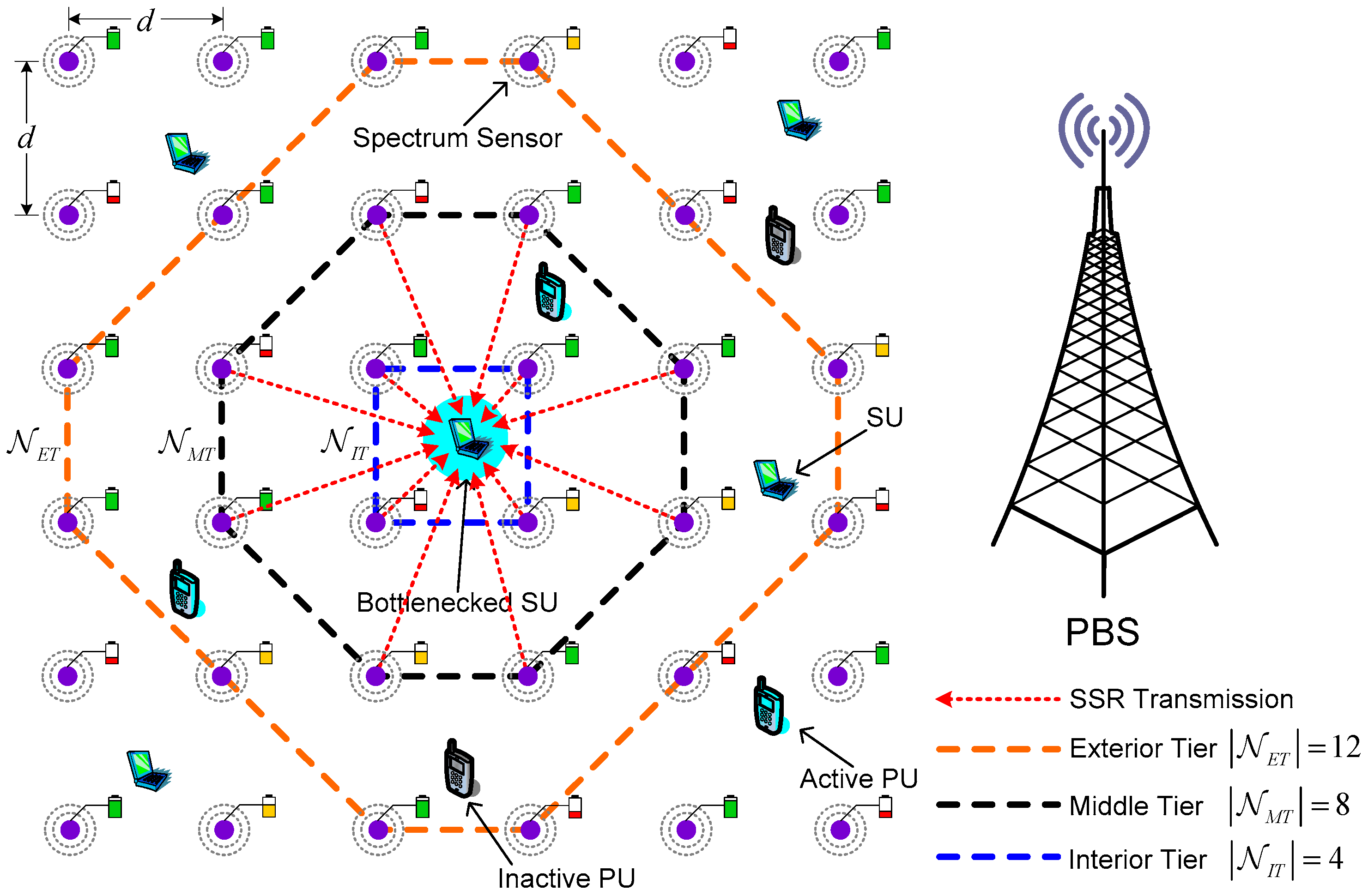
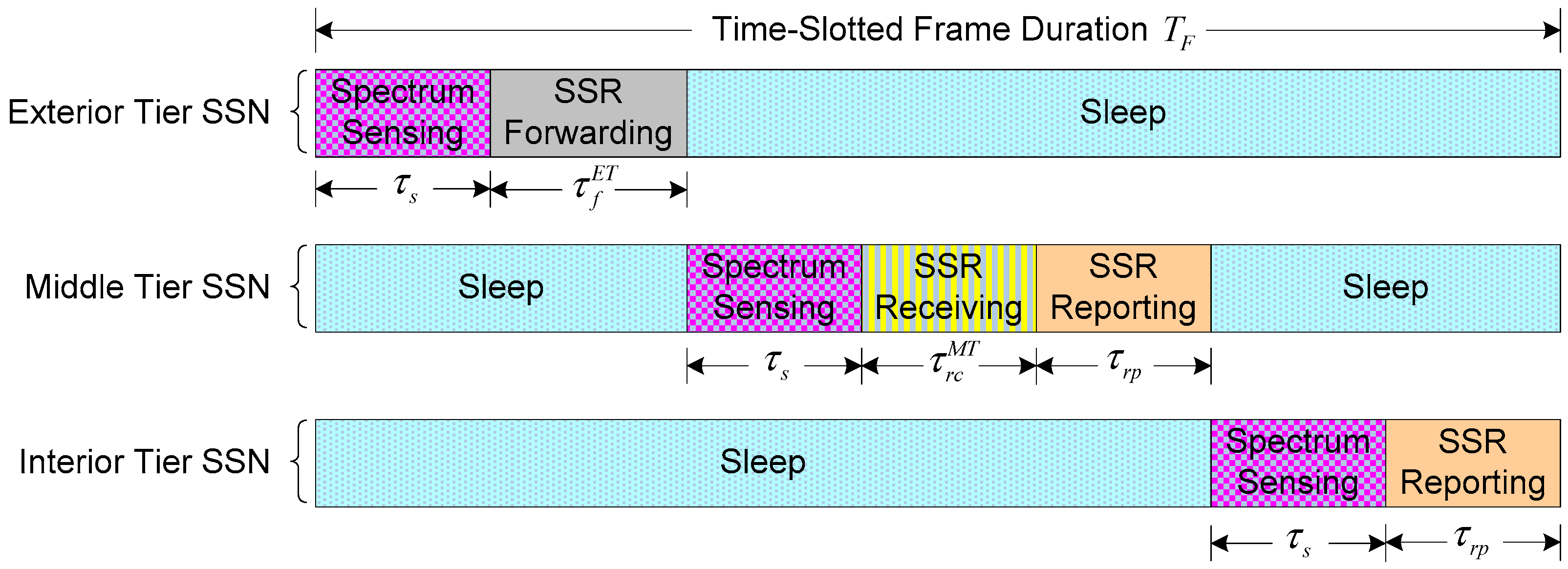
1. Introduction
Cognitive radio (CR) [
1] has newly emerged as a promising solution to improve the spectrum utilization by allowing unlicensed secondary users (SUs) to access the idle licensed spectrum. In a CR network (CRN), SUs can periodically sense the licensed spectrum and opportunistically access the spectrum holes or spectrum opportunities (SOPs) unoccupied by primary users (PUs). Most of the existing research efforts in CRNs mainly focus on the issues of the physical and MAC layers for an infrastructure-based single hop scenario, such as spectrum sensing, spectrum access and sharing techniques [
2,
3,
4]. In addition, SUs can also form a multi-hop ad hoc network without the support of infrastructure. In a cognitive radio ad hoc network (CRANET) [
5], SUs can only access the SOPs by seeking to underlay, overlay, or interweave their signals with those of the existing PUs without significantly impacting their communications.
Spectrum sensing is one of the key enabling technologies for the establishment of CRNs, because it constantly allows for the opportunistic identification and use of the SOPs from a licensed primary network without causing harmful interference to the PUs. In order to improve the sensing performance, collaborative spectrum sensing has been proposed as an effective way to reliably detect the activity of PUs by addressing the issues imposed by the hidden PU terminal problem and the wireless channel impairments, such as the heavy shadowing and fading [
6,
7,
8]. In this way, cooperation is achieved by allowing different SUs to collaborate and share their spectrum sensing results (SSR) through a fusion center (FC), which makes a global decision on the occupancy status of the licensed band. However, this centralized FC is not available in decentralized CRANETs. Clearly, each SU under this scenario must perform the distributed collaborative spectrum sensing, which is preferred to the centralized FC scheme because of its scalability, fault tolerance and flexibility [
9].
In order to facilitate the spectrum sensing functionality, high sampling rates, high resolution analog to digital converters with large dynamic range, and high speed signal processors are required to be incorporated into an individual SU transceiver [
10], which increases hardware cost and power consumption, especially for the double-radio sensing architecture of SU transceiver. An alternative approach is to adopt the cost-effective and dedicated spectrum sensor nodes (SSNs) that perform distributed collaborative spectrum sensing and report SSR to SUs acting as FCs in CRANETs [
11]. Technically, s wireless sensor network can be naturally exploited to assist a CRANET by providing SSR about the current spectrum occupancy of PUs in a cooperation fashion. The concept of sensor network embedded into CRANETs has further called sensor network-aided CRANETs (SN-CRNs), which has been considered as one of the most appealing approaches to perform cost-effective spectrum sensing in CR systems [
7,
11,
12].
Similar to most other traditional wireless networks or wireline Internet, network congestion in SN-CRNs will also occur when offered data load that exceed the available capacity of a SU due to buffer overflow caused by the data sequence of the SSR injected from SSNs together with the data traffic from upstream SUs. This therefore leads to energy consumption of SSNs, aggressive retransmission, queuing delay, and blocking of new flows from upstream SUs. Indubitably, a congestion control technique in the transport layer is essential to balance resource loads and avoid excessive congestion. However, the congestion control mechanism for the traditional Transmission Control Protocol (TCP) via the acknowledgement-triggered or window-based methods was initially designed and optimized to perform in reliable wired links with constrained bit error rates and round trip times (RTTs) [
13]. A recent study [
14] has reported that the performance of HTTP download deteriorates as much as about 40% under the TCP window control in an IEEE P1900.4 based cognitive wireless system by using User Datagram Protocol (UDP) and TCP transport protocols. On the other hand, some other research efforts about congestion control have also been conducted from the perspective of finding methods to modify the TCP protocol, such as TCP monitoring delayed acknowledgment, segment-based selective acknowledgement, TCP adaptive delayed-acknowledgment window, etc. [
15], aiming to accommodate the challenging multi-hop wireless environments. Unfortunately, it has been shown that these methods of TCP modification and extension cannot be directly applied into SN-CRNs due to sudden large-scale bandwidth fluctuation, periodic interruption caused by spectrum sensing and channel switching [
16].
Recently, there have also been previous works on congestion control for multi-hop CRANETs from a cross-layer design perspective. In [
17], an end-to-end congestion control framework was proposed under the constraint of the non-uniform channel availability by taking into account the interactions from the physical layer to the transport layer. In [
18], a cross-layer framework for joint optimization of MAC, scheduling, routing and congestion control was presented to maximize the throughput of a set of multi-hop end-to-end packet flows. However, the end-to-end control policy in [
17,
18] is ill suited for operation over wireless links characterized by higher RTTs. On the contrary, the hop-by-hop control reacts to congestion faster where the rates are adjusted at intermediate SUs by feedback information about the congestion state of congested SUs. A cross-layer framework to jointly achieve both congestion and power control through a non-convex optimization method was proposed in [
19]. In [
20], an optimization framework achieving tradeoff between energy efficiency and network utility maximization was devised, which can jointly balance interference, collision, and congestion among SUs by adjusting transmit power, persistence probability, together with data rate simultaneously via interaction between MAC and other layers. However, the proposed frameworks in [
19,
20] are just suited to mitigate the congestion caused by the data traffic from upstream SUs in multi-hop CRANETs, ignoring the impact of the data sequence of the SSR injected from SSNs on the congestion of SUs.
To the best of our knowledge, aside from some studies on congestion control for CRANETs as mentioned before, there is no related work reported in the literature related to congestion control over SN-CRNs. As a result, there is a strong motivation to explore congestion mitigation approach in SN-CRNs. Under this scenario, it is certainly not a surprise that the channel capacity between any SSN and FC is a concave function of the transmit power of this SSN and channel conditions [
21]. In principle, effective transmit power control strategies have been widely used to maximize the total system capacity in conventional celluar wireless networks while adapting to the changing channel and interference conditions. Recent research efforts have achieved the capacity and energy efficiency maximization by devising the optimal power allocation on subchannels in two-tier femtocell networks based on orthogonal frequency division multiple access (OFDMA) [
22], together with the optimal power control allocation and sensing time optimization in OFDMA cognitive small cell networks [
23]. In addition, the transmission rate of this SSN always depends on channel capacity and is also a function of the transmit power according to the Shannon channel theorem. Thus, the congestion at FC can be controlled and mitigated through the transmission rate adjustment with the help of an optimal power allocation policy for this SSN in the physical layer. During a time interval, the amount of bits of the data sequence of SSR transmitted from this SSN to FC also approximately depends on the channel capacity [
24]. For this observation it turns out that we can fully achieve the congestion mitigation for FC by reducing the amount of bits of the data sequence of the SSR transmitted from this SSN, aiming to release the capacity of the internal buffer for FC. In this paper, we propose a congestion mitigation approach by constructing a distributed power control framework for SSNs over the rectangular grid based SN-CRN. The main contributions of this paper are summarized as follows:
To evaluate the performance of local spectrum sensing, we present the relative divergence between the detection probability and the false alarm probability for each SSN under any uplink channel via the Kullback-Leibler divergence framework. By the aid of mathematical statistics, we obtain the detection probability and false alarm probability distributions for each SSN, and also model the stability metric of local spectrum sensing as the relative divergence by applying the entropy modeling framework.
We propose a distributed power control framework for SSNs from the interior tier (IT) and middle tier (MT) perspective in order to achieve the tradeoff between channel capacity and energy consumption. In particular, the power control problem is formulated as a differential game model by taking into account the utility function maximization together with the linear differential equation constraint with respect to energy consumption. We further present the theoretical results of the optimal solutions to this differential game model in a cooperative or noncooperative manner by using dynamic programming.
With the help of the proposed distributed power control framework, we attain the congestion mitigation for bottleneck SU by alleviating its buffer load over its internal buffer. We also rigorously analyze the impact of noncooperative and cooperative optimal transmit power for IT and MT SSNs on the internal buffer of bottleneck SU, respectively.
The rest of paper is organized as follows:
Section 2 describes the system model. In
Section 3, we present the spectrum sensing quality analysis method based on local spectrum sensing by SSNs. In
Section 4, we formulate the distributed power control for IT and MT SSNs as a differential game model, and derive the noncooperative and cooperative optimal solutions. The congestion mitigation approach for bottleneck SU is analyzed rigorously in
Section 5.
Section 6 presents the simulation results. Finally,
Section 7 concludes the paper.
3. Spectrum Sensing Quality Analysis
In this section, our objective is to analyze the spectrum sensing quality of each SSN via a local spectrum sensing model, aiming to provide the quantification result with the emphasis to evaluate the spectrum sensing performance of each SSN. More importantly, the analysis results will be employed to formulate the distributed power control framework for IT and MT SSNs. By revisiting Equations (9) and (10) in local spectrum sensing model, we can observe that the detection probability
in
and the false alarm probability
in
can be referred to the random variables for the
m-th SSN under the
k-th uplink channel due to the uncertainty of the presence and absence of the PU. It is worth noting that the errors in spectrum sensing for a SSN will be generally considered negligible due to imperfect spectrum sensing [
27], e.g., misdetection and false alarm caused by hardware capability of SSN and practical time-varying channel conditions. So the errors in spectrum sensing for a SSN will further incur the fact that different uplink channels will hold different probabilities of detection and false alarm. In particular, the higher the detection probability in
, the better the PUs are protected; the lower the false alarm probability in
, the more efficiently the uplink channel can be reutilized by SUs [
7]. Based on this observation, the higher the relative divergence between
and
, the better the performance of local spectrum sensing. It has been revealed that the Kullback–Leibler divergence is an effective measure of how one probability diverges from a second probability [
30]. Hence, the relative divergence between
and
for the
m-th SSN under the
k-th uplink channel can be defined as follows based on a Kullback–Leibler divergence framework:
With respect to the entire set of uplink channels, the relative divergence between
and
for the
m-th SSN can be denoted as:
It is noticeable that the relative divergence between the detection probability and the false alarm probability just reflects the performance of local spectrum sensing by each SSN. Viewed from the SU perspective, we are also interested in the impact of the SOP usage probability on the spectrum sensing quality. To this end, we characterize the spectrum sensing quality factor which can be expressed by a function of two parameters including the relative divergence between
and
along with the SOP usage probability
for bottleneck SU
b. Specifically, the spectrum sensing quality factor
of the
m-th SSN with respect to bottleneck SU
b can be defined as:
By using mathematical statistics theory, next we start by formulating the detection probability distribution and the false alarm probability distribution , which have been derived from Algorithm 1.
| Algorithm 1: Generation Procedure of Distribution and Distribution |
| 1: | Input: The detection probability set and the false alarm probability set . |
| 2: | Output: The detection probability distribution |
| | The false alarm probability distribution . |
| | The detection probability distribution generation: |
| 1: | Sort the detection probability in ascending order and constitute the sorted sequence as . |
| 2: | , for and . |
| 3: | Divide interval into equal subintervals, i.e., . |
| 4: | for do |
| 5: | . |
| 6: | Calculate the number of the detection probabilities within subinterval denoted by . |
| 7: | Calculate the probability . |
| 8: | end for |
| 9: | Return: . |
| | The false alarm probability distribution generation: |
| 1: | Sort the false alarm probability in ascending order and constitute the sorted sequence as . |
| 2: | , for and . |
| 3: | Divide interval into equal subintervals, i.e., . |
| 4: | for do |
| 5: | . |
| 6: | Calculate the number of the false alarm probabilities within subinterval denoted by . |
| 7: | Calculate the probability . |
| 8: | end for |
| 9: | Return: . |
Owing to the fact that the number of the detection probabilities or the false alarm probabilities is calculated under the constraint of
, it is clear that the distributions
and
fall into the complete probability distributions, i.e.,
and
. Apparently, the entropy paradigm should be used for a measure of the uncertainty associated with a random variable of a distribution in information theory [
31], and can be also applied to measure the uncertainty of the distributions
and
. As a result, for the
m-th SSN over the entire uplink channels, the uncertainty characterization of the distributions
and
can be respectively described as based on the entropy modeling framework:
In what follows, we are also interested in gaining a better understanding of how to apply this entropy measurement to evaluate the stability of local spectrum sensing. It should be admitted that the entropy tends to be larger when the change of the random variable values in given distribution is disorder or randomness [
32]. That is, a more disordered probability distribution will result in larger entropy. Thus, the better performance of spectrum sensing for the
m-th SSN will bring about the more ordered probability distributions
and
. In this way, the stability of the distributions
and
will decrease because of more disorder for the values of the detection probability and false alarm probability in the distributions
and
. Based on the insight, we model the stability metric of local spectrum sensing by the relative divergence between the entropy of the detection probability distribution and the entropy of the false alarm probability distribution. Thus, the stability metric of local spectrum sensing for the
m-th SSN over the entire uplink channels denoted by
can be calculated as follows:
5. Congestion Mitigation for Bottlenecked Secondary User
We have shown that the bottlenecked SU is a little more inclined to be a congested SU node during the slot
due to its buffer overflow under the scenario of the hop-by-hop fluid flows of the data sequence of the SSR injected from
IT and MT SSNs to this bottlenecked SU. We use the buffer size
to denote the buffer saturation value of bottlenecked SU
b. Recall that the amount of data traffic
in buffer of SU
b at time
evolves according to Equation (2) for the given slot
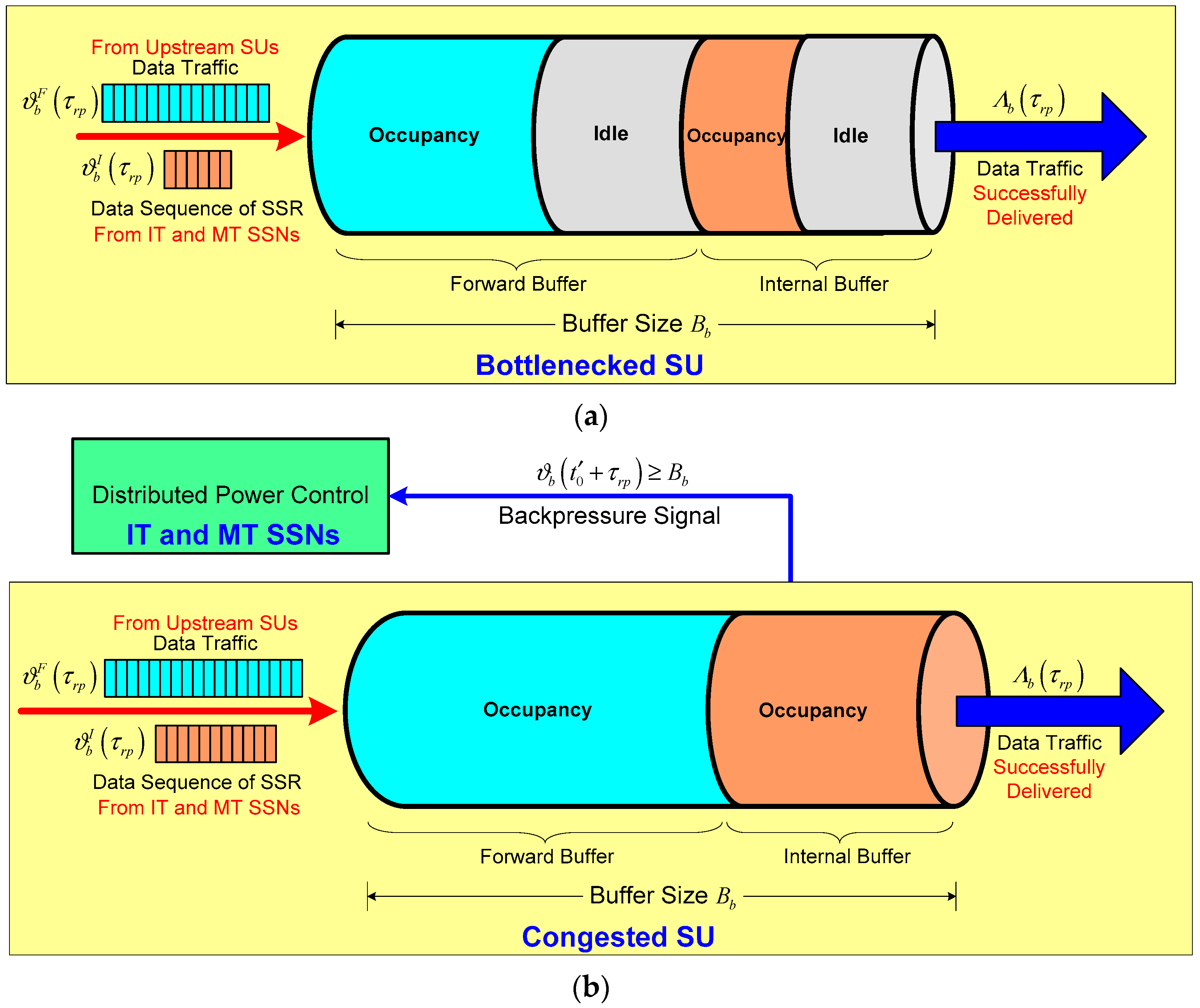
. As depicted in
Figure 3a, the buffer of bottlenecked SU
b is composed of two buffer segments, i.e., the forward buffer that holds data traffic injected from upstream SUs denoted by
, and the internal buffer that stores the data sequence of SSR transmitted from IT and MT SSNs denoted by
. Normally, there exist idle segments within the forward buffer or the internal buffer of bottlenecked SU
b when
. This phenomenon is referred to the normal status where the offered data load does not exceed available buffer capacity of bottleneck SU
b because of its higher data rate to deliver the amount of data traffic to other SUs and remove the amount of the data sequence of SSR during the slot
.
However, congestion in bottlenecked SU
b will occur when the offered data load exceeds its available buffer capacity due to buffer overflow imposed by the data load involving the data sequence of the SSR injected from IT and MT SSNs together with the data traffic from upstream SUs. We assume that the congestion detection information of bottlenecked SU
b can be transferred back to the
m-th SSN by means of a hop-by-hop backpressure signal via the CCC form bottlenecked SU
b to the
m-th SSN. As a result, bottlenecked SU
b is said to be a congested SU if and only if the amount of its current data traffic
during the slot
, as shown in
Figure 3b. We further assume that the
m-th SSN has the data sequence of the SSR with
bits to transmit at time
. According to [
24], the data sequence of SSR with
bits to transmit from the
m-th SSN to bottlenecked SU
b during the slot
under the transmit power
can be approximately expressed as follows based on channel capacity
given by Equation (4):
Clearly,
depends on channel capacity
and is also a function of the transmit power
. For ease of exposition, we use
to denote the amount of bits of the data sequence of SSR transmitted from the
m-th SSN to bottlenecked SU
b under transmit power
. Therefore, the aggregated amount of bits of the data sequence of SSR from all
IT and MT SSNs to bottleneck SU
b during the slot
under transmit power
is given as
, for
. Recall that the internal buffer of bottlenecked SU
b is used to store the amount of the data sequence of SSR transmitted from SSNs denoted by
during the slot
by using Equation (2). Hence, within the time interval
,
of bottlenecked SU
b can be further formulated by:
where
is the amount of the data sequence of SSR removed by bottlenecked SU
b within a time interval
.
So far, we have mathematically derived the amount of the data sequence of SSR transmitted from SSNs to bottlenecked SU
b under the condition that the
m-th SSN employs the transmit power
, for
. Next, we are concerned with how to mitigate the congestion of bottlenecked SU
b by the aid of the proposed distributed power control framework for IT and MT SSNs. The basic idea of congestion mitigation for bottlenecked SU
b is to alleviate its buffer load because of the accumulated amount of the data sequence of the SSR transmitted from IT and MT SSNs. It is uncovered that the transmit power of the
m-th SSN may have a bearing on
from Equation (38). Our objective is to leverage the distributed power control to reduce the amount of bits of the data sequence of the SSR transmitted from the
m-th SSN to bottlenecked SU
b, in order to lower the amount of the data sequence of the SSR in the internal buffer of bottlenecked SU
b. This operation will further ensure that offered data load does not exceed available buffer capacity of bottlenecked SU
b, i.e.,
. The key point to achieve congestion mitigation for bottlenecked SU
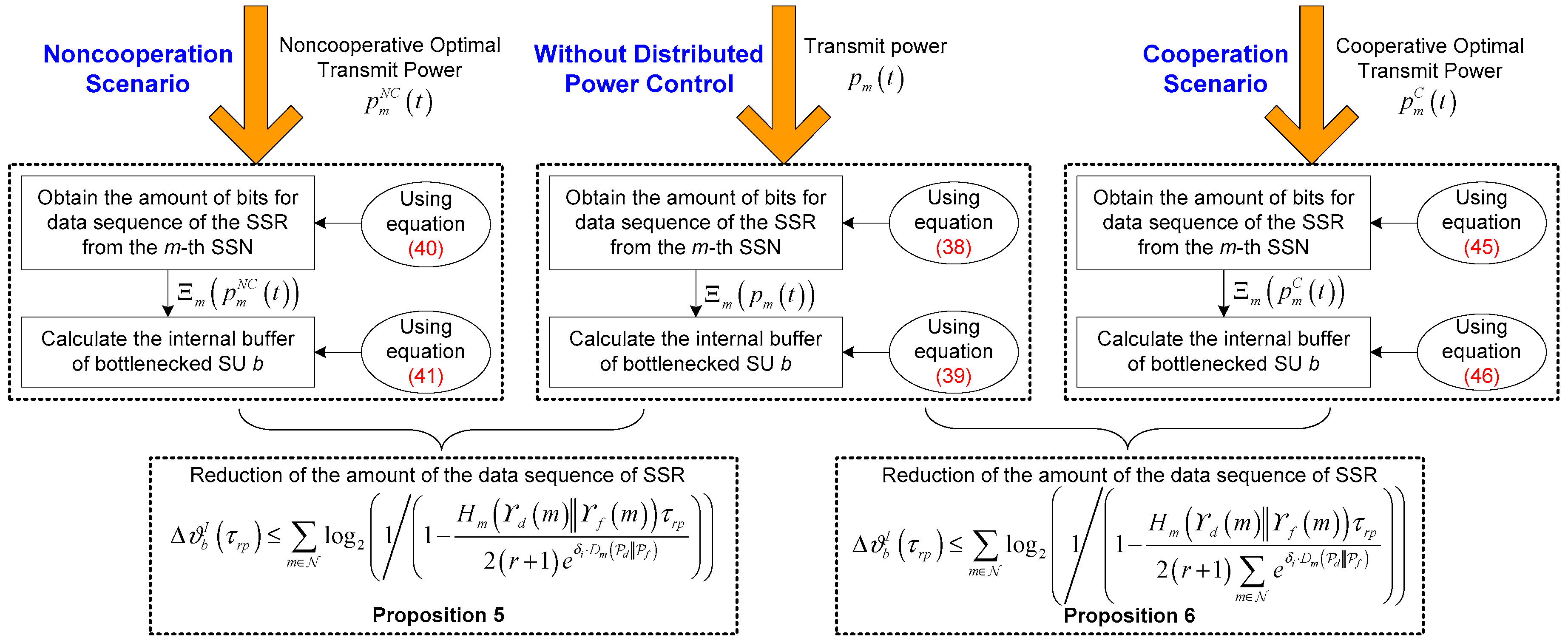
b is established with a block diagram shown in
Figure 4. It is worth remarking that the amount of the data sequence of SSR in the internal buffer of bottlenecked SU
b can be effectively reduced by the proposed distributed power control framework for IT and MT SSNs under the noncooperation and cooperation scenarios. Conceptually, the reduction of the amount of the data sequence of SSR will release the capacity of the internal buffer for bottlenecked SU
b, which naturally further attains the congestion mitigation for bottlenecked SU
b. In the following, we analyze the impact of optimal transmit power for the
m-th SSN on the reduction of the amount of the data sequence of SSR in the internal buffer of bottleneck SU
b rigorously from the noncooperation and cooperation cases.
(1)
Noncooperative Optimal Transmit Power Case: In this case, suppose, without loss of generality, that
. By replacing
in Equation (38) with
in Equation (28),
for the
m-th SSN within a time interval
can be expressed as:
By plugging
into Equation (39), we have:
Thus, the reduction of the amount of the data sequence of SSR in the internal buffer of bottlenecked SU
b, denoted by
, is equivalent to:
Proposition 5. Under the condition of the transmit power for the m-th SSN, satisfies the following upper bound: Proof. Since
. Under this condition, using Equation (28), we have:
Then we obtain the upper bound in Equation (43), thus completing the proof. ☐
(2)
Cooperative Optimal Transmit Power Case: In this case, with the assumption
, by replacing
in Equation (38) with
in Equation (34),
for the
m-th SSN within a time interval
can be given by:
By substituting
into Equation (39), we obtain:
Therefore, similar to Equation (42),
is also approximately formulated as:
Proposition 6. Under the condition of the transmit power for the m-th SSN, satisfies the following upper bound: Proof. Similar to the proof of Proposition 5, it is easy to identify the upper bound in Equation (48), thus completing the proof. ☐
6. Simulation Results
In this section, we provide simulation results to evaluate the performance of the proposed congestion mitigation approach by using the distributed power control framework for IT and MT SSNs in the rectangular grid based SN-CRN, and investigate the impact of key system parameters on the performance. Particularly, our simulations pay more attention to evaluate the effect of the proposed distributed power control framework for IT and MT SSNs on the reduction of the amount of the data sequence of SSR in the internal buffer of bottlenecked SU
b. Technically, the reduction of the amount of the data sequence of SSR in the internal buffer will free the buffer capacity of bottlenecked SU
b, which can bring about the congestion mitigation for bottlenecked SU
b. As illustrated in
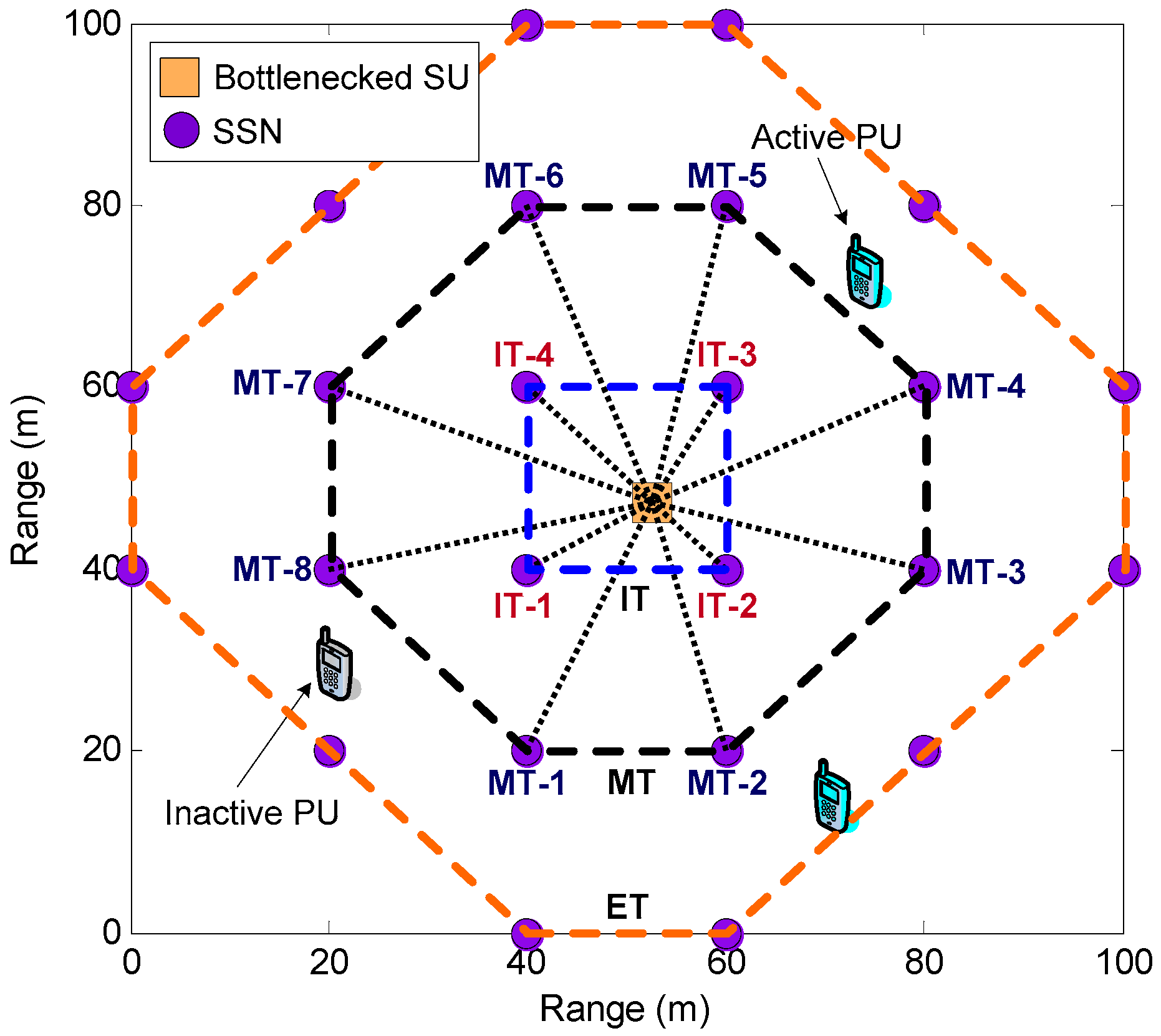
Figure 5, all the simulations are carried out on a rectangular grid topology within a torus area of 100 m × 100 m where one bottlenecked SU is randomly placed within the area of IT over three-tier structure. It suffices to mention that the horizontal or vertical distance between any SSNs is initialized to be
= 20 m. For convenience, the IT SSN and the MT SSN are marked by IT-
m and MT-
n in sequence for
and
, respectively, as shown in
Figure 5. We assume that there are
= 12 licensed uplink channels allocated to PUs. The SOP usage probability
is set to 0.65 for the bottlenecked SU. Also, the total average power constraint assigned to IT and MT SSNs are assumed to
= 18 dBm and
= 8 dBm, respectively, to mitigate the interference among IT and MT SSNs. As for the AWGN multiple-access channel, the path-loss exponent
has been set to 8, and the channel bandwidth used for SSNs is assumed to be 2 MHz according to IEEE 802.15.4a channel model. The constant
under the channel capacity formulation given in Equation (4) is defined as 0.005. In addition, the noise power spectral density
under this channel model is initialized as −3 dBm. We also adopt the receiving reference power by bottleneck SU
b = 20 dBm under the reference distance
= 20 m.
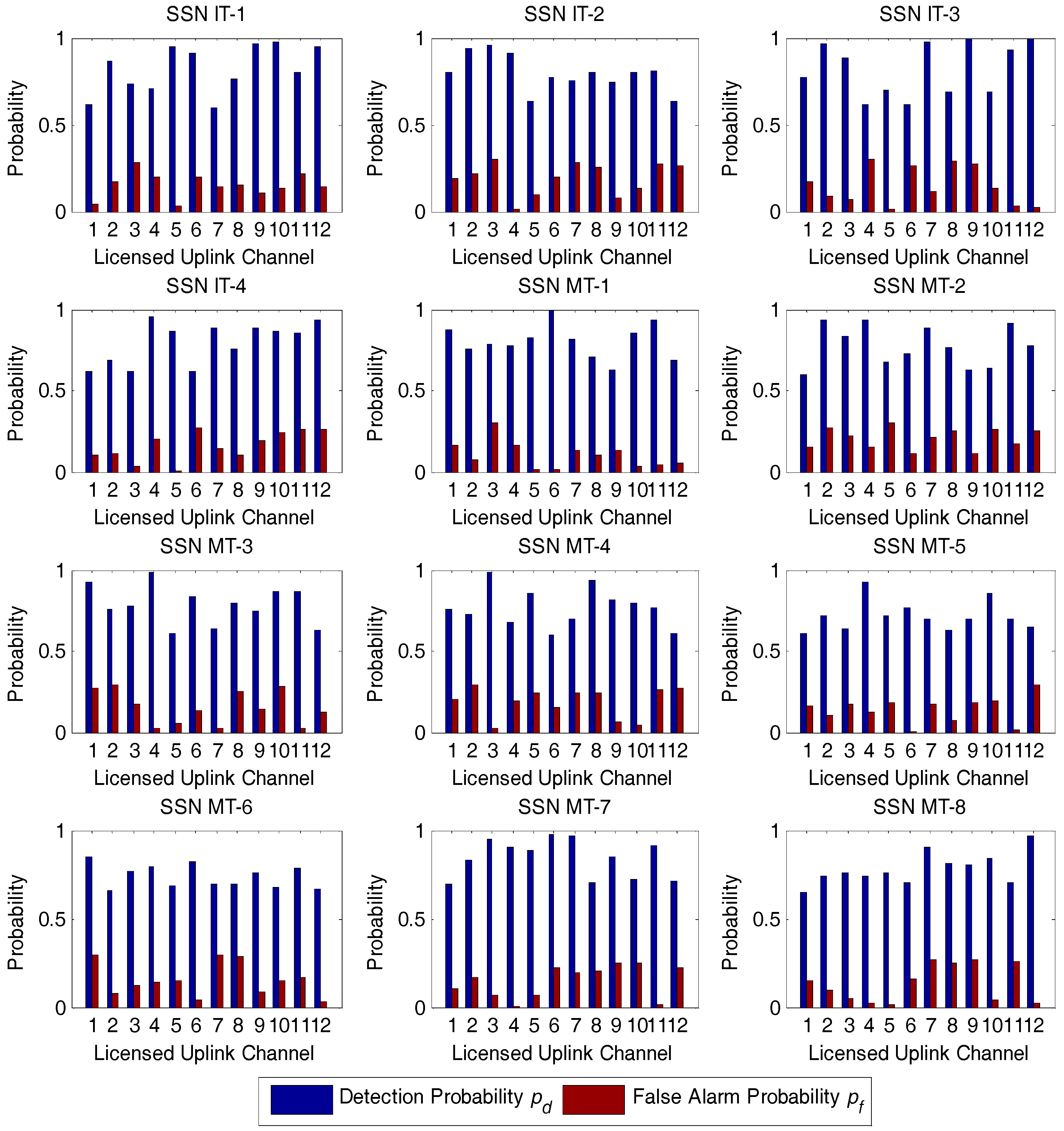
In all the simulations, the detection and false alarm probabilities for IT and MT SSNs over
licensed uplink channels have been initialized as in
Figure 6. We also set the number of subintervals in Algorithm 1 to be the same value for all SSNs, i.e.,
. We also assume that the minimum value
and the maximum value
in derivation of the detection probability distribution are set to 0.6 and 1, respectively. Likewise, the minimum value
and the maximum value
in derivation of the false alarm probability distribution are set at 0 and 0.3, respectively.
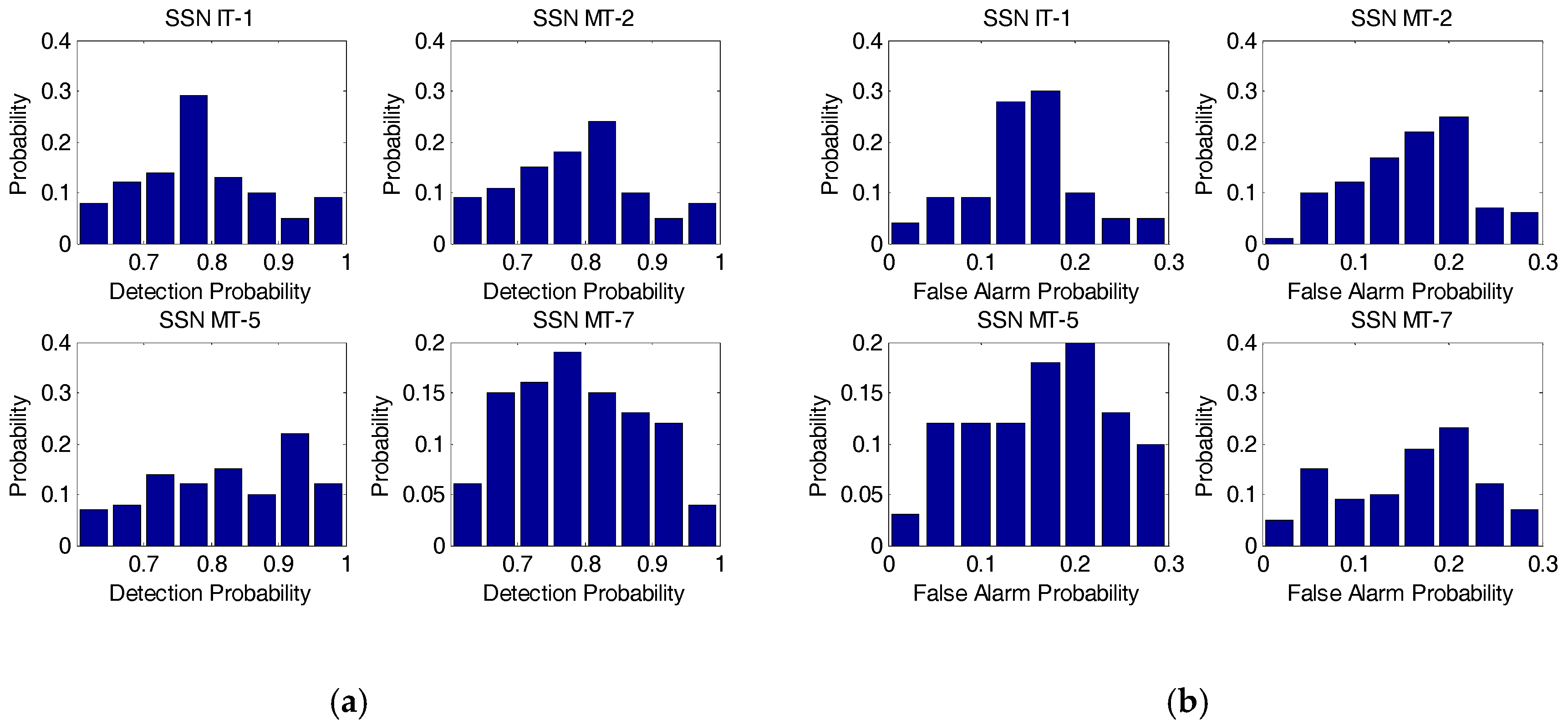
For simplicity, we deliberately choose some of the IT and MT SSNs in the simulation including IT-1, MT-2, MT-5, and MT-7, to evaluate the performance of our developed approach. Specifically, the detection probability and false alarm probability distributions of the selected SSNs from IT and MT generated from Algorithm 1 are assumed to comply with the corresponding distributions as given by
Figure 7.
The proposed OTPA algorithm for both the NoCoPC problem and the CoPC problem under the distributed power control framework for IT and MT SSNs is compared with the well-known power balancing (PB) algorithm in [
35]. The PB algorithm is also a SNR balancing constrained power control iterative method which iteratively searches for decentralized transmit power level updated from the
l-th iteration to the (
l + 1)-th iteration. Let
denote the target SNR for the
m-th SSN to maintain a certain QoS requirement, for
. In this simulation, the target SNR can be set to
dB. Therefore, the PB algorithm iteratively updates the transmit power for the
m-th SSN according to [
35]:
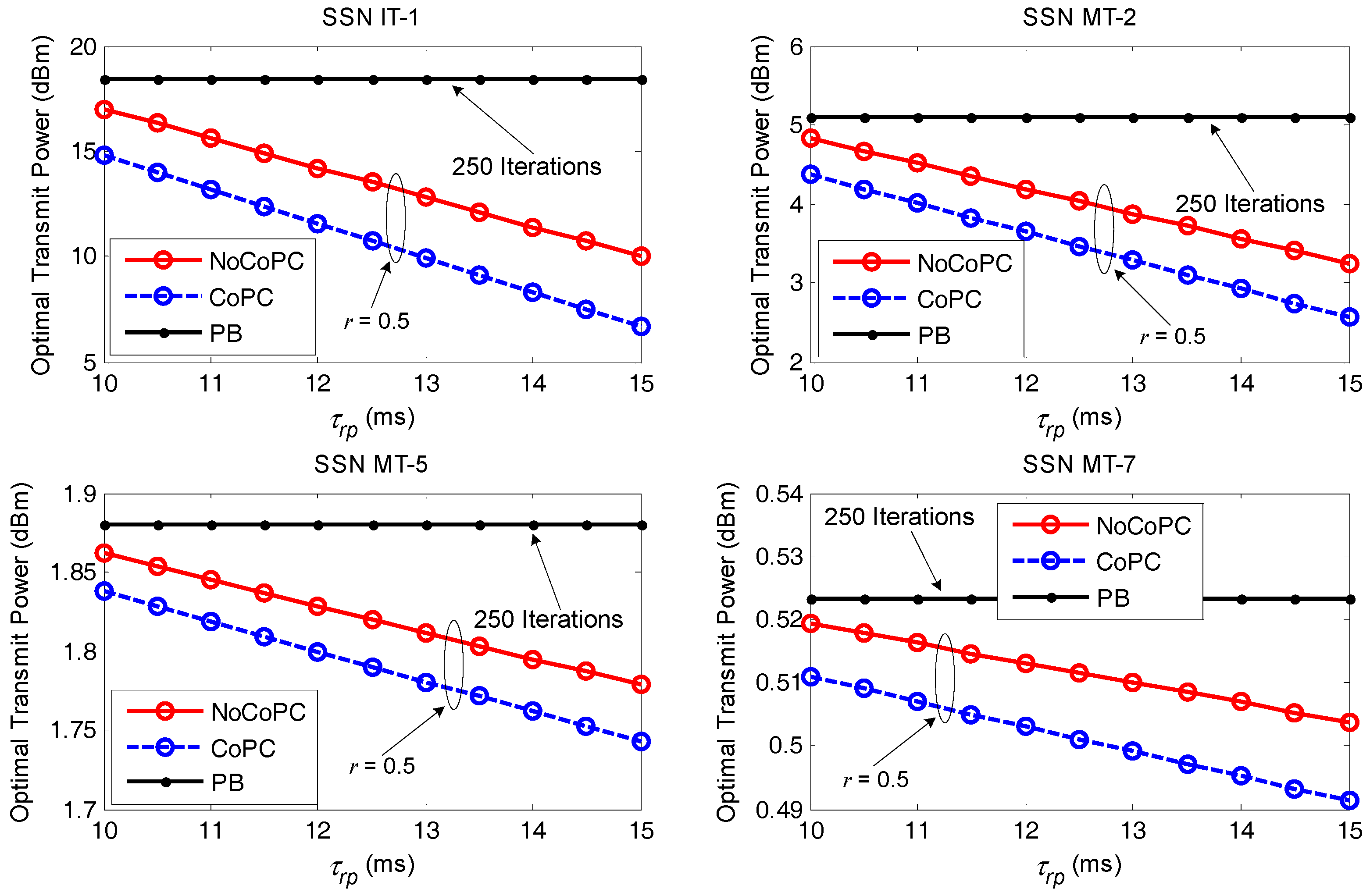
First the optimal transmit power is compared between PB algorithm with 250 iterations and our proposed distributed power control framework via the noncooperation and cooperation scenarios under the slot
= 12 ms with the evolution of discount factor
r, as exhibited in
Figure 8. It is shown that an increased discount factor from 0.1 to 0.9 will enhance the optimal transmit power of selected SSNs (i.e., IT-1, MT-2, MT-5, and MT-7) under the proposed OTPA algorithm for both the NoCoPC problem and the CoPC problem within the slot
= 12 ms. This is due to the fact that the discount factor
r has an affect on the optimal transmit power of selected SSNs via Equations (28) and (34). Specifically, the optimal transmit power of selected SSNs grows in proportion to discount factor
r. It is also revealed that the optimal transmit power of selected SSNs under a given discount factor satisfy the average power constraint of
= 18 dBm and
= 8 dBm. Thus, the optimal transmit power of selected SSNs will not be adjusted through OTPA algorithm. Comparing the performance of the NoCoPC problem and CoPC problem with the slot
= 12 ms, we can also observe that the optimal transmit power of selected SSNs by using PB algorithm presents a fixed constant value. The reason for this is that the optimal transmit power of the selected SSN by using PB algorithm converges to an expected equilibrium point after 250 iterations. It is also interesting that Proposition 2 has turned out that the optimal transmit power of selected SSNs derived by NoCoPC problem converges to a fixed Nash equilibrium point. Moreover, Proposition 4 has also guaranteed that the optimal transmit power of selected SSNs under the CoPC problem will reach to a fixed value. From
Figure 8, it is implicitly revealed that the optimal transmit power of selected SSNs by the OTPA algorithm is obviously lower than that of PB algorithm. This observation is reasonable since PB algorithm generates more power consumption to maintain the target SNR. However, the optimal transmit power of selected SSNs via the proposed OTPA algorithm fully depends on the maximum transmit power of the selected SSNs and the pricing factors in differential game model.
Figure 9 displays the optimal transmit power comparison between PB algorithm with 250 iterations and our proposed distributed power control framework under discount factor
= 0.5 with the evolution of the slot
from 10 ms to 15 ms. As can be seen, the proposed OTPA algorithm for both the NoCoPC problem and CoPC problem under the condition of discount factor
= 0.5 outperforms PB algorithm with 250 iterations significantly in terms of the optimal transmit power of selected SSNs with the growth of the slot
. This result further validates PB algorithm will result in much more power consumption aiming to maintain the target SNR. However, the optimal transmit power of selected SSNs by using the proposed OTPA algorithm entirely depends upon maximum transmit power of selected SSNs and pricing factors in differential game model. We can also observe that the optimal transmit power of selected SSNs of the proposed OTPA algorithm for the CoPC problem under discount factor
= 0.5 is considerably lower than that of the NoCoPC problem. That is, the proposed OTPA algorithm for the CoPC problem outperforms that of the NoCoPC problem. This can be intuitively explained by the fact that there exists an operation of summing with respect to
in the denominator of the analytical cooperative optimal transmit power
. Moreover, the increase of the slot
will generate lower transmit power for both the NoCoPC problem and CoPC problem with discount factor
= 0.5. This is because based on Equations (28) and (34), the optimal transmit power for both the NoCoPC problem and CoPC problem is inversely proportional to the slot
. This observation emphasizes the importance of selecting the proper time interval of slot
on the optimal transmit power.
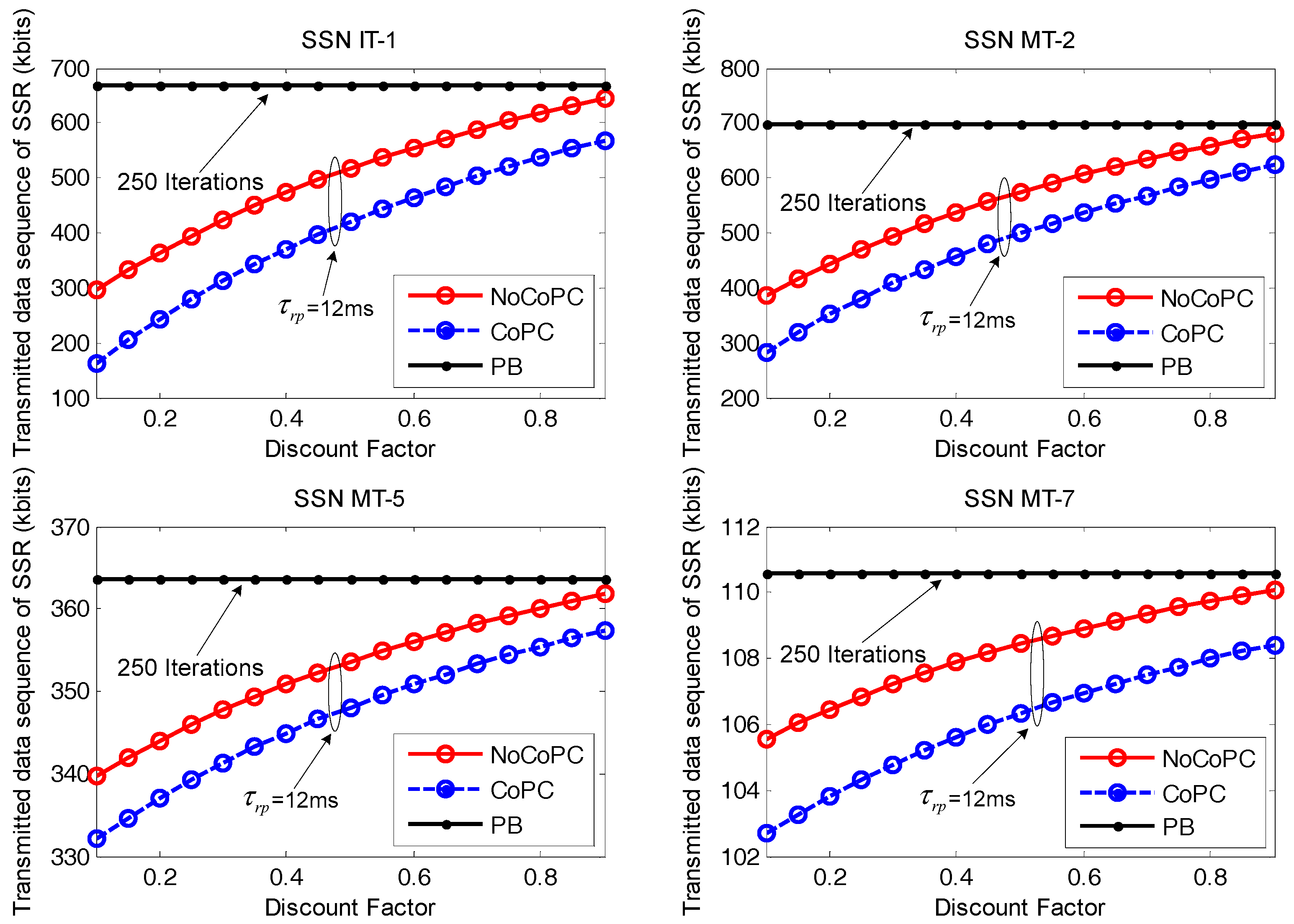
In
Figure 10, we look at the performance of the transmitted data sequence of SSR from selected SSNs to bottlenecked SU
b during the slot
= 12 ms with the evolution of discount factor
r from 0.1 to 0.9. From the results, we can see the transmitted data sequence of SSR for selected SSNs gradually increase with the growth of discount factor
r. Meanwhile, the transmitted data sequence of SSR for PB algorithm with 250 iterations and our proposed distributed power control framework under the condition of the slot
= 12 ms tends to be close when discount factor
r = 0.9. The reason for this is that the transmitted data sequence of SSR can be approximately expressed as a function of channel capacity according to Equation (38), which is in direct proportion to the optimal transmit power of selected SSNs. It has also been shown that an increased discount factor from 0.1 to 0.9 will increase the optimal transmit power of selected SSNs under the proposed OTPA algorithm for both the NoCoPC problem and CoPC problem with the slot
= 12 ms. Consequently, higher optimal transmit power yields more transmitted data sequence of SSR.
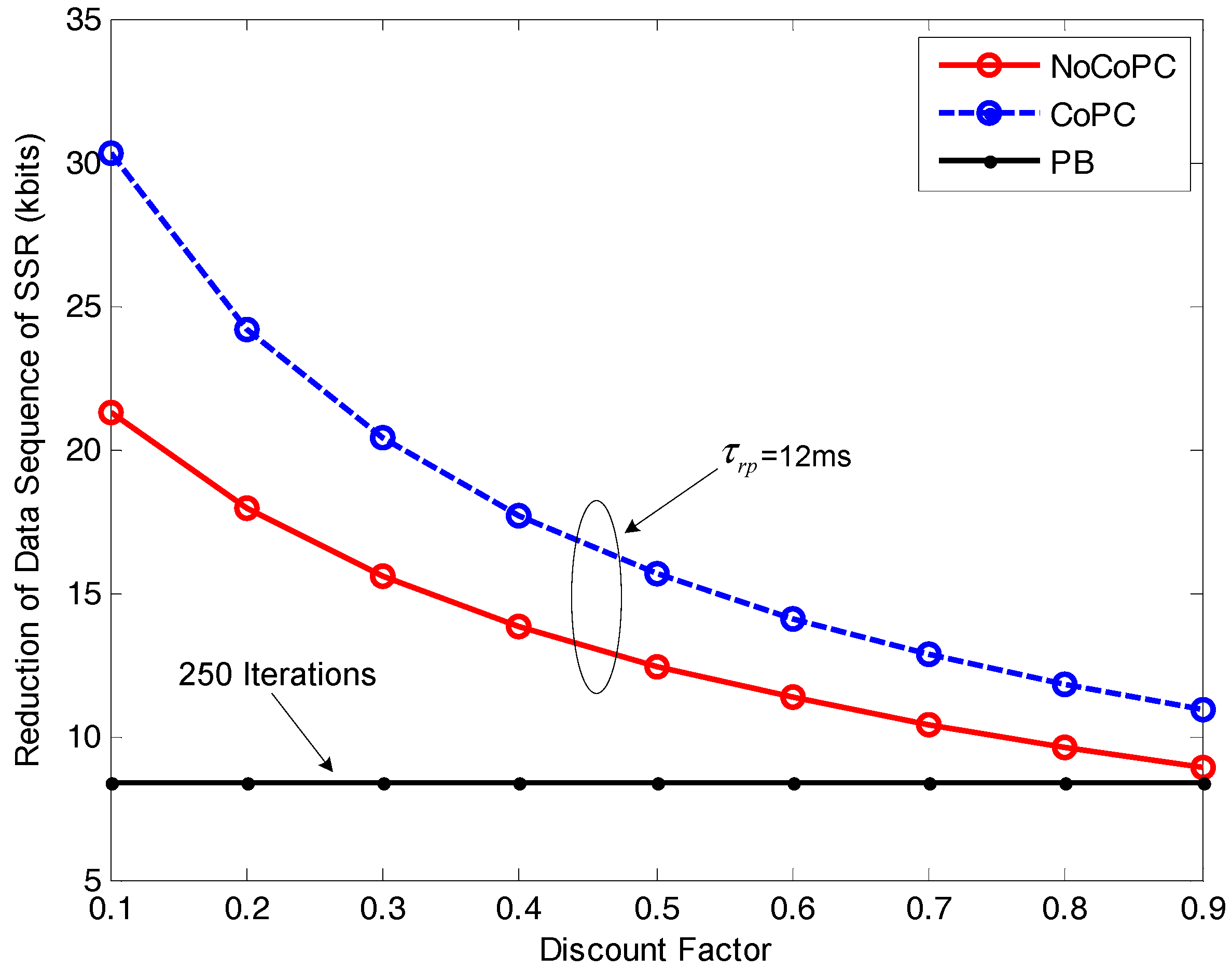
In
Figure 11, we examine the impact of discount factor
r from 0.1 to 0.9 on the reduction of data sequence of SSR with respect to selected SSNs in the internal buffer of bottleneck SU
b. It can be observed from the figure that the reduction of data sequence of SSR by our proposed congestion mitigation approach under the slot
= 12 ms will gradually decrease with the growth of discount factor
r, except that the reduction result by PB algorithm with 250 iterations appears to a fixed constant value. This trend is the result of the inverse relationship between the reduction of the data sequence of SSR
and the optimal transmit power of selected SSNs
for the NoCoPC problem or
for the CoPC problem according to Equations (42) and (47). Additionally, in
Figure 11, we can also observe that the proposed congestion mitigation approach by using the OTPA algorithm for the CoPC problem with the slot
= 12 ms achieves the higher reduction of the data sequence of SSR compared with those of the NoCoPC problem and PB algorithm with 250 iterations. In other words, through cooperation among all IT and MT SSNs, the reduction of the data sequence of SSR in the internal buffer of bottlenecked SU
b can be further improved. This observation has verified the analytical derivation of the proposed congestion mitigation approach. The explanation is twofold: (i) The proposed OTPA algorithm for the CoPC problem outperforms that of the NoCoPC problem owing to the lower cooperative optimal transmit power
obtained by the CoPC problem compared with the noncooperative optimal transmit power
by the NoCoPC problem; (ii) The reduction of the data sequence of SSR is inversely proportional to the optimal transmit power of selected SSNs.
Figure 12 shows the comparison of the reduction of data sequence of SSR with respect to selected SSNs in the internal buffer of bottlenecked SU
b, versus the slot
under the condition of discount factor
r = 0.3, for the proposed congestion mitigation approach and PB algorithm with 250 iterations. As seen from
Figure 11, the reduction of data sequence of SSR through PB algorithm has converged to the same constant value after the 250 iterations. This is the direct influence that the optimal transmit power of selected SSN will converge to an expected equilibrium point by using PB algorithm. As expected, the reduction of data sequence of SSR by the proposed congestion mitigation approach with discount factor
r = 0.3 is larger than that of PB algorithm with 250 iterations. This is because our proposed approach can obtain smaller optimal transmit power than PB algorithm. According to Equations (42) and (47), the smaller optimal transmit power will lead to the more reduction of data sequence of SSR with respect to selected SSNs. It is also interesting that with the growth of the slot
the reduction of data sequence of SSR by our proposed approach will gradually increase, and the reduction by the CoPC problem is much higher than that of the NoCoPC problem. This result can be interpreted by the fact that the optimal transmit power of selected SSNs by the CoPC problem under discount factor
= 0.3 is clearly lower than that of the NoCoPC problem with the growth of the slot
. This result further gives rise to the larger reduction of data sequence of SSR.