A PUF- and Biometric-Based Lightweight Hardware Solution to Increase Security at Sensor Nodes
Abstract
:1. Introduction
- The proposal of sensor nodes authenticated by their physical identity and the physical presence of their users.
- A low-cost solution that uses the SRAM PUF of the sensor node to prove the physical identity of the node, to obfuscate secret keys, and to obtain the nonces of the proposed communication protocol.
- The proposal of a lightweight fingerprint recognition solution that proves the physical presence of the user and that protects biometric data with the PUF response at the sensor node.
- Experimental results showing that the proposed solutions can be implemented in low-cost hardware platforms.
2. Application Scenarios
2.1. Sensor Nodes in the Industrial Internet of Things (IIoT)
2.2. Sensor Nodes Used for Regulation Compliance
2.3. Sensor Nodes into Soldier Uniforms
2.4. Sensor Nodes Used for Arms Control
3. Trusted Sensor Nodes Based on SRAM PUFs
3.1. Physical Identities of Sensor Nodes Based on SRAM PUFs
3.2. A Low-Cost Solution to Obfuscate Sensitive Information through SRAM PUFs
4. Novel Biometric Sensor Nodes Using QFM-Based Fingerprint Features
4.1. Orientation Computation and Quality Estimation
4.2. Alignment
4.3. Feature Extraction
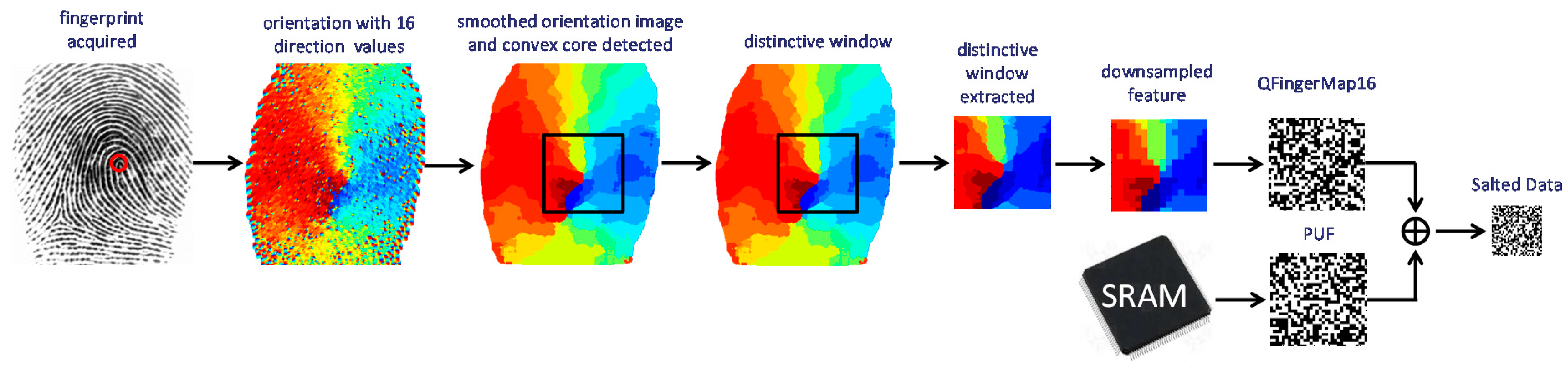
4.4. A Low-Cost Solution to Obfuscate Sensitive Fingerprint Information at Sensor Nodes
5. Lightweight Protocol to Authenticate Sensor Nodes by Dual-Factor
- represents the plaintext data “a” concatenated with the plaintext data “b”.
- represents the plaintext data “c” encrypted by the key “K” using, for example, the block cipher AES (Advanced Encryption Standard). AES was approved in 2001 as a US federal standard (FIPS PUB 197) and then, it was included in the ISO/IEC 18033-3 standard. Hence, AES is the dominant symmetric-key algorithm in many commercial applications and it is included as hardware module in many sensor node microcontrollers.
- represents a randomly initialized index which increases by 1 both in the sensor and the base station simultaneously after each message exchange is successfully completed.
- and represents, respectively, the random seed generated by the base station and the sensor, which are used to derive the new key from the old key .
- h (x,E) refers to a cryptographic hash function approved by NIST and “E” is the identifier of the network.
6. Experimental Results and Discussion
6.1. Trusted Sensor Nodes Based on SRAM PUFs
6.2. Dual-Factor Authenticated Sensor Nodes
6.3. Implementation Results
6.4. Security and Privacy
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Chen, X.; Makki, K.; Yen, K.; Pissinou, N. Sensor Network Security: A Survey. IEEE Commun. Surv. Tutor. 2009, 11, 52–73. [Google Scholar] [CrossRef]
- Samyde, D.; Skorobogatov, S.; Anderson, R.; Quisquater, J.-J. On a New Way to Read Data from Memory. In Proceedings of the 1st International IEEE Security in Storage Workshop (SISW), Greenbelt, MD, USA, 11 December 2002; pp. 65–69. [Google Scholar]
- ARM. Building a Secure System Using Trust Zone Technology; Technical Report; ARM: Cambridge, UK, 2009. [Google Scholar]
- Azema, J.; Fayad, G. M-Shield Mobile Security Technology: Making Wireless Secure; Technical Report; Texas Instruments: Dallas, TX, USA, 2008. [Google Scholar]
- Intel Software Guard Extensions (Intel SGX). Available online: https://software.intel.com/en-us/sgx (accessed on 23 July 2018).
- Schwarz, M.; Weiser, S.; Gruss, D. Malware Guard Extension: Using SGX to Conceal Cache Attacks. 2017. Available online: https://arxiv.org/pdf/1702.08719.pdf (accessed on 23 July 2018).
- Maes, R. PUF-Based Entity Identification and Authentication. In Physically Unclonable Functions: Constructions, Properties and Applications; Springer: Berlin,/Heidelberg, Germany, 2013; pp. 117–141. [Google Scholar]
- Martínez-Rodríguez, M.C.; Prada-Delgado, M.A.; Brox, P.; Baturone, I. VLSI Design of Trusted Virtual Sensors. Sensors 2018, 18, 347. [Google Scholar] [CrossRef] [PubMed]
- Baturone, I.; Prada-Delgado, M.A.; Eiroa, S. Improved Generation of Identifiers, Secret Keys, and Random Numbers from SRAMs. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2653–2668. [Google Scholar] [CrossRef]
- Dodis, Y.; Ostrovsky, R.; Reyzin, L.; Smith, A. Fuzzy extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data. SIAM J. Comput. 2008, 38, 97–139. [Google Scholar] [CrossRef]
- Guajardo, J.; Kumar, S.; Schrijen, G.; Tuyls, P. FPGA intrinsic PUFs and their use for IP protection. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems (CHES), Vienna, Austria, 10–13 September 2007; pp. 63–80. [Google Scholar]
- Malasri, K.; Wang, L. Design and Implementation of a Secure Wireless Mote-Based Medical Sensor Network. Sensors 2009, 9, 6273–6297. [Google Scholar] [CrossRef] [PubMed]
- Nieto, A.; Rios, R.; Lopez, J. IoT-Forensics Meets Privacy: Towards Cooperative Digital Investigations. Sensors 2018, 18, 492. [Google Scholar] [CrossRef] [PubMed]
- Jain, A.K.; Ross, A.A.; Nandakumar, K. Introduction to Biometrics: A Textbook; Springer: New York, NY, USA, 2011. [Google Scholar]
- Maltoni, D.; Maio, D.; Jain, A.; Prabhakar, S. Handbook of Fingerprint Recognition, 2nd ed.; Springer: London, UK, 2009. [Google Scholar]
- Campisi, P. Security and Privacy in Biometrics; Springer: London, UK, 2013. [Google Scholar]
- Kindt, E.J. Privacy and Data Protection Issues of Biometric Applications; Springer: Dordrecht, The Netherlands, 2013. [Google Scholar]
- Jin, A.T.B.; Ling, D.N.C.; Goh, A. Biohashing: Two Factor Authentication Featuring Fingerprint Data and Tokenised Random Number. Pattern Rcognit. 2004, 37, 2245–2255. [Google Scholar] [CrossRef]
- Maes, R.; van der Leest, V.; van der Sluis, E.; Willems, F. Secure Key Generation from Biased PUFs. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems (CHES), Saint-Malo, France, 13–16 September 2015; pp. 517–534. [Google Scholar]
- Prada-Delgado, M.A.; Vazquez-Reyes, A.; Baturone, I. Physical Unclonable Keys for Smart Lock Systems using Bluetooth Low Energy. In Proceedings of the 42nd Annual Conference of the IEEE Industrial Electronics Society (IECON), Florence, Italy, 23–26 October 2016; pp. 4808–4813. [Google Scholar]
- Bösch, C.; Guajardo, J.; Sadeghi, A.-R.; Shokrollahi, J.; Tuyls, P. Efficient Helper Data Key Extractor on FPGAs. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems (CHES), Washington, DC, USA, 10–13 August 2008; pp. 181–197. [Google Scholar]
- Daugman, J. The importance of being random: Statistical Principles of Iris Recognition. Pattern Rcognit. 2003, 36, 279–291. [Google Scholar] [CrossRef]
- Jain, A.K.; Prabhakar, S.; Hong, L.; Pankanti, S. Filterbank-based Fingerprint Matching. IEEE Trans. Image Process. 2000, 9, 846–859. [Google Scholar] [CrossRef] [PubMed]
- Nanni, L.; Lumini, A. Descriptors for Image-based Fingerprint Matchers. Expert Syst. Appl. 2009, 36, 12414–12422. [Google Scholar] [CrossRef]
- Jabid, T.; Kabir, M.H.; Chae, O. Local directional pattern (LDP)—A Robust Image Descriptor for Object Recognition. In Proceedings of the 7th IEEE International Conference on Advanced Video Signal Based Surveillance, Boston, MA, USA, 29 August–1 September 2010; pp. 482–487. [Google Scholar]
- Imamverdiyev, Y.; Teoh, A.; Kim, J. Biometric Cryptosystem based on Discretized Fingerprint Texture descriptors. Expert Syst. Appl. 2013, 40, 1888–1901. [Google Scholar] [CrossRef]
- Arjona, R.; Baturone, I. A fingerprint biometric cryptosystem in FPGA. In Proceedings of the IEEE International Conference on Industrial Technology (ICIT), Seville, Spain, 17–19 March 2015; pp. 1554–1559. [Google Scholar]
- Oliveira, M.A.; Leite, N.J. A Multiscale Directional Operator and Morphological Tools for Reconnecting Broken Ridges in Fingerprint Images. Pattern Rcognit. 2008, 41, 367–377. [Google Scholar] [CrossRef]
- Arjona, R.; Baturone, I. A Hardware Solution for Real-Time Intelligent Fingerprint Acquisition. J. Real Time Image Process. 2014, 9, 95–109. [Google Scholar] [CrossRef]
- Ghuneim, A.G. Moore-Neighbor Tracing. Available online: http://www.imageprocessingplace.com/downloads_V3/root_downloads/tutorials/contour_tracing_Abeer_George_Ghuneim/moore.html (accessed on 23 July 2018).
- Juels, A.; Wattenberg, M. A Fuzzy Commitment Scheme. In Proceedings of the 6th ACM Conference on Computer and Communications Security (CCS), Singapore, 1–4 November 2009; pp. 28–36. [Google Scholar]
- Barker, E.; Roginsky, A. Recommendation for Cryptographic Key Generation; NIST Special Publication; U.S. Department of Commerce: Washington, DC, USA, 2012; pp. 1–26.
- Grassi, P.A.; Newton, E.M.; Perlner, R.A.; Regenscheid, A.R.; Burr, W.E.; Richer, J.P.; Lefkovitz, N.B.; Danker, J.M.; Choong, Y.-Y.; Greene, K.; et al. Digital Identity Guidelines: Authentication and Lifecycle Management; NIST Special Publication 800-63B; Department of Commerce: Washington, DC, USA, 2017. Available online: https://doi.org/10.6028/NIST.SP.800-63b (accessed on 23 July 2018).
- Arcenegui, J.; Arjona, R.; Baturone, I. Demonstrator of a Fingerprint Recognition Algorithm into a Low-Power Microcontroller. In Proceedings of the IEEE Conference on Design and Architectures for Signal and Image Processing (DASIP), Dresden, Germany, 27–29 September 2017. [Google Scholar]
- He, Y.; Tian, J.; Li, L.; Chen, H.; Yang, X. Fingerprint Matching based on Global Comprehensive Similarity. IEEE Trans. Pattern Anal. Mach. Intell. 2006, 28, 850–862. [Google Scholar] [PubMed]
- Yang, S.; Sakiyama, K.; Verbauwhede, I.M. Efficient and Secure Fingerprint Verification for Embedded Devices. EURASIP J. Adv. Signal Process. 2006, 1–11. [Google Scholar] [CrossRef]
- Fons, M.; Fons, F.; Cantó, E. FPGA-based Personal Authentication using Fingerprints. J. Signal Process. Syst. 2012, 66, 153–189. [Google Scholar] [CrossRef]
- Chao, G.; Lee, S.; Lai, H.; Horng, S. Embedded Fingerprint Verification System. In Proceedings of the 11th IEEE International Conference on Parallel and Distributed Systems (ICPADS), Fukuoka, Japan, 20–22 July 2005; pp. 1–5. [Google Scholar]
- Fons, M.; Fons, F.; Cantó, E. Fingerprint Image Processing Acceleration through Run-Time Reconfigurable Hardware. IEEE Trans. Circuits Syst. II Express Briefs 2010, 57, 991–995. [Google Scholar] [CrossRef]
- Chan, K.C.; Moon, Y.S.; Cheng, P.S. Fast Fingerprint Verification using Subregions of Fingerprint Images. IEEE Trans. Circuits Syst. Video Technol. 2004, 14, 95–101. [Google Scholar] [CrossRef]
- Barrenechea, M.; Altuna, J.; San Miguel, M. A low-cost FPGA-based Embedded Fingerprint Verification and Matching System. In Proceedings of the 5th Workshop on Intelligent Solutions in Embedded Systems (WISES), Leganes, Spain, 21–22 June 2007; pp. 1–10. [Google Scholar]
- ARM922T with AHB System-on-Chip Platform OS Processor Product Overview. 2007. Available online: http://docs-api-peg.northeurope.cloudapp.azure.com/assets/dvi0025/b/DVI0025.pdf (accessed on 23 July 2018).
- ARM Cortex-M3 Documentation. 2018. Available online: https://developer.arm.com/products/processors/cortex-m/cortex-m3 (accessed on 23 July 2018).
- ARM Cortex-M4 Documentation. 2018. Available online: https://developer.arm.com/products/processors/cortex-m/cortex-m4 (accessed on 23 July 2018).
- Göhringer, D.; Obie, J.; Hübner, M.; Becker, J. Impact of Task Distribution, Processor Configurations and Dynamic Clock Frequency Scaling on the Power Consumption of FPGA-based Multiprocessors. In Proceedings of the 5th International Workshop on Reconfigurable Communication Centric Systems-on-Chip (ReCoSoC), Karlsruhe, Germany, 17–19 May 2010. [Google Scholar]
- Hwang, D.D.; Verbauwhede, I. Design of Portable Biometric Authenticators-Energy, Performance, and Security Tradeoffs. IEEE Trans. Consum. Electron. 2004, 50, 1222–1231. [Google Scholar] [CrossRef]
- Senn, L.; Senn, E.; Samoyeau, C. Modelling the Power and Energy Consumption of NIOS II Softcores on FPGA. In Proceedings of the IEEE International Conference on Cluster Computing Workshops, Beijing, China, 24–28 September 2012; pp. 179–183. [Google Scholar]
- Intel StrongARM SA-1110 Microprocessor Brief Datasheet. 2000. Available online: https://www-s.acm.illinois.edu/sigembedded/old/projects/strongarm/documentation/SA-1110_DevManual.pdf (accessed on 23 July 2018).
- Johnston, A.H.; Weiss, G.M. Smartwatch-based Biometric Gait Recognition. In Proceedings of the 7th IEEE International Conference on Biometrics Theory, Applications and Systems (BTAS), Arlington, VA, USA, 8–11 September 2015; pp. 1–6. [Google Scholar]
- Kang, S.J.; Lee, S.Y.; Cho, H.I.; Park, H. ECG Authentication System Design based on Signal Analysis in Mobile and Wearable Devices. IEEE Signal Process. Lett. 2016, 23, 805–808. [Google Scholar] [CrossRef]
- Peng, G.; Zhou, G.; Nguyen, D.T.; Qi, X.; Yang, Q.; Wang, S. Continuous Authentication with Touch Behavioral Biometrics and Voice on Wearable Glasses. IEEE Trans. Hum.–Mach. Syst. 2017, 47, 404–416. [Google Scholar] [CrossRef]
- Li, J.; Liu, Y.; Nie, Z.; Qin, W.; Pang, Z.; Wang, L. An Approach to Biometric Verification Based on Human Body Communication in Wearable Devices. Sensors 2017, 17, 125. [Google Scholar] [CrossRef] [PubMed]
- Vitabile, S.; Conti, V.; Lentini, G.; Sorbello, F. An Intelligent Sensor for Fingerprint Recognition. In Proceedings of the Embedded and Ubiquitous Computing (EUC), Nagasaki, Japan, 6–9 December 2005; pp. 27–36. [Google Scholar]
- Lindoso, A.; Entrena, L.; Liu-Jiménez, J.; San Millán, E. Increasing Security with Correlation-based Fingerprint Matching. In Proceedings of the 41st Annual IEEE International Carnahan Conference on Security Technology, Ottawa, ON, Canada, 8–11 October 2007; pp. 37–43. [Google Scholar]
- Conti, V.; Vitabile, S.; Vitello, G.; Sorbello, F. An Embedded Biometric Sensor for Ubiquitous Authentication. In Proceedings of the AEIT Annual Conference, Mondello, Italy, 3–5 October 2013. [Google Scholar]











| Proposal | Platform | Freq. (MHz) | Extraction Time (s) | Matching Time (s) | Power (mW) |
|---|---|---|---|---|---|
| QFM | ARM Cortex-M3 | 120 | 2.21 | 2.62 × 10−4 | 1.32 |
| QFM | ARM Cortex-M4 | 204 | 1.12 | 1.46 × 10−4 | 2.50 |
| Minutiae [37] | ARM922T | 200 | 15.74 | 280.01 | 180 |
| Minutiae [38] | NIOS | 33 | 55.88 | 0.15 | >200 |
| Minutiae [39] | Microblaze | 100 | 2.65 | 140.04 | >269 |
| Minutiae [40] | Strong ARM SA-1110 | 206 | 0.56 | 0.01 | <400 |
| Minutiae [41] | LEON2 without FPU | 50 | 157 | 51 | 500 |
| Minutiae [36] | LEON2 with FPU | 50 | 9.04 | 0.067 | 500 |
| DB | FVC 2000 DB2a | FVC 2002 DB1a | |
|---|---|---|---|
| 3 samples in enrollment. 2 samples in verification. 2 fingers | EER (%) | 0.04 | 0.22 |
| Proposal | No. Individuals | Error Rate (%) |
|---|---|---|
| Gait [49] | 59 | EER = 2.6 |
| Electrocardiogram [50] | 28 | FMR = 5.2, FNMR = 1.9 |
| Touch Behavioral and Voice [51] | 32 | EER = 9–16.6 for touch behavioral |
| EER = 4.88 for voice | ||
| Human Body Communication [52] | 10 | EER = 7.06 |
| Fingerprint (one finger) [36] | 10 | FMR < 0.1, FNMR = 1 |
| Fingerprint (one finger) [53] | 96 | FMR = 1.07, FNMR = 8.33 |
| Fingerprint (one finger) [54] | 100 | EER = 8 (FVC 2000 DB2a) |
| Fingerprint (one finger) [55] | 10 | FMR = 1.52, FNMR = 20.35 (FVC 2002 DB2) |
| This work (two fingers) | 50 | EER = 0.04 (FVC 2000 DB2a) |
| EER = 0.22 (FVC 2002 DB1a) |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Arjona, R.; Prada-Delgado, M.Á.; Arcenegui, J.; Baturone, I. A PUF- and Biometric-Based Lightweight Hardware Solution to Increase Security at Sensor Nodes. Sensors 2018, 18, 2429. https://doi.org/10.3390/s18082429
Arjona R, Prada-Delgado MÁ, Arcenegui J, Baturone I. A PUF- and Biometric-Based Lightweight Hardware Solution to Increase Security at Sensor Nodes. Sensors. 2018; 18(8):2429. https://doi.org/10.3390/s18082429
Chicago/Turabian StyleArjona, Rosario, Miguel Ángel Prada-Delgado, Javier Arcenegui, and Iluminada Baturone. 2018. "A PUF- and Biometric-Based Lightweight Hardware Solution to Increase Security at Sensor Nodes" Sensors 18, no. 8: 2429. https://doi.org/10.3390/s18082429
APA StyleArjona, R., Prada-Delgado, M. Á., Arcenegui, J., & Baturone, I. (2018). A PUF- and Biometric-Based Lightweight Hardware Solution to Increase Security at Sensor Nodes. Sensors, 18(8), 2429. https://doi.org/10.3390/s18082429





