Worst-Case Cooperative Jamming for Secure Communications in CIoT Networks
Abstract
:1. Introduction
2. Related Work
2.1. Existing Work on Jamming in Physical Layer Security
2.2. Existing Work on Auction
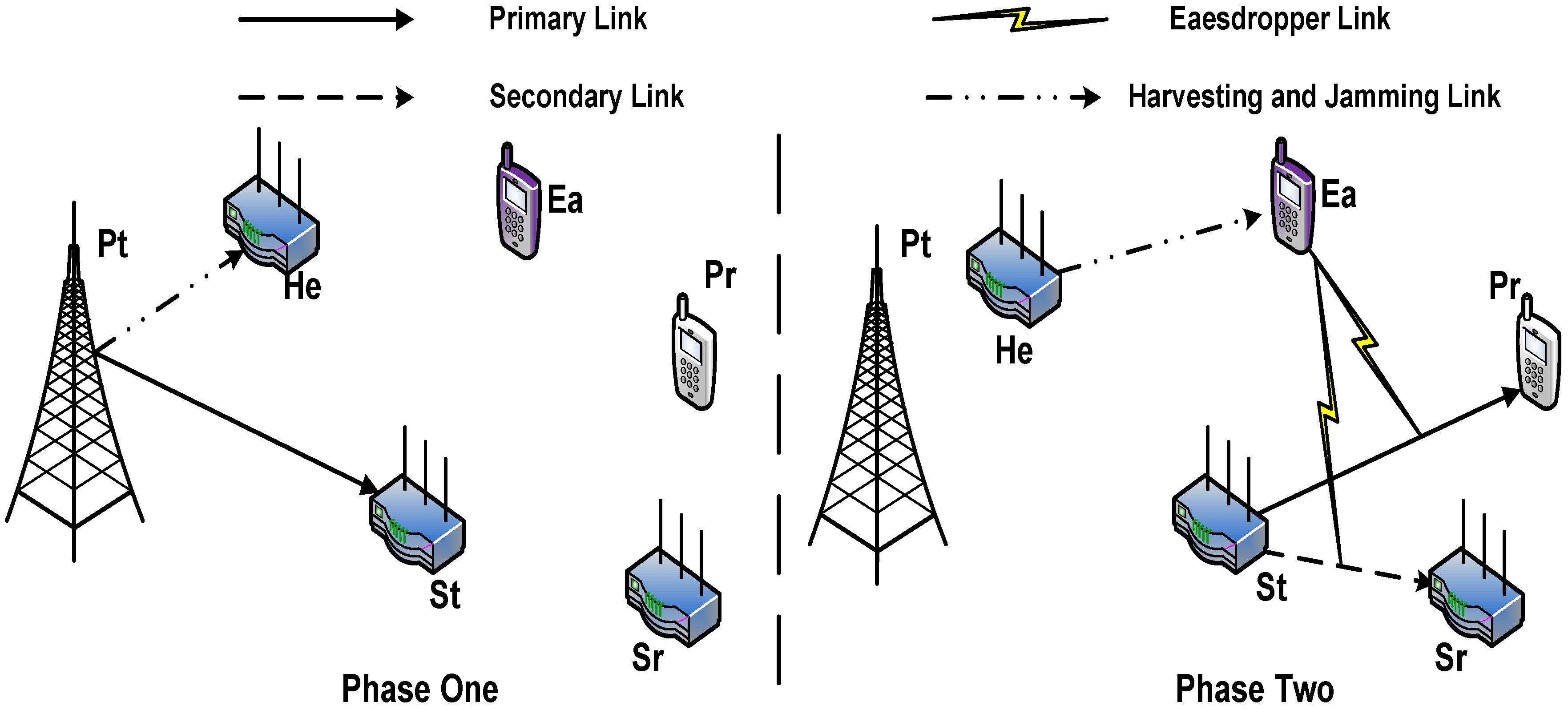
3. System and Communication Models
3.1. Communication Process in Phase 1
3.2. Communication Process in Phase 2
4. Proposed Cooperative Jamming Scheme
4.1. Problem Formulation
4.2. Proposed Solutions
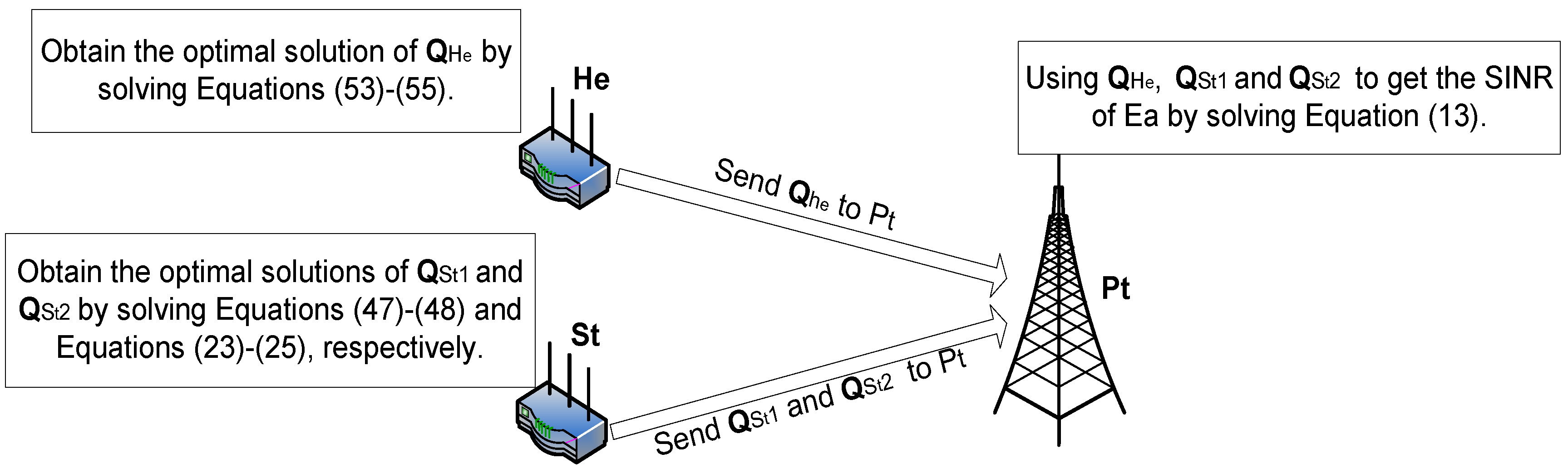
4.2.1. The First Stage
4.2.2. The Second Stage
4.3. An Illustrative Example
5. Proposed Auction Framework
- The Vickrey auction guarantees truthfulness. As we know, truthfulness means that for each bidder, reporting true optimal demand is the best strategy regardless of how the other bidders bid. Additionally, it is the critical property for an auction.
- The Vickrey auction is individual rational. Individual rationality means that the utilities of the auctioneer and the winner bidder are always positive. Achieving individual rationality ensures that both the primary user and the secondary users have incentives to participate in the auction.
5.1. Mathematical Definitions
- Auctioneer: primary user .
- Bidder: , where is the set of secondary users with size N.
- Characteristic of bidders: , where denotes the characteristic of bidder .
- Valuation of bidder : ’s valuation can be formulated as:where denotes the SINR at and denotes the expected SINR at . is the energy that has to provide to to achieve the expected SINR at .
- Bidding of bidders: , where denotes the bidding of bidder . is related to its individual valuation .
- Strategy of bidders: Φ, where describes a strategy of bidder .
- Utility of bidder : , where and denote the vectors of strategies and characteristics of the bidders, except , respectively.
5.2. Strategy of Bidders
- (1)
- , and wins the auction; one can find that the utility of would be unaffected with an unchanged . Thus, the strategy of making a false bidding cannot improve the bidder’s utility.
- (2)
- , and loses the auction; under this circumstance, the utility of equals zero.
5.3. Implementation Details
6. Simulation Study
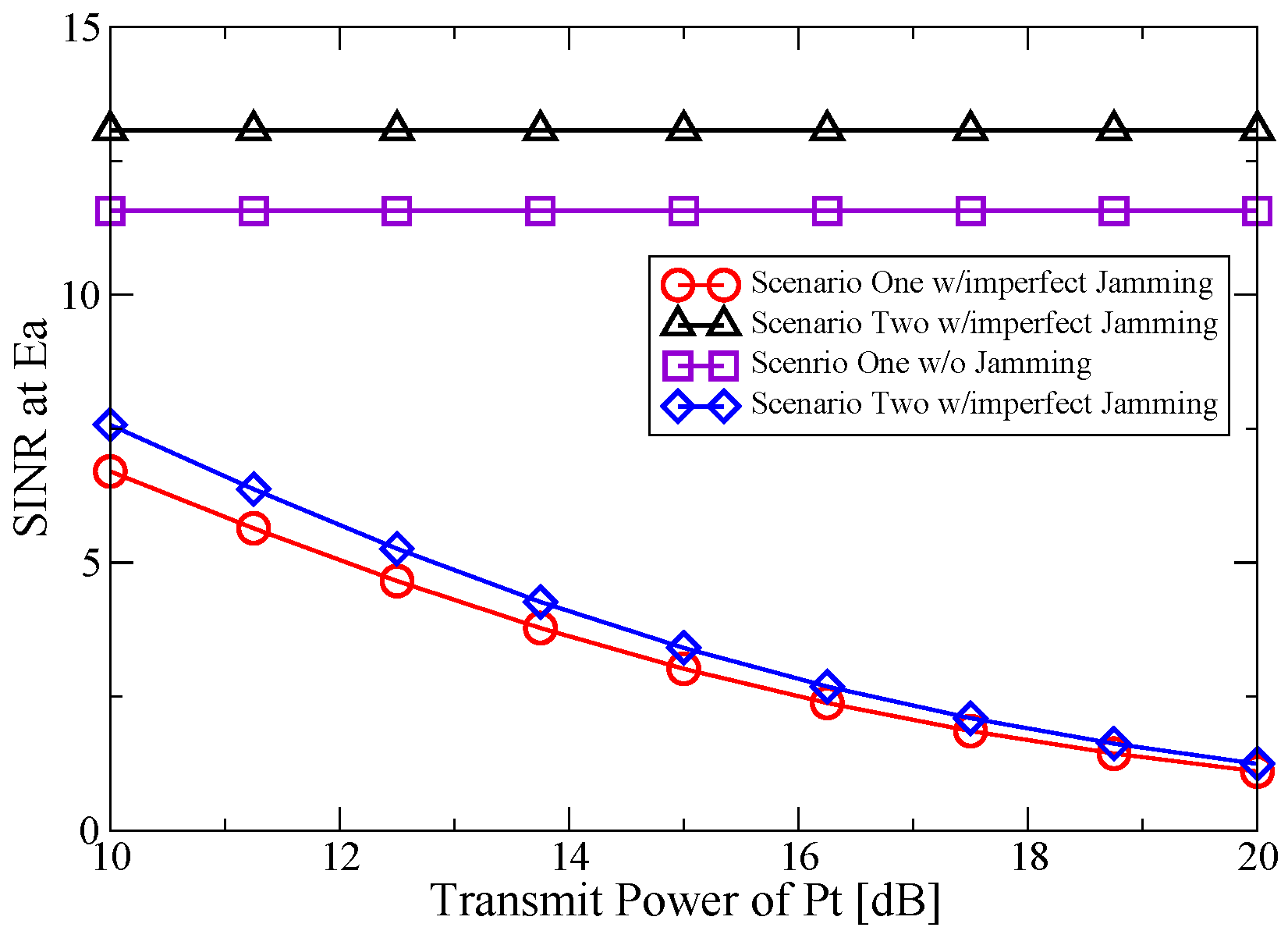
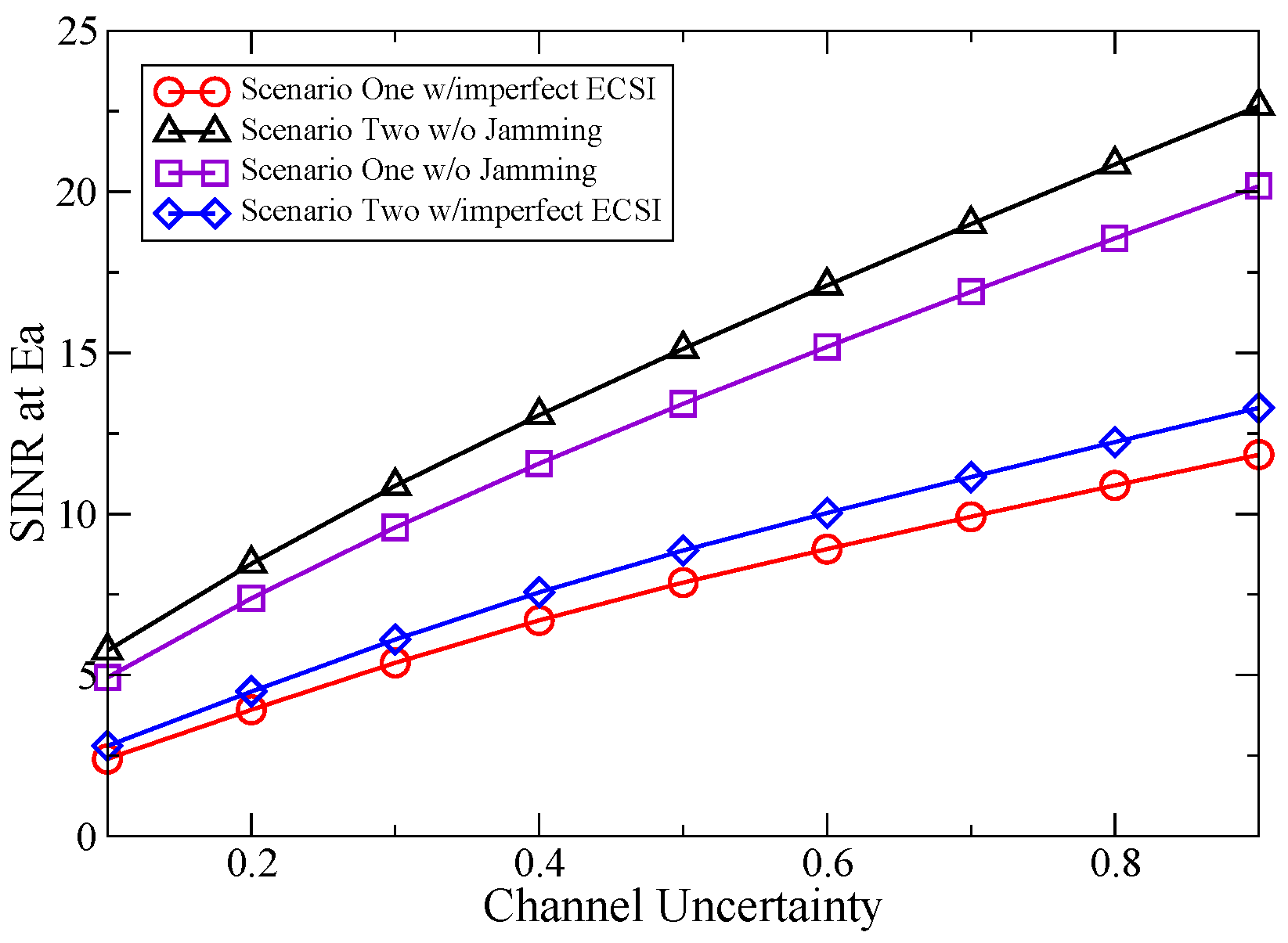
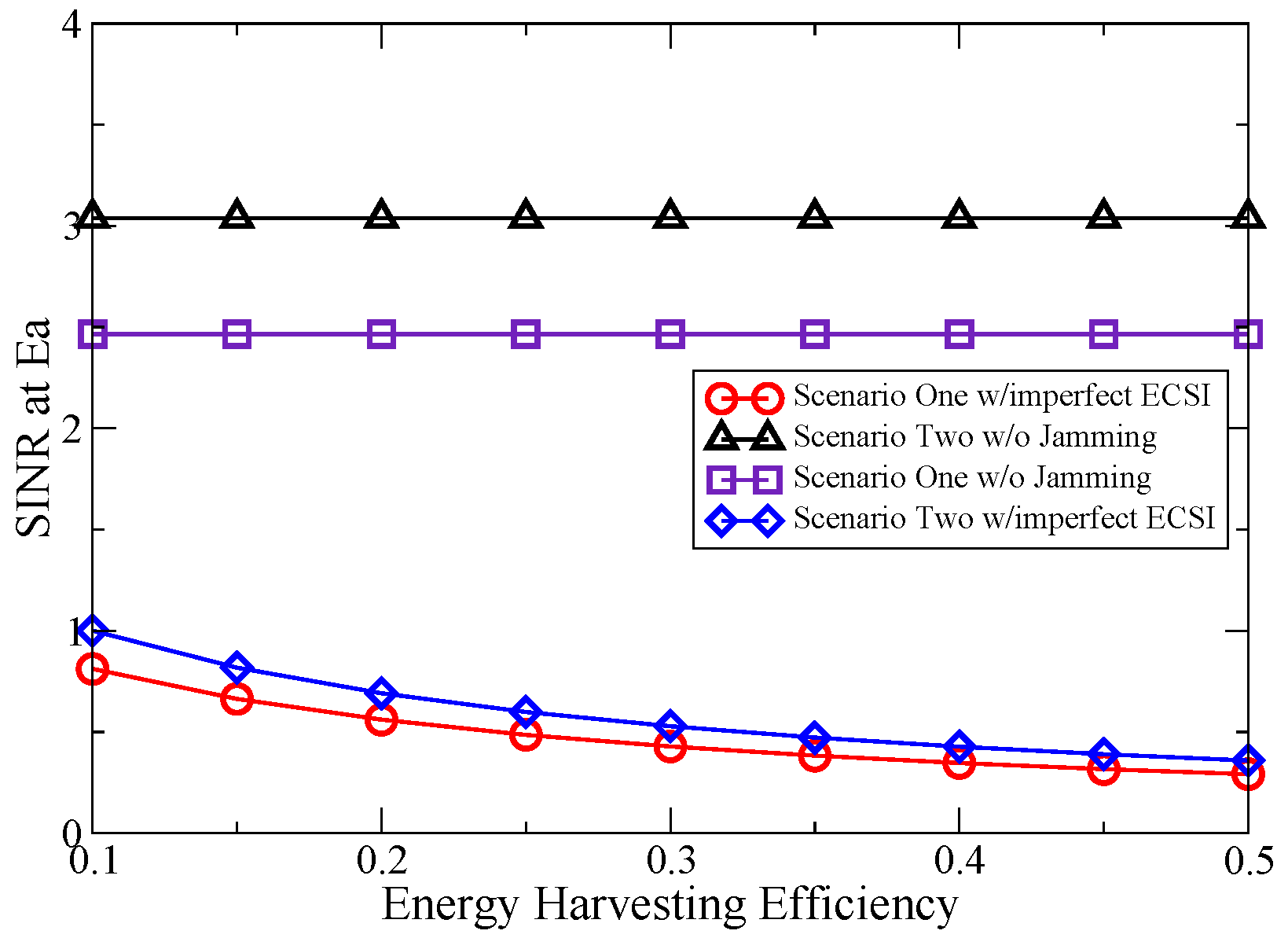
6.1. Simulation Study of the Proposed Jamming Scheme
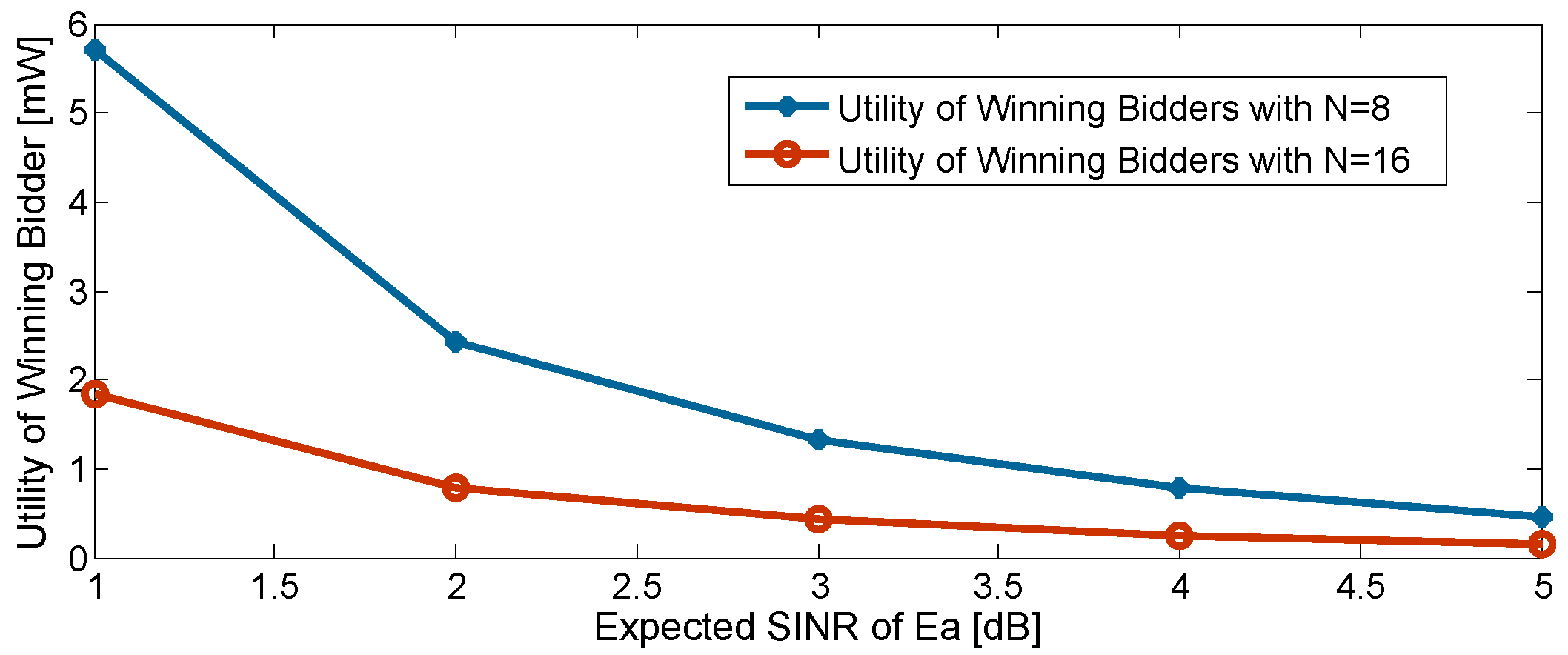
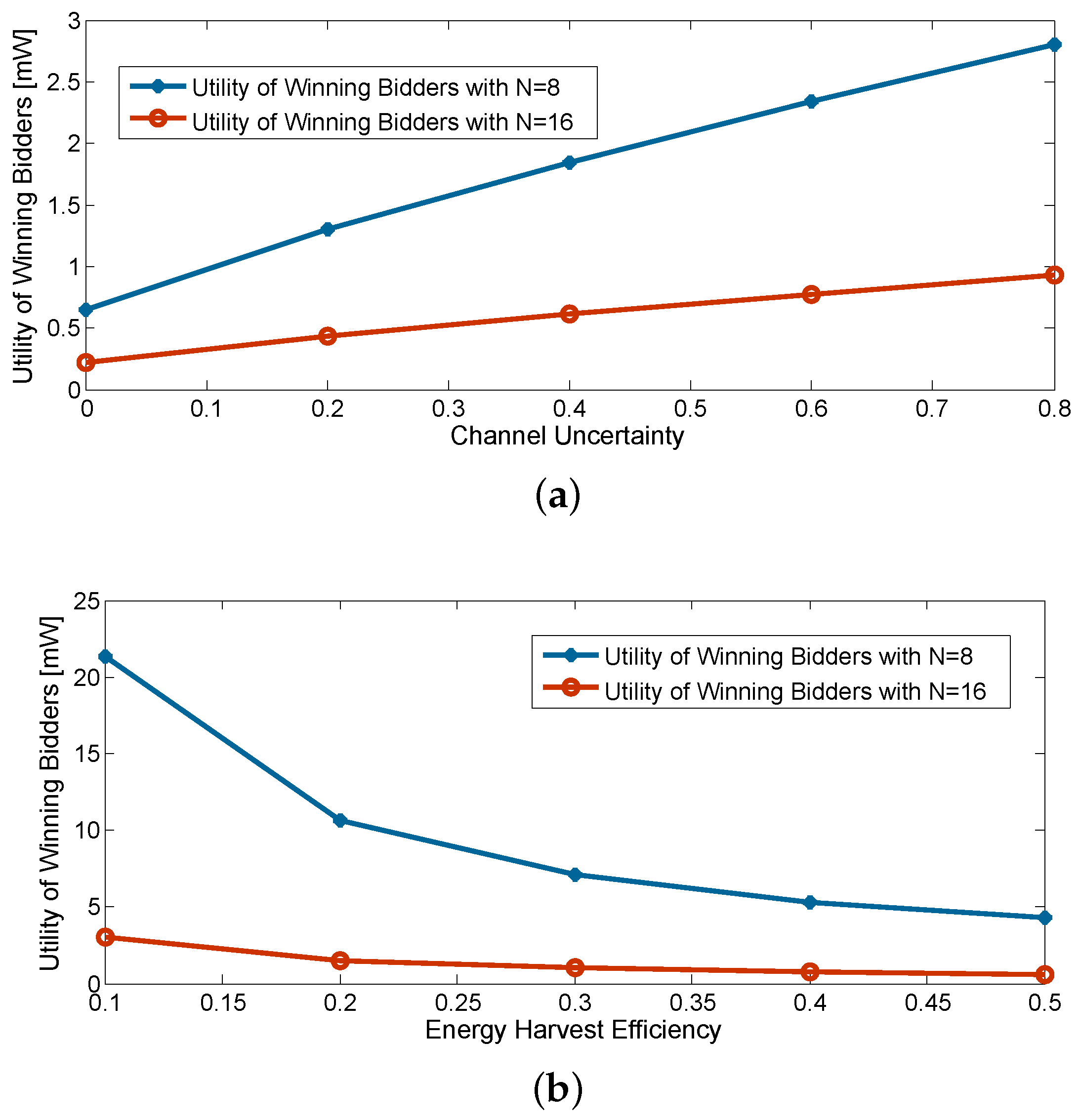
6.2. Simulation Study of the Proposed Auction Framework
7. Summary and Future Work
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Perera, C.; Zaslavsky, A.; Christen, P.; Georgakopoulos, D. Context Aware Computing for The Internet of Things: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 414–454. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Jara, A.J.; Belchi, F.J.; Alcolea, A.F.; Santa, J.; Zamora-Izquierdo, M.A.; Gomez-Skarmeta, A.F. A Pharmaceutical Intelligent Information System to detect allergies and Adverse Drugs Reactions based on Internet of Things. In Proceedings of the IEEE Pervasive Computing and Communications Workshops, Mannheim, Germany, 29 March–2 April 2010; pp. 809–812.
- Afzal, A.; Zaidi, S.A.R.; Shakir, M.Z.; Imran, M.A.; Ghogho, M.; Vasilakos, A.V.; McLernon, D.C.; Qaraqe, K. The Cognitive Internet of Things: A Unified Perspective. Mob. Netw. Appl. 2015, 20, 72–85. [Google Scholar] [CrossRef]
- Massouri, A.; Cardoso, L.; Guillon, B.; Hutu, F.; Villemaud, G.; Risset, T.; Gorce, J.-M. CorteXlab: An open FPGA-based facility for testing SDR And cognitive radio networks in a reproducible environment. In Proceedings of the IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 27 April–2 May 2014; pp. 103–104.
- Wu, Q.H.; Ding, G.R.; Xu, Y.H.; Feng, S.; Du, Z.Y.; Wang, J.L.; Long, K.P. Cognitive Internet of Things: A New Paradigm Beyond Connection. IEEE Internet Things J. 2014, 1, 129–143. [Google Scholar] [CrossRef]
- Shah, M.A.; Zhang, S.J.; Maple, C. Cognitive radio networks for Internet of Things: Applications, challenges and future. In Proceedings of the 19th International Conference on Automation and Computing, London, UK, 13–14 September 2013; pp. 1–6.
- Aijaz, A.; Aghvami, A.H. Cognitive Machine-to-Machine Communications for Internet-of-Things: A Protocol Stack Perspective. IEEE Internet Things J. 2015, 2, 103–112. [Google Scholar] [CrossRef]
- Zhang, B.; Chen, K. Selective spectrum leasing in Internet of Things via Nash Bargaining Solutions. In Proceedings of the IEEE 2nd International Conference on Cloud Computing and Intelligent Systems, Hangzhou, China, 30 October–1 November 2012; pp. 841–845.
- Zhang, N.; Lu, N.; Cheng, N.; Mark, J.W.; Shen, X.M. Cooperative networking towards secure communications for CRNs. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Shanghai, China, 7–10 April 2013; pp. 1691–1696.
- Kim, S. Cognitive Radio Anti-Jamming Scheme for Security Provisioning IoT Communications. KSII Trans. Internet Inf. Syst. 2015, 9, 4177–4190. [Google Scholar]
- Negi, R.; Goel, S. Secret communication using artificial noise. In Proceedings of the 2005 IEEE 62nd Vehicular Technology Conference, Dallas, TX, USA, 25–28 September 2005; pp. 1906–1910.
- Khisti, A.; Wornell, G.; Wiesel, A.; Eldar, Y. On the Gaussian MIMO Wiretap Channel. In Proceedings of the IEEE International Symposium on Information Theory, Nice, France, 24–29 June 2007; Volume 3, pp. 1906–1910.
- Swindlehurst, A.L. Fixed SINR solutions for the MIMO wiretap channel. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing, Taipei, Taiwan, 19–24 April 2009; pp. 2437–2440.
- Mukherjee, A.; Swindlehurst, A.L. Robust Beamforming for Security in MIMO Wiretap Channels with Imperfect CSI. IEEE Trans. Signal Process. 2011, 59, 1906–1910. [Google Scholar] [CrossRef]
- Tekin, E.; Yener, A. The general Gaussian multiple Access and two-way Wire-tap channels. IEEE Trans. Inf. Theory 2010, 56, 4762–4763. [Google Scholar] [CrossRef]
- Huang, J.; Swindlehurst, A.L. Cooperative Jamming for Secure Communications in MIMO Relay Networks. IEEE Trans. Signal Process 2011, 59, 4871–4884. [Google Scholar] [CrossRef]
- Araujo, A.; Blesa, J.; Romero, E.; Nieto-Taladriz, O. Co-operative jam technique to increase physical-layer security in CWSN. In Proceedings of the 2nd International Conference on Advances in Cognitive Radio COCORA 2012, Chamonix / Mont Blanc, France, 29 April–4 May 2012.
- Mukherjee, A. Physical-Layer Security in the Internet of Things: Sensing and Communication Confidentiality Under Resource Constraints. Proc. IEEE 2015, 103, 1747–1761. [Google Scholar] [CrossRef]
- Trappe, W. The challenges facing physical layer security. IEEE Commun. Mag. 2015, 53, 16–20. [Google Scholar] [CrossRef]
- Mukherjee, A.; Fakoorian, S.A.A.; Jing, H.; Swindlehurst, A.L. Principles of Physical Layer Security in Multiuser Wireless Networks: A Survey. IEEE Commun. Commun. Surv. Tutor. 2014, 16, 1550–1573. [Google Scholar] [CrossRef]
- Massey, J.L. An introduction to contemporary cryptology. Proc. IEEE 1988, 76, 533–549. [Google Scholar] [CrossRef]
- Cordeiro, C.; Challapali, K.; Birru, D.; Sai Shankar, N. IEEE 802.22: The first worldwide wireless standard based on cognitive radios. In Proceedings of the International Symposium on New Frontiers in Dynamic Spectrum Access Networks, Baltimore, MD, USA, 8–11 November 2005; pp. 328–337.
- Liu, L.; Zhang, R.; Chuan, K.C. Secrecy Wireless Information and Power Transfer With MISO Beamforming. IEEE Trans. Signal Process. 2014, 62, 1850–1863. [Google Scholar] [CrossRef]
- Pei, Y.Y.; Liang, Y.C.; Zhang, L.; Teh, K.C.; Li, K.H. Secure communication over MISO cognitive radio channels. IEEE Trans. Wirel. Commun. 2010, 9, 1494–1502. [Google Scholar] [CrossRef]
- Li, J.Y.; Petropulu, A.P.; Weber, S. On Cooperative Relaying Schemes for Wireless Physical Layer Security. IEEE Trans. Signal Process. 2011, 59, 4985–4997. [Google Scholar] [CrossRef]
- Hu, B.; Zhao, H.V.; Jiang, H. Wireless Multicast Using Relays: Incentive Mechanism and Analysis. IEEE Trans. Veh. Technol. 2013, 62, 2204–2219. [Google Scholar] [CrossRef]
- Huang, J.; Swindlehurst, A.L. Robust Secure Transmission in MISO Channels Based on Worst-Case Optimization. IEEE Trans. Signal Process. 2012, 60, 1696–1707. [Google Scholar] [CrossRef]
- Pei, Y.Y.; Liang, Y.C.; Zhang, L.; Teh, K.C.; Li, K.H. Secure Communication in Multiantenna Cognitive Radio Networks With Imperfect Channel State Information. IEEE Trans. Signal Process. 2011, 59, 1683–1693. [Google Scholar] [CrossRef]
- Kaur, N.; Sood, S.K. An Energy-Efficient Architecture for the Internet of Things (IoT). IEEE Syst. J. 2015, PP, 1–10. [Google Scholar] [CrossRef]
- Zhang, N.; Lu, N.; Cheng, N.; Mark, J.W.; Shen, X.S. Cooperative Spectrum Access Towards Secure Information Transfer for CRNs. IEEE J. Sel. Areas Commun. 2013, 31, 2453–2464. [Google Scholar] [CrossRef]
- Kamalinejad, P.; Mahapatra, C.; Sheng, Z.G.; Mirabbasi, S.; Leung, V.C.M.; Guan, Y.L. Wireless energy harvesting for the Internet of Things. IEEE Commun. Mag. 2015, 53, 102–108. [Google Scholar] [CrossRef]
- Khandaker, M.R.A.; Wong, K.K. SWIPT in MISO Multicasting Systems. IEEE Wirel. Commun. Lett. 2014, 3, 277–280. [Google Scholar] [CrossRef]
- Martinez, G.; Li, S.F.; Zhou, C. Wastage-Aware Routing in Energy-Harvesting Wireless Sensor Networks. IEEE Sens. J. 2014, 14, 2967–2974. [Google Scholar] [CrossRef]
- Xing, H.; Chu, Z.; Ding, Z.G.; Nallanathan, A. Harvest-and-jam: Improving security for wireless energy harvesting cooperative networks. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Austin, TX, USA, 8–12 December 2014; pp. 3145–3150.
- Li, W.; Wang, S.L.; Cheng, X.Z. Truthful Multi-attribute Auction with Discriminatory Pricing in Cognitive Radio Networks. In Proceedings of the 1st ACM Workshop on Cognitive Radio Architectures for Broadband, Miami, FL, USA, 30 September–4 October 2013; pp. 21–30.
- Zou, J.N.; Xu, H.W. Auction-Based Power Allocation for Multiuser Two-Way Relaying Networks. IEEE Trans. Wirel. Commun. 2013, 12, 31–39. [Google Scholar] [CrossRef]
- Wang, K.; Li, L.; Hausheer, D.; Liu, Z.Y.; Li, W.; Shi, D.N.; He, G.L.; Stiller, B. A trust-incentive-based combinatorial double auction algorithm. In Proceedings of the 2010 IEEE Network Operations and Management Symposium (NOMS), Osaka, Japan, 19–23 April 2010; pp. 209–215.
- Tsiaras, C.; Stiller, B. Challenging the Monopoly of Mobile Termination Charges with an Auction-Based Charging and User-Centric System (AbaCUS). In Proceedings of the 2013 Conference on Networked Systems (NetSys), Stuttgart, Germany, 11–15 March 2013; pp. 110–117.
- Wang, X.; Ji, Y.; Zhou, H.; Li, J. A Non-monetary QoS-aware Auction Framework towards Secure Communications for Cognitive Radio Networks. IEEE Trans. Veh. Technol. 2015, PP. [Google Scholar] [CrossRef]
- Ly, H.D.; Liu, T.; Liang, Y.B. Multiple-Input Multiple-Output Gaussian Broadcast Channels With Common and Confidential Messages. IEEE Trans. Inf. Theory 2010, 56, 5477–5487. [Google Scholar] [CrossRef]
- Li, Q.; Yang, Y.; Ma, W.K.; Lin, M.L.; Ge, J.H.; Lin, J.R. Robust Cooperative Beamforming and Artificial Noise Design for Physical-Layer Secrecy in AF Multi-Antenna Multi-Relay Networks. IEEE Trans. Signal Process. 2015, 63, 206–220. [Google Scholar] [CrossRef]
- Yang, Y.; Li, Q.; Ma, W.K.; Ge, J.H.; Ching, P.C. Cooperative Secure Beamforming for AF Relay Networks With Multiple Eavesdroppers. IEEE Signal Process. Lett. 2013, 20, 35–38. [Google Scholar] [CrossRef]
- Li, Z.; Jing, T.; Cheng, X.Z.; Huo, Y.; Zhou, W.; Chen, D.C. Cooperative jamming for secure communications in MIMO Cooperative Cognitive Radio Networks. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 7609–7614.
- Chui, L.U.; Murch, R.D. A transmit preprocessing technique for multiuser MIMO systems using a decomposition approach. IEEE Trans. Wirel. Commun. 2004, 3, 20–24. [Google Scholar] [CrossRef]
- Boyd, S.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]
- Sturm, J.F. Using SeDuMi 1.02, a MATLAB toolbox for optimization over symmetric cones. Optim. Methods Softw. 1999, 11, 625–653. [Google Scholar] [CrossRef]
- Stanojev, I.; Simeone, O.; Spagnolini, U.; Bar-Ness, Y.; Pickholtz, R.L. Cooperative ARQ via auction-based spectrum leasing. IEEE Trans. Commun. 2010, 58, 1843–1856. [Google Scholar] [CrossRef]
- Krishna, V. Auction Theory; Academic Press: New York, NY, USA, 2002. [Google Scholar]
- Lu, X.; Wang, P.; Niyato, D.; Hossain, E. Dynamic spectrum access in cognitive radio networks with RF energy harvesting. IEEE Wirel. Commun. 2014, 21, 102–110. [Google Scholar] [CrossRef]
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, Z.; Jing, T.; Ma, L.; Huo, Y.; Qian, J. Worst-Case Cooperative Jamming for Secure Communications in CIoT Networks. Sensors 2016, 16, 339. https://doi.org/10.3390/s16030339
Li Z, Jing T, Ma L, Huo Y, Qian J. Worst-Case Cooperative Jamming for Secure Communications in CIoT Networks. Sensors. 2016; 16(3):339. https://doi.org/10.3390/s16030339
Chicago/Turabian StyleLi, Zhen, Tao Jing, Liran Ma, Yan Huo, and Jin Qian. 2016. "Worst-Case Cooperative Jamming for Secure Communications in CIoT Networks" Sensors 16, no. 3: 339. https://doi.org/10.3390/s16030339




