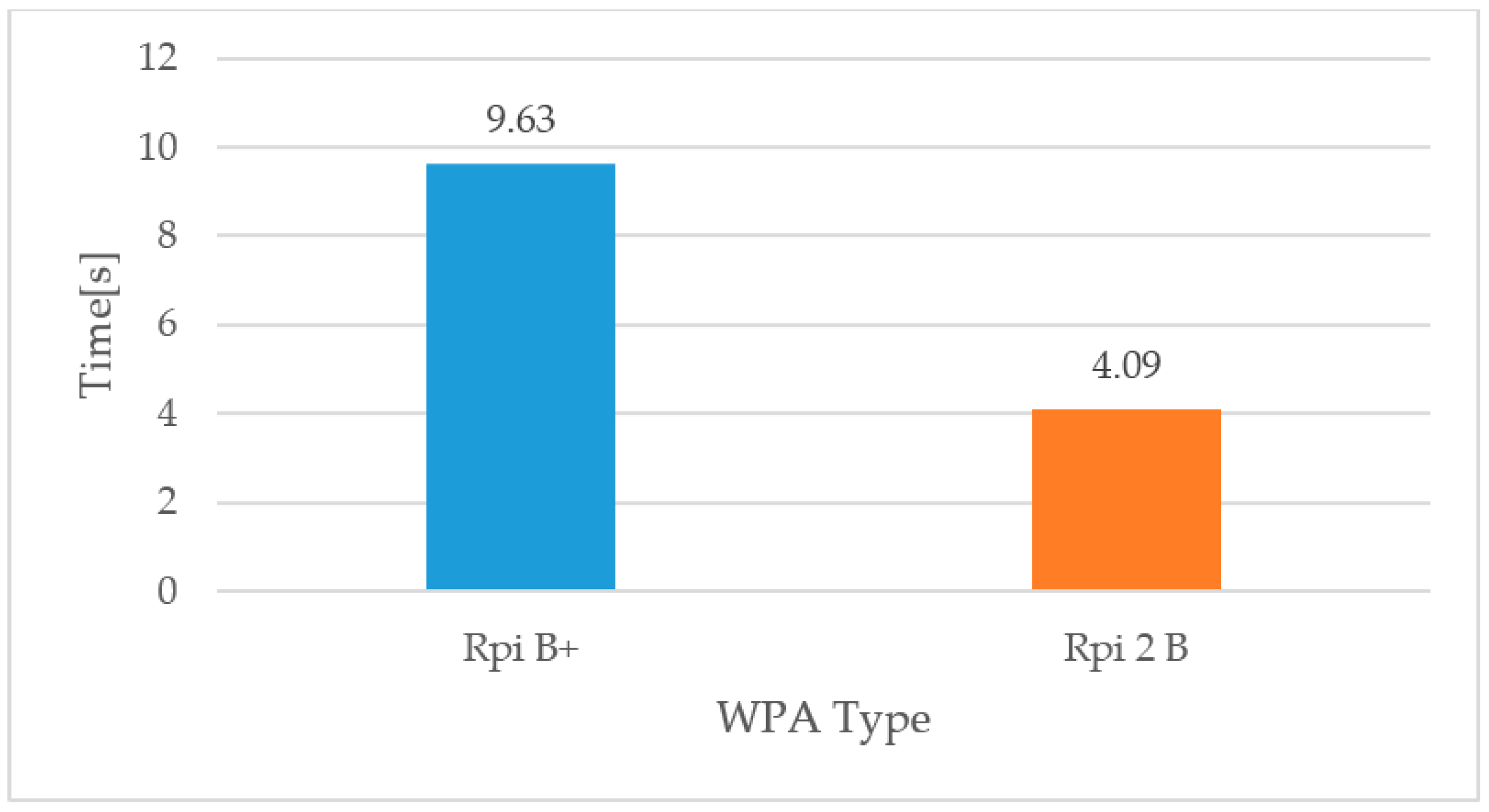
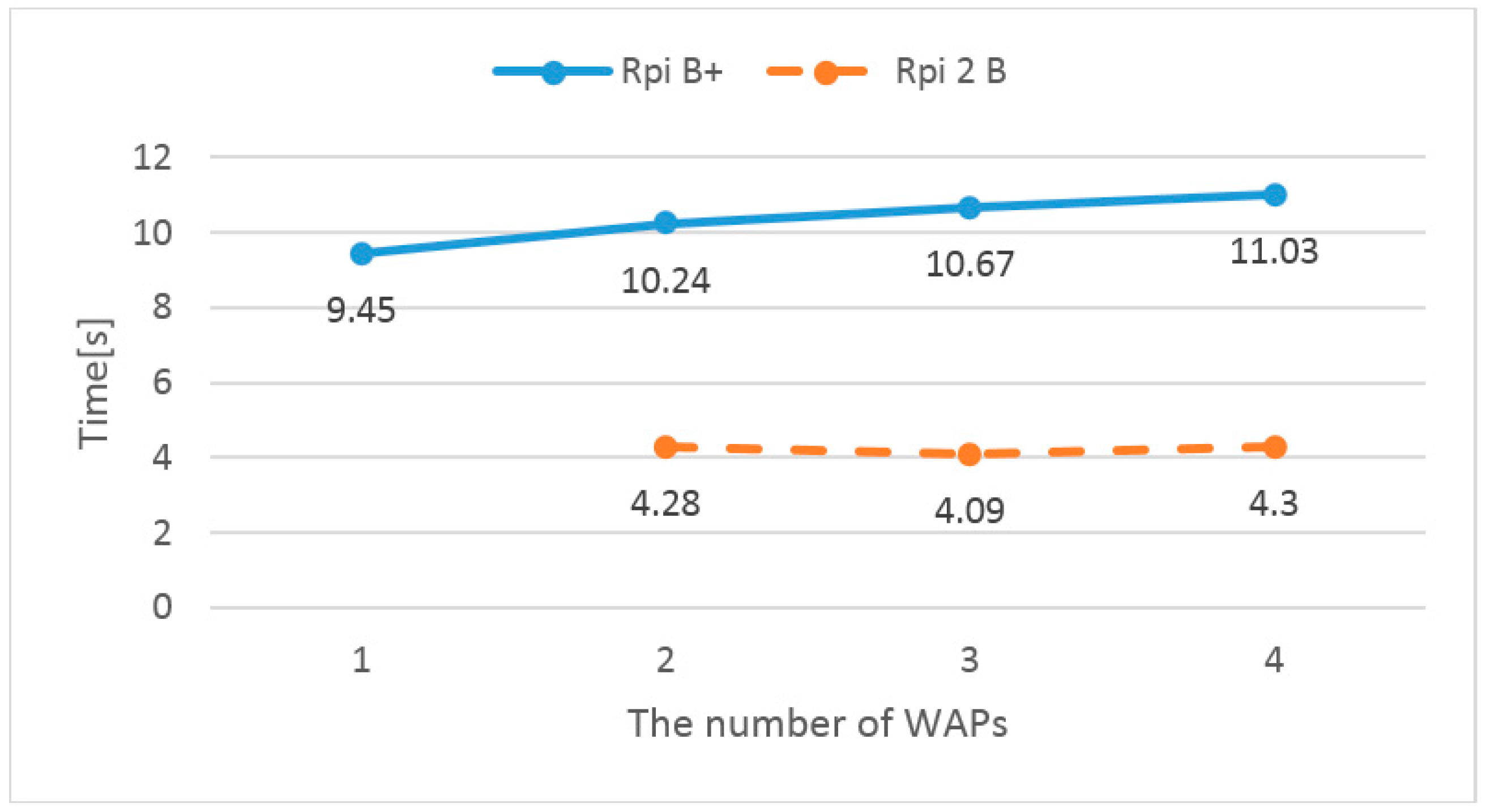
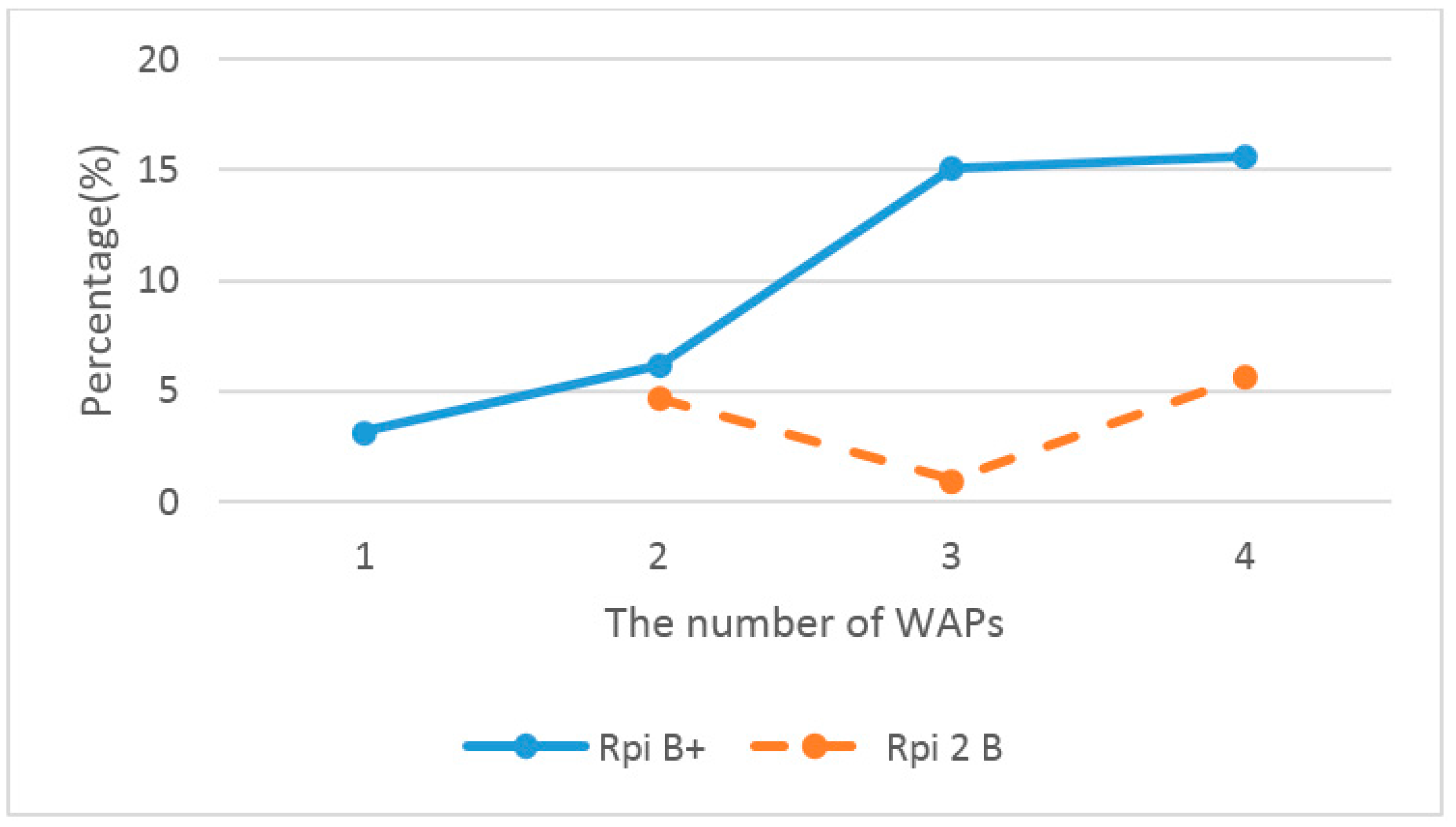
4.2. Performance of the Firmware Upgrade System
4.3. Security Analysis of the Protocol
4.3.1. Security Analysis
4.3.2. Analysis of the Proposed Protocol’s Security Attributions
4.3.3. Limitations
5. Conclusions
Author Contributions
Conflicts of Interest
Appendix A. Firmware Upgrade Pseudocode
References
- Egevang, K.; Francis, P. The IP Netw ork Address Translator (NAT). Available online: http://www.rfc-editor.org/info/rfc1631 (accessed on 23 August 2016).
- Gartner. Gartner Says 6.4 Billion Connected “Things” Will Be in Use in 2016, Up 30 Percent from 2015. Available online: http://www.gartner.com/newsroom/id/3165317 (accessed on 23 August 2016).
- Proofpoint. Proofpoint Uncovers Internet of Things (IoT) Cyberattack; Proofpoint Release: Sunnyvale, CA, USA, 2014. [Google Scholar]
- Stiawan, D.; Idris, M.Y.; Abdullah, A.H. Penetration Testing and Network Auditing: Linux. JIPS 2015, 11, 104–115. [Google Scholar]
- Nohl, K.; Lell, J. BadUSB—On Accessories that Turn Evil. Available online: http://www.slideshare.net/cisoplatform7/sr-labs-badusbv2 (accessed on 23 August 2016).
- Delugré, G. Closer to Metal: Reverse-Engineering the Broadcom NetExtreme’s Firmware. Available online: http://esec-lab.sogeti.com/static/publications/10-hack.lu-nicreverse_slides.pdf (accessed on 23 August 2016).
- Miller, C. Battery Firmware Hacking. Available online: http://www.hakim.ws/BHUS2011/materials/Miller/BH_US_11_Miller_Battery_Firmware_Public_WP.pdf (accessed on 23 August 2016).
- Choi, B.C.; Lee, S.H.; Na, J.C.; Lee, J.H. Secure firmware validation and update for consumer devices in home networking. IEEE Trans. Consum. Electron. 2016, 62, 39–44. [Google Scholar] [CrossRef]
- Tom, S. The Hackers New Weapons Routers and Printers; MIT Technology Review: San Diego, CA, USA, 2015. [Google Scholar]
- Dacosta, I.; Ahamad, M.; Traynor, P. Trust No One Else: Detecting MITM Attacks against SSL/TLS without Third-Parties. In Computer Security—ESORICS 2012; Springer: Berlin, Germany, 2012; pp. 199–216. [Google Scholar]
- Karapanos, N.; Capkun, S. On the Effective Prevention of TLS Man-in-the-Middle Attacks in Web Applications. In Proceedings of the 23rd USENIX Security Symposium (USENIX Security 14) 2014, San Diego, CA, USA, 20–22 August 2014; pp. 671–686.
- Odat, H.A.; Nsour, A.; Ganesan, S. Firmware over the Air Ad-Hoc Network, FOTANET. In Proceedings of the 2015 IEEE International Conference on Electro/Information Technology (EIT), Dekalb, IL, USA, 21–23 May 2015; pp. 101–106.
- Postel, J. RFC 793: Transmission Control Protocol. Available online: https://tools.ietf.org/html/rfc793 (accessed on 23 August 2016).
- Tsague, H.D.; Van Der Merwe, J.; Moabalobelo, T. Secure Firmware Updates for Point of Sale Terminals. In Proceedings of the 10th International Conference on Cyber Warfare and Security, Kruger National Park, South Africa, 24–25 March 2015; Academic Conferences Limited: Sonning Common, UK, 2015; p. 337. [Google Scholar]
- Forouzan, B.A.; Mukhopadhyay, D. Cryptography and Network Security (Sie.); McGraw-Hill Education: New York, NY, USA, 2011; pp. 2–7, 507–548. [Google Scholar]
- Steger, M.; Karner, M.; Hillebrand, J.; Rom, W.; Armengaud, E.; Hansson, M.; Boano, C.A.; Römer, K. Applicability of IEEE 802.11s for Automotive Wireless Software Updates. In Proceedings of the 13th International Conference on Telecommunications (ConTEL) 2015, Graz, Austria, 13–15 July 2015; pp. 1–8.
- Cui, A.; Costello, M.; Stolfo, S.J. When Firmware Modifications Attack: A Case Study of Embedded Exploitation. Available online: http://ids.cs.columbia.edu/sites/default/files/ndss-2013.pdf (accessed on 23 August 2016).
- Zaddach, J.; Costin, A. Embedded Devices Security and Firmware Reverse Engineering. Available online: https://media.blackhat.com/us-13/US-13-Zaddach-Workshop-on-Embedded-Devices-Security-and-Firmware-Reverse-Engineering-WP.pdf (accessed on 23 August 2016).
- Dierks, T. The Transport Layer Security (TLS) Protocol Version 1.2. Available online: https://www.ietf.org/rfc/rfc5246.txt (accessed on 23 August 2016).
- Stallings, W. Cryptography and Network Security, 4/E; Pearson Education India: Kormangala, India, 2006; pp. 22–24. [Google Scholar]
- Newman, C.; Menon-Sen, A.; Melnikov, A.; Williams, N. RFC 5802: Salted Challenge Response Authentication Mechanism (SCRAM) SASL and GSS-API Mechanisms. Available online: https://tools.ietf.org/html/rfc5802 (accessed on 23 August 2016).
- Turan, M.S.; Barker, E.; Burr, W.; Chen, L. Recommendation for Password-Based Key Derivation. Available online: http://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-132.pdf (accessed on 23 August 2016).
- Moein, S.; Gebali, F.; Traore, I. Analyzis of covert hardware attacks. J. Converg. 2014, 5, 26–30. [Google Scholar]
- Cooper, D. Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. Available online: https://tools.ietf.org/html/rfc5280 (accessed on 23 August 2016).
- Burkholder, P. SSL Man-in-the-Middle Attacks. Available online: http://www.windowsecurity.com/articles-tutorials/authentication_and_encryption/Understanding-Man-in-the-Middle-Attacks-ARP-Part4.html (accessed on 23 August 2016).
- Ellison, C.; Schneier, B. Ten risks of PKI: What you’re not being told about public key infrastructure. Comput. Secur. J. 2000, 16, 1–7. [Google Scholar]
- Fagan, M.; Khan, M.M.H.; Nguyen, N. How does this message make you feel? A study of user perspectives on software update/warning message design. Hum. Centric Comput. Inf. Sci. 2015, 5, 1–26. [Google Scholar] [CrossRef]
- Sheffer, Y.; Holz, R.; Saint-Andre, P. Recommendations for Secure Use of Transport. Layer Security (TLS) and Datagram Transport. Layer Security (DTLS). Available online: https://tools.ietf.org/html/rfc7525 (accessed on 23 August 2016).
- Rescorla, E. Diffie–Hellman Key Agreement Method. Available online: https://www.ietf.org/rfc/rfc2631.txt (accessed on 23 August 2016).
- Top 20 Rated Wireless Access Points Reviews 2016. Available online: https://www.vbestreviews.com/top-10-rated-wireless-access-point-reviews-2015/ (accessed on 23 August 2016).
- FIPS. 197: The official AES standard. Figure 2: Working scheme with four LFSRs and their IV generation LFSR1. LFSR 2001, 2, 1–3. [Google Scholar]
- Bellare, M.; Rogaway, P. Entity Authentication and Key Distribution. In Proceedings of the Annual International Cryptology Conference, Barbara, CA, USA, 22–26 August 1993; Springer: Berlin, Germany, 1993; pp. 232–249. [Google Scholar]
- Paar, C.; Pelzl, J. Understanding Cryptography: A Textbook for Students and Practitioners; Springer Science & Business Media: Berlin, Germany, 2009; pp. 319–329, 331–353. [Google Scholar]
- Stinson, D.R. Cryptography: Theory and Practice; CRC Press: Boca Raton, FL, USA, 2005; pp. 436–438. [Google Scholar]
- Mitchell, C.J.; Ward, M.; Wilson, P. Key control in key agreement protocols. Electron. Lett. 1998, 34, 980–981. [Google Scholar] [CrossRef]
- Akram, R.N.; Markantonakis, K.; Mayes, K. A Privacy Preserving Application Acquisition Protocol. In Proceedings of the 2012 IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications, Liverpool, UK, 25–27 June 2012; pp. 383–392.
- Blake-Wilson, S.; Menezes, A. Unknown Key-Share Attacks on the Station-to-Station (STS) Protocol; Public Key Cryptography, Springer: Berlin, Germany, 1999; pp. 154–170. [Google Scholar]
- Cremers, C.; Horvat, M. Improving the ISO/IEC 11770 Standard for Key Management Techniques. In Proceedings of the International Conference on Research in Security Standardisation, London, UK, 16–17 December 2014; pp. 215–235.
- Chen, L.; Mitchell, C. Security Standardization Research. In Proceedings of the First International Conference SSR 2014, London, UK, 16–17 December 2014.
- Hlauschek, C.; Gruber, M.; Fankhauser, F.; Schanes, C. Prying Open Pandora’s Box: KCI Attacks against TLS. In Proceedings of the 9th USENIX Workshop on Offensive Technologies (WOOT 15), Washington, DC, USA, 24 June 2015.
- Holz, R.; Riedmaier, T.; Kammenhuber, N.; Carle, G. X.509 Forensics: Detecting and Localizing the SSL/TLS Men-in-the-Middle. In Computer Security—Esorics 2012; Springer: Berlin, Germany, 2012; pp. 217–234. [Google Scholar]





| Notation | Definition |
|---|---|
| WAP TLS Protocol Version | |
| Firmware Server TLS Protocol Version | |
| WAP Random Number | |
| Firmware Server Random Number | |
| WAP Session ID | |
| Firmware Server Session ID | |
| WAP Cipher Suites | |
| Firmware Server Cipher Suites | |
| WAP Compression Methods | |
| Firmware Server Compression Methods | |
| Firmware Server Certificate | |
| Sign the Diffie–Hellman Parameter and Half-key with the Firmware Server Private Key | |
| WAP Half-key | |
| WAP CipherSuiteSpec | |
| Firmware Server CipherSuiteSpec | |
| WAP ID | |
| Salt Value Used for the Secure Hash Value in the WAP | |
| Iteration Counter Used for the Secure Hash Value in the WAP | |
| Hash (Password, Salt, It) ⨁ ⨁ | |
| Firmware Server Validation Result of the Revised Firmware | |
| WAP Random Number | |
| Firmware Server Random Number |
| Devices | Specifications |
|---|---|
| Desktop PC | Ubuntu 16.04 LTS 64 bits, 10 GB RAM, Intel core i5 2.80 GHz × 4 |
| Raspberry Pi B+ | Raspbian, 700 MHz single-core ARM1176JZF-S, 256 MB RAM |
| Raspberry Pi 2 B | Raspbian, 900 MHz quad-core ARM Cortex-A7, 1 GB RAM |
| Router | PISnet P150N, RT5350, 150 Mbps/170 Mbps 802.11b/g/n |
| Wi-Fi dongle | Iptime N100mini, 150 Mbps 802.11b/g/n |
| Wi-Fi dongle | NEXT-201N MINI, 150 Mbps 802.11b/g/n |
| Firmware Size (MB) | Time (s) | VIRT | RES | SHR | MEM (%) |
|---|---|---|---|---|---|
| 2 | 9.63 | 17,080 | 11,920 | 6256 | 2.7 |
| 4 | 18.94 | 17,080 | 11,964 | 6300 | 2.6 |
| 6 | 28.15 | 17,080 | 12,036 | 6372 | 2.7 |
| 8 | 37.67 | 17,080 | 11,989 | 6287 | 2.7 |
| 10 | 46.89 | 17,080 | 12,010 | 6303 | 2.7 |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jang, J.; Jung, I.Y. Sustainable and Practical Firmware Upgrade for Wireless Access Point Using Password-Based Authentication. Sustainability 2016, 8, 876. https://doi.org/10.3390/su8090876
Jang J, Jung IY. Sustainable and Practical Firmware Upgrade for Wireless Access Point Using Password-Based Authentication. Sustainability. 2016; 8(9):876. https://doi.org/10.3390/su8090876
Chicago/Turabian StyleJang, Jaejin, and Im Y. Jung. 2016. "Sustainable and Practical Firmware Upgrade for Wireless Access Point Using Password-Based Authentication" Sustainability 8, no. 9: 876. https://doi.org/10.3390/su8090876
APA StyleJang, J., & Jung, I. Y. (2016). Sustainable and Practical Firmware Upgrade for Wireless Access Point Using Password-Based Authentication. Sustainability, 8(9), 876. https://doi.org/10.3390/su8090876





