Virtual-Lattice Based Intrusion Detection Algorithm over Actuator-Assisted Underwater Wireless Sensor Networks
Abstract
:1. Introduction
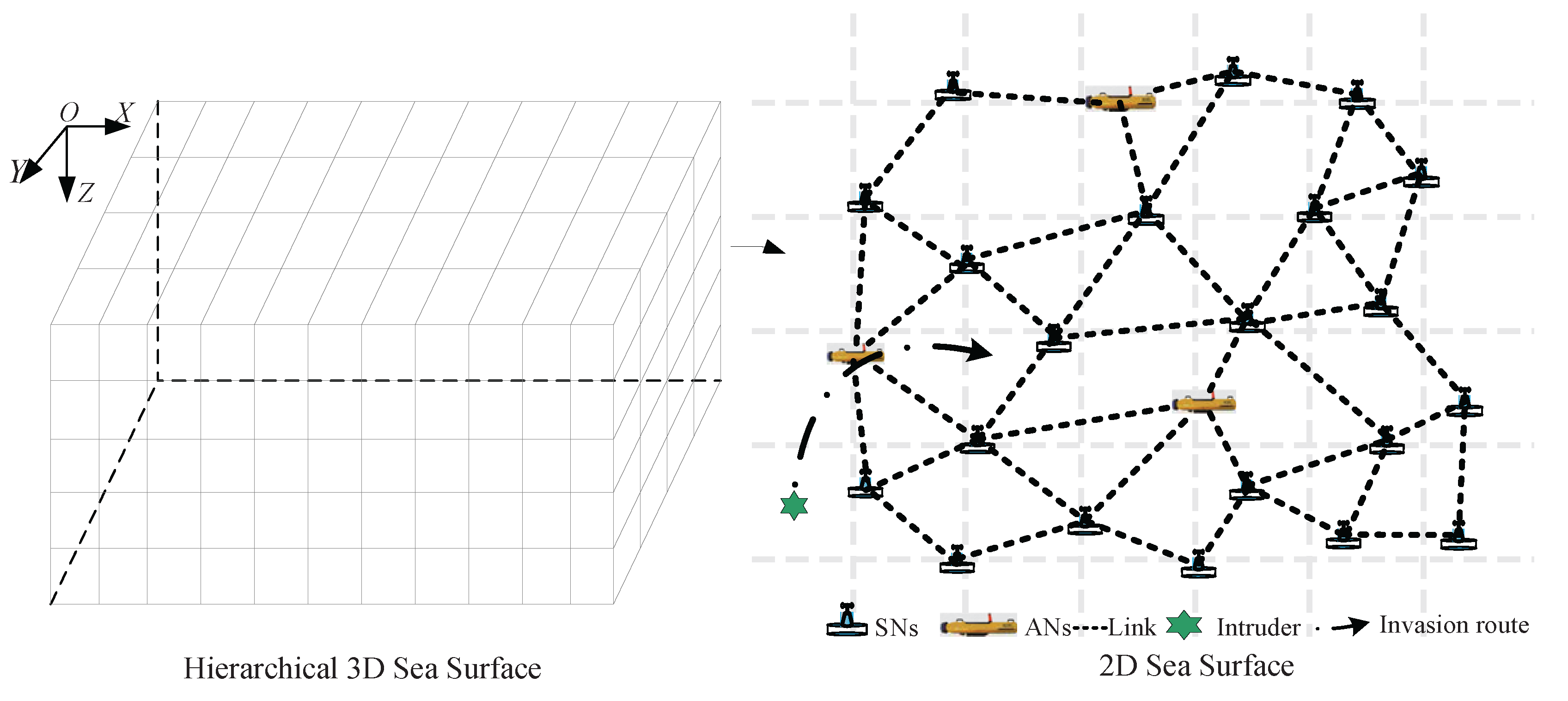
2. Problem Formulation and Preliminaries
2.1. Sensing Model of SNs and ANs
2.2. Energy Model for Communication Consumption
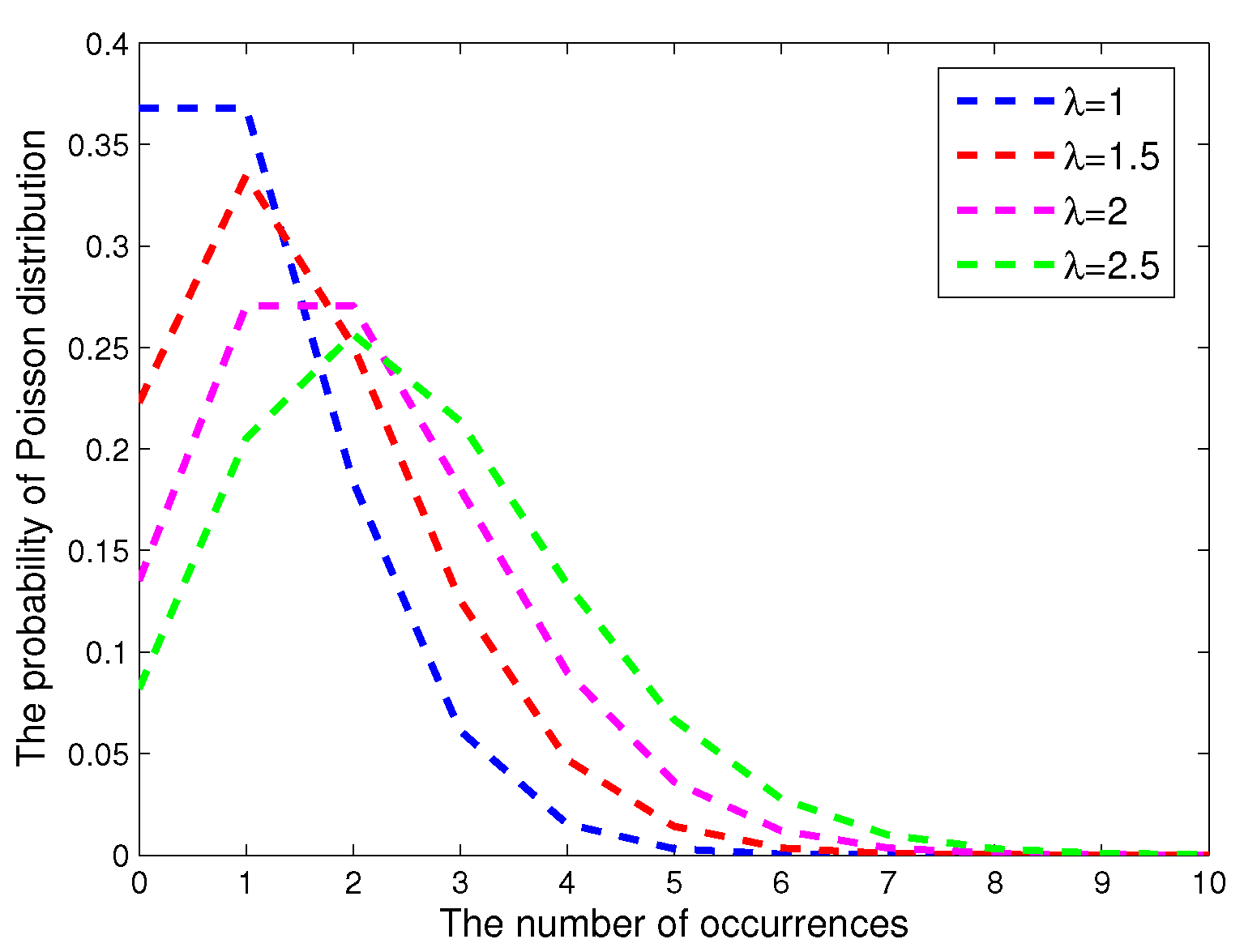
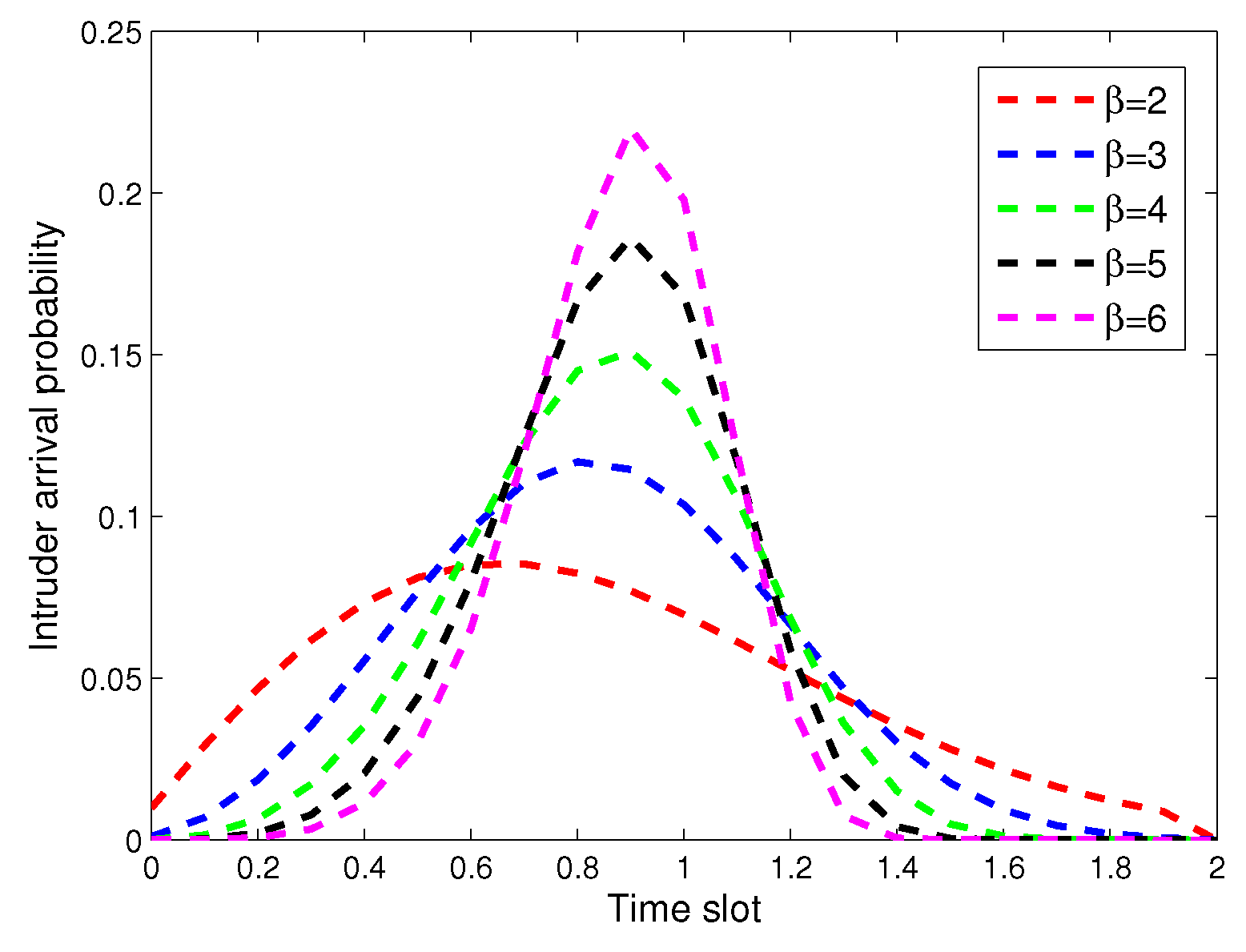
2.3. Average Intruder Detection Probability
2.4. Problem Definition
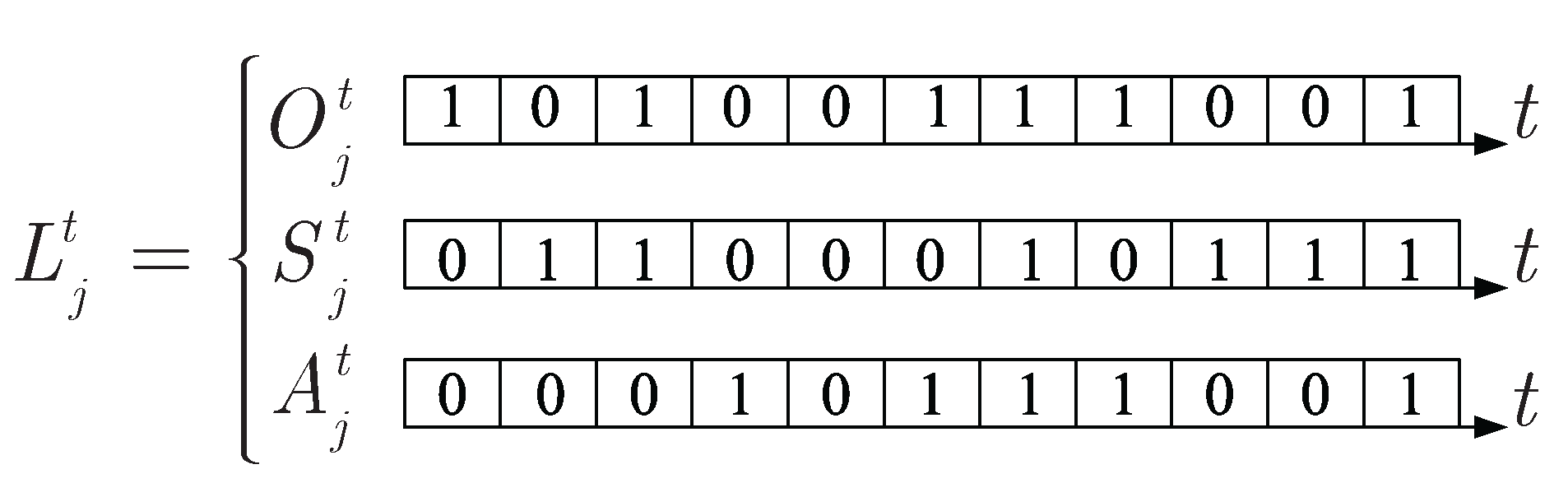
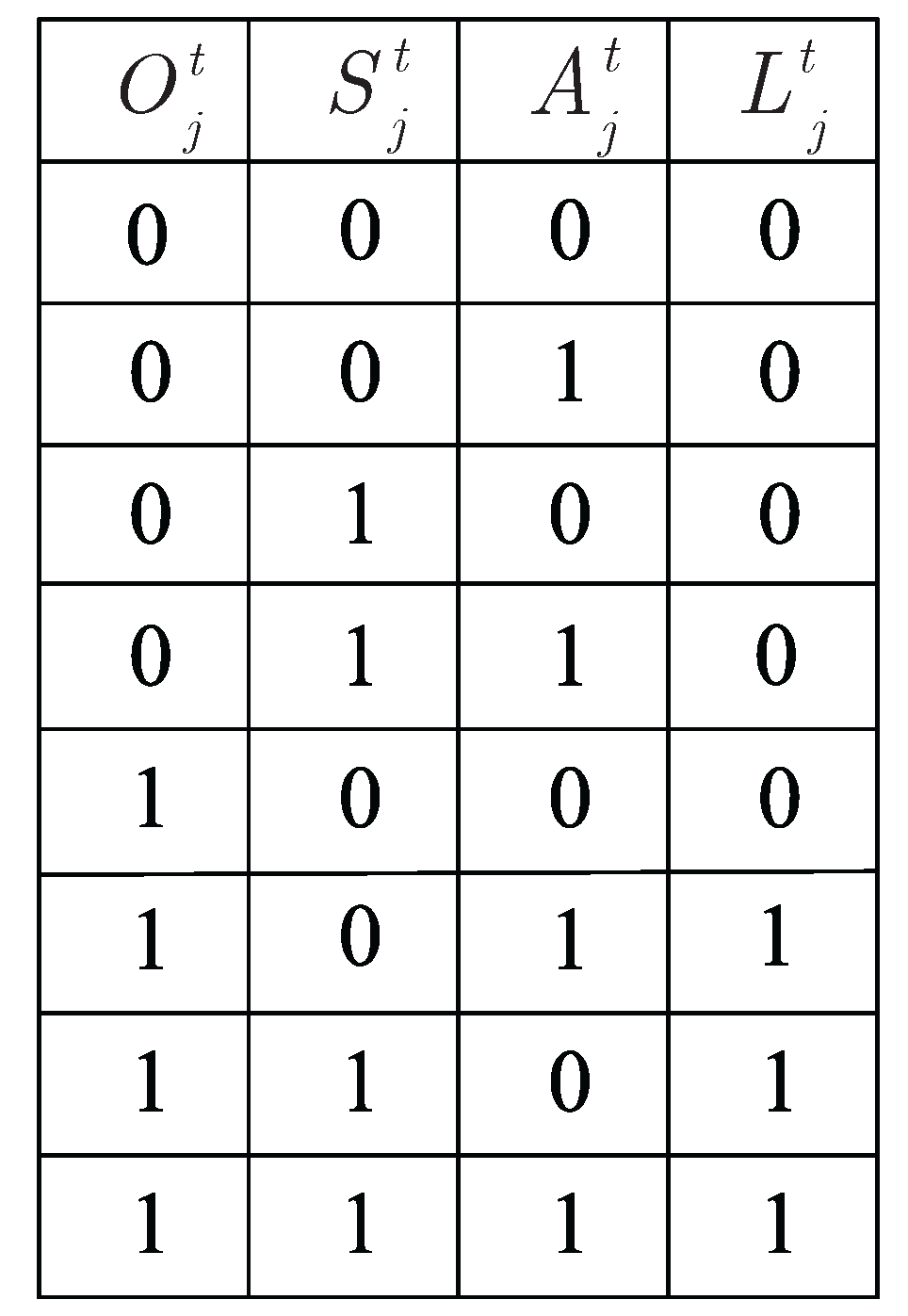
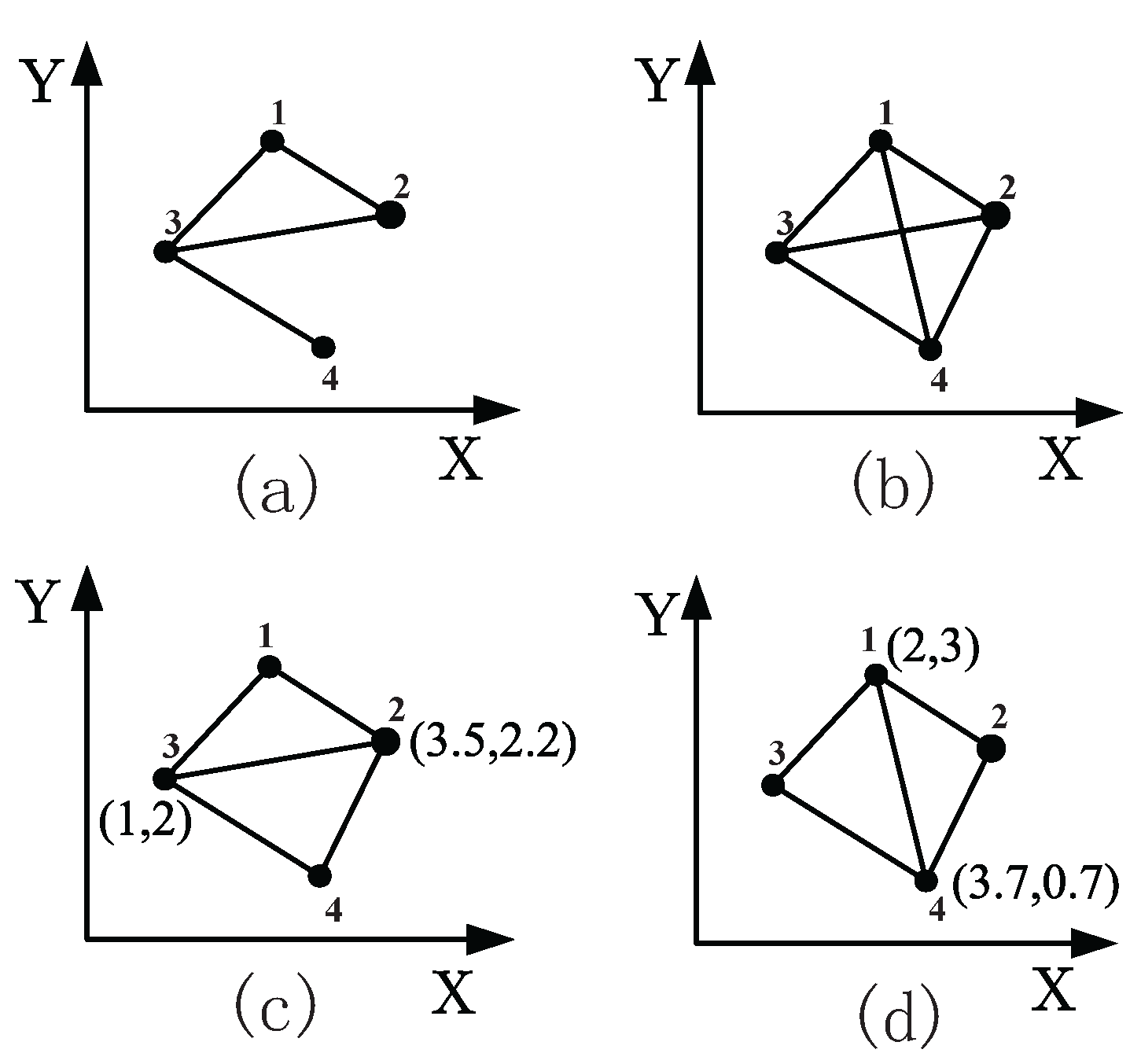
2.5. Graph Preliminaries
3. Algorithm Description and Analysis
3.1. Virtual-Lattice-Based Monitor Algorithm
| Algorithm 1 Virtual Lattice-Based Monitor Algorithm |
|
3.2. The Optimal and Coordinate Lattice Monitor Algorithm
| Algorithm 2 Optimal Lattice Monitor Path Algorithm |
|
| Algorithm 3 Equal Price-Basedd Search Method With Coordination SNs Monitor Patrolling Algorithm |
|
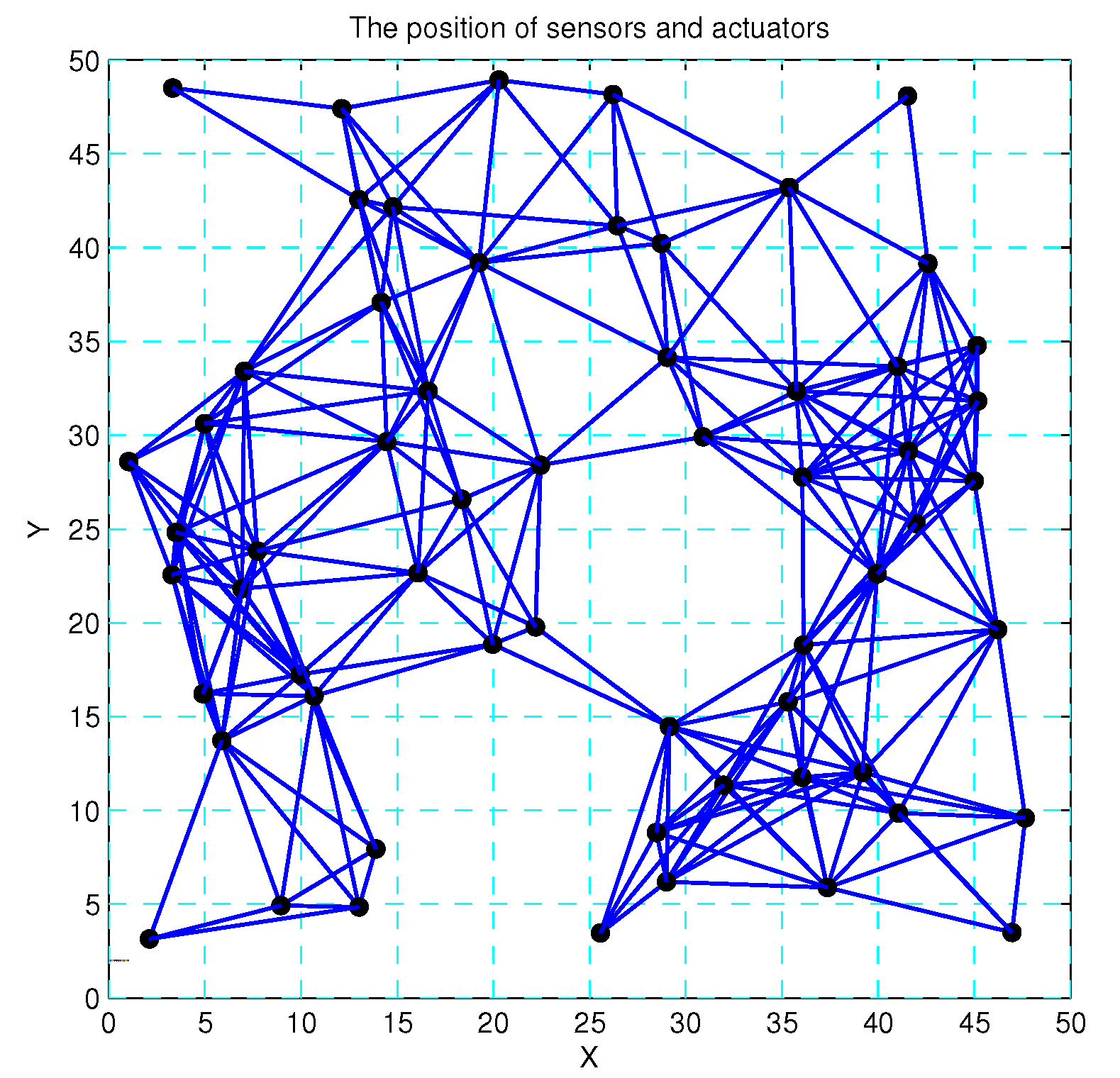
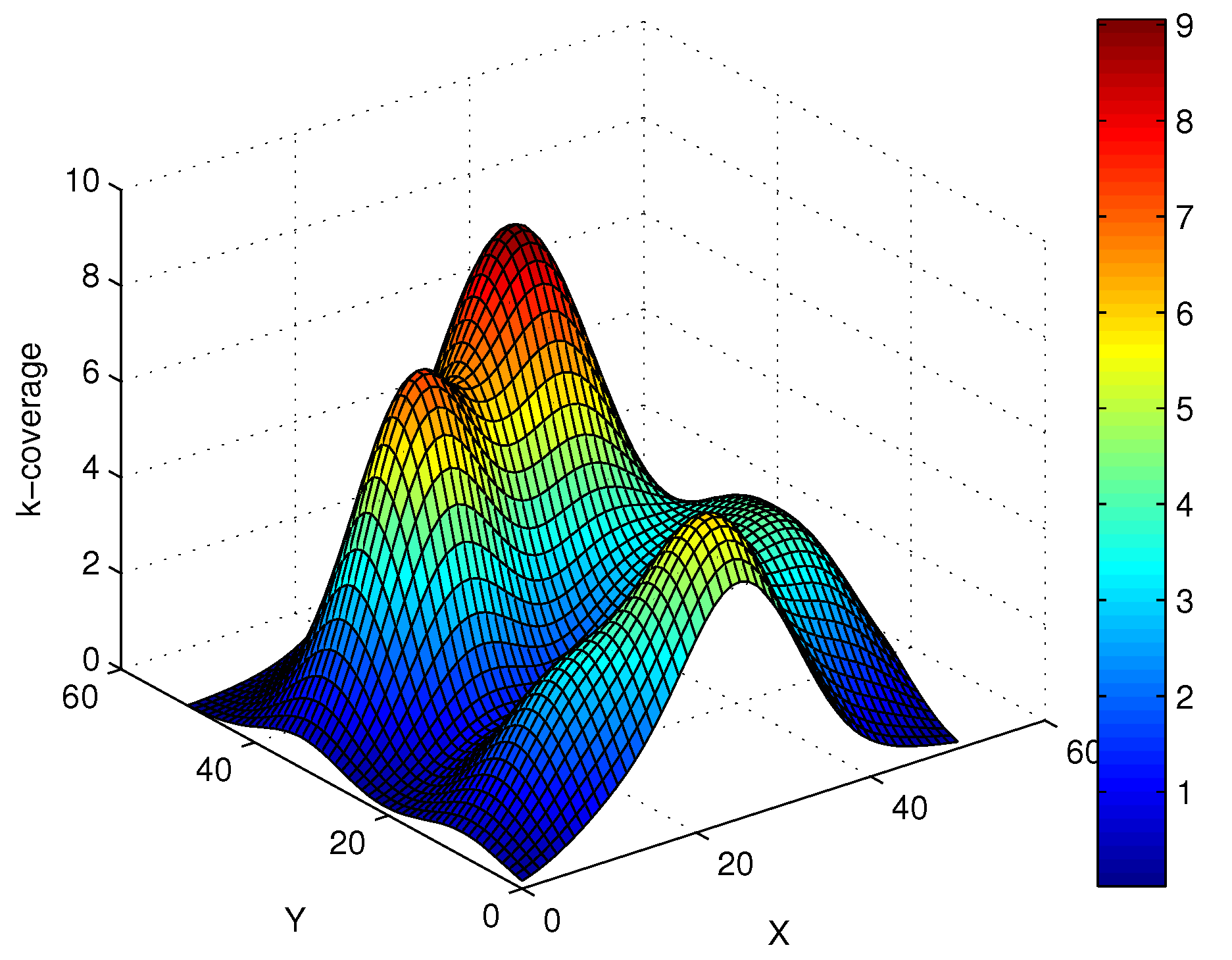
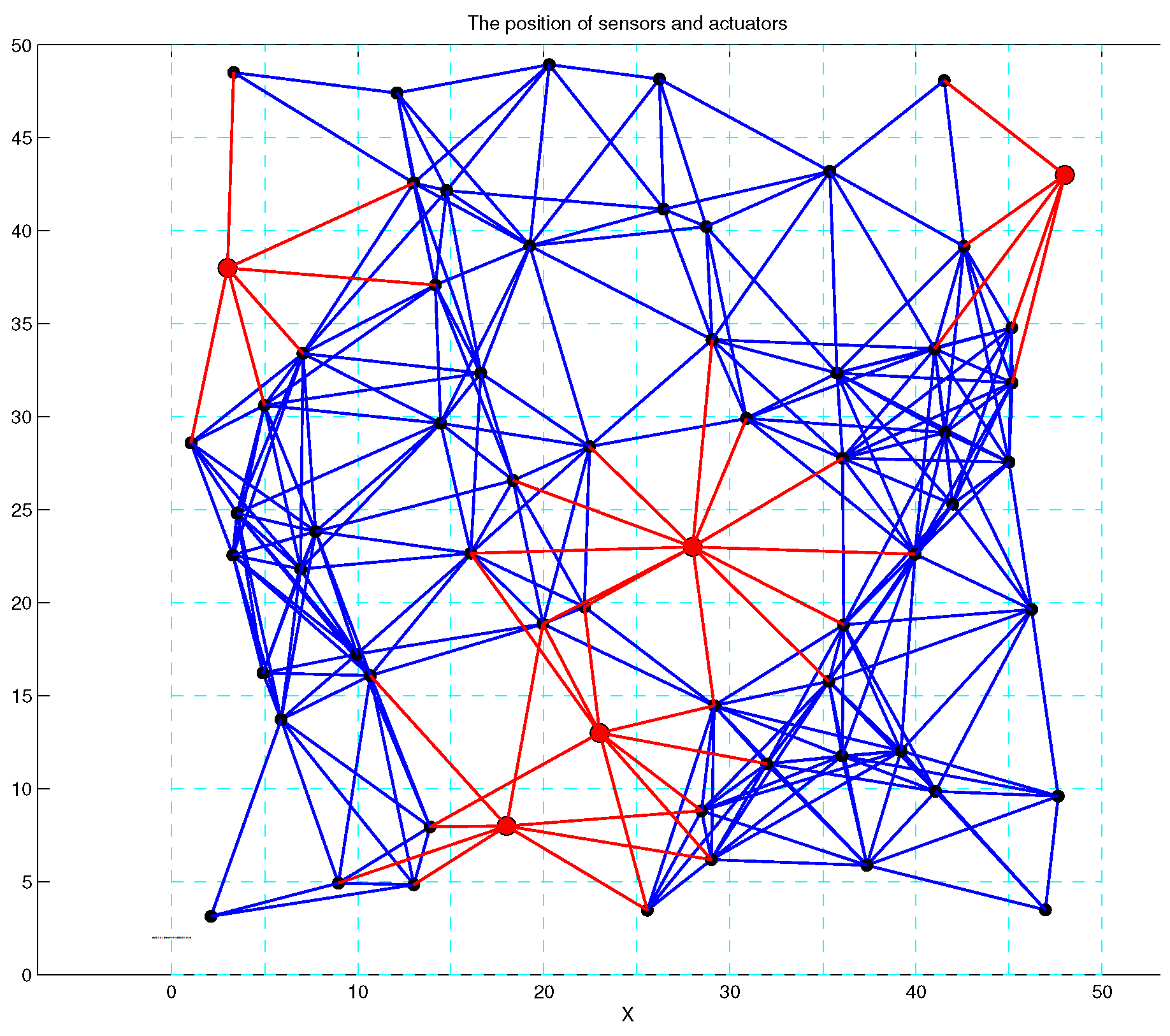
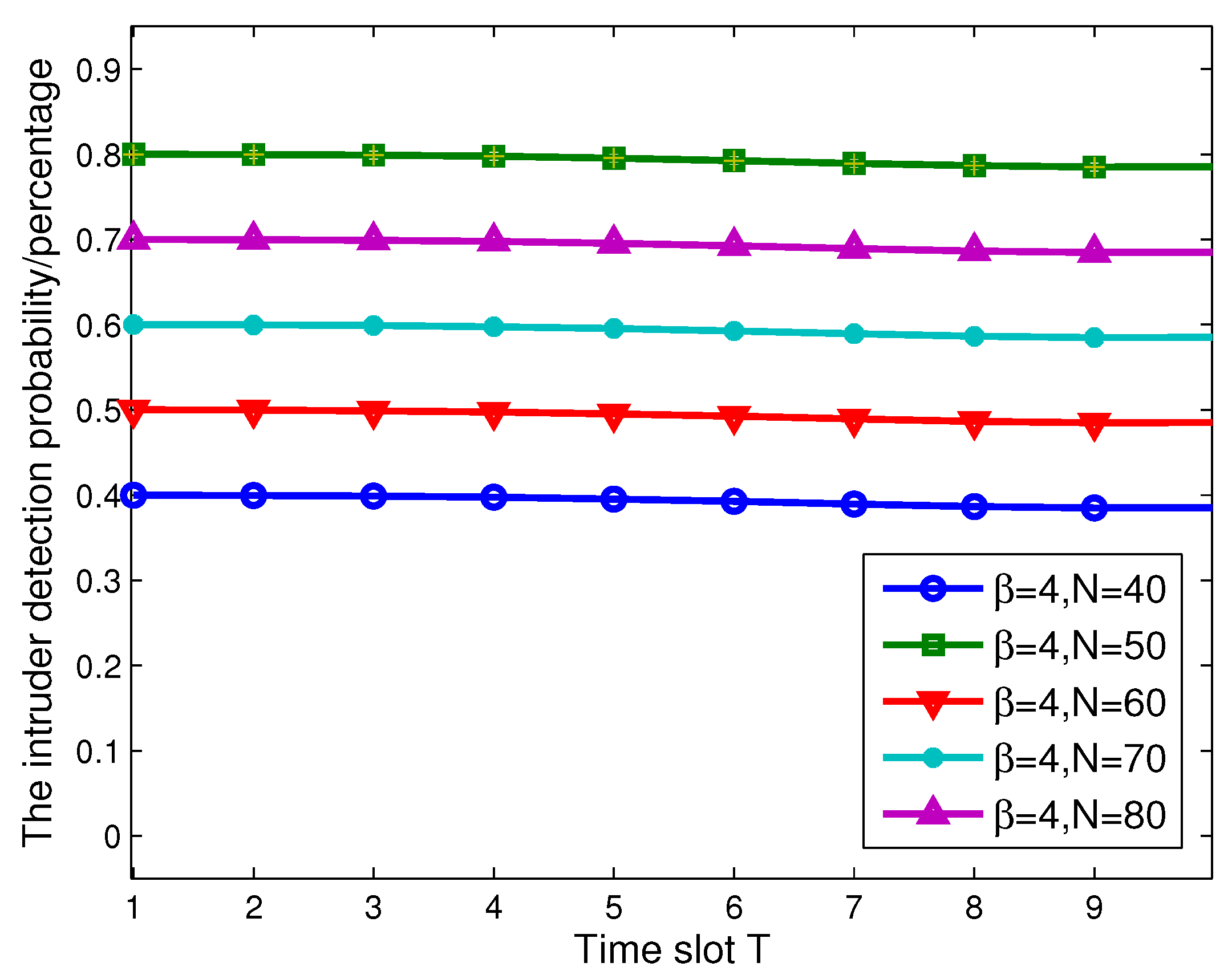
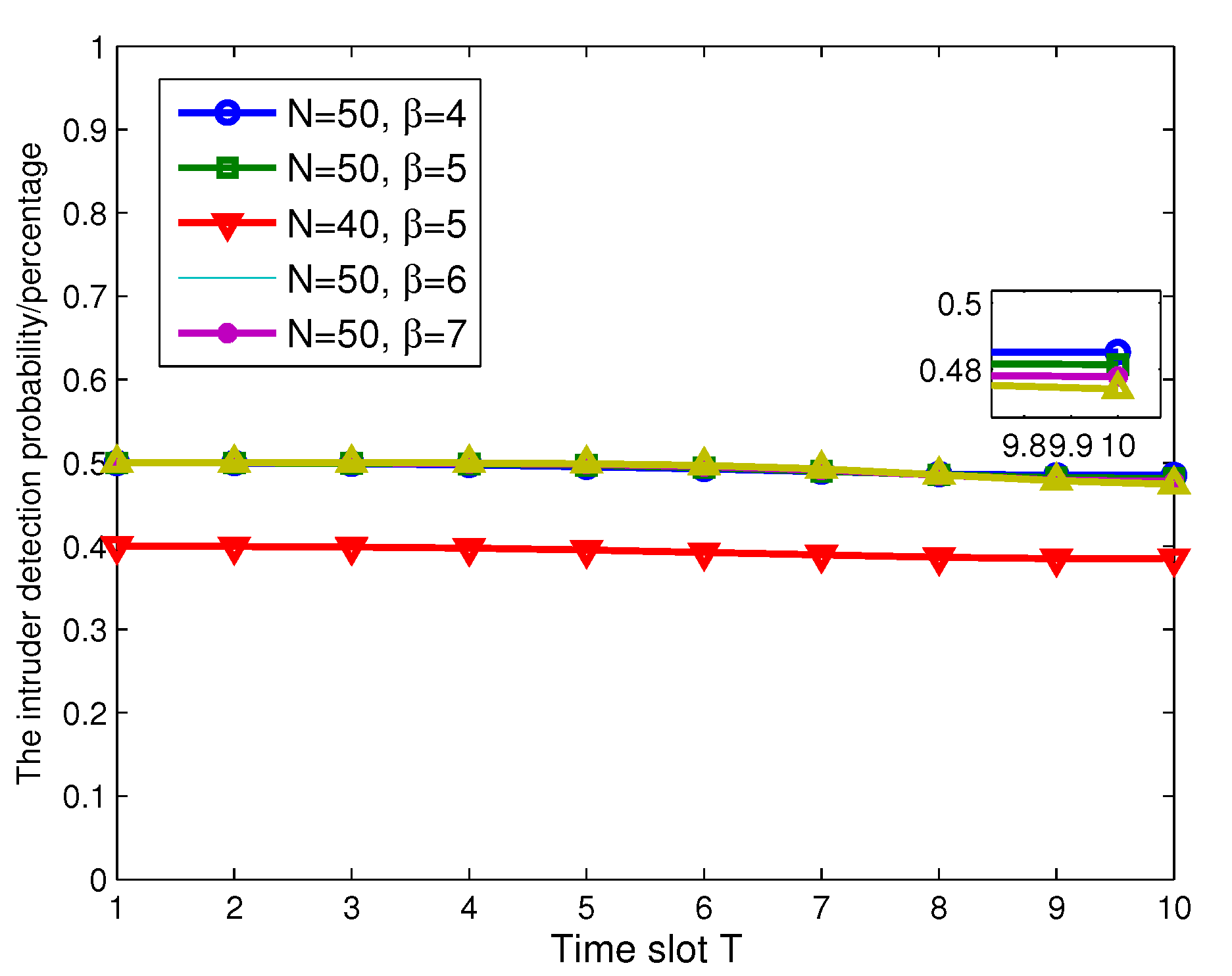
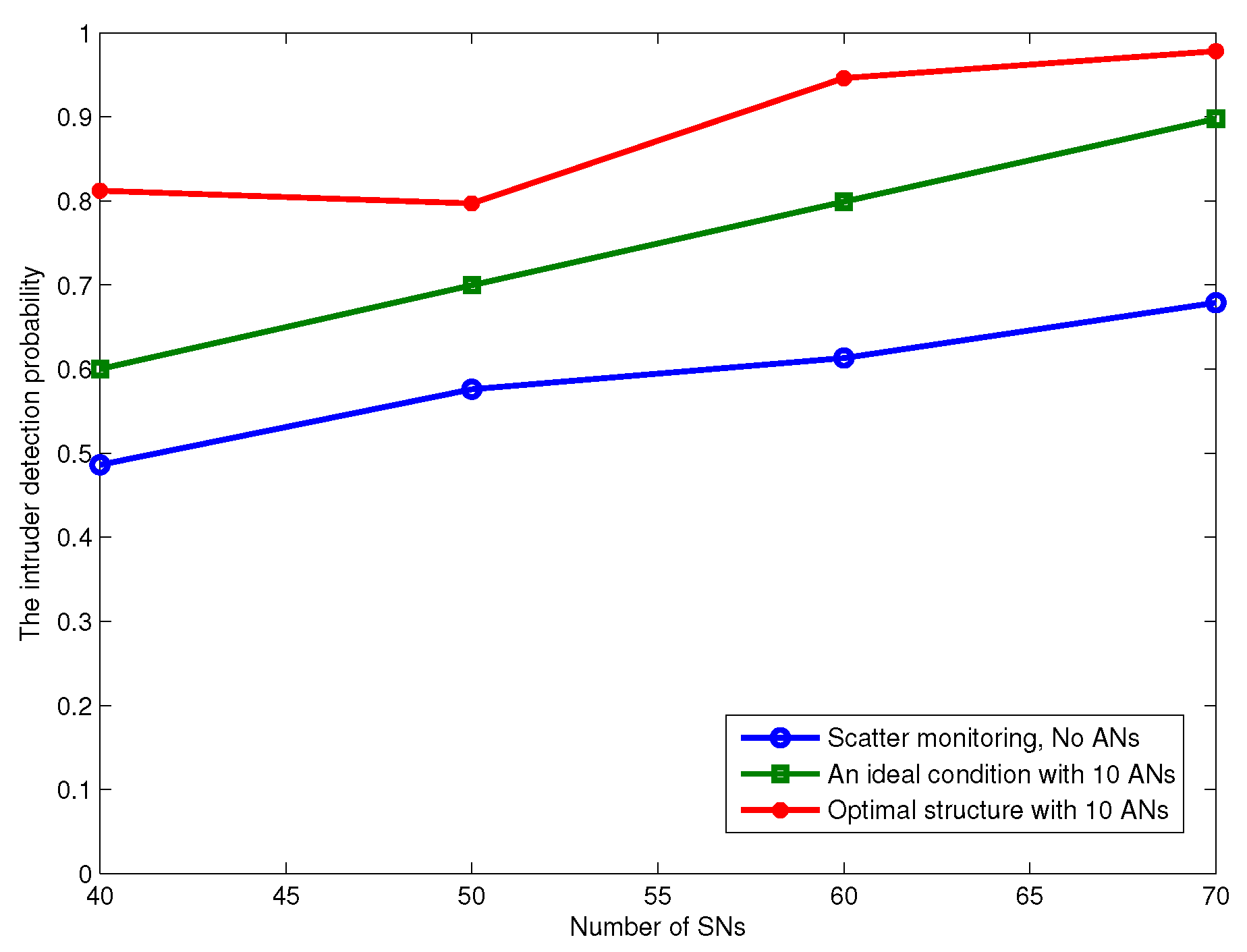
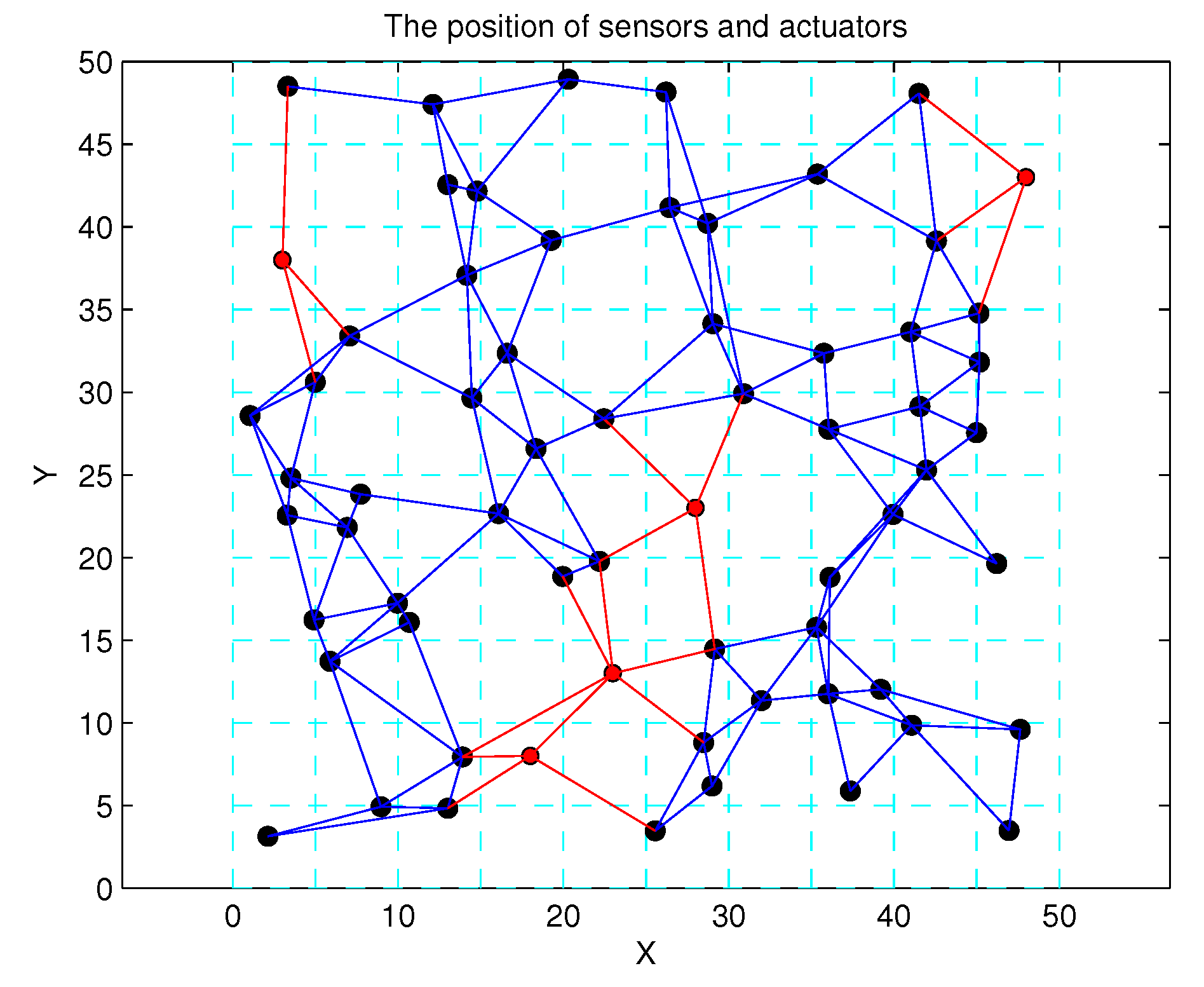
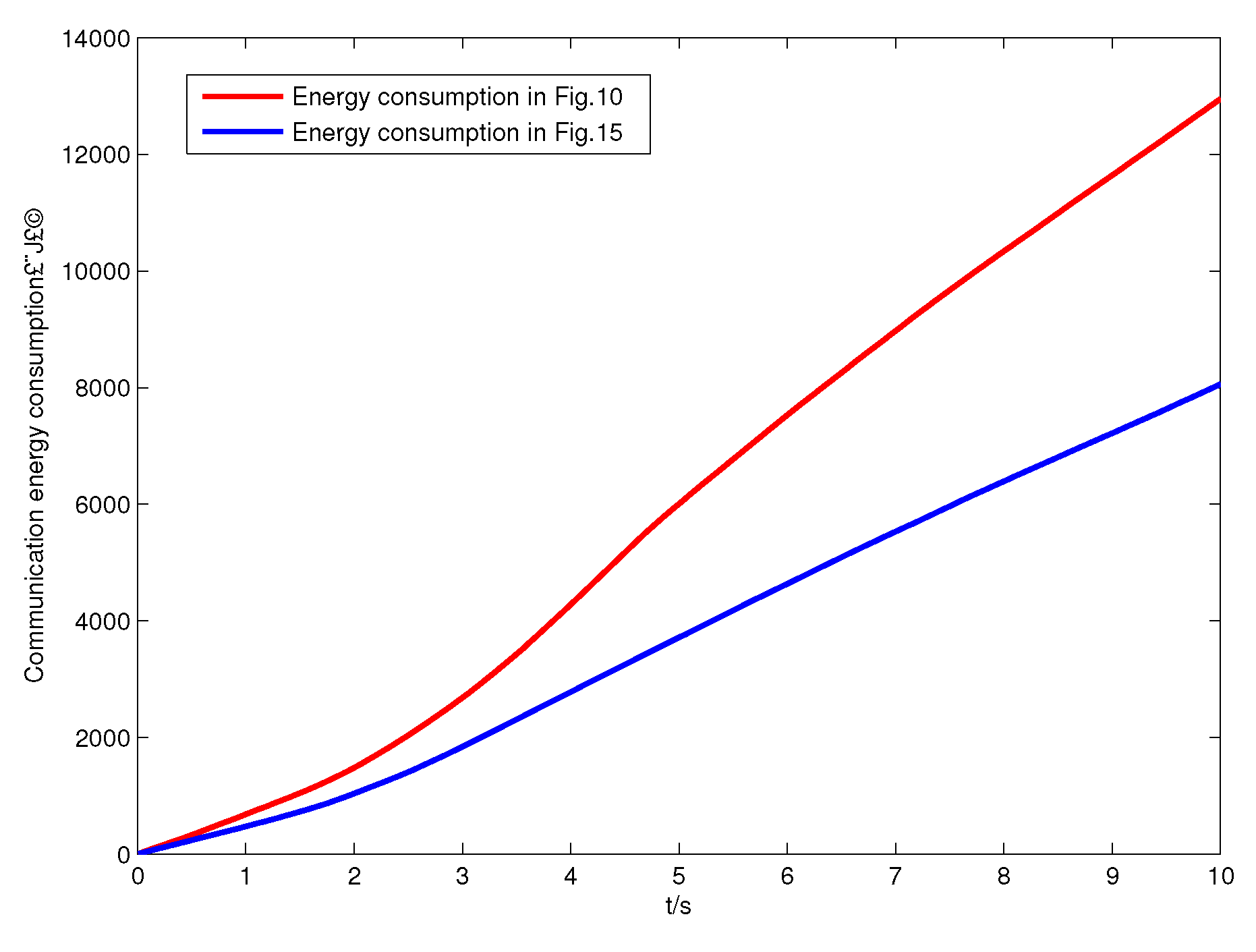
4. Simulation Results
5. Conclusion and Future Work
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Akyildiz, I.; Pompili, D.; Melodia, T. Underwater Acoustic Sensor Networks: Research Challenges. Ad Hoc Netw. 2005, 3, 257–279. [Google Scholar] [CrossRef]
- Zeng, Z.; Fu, S.; Zhang, H.; Dong, Y.; Cheng, J. A survey of underwater optical wireless communications. IEEE Commun. Surv. Tutor. 2017, 19, 204–238. [Google Scholar] [CrossRef]
- Kim, H.; Cho, H. SOUNET: Self-organized underwater wireless sensor network. Sensors 2017, 17, 283. [Google Scholar] [CrossRef] [PubMed]
- Braca, P.; Goldhahn, R.; Ferri, G.; Lepage, K. Distributed information fusion in multistatic sensor networks for underwater surveillance. IEEE Sens. J. 2015, 16, 4003–4014. [Google Scholar] [CrossRef]
- Xu, B.; Zhu, Y.; Kim, D.; Li, D.; Jiang, H.; Tokuta, A. Strengthening barrier-coverage of static sensor network with mobile sensor nodes. Wire. Netw. 2016, 22, 1–10. [Google Scholar] [CrossRef]
- Ma, H.; Yang, M.; Li, D.; Hong, Y. Minimum camera barrier coverage in wireless camera sensor networks. In Proceedings of the IEEE INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 217–225. [Google Scholar]
- Chen, J.; Li, J.; Lai, T. Energy-Efficient Intrusion Detection with a Barrier of Probabilistic Sensors: Global and Local. IEEE Trans. Wirel. Commun. 2012, 12, 118–126. [Google Scholar] [CrossRef]
- Chen, A.; Kumar, S.; Lai, T. Local barrier coverage in wireless sensor networks. IEEE Trans. Mob. Comput. 2010, 9, 491–504. [Google Scholar] [CrossRef]
- He, S.; Chen, J.; Li, X.; Shen, X.; Sun, Y. Mobility and intruder prior information improving the barrier coverage of sparse sensor networks. IEEE Trans. on Mob. Comput. 2014, 13, 1268–1282. [Google Scholar]
- Li, S.; Shen, H. Minimizing the maximum sensor movement for barrier coverage in the plane. In Proceedings of the IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April–1 May 2015; pp. 244–252. [Google Scholar]
- Kim, D.; Wang, W.; Son, J.; Wu, W.; Lee, W.; Tokuta, A. Maximum lifetime combined barrier-coverage of weak static sensors and strong mobile sensors. IEEE Trans. Mob. Comput. 2017, in press. [Google Scholar] [CrossRef]
- Kumar, S.; Lai, T.; Arora, A. Barrier coverage with wireless sensors. Wirel. Netw. 2007, 13, 817–834. [Google Scholar] [CrossRef]
- Pompili, D.; Melodia, T.; Akyildiz, I. Three-dimensional and two-dimensional deployment analysis for underwater acoustic sensor networks. Ad Hoc Netw. 2009, 7, 778–790. [Google Scholar] [CrossRef]
- Ammari, H.; Das, S. A study of k-coverage and measures of connectivity in 3D wireless sensor networks. IEEE Trans. Comput. 2010, 59, 243–257. [Google Scholar] [CrossRef]
- Lin, K.; Xu, T.; Song, J.; Sun, Y. Node scheduling for all-directional intrusion detection in SDR-based 3D WSNs. IEEE Sens. J. 2016, 16, 7332–7341. [Google Scholar] [CrossRef]
- Liu, J.; Wang, Z.; Peng, Z.; Cui, J.; Fiondella, L. Suave: Swarm underwater autonomous vehicle localization. In Proceedings of the IEEE Conference on Computer Communications (INFOCOM), Toronto, ON, Canada, 27 April–2 May 2014; pp. 64–72. [Google Scholar]
- Namesh, C.; Ramakrishnan, D. Analysis of VBF protocol in underwater sensor network for static and moving nodes. Int. J. Comput. Netw. Appl. 2015, 2, 20–26. [Google Scholar]
- Luo, X.; Feng, L.; Yan, J.; Guan, X. Dynamic coverage with wireless sensor and actor networks in underwater environment. J. Autom. Sin. 2015, 2, 274–281. [Google Scholar]
- Yan, J.; Chen, C.; Luo, X.; Yang, X.; Hua, C.; Guan, X. Distributed formation control for teleoperating cyber-physical system under time delay and actuator saturation constrains. Inf. Sci. 2016, 370–371, 680–694. [Google Scholar] [CrossRef]
- Barr, S.; Wang, J.; Liu, B. An efficient method for constructing underwater sensor barriers. J. Commun. 2011, 6, 370–383. [Google Scholar] [CrossRef]
- Liu, J.; Wang, Z.; Zuba, M.; Peng, Z.; Cui, J.; Zhou, S. DA-Sync: A doppler-assisted time-synchronization scheme for mobile underwater sensor networks. IEEE Trans. Mob. Comput. 2014, 13, 582–595. [Google Scholar] [CrossRef]
- Yan, J.; Xu, Z.; Wan, Y.; Chen, C.; Luo, X. Consensus estimation-based target localization in underwater acoustic sensor networks. Int. J. Robust Nonlin. Control 2017, 27, 1607–1627. [Google Scholar] [CrossRef]
- Cayirci, E.; Tezcan, H.; Dogan, Y.; Coskun, V. Wireless sensor networks for underwater survelliance systems. Ad Hoc Netw. 2006, 4, 431–446. [Google Scholar] [CrossRef]
- Liu, B.; Ren, F.; Lin, C.; Yang, Y.; Zeng, R.; Wen, H. The redeployment issue in underwater sensor networks. In Proceedings of the Global Telecommunications Conference, New Orleans, LO, USA, 30 November–4 December 2008; pp. 1–6. [Google Scholar]
- Partan, J.; Kurose, J.; Levine, B. A survey of practical issues in underwater networks. SIGMOBILE Mob. Comput. Commun. Rev. 2007, 11, 23–33. [Google Scholar] [CrossRef]
- Sozer, E.; Stojanovic, M.; Proakis, J. Underwater acoustic networks. IEEE Ocean Eng. 2000, 25, 72–83. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, X.; Xie, B.; Wang, D.; Agrawal, D. Intrusion detection in homogeneous and heterogeneous wireless sensor networks. IEEE Trans. Mob. Comput. 2008, 7, 698–711. [Google Scholar] [CrossRef]
- Luo, X.; Yan, Y.; Li, S.; Guan, X. Topology control based on optimally rigid graph in wireless sensor networks. Comput. Netw. 2013, 57, 1037–1047. [Google Scholar] [CrossRef]
- Maehara, H. Distance graphs in Euclidean space. Ryukyu Math. J. 1992, 5, 33–51. [Google Scholar]
- Yan, J.; Chen, C.; Luo, X.; Liang, H.; Yang, X.; Guan, X. Topology optimization based distributed estimation in relay assisted wireless sensor networks. IET Control Theor. Appl. 2014, 8, 2219–2229. [Google Scholar] [CrossRef]
- Jiang, P.; Feng, Y.; Wu, F. Underwater sensor network redeployment algorithm based on wolf search. Sensors 2016, 16, 1754. [Google Scholar] [CrossRef] [PubMed]
- Mostafaei, H.; Meybodi, M. An energy efficient barrier coverage algorithm for wireless sensor networks. Wirel. Pers. Commun. 2014, 77, 2099–2115. [Google Scholar] [CrossRef]


© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yan, J.; Li, X.; Luo, X.; Guan, X. Virtual-Lattice Based Intrusion Detection Algorithm over Actuator-Assisted Underwater Wireless Sensor Networks. Sensors 2017, 17, 1168. https://doi.org/10.3390/s17051168
Yan J, Li X, Luo X, Guan X. Virtual-Lattice Based Intrusion Detection Algorithm over Actuator-Assisted Underwater Wireless Sensor Networks. Sensors. 2017; 17(5):1168. https://doi.org/10.3390/s17051168
Chicago/Turabian StyleYan, Jing, Xiaolei Li, Xiaoyuan Luo, and Xinping Guan. 2017. "Virtual-Lattice Based Intrusion Detection Algorithm over Actuator-Assisted Underwater Wireless Sensor Networks" Sensors 17, no. 5: 1168. https://doi.org/10.3390/s17051168
APA StyleYan, J., Li, X., Luo, X., & Guan, X. (2017). Virtual-Lattice Based Intrusion Detection Algorithm over Actuator-Assisted Underwater Wireless Sensor Networks. Sensors, 17(5), 1168. https://doi.org/10.3390/s17051168






