Transmitting Pulse Encoding for Beyond-PRT Retransmitting Deception Jamming Detection in Spaceborne Synthetic Aperture Radar (SAR)
Abstract
:1. Introduction
2. Spaceborne SAR Beyond-PRT RDJ Model
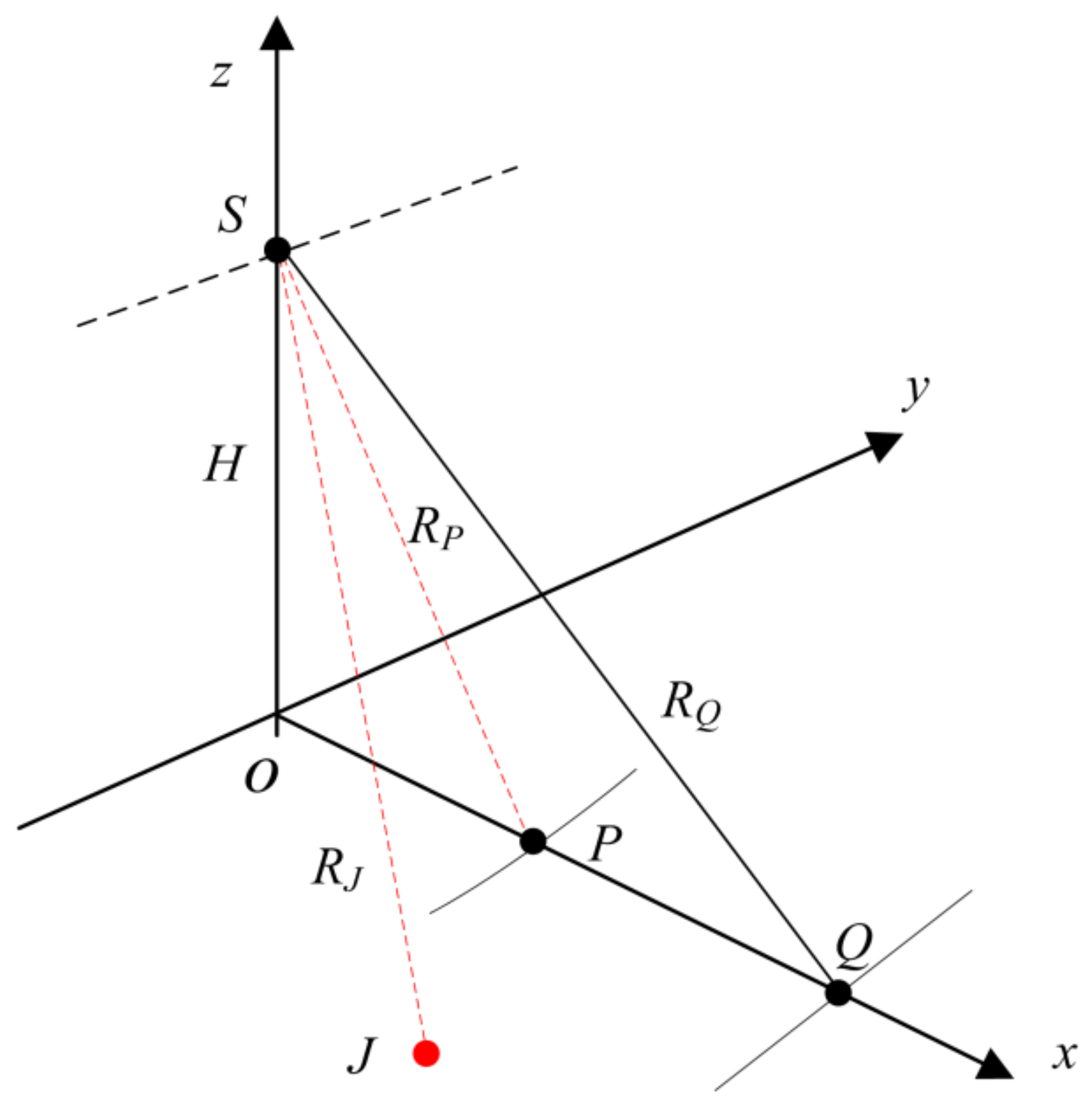
2.1. Geometry Model
2.2. Signal Model
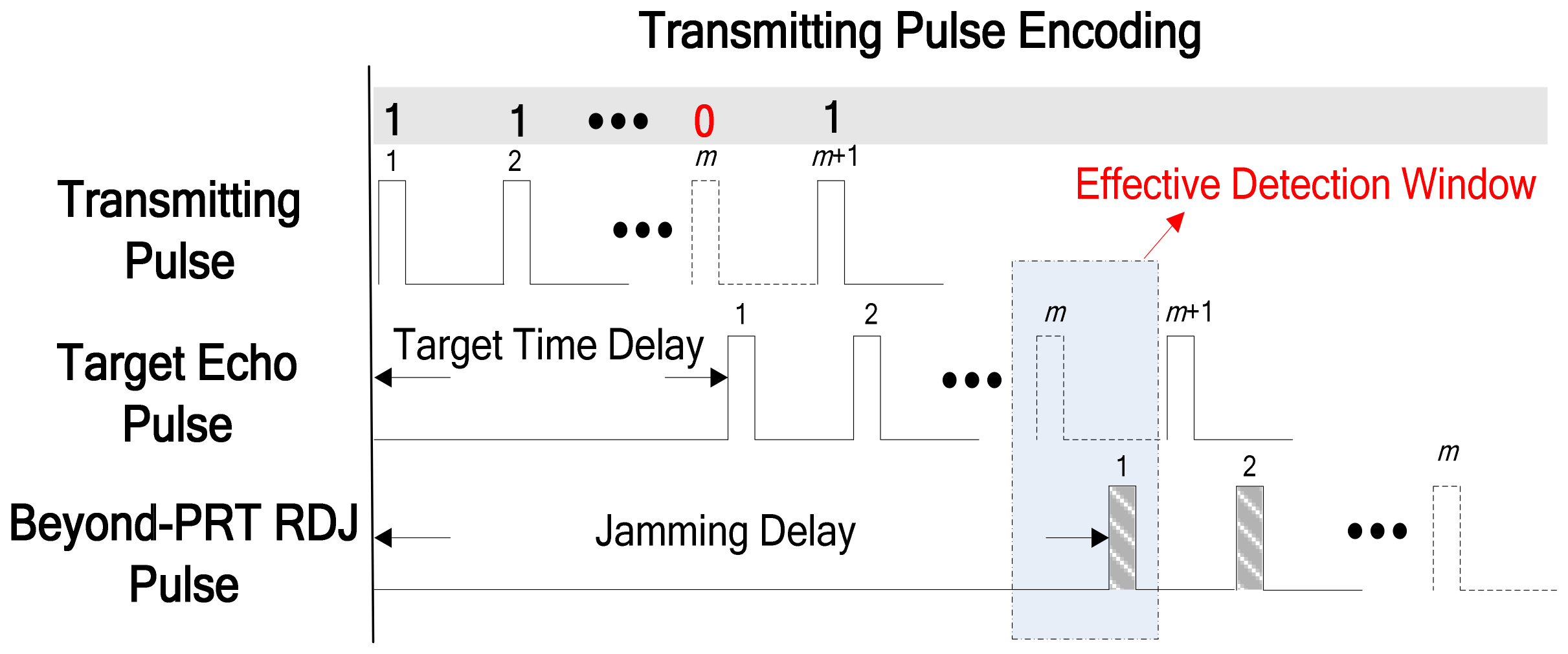
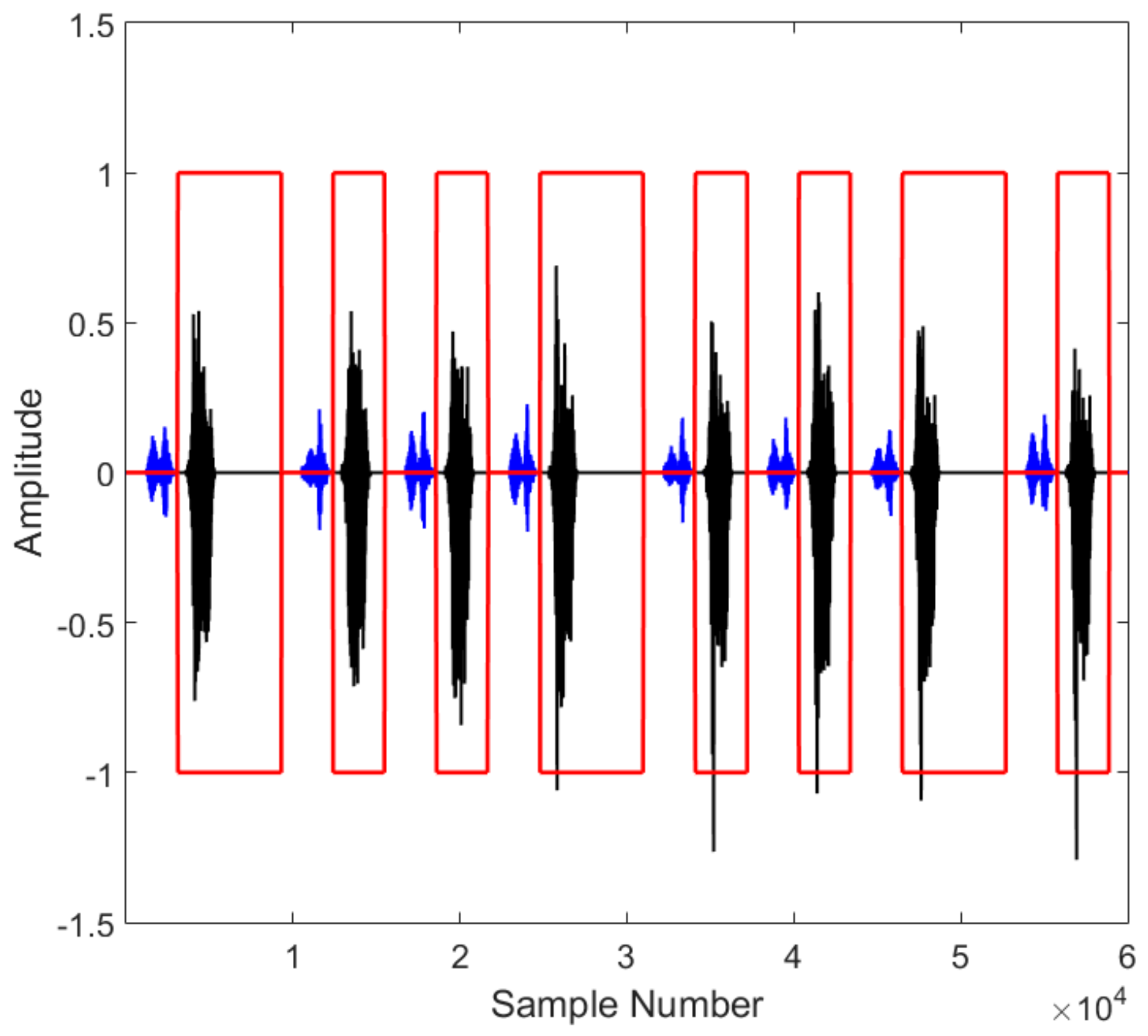
2.3. Example of Transmitting Pulse Encoding
3. Transmitting Pulse Encoding Method and Analysis of Encoding Efficiency
3.1. Encoding Method
- Step 1: Initialization of transmitting code T and jamming code WJ.Let d = 0 and T = B(d) which converts d from decimal to binary. Let WJ = T.
- Step 2: Right-shift operation on jamming code WJ.
- Step 3: Exclusive OR operation of WJ and T.
- Step 4: Obtaining the beyond-PRT RDJ detection result WD.
- Step 5: Judging the effectiveness of transmitting code T.
- Step 6: Determining the optimum transmitting pulse codes.
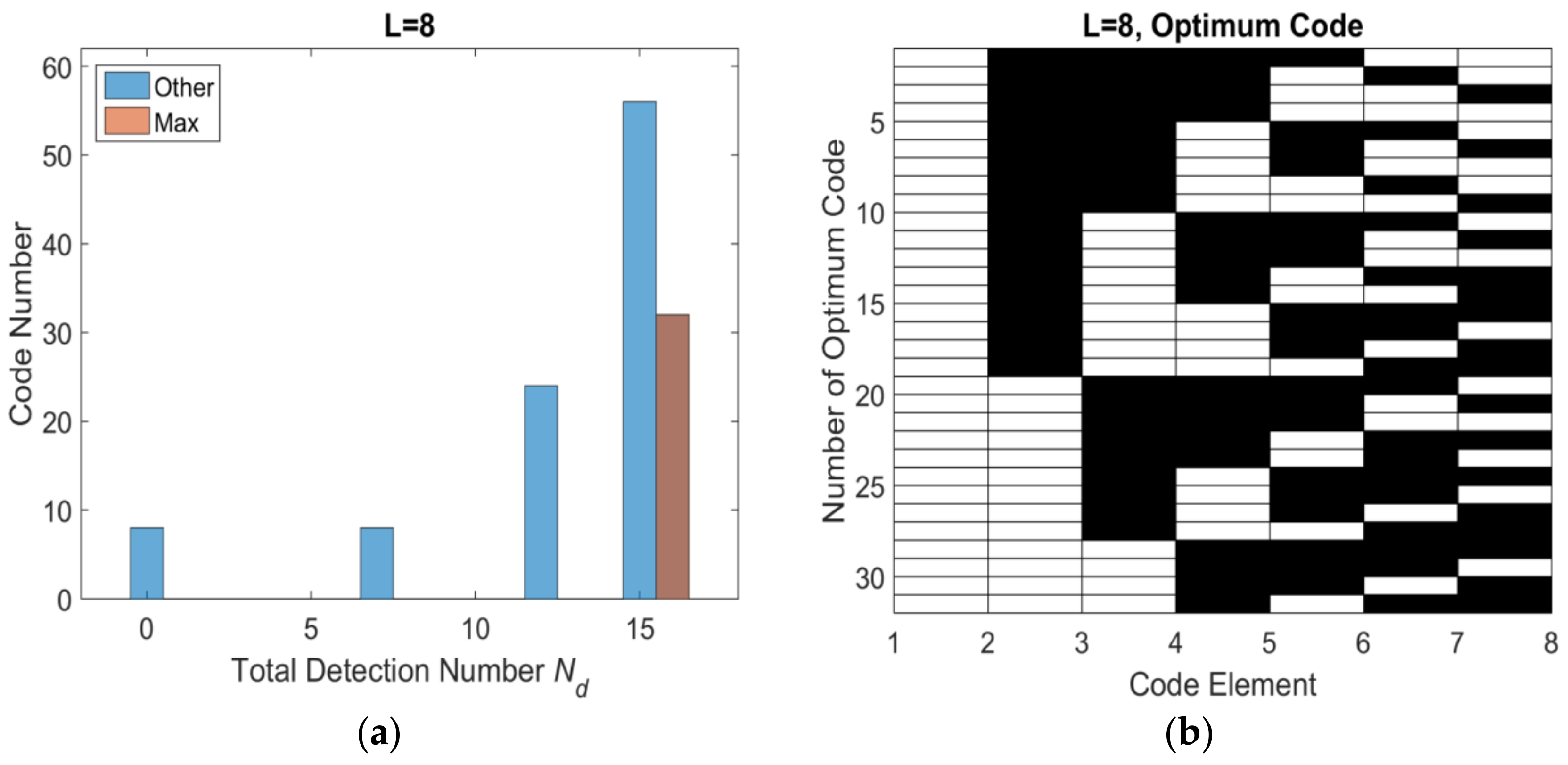
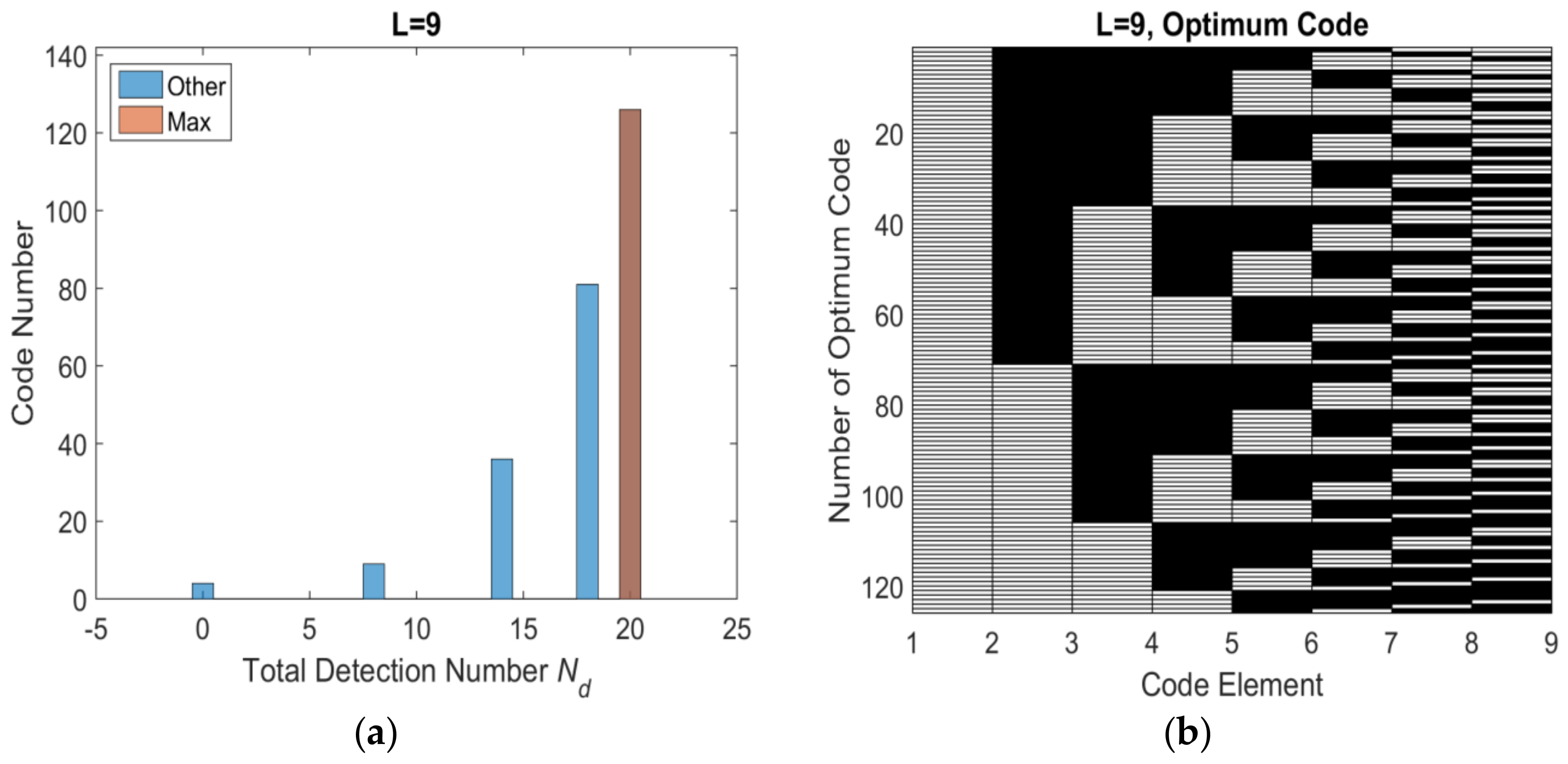
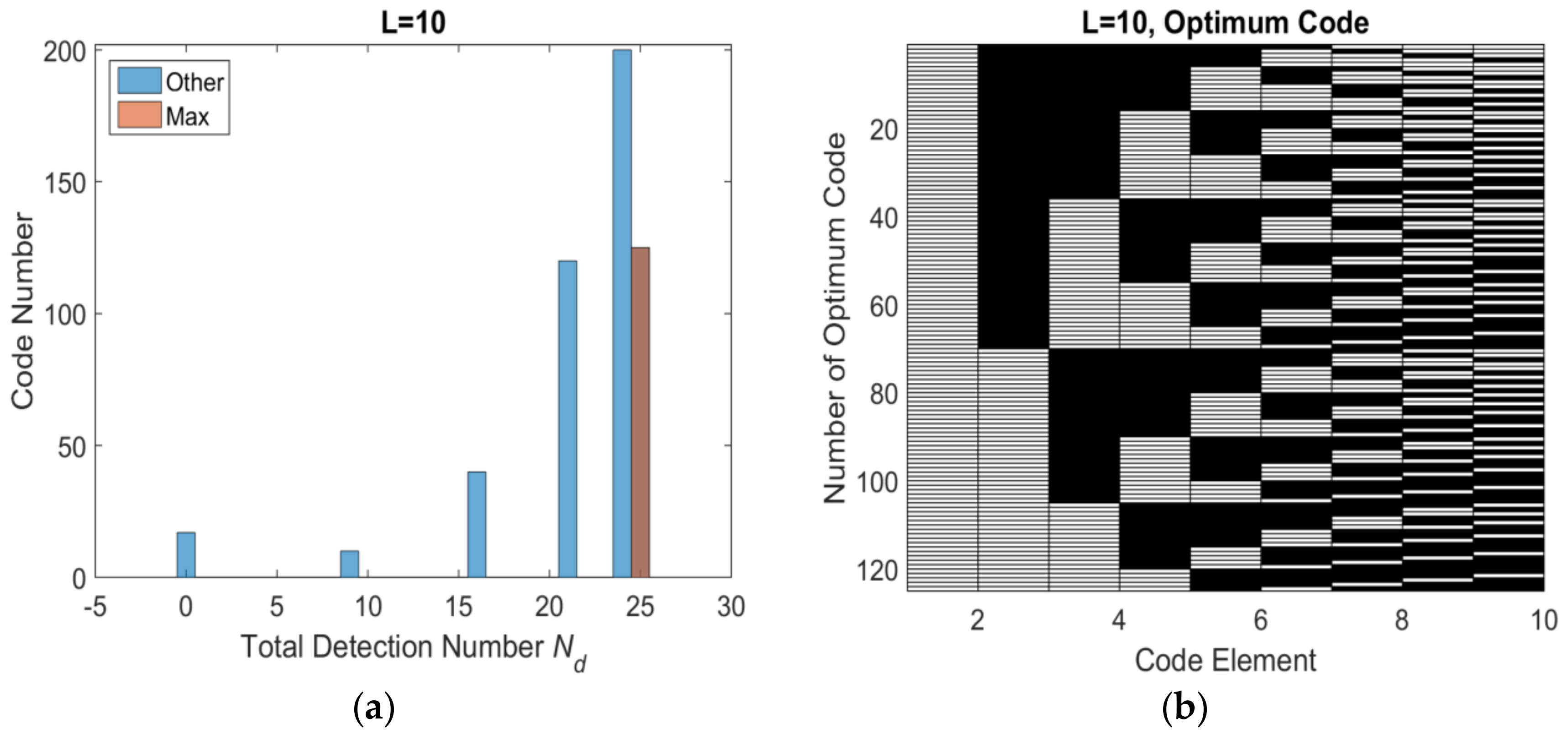
3.2. Encoding Efficiency Analysis
3.3. Detection Threshold
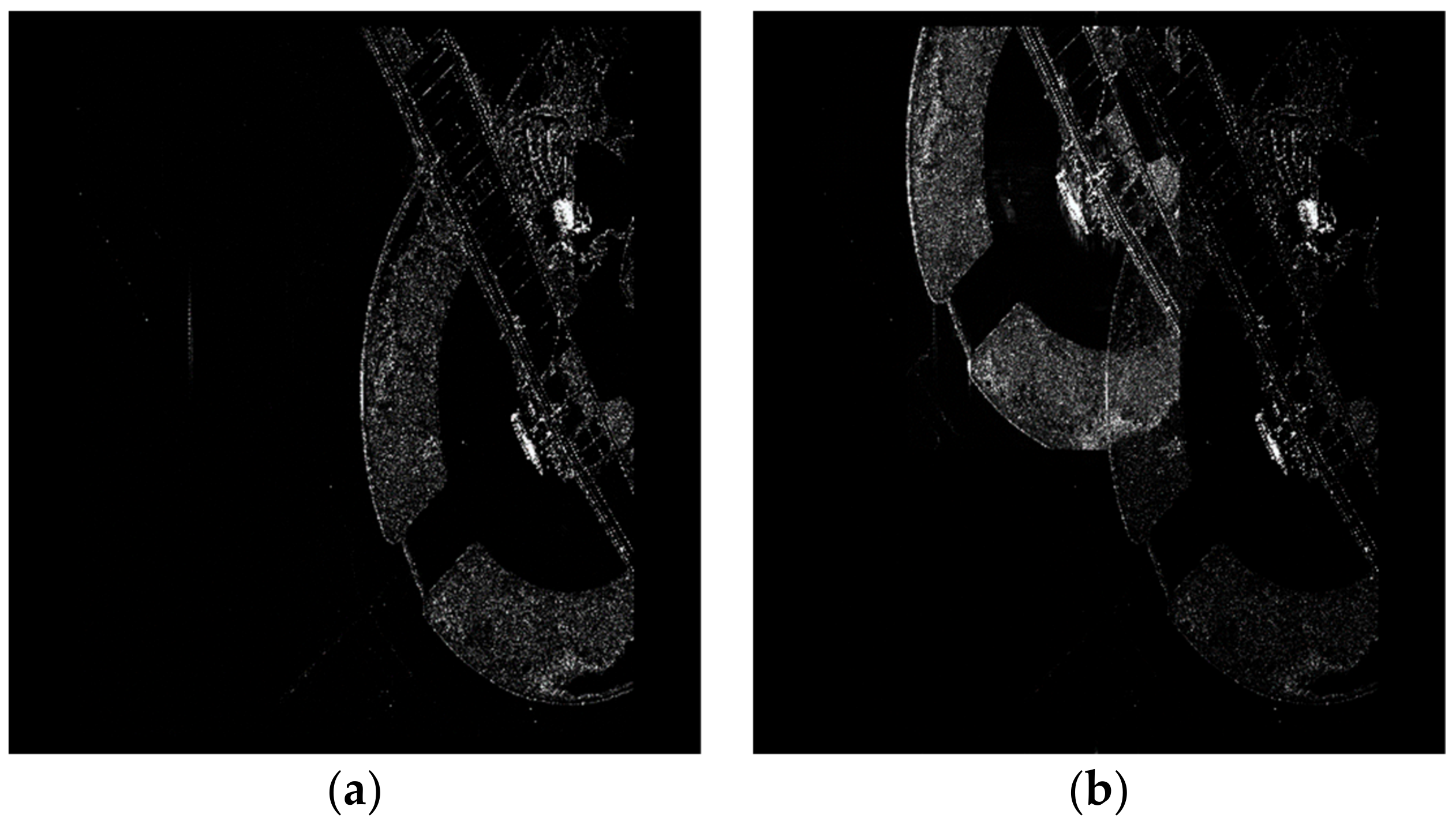
4. Simulation
5. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Breit, H.; Fritz, T.; Balss, U.; Lachaise, M.; Niedermeier, A.; Vonavka, M. TerraSAR-X SAR processing and products. IEEE Trans. Geosci. Remote Sens. 2010, 48, 727–740. [Google Scholar] [CrossRef]
- Zhao, B.; Zhou, F.; Bao, Z. Deception jamming for squint SAR based on multiple receivers. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2015, 8, 3988–3998. [Google Scholar] [CrossRef]
- Zhao, B.; Zhou, F.; Tao, M.; Zhang, Z.; Bao, Z. Improved method for synthetic aperture radar scattered wave deception jamming. IET Radar Sonar Navig. 2014, 8, 971–976. [Google Scholar] [CrossRef]
- Huang, L.; Dong, C.; Shen, Z.; Zhao, G. The influence of rebound jamming on SAR GMTI. IEEE Trans. Geosci. Remote Sens. 2015, 12, 399–403. [Google Scholar] [CrossRef]
- Xu, H.; Wu, Z.; Liu, W.; Li, J.; Feng, Q. Analysis of the effect of interference on InSAR. IEEE Sens. J. 2015, 15, 5659–5668. [Google Scholar] [CrossRef]
- Zhou, F.; Xing, M.; Bai, X.; Sun, G.; Bao, Z. Narrow-band interference suppression for SAR based on complex empirical mode decomposition. IEEE Trans. Geosci. Remote Sens. 2009, 6, 423–427. [Google Scholar] [CrossRef]
- Vu, V.T.; Sjogren, T.K.; Pettersson, M.I.; Hakansson, L.; Gustavsson, A.; Ulander, L.M.H. RFI suppression in ultrawideband SAR using an adaptive line enhancer. IEEE Trans. Geosci. Remote Sens. 2010, 7, 694–698. [Google Scholar] [CrossRef]
- Zhou, F.; Tao, M.; Bai, X.; Liu, J. Narrow-band interference suppression for SAR based on independent component analysis. IEEE Trans. Geosci. Remote Sens. 2013, 51, 4952–4960. [Google Scholar] [CrossRef]
- Potsis, A.; Reigber, A.; Sutor, T.; Papathanassiou, K.P. A phase preserving method for RF interference suppression in P-band synthetic aperture radar interferometric data. In Proceedings of the IEEE 1999 International, Hamburg, Germany, 28 June–2 July 1999; pp. 2655–2657. [Google Scholar] [CrossRef]
- Zhang, S.X.; Xing, M.D.; Guo, R. Interference suppression algorithm for SAR based on time-frequency transform. IEEE Trans. Geosci. Remote Sens. 2011, 49, 3765–3779. [Google Scholar] [CrossRef]
- Sergio, B.; Anna, S. Adaptive time-varying cancellation of wideband interference in spread-spectrum communications based on time-frequency distributions. IEEE Trans. Signal Process. 1999, 47, 957–965. [Google Scholar] [CrossRef]
- Stankovic, L.J.; Thayaparan, T.; Dakovic, M. Signal decomposition by using the S-method with application to the analysis of HF radar signals in sea-clutter. IEEE Trans. Signal Process. 2006, 54, 4332–4342. [Google Scholar] [CrossRef]
- Li, D.; Liu, H.; Yang, L. Efficient time-varying interference suppression method for synthetic aperture radar imaging based on timefrequency reconstruction and mask technique. IET Radar Sonar Navig. 2015, 9, 827–834. [Google Scholar] [CrossRef]
- Zhou, F.; Tao, M. Research on methods for narrow-band interference suppression in synthetic aperture radar data. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2015, 8, 3476–3485. [Google Scholar] [CrossRef]
- Tao, M.; Zhou, F.; Zhang, Z. Wideband interference mitigation in high-resolution airborne synthetic aperture radar data. IEEE Trans. Geosci. Remote Sens. 2016, 54, 74–87. [Google Scholar] [CrossRef]
- Wang, R.; Chen, J.; Wang, X.; Sun, B. High-performance antiretransmission deception jamming utilizing range direction multiple input and multiple output (mimo) synthetic aperture radar (sar). Sensors 2017, 17, 123. [Google Scholar] [CrossRef] [PubMed]
- Ferrell, B.H. Interference suppression in UHF synthetic aperture radar. In Algorithms for Synthetic Aperture Radar Imagery II; Lovas, L.A., Ed.; SPIE: Washington, DC, USA, 1995. [Google Scholar] [CrossRef]
- Suwa, K.; Wakayama, T. Spatially variant interference suppression method based on superresolution algorithm for synthetic aperture radar. In Algorithms for Synthetic Aperture Radar Imagery XVIII; SPIE: Washington, DC, USA, 2011. [Google Scholar] [CrossRef]
- Gebert, N.; Krieger, G. Azimuth phase center adaptation on transmit for high-resolution wide-swath SAR imaging. IEEE Trans. Geosci. Remote Sens. 2009, 6, 782–786. [Google Scholar] [CrossRef]
- Huang, P.-P.; Deng, Y.-K.; Xu, W.; Qi, W.-K. The research of multiple-input and multiple-output SAR based on frequency synthetic. J. Electron. Inform. Technol. 2011, 33, 401–406. [Google Scholar] [CrossRef]
- Song, X.F.; Willett, P.; Zhou, S.; Luh, P.B. The MIMO radar and jammer games. IEEE Trans. Signal Process. 2012, 60, 687–699. [Google Scholar] [CrossRef]
- Ma, X.; Qing, J.; He, Z. Three-channel cancellation of SAR blanketing jamming suppression. Acta Electron. Sin. 2007, 35, 1015–1020. [Google Scholar] [CrossRef]
- Wang, H.; Chen, C.; Han, F. A comparative analysis of adaptive beamforming algorithms for satellite multiple-beam antennas. Acta Electron. Sin. 2001, 29, 358–360. [Google Scholar] [CrossRef]
- Ciuonzo, D.; De Maio, A.; Orlando, D. A unifying framework for adaptive radar detection in homogeneous plus structured interference—Part II: Detectors design. IEEE Trans. Signal Process. 2016, 64, 2907–2919. [Google Scholar] [CrossRef]
- Dong, Y.; Liu, M.; Li, K.; Tang, Z.; Liu, W. Adaptive Direction Detection in Deterministic Interference and Partially Homogeneous Noise. IEEE Signal Process. Lett. 2017, 24, 599–603. [Google Scholar] [CrossRef]
- Ciuonzo, D.; De Maio, A.; Orlando, D. On the statistical invariance for adaptive radar detection in partially homogeneous disturbance plus structured interference. IEEE Trans. Signal Process. 2017, 65, 1222–1234. [Google Scholar] [CrossRef]





| Odd | Even | ||||
|---|---|---|---|---|---|
| L | Nd | Nbest | L | Nd | Nbest |
| 5 | 6 | 10 | 6 | 9 | 9 |
| 7 | 12 | 35 | 8 | 16 | 32 |
| 9 | 20 | 126 | 10 | 25 | 125 |
| 11 | 30 | 462 | 12 | 36 | 450 |
| 13 | 42 | 1716 | 14 | 49 | 1715 |
| 15 | 56 | 6435 | 16 | 64 | 6400 |
| 17 | 72 | 24,310 | 18 | 81 | 24,300 |
| 19 | 90 | 92,378 | 20 | 100 | 92,250 |
| Parameter | Value |
|---|---|
| Orbit Height | 680 km |
| Eccentricity | 0.01 |
| Orbit Inclination | 98 |
| Pitch Angle | 20° |
| Incident Angle | 23.8° |
| PRF | 2000 Hz |
| Band Width | 50 MHz |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, R.; Bing, S.; Wang, X.; Cheng, S. Transmitting Pulse Encoding for Beyond-PRT Retransmitting Deception Jamming Detection in Spaceborne Synthetic Aperture Radar (SAR). Sensors 2018, 18, 1666. https://doi.org/10.3390/s18051666
Wang R, Bing S, Wang X, Cheng S. Transmitting Pulse Encoding for Beyond-PRT Retransmitting Deception Jamming Detection in Spaceborne Synthetic Aperture Radar (SAR). Sensors. 2018; 18(5):1666. https://doi.org/10.3390/s18051666
Chicago/Turabian StyleWang, Ruijia, Sun Bing, Xing Wang, and Siyi Cheng. 2018. "Transmitting Pulse Encoding for Beyond-PRT Retransmitting Deception Jamming Detection in Spaceborne Synthetic Aperture Radar (SAR)" Sensors 18, no. 5: 1666. https://doi.org/10.3390/s18051666




