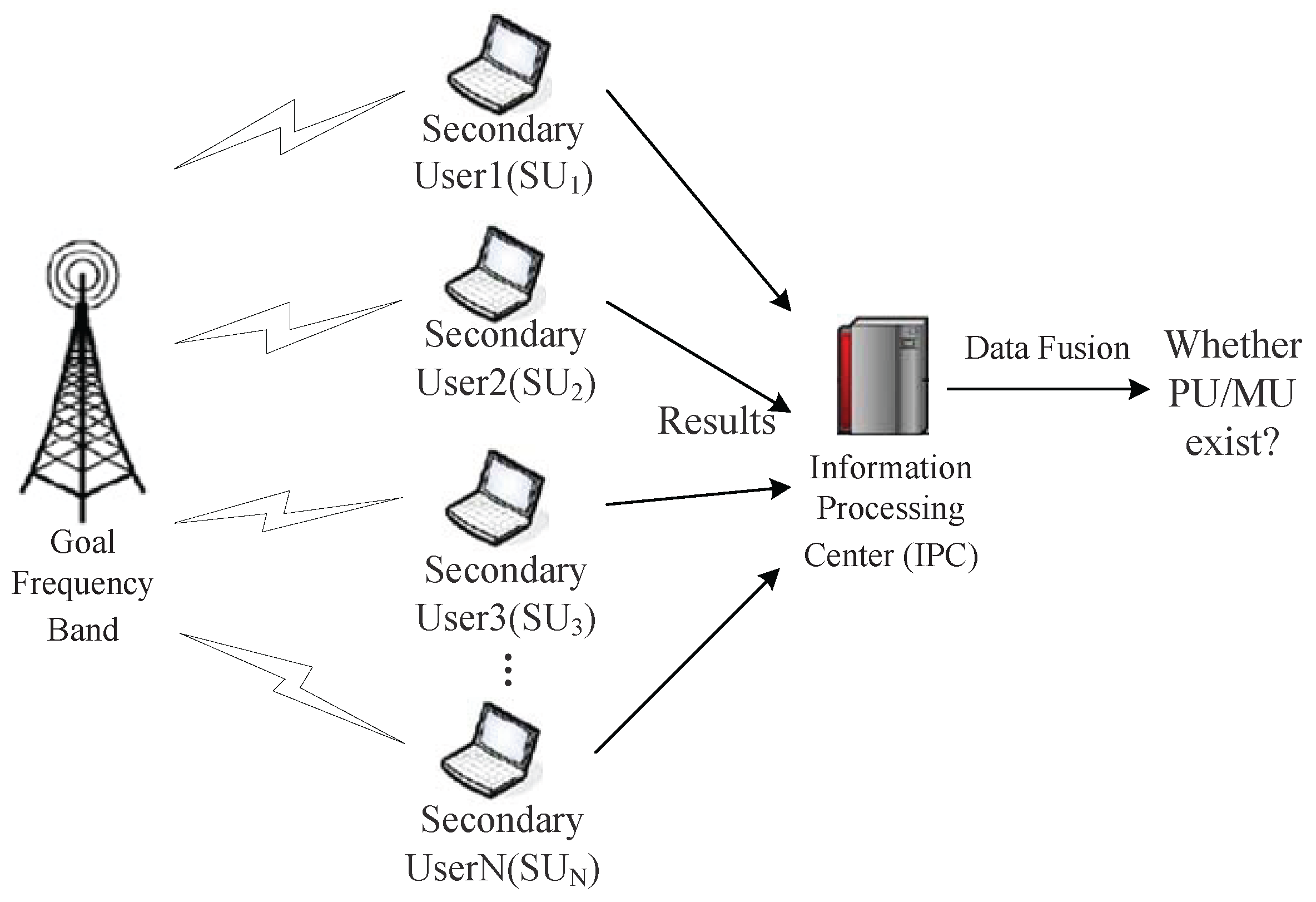
1. Introduction
At the present stage, the static spectrum allocation scheme greatly hinders the development of wireless communication technology and the expansion of the mobile communication business. The concept of dynamic spectrum access arises on this occasion. On the premise of not causing interference to primary users (PUs), secondary users in wireless network can adaptively change its communication parameters, access licensed band in order to communicate effectively through a sensing wireless environment, thus improving the spectrum utilization. As an effective technique to ease the contradiction among limited spectrum resources, increasing spectrum requirement and low frequency spectrum utilization, cognitive radio (CR) [
1] technology has attracted wide attention. In cognitive radio networks, PUs have priority rights to access the licensed band. During the process of using spectrum holes to communicate, CRs should be able to quickly detect the emergence of PU, in order to withdraw from an occupied spectrum in a timely manner [
2].
However, in an unauthentic network, malicious users (MUs) may easily fake the features of PUs and transmit within the cognitive network sensing band by reconfiguring the air interface of CR. Based on cognitive-etiquette [
3] of spectrum access priority, CRNs would mistakenly consider MU as legal PU and shift scanning band, thus remarkably reducing the available spectrum resource in CRNs, which is called primary user emulation attack (PUEA) [
4]. It is apparent that such attacks will cause numerous SUs to lose access to the network services. In particular, information about PUs location could enable several key capabilities in CR networks, including improved spatio-temporal sensing, intelligent location-aware routing, as well as aiding spectrum policy enforcement [
5]. Fortunately, with the restriction of the transmitting power, it is hard for MUs to imitate energy level and position information of PUs at the same time. Thus, combining the energy level with position information of source signal, and further confirm the identity of detection signal can prevent PUEA when MUs has successfully simulated the signal features of PUs. In addition, the positioning mechanism based on signal source can also be integrated into the CRNs spectrum sensing process, in order to enhance the credibility of the sensing results of SUs, which prevents spectrum sensing data falsification (SSDF) attacks to a certain extent. Therefore, research about signal source localization algorithm within the authorized frequency band is of important significance. As FCC has considered opening free TV band for cognitive users in dynamic spectrum access [
6]. Thus, existing research on signal source localization algorithm in CRNs usually assumes that the authorized user networks are the TV tower with fixed position.
In order to facilitate the process of obtaining the source position in CRNs, CRNs can be regarded as wireless sensor networks [
7] (WSNs), then the source in the sensing spectrum band becomes a goal node in WSN, and SU is a beacon node in WSN [
8]. The existing localization algorithms in WSN can be divided into range-based [
9] and range-free [
10] localization algorithms according to the different means of measurement. Range-based techniques such as multi-alteration require high hardware demand and are sensitive to noise. In contrast, range-free localization schemes locate the target nodes depending on the correlation among network nodes, among which the centroid scheme is a classic one [
11]. Centroid scheme equally treats influence of normal nodes acting on the goal nodes, leading to ordinary localization performance. The WCL algorithm and the RR-WCL algorithm based on centroid scheme were proposed in [
12,
13]. These research papers introduced different methods to calculate the weights of beacon nodes through received signal strength (RSS), thus reflecting the influence extent of beacon nodes exerting to centroid position. However, both merely concern the correlation between each beacon node and the goal node instead of the correlation between all the beacon nodes and the goal node integrally. Consequently, the obtained degree of correlation is not enough to accurately locate the position of goal nodes.
In this paper, we proposed a new primary user localization algorithm based on compressive sensing in CRN. Initially, energy detection is adopted by secondary users for collecting the energy fingerprint of source signal, and then the correlation coefficients between source signal and SUs are constructed by compressive sensing [
14] to determine weights of SUs. Finally, the weighted centroid algorithm is used to estimate source position and compare with the primary nodes position, which is known in CRN. This confirms whether PUEA exists.
The rest of this paper is organized as follows. The system model is introduced in
Section 2. Compressive sensing theory is briefly introduced in
Section 3.
Section 4 describes the proposed localization algorithm based CS.
Section 5 demonstrates the simulation results, and conclusion is given in
Section 6.
3. Compressive Sensing Theory
Compressive sensing is a technique that can efficiently acquire a signal using relatively few measurements, by which unique representation of the signal can be found based on the sparseness or compressibility of signal in some domain. As the authorised spectrum is inherently sparse due to its low spectrum utilization, compressive sensing becomes a promising candidate to realize spectrum sensing by using sub-Nyquist sampling rates [
14].
Compressive sensing theory indicates that if signal
is sparse in a transform domain, then the high-dimensional coefficient
in domain
of the signal
can be projected into a low-dimensional space through measurement matrix, and the original sparse signal can be reconstructed with high probability by solving an optimization problem [
18,
19].
In CS model, sparse transformation is first proceeded for signal
:
where for a sparse signal vector
, sparse matrix basis
and coefficient vector
, if
is full rank and only
of the
are nonzero, then define the signal
is
k sparse in the sparse matrix
.
Afterwards, signal
is projected into a measurement matrix
which satisfies the restricted isometric property (RIP) condition, then the measurement vector
is obtained:
where
and
is the measurement matrix.
Finally, substitute Equation (2) into Equation (3), then obtain:
where
is observation dictionary and the measurement
is incoherence with the basis
.
Theoretically speaking, reconstructing the sparse coefficient sequence
is equivalent to solving an optimization problem, the
minimization problem, as follows:
Since the problem as formulated in Equation (5) is a NP-hard problem and numerically unfeasible, we may opt for the basis pursuit algorithm with minimization.
The reconstruction of the signal, namely the process of recovering N-dimensional sparse signal from M-dimensional observation signal , can be solved by conducting -norm minimization optimization to Equation (5).
In the theory of compressive sensing, observation dictionary must satisfy the RIP condition, selecting
L column from
(
,
) to constitute one submatrix
,
satisfies:
where
represents the
S-restricted isometric constant of
, and it is the minimum value to hold the above formula. The essence of the above-mentioned conditions is that the requirement of matrix
is a kind of approximate orthogonal matrix (due to
, the complete orthogonal cannot be realized).
The sparse transformation matrix is commonly an orthogonal type of matrix; therefore, to render it is necessary to meet the RIP property, which takes only matrix satisfying RIP conditions. Normally, if matrix is a stochastic matrix, then it satisfies the RIP with a large probability.
As a practical example, consider a single-pixel [
20], which was developed by researchers from Rice University in the United States using compressed sensing principle, and has been widespread recently. The main component is a digital micromirror device (DMD), which consists of a large number of bacteria size lenses, each lens has two sides, reflective and non-reflective, and can quickly flip. To reconstruct the image, each sampling state of DMD is necessary,
i.e., which lenses are in a reflective state, and which are not. In [
20], the signals at the Scene amount to input signal
. The input signal directly hit DMD after some pretreatment. DMD array is equivalent to the matrix
in CS. The processing for the convergence of the natural image at the photodiode is equivalent to addition. The bitstream is the output vector
after the observation matrix. Finally, with the aid of observation vector
and matrix
, the image is reconstructed using the above mentioned reconstruction algorithm. The image is the final decoded signal if it is present in encoding and decoding theory. The single pixel camera is an excellent example of the application of compressed sensing theory, which can be closely linked with the framework of CS theory. At the same time, it is also a good invention, which confirms the availability of compressed sensing.
4. Basic Idea of PU-CSL Algorithm and Efficiency Analysis
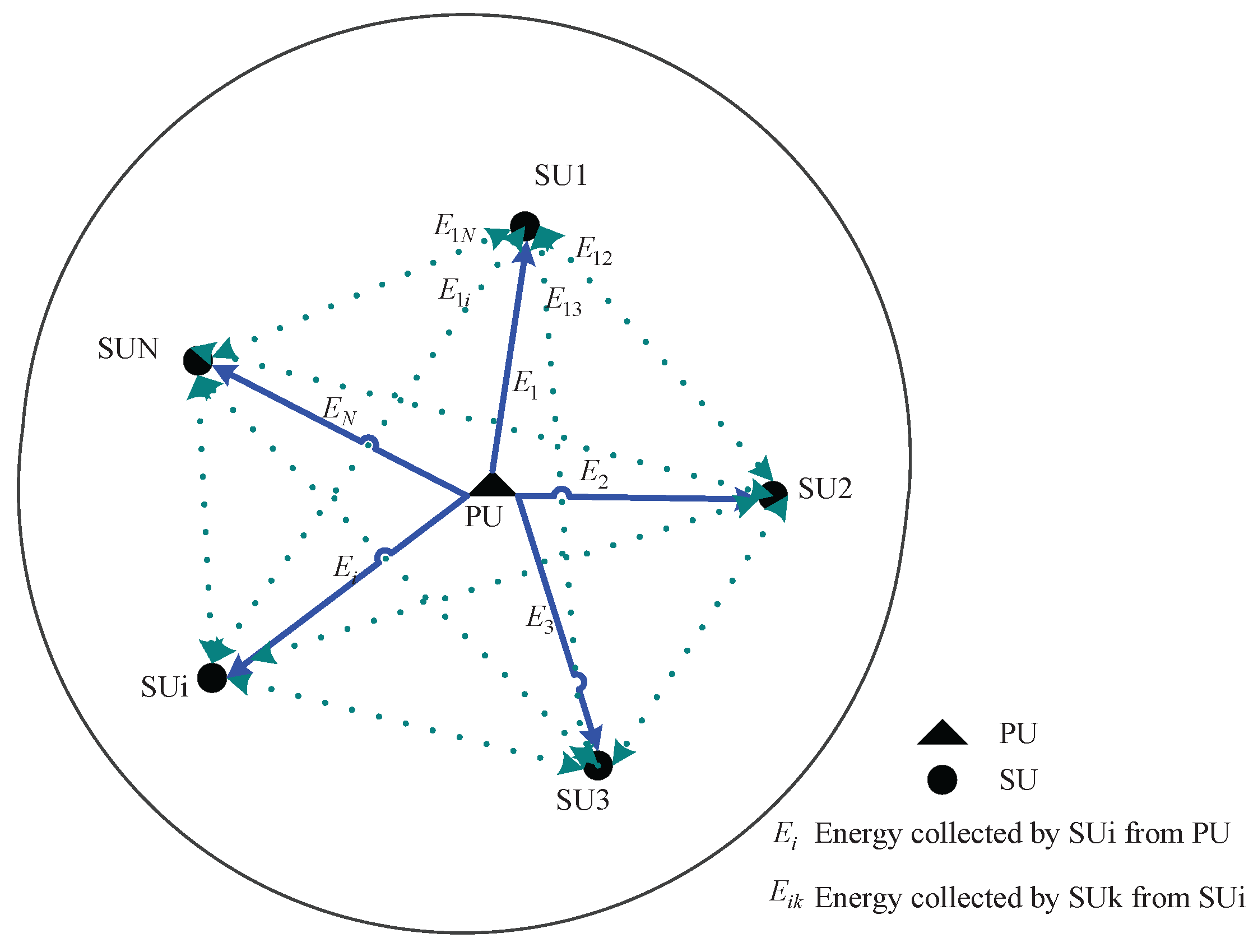
The data shown in
Figure 2 assume that
N SUs are randomly distributed in CRN. Based on the corresponding relation between received source signal energy and its location, the source signal collects received energy at each receiver, namely energy fingerprint, which is regarded as its exclusive identity label. Within one sensing period, SUs collect the energy of the source signal within the sensing band. We define
as the energy collected at the
SU from source signal node, where
, then the energy fingerprint of the source signal node can be described as:
Similarly, we define as energy from the SU to the SU (the theoretical energy value between two nodes can be calculated using the signal transmission model). Then energy fingerprints between the cognitive node and all SUs are defined as , where the value of can be obtained using channel transmission model or actual measurement. In distributed cognitive radio networks, nodes that participate in the collaborative spectrum sensing can acquire sensing information of neighboring nodes by reporting channels (such as the energy values required by the algorithm in this paper). The channel transmission model or measured values are two kinds of means to obtain energy values. We use the channel transmission model to obtain the energy value and use the software platform to simulate the algorithm. When the algorithm is applied to the actual wireless scenarios, the measured energy values are indispensable.
All the energy fingerprints of SUs in CRN are combined into the sparse transforming matrix
M:
Energy fingerprint
can be represented according to sparse transforming basis
:
where
represents the degree of correlation between the
SUs and source signal node,
. Generally, once SUs get closer to the source signal node, the signal energy fingerprint between it and other SUs becomes more similar. In other words, as the distance between SUs and the source signal node gets smaller, the degree of correlation
becomes greater, otherwise
will be smaller or even zero. Furthermore, the main constituents of energy fingerprint
are described by a few close SUs’ energy fingerprints. Only several SUs has greater correlation coefficients, and the rest are zero or close to zero. It means that the degree of correlation vector
μ is sparse.
According to Equation (4), defining CS information operator as
, thus measurement vector
can be written as
where
y is the measurement vector of each SU received signal strength (RSS),
is grid transfer relationship between each SU and PU source signal. The normalized correlation coefficient
μ can be reconstructed by basic CS according to Equation (6).
Then the weighted value
of each SU can be obtained as follows
Assume
is coordinate of the
SU, then 2-dimensional location of source signal node
can be estimated by using WCL
The following
Figure 3 denotes the source node localization flowchart of the PU-CSL algorithm during one sensing period.
In fact, the correlation degree increases as nodes become closer to each other. However, there is also one point that needs to be clear: the proposed PU-CSL algorithm that integrally explores the correlation between source signal and SUs using CS. The correlation between source signal and SUs is the decisive factor to determine the result of the positioning. Hence we put the main focus on how to integrally explore the correlation between source signal and SUs and achieve higher localization accuracy.
Figure 4 describes how the source node is linearly represented by 40 SUs which are randomly distributed in a quadrate sensing area of 100 × 100 m
2. The black solid triangles in the figure are the source node, the circles and five-pointed star show the SUs, the circle represents a SU whose correlation coefficient is zero, and the five-pointed star denotes the the SUs whose correlation coefficient is nonzero. There is positive correlation between the size of pentagram and the correlation coefficient of the node.
As can be seen from
Figure 4, the greater the correlation coefficient of the node is, the closer the geometric position are to the source node. The SU with relatively small and even zero correlation coefficient is always far away from the source node.
More importantly, in the sensing area, few SUs have a large correlation coefficient. Most of the nodes’ correlation coefficients are zero or close to zero, that is, the vector that constitutes of all the correlation coefficient of SUs is sparse. The conclusion is consistent with the above theoretical analysis. Therefore, the degree of correlation between SUs and source node can be accurately reconstructed using CS theory, thus it is possible to estimate the location of the source node.
5. Simulation and Analysis of Localization Performance
The localization performance of the proposed PU-CSL scheme has been simulated and compared with RR-WCL scheme using MATLAB ( [
13] has proved that the localization performance of RR-WCL is much better than W-Centroid, RR-WCL is then chosen as comparison). Here is the simulation environment. There is one source signal node,
. SUs are randomly distributed in a quadrate sensing localization area of
. The parameters of the signal model are respectively set as
,
,
. After balancing spectrum efficiency and observation times, the death rate
α and birth rate
β in the PU activity model [
17] are both set as 1. The mean and standard deviation value of shadow fading factor
are respectively 0 and 4. The energy fingerprints of nodes are obtained based on signal loss model Equation (2), the correlation coefficients are reconstructed by CS using BP algorithm.
Figure 5 displays the comparative result of PU-CSL and RR-WCL concerning the root mean square error of location error (we recall the definition of root mean square error as RMSE =
, where
X is the original observation and
is the reconstructed signal) and MLE (the maximum location error is the maximum distance between the actual position and the predicted position of the node). The signal-to-noise ratio (SNR) is 0 dB∼20 dB and the amount of SUs
N in spectrum sensing is 40.
Several points can be found from the curves. Firstly, the root mean square error and maximum location error of both algorithms continually decrease as increases. This is because the energy fingerprints of the SUs and the source signal node become more similar when is lower, which leads to better localization performance. Secondly, as changed between and , the root mean square error and maximum location error of the PU-CSL respectively improved by 33.38%∼65.66% and 28.20%∼71.04% compared to the PR-WCL, which means that PU-CSL exhibits better anti-noise performance. Besides, under the condition of same , both of the root mean square error and maximum location error of PU-CSL are smaller than RR-WCL. Therefore, PU-CSL shows higher localization accuracy. Since RR-WCL merely concerns the degree of correlation between nodes and the source node, the proposed PU-CSL algorithm integrally explores the correlation between source signal and SUs using CS. Hence, the source signal node is preferably described by SUs with correlation property. However, PU-CSL achieves higher localization accuracy.
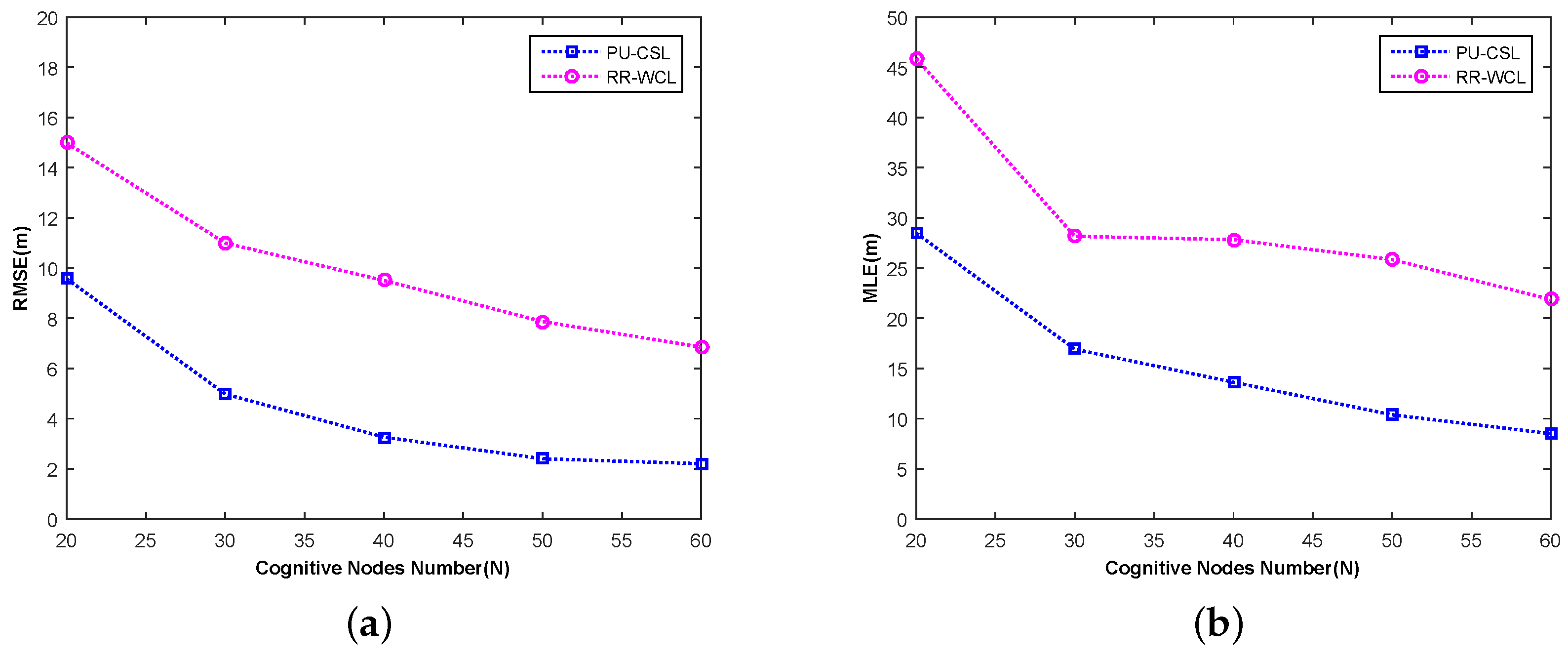
Figure 6 shows the localization performance with respect to the change of root mean square error and maximum location error as the number of SUs
N changes, where
.
There are two aspects that can be inferred from
Figure 6. Firstly, the root mean square error and maximum location error of both algorithms decrease with the increase of the amount of SUs. In other words, the more nodes getting involved in CSS, the higher localization accuracy of the source signal node is obtained. However, in actual CRN, as the number of SUs increases, the information sent to IPC also increases and request for
data processing ability gets higher. Thus, in practice, we should choose a suitable number of cognitive nodes for the localization of source signal node, comprehensively considering the hardware cost and localization performance of the network in the meantime. Secondly, as the number of SUs changes between 20 and 60, the root mean square error and maximum location error of the PU-CSL algorithm respectively improved by 36.10%∼69.46% and 37.92%∼61.08% compared to the PR-WCL, which means that the PU-CSL exhibits better localization performance. Besides, with the same number of cognitive nodes, the PU-CSL outperforms the RR-WCL in localization performance. Being different from RR-WCL, PU-SCL explores the degree of correlation between source signal and SUs integrally at one time using CS. Therefore, it performs higher localization accuracy due to making more comprehensive consideration of the source localization.