Danger-Pose Detection System Using Commodity Wi-Fi for Bathroom Monitoring
Abstract
:1. Introduction
- We verify the feasibility of Wi-Fi CSI sensing for danger detection in a bathroom environment, especially in a bathtub. To the best of our knowledge, this is a first work to use CSI for anomaly detection.
- We propose a dynamic feature extraction method of CSI, which effectively reduces the influence of environmental changes.
- We only rely on training data derived in normal situations. We collect data when a user is normally bathing/showering and feed them into an anomaly-detection algorithm to avoid collecting the data in dangerous situations, which is difficult to collect in practical use.
- We measured the performance of this method in an actual environment. The experimental results show that the danger-pose detection system has high detection performance in a non-line-of-sight (NLOS) scenario.
2. Related Work
2.1. Traditional Healthcare Methods
2.2. Sensing Using Wireless Communication Signals
- Bath water might cover human body and let body become unrecognizable by wireless signals.
- Training data in dangerous situations for a machine learning algorithm is hard to obtain. We can simulate danger poses and get data for evaluation, which are not suitable as training data in practical use.
- Due to the lack of training data, over fitting is a problem that should be solved for bathroom monitoring.
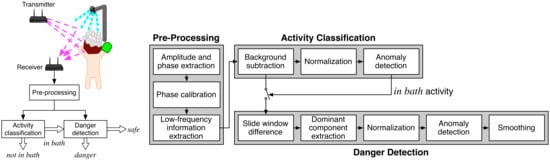
3. Danger-Pose Detection System in Bathroom
3.1. Overview
3.2. Pre-Processing
3.2.1. Amplitude and Phase Extraction
3.2.2. Phase Calibration
3.2.3. Low-Frequency Information Extraction
3.3. Activity Classification
3.3.1. Background Subtraction
3.3.2. Normalization
3.3.3. Anomaly Detection
3.4. Danger Detection
3.4.1. Slide Window Difference
3.4.2. Dominant Component Extraction
3.4.3. Anomaly Detection
3.4.4. Smoothing
4. Experiment
4.1. Experiment Setup
4.2. Classification Performance of Each Block
4.3. Total Danger Detection Performance
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| CSI | channel state information |
| FFT | fast Fourier transform |
| FN | false negative |
| FP | false positive |
| LOS | line-of-sight |
| MIMO | multiple input multiple output |
| NLOS | non-line-of-sight |
| OFDM | orthogonal frequency division multiplexing |
| PCA | principal components analysis |
| RSS | received signal strength |
| SVM | support vector machine |
| TP | true positive |
References
- Japanese Society of Legal Medicine. Investigation of Case Death in Bathtub. 2014. Available online: http://www.jslm.jp/problem/yokusou.pdf (accessed on 10 December 2018).
- Otsuka, Y.; Inokuma, S.; Sugimoto, Y. Analysis of Bathing Related Accidents -Collaboration with Japanese Association for Acute Medicine. J. Jpn. Soc. Balneol. Climatol. Phys. Med. 2010, 73, 267–268. [Google Scholar] [CrossRef]
- Fleury, A.; Vacher, M.; Noury, N. SVM-based multimodal classification of activities of daily living in health smart homes: Sensors, algorithms, and first experimental results. IEEE Trans. Inf. Technol. Biomed. 2010, 14, 274–283. [Google Scholar] [CrossRef] [PubMed]
- Kasteren, T.L.; Englebienne, G.; Kröse, B.J. An activity monitoring system for elderly care using generative and discriminative models. J. Pers. Ubiquitous Comput. 2010, 14, 489–498. [Google Scholar] [CrossRef] [Green Version]
- Nee, R.V.; Prasad, R. OFDM for Wireless Multimedia Communications; Artech House, Inc.: Norwood, MA, USA, 2000. [Google Scholar]
- Choi, L.U.; Murch, R.D. A transmit preprocessing technique for multiuser MIMO systems using a decomposition approach. IEEE Trans. Wirel. Commun. 2004, 3, 20–24. [Google Scholar] [CrossRef]
- Wang, H.; Zhang, D.; Wang, Y.; Ma, J.; Wang, Y.; Li, S. RT-Fall: A Real-Time and Contactless Fall Detection System with Commodity WiFi Devices. IEEE Trans. Mob. Comput. 2017, 16, 511–526. [Google Scholar] [CrossRef]
- Wang, X.; Yang, C.; Mao, S. TensorBeat: Tensor Decomposition for Monitoring Multiperson Breathing Beats with Commodity WiFi. ACM Trans. Intell. Syst. Technol. (TIST) 2017, 9, 1–27. [Google Scholar] [CrossRef]
- Vallabh, P.; Malekian, R. Fall Detection Monitoring Systems: A Comprehensive Review. J. Ambient Intell. Hum. Comput. 2018, 9, 1809–1833. [Google Scholar] [CrossRef]
- Lotfi, A.; Albawendi, S.; Powell, H.; Appiah, K.; Langensiepen, C. Supporting Independent Living for Older Adults; Employing a Visual Based Fall Detection Through Analysing the Motion and Shape of the Human Body. IEEE Access 2016, 6, 70272–70282. [Google Scholar] [CrossRef]
- Zhang, Z.; Conly, C.; Anthitsos, V. A Survey on Vision-based Fall Detection. In Proceedings of the 8th ACM International Conference on Pervasive Technologies Related to Assistive Environments, Corfu, Greece, 1–3 July 2015; pp. 1–7. [Google Scholar]
- De Miguel, K.; Brunete, A.; Hernando, M.; Gambao, E. Home camera-based fall detection system for the elderly. Sensors 2017, 17, 2864. [Google Scholar] [CrossRef] [PubMed]
- Balakrishnan, G.; Durand, F.; Guttag, J. Detecting pulse from head motions in video. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Portland, OR, USA, 25–27 June 2013; pp. 3430–3437. [Google Scholar]
- Jain, H.; Chen, H. A Portable Fall Detection and Alerting System Based on k-NN Algorithm and Remote Medicine. China Commun. Mag. 2015, 12, 23–31. [Google Scholar] [CrossRef]
- Sabatini, A.M.; Ligorio, G.; Mannini, A.; Genovese, V.; Pinna, L. Prior-to- and Post-Impact Fall Detection Using Inertial and Barometric Altimeter Measurements. IEEE Trans. Neural Syst. Rehabil. Eng. 2016, 24, 774–783. [Google Scholar] [CrossRef]
- Zigel, Y.; Litvak, D.; Gannot, I. A Method for Automatic Fall Detection of Elderly People Using loor Vibrations and Sound—Proof of Concept on Human Mimicking Doll Falls. IEEE Trans. Biomed. Eng. 2009, 56, 2858–2867. [Google Scholar] [CrossRef]
- Luque, R.; Casilari, E.; Morón, M.J.; Redondo, G. Comparison and Characterization of Android-Based Fall Detection Systems. Sensors 2014, 14, 18543–18574. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Garripoli, C.; Mercuri, M.; Karsmakers, P.; Soh, P.J.; Crupi, G.; Vandenbosch, G.A.E.; Pace, C.; Leroux, P.; Schreurs, D. Embedded DSP-Based Telehealth Radar System for Remote In-Door Fall Detection. IEEE J. Biomed. Health Inform. 2015, 19, 92–101. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Jokanović, B.; Amin, M. Fall Detection Using Deep Learning in Range-Doppler Radars. IEEE Trans. Aerosp. Electron. Syst. 2018, 54, 180–189. [Google Scholar] [CrossRef]
- Sugano, M.; Kawazoe, T.; Ohta, Y.; Murata, M. Indoor Localization System using RSSI Measurement of Wireless Sensor Network based on ZigBee Standard. In Proceedings of the 2006 IFIP International Conference on Wireless and Optical Communications, Bangalore, India, 11–13 April 2006; pp. 1–6. [Google Scholar]
- Vasisht, D.; Kumar, S.; Katabi, D. Decimeter-Level Localization with a Single WiFi Access Point. In Proceedings of the USENIX Symposium on Networked Systems Design and Implementation (NSDI), Santa Clara, CA, USA, 16–18 March 2016; pp. 165–178. [Google Scholar]
- Ali, K.; Liu, A.X.; Wang, W.; Shahzad, M. Recognizing Keystrokes Using WiFi Devices. IEEE J. Sel. Areas Commun. 2017, 35, 1175–1190. [Google Scholar] [CrossRef]
- Zhao, M.; Li, T.; Abu Alsheikh, M.; Tian, Y.; Zhao, H.; Torralba, A.; Katabi, D. Through-wall human pose estimation using radio signals. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Salt Lake City, UT, USA, 19–21 June 2018; pp. 7356–7365. [Google Scholar]
- Halperin, D.; Hu, W.; Sheth, A.; Wetherall, D. Tool release: Gathering 802.11n traces with channel state information. ACM SIGCOMM Comput. Commun. Rev. 2011, 41, 53. [Google Scholar] [CrossRef]
- Wang, X.; Gao, L.; Mao, S. PhaseFi: Phase fingerprinting for indoor localization with a deep learning approach. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–6. [Google Scholar]
- Wang, X.; Gao, L.; Mao, S. CSI phase fingerprinting for indoor localization with a deep learning approach. IEEE Internet Things J. 2016, 3, 1113–1123. [Google Scholar] [CrossRef]
- IEEE Standards Association. IEEE Std 802.11-2016, IEEE Standard for Local and Metropolitan Area Networks—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications, 2016. Available online: http://standards.ieee.org/ (accessed on 19 November 2018).
- Di Domenico, S.; De Sanctis, M.; Cianca, E.; Giuliano, F.; Bianchi, G. Exploring Training Options for RF Sensing Using CSI. IEEE Commun. Mag. 2018, 56, 116–123. [Google Scholar] [CrossRef]









| (a) | (b) | ||||||
|---|---|---|---|---|---|---|---|
| Estimated | in Bath | not in Bath | Estimated | Danger | Safe | ||
| Actual | Actual | ||||||
| in bath (Positive) | 294,402 | 15,461 | danger (Positive) | 19,878 | 1694 | ||
| not in bath (Negative) | 5174 | 114,150 | safe (Negative) | 14,874 | 273,417 | ||
| Precision | 98.27% | Precision | 57.20% | ||||
| Recall | 95.01% | Recall | 92.15% | ||||
| F1 | 96.61% | F1 | 70.58% | ||||
| Estimated | Danger | Safe | |
|---|---|---|---|
| Actual | |||
| not in bath | 2377 | 2797 | |
| Estimated | Danger | Not Danger | |
|---|---|---|---|
| Actual | |||
| danger (Positive) | 51 | 2 | |
| not danger (Negative) (= not in bath or safe) | 10 | 1008 | |
| Precision | 83.61% | ||
| Recall | 96.23% | ||
| F1 | 89.47% | ||
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, Z.; Ishida, S.; Tagashira, S.; Fukuda, A. Danger-Pose Detection System Using Commodity Wi-Fi for Bathroom Monitoring. Sensors 2019, 19, 884. https://doi.org/10.3390/s19040884
Zhang Z, Ishida S, Tagashira S, Fukuda A. Danger-Pose Detection System Using Commodity Wi-Fi for Bathroom Monitoring. Sensors. 2019; 19(4):884. https://doi.org/10.3390/s19040884
Chicago/Turabian StyleZhang, Zizheng, Shigemi Ishida, Shigeaki Tagashira, and Akira Fukuda. 2019. "Danger-Pose Detection System Using Commodity Wi-Fi for Bathroom Monitoring" Sensors 19, no. 4: 884. https://doi.org/10.3390/s19040884