An IoT-Oriented Offloading Method with Privacy Preservation for Cloudlet-Enabled Wireless Metropolitan Area Networks
Abstract
:1. Introduction
1.1. Background
1.2. Motivation
1.3. Paper Contributions
- Construct a systematic model of the resource utilization, the energy consumption and the data transmission time of the cloudlets when offloading the IoT data to the cloudlets.
- Adopt the Dijkstra algorithm to calculate the shortest path between AP points in a WMAN in order to reduce the transmission time of data.
- Optimize the multi-objective problem model by the nondominated sorting differential evolution (NSDE) algorithm with privacy preservation considered, and finally the optimal offloading strategies are output.
- Conduct extensive experimental evaluations and comparison analysis to demonstrate the efficiency and effectiveness of the proposed method.
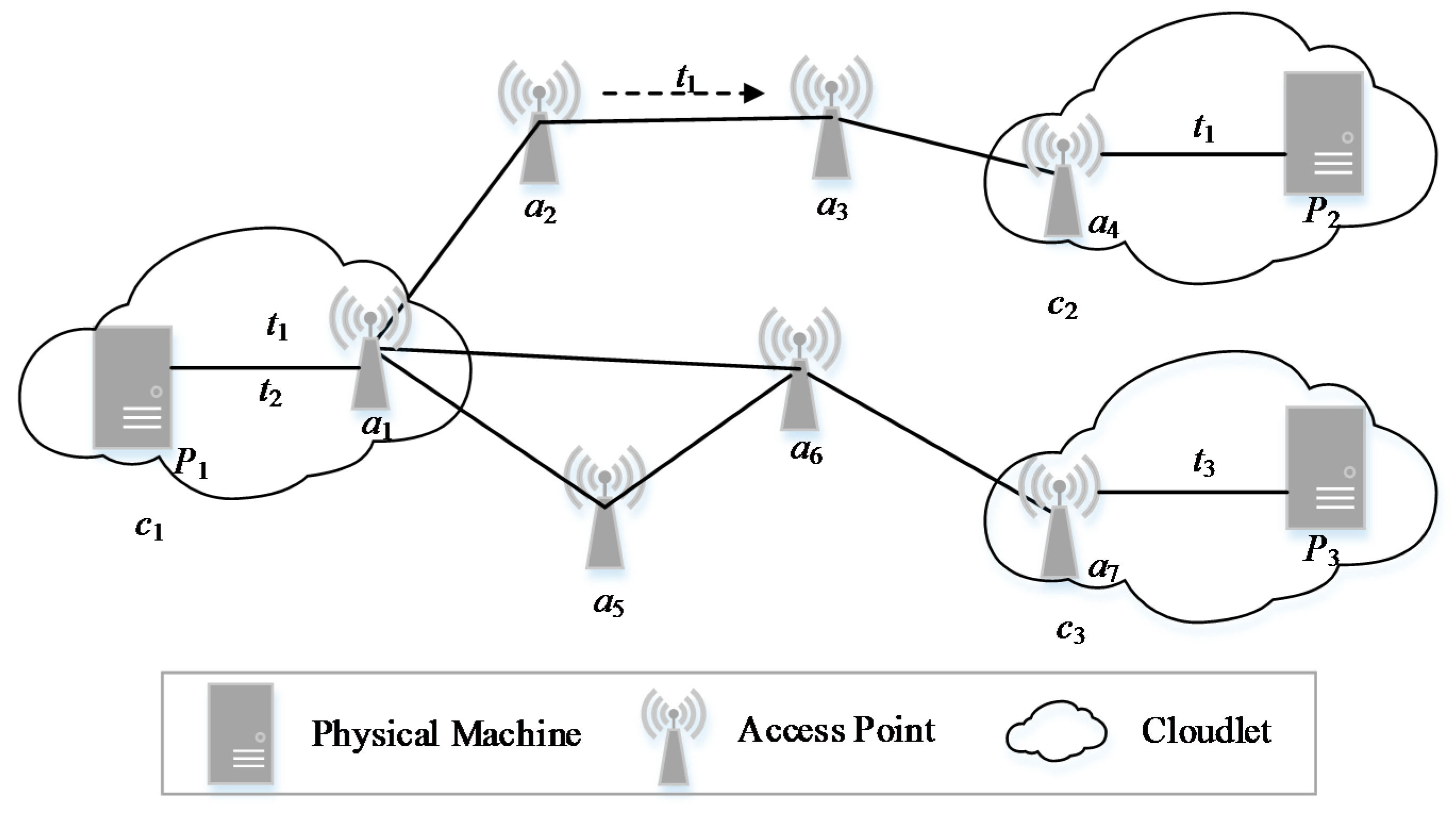
2. System Model and Problem Formulation
2.1. Resource Model
2.2. Resource Utilization Model
2.3. Data Transmission Model
2.4. Energy Consumption Model
2.5. Data Privacy Preservation Model of the Comouting Tasks
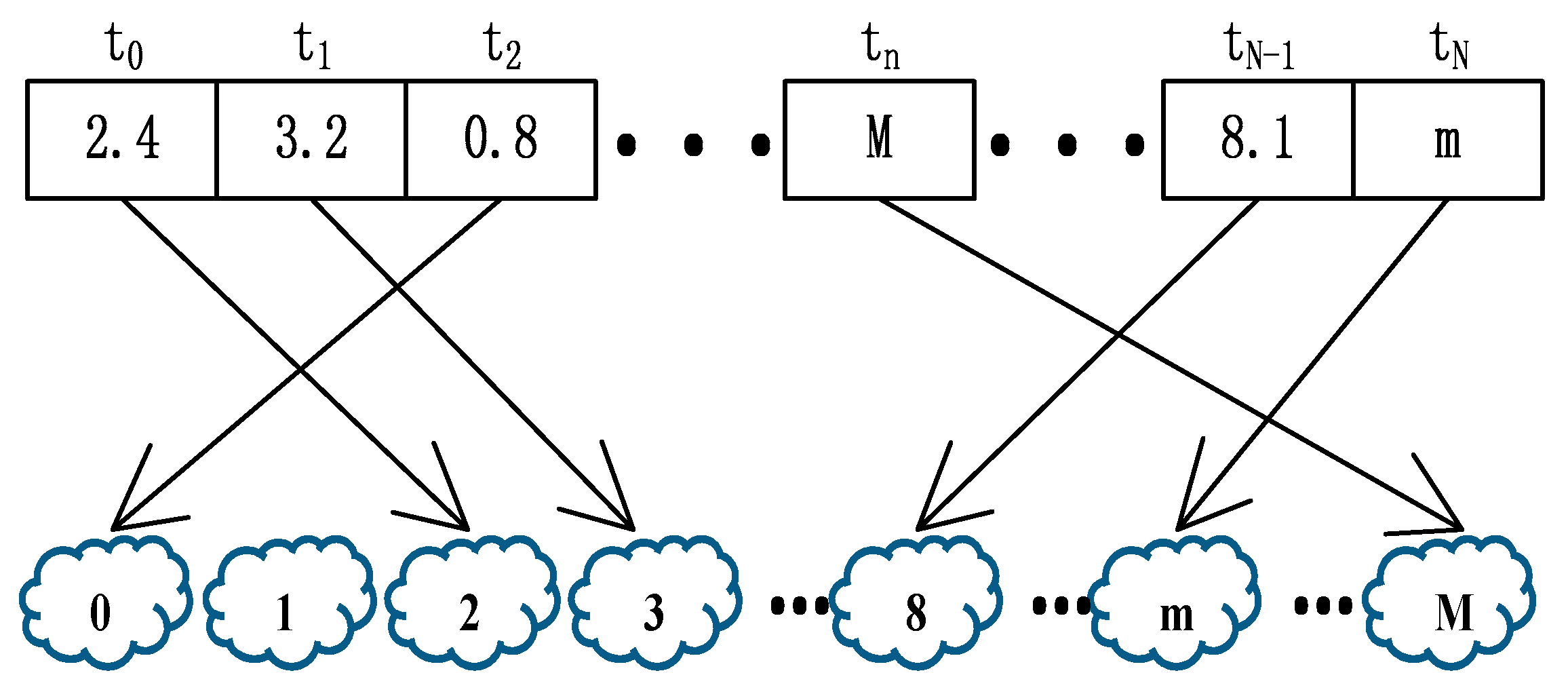
3. An IoT-Oriented Offloading Method with Privacy Preservation
3.1. Shortest Path Acquisition of APs in WMAN Based on Dijkstra Algorithm
3.2. Optimization Problem Model by NSDE
| Algorithm 1. nondominated sorting differential evolution based offloading strategy acquisition. |
| Input: the size of the population NP, the number of the cloudlets M, the number of the iterations G, the mutation factor F, the crossover factor CR Output: the better solution set S 01: g = 0 02: P = Initialization (NP, M) 03: while g < G do 04: Q = Crossover and mutation(P, F, CR) 05: O = P + Q) 06: L = nondominated sort(O)) 07: P = Ø, Q = Ø, i = 0) 08: while size(P) + num (Li) < NP do 09: P += Li 10: i ++ 11: end while 12: Calculate crowding distance (Li) by (16) 13: Li,j = Sort (Li) according to Dj from large to small 14: j = 0 15: while size(P) < NP do 16: P += Li,j 17: j ++ 18: end while 19: g ++ 20: end while 21: return the better solution set S |
4. Experimental Evaluation
4.1. Simulation Setup
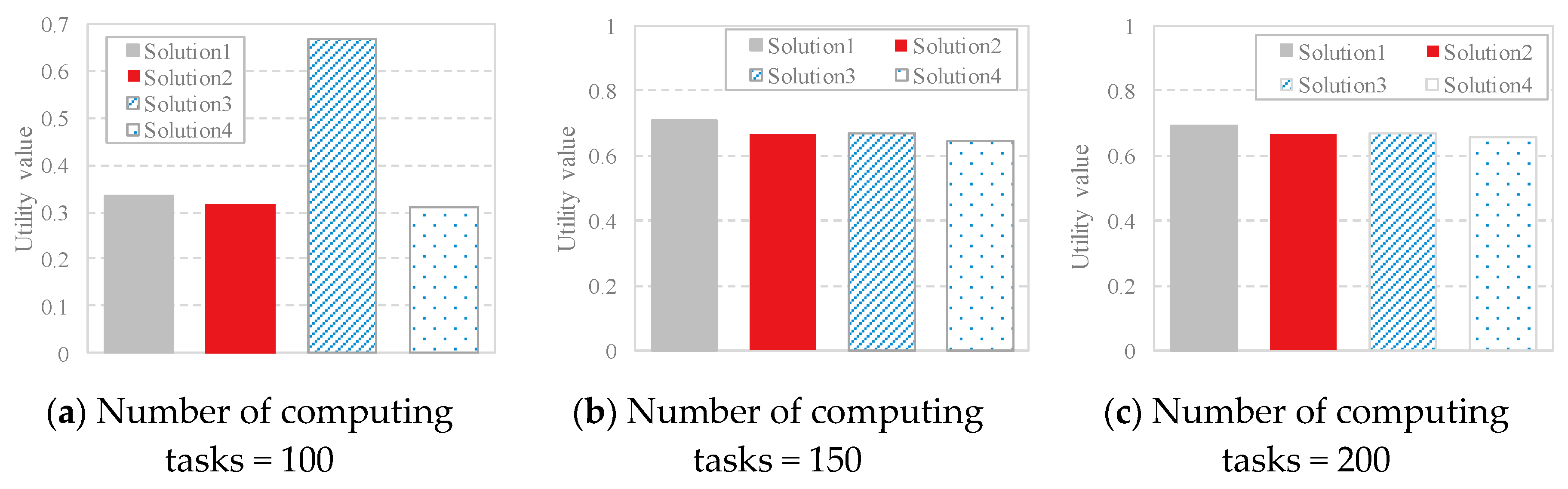
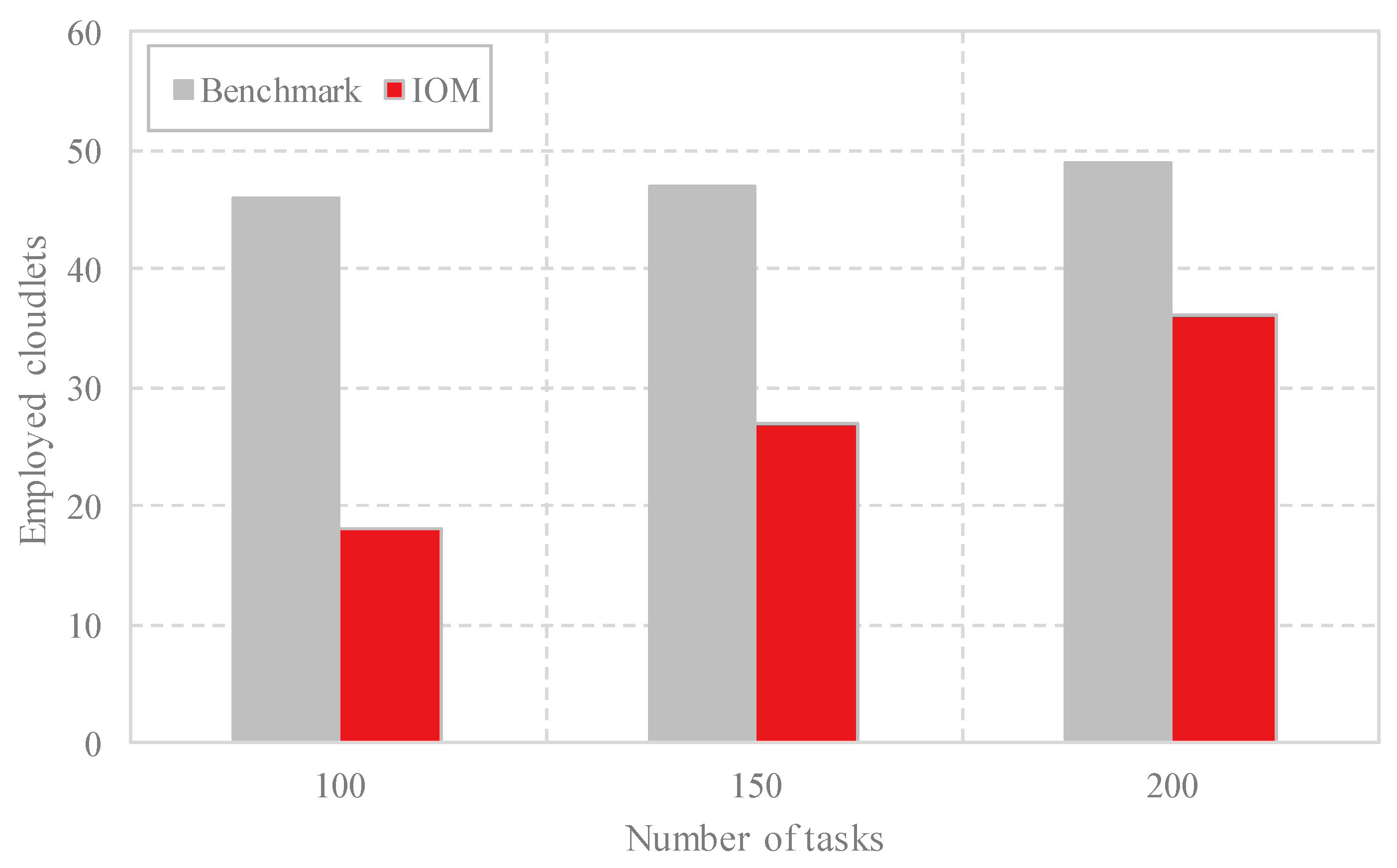
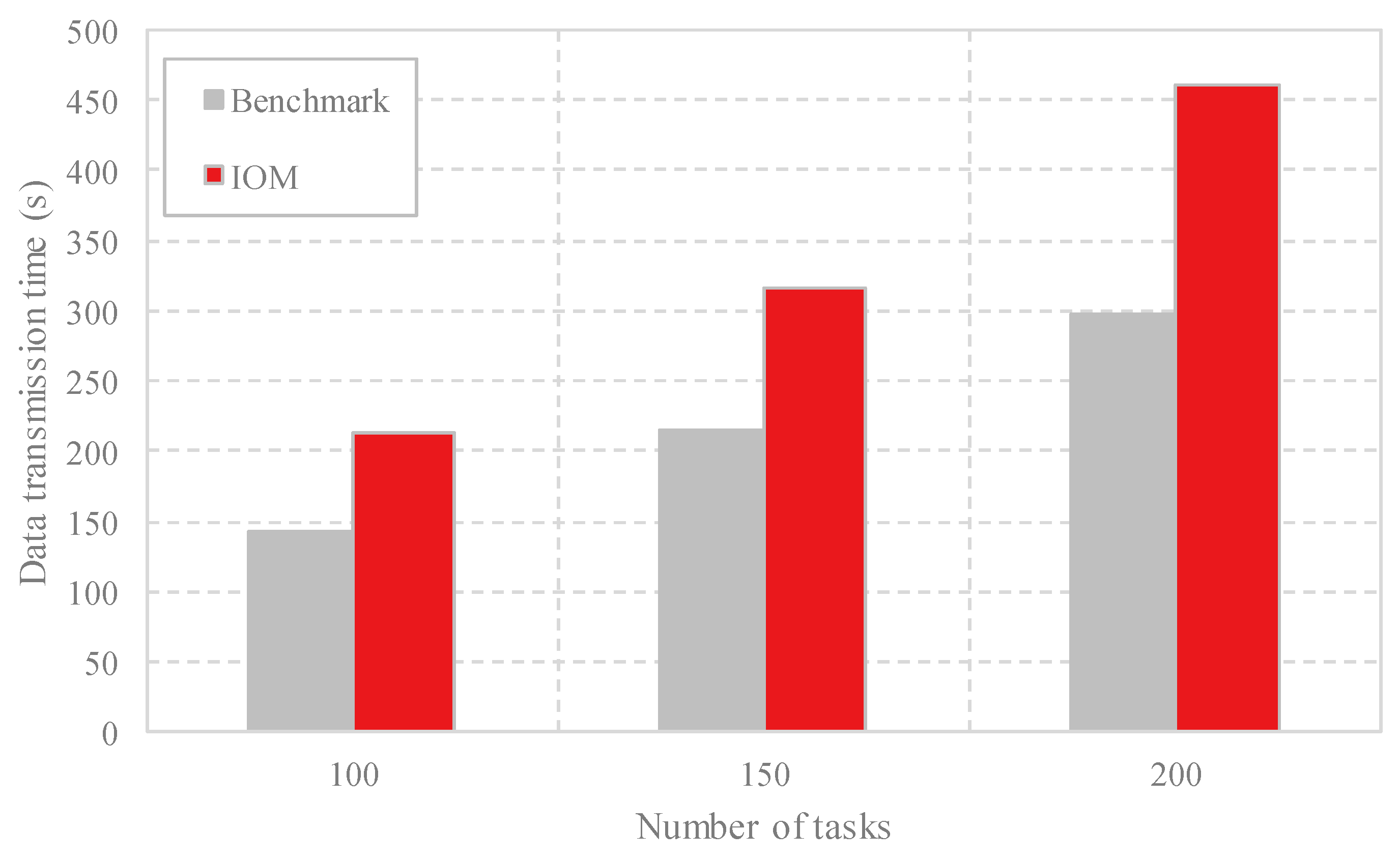
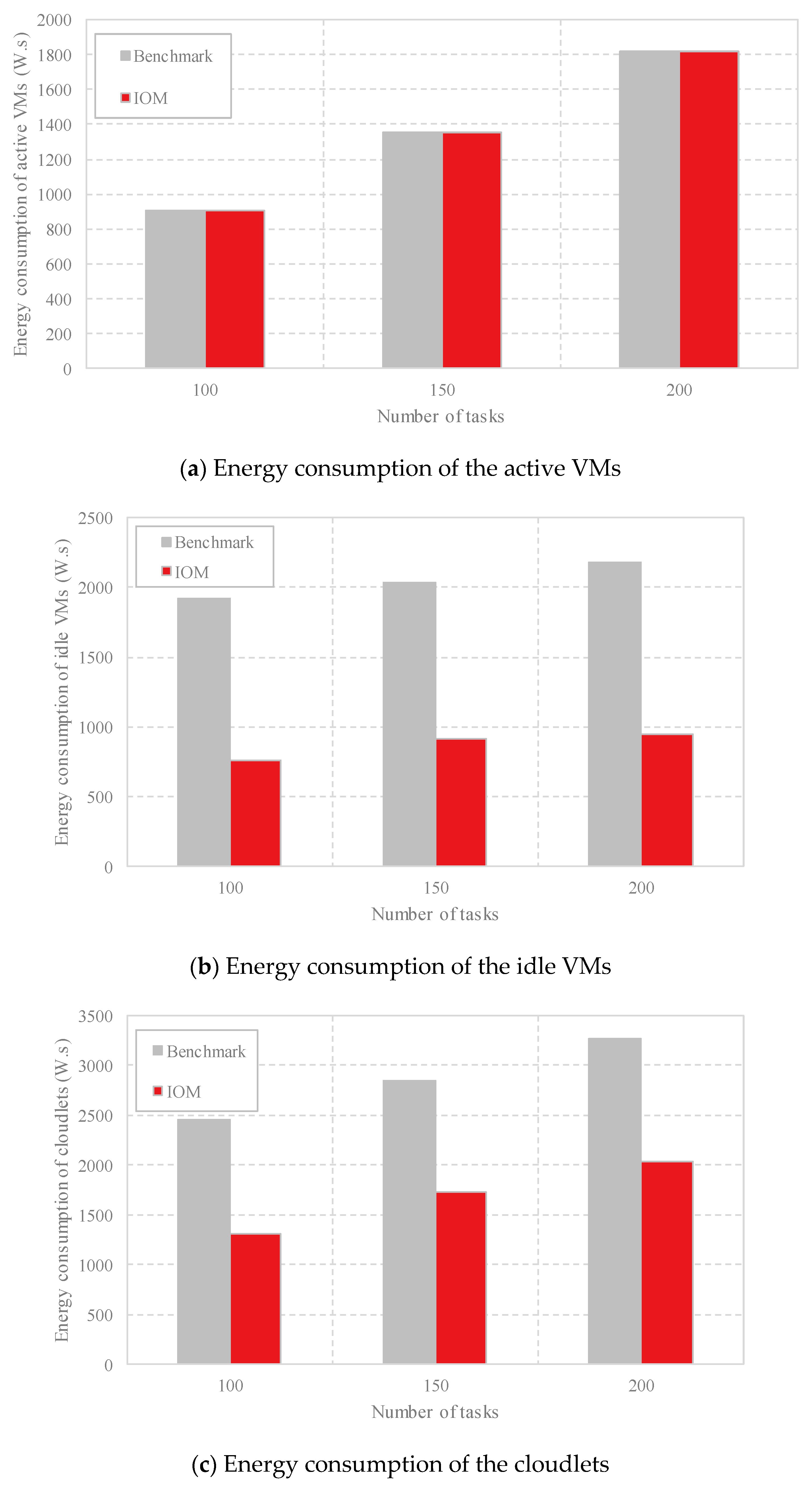
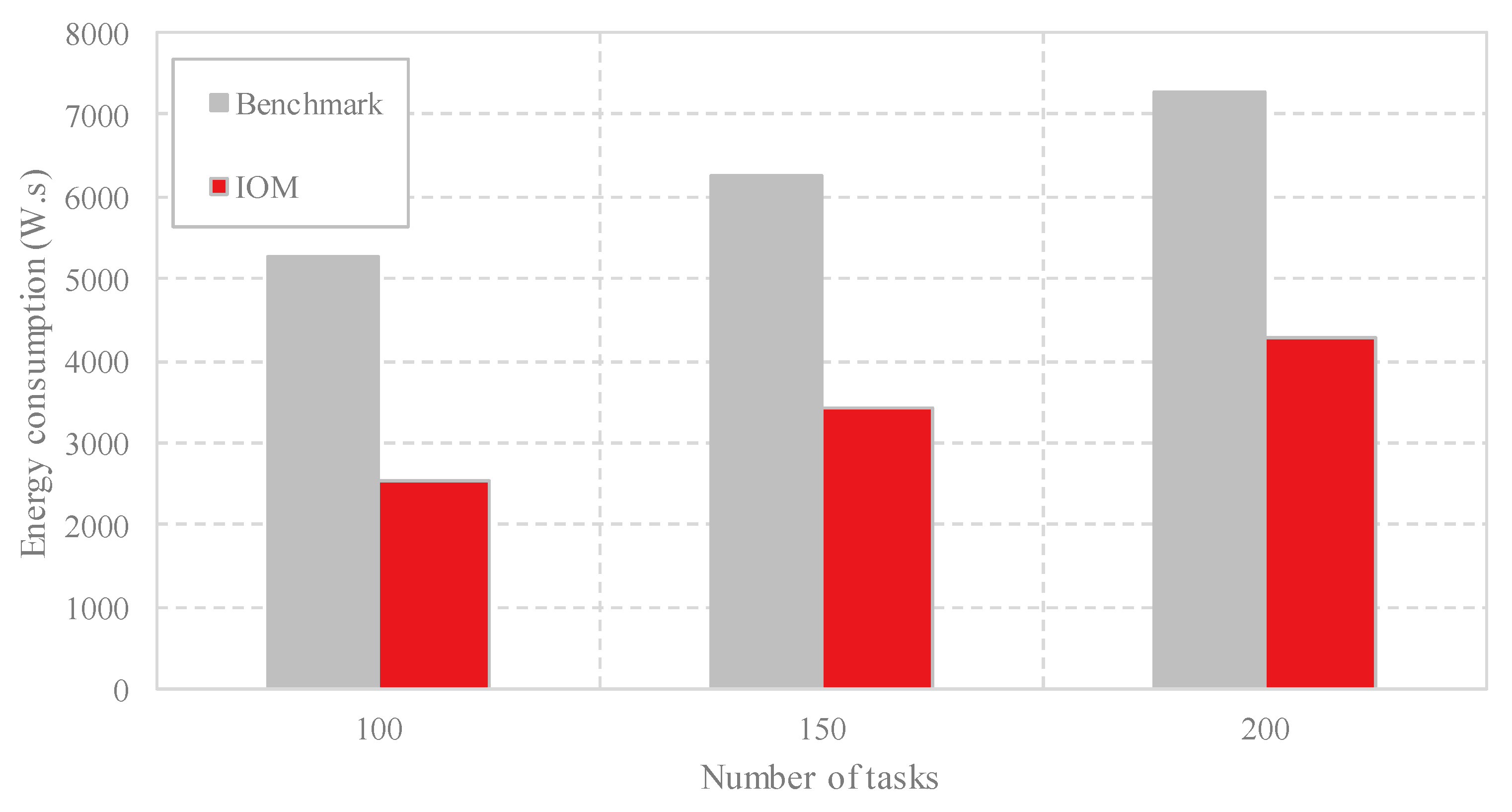
4.2. Performance Evaluation of IOM
4.3. Comparison Analysis
5. Related Work
6. Conclusions and Future Work
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Baskaran, S.B.M.; Raja, G. Blind key distribution mechanism to secure wireless metropolitan area network. CSI Trans. ICT 2016, 4, 157–163. [Google Scholar] [CrossRef]
- Zhou, B.; Dastjerdi, A.V.; Calheiros, R.N.; Srirama, S.N.; Buyya, R. mCloud: A context-aware offloading framework for heterogeneous mobile cloud. Trans. Serv. Comput. 2015, 10, 797–810. [Google Scholar] [CrossRef]
- Karloff, H.; Subbaraman, R. Designing wireless metropolitan-area networks using mathematical optimization. In Proceedings of the Wireless Telecommunications Symposium (WTS), New York, NY, USA, 15–17 April 2015; pp. 1–8. [Google Scholar]
- Al-Janabi, S.; Al-Shourbaji, I.; Shojafar, M.; Abdelhag, M. Mobile Cloud Computing: Challenges and Future Research Directions. In Proceedings of the 10th International Conference on Developments in eSystems Engineering (DeSE), Paris, France, 14–16 June 2017; pp. 62–67. [Google Scholar]
- Zhaoqing, P.; Jianjun, L.; Yajuan, Z.; Wang, F.L. Adaptive fractional-pixel motion estimation skipped algorithm for efficient HEVC motion estimation. ACM Trans. Multimed. Comput. Commun. Appl. 2018, 14, 12–19. [Google Scholar]
- Chen, X. Decentralized computation offloading game for mobile cloud computing. Trans. Parallel Distrib. Syst. 2015, 26, 974–983. [Google Scholar] [CrossRef]
- Jara, A.J. Wearable internet: Powering personal devices with the internet of things capabilities. In Proceedings of the International Conference on Identification, Information and Knowledge in the Internet of Things (IIKI), Beijing, China, 17–18 October 2014; pp. 1–7. [Google Scholar]
- Li, P.; Zhao, S.; Zhang, R. A cluster analysis selection strategy for supersaturated designs. Comput. Stat. Data Anal. 2010, 54, 1605–1612. [Google Scholar] [CrossRef]
- Keng, D.; Koo, S.G.M. Spatial standards for Internet of Things. In Proceedings of the Conference on Internet of Things (iThings), Taipei, Taiwan, 1–3 September 2014; pp. 284–287. [Google Scholar]
- Tian, G.L.; Wang, M.; Song, L. Variable selection in the high-dimensional continuous generalized linear model with current status data. J. Appl. Stat. 2014, 41, 467–483. [Google Scholar] [CrossRef] [Green Version]
- Li, S.; Zhang, Y. On-Line Scheduling on Parallel Machines to Minimize the Makespan. J. Syst. Sci. Complex. 2016, 29, 472–477. [Google Scholar] [CrossRef]
- Wang, Y.; Sun, X.; Meng, F. On the conditional and partial trade credit policy with capital constraints: A Stackelberg model. Appl. Math. Model. 2016, 40, 1–18. [Google Scholar] [CrossRef]
- Meng, S.; Wang, S.; Wu, T.; Li, D.; Huang, T.; Wu, X.; Xu, X.; Dou, W. An uncertainty-aware evolutionary scheduling method for cloud service provisioning. In Proceedings of the IEEE International Conference on Web Services (ICWS), San Francisco, CA, USA, 27 June–2 July 2016; pp. 506–513. [Google Scholar]
- Wang, G.; Huang, X.X.; Zhang, J. Levitin-Polyak well-posedness in generalized equilibrium problems with functional constraints. Pac. J. Optim. 2010, 6, 441–453. [Google Scholar]
- Qu, B.; Zhao, J. Methods for Solving Generalized Nash Equilibrium. J. Appl. Math. 2013. [Google Scholar] [CrossRef]
- Zhang, J.; Qu, B.; Xiu, N. Some projection-like methods for the generalized Nash equilibria. Comput. Optim. Appl. 2010, 45, 89–109. [Google Scholar] [CrossRef]
- Li, Y.; Gao, W. Code offload with least context migration in the mobile cloud. In Proceedings of the Conference on Computer Communications (ICCC), Kowloon, Hong Kong, 26 April–1 May 2015; pp. 1876–1884. [Google Scholar]
- Soyata, T.; Muraleedharan, R.; Funai, C.; Kwon, M.; Heinzelman, W. Cloud-vision: Real-time face recognition using a mobile cloudlet-cloud acceleration architecture. In Proceedings of the IEEE Symposium on Computers and Communications (ISCC), Cappadocia, Turkey, 1–4 July 2012; pp. 59–66. [Google Scholar]
- Li, Y.; Anh, N.T.; Nooh, A.S.; Ra, K.; Jo, M. Dynamic Mobile Cloudlet Clustering for Fog Computing. In Proceedings of the International Conference on Electronics, Information, and Communication (CEIC), Honolulu, HI, USA, 24–27 January 2018; pp. 1–4. [Google Scholar]
- Shen, J.; Tan, H.-W.; Wang, J.; Wang, J.-W.; Lee, S.-Y. A novel routing protocol providing good transmission reliability in underwater sensor networks. J. Internet Technol. 2015, 16, 171–178. [Google Scholar]
- Xiang, H.; Xu, X.; Zheng, H.; Li, S.; Wu, T.; Dou, W.; Yu, S. An adaptive cloudlet placement method for mobile applications over cloud. In Proceedings of the Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016. [Google Scholar]
- Li, H.; Wang, S. Partial condition number for the equality constrained linear least squares problem. Calcolo 2017, 54, 1121–1146. [Google Scholar] [CrossRef]
- Li, P.; Li, T.; Ye, H.; Li, J.; Chen, X.; Xiang, Y. Privacy-preserving machine learning with multiple data providers. Future Gener. Comput. Syst. 2018, 87, 341–350. [Google Scholar] [CrossRef]
- He, K.; Chen, J.; Du, R.; Wu, Q.; Xue, G.; Zhang, X. Deypos: Deduplicatable dynamic proof of storage for multi-user environments. IEEE Trans. Comput. 2016, 65, 3631–3645. [Google Scholar] [CrossRef]
- Namjoshi, J.; Gupte, A. Service oriented architecture for cloud based travel reservation software as a service. In Proceedings of the 2009 IEEE International Conference on Cloud Computing (ICCC), Bangalore, India, 21–25 September 2009; pp. 147–150. [Google Scholar]
- Xue, S.; Zhang, Y.; Xu, X.; Xing, G.; Xiang, H.; Ji, S. QET: A QoS-Based Energy-Aware Task Scheduling Method in Cloud Environment. Clust. Comput. 2017. [Google Scholar] [CrossRef]
- Yang, J.; Xu, X.; Dou, W. A Task Scheduling Method for Energy-Performance Trade-off in Clouds. In Proceedings of the 18th International Conference on High Performance Computing and Communications (HPCC), Sydney, Australia, 12–14 December 2016; pp. 1029–1036. [Google Scholar]
- Su, M.; Zhang, L.; Wu, Y.; Chen, K.; Li, K. Systematic data placement optimization in multi-cloud storage for complex requirements. IEEE Trans. Comput. 2016, 65, 1964–1977. [Google Scholar] [CrossRef]
- Jia, M.; Liang, W.; Xu, Z.; Huang, M.; Ma, Y. QoS-Aware Cloudlet Load Balancing in Wireless Metropolitan Area Networks. IEEE Trans. Cloud Comput. 2018. [Google Scholar] [CrossRef]
- Jia, M.; Liang, W.; Xu, Z.; Huang, M. Cloudlet load balancing in wireless metropolitan area networks. In Proceedings of the Conference on Computer Communications (INFOCOM), San Francisco, CA, USA, 10–14 April 2016; pp. 1–9. [Google Scholar]
- Khan, A.M.; Freitag, F. On Edge Cloud Service Provision with Distributed Home Servers. In Proceedings of the IEEE International Conference on Cloud Computing Technology and Science (CloudCom), Hong Kong, China, 11–14 December 2017; pp. 223–226. [Google Scholar]
- Barbera, M.; Kosta, S.; Mei, A.; Stefa, J. To offload or not to offload? the bandwidth and energy costs of mobile cloud computing. In Proceedings of the IEEE International Conference on Computer Communications (INFOCOM), Turin, Italy, 14–19 April 2013; pp. 1285–1293. [Google Scholar]
- Zhang, Z.; Li, S. A Survey of Computational Offloading in Mobile Cloud Computing. In Proceedings of the IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), Oxford, UK, 29 March–1 April 2016; pp. 81–82. [Google Scholar]
- Wang, P.; Zhao, L. Some geometrical properties of convex level sets of minimal graph on 2-dimensional Riemannian manifolds. Nonlinear Anal. 2016, 130, 1–17. [Google Scholar] [CrossRef]
- Wang, S.; Huang, L.; Hsu, C.-H.; Yang, F. Collaboration reputation for trustworthy Web service selection in social networks. J. Comput. Syst. Sci. 2016, 82, 130–143. [Google Scholar] [CrossRef]
- Xu, Z.; Liang, W.; Xu, W.; Jia, M.; Guo, S. Capacitated cloudlet placements in wireless metropolitan area networks. In Proceedings of the IEEE International Conference on Local Computer Networks (LCN), Clearwater Beach, FL, USA, 26–29 October 2015; pp. 570–578. [Google Scholar]
- Hoang, D.T.; Niyato, D.; Wang, P. Optimal admission control policy for mobile cloud computing hotspot with cloudlet. In Proceedings of the Conference on Wireless Communications and Networking Conference (IWCNC), Shanghai, China, 1–4 April 2012; pp. 3145–3149. [Google Scholar]
- Whaiduzzaman, M.; Gani, A.; Naveed, A. Pefc: Performance enhancement framework for cloudlet in mobile cloud computing. In Proceedings of the Symposium on Robotics and Manufacturing Automation, Kuala Lumpur, Malaysia, 15–16 December 2014; pp. 224–229. [Google Scholar]
- Artail, A.; Frenn, K.; Safa, H.; Artail, H. A framework of mobile cloudlet centers based on the use of mobile devices as cloudlets. In Proceedings of the Conference on Advanced Information Networking and Applications (AINA), Gwangiu, Korea, 24–27 March 2015; pp. 777–784. [Google Scholar]
- Ciobanu, R.I.; Negru, C.; Pop, F.; Dobre, C. Drop computing: Ad-hoc dynamic collaborative computing. Future Gener. Comput. Syst. 2017. [Google Scholar] [CrossRef]
- Mao, Y.; Zhang, J.; Letaief, K.B. Joint task offloading scheduling and transmit power allocation for mobile-edge computing systems. In Proceedings of the in Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017; pp. 1–6. [Google Scholar]
- Lian, S.; Duan, Y. Smoothing of the lower-order exact penalty function for inequality constrained optimization. J. Inequal. Appl. 2016, 2016, 185. [Google Scholar] [CrossRef]
- Wu, H.; Ren, Y.; Hu, F. Continuous dependence property of BSDE with constraints. Appl. Math. Lett. 2015, 45, 41–46. [Google Scholar] [CrossRef]
- Wang, C.; Ma, C.; Zhou, J. A new class of exact penalty functions and penalty algorithms. J. Glob. Optim. 2014, 58, 51–73. [Google Scholar] [CrossRef]
- Fan, Q.; Ansari, N.; Sun, X. Energy driven avatar migration in green cloudlet networks. IEEE Commun. Lett. 2017, 21, 1601–1604. [Google Scholar] [CrossRef]
- Wang, S.; Lei, T.; Zhang, L.; Hsu, C.-H.; Yang, F. Offloading Mobile Data Traffic for QoS-aware Service Provision in Vehicular Cyber-Physical Systems. Future Gener. Comput. Syst. 2016, 61, 118–127. [Google Scholar] [CrossRef]
- Jia, M.; Cao, J.; Liang, W. Optimal cloudlet placement and user to cloudlet allocation in wireless metropolitan area networks. IEEE Trans. Cloud Comput. 2017, 5, 725–737. [Google Scholar] [CrossRef]
- Satyanarayanan, M.; Simoens, P.; Xiao, Y.; Pillai, P.; Chen, Z.; Ha, K.; Hu, W.; Amos, B. Edge analytics in the internet of things. IEEE Perv. Comput. 2015, 2, 24–31. [Google Scholar] [CrossRef]
- ARahman; Hassanain, E; Hossain, M.S. Towards a secure mobile edge computing framework for Hajj. IEEE Access 2017, 5, 11768–11781. [Google Scholar]
- Chen, M.; Qian, Y.; Chen, J.; Hwang, K.; Mao, S.; Hu, L. Privacy protection and intrusion avoidance for cloudlet-based medical data sharing. IEEE Trans. Cloud Comput. 2016. [Google Scholar] [CrossRef]
- Liu, B.; Qu, B.; Zheng, N. A Successive Projection Algorithm for Solving the Multiple-Sets Split Feasibility Problem. Numer. Funct. Anal. Optim. 2014, 35, 1459–1466. [Google Scholar] [CrossRef]
- Cai, J.Q.; Li, H. An implicit degree condition for relative length of long paths and cycles in graphs. Acta Math. Appl. Sin. 2016, 32, 365–372. [Google Scholar] [CrossRef]
- Li, L.; Meng, F.; Ju, P. Some new integral inequalities and their applications in studying the stability of nonlinear integro-differential equations with time delay. J. Math. Anal. Appl. 2011, 377, 853–862. [Google Scholar] [CrossRef]

| Terms | Descriptions |
|---|---|
| C | The cloudlet collection |
| A | The AP(Access Point) collection |
| T | The computing task collection |
| D | The dataset collection of the computing tasks |
| X | The data offloading policy collection for T |
| P | The number of computing tasks |
| ln(X) | The resource utilization rate of the cloudlet cn |
| σ(X) | The number of the occupied cloudlets |
| ψ(X) | The average of ln(X) |
| TT(X) | The propagation delay time of the computing tasks |
| T(X) | The average of propagation delay time |
| βP,n(X) | The execution time of the task xp in the cloudlet cn |
| ST(X) | The maximal execution time of the task in the cloudlet cn |
| The energy consumption of the idle VMs (Virtual Machines) | |
| The energy consumption of the active VMs | |
| Ec(X) | The energy consumption of the cloudlets |
| E(X) | The total energy consumption |
| Parameter Description | Value |
|---|---|
| The total number of cloudlets | 50 |
| The maximum number of VMs a cloudlet owns | 10 |
| The transmission speed of AP | 540 M/s |
| The transmission speed of the cloudlet | 1200 M/s |
| The execution speed of the VMs | 2000 MHz |
| The power rate of the active VMs | 50 W |
| The power rate of the idle VMs | 30 W |
| The power rate of the cloudlets | 300 W |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, Z.; Gu, R.; Huang, T.; Xiang, H.; Zhang, X.; Qi, L.; Xu, X. An IoT-Oriented Offloading Method with Privacy Preservation for Cloudlet-Enabled Wireless Metropolitan Area Networks. Sensors 2018, 18, 3030. https://doi.org/10.3390/s18093030
Xu Z, Gu R, Huang T, Xiang H, Zhang X, Qi L, Xu X. An IoT-Oriented Offloading Method with Privacy Preservation for Cloudlet-Enabled Wireless Metropolitan Area Networks. Sensors. 2018; 18(9):3030. https://doi.org/10.3390/s18093030
Chicago/Turabian StyleXu, Zhanyang, Renhao Gu, Tao Huang, Haolong Xiang, Xuyun Zhang, Lianyong Qi, and Xiaolong Xu. 2018. "An IoT-Oriented Offloading Method with Privacy Preservation for Cloudlet-Enabled Wireless Metropolitan Area Networks" Sensors 18, no. 9: 3030. https://doi.org/10.3390/s18093030





