2.1. The BORPN Class Properties
In this section we will to explain the
Petri net class properties [
15,
16]. This class is a subclass of the
[
1,
2] and
[
3] Petri nets, therefore, all the existing theoretical results for these networks can be applied to this subclass, however contrary reasoning is not possible. The
class has valuable structural information given by its reduced structure that comes from the restriction imposed on transitions of the BORPN class, because it only performs binary operations. Each transition could take or release resources as a unit, much like the behavior of a routing algorithm as the type of wormhole that requests and releases the channels as resources to transport messages like chains of bits or flits. The BORPN class is defined as follows:
Definition 1. (
The Petri Net Class for Ordered Binary Resources).
Let’s say that is a finite set of indices. A Petri Net Class for Ordered Binary Resources is a strongly connected Petri net, self-loops-free where:
- (1)
is a partition such that:- (a)
, y , for all .
- (b)
- (c)
, .
- (2)
is a partition such that:- (a)
, , , for each , for all .
- (b)
, , , for each , for all .
- (3)
For all , the subnet generated by is a strongly connected state machine, such that each cycle contains and induces a minimal T-Semiflow.
- (4)
For each there is a minimal P–Semiflow, , such that y .
- (5)
.
The whole model of Petri net BORPN comprises various strongly connected networks represented by where . A loop-free Petri net exists if and only if being state machine (SM). Where each SM corresponds to a subnet. These SMs together build a single Petri net of the class. The deadlock problems are related to unachievable states produced by diverse processes that, in a simultaneous manner, retain and ask for resources, thus generating a loop that does not allow any evolution of the processes. As shown in Definition 1, Paragraph 1, places are partitioned into three groups representing: (a) process places ; (b) idle places representing pending messages; and (c) resources . Resource places represent the availability of the resources that, due to the RAS perspective, cannot be created or destroyed by the processes. The structure of the BORPN class requires that each cycle contains the idle places . If a process starts, it acquires a mark from the idle place and when the process ends, the mark of the idle place should return. In other words, during the evolution of the process, various resources can be used, although they must be released when the process is completed. Liveliness property is sought to ensure completion of the processes and thus have the system free of deadlocks. Each process requires the use of at least one resource, however it must be acquired or released as a unit. For the above reason, the component is a Boolean vector due to the peculiar behavior of this network.
Transitions in a
have a particular behavior following our approach of the
RAS perspective. We consider that the process behavior resembles a pipe, which can be partitioned into process units. The first processing unit acquiring resources is the last unit to release them. This approach restricts the behavior of the transitions and allows us to model particular systems more accurately, unlike traditional approaches. Therefore, we are able to model a process that represents the transportation of objects (
messages,
items, etc.) via networks or warehouse distribution centers. Definition 1, Paragraph 2 is related to transitions that are partitioned into two disjoint sets. Transitions
and
mean “acquire” and “release”, respectively. Therefore,
and
where
. However, this restriction does not impede
bifurcations, one useful characteristic to represent complex systems where deadlock problems arise. In [
13] where it is proved that a state machine strongly connected
is live, which is why it induces an invariant property in the conservation of the marks in the places. For a
, this property is established in Definition 1,
Section 3, where for all
, the subnet
generated by
where
is a strongly connected state machine, such that each cycle contains a place of
. Each cycle containing the
idle place closes a circuit that induces a
T-Semiflow on that path. Finally, in the Definition 1, Paragraphs 4 and 5 are related to the invariant structural properties of the resources and idle places respectively. Thus, for any
there is a minimum
P-Semiflow where
. Process places joined with the resource
are known as carrier places
. These places charge the availability of resources while representing a process state, as shown by Definition 2.
Definition 2. Consider that is a BORPN and the set of resource locations. The set of carrier places of is the support of the minimal P-Semiflow resource where .
A
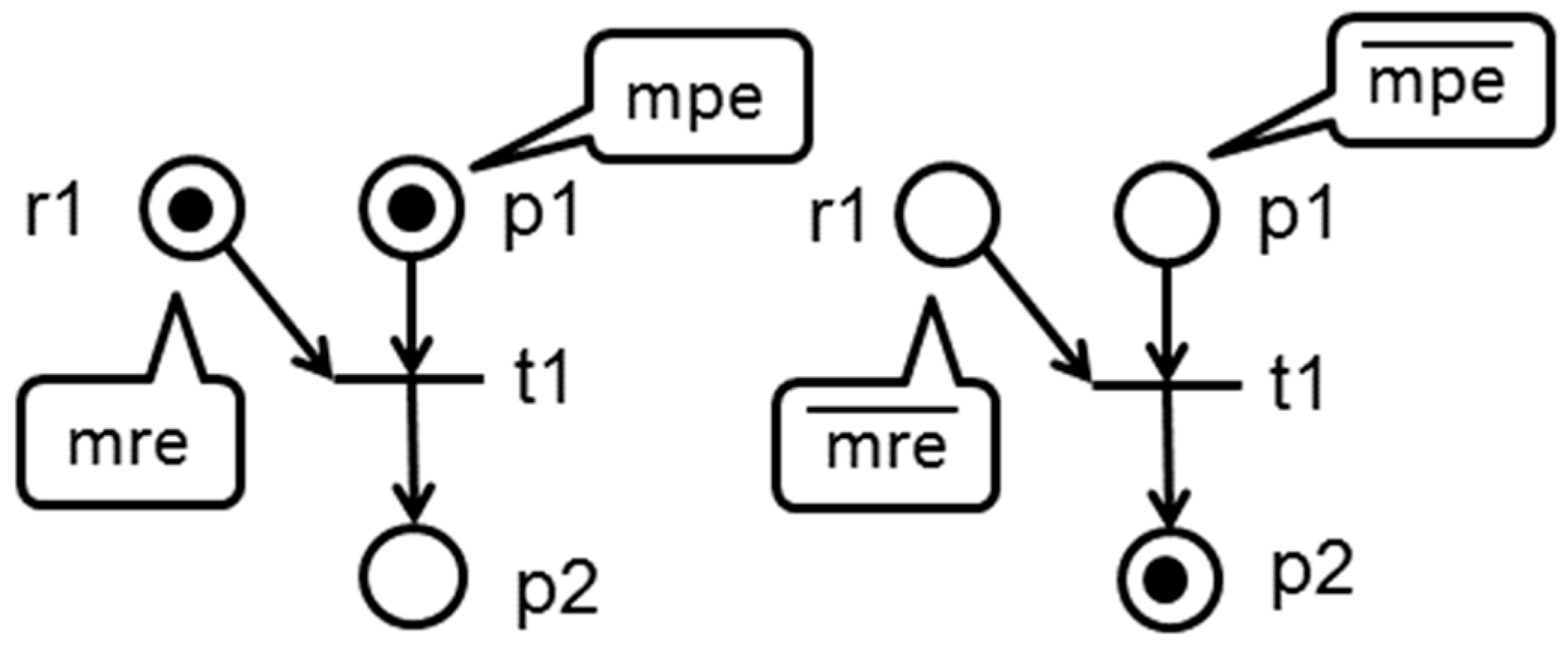
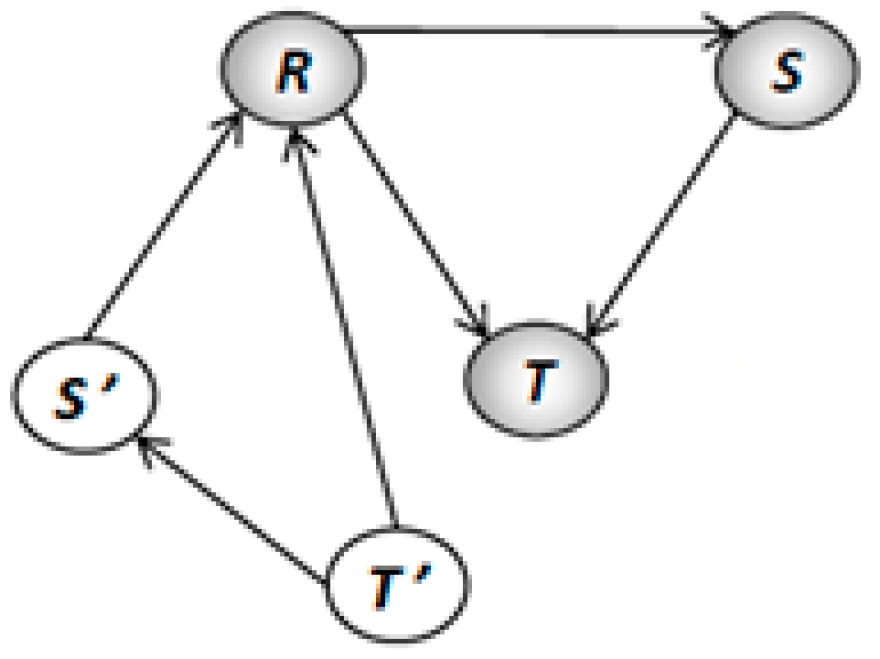
is a state machine strongly connected with resources, therefore all transitions have a single point of entry/exit process and would have a single place input/output resource. Thus, transitions may be characterized as enabled or disabled, by marking the place of resource as shown in
Figure 1 and more formally explained in the Definitions 3 and 4.
Definition 3. Consider that is a BORPN, with the set of resources places and the set of process places. A transaction is enabled on the marking or (disabled on the marking) summarized or () iff in the M marking of p or ().
Definition 4. Consider that is a BORPN, being the set of resources places and the set of process places. Transition is enabled on the marking or (disabled on the marking) summarized or () iff the M marking of p as or ().
For transitions that release resources,
, markings in
are enough for them so they can be fired, but for the set that acquire resources,
, there should be markings in
and
so that they can be fired. The
transition from the left side of
Figure 1 is
enabled in the process marking and
enabled in the resources marking, which is the opposite to the transition from the right side that is disabled in the process marking process and disabled in the resource marking resource. A path is a
T-Semiflow of
as
, where for each
does not satisfy one of the four conditions that are sufficient and necessary for the existence of a deadlock in [
14]. This type of route does not have the
retention and wait condition because it only requests a resource to complete the entire process. Therefore, each
place that belongs to this type of
T-Semiflow is as follows:
where
. Due to the structure of the
class, some places will never be included in a deadlocked situation and are known as places-without-deadlock.
Definition 5. Consider that is a BORPN, with the set of resources places and the set of process places. A place is called deadlock-free-place iff .
The places that meet requirements of Definition 5 will be fired when they have the marking mpe, so they never belong to a state of deadlock, however, they can form a structural part of a siphon.
2.2. BORPN Class
This class is defined to face deadlock problems in concurrent systems [
16] such as sensor networks that use wormhole routing algorithms following our
RAS viewpoint of the processes. The
is an ordinary Petri nets class where the
P-Semiflow of a resource is a binary vector, which is why there is a directed path between the transitions that take the resource and the transitions that release it.
Definition 6. (A directed path). A directed path is a sequence of places and transitions such that from to where and , for and .
When this directed path is related to a class it is known as a resource zone, as shown in Definition 7. This characteristic is very important in order to avoid extensive structural analysis of the Petri net model, hence reducing the amount of states of the system that will be analyzed.
Definition 7. (Zone of a resource). Consider that , is a BORPN and the set of resources. The zone of a resource is the set of places holders of that intercepts the net as , where and .
The subindex represents the BORPN class, and if there is more than one zone, the subindex will increase. When the index j is omitted, we assume only one zone for this resource. In linear processes there is only one path between capture and release of the resource, however for non-linear processes there will be more than a catch or release of the resource. Corollary 1 states the existing structure for a zone in linear processes.
Corollary 1. (Zone of a resource in linear processes). Consider that is a BORPN with only lineal processes, where is the set of resources places. Consider that , such that the zone of a resource r in the net for . The place where . So that such that and .
In a strongly connected state machine there could be non-linear processes, so in this network, the zone of a resource should be generalized to consider different acquisitions and releases of the resources. Due to the RAS approach to the process, the places of the first part of the process are of the set where means acquiring. The places that are maintained in the latter part of the process belong to the set , where means releasing. Corollary 2 describes the structure for a zone in non-linear processes.
Corollary 2. (Zone of a resource in non-linear processes). Consider that is a BORPN with non-lineal processes, where is the set of resources places and . Consider , where In this way, such that So that, and
The zoning of resources would produce an overlap on the zones of the resources. When there is an overlap between different resource zones, it will be known as teams of resources. The concept of team comes from the point of view where a process acquires/releases various resources in strict order. They are all working together for the progress of the process as a team. Moreover, teams are a characterization of this order and will be used to describe the new BORPN class. Definition 8 summarizes this concept of team in a .
Definition 8. Consider that is a BORPN, being the set of resources. A team of resources is a set of places where , satisfying that (1) and (2) ; (3)
The set exists because of the intersection or overlapping between two resources in the Petri net model, however it should be a unique set. The second condition prevents the existence of more than one set through the input and output resources. Finally, to prevent subsets between resources becoming involved, a particular set of locations must exist. There must be a place that does not belong to P-Semiflow of the other resource involved. If the previous conditions are met, there will be an overlapping among all involved resources, and this would be called a team of resources. A Petri net where all resources belong to a team of resources is a class and, additionally, it is necessary that all the places of a process belong to any P-Semiflow of the team resources. Finally, for each transition where the resource of the team is acquired, there is only one way, in the strongly connected state machine, to reach each transition where the resource is released.
Definition 9. (Properties of a resource of class). A Petri net is a BORPN class if all the resources belong to a team and such that , .
Some features of a BORPN class:
The initial and final states are in a collapsed state, called idle place.
The options between the paths are permitted, but iterations or loops are not.
The resources cannot be created nor destroyed.
The resources are shared between paths.
Resource places have a mark indicating the availability.
A state could use several resources.
The order in which resources are allocated must be the same as they are released.
Transitions acquire or release resources but never both events at the same time.
The behavior of several systems can be described in terms of states of the systems, since these states and their changes have a physical meaning. Based on this, we can say that an initial mark represents the lack of activity in the system and allows the start of the processes. The class is conservative with resources due to P-Semiflow, so all reachable markings will represent possible states of the system from an acceptable initial marking. The marks in places represent the maximum amount of processes waiting in the same Petri net or state machine. The marks in places model the availability of resources, therefore a mark is enough to represent it. The process place lacks initial marking because this marking represents the lack of activity in the system.
Definition 10. Consider that is a BORPN net. An initial marking is acceptable for iff:
- (1)
- (2)
- (3)
Usually, in order to implement the policy of deadlock prevention it is necessary to consider the initial marking for the Petri net model. In our avoidance control policy of deadlock, the Petri net model does not get modified, so the initial marking remains unchanged. In order to apply our policy of deadlock prevention it is necessary to add virtual resources to make the Petri net model free of deadlocks, which will keep the same initial marking as in previous resources.
All the same, if new places of processes are added, they remain empty in the initial marking. Our control policy deadlock does not add new processes to Petri net model, so no idle place will be added.