A Secure and Verifiable Outsourced Access Control Scheme in Fog-Cloud Computing
Abstract
:1. Introduction
1.1. Related Work
1.1.1. Outsourced Computation
1.1.2. Revocation
1.2. Our Contribution
- (1)
- We propose the verifiable outsourced multi-authority access control scheme (VO-MAACS), which is secure against collusion attacks. Most of the encryption and decryption computation is outsourced to fog devices, which greatly reduces the computation on the user side.
- (2)
- We provide a verification method for the outsourced encryption and decryption. If a fog device returns incorrect results, users can notice it immediately by running the corresponding verification algorithm.
- (3)
- We design an efficient user and attribute revocation method for our scheme. During the process of attribute revocation, most of the update and re-encryption operations are outsourced to the cloud server, and only a few components which are associated with the revoked attribute need to be updated, while the other components are not changed.
- (4)
- We provide a security and performance analysis of our scheme, which shows that our scheme is both secure and highly efficient.
1.3. Organization
2. Preliminaries
2.1. Bilinear Maps
- (1)
- Bilinearity: for all , and , .
- (2)
- Non-degeneracy: there exists , such that .
- (3)
- Computability: there is an efficient algorithm to compute for any and .
2.2. Access Structure
2.3. Linear Secret Sharing Schemes
- (1)
- The piece for each party forms a vector over .
- (2)
- During the generation of the pieces, the dealer chooses independent random variables, denoted , each one distributed uniformly over . Each coordinate of the piece of every party is a linear combination of and the secret . That is, let denotes a matrix with rows and columns. For the vector and any authorized set, there exist constants such that, if are valid shares of any secret according to , then , where and .
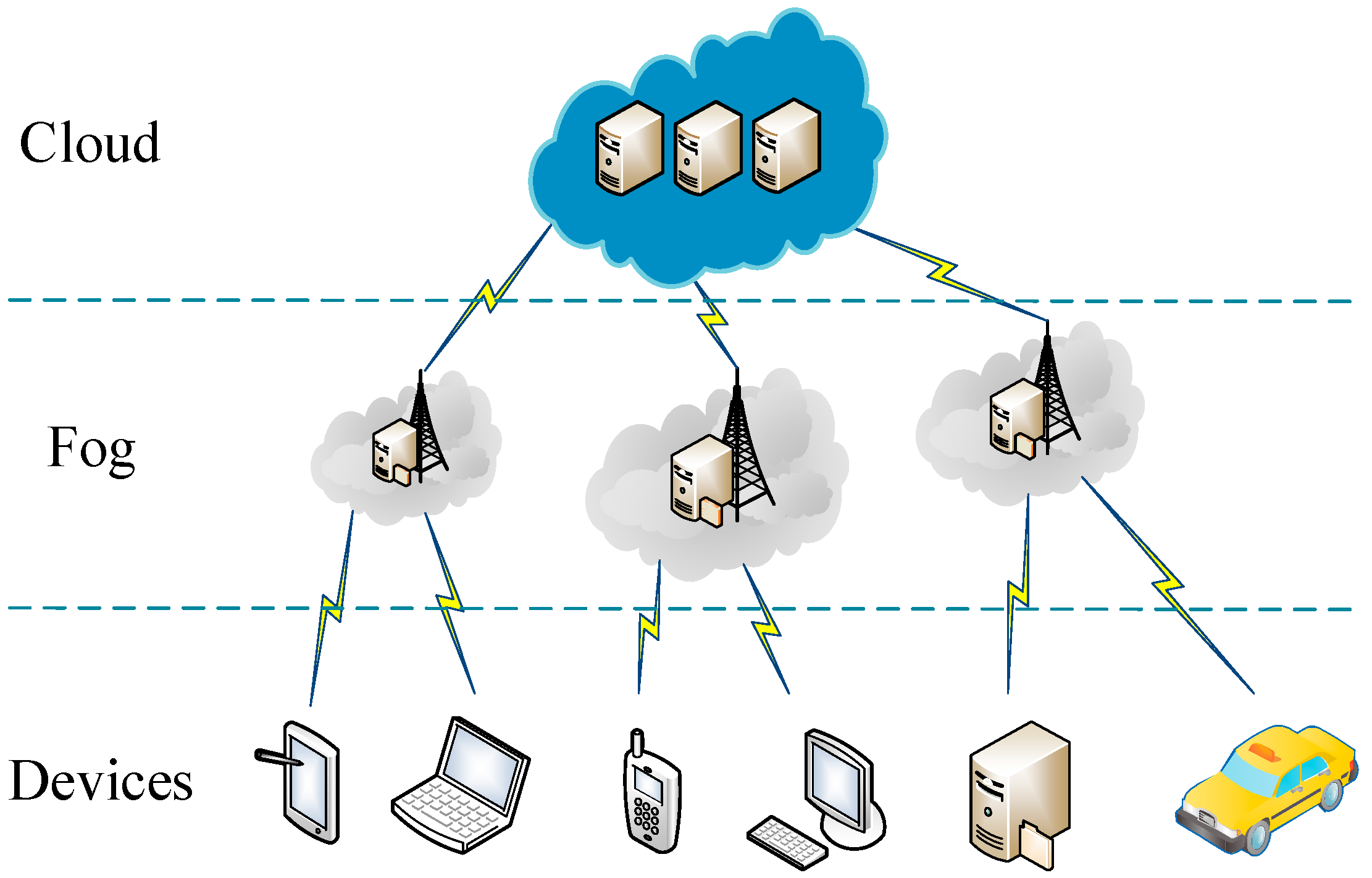
3. System Model and Framework
3.1. System Model
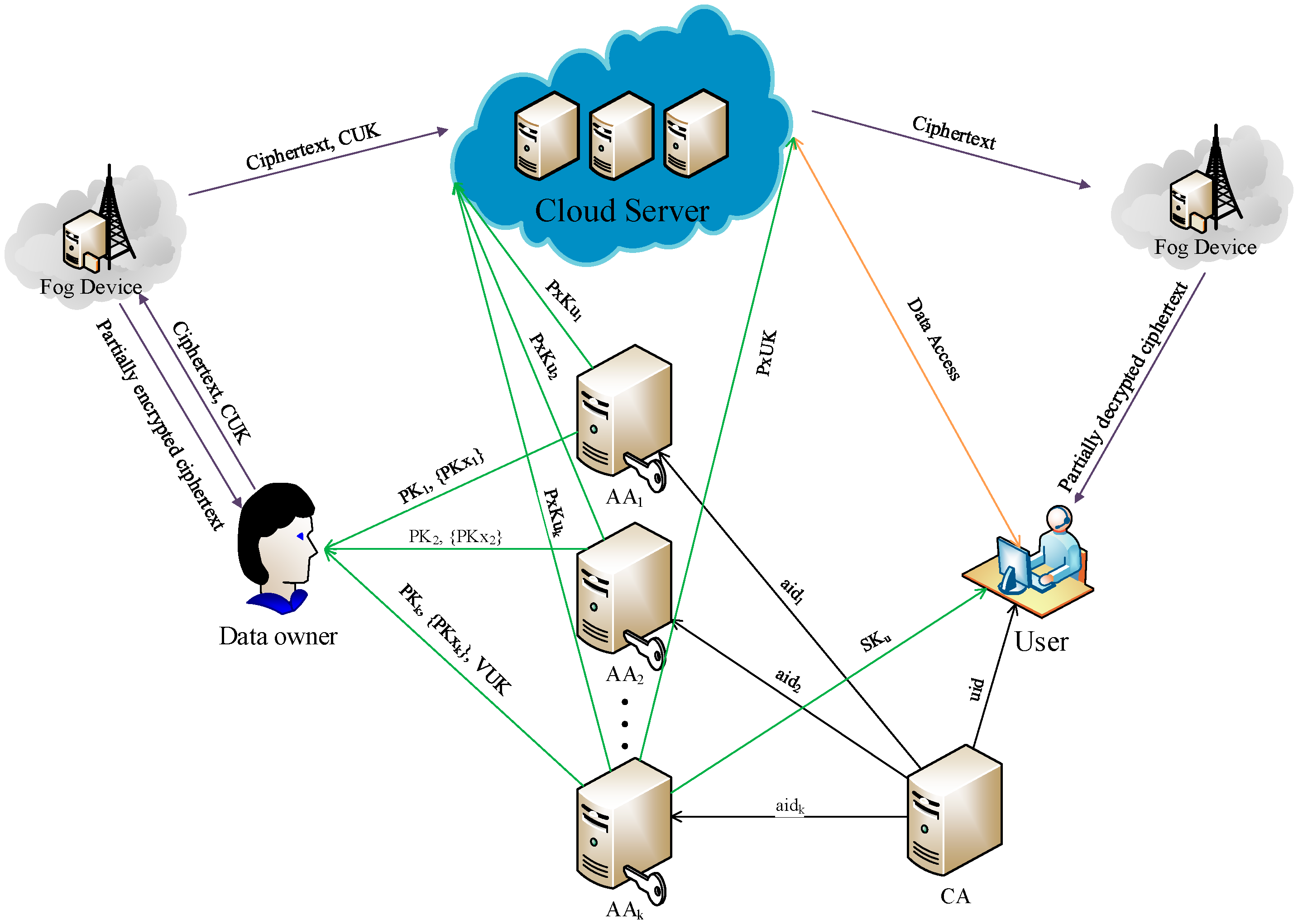
3.2. Framework
4. VO-MAACS: Verifiable Outsourced Multi-Authority Access Control Scheme
4.1. Construction of VO-MAACS
4.2. Verification Method
4.3. Revocation Scheme
4.3.1. User Revocation
4.3.2. Attribute Revocation
5. Analysis of Our Scheme
5.1. Security Analysis
5.1.1. Correctness
5.1.2. Data Confidentiality
5.1.3. Collusion tolerance
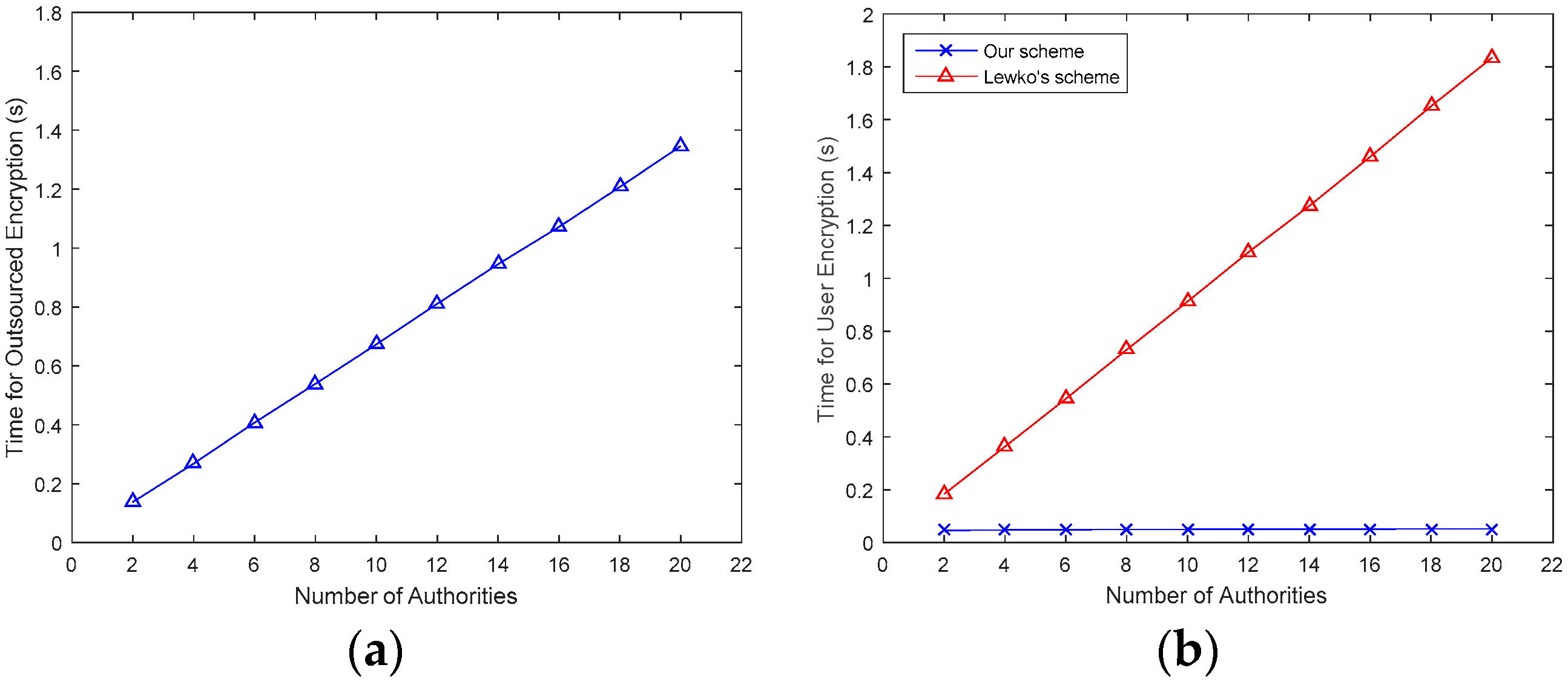
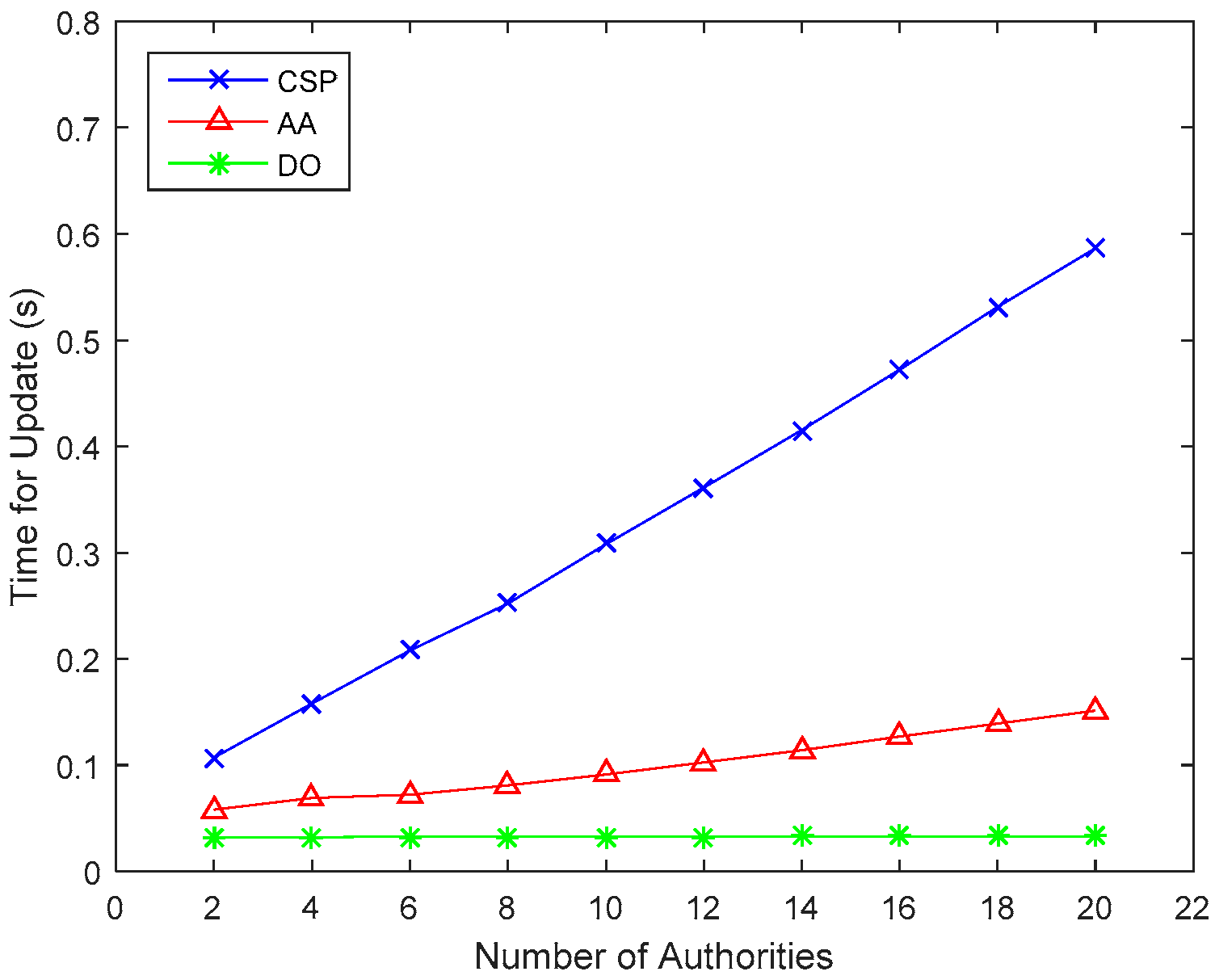
5.2. Performance Analysis
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 17 August 2012; pp. 13–16. [Google Scholar]
- Shojafar, M.; Cordeschi, N.; Baccarelli, E. Energy-efficient adaptive resource management for real-time vehicular cloud services. IEEE Trans. Cloud Comput. 2016, 99, 1. [Google Scholar] [CrossRef]
- Zaghdoudi, B.; Ayed, H.K.B.; Harizi, W. Generic Access Control System for Ad Hoc MCC and Fog Computing. In Proceedings of the International Conference on Cryptology and Network Security, Milan, Italy, 14–16 November 2016; pp. 400–415. [Google Scholar]
- Baccarelli, E.; Naranjo, P.G.V.; Scarpiniti, M.; Shojafar, M.; Abawajy, J.H. Fog of Everything: Energy-efficient Networked Computing Architectures, Research Challenges, and a Case Study. IEEE Access 2017, 5, 9882–9910. [Google Scholar] [CrossRef]
- Hajibaba, M.; Gorgin, S. A review on modern distributed computing paradigms: Cloud computing, jungle computing and fog computing. J. Comput. Inf. Technol. 2014, 22, 69–84. [Google Scholar] [CrossRef]
- Aazam, M.; Huh, E.N. Fog Computing and Smart Gateway Based Communication for Cloud of Things. In Proceedings of the International Conference on Future Internet of Things and Cloud IEEE, Barcelona, Spain, 27–29 August 2014; pp. 464–470. [Google Scholar]
- Stojmenovic, I.; Wen, S.; Huang, X.; Luan, H. An overview of Fog computing and its security issues. Concurr. Comput. Pract. Exp. 2015, 28, 2991–3005. [Google Scholar] [CrossRef]
- Yi, S.; Qin, Z.; Li, Q. Security and privacy issues of fog computing: A survey. In Proceedings of the International Conference on Wireless Algorithms, Systems, and Applications, Qufu, China, 10–12 August 2015; pp. 685–695. [Google Scholar]
- Lu, R.; Rahulamathavan, Y.; Zhu, H.; Xu, C.; Wang, M. Security and Privacy Challenges in Vehicular Cloud Computing. Mob. Inf. Syst. 2016, 2016, 1–2. [Google Scholar] [CrossRef]
- Lu, R.; Heung, K.; Lashkari, A.H.; Ghorbani, A.A. A Lightweight Privacy-Preserving Data Aggregation Scheme for Fog Computing-Enhanced IoT. IEEE Access 2017, 5, 3302–3312. [Google Scholar] [CrossRef]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the Security and Privacy, Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Chase, M. Multi-authority attribute based encryption. Theory Cryptogr. Conf. 2007, 4392, 515–534. [Google Scholar] [CrossRef]
- Waters, B. Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization. Public Key Cryptogr. PKC 2011, 6571, 53–70. [Google Scholar] [CrossRef]
- Lewko, A.; Waters, B. Decentralizing attribute-based encryption. In Proceedings of the Advances in Cryptology–EUROCRYPT, Tallinn, Estonia, 15–19 May 2011; pp. 568–588. [Google Scholar]
- Ruj, S.; Nayak, A.; Stojmenovic, I. DACC: Distributed access control in Clouds. In Proceedings of the TrustCom, Changsha, China, 16–18 November 2011; pp. 91–98. [Google Scholar]
- Zhou, Z.; Huang, D.; Wang, Z. Efficient privacy-preserving ciphertext-policy attribute based-encryption and broadcast encryption. IEEE Trans. Comput. 2015, 64, 126–138. [Google Scholar] [CrossRef]
- Wang, S.; Zhou, J.; Liu, J.K.; Yu, J.; Chen, J.; Xie, W. An efficient file hierarchy attribute-based encryption scheme in cloud computing. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1265–1277. [Google Scholar] [CrossRef]
- Green, M.; Hohenberger, S.; Waters, B. Outsourcing the decryption of abe ciphertexts. In Proceedings of the USENIX Security Symposium, San Francisco, CA, USA, 8–12 August 2011; p. 34. [Google Scholar]
- Yang, K.; Jia, X. Attributed-based access control for multi-authority systems in cloud storage. In Proceedings of the 32nd International Conference on Distributed Computing Systems (ICDCS), Macau, China, 18–21 June 2012; pp. 536–545. [Google Scholar]
- Yang, K.; Jia, X. Expressive, efficient, and revocable data access control for multi-authority cloud storage. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 1735–1744. [Google Scholar] [CrossRef]
- Li, J.; Chen, X.; Li, J.; Jia, C.; Ma, J.; Lou, W. Fine-grained access control system based on outsourced attribute-based encryption. In Proceedings of the European Symposium on Research in Computer Security, Egham, UK, 9–13 September 2013; pp. 592–609. [Google Scholar]
- Lai, J.; Deng, R.H.; Guan, C.; Weng, J. Attribute-based encryption with verifiable outsourced decryption. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1343–1354. [Google Scholar] [CrossRef]
- Li, J.; Huang, X.; Li, J.; Chen, X.; Xiang, Y. Securely outsourcing attribute-based encryption with checkability. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 2201–2210. [Google Scholar] [CrossRef]
- Chen, Y.; Song, L.; Yang, G. Attribute-Based Access Control for Multi-Authority Systems with Constant Size Ciphertext in Cloud Computing. China Commun. 2016, 13, 146–162. [Google Scholar] [CrossRef]
- Li, X.; Tang, S.; Xu, L.; Wang, H.; Chen, J. Two-Factor Data Access Control With Efficient Revocation for Multi-Authority Cloud Storage Systems. IEEE Access 2017, 5, 393–405. [Google Scholar] [CrossRef]
- Mao, X.; Lai, J.; Mei, Q.; Chen, K.; Weng, J. Generic and efficient constructions of attribute-based encryption with verifiable outsourced decryption. IEEE Trans. Dependable Secur. Comput. 2016, 13, 533–546. [Google Scholar] [CrossRef]
- Ostrovsky, R.; Sahai, A.; Waters, B. Attribute-based encryption with non-monotonic access structures. In Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 29 October–2 November 2007; pp. 195–203. [Google Scholar]
- Ibraimi, L.; Petkovic, M.; Nikova, S.; Hartel, P.; Jonker, W. Mediated Ciphertext-Policy Attribute-Based Encryption and Its Application. In Information Security Applications; Springer: Berlin/Heidelberg, Germany, 2009; pp. 309–323. [Google Scholar]
- Yu, S.; Wang, C.; Ren, K.; Lou, W. Attribute based data sharing with attribute revocation. In Proceedings of the 5th ACM Symposium on Information, Computer and Communications Security, Beijing, China, 13–16 April 2010; pp. 261–270. [Google Scholar]
- Hur, J.; Noh, D.K. Attribute-based access control with efficient revocation in data outsourcing systems. IEEE Trans. Parallel Distrib. Syst. 2011, 22, 1214–1221. [Google Scholar] [CrossRef]
- Xie, X.; Ma, H.; Li, J.; Chen, X. New ciphertext-policy attribute-based access control with efficient revocation. In Proceedings of the Information and Communication Technology-EurAsia Conference, Yogyakarta, Indonesia, 25–29 March 2013; pp. 373–382. [Google Scholar]
- Yang, Y.; Liu, J.K.; Liang, K.; Choo, K.R.; Zhou, J. Extended proxy-assisted approach: Achieving revocable fine-grained encryption of cloud data. In Proceedings of the European Symposium on Research in Computer Security, Vienna, Austria, 21–25 September 2015; pp. 146–166. [Google Scholar]
- Beimel, A. Secure Schemes for Secret Sharing and Key Distribution; Technion-Israel Institute of Technology, Faculty of Computer Science: Haifa, Israel, 1996; pp. 22–28. [Google Scholar]
- Bellare, M.; Garay, J.A.; Rabin, T. Fast batch verification for modular exponentiation and digital signatures. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Espoo, Finland, 31 May–4 June 1998; pp. 236–250. [Google Scholar]
- Akinyele, J.A.; Garman, C.; Miers, I.; Pagano, M.W.; Rushanan, M.; Green, M.; Rubin, A.D. Charm: A framework for rapidly prototyping cryptosystems. J. Cryptogr. Eng. 2013, 3, 111–128. [Google Scholar] [CrossRef]


© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fan, K.; Wang, J.; Wang, X.; Li, H.; Yang, Y. A Secure and Verifiable Outsourced Access Control Scheme in Fog-Cloud Computing. Sensors 2017, 17, 1695. https://doi.org/10.3390/s17071695
Fan K, Wang J, Wang X, Li H, Yang Y. A Secure and Verifiable Outsourced Access Control Scheme in Fog-Cloud Computing. Sensors. 2017; 17(7):1695. https://doi.org/10.3390/s17071695
Chicago/Turabian StyleFan, Kai, Junxiong Wang, Xin Wang, Hui Li, and Yintang Yang. 2017. "A Secure and Verifiable Outsourced Access Control Scheme in Fog-Cloud Computing" Sensors 17, no. 7: 1695. https://doi.org/10.3390/s17071695





