1. Introduction
The internet of things is now applied into many parts of our daily life. Smart meters are one of these. The European Commission has formulated the goal to provide 80% of all households with smart electricity meters by the year 2020 [
1]. As a smart meter can report its measurements periodically to the utility supplier instantaneously, the utility supplier can dynamically change the supplement according to the reported data. With more and more smart meters applied, authentication and key establishment have become an important issue in the smart grid area. According to Sanjab et al. (2016) [
2], “a robust authentication protocol is needed while communicating between smart grid parties.” According to the Report on Workshop on Security & Privacy in IoT of Europe (2016) [
3], “identification and authentication of end-devices, gateways and servers as very first requirement.” is considered to help manage scalability, evolutivity and risk assessment of the overall IoT system. Authentication enables the parties in the smart grid to authenticate each other and establish a shared key. But as privacy becomes a concern, people start trying to find ways that smart grid parties could authenticate each other without leaking their identity to adversaries.
First, as a smart meter is installed beside the house of inhabitants, as stated in [
4], “this malicious attacker might be able to forge sensed data such as the amount of electricity usage at this house before sending these forged data back to the corresponding service server.” Passive attacks are easily launched by an attacker, such as eavesdrop attack, and some other attacks launched by the attackers. Authentication and encryption methods should be applied in this scenario.
Second, electricity usage naturally includes personal information of the inhabitants, according to the electricity consumption, it is easy to judge if inhabitants are at home or not, and with fine-grained electricity consumption reporting instantly, privacy-sensitive information, regarding which appliances are active, can be obtained. Also, by data mining or static methods, according to the electricity consumption, the status and income of the inhabitants may be revealed, so anonymous authentication is needed; in FAuth, the identity of the smart meter is encrypted before sending.
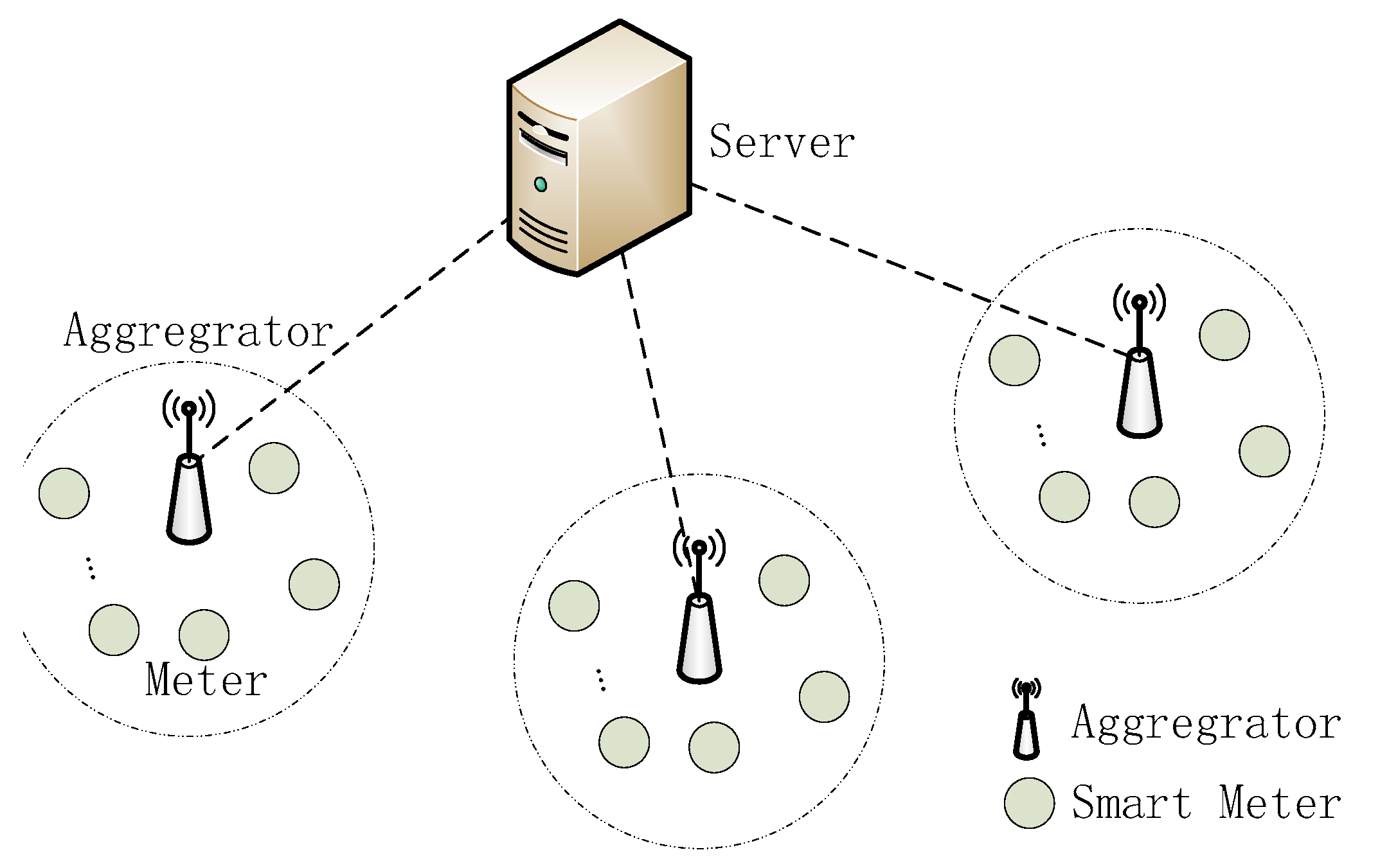
Third, as smart meters have constrained computability compared to aggregators, it is necessary to try to lower the computation cost at the smart meter side; in FAuth, the computation cost at the smart meter side is the lowest compared to other schemes.
So, in this paper, we proposed an anonymous authentication scheme based on bilinear maps and the computational Diffie–Hellman problem: FAuth, which totally meets the above three requirements as stated. The contributions of this paper include the following three points:
This paper is organized as follows: We discuss the related works in
Section 2. Some preliminary knowledge is described in
Section 3. A review of Odelu’s scheme is presented in
Section 4. The security limitations of Odelu’s scheme are discussed at
Section 5. The scheme: FAuth is proposed in
Section 6. We conduct two separate security analyses using BAN logic and random oracle model in
Section 7 and
Section 8. We provide a comparison with the related schemes in
Section 9. A brief introduction of the I3RES Project is given in
Section 10. We conclude the paper with a summary of the contributions in
Section 11.
2. Related Work
Tsai-Lo and Nai-Wei Lo proposed an authentication scheme based on bilinear map, and the computational Diffie–Hellman problem [
4]. The advantage of their scheme is that a smart meter can be quickly authenticated without involving the trust anchor because of the two identity based cryptosystems. Odelu et al. (2016) provide a scheme with security functionalities, including strong credentials’ privacy and SK-security under the CK-adversary model [
5]. Their scheme provided a variety of security functionalities, and reduced computational costs for both the smart meter and service provider. Xia and Wang proposed a key distribution scheme for smart grid network [
6]. They used a trusted third party which can conduct key revocation, and the third party can be easily duplicated in case power outages occur. Jo et al. (2016) proposed efficient and privacy-preserving protocols for a smart grid in [
7]. The proposed protocols were shown to be robust against attacks of data collection unit (DCU) compromise attacks. Further, in their protocol, the response of messages were more efficient by the adoption of the distributed verification method.
Zhang et al. (2017) proposed a new, efficient, certificate-less, generalized signcryption (CLGSC) scheme, and a lightweight and robust security-aware (LRSA) D2D-assist data transmission protocol that was proposed based on CLGSC [
8]. Their security analysis demonstrated that the LRSA protocol can achieve data confidentiality and integrity, mutual authentication, contextual privacy, anonymity, and so on. Their experimental results show that the LRSA protocol outperforms the existing schemes in terms of computational and communication overhead. Liu et al. (2014) proposed a certificate-less signature scheme based on bilinear pairings [
9]. And based on this scheme, they proposed two certificate-less remote anonymous schemes for wireless body area networks. A client could anonymously be authenticated and establish a key with the application provider. He et al. (2016) provided an improved scheme where the application provider does not have to store any information for the authenticating users [
10]. Li et al. (2013) also proposed an authentication scheme based on bilinear pairings [
11]. Tsai-Lo and Lo proposed a new anonymous authentication scheme based on nonce and bilinear pairing [
12], which supports mutual authentication, key exchange, user anonymity, and user untraceability. It is claimed that their scheme withstands all major security threats and meets general security requirements. In addition, no verification table is required to be implemented at service providers or the trusted SCG service.
He et al. (2017) proposed a data aggregation scheme [
13] that can thwart internal attacks for the smart grid environment. They claimed their scheme is provably secure and can meet the security requirements, and incurs lower communication costs.
H. Xiong briefly described the work of [
9] in [
14], and according to their opinion, certificate managements, scalability, and forward security are the three parts that can be improved in the scheme of the work of [
9]. In his scheme, only registered users can authenticate each other and build a shared key, besides, this shared key is only known by the two registered users and the network manager would not know this shared key. Also, according to the public information transmitted between the two users, an adversary is unable to learn this shared key. However, in this scheme, the server does not check the validity of incoming users. Li and J. Hong proposed a modified BDCPS scheme [
15], which is an efficient certificate-less access control for wireless body area networks. In this scheme, every user first generates a public key pair (
), and then registers at a key generating center (KGC), to get a partial private key
. After the user gets this partial private key, he can generate his public key pair (
). As only registered user could generate this public key pair, this public key pair can be used as a measure to test if a user is legal or not, as only the public key is transferred, so the identity of the user is hidden.
Liu et al. (2016) proposed an authentication scheme [
16] which could well protect the identity and privacy of the user, while the scheme is very cost-effective compared to [
9]. Islam and Khan proposed a partial public key method [
17], where a user registers at the server several times in order to get more than one authentication keys, then the user uses different keys for authentication to achieve anonymity. He et al. (2015) applied the partial key concept to the vehicular ad hoc networks, and proposed an efficient identity-based privacy preserving authentication scheme, and their scheme enables batch verification of multiple messages [
18]. Further, they applied a similar method into public auditing in cloud-based body area networks in [
19], by D. He, S. Zeadally, and L. Wu.
Porambage et al. (2014) proposed a pervasive authentication protocol and key establishment scheme [
20], their scheme is also based on a partial public key method. But in their scheme,
is a fixed value, so the user in this scheme could be tracked by
. The registration phase of FAuth is similar to those of [
13,
20].
Zhang et al. (2014) proposed a scheme based on ECC public key infrastructure [
21], but they do not take into account the anonymity of the user, as the user names are sent directly. In [
22], Tu et al. (2015) improved the scheme [
21], but the username is sent without processing, too. Odelu et al. (2015) [
23] proposed an authentication scheme between two users, with the help of a server node, the scheme is also based on a partial public key by elliptic curve cryptography (ECC). They also proposed a similar authentication scheme between two users, but their scheme does not need there to be a trusted server to help the two users to finish the authentication process, as the scheme uses the ECC based El-Gammal type signature [
24].
The scheme in [
25] is the first one that defines a formal model to capture the feature of user untraceability, and that highlights the damaging threat of de-synchronization attacks on privacy-preserving two-factor authentication schemes.
The schemes in [
26,
27,
28,
29], and [
30] use elliptic curve cryptography (ECC) to generate a shared key with the server. The scheme in [
30] suffers from impersonation attacks in the registration phase, offline password guessing attacks in the login phase, and offline password guessing attacks in the password change phase. The schemes in [
31,
32] provide a lightweight scheme based on ECC, but they do not protect the privacy of the user, since the user names are sent transparently. Huang et al. (2015) provides an ECC-based authentication scheme between user and server [
33], while their scheme is found to be vulnerable to inner side impersonate attacks by [
34] by Chaudhry et al. (2016). Li et al. (2015) [
35] provide an authentication between user and cloud server, as they use a symmetric key as a way of authentication, and an asymmetric key to establish the shared key, but the
of a user is transferred transparently, so a user could be tracked. The method in [
11] is similar to [
35], only their shared key is based on a symmetric key, and the scheme in [
11] suffers from inner side user attacks, as they shared a same key. Jiang et al. (2016) built their scheme based on the knowledge of chaotic maps [
27].
The proposed scheme: FAuth is an improvement of the schemes of [
4,
5,
36], which specially focused on the smart meter authentication problem. The second scheme of [
36] could not provide smart meter anonymity at the authentication phase, and suffers from “unknown key share attacks” according to [
4]. According to [
5], scheme [
4] fails to protect the smart secret credentials if the ephemeral secret is revealed as an adversary. The registration manner of smart meters and aggregators in the proposed scheme are changed to provide better security endurance, compared to [
5]; besides, a detailed computation of computation and communication costs were conducted, and all the results show the proposed scheme is more suitable for smart grid environments.
8. Security Analysis Using Random Oracle
In this section, a security proof of random oracle is provided, based on the model of [
5,
30]. In order to simplify, it is supposed that only two entities are in FAuth: a smart meter
, and an aggregator
.
While each entity has many instances, using
stands for the
ith smart meter, and
for the
jth aggregator.
can be used as
or
. An instance is considered as an oracle, and a simulator is used to answer the input message. Under this model,
is considered as a participant or an oracle [
5]. To crack the scheme, an adversary could use a simulator to ask for the following queries:
Send (): this oracle receives a message, , from an entity, and answers this query with the corresponding message.
Execute (): this query simulates the passive attack, and the adversary, A, can learn the message transmitted between .
ReveralSerrsion (): the adversary A can learn the session specific information, and the answer of this query doesn’t include the private key of or .
ReveralSk (): the adversary, A, can learn the session key of the oracle .
Corrupt (): the adversary, A, can learn the private key of the entity .
Expire (): this query erases the session key of a completed session held by the oracle .
Test (): returns a session key or a random key, only before any of the ReveralSerrsion (), ReveralSk () and Corrupt () have been asked.
Lemma 1 (Difference Lemma). Let represent the events defined in some probability distribution. If , we have .
Theorem 1. Let A be a t polynomial time adversary against the semantic security, and make no more than send queries, execute queries, and hash queries. The advantage of A in our scheme is given by , where , and is the time for multiplication operation in group.
In order to prove Theorem 1, we introduce four games, , and the first game represents the real attack, is the event that in Game the adversary correctly guesses the result of the Test ().
Game
: This game simulates the real scheme under random oracle, according to sematic security, and it is clear that:
Game
: This game simulates all the oracles,
stores all the answers to hash queries, if the hash query is asked by adersary, then the answer is sotred in
, and
stores the transcripts of all the messages, all oracles are demonstrated in in
Table 12 and
Table 13, and an adversary is unable to distinguish between the two games:
Game : This game simulates all the oracles in Game , but two kinds of collisions are trying to be avoided here, and the results are obtained by the birthday paradox:
Random numbers of and should be different in different sessions, and the probability is bounded by: .
The probability of a hash result collision is bounded by , where is the length of a result of a hash function.
These two kinds of collisions should be avoided, so the two games differ by:
Game : This game simulates the situation where an adversary may guess the result of a hash function and without asking the random oracle.
For a Send , , ) query, has to check if belongs to the transcripts, and check if ; if either of them fails, terminates the session, the probability is bounded by ; for the checking of if , and the probability is bounded by , so for a Send , , ) query, the probability is bounded by . For a Send (, , ) or Send (, , ) query, the probability is bounded by , too.
This game and the previous one are indistinguishable unless the smart meter and aggregator reject valid authentication information:
Game
: The CDH problem is brought in this game. In order to win the game,
A should ask the query
and broke the CDH problem; the adversary’s goal is to compute the session key by asking
Execute (
,) query and the corresponding hash query, and the adversary can also get the transcripts. The proposed scheme fits the SK-security [
5] in the following four cases.
Case 1 RevealSession () and RevealSession ():
Adversary can get the session state information of , and for the matching instance . Where and .
Case 2 RevealSession () and Corrupt ():
Adversary can get the session state information of , the private key for the matching instance without session information.
Case 3 Corrupt () and RevealSession ():
Adversary can get the private key of , but could not get the session information of , and can get for the matching instance .
Case 4 Corrupt () and Corrupt ():
Adversary can get the private key of , but could not get the session information, and can get the private key for the matching instance without session information, too.
However, in all the above four cases, adversary
A is unable to solve the CDH problem given the information it gets in the four cases. The shared key
sk can be gotten with the probability
in the list of
,
be the running time in all, then it is not hard to get:
Until now, through the games and using the lemma 1, theorem 1 is proven.