1. Introduction
With the increase in network traffic through the introduction of devices such as remote sensors, intelligent devices, self-drive Global Positioning System (GPS)-connected vehicles, 5G data transmission, smartphones, and cloud computing, the size of the internet is rapidly increasing [
1]. There are approximately 4.66 billion internet users globally, which amounts to 59.5% of the global population. Similarly, approximately 53.6% of the global population are social media users, while smartphone users constitute 66.6%. Overall, the total population connected to the digital world was approximately 7.83 billion in 2021, with an anticipated annual growth of 316 million users. The expected internet user growth is alarming, especially when it comes to internet security and the integrity of Cyber–Physical Systems (CPS) [
2]. Although the internet helps with different aspects of life and makes life more convenient, it creates many security risks. A typical example of these risks is malicious attacks such as DoS attacks, deception attacks, and reply attacks, all of which are types of cyber-attack. Their objectives and methods are different. DoS attacks aim to disrupt availability and deception attacks involve manipulation and trickery, whereas replay attacks focus on intercepting and reusing valid data to gain unauthorized access or manipulate systems. In addition, Denial-of-Service (DoS) attacks are related to breaches in user privacy and compromised security [
3].
Generally, two forms of DoS attack are troubling, DoS and DDoS (DDoS). Typically, DDoS attacks occur through linked devices from numerous locations. The attack can cause unusual activity that interrupts the regular traffic of specific servers, services, and networks through data bombardment from nearby infrastructure. This unusual activity creates tremendous continuous service requests to the servers and networks, making it difficult to identify a trustworthy source. For example, in the Internet of things (IoT) environment, an attacker can quickly attack thousands of devices on a large scale [
4,
5,
6,
7]. For a practical CPS communication network, time delay is an important issue. A durable, adaptive DSC based on the dwell-time strategy and switching perspective was developed for a time-delayed switched nonlinear CPS under hybrid attacks on sensor measurements [
8]. To investigate the stochastic characteristics of end-to-end network-induced time delay in a time-critical smart substation CPS context, the components of a smart substation CPS, such as data flow, communication network, and intelligent electronic devices (IEDs), are modelled [
9]. In the case of time delay attacks (TDAs), which exploit communication channel weaknesses to cause potentially serious harm to a system, many of the approaches suggested for TDA detection have been evaluated exclusively offline and under strict assumptions of building a practical method for dealing with real-world problems [
10]. DDoS attacks can be application layer attacks, protocol attacks, and volume-based attacks, and detecting them is more challenging on high-speed networks (HSNs). In HSNs, which consist of optical fiber networks with data rates of 100 Gbs, the context switching of network processing due to a DoS attack can reduce network speed due to a packet associated with a system call and a copy of the transition propagating across the network [
11].
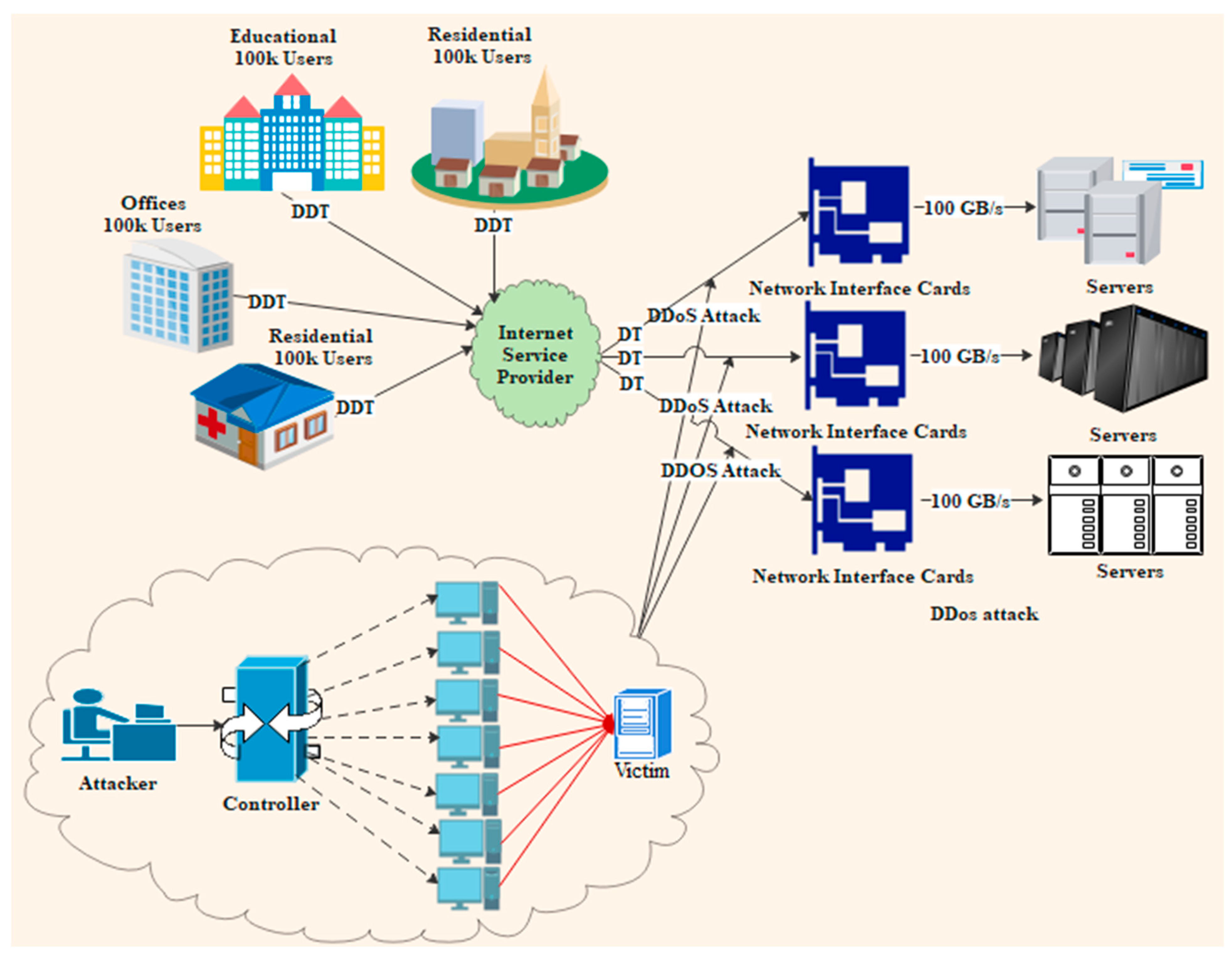
Since the speed of data processing on networks has grown, detecting DDoS attacks has become more complicated, raising security risks.
Figure 1 illustrates a scenario of a DDoS attack occurring in a high-speed network. Additionally, researchers face enormous challenges in addressing DDoS attacks due to the network speed and different types of data entering the network [
12]. Several DDoS attack detection techniques have been proposed, with two common types of detection, namely misuse detection and abnormal detection [
13,
14]. Both detection systems have limitations regarding the parameters selected for detecting network patterns. The advantage of misuse detection is that it provides a high accuracy; however, it requires complete information on the network. In contrast, prior knowledge of the network is not acquired in abnormal detection, but this approach does not provide the high accuracy offered by misuse detection [
15].
In recent years, there have been several reviews in the literature of DoS attacks. For example, the authors of [
16] presented the taxonomy of low-rate DoS attacks based on a three-layer modus operandi. The review included slow rate, service queue, and Quality of Service (QOS) attacks and described the various detection approaches against eight low-rate DoS attacks. However, the paper did not mention high-speed Network DDoS attacks. The authors of [
17] presented cutting-edge defense techniques that help to prevent DDoS attacks and reduce the damage to user information. The review elaborates on the prevention techniques for IoT and Software-Defined Network devices. Ironically, DDoS attacks in a high-speed network scenario are not discussed. In [
18], the authors described a defense mechanism against DDoS attacks, including the attack response, traffic classification, and attack detection, but not the network details. Motivated by the above observations, the aims of this review are to present:
A comprehensive review of the types of DDoS attacks, detection, and prevention techniques;
A survey of recent DDoS attacks on high-speed networks;
An organized taxonomy of irregular traffic detection patterns in high-speed networks;
A comprehensive investigation of the conventional weaknesses and strengths of DDoS detection techniques.
The paper’s road map is as follows;
Section 2 elaborates on the research motive and background of high-speed data networks and illustrates the taxonomy of high-speed networks. The third section presents DDoS attack detection and prevention. The fourth section discusses the current state-of-the-art of high-speed network and the limitation of a DDoS attack. The fifth section explains the issues and challenges in high-speed data monitoring and analyzing networks for DDoS attack detection. The last section elaborates on the paper’s conclusion and future direction. The acronyms used in this paper are noted at the end of the paper.
2. Background of High-Speed Network
The development of network speed can be traced back to the 1960s, when the first computer networks were created. These networks allowed numerous computers to share resources, such as printers and data. Ethernet technology was invented in the 1980s, allowing computers to communicate at speeds of up to 10 Mbps [
19]. This was followed in the 1990s by the creation of Fast Ethernet, which boosted this speed to 100 Mbps [
20]. Gigabit Ethernet was created in the early 2000s, allowing for up to 1 Gbps rates. This was followed by 10 Gigabit Ethernet, which offers up to 10 Gbps rates [
21]. Fast data transfer rates with a low latency, high bandwidth, and reliable and consistent performance are called high-speed networks (HSN). HSN technologies are being developed to enable even quicker and more efficient communication between devices. Among these technologies are 40 Gigabit Ethernet, 100 Gigabit Ethernet, and InfiniBand [
22]. A Cisco Report predicted that the internet protocol may cross 4.3 zettabytes in 2023, which is 1879 exabytes higher than 2018 [
3]. The variety of devices connected to the internet leads to massive data transfer on the network with a high velocity, which fulfils the critical demand of big data [
18]. Smart devices face many security threats due to their internet connectivity and the various applications running on high-speed networks [
23]. A high-speed communication network has a high bandwidth and low-latency communication. A data stream analysis is necessary for high-speed real-time data from many resources connected to the network [
24]. According to [
25], packet speed categories can be classified as shown in
Table 1, while
Table 2 shows the traffic types with their characteristics.
The vast amount of heterogeneous data gathered from network devices poses challenges in monitoring and detecting irregularities in the network [
26]. The current network traffic supports IoT infrastructure with numerous devices, and big data stored in the cloud [
27]. Mobile cloud is an emerging technology involved in different domains to reduce the mobile cloud (MC) limitations using cloud services due to connected wireless media [
28]. Due to minimal storage resources, the data gathered from various smart devices is stored and processed in the cloud [
29]. Cloud computing provides information technology services at various locations. For example, Mobile Cloud Computing (MCC) offers customer service on board [
30]. Mobile health applications enable access to monitoring health activity electronically with the help of cloud services [
31,
32]. Nowadays, cloud service providers, such as Amazon, Google Cloud, Microsoft, IBM, Oracle, and many others, adopt big data technologies. The cloud needs immediate processing software for fast data processing and monitoring [
33].
2.1. Architecture of High-Speed Network
A high-speed network enables fast and effective communication between computers and the other devices possible. Applications for these networks include data centers, telecommunications, and high-performance computing.
The proposed HSN architecture is presented in
Figure 2. The architecture of a high-speed network typically consists of the following components: The Network Interface Card (NIC), which is a hardware component that connects the computer to the network server. The classification of its speed as bits or bytes is discussed above in
Table 1. It is responsible for transmitting and receiving data between the computer and the network. The hardware that joins various computers on a network is known as a switch. It makes data transmission between the computers on the network possible. Hardware devices connect to multiple networks via a router. Fiber Optic Cable: High-speed networks typically use fiber-optic cables for transmitting data. These cables can transmit data at very high speeds over long distances. Network Operating System (NOS): The NOS is a software component that manages the operation of the network. It contains network resources, such as file sharing and printing. Another high-concern application for high-speed network is in the automotive industry. The automotive industry relies heavily on the internet, especially for procedures such as assuming two cars are going parallel. The vehicles may collide if they cannot be connected to each other. Additionally, attackers can target the vehicle’s data and hack its information. In advanced emerging auto drive, cars have several modules, such as in-vehicle networks, engine control units, body control modules, and smartphone integration modules, that provide the vehicle safety functionality [
34,
35]. The modules for DDoS detection must be analyzed due to the fast online data processing.
Anomaly detection is a severe issue in monitoring the services of patient due to various factors, such as patient conditions, machine error, and human ambiguity, particularly concerning disease outbreaks. For instance, many older people require routine check-ups, but cannot move in crowded places due to COVID-19 [
36]. Online medical check-up applications in this era can be immensely helpful for patients with critical conditions, as they can monitor themselves from a mobile location [
37]. Patient records containing essential information, such as name, age, gender, sugar level, and blood information, must be accurately monitored [
38]. Real-time anomaly detection plays a vital role in tracking patients’ services and in detecting anomalies promptly. Therefore, a High-speed Network architecture can be instrumental in quickly responding to patients’ queries, as a large number of requests come in remotely [
39].
2.2. High-Speed Network Evaluation Factors
Accuracy and speed are valuable parameters for intrusion detection and prevention systems in high-speed networks. As numerous attacks continue to emerge, accurately monitoring vulnerability using regular expression is not straightforward [
40]. The taxonomy of high-speed network evaluation factors is shown in
Figure 3. The proposed taxonomy is categorically divided into accuracy evaluation, traffic monitoring, and resource sharing.
An accuracy evaluation of a network depends on various factors that require different assessment options, such as knowledge of the network, scalability, minimum packet drop and receive ratio, and authentication of the source and destination, as well as fault and error analyses [
41]. Mainly, these evaluations are categorized into processes, impact, outcomes, and result. Traffic monitoring, also known as network monitoring, involves the processing and analyzing of the incoming and outgoing network data using particular hardware and/or software [
42]. At the basic level, different types of tools are used to monitor the network, and various parameters are checked, including information on the packet size, type of traffic (voice/I.P., control traffic, and web traffic, etc.), traffic source, and packet processing speed. During this monitoring, the data uploaded and downloaded should be displayed to the network administrator to necessitate advanced reporting. Resource sharing refers to the sharing of library resources by specific participating libraries based on cooperation. Resource sharing means making one library’s collections available to consumers. Resource sharing contains technical capabilities, end-to-end time, stability of the required resources, expertise in traffic congestion handling, and the policies of routing and switching vital to obtaining that aim.
High-speed networks are vulnerable to various security threats and attacks, compromising network resources’ confidentiality, integrity, and availability. Here are some examples of high-speed network attacks: Denial-of-Service (DoS) attacks: high-speed networks are particularly susceptible to DoS attacks, which flood the network with excessive traffic, causing it to slow down or even crash. Man-in-the-middle (MITM) attacks: in MITM attacks, an attacker intercepts the communication between two parties on the network and can eavesdrop on or modify the transmitted data. Packet sniffing: an attacker can use a packet sniffer tool to capture and analyze the network traffic, including sensitive data such as passwords, usernames, and credit card information. Malware and virus attacks: malware and viruses can infect network devices and spread quickly across high-speed networks, causing significant damage. Insider threats: high-speed networks are also vulnerable to insider threats, such as employees with malicious intent who can access confidential information and compromise network security. To protect high-speed networks from these vulnerabilities, there is a need to implement automatic security measures such as firewalls, intrusion detection and prevention systems, encryption, access controls, and regular security audits and updates [
43].
4. DDOS Attack Detection in High-Speed Network
An open-source Intrusion Detection System, Snort and Suricata [
78], explains how to evaluate the drop rates and accuracy rates in a 100 Gbps network using their comparison and benchmarks [
79]. This evaluation includes the usage of system resources, packet processing speed, packet drop ratio, and detection accuracy. However, a shortcoming of this study is that it does not consider the extensive data on the network. Another model proposed by [
80], the Very Long Short-Term Memory (VLSTM) learning model, deals with the challenges of high dimensionality and unfairness. Its performance in experiments has resulted in using the UNSW-NB15 open dataset. A study presented reconstruction loss, classification loss, and divergence loss. However, anomaly detection tasks are still challenging for imbalanced data.
An Extended Barkley packet filtering (eBPF) and express data path are presented by M. A. Vieira [
81] to introduce new technology for packet filtering and provide an example of a standard procedure of these technologies. The XDP program is written in the C or P4 languages, and the instructions are processed through the kernel and other programmable devices, such as a smart network interface card. This work mainly focuses on network monitoring, traffic analysis, load balancing, and system profiling. Moreover, the authors dealt with the high speed of network data but did not address the packet drop ratio. In given
Table 5, the studies of the recent five years are categorized based on different parameters such as year, article reference, main features, advantages, and weaknesses.
The researchers in [
84] processed a massive amount of network traffic with a verification technique that checked the reliability based on the classifier’s outcomes. The Big-Flow classification model is adjusted once suspect packets are found. The focus of this study is to deal with the network traffic dataset, but it does not consider the packet drop ratio. According to [
59], the DDoS detection schema has numerous traffic functions. This scheme generates precise per-subnet alarms implemented in the data plane without external controllers, allowing for tight control loops. The findings include accurate detection relying on a realistic attack using accessible traces. It deals with incoming flows and the packet symmetry ratio observed per secured sub-network. The express data path is a suitable framework for DDoS protection and creating a novel scheme to prevent cyber threats. Nevertheless, it features packet rates of 1–2 Mpps for 10 Gigabit links not more than 10 Giga bit.
Table 6 shows the comparison of an irregular traffic pattern.
A Linux subsystem is capable of tracking containerized user-space programs for Inter ledger connectors, with the ability to control the software stack in development [
43]. The tests investigated and evaluated the tool landscape developed to assist eBPF in this project. This project does not show the end-to-end view of a distributed system. In addition, HTTPS encrypted traffic is analyzed to determine the user’s operating system and track the user’s local explorer and other methods, resulting in a 20,000 dataset example with a 96.06% classification accuracy [
96]. The traffic analysis technique, which employs SSL/TLS, is a powerful method. The attacker can use statistics to identify the user’s operating system.
A data distributed control system (DDCS) can be used for data-driven cyber security, social, and internet traffic analyses, cyber security data collection, cyber security feature engineering, and simulation [
85]. The DDCS shows a strong link among data, models, and methodology while reviewing the key recent works in Twitter spam detection and I.P. traffic classification. However, this work does not mention high-speed data.
The research in [
80] suggested a new malicious classification scheme based on the Long Short-Term Memory (LSTM) model. Data annotation for effective traffic classification can result in network loops and bandwidth issues. The selection of LSTM makes it accurate. In a DDoS, the detection schema has numerous traffic functions [
59]. These features are known as formal DoS parameters, such as the arriving flow pattern and packet symmetry levels observed per secured sub-network. In [
97], a full-packet capture in (FPC-NM) systems in 20 Gb/s was developed and deployed. A nanosecond timestamp was used in the FPC-NM system, significantly boosting the accuracy of a security incident retrospective analysis.
Implementing the FPC-NM system achieves a 17 Gb/s throughput with a connection of 160,000, experiencing zero packet loss. These parameters encompass packet reception, nanosecond timestamping, load balancing, preprocessing packets, application layer protocol analysis, data packet storage, and log management. By utilizing LZ4 compression, the system achieves real-time compression and storage efficiency at 10 Gb/s, but up to 40 Gb/s. However, it does not support 70 Gbps and 100 Gbps. As industry and research institutions are installing 100 Gbps networks to meet data transfer demands, high-speed networks are becoming more common, leading to significant technical challenges. An Intrusion Detection System cannot efficiently handle network activities with high rates of traffic monitoring and packet drop ratios, which directly affects the detection accuracy. This paper [
87] provides a detailed explanation of the open-source IDS, namely, Snort and Suricata, with comparative parameters in a 100 Gb/s network.
A low-rate DDoS attack detection method (LDDM) using a multidimensional sketch structure and network flow measuring allows for a reduction in the data storage cast and improves the detection accuracy [
65]. The measurements depend on the daubechies four wavelets transform to calculate each sketch’s energy percentage. This approach differentiates between the regular and attack traffic. The LDDM is used to evaluate low-rate DDoS attack datasets, but a high-rate DDoS attack is not considered.
Figure 6 shows different irregular traffic pattern detection.
The architecture in [
98] allows for network operators to estimate the flow size of encrypted data at multi-Gbps line rates using samples and sketching mechanisms. It also helps in understanding the behavior of VPN-buffered traffic. The implementation shows a 99% accuracy of the service provider on 6000 tracks for three key factors. Evaluation studies depend on the track time and starting point, achieving more than a 90% precision for the content classification of a given service provider in the best case. The examiner presents the time path’s performance (XDP). eBPF is used for XDP to process incoming traffic before allocating kernel data structures, which improves the performance. The second case study uses eBPF to set up socket-level application-specific packet-filtering options. To eliminate errors and produce a custom binary for a specific network function, Packet-Mill boosts the throughput (up to 36.4 Gb/s—70%) and reduces the latency (up to 101 Gb/s—28%) without continuing unnecessary packet processing at 100 Gb/s. However, new packets arrive 10 times faster than main memory access times while utilizing only one processor core [
91]. Apache storm used the Netty communication component [
98], a TCP/IP protocol stack applied for an asynchronous server, and a client framework that decreased efficiency due to context switching and memory copying. It increased the IP over the InfiniBand communication mode on the CPU load. With the aid of remote direct memory access (RDMA) technology, the scheme implementation can reach up to five times faster than IPoIB and ten times faster than Gigabit Ethernet when tested on Mellanox QDR Cards (40 Gb/s). Additionally, this approach considerably reduces the CPU burden and boosts the system throughput.
Comma-separated values (CSV) [
97] are a frequently used data interchange format. Concerning format, all industries’ potent databases and stream processing of frameworks have utilized CSV as an input. The speed of input or output hardware poses significant challenges due to advanced input or output gadgets such as InfiniBand NICs and NVMe SSDs, with transfer rates of 100 Gb/s and higher. This article aims to increase the input speed of CSV with the help of graphics processing unit GPUs. A new parsing strategy is created that simplifies the control flow, while correctly handling context-sensitive CSV features such as quotes. In
Table 7, the articles have been studied and categorized based on their main features, advantages, and drawbacks. This section defines the thematic taxonomy of the characterization and classification of the irregular traffic pattern schemes on high-speed data networks, in order to achieve the following objectives: end-to-end time, packet drop, packet delay time, scalability, packet processing speed, and detection accuracy. The stated studies are categorized based on six characteristics: (i) detection techniques, (ii) traffic monitoring, (iii) NICs, (iv) traffic flow, (v) traffic filtering, and (vi) objective function.
Network traffic monitoring is a task to ensure that the operation of a network performs smoothly. When any unusual packet comes on the network, the Network Traffic Monitoring Tool (NTMT) [
105] captures that packet. Generally, NTMT observes all incoming and outgoing packets on the network. Detection accuracy implies the agreement between the actual and detection values. The exact value is unknown in several cases, but is compared with the standard. Accuracy is a ratio of the nearest value to the real value, which is the result. Scalability is a characteristic of a system, model, or function that elaborates on the ability to manage the workload. In the scalability test, many parameters are included, such as throughput, memory usage, CPU usage, network usage, and response time. Delay time is the time between the source signal and its echo. The most uncomplicated delay effect is a single repeat. The minimum delay is counted as 30 and 100 ms to create a slap-back echo, while longer delay times produce a more distant echo.
5. Issues and Challenges
This section explains the open research issues and challenges concerning HSNs. HSN issues are characterized based on factors such as data processing, traffic monitoring, packet filtering, traffic filtering, packet drop, response time, and packet size, as presented in
Figure 7. Moreover,
Table 8 shows the types of DDoS attacks with respect to the different parameters in high-speed networks, as highlighted in
Figure 7.
Table 8 comprises four horizontal sections (year, reference, DDoS attack, and network issues), and the existing works are stated vertically. The existing literature is presented based on publication year in the first two columns. DDoS attacks are generally categorized into three types: application-layer attacks, volume-based attacks, and protocol attacks. In this section, a detailed explanation is provided by dividing the existing literature with respect to the DDoS attack categorization [
106].
Application-layer attacks occur at the seventh layer of the Open Systems Interconnection (OSI) model. First, an attacker establishes a connection with the target. After establishing a link, the attacker exploits the resources to jam the traffic by inundating the system with excessive requests. This scenario exemplifies HTTP floods and Domain Name System floods [
107]. Volume-based attacks are launched against individual targets, and commonly target service providers (SPs). The attacker monopolizes the network’s bandwidth and inundates the server with a barrage of packets to overwhelm it. Examples include TCP floods and UDP flood attacks [
56]. Protocol attacks involve sending a flood of traffic with false data to the server, causing data overflow, server crashes, and rendering the resources of the server unavailable. For instance, Border Gateway Protocol (BGP) and ping of death [
108].
Detecting attacks, such as DoS and DDoS, is very complex to handle in a high-speed network due to the fast packet processing required. The flow of data from numerous IoT devices occurs at a high speed, making it challenging to monitor and classify traffic accurately. DDoS attacks, in particular, generate vast amounts of traffic from multiple devices to overwhelm the server resources, and the data processing must be extremely fast. Consequently, network monitoring struggles to keep up with the high-rate traffic and may result in packet drop and a reduced scalability [
109]. Various software-defined network techniques have been developed to mitigate DDoS attacks [
12,
52], including content delivery networks that improve performance while countering DDoS attacks [
60]. In recent studies [
110,
111], XDP (express data path) and eBPF (extended Berkeley packet filter) have been utilized for high-performance data analysis paths on networks, such as in Netmap [
109] and Data Plane Development Kit (DPDK) [
71,
112]. These techniques have proved valuable in processing data at the application layer. Despite the numerous frameworks proposed for packet classification and network traffic analysis, the speed of packet processing speed still requires improvement, especially when dealing with specialized hardware [
97].
Figure 7 highlights the discussion on the challenges of high-speed networks.
The term objective function is explained as end-to-end delay (EED) or one-way delay (OWD), both of which refer to calculating the time duration of a packet’s transfer from the source to destination. EED is commonly used for IP network monitoring, but it contrasts with round-trip time (RTT), which calculates the time for a packet to travel from the source to destination and back. Packet drops or losses can occur due to network traffic congestion, hardware issues, or software viruses. In computer networks, a DoS attack can manifest in different forms, such as packet drop attacks or black hole attacks. Detecting and preventing packet drop attacks is much harder, especially in high-speed data transfers on a network. The speed of the packet processing is directly related to the rate at which the data or information are processed across the network, and a higher performance of the network interfaces requires faster packet-processing speeds. High-speed routers act as forwarding engines, allowing them to handle the growing internet traffic demand without slowing down. To accommodate multi-terabit IP routers, data centers also require switches that can sustain a throughput of a hundred Gbps and multiple Tbps.
When a large packet is transmitted on a 100 gigabit lane network, the number of packets per second should decrease. The packet drop ratio is high when small packages are sent over this network interface card. The snort performs tests accurately on the data processing, detecting malicious activity on the network at an average speed. It focuses on high-speed traffic, inspecting incoming packets for potential threats. The ratio of dropped packets is higher for malicious traffic. Custom snort rules have been tested on 1 Gbps NICs by using different attack generators [
111]. Despite various security technologies, compressive techniques to solve DDoS issues remain challenging. The researcher in [
113] faced some challenges while trying to detecting DDoS attack solutions, as described below. High-rate flooding attacks are achieved by deploying open-source DDoS tools on the attacker’s machine during a DDoS attack, maintaining the server resources until the session expires [
114]. In a high-speed network, fast monitoring tools are utilized when a DDoS attack occurs, considering factors such as the number of connections, attack force, and impulsive protocols. The DDoS prevention system works keenly to stop malicious data from distributed nodes, grouping the malicious in the data-processing system. A bottleneck at a buffer queue creates a link with the attacking packets when the attack rate is high. It is impossible to decide which resources to allocate for the server without employing a classification approach [
115]. Datasets for DDoS prevention systems analyze the standard of testing for real-time implementation. However, the authors of [
116] failed identify the actual standard dataset for the testbed. The DDoS signature base attacks enlist all the feasible features of signatures in real-time [
117].
Application-layer DDoS attacks prevent applications from providing specific content to users. Commonly targeted web servers and applications include Session Initiation Protocol (SIP) voice servers and BGP [
65]. Hence, DDoS attacks are often initiated by intelligent clients, and they typically do not spoof IoT devices. There are seven types of application-layer attacks: slow loris, slow post, slow read, HTTP flooding, low and slow attack, large payload post, and Mimicked User browsing. Conversely, HTTP flood attacks involve a botnet, where the attacker sends numerous requests to overwhelm the target [
118,
119]. Volume-based DDoS assaults concentrate on the server’s bandwidth. Attackers frequently craft large requests with small sizes to overload the server, leading to crashes or instability. Some examples of Volumetric DDoS attacks at layer 3 are: a DNS NX domain flood, DNS Query flood, GRE attack, Internet Control Message Protocol type (ICMP) flood, and IP/ICMP fragmentation garbage flood [
119]. A sign of a volumetric DDoS attack is a higher bandwidth with ongoing data, reaching up to 100 Gb or terabits/second. A volumetric attack is easy to generate by applying easy amplification techniques. The sheer quantity of the traffic generated by the attack can entirely block access to end resources (a website or a service). The magnitude of the attack is typically measured in bits or packets per second [
120]. These attacks expose weaknesses in layer 3 and the four protocol stack. Protocol attacks consume the processing capacity of the attack target or intermediate critical resources, causing service disruptions. For instance, SYN floods and ping of death are examples of protocol-based attacks. A TCP SYN flood is a protocol-based attack where a sequence of TCP SYN requests is sent directly to the target server, making it unresponsive. In a recent DDoS outage, an application-layer attack involved TCP SYN floods targeting port 53 of Dyn’s DNS servers [
78].