From Intrusion Detection to an Intrusion Response System: Fundamentals, Requirements, and Future Directions
Abstract
:1. Introduction
2. Types of Intrusion
3. Common Solutions to Intrusions
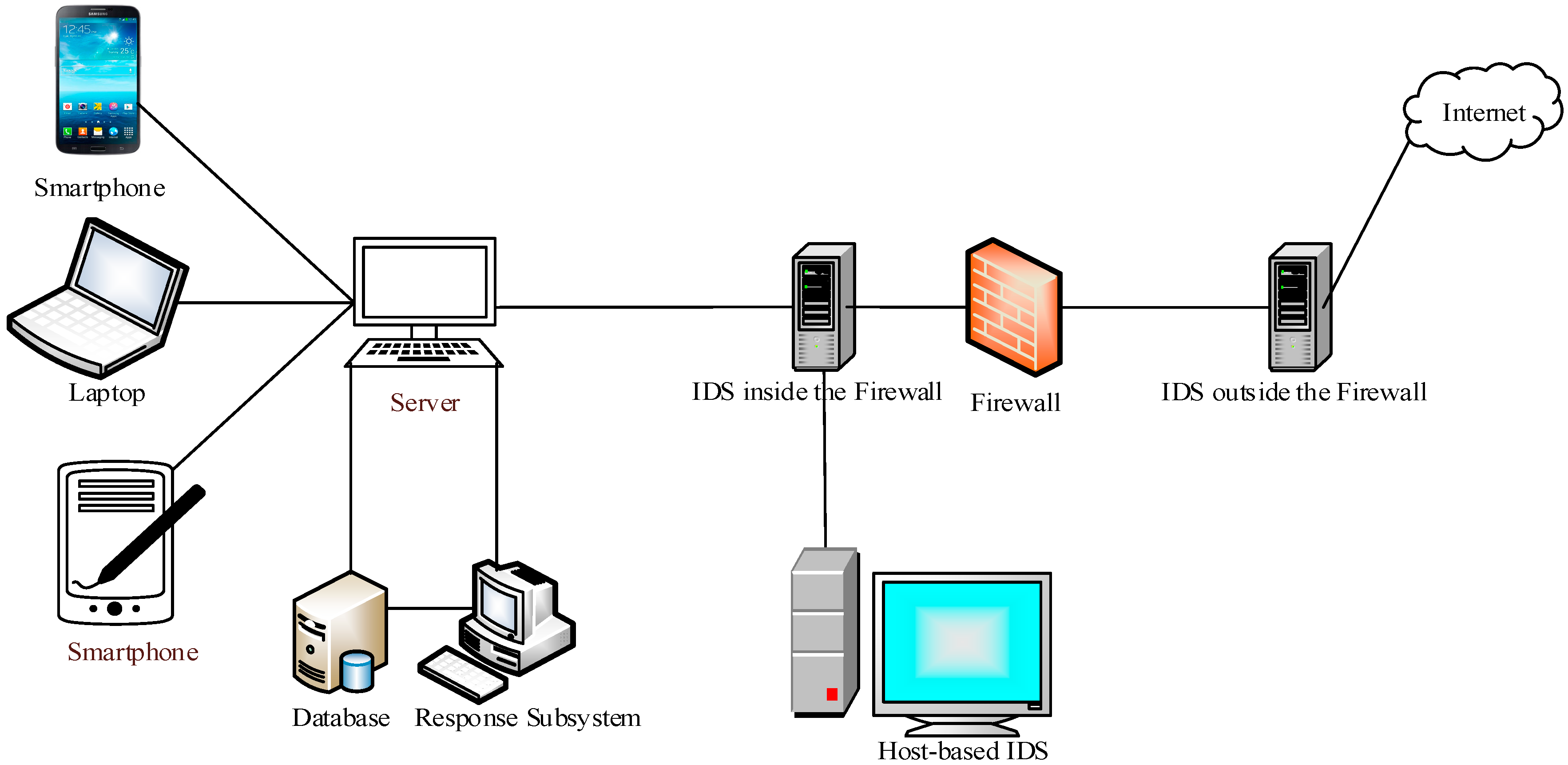
3.1. Intrusion Detection System
3.2. Intrusion Response System
4. Comparison of Attacks According to Affected Parameters
Data Threats and Response Options
5. Responses to Attacks
6. Current Challenges to IRS
6.1. Real-Time Response
6.2. Alert Parallelization
6.3. Controlling-False Alarm
6.4. Risk Assessment
7. Future Directions
8. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Ren, S.Q.; Tan, B.H.M.; Sundaram, S.; Wang, T.; Ng, Y.; Chang, V.; Aung, K.M.M. Secure searching on cloud storage enhanced by homomorphic indexing. Future Gener. Comput. Syst. 2016, 65, 102–110. [Google Scholar] [CrossRef]
- Asia Pacific Computer Emergency Response Team. Available online: http://www.apcert.org/ (accessed on 20 September 2016).
- Malaysia Computer Emergency Responce Team Incident Statistics. Available online: http://www.mycert.org.my/en/ (accessed on 20 September 2016).
- Scarfone, K.; Mell, P. Guide to Intrusion Detection and Prevention Systems (IDPS); Report Number: 800-94; NIST Special Publication: Gaithersburg, MD, USA, 2007. [Google Scholar]
- Inayat, Z.; Gani, A.; Anuar, N.B.; Anwar, S.; Khan, M.K. Cloud-Based Intrusion Detection and Response System: Open Research Issues, and Solutions. Arab. J. Sci. Eng. 2017, 7, 1–25. [Google Scholar] [CrossRef]
- Fraga, J.; Powell, D. A fault-and intrusion-tolerant file system. In Proceedings of the 3rd International Conference on Computer Security, Dublin, Ireland, 12–15 August 1985; pp. 203–218. [Google Scholar]
- Inayat, Z.; Gani, A.; Anuar, N.B.; Khan, M.K.; Anwar, S. Intrusion response systems: Foundations, design, and challenges. J. Netw. Comput. Appl. 2016, 62, 53–74. [Google Scholar] [CrossRef]
- Anuar, N.B.; Papadaki, M.; Furnell, S.; Clarke, N. An investigation and survey of response options for Intrusion Response Systems (IRSs). In Proceedings of the Information Security for South Africa (ISSA), Johannesburg, South Arfica, 2–4 August 2010. [Google Scholar]
- Hajian, S.; Domingo-Ferrer, J.; Martinez-Balleste, A. Discrimination prevention in data mining for intrusion and crime detection. In Proceedings of the 2011 IEEE Symposium on Computational Intelligence in Cyber Security (CICS), Paris, France, 11–15 April 2011; pp. 47–54. [Google Scholar]
- Neela, K.; Kavitha, V. A survey on security Issues and vulnerabilities on cloud computing. Int. J. Comput. Sci. Eng. Technol. (IJCSET) 2013, 4, 855–860. [Google Scholar]
- Wu, Z.; Xu, Z.; Wang, H. Whispers in the Hyper-space: High-speed Covert Channel Attacks in the Cloud. In Proceedings of the USENIX Security Symposium, Washington, DC, USA, 14–17 August 2012; pp. 159–173. [Google Scholar]
- Yarom, Y.; Falkner, K. FLUSH+ RELOAD: A High Resolution, Low Noise, L3 Cache Side-Channel Attack. In Proceedings of the USENIX Security, San Diego, CA, USA, 20–22 August 2014; pp. 719–732. [Google Scholar]
- Chang, C.-W.; Lee, S.; Lin, B.; Wang, J. The taming of the shrew: Mitigating low-rate TCP-targeted attack. IEEE Trans. Netw. Serv. Manag. 2010, 7. [Google Scholar] [CrossRef]
- Anwar, S.; Zain, J.M.; Zolkipli, F.; Inayat, Z. A Review Paper on Botnet and Botnet Detection Techniques in Cloud Computing. In Proceedings of the ISCI 2014—IEEE Symposium on Computers & Informatics, Sabah, Malaysia, 28–29 September 2014; p. 5. [Google Scholar]
- Workman, M. A behaviorist perspective on corporate harassment online: Validation of a theoretical model of psychological motives. Comput. Secur. 2010, 29, 831–839. [Google Scholar] [CrossRef]
- Bernaschi, M.; Ferreri, F.; Valcamonici, L. Access points vulnerabilities to DoS attacks in 802.11 networks. Wirel. Netw. 2008, 14, 159–169. [Google Scholar] [CrossRef]
- Duc, A.; Dziembowski, S.; Faust, S. Unifying Leakage Models: From Probing Attacks to Noisy Leakage. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Copenhagen, Denmark, 11–15 May 2014; pp. 423–440. [Google Scholar]
- Halfond, W.G.; Viegas, J.; Orso, A. A classification of SQL-injection attacks and countermeasures. In Proceedings of the IEEE International Symposium on Secure Software Engineering, Washington, DC, USA, 13–15 March 2006; pp. 13–15. [Google Scholar]
- Naser, A.; Majid, M.A.; Zolkipli, M.F.; Anwar, S. Trusting cloud computing for personal files. In Proceedings of the 2014 International Conference on Information and Communication Technology Convergence (ICTC), Busan, South Korea, 22–24 October 2014; pp. 488–489. [Google Scholar]
- Hoque, M.S.; Mukit, M.; Bikas, M.; Naser, A. An implementation of intrusion detection system using genetic algorithm. arXiv, 2012; arXiv:1204.1336. [Google Scholar]
- Ranjan, S.; Swaminathan, R.; Uysal, M.; Knightly, E.W. DDoS-Resilient Scheduling to Counter Application Layer Attacks Under Imperfect Detection. In Proceedings of the INFOCOM, Barcelona, Spain, 23–29 April 2006. [Google Scholar]
- Yi, S.; Naldurg, P.; Kravets, R. Security-aware ad hoc routing for wireless networks. In Proceedings of the 2nd ACM International Symposium on Mobile Ad Hoc Networking & Computing, Long Beach, CA, USA, 4–5 October 2001; pp. 299–302. [Google Scholar]
- Liu, F.; Yarom, Y.; Ge, Q.; Heiser, G.; Lee, R.B. Last-level cache side-channel attacks are practical. In Proceedings of the 2015 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 17–21 May 2015; pp. 605–622. [Google Scholar]
- US-CERT. Available online: https://www.us-cert.gov/ncas/tips/ST04-004 (accessed on 12 September 2016).
- Khan, S.; Shiraz, M.; Wahab, A.W.A.; Gani, A.; Han, Q.; Rahman, Z.B.A. A Comprehensive Review on Adaptability of Network Forensics Frameworks for Mobile Cloud Computing. Sci. World J. 2014, 2014, 27. [Google Scholar] [CrossRef] [PubMed]
- Genge, B.; Siaterlis, C.; Karopoulos, G. Data fusion-base anomay detection in networked critical infrastructures. In Proceedings of the 2013 43rd Annual IEEE/IFIP Conference on Dependable Systems and Networks Workshop (DSN-W), Budapest, Hungary, 24–27 June 2013; pp. 1–8. [Google Scholar]
- Sequeira, D. Intrusion Prevention Systems Security’s Silver Bullet? Available online: http://www.sans.org/reading-room/whitepapers/detection/intrusion-prevention-systems-securitys-silver-bullet-366?show=366.php&cat=detection (accessed on 9 September 2016).
- Anwar, J.M.Z.S.; Zolkipli, M.F.; Inayat, Z.; Jabir, A.N.; Odili, J.B. Response Option for Attacks Detected by Intrusion Detection System. In Proceedings of the 4th International Conference on Software Engineering and Computer System, Kuantan, Malaysia, 19–21 August 2015; p. 7. [Google Scholar]
- Asosheh, A.; Ramezani, N. A comprehensive taxonomy of DDOS attacks and defense mechanism applying in a smart classification. WSEAS Trans. Comput. 2008, 7, 281–290. [Google Scholar]
- Shameli-Sendi, A.; Cheriet, M.; Hamou-Lhadj, A. Taxonomy of intrusion risk assessment and response system. Comput. Secur. 2014, 45, 1–16. [Google Scholar] [CrossRef]
- Foo, B.; Wu, Y.-S.; Mao, Y.-C.; Bagchi, S.; Spafford, E. ADEPTS: Adaptive intrusion response using attack graphs in an e-commerce environment. In Proceedings of the International Conference on Dependable Systems and Networks, Yokohama, Japan, 28 June–1 July 2005; pp. 508–517. [Google Scholar]
- Genge, B.; Haller, P. A hierarchical control plane for software-defined networks-based industrial control systems. In Proceedings of the IFIP Networking Conference (IFIP Networking) and Workshops, Vienna, Austria, 17–19 May 2016; pp. 73–81. [Google Scholar]
- Stakhanova, N.; Basu, S.; Wong, J. A Cost-Sensitive Model for Preemptive Intrusion Response Systems. In Proceedings of the AINA, ON, Canada, 21–23 May 2007; pp. 428–435. [Google Scholar]
- Ilgun, K. USTAT: A real-time intrusion detection system for UNIX. In Proceedings of the 1993 IEEE Computer Society Symposium on Research in Security and Privacy, Okland, CA, USA, 24–26 May 1993; pp. 16–28. [Google Scholar]
- Nadeem, A.; Howarth, M. Protection of MANETs from a range of attacks using an intrusion detection and prevention system. Telecommun. Syst. 2013, 52, 2047–2058. [Google Scholar] [CrossRef]
- Nadeem, A.; Howarth, M.P. An intrusion detection & adaptive response mechanism for MANETs. Ad Hoc Netw. 2014, 13, 368–380. [Google Scholar]
- Kizza, J.M. A Guide to Computer Network Security; Springer: London, UK, 2009. [Google Scholar]
- Khan, S.; Gani, A.; Wahab, A.W.A.; Bagiwa, M.A. SIDNFF: Source identification network forensics framework for cloud computing. In Proceedings of the 2015 IEEE International Conference on Consumer Electronics-Taiwan (ICCE-TW), Taipei, Tiwan, 6–8 June 2015; pp. 418–419. [Google Scholar]
- Ragsdale, D.J.; Carver, C.A.; Humphries, J.W.; Pooch, U.W. Adaptation techniques for intrusion detection and intrusion response systems. In Proceedings of the 2000 IEEE International Conference on Systems, Man, and Cybernetics, Nashville, TN, United States, 8–11 October 2000; pp. 2344–2349. [Google Scholar]
- Carver, A.C.J. Adaptive Agent-Based Intrusion Response. Ph.D. Thesis, Texas A&M University, College Station, TX, USA, May 2001. [Google Scholar]
- Anwar, S.; Zain, J.M.; Inayat, Z.; Haq, R.U.; Karim, A.; Jabir, A.N. A Static Approach Towards Mobile Botnet Detection. In Proceedings of the 2016 3rd International Conference on Electronic Design (ICED), Phuket, Thailand, 11–12 August 2016; pp. 563–567. [Google Scholar]
- Toth, T.; Kruegel, C. Evaluating the impact of automated intrusion response mechanisms. In Proceedings of the 18th Annual Computer Security Applications Conference, Washington, DC, USA, 9–13 December 2002; pp. 301–310. [Google Scholar]
- Jou, Y.; Gong, F.; Sargor, C.; Wu, X.; Wu, S.; Chang, H.; Wang, F. Design and implementation of a scalable intrusion detection system for the protection of network infrastructure. In Proceedings of the DARPA Information Survivability Conference and Exposition, DISCEX’00, Hilton Head, CA, USA, 25–27 January2000; pp. 69–83. [Google Scholar]
- Porras, P.A.; Neumann, P.G. EMERALD: Event monitoring enabling response to anomalous live disturbances. In Proceedings of the 20th National Information Systems Security Conference, Baltimore, MD, USA, 7–10 October 1997; pp. 353–365. [Google Scholar]
- Shiraz, M.; Gani, A.; Khokhar, R.H.; Buyya, R. A review on distributed application processing frameworks in smart mobile devices for mobile cloud computing. IEEE Commun. Surv. Tutor. 2013, 15, 1294–1313. [Google Scholar] [CrossRef]
- Ying, L.; Yan, Z.; Ou, Y. The design and implementation of host-based intrusion detection system. In Proceedings of the 2010 Third International Symposium on Intelligent Information Technology and Security Informatics (IITSI), Jian, China, 2–4 April 2010; pp. 595–598. [Google Scholar]
- Intrusion Prevention for the Cisco ASA 5500-X, Series. Available online: http://www.cisco.com/c/dam/en/us/products/collateral/security/asa-5500-series-next-generation-firewalls/data_sheet_c78_459036.pdf (accessed on 15 August 2016).
- Hansman, S.; Hunt, R. A taxonomy of network and computer attacks. Comput. Secur. 2005, 24, 31–43. [Google Scholar] [CrossRef]
- Zhang, Y.; Lee, W. Intrusion detection in wireless ad-hoc networks. In Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, Boston, MA, USA, 6–11 August 2000; pp. 275–283. [Google Scholar]
- Stakhanova, N.; Basu, S.; Wong, J. A taxonomy of intrusion response systems. Int. J. Inf. Comput. Secur. 2007, 1, 169–184. [Google Scholar] [CrossRef]
- Chang, V.; Kuo, Y.-H.; Ramachandran, M. Cloud computing adoption framework: A security framework for business clouds. Future Gen. Comput. Syst. 2016, 57, 24–41. [Google Scholar] [CrossRef]
- Patel, A.; Taghavi, M.; Bakhtiyari, K.; JúNior, J.C. An intrusion detection and prevention system in cloud computing: A systematic review. J. Netw. Comput. Appl. 2013, 36, 25–41. [Google Scholar] [CrossRef]
- White, G.B.; Fisch, E.A.; Pooch, U.W. Cooperating security managers: A peer-based intrusion detection system. Netw. IEEE 1996, 10, 20–23. [Google Scholar] [CrossRef]
- Vigna, G.; Kemmerer, R.A. NetSTAT: A network-based intrusion detection system. J. Comput. Secur. 1999, 7, 37–71. [Google Scholar] [CrossRef]
- Garcia-Teodoro, P.; Diaz-Verdejo, J.; Maciá-Fernández, G.; Vázquez, E. Anomaly-based network intrusion detection: Techniques, systems and challenges. Comput. Secur. 2009, 28, 18–28. [Google Scholar] [CrossRef]
- Nadeem, A.; Howarth, M. Adaptive intrusion detection & prevention of denial of service attacks in MANETs. In Proceedings of the 2009 International Conference on Wireless Communications and Mobile Computing: Connecting the World Wirelessly, Leipzig, Germany, 21–24 June 2009; pp. 926–930. [Google Scholar]
- Shanmugavadivu, R.; Nagarajan, D.N. Network intrusion detection system using fuzzy logic. Indian J. Comput. Sci. Eng. (IJCSE) 2011, 2, 101–111. [Google Scholar]
- Lindqvist, U.; Jonsson, E. How to systematically classify computer security intrusions. In Proceedings of the 1997 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 4–7 May 1997; pp. 154–163. [Google Scholar]
- Corona, I.; Giacinto, G.; Roli, F. Adversarial attacks against intrusion detection systems: Taxonomy, solutions and open issues. Inf. Sci. 2013, 239, 201–225. [Google Scholar] [CrossRef]
- Banerjee, U.; Arya, K. Experimental Study and Analysis of Security Threats in Compromised Networks. In Emerging Trends in Computing and Communication; Springer: Kolkata, India, 2014; pp. 53–60. [Google Scholar]
- Rubinstein, I.S. Big Data: The End of Privacy or a New Beginning? Int. Data Priv. Law 2013, 3, 12–56. [Google Scholar] [CrossRef]
- TechNet. Available online: http://technet.microsoft.com/en-us/library/cc959354.aspx (accessed on 28 September 2016).
- Modi, C.; Patel, D.; Borisaniya, B.; Patel, H.; Patel, A.; Rajarajan, M. A survey of intrusion detection techniques in cloud. J. Netw. Comput. Appl. 2013, 36, 42–57. [Google Scholar] [CrossRef]
- Spam and Fraud Activity Trends. Available online: http://www.symantec.com/ (accessed on 7 September 2016).
- Nadeem, A.; Howarth, M.P. A Survey of MANET Intrusion Detection & Prevention Approaches for Network Layer Attacks. IEEE Commun. Surv. Tutor. 2012, 15, 2027–2045. [Google Scholar]
- Moore, D.; Shannon, C. Code-Red: A case study on the spread and victims of an Internet worm. In Proceedings of the 2nd ACM SIGCOMM Workshop on Internet Measurment, Marseille, France, 6–8 November 2002; pp. 273–284. [Google Scholar]
- Wang, Z.; Lee, R.B. Covert and side channels due to processor architecture. In Proceedings of the 22nd Annual Computer Security Applications Conference, ACSAC’06, Washington, DC, USA, 1–15 December 2006; pp. 473–482. [Google Scholar]
- Khan, N.; Yaqoob, I.; Hashem, I.A.T.H.; Inayat, Z.; Ali, W.K.M.; Alam, M.; Shiraz, M.; Gani, A. Big Data: Survey, Technologies, Opportunities, and Challenges. Sci. World J. 2014, 2014. [Google Scholar] [CrossRef] [PubMed]
- Xu, Q.; Liu, G. Configuring clark-wilson integrity model to enforce flexible protection. In Proceedings of the International Conference on Computational Intelligence and Security, CIS’09, San Jose, CA, USA, 11–14 December 2009; pp. 15–20. [Google Scholar]
- Bace, R.; Mell, P. NIST Special Publication on Intrusion Detection Systems; DTIC Document 2001; Macmillan: McLean, VA, USA, 2001. [Google Scholar]
- Yue, W.T.; Çakanyıldırım, M. A cost-based analysis of intrusion detection system configuration under active or passive response. Decis. Support Syst. 2010, 50, 21–31. [Google Scholar] [CrossRef]
- Raju, P.N. State-of-the-Art Intrusion Detection: Technologies, Challenges, and Evaluation. Master Thesis, Linköping University, Linköping, Sweden, February 2005. [Google Scholar]
- Cansian, A.M.; Moreira, E.; Carvalho, A.; Bonifacio, J. Network intrusion detection using neural networks. In Proceedings of the International Conference on Computational Intelligence and Multimedia Applications, Gold Coast, Australia, 10–12 February; pp. 276–280.
- Bonifaco, J.; Moreira, E. An adaptive intrusion detection system using neural networks. In Proceedings of the International Federation for Information Processing (IFIP) Information Security & Privacy Conference, Poznan, Poland, 31 August–4 September 1998. [Google Scholar]
- Bace, R.G. Intrusion Detection. Available online: http://books.google.com.my/books?isbn=1578701856 (accessed on 20 September 2016).
- Hasswa, A.; Zulkernine, M.; Hassanein, H. Routeguard: An intrusion detection and response system for mobile ad hoc networks. In Proceedings of the IEEE International Conference on Wireless and Mobile Computing, Networking and Communications, (WiMob’2005), Big Island, HI, USA, 2005; pp. 336–343. [Google Scholar]
- Wang, S.-H.; Tseng, C.H.; Levitt, K.; Bishop, M. Cost-sensitive intrusion responses for mobile ad hoc networks. In Recent Advances in Intrusion Detection; Springer: Berlin, Germany, 2007; pp. 127–145. [Google Scholar]
- Hawrylkiw, D. SANS. Available online: http://www.sans.org/security-resources/idfaq/auto_res.php (accessed on 30 April 2014).
- Symantec. February 2007. Available online: http://www.symantec.com/security_response/writeup.jsp?docid=2001-080421-3353-99 (accessed on 24 September 2016).
- Anuar, N.B.; Furnell, S.; Papadaki, M.; Clarke, N. Response Mechanisms for Intrusion Response Systems (IRSs); University of Plymouth: Plymouth, UK, 2009. [Google Scholar]
- Kruegel, C.; Valeur, F.; Vigna, G. Intrusion Detection and Correlation: Challenges and Solutions; Springer: New York, NY, USA, 2004; Volume 14. [Google Scholar]





| Symbol | Description |
|---|---|
| IDS | Intrusion Detection System |
| IRS | Intrusion Response System |
| IPS | Intrusion Prevention System |
| IDRS | Intrusion Detection and Response System |
| DIDS | Distributed Intrusion Detection System |
| CIA | Confidentiality, Integrity, Availability |
| DOS | Denial of Service |
| DDOS | Distributed Denial of Service |
| NIDS | Network-Based Intrusion Detection System |
| HIDS | Host-Based Intrusion Detection System |
| AD | Anomaly Detection |
| SD | Signature Based Detection |
| AIRS | Automatic Intrusion Response System |
| AAIRS | Adaptive Automatic Intrusion Response System |
| CSM | Cooperating Security Managers |
| MANET | Mobile Ad hoc Network |
| GIDP | Generalized Intrusion Detection System |
| IDAR | Intrusion-Detection and-Adaptive Response-Mechanism |
| AudES | Audit Expert System |
| Types of Attacks | Ref. | Attack Name | Description | |
|---|---|---|---|---|
| Active Attacks | [7] | Routing Attacks | Black Hole | Refers to dropped traffic in networks. |
| Gray Hole | Behaves like a malicious node to drop malicious packets, but later switches back to normal. | |||
| Rushing | A malicious node raising the speed of the routing process. | |||
| Man in the Middle | Attacker secretly relays and intercepts messages between two parties. | |||
| Sleep Deprivation | It targets the sensor of nodes to maximize power consumption. | |||
| Spoof | When an attacker imitates someone else’s device or a user in order to initiate attacks against network hosts, bypass access controls, steal data, or spread malware. | |||
| Sybil | It is an attack wherein a reputation system is subverted by foreign identities in P2P networks. | |||
| Malicious Packet Dropping | It is a type of DDoS attack similar to black hole attacks. | |||
| Passive Attacks | [5] | Eavesdropping | Network layer attacks that intercept private communication. | |
| Traffic Analysis | An attack that examines the communication patterns between entities in a system. | |||
| Location Disclosure | Can expose anything about the network structure or the nodes’ locations. | |||
| Fraud | [9] | Hijacked | The attackers take control of communication between nodes and networks, alias man-in-the-middle attacks. | |
| Defacement | It changes the physical appearance of a website or page. | |||
| Phishing | It is an e-mail fraud scam that tries to obtain credentials such as credit card details, usernames, and passwords. | |||
| Illegal Investment | Investment through others’ accounts in an illegal way. | |||
| Account Compromised | - | |||
| Site | This fraud occurs when a user opens an infected website. | |||
| Purchase | Using fake or stolen credit card for a transaction. The most common fraud is credit cards. | |||
| Lottery Scam | An advanced type of Internet fraud where you get an unexpected e-mail explaining that you won a huge amount to attract victims. | |||
| Unauthorized Transaction | Using stolen information from someone’s credit card to perform a transaction. | |||
| Counterfeit Item | Making a fake or copy of original items. | |||
| Online | Criminal activities performed online: attackers may get someone’s personal information, credit card data, or anything else private in an illegal way. | |||
| Sniffer Attacks | [10] | - | Capturing network packets and interrupting network protocol analyzing activities. | |
| Covert Channel Attacks | [11] | Storage Channel Attacks | A covert channel allows transfer of information by an unauthorized process. A storage channel communicates by modifying a storage location. A timing channel performs operations that affect the response time observed by the receiver. | |
| Timing Channel Attacks | ||||
| Side-Channel-Attacks | [12] | Timing-driven attacks | This is a common threat to multi-level system such as databases, operating systems, and networks in which attackers extract information about the sensor of data that is used in the devices. | |
| Access-driven attacks | ||||
| Trace-driven attacks | ||||
| Low rate TCP Attacks | [13] | It sends a burst of settled-timed packets, conceiving packet loss and incrementing the retransmission timeout for certain TCP flows. It has a severe impact on the Border Gateway Protocol (BGP). | ||
| Close-in Attacks | [5] | - | Social engineering is the main type of this attack. Getting closer to the network devices to get more information about them is known as a close-in attack. | |
| Exploit Attacks | [7] | - | Using illegal means to utilize something to one’s advantage. | |
| Insider Attacks | [7] | User to Root (U2R) | An attacker accesses the account of normal users on a system and exploits some vulnerability. | |
| Port Scanning | Scan the free and less secure port for attempting attacks. | |||
| Flooding | Sending requests to a server at the same time to shut it down by keeping the system busy. | |||
| Malicious Attacks | [14] | Bot/ Botnet | A network of infected devices connected to the Internet performs criminal activities in a group. | |
| Malware | This is software specially designed to damage or destroy a system or database. | |||
| Malware Hosting | The place where malware resides can be mobile or a Personal Computer (PC). | |||
| DDOS/DOS | [10] | Buffer Overflow | When a program overruns the buffer boundary and overwrites the adjacent memory location. | |
| Ping of Death | It is a request that destroys the target device by putting an invalid packet size value in the packet header. | |||
| ICMP | It is a kind of DDoS attack sending a huge flood of ICMP packets to the victim machine in order to crash it. | |||
| Smurf | Sending a large number of ICMP packets to perform DDoS attack. | |||
| UDP Flood | Sending a large number of UDP packets to random ports. | |||
| SYN Flood | Consume enough server resources to make the system unresponsive to legitimate traffic. | |||
| Cyber Harassment | [15] | Cyberbullying | A type of bullying using the Internet. This attack can be performed using mobile devices or websites. | |
| Cyber Stalking | Using electronic media such as e-mail messages to harass a victim. | |||
| Sexual | The Internet is the main source for the sexual harassment, harassment using Internet-based technologies such as email and social media platform. | |||
| Religious | Includes forced religion conversion using electronic media and social media. | |||
| Racial | Refers to harassment suffered by individuals or groups because of their color or race. | |||
| Vulnerabilities Report | [16] | Web | An interlinked documents type of hypertext that is accessed through the Internet. | |
| Misconfiguration | Configuration mistakes that result in unintended application behavior that includes misuse of default passwords, privileges, and excessive debugging information disclosure. | |||
| System | - | |||
| Probing | [17] | - | Combining several different familiar dodging techniques for network attacks. | |
| Content-Related | National | - | ||
| Intellectual Properties | After research and work, finding something new or inventing something as the result of creativity is called IP. | |||
| Pornography | Magazines, pictures, or movies that show naked people or sex in an open way. | |||
| SQL Injection | [18] | - | SQL injection is a code injection technique performed to attack data-driven applications to inject SQL statements for malicious intent. | |
| Spam | [19] | Spam Relay | Sending e-mails to a huge number of victims by hiding the source address of e-mails. | |
| Spam | Sending the same messages to a large number of Internet users. These inappropriate or irrelevant e-mails are sent on the Internet to a huge number of victims. | |||
| Remote to Local User | [20] | - | Man-in-the-middle attacks can take place here. | |
| Distributed Attacks | [19] | Backdoor Program | - | |
| Trojan Horse | A computer application or software that sends malicious emails or spam, or performs DDoS attacks. | |||
| Application Layer | [21] | - | It is very hard to defend, and vulnerabilities are always encountered here for complex user input. | |
| Compromised Key | [22] | - | Attacker uses stolen key to gain access to the secure system or transmission, which allows the user to decrypt the encrypted data being sent by someone or a system. | |
| Password Attacks | [23] | Dictionary | Dictionary attacks are used for decrypting the encrypted message. | |
| Login Brute Force | Mainly aims to get access to a website by applying the simplest method. It always involves trying several usernames and passwords again and again. | |||
| Hybrid | It is a combination of dictionary and brute force attacks. | |||
| Adversarial Attacks against IDS | [5] | Evasion | Attacker tries to change the intrusion pattern in order to deceive the IDRS. | |
| Overstimulation | Intruders try to feed the IDRS with a huge number of attacks pattern to enforce to generate many false alarms. | |||
| Poisoning | Attacker tries to inject a well-crafted pattern into the data, aiming to alter the data that are used to train and construct the detection algorithm. | |||
| Reverse Engineering | Adversary tries to access the internal processing of IDRS and stimulates the IDRS with a familiar attack signature. | |||
| Intrusion Solution | Intrusion Types | Description | Attack Examples |
|---|---|---|---|
| Firewall | External | It is a system designed to stop unauthorized access. | IP spoofing, eavesdropping, DOS, port scan, and fragmentation attacks. |
| Access Control | External | These are systems that control or limit illegal access to a system. | Unauthorized access, password attacks, dictionary attacks, rainbow table attacks, and sniffer attacks. |
| Cryptography | External | To stop the coding or decoding of secret messages. | Meet-in-the-middle attacks, brute force attacks, and birthday attacks. |
| IDS | Internal + External | A system or device that controls and monitors a network or system. | DOS, DDOS, user to root (U2R), port scanning, and flooding. |
| IPS | Internal + External | Network security appliances that monitor network and/or system activities for malicious activity. | ICMP storms, ping to death, SSL evasion, and SMTP mass mailing attacks. |
| IDPS | Internal + External | Also known as IPS | DOS and DDOS. |
| IRS | Internal + External | DOS, user to root, remote to local, and prob. |
| Types of IDS | Description | Pros | Cons |
|---|---|---|---|
| Host-Based | Host-based IDSs are installed on a specific machine such as a server and mobile devices that monitor the operating system’s audit information for any sign of intrusion. In addition, they detect which programs are accessing which part of the system or resources. |
|
|
| Network-Based | Network-based IDSs monitor network traffic and application protocol activity between any two computers for any type of intrusion. |
|
|
| Hybrid | This is combination of both HIDS and NIDS components using mobile agents and a combination of anomaly- and misuse-based approaches. A system log file checker is performed by the mobile agent traveling to each host, while the overall network can be checked by a central agent for the existence of anomalies. |
|
|
| Distributed | Various IDS (HIDS and NIDS) are combined by working as faraway sensors and constructing a report about intrusions. Later submits report to a centralized control, called distributed IDS. Uses remote sensors that can be host-based, network-based or even a combination of host- and network-based. |
|
|
| Domain | Ref | IRS | Underlying Detection Techniques | Description |
|---|---|---|---|---|
| IRS in Networks | [54] | NetSTAT | Misuse | To propose IRS, in which stream of audit data is matched with a stored signature of attacks descriptions for the evidence of the occurring attacks. |
| [55] | A-NIDS | Anomaly | To detect intrusion events that are previously unobserved, but for which the false alarm rate is high. | |
| [56] | AIDP | Anomaly | To propose AIDP in MANET for the detection and mitigation of DDoS attacks. | |
| [36] | IDAR | Hybrid | To provide a flexible response to attacks instead of a static response without isolating the effected node. | |
| [57] | A-NIDS using Fuzzy | Anomaly | To propose intelligent techniques with the help of machine learning such as fuzzy logic to prevent and classify network attacks. | |
| [35] | GIDP | Hybrid | To propose a fixed response approach to intrusions by isolating the intruding node. | |
| Network IRS | N/A | To compare intrusion severity and response cost, an assessment algorithm is proposed. |
| Attacks | Ref. | Example | Objectives | Affected Parameters | ||
|---|---|---|---|---|---|---|
| Confidentiality | Integrity | Availability | ||||
| Insider | [60] | Flooding attacks, user to root, and port scanning. | The authorized user tries to harm the network. | ✓ | ⨯ | ✓ |
| Flooding Attacks | [61] | DOS, DDOS, Direct and Indirect DOS, | Attackers try to flood or block a machine or network by sending invalid information. | ⨯ | ⨯ | ✓ |
| DOS | [61,62] | Ping of death, Buffer overflow, ICMP flood, Smurf, UDP flood, SYN flood. | Attackers try to make resources unavailable to the intended users. | ⨯ | ⨯ | ✓ |
| Port Scanning | [63] | TCP scanning, UDP Scanning, SYN scanning, FIN scanning, ACK scanning, and Window scanning. | Attackers try to find the open port, closed ports, and filtered port in a list of open ports for attacking services running on these ports. | ⨯ | ⨯ | ✓ |
| Application Layer Attacks or Host based attacks | [62] | Spamming, race condition attacks, buffer overflow attacks, and man-in-the-middle attacks. | These attacks target the application layer and cause faults in the application or in a server's operating system. | ⨯ | ✓ | ✓ |
| Passive attacks | [35,64] | Eavesdropping, traffic analysis, and location disclosure. | The intention of passive attackers is to disturb the performance and operation of the network and locate valuable information. | ✓ | ✓ | ⨯ |
| Active attacks | [35,64] | Routing attacks and malicious traffic dropping. | Active attacks interrupt the network operation by introducing malicious code, modifying information, and causing damage to the entire network, which results in network performance degradation. | ✓ | ✓ | ✓ |
| Routing Attacks | [65] | Spoofing attacks (IP and URL spoofing), rushing, gray hole, black hole, Cybil, man-in-the-middle attacks, and sleep deprivation. | Routing attacks aim to modify the routing protocol in mobile ad hoc network (MANET). | ✓ | ✓ | ✓ |
| Code Red Attacks | [66] | To exploit a known vulnerability in Microsoft IIS servers. | ⨯ | ✓ | ✓ | |
| Side Channel Attack | [23] | To extract confidential information from systems by exploiting computational characteristics. | ✓ | ✓ | ✓ | |
| Covert Channel Attack | [67] | To extract secret information by using a covert channel. | ✓ | ✓ | ✓ | |
| Adversarial Attacks Against IDS | [59] | These attacks disable the IDRS and affect the detection accuracy of IDS by modifying their internal processing and disrupting the functionality of the detection algorithm. | ⨯ | ⨯ | ✓ | |
| Responses | Description |
|---|---|
| Report/Alarm generation | An alarm or report is generated with the detection of an intrusion attack. |
| Isolation | Completely and immediately isolates the affected node. |
| Relocation | Relocates the affected server by allotting a new different address. |
| No Punishment | In some cases, when the response causes a blip in the network performance, it ignores the attack. |
| Service Denial | Upon detection of an intrusion, the nodes stop providing services (not sending or receiving data). |
| User Account Locking | Once the user accounts are changed, the intruders should be locked out. |
| Remote Locking | In this response the affected server is blocked from remote areas. |
| IP Address Blocking | Once the intrusion is detected, the IP address of that network node should be blocked. |
| Network Disconnection | The affected node is disconnected from the network. |
| Attack Port Disabling | The port that may be the cause of an intrusion is disabled. |
| Backup Creation | If there is an attack detected, a backup of the infected device should be created. |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Anwar, S.; Mohamad Zain, J.; Zolkipli, M.F.; Inayat, Z.; Khan, S.; Anthony, B.; Chang, V. From Intrusion Detection to an Intrusion Response System: Fundamentals, Requirements, and Future Directions. Algorithms 2017, 10, 39. https://doi.org/10.3390/a10020039
Anwar S, Mohamad Zain J, Zolkipli MF, Inayat Z, Khan S, Anthony B, Chang V. From Intrusion Detection to an Intrusion Response System: Fundamentals, Requirements, and Future Directions. Algorithms. 2017; 10(2):39. https://doi.org/10.3390/a10020039
Chicago/Turabian StyleAnwar, Shahid, Jasni Mohamad Zain, Mohamad Fadli Zolkipli, Zakira Inayat, Suleman Khan, Bokolo Anthony, and Victor Chang. 2017. "From Intrusion Detection to an Intrusion Response System: Fundamentals, Requirements, and Future Directions" Algorithms 10, no. 2: 39. https://doi.org/10.3390/a10020039







