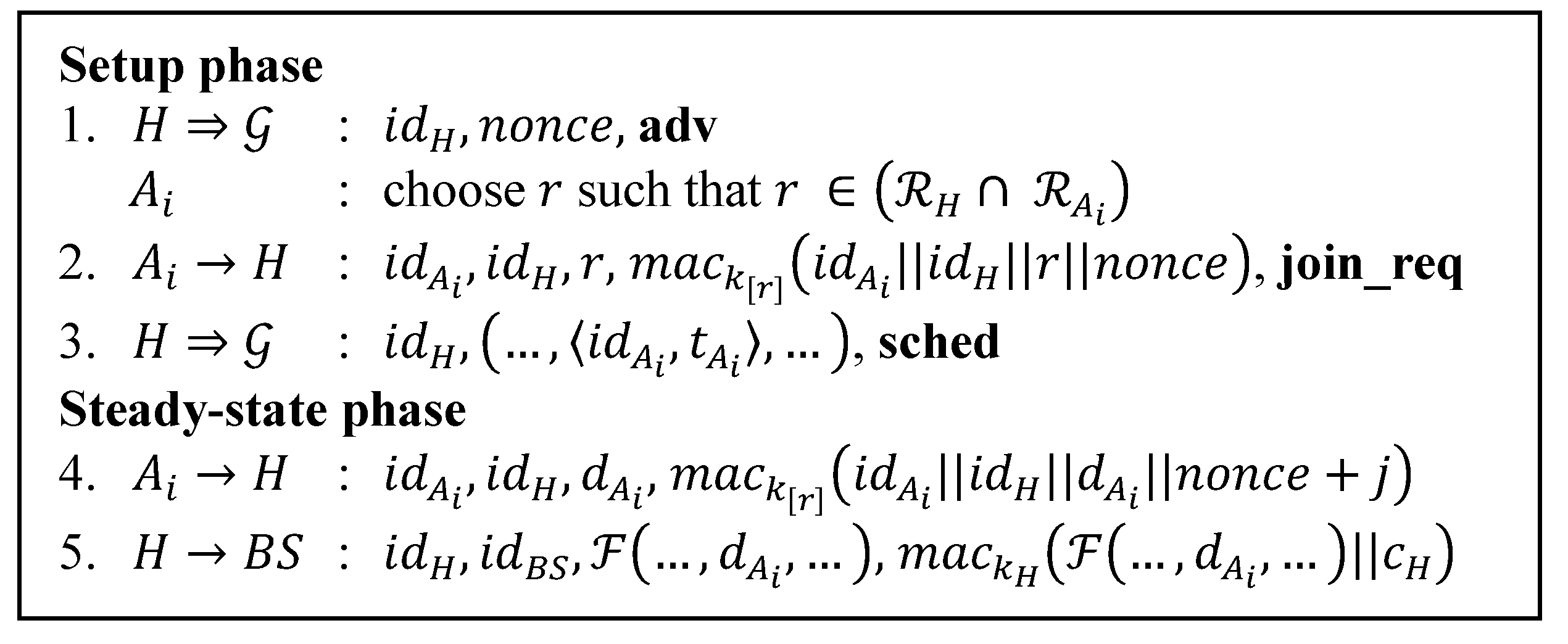In this section we evaluate the proposed protocol in detail. We compare it with its counterparts in the context of security, communication and computational complexity.
6.1. Security Evaluation
In this section the security comparison is done in the context of secure routing and then of secure data aggregation. We list all possible attacks for each context. We then identify each possible attack that applies in each context based on which security property (data integrity, source authentication, data confidentiality or data freshness, even availability) it attempts to compromise.
In evaluating the proposed protocol, we exclude the attacks launched by compromised nodes, or in other words internal attacks are excluded since by design the proposed protocol adopts LEACH-based secure routing and ESPDA that are not equipped to detect compromised nodes or even to punish them. Up until this stage, the proposed protocol does not employ any algorithm (such as witness-based detection to monitor a certain node’s behavior, etc) to punish compromised nodes. Therefore we do not consider internal attacks launched by compromised nodes.
First we evaluate the proposed protocol from the perspective of secure routing, comparing it to its counterparts (SLEACH, SecLEACH and MS-LEACH). In [
4], Karlof and Wagner study the attacks and countermeasures for secure routing protocols in WSN. These attacks are:
- ▪
spoofed, altered, or replayed routing information;
- ▪
selective forwarding;
- ▪
sinkhole attacks;
- ▪
Sybil attacks;
- ▪
Wormholes;
- ▪
HELLO flood attacks;
- ▪
acknowledgment spoofing.
The study also presents attacks specific to LEACH-family protocols. These are selective forwarding and HELLO floods attacks. The listed attacks and their descriptions provided in [
25] help our evaluation. We filter which attacks are applicable in our context. Those attacks are HELLO floods, selective forwarding, sinkhole attacks, and spoofed/altered/replaying routing information.
As we know, a successful launch of a certain attack can lead to the mounting of other attacks. For example, the HELLO floods attack launched by a malicious node may lure many other nodes to join that malicious node’s cluster, which later on results in selective forwarding or sinkhole attacks. So we can consider only the HELLO flood attack to simplify our evaluation.
Since in LEACH-based secure routing protocols, every node can take a role of either a CH or ordinary node, we consider a node impersonation attack which can be launched to target a CH or ordinary node. If we relate this attack to the previous explained HELLO flood attack, actually the HELLO flood attack is a type of CH impersonation attack since the target here is the CHs. Adversaries may impersonate any legal CH and advertise themselves to the network tricking many other ordinary nodes to join their cluster. This is similar to the HELLO floods attack. Therefore, we use the term CHs impersonation attack to represent HELLO flood attacks in our evaluation.
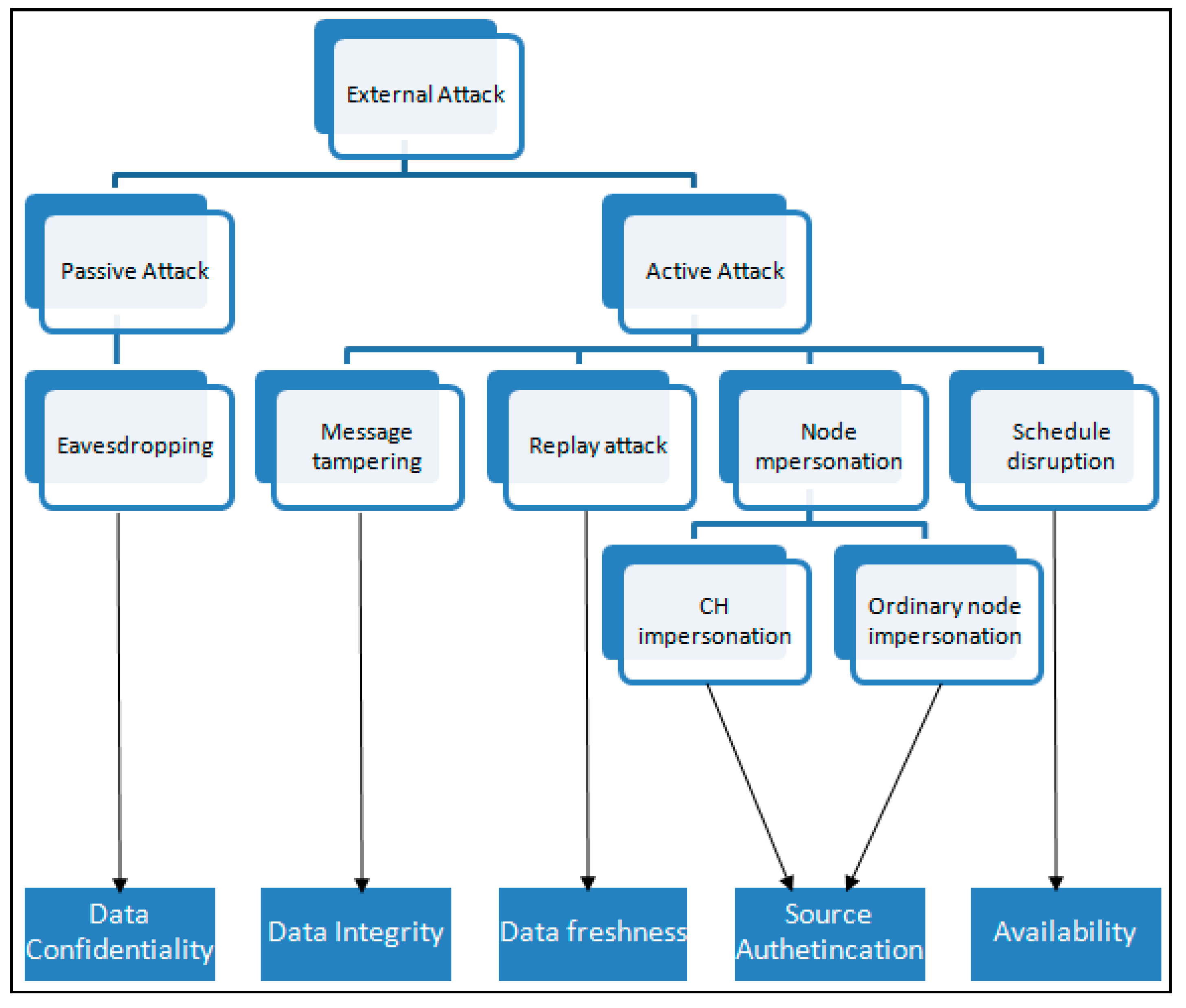
If the node impersonation attack’s target is ordinary nodes, then the goal of this attack is to insert false sensor readings. The significant contribution of false sensor readings can obscure the view of the actual network condition. We then add eavesdropping and an attack specific to the LEACH protocol, schedule disruption. This attack is identified when we analyze the vulnerabilities of the LEACH-based secure routing protocols in shown in
Section 4.
Figure 8.
Relating each possible attack with the corresponding attacked security property.
Figure 8.
Relating each possible attack with the corresponding attacked security property.
Furthermore, we check each attack against the security objectives it attempts to compromise. In
Section 3, the explained security properties are data confidentiality, data integrity, data freshness, source authentication and availability property.
Figure 8 is the diagram that summarizes our approach in the evaluation. We relate each attack with the targeted security property. By identifying each attack based on the security property it attempts to compromise, we can simply recognize how each protocol addresses the listed possible attacks. Readers may refer to
Table 2 that presents the summary of countermeasures we use for our protocol to fulfill the security requirements.
Table 3 summarizes our evaluation on the list of possible attacks against SLEACH, SecLEACH, MS-LEACH and the proposed protocol from secure routing point of view. Reader may refer to the
Section 3.3 for the explanation.
Table 3.
Possible attacks addressed, in comparison with other secure routing protocols.
Table 3.
Possible attacks addressed, in comparison with other secure routing protocols.
| Possible Attacks Observed | SLEACH | SecLEACH | MS-LEACH | Proposed Protocol |
|---|
| Eavesdropping | No | No | Yes | Yes |
| Message tampering | No | No | Yes | Yes |
| Replay | Yes | Yes | Yes | Yes |
| Ordinary nodes impersonation | No | Yes | No | Yes |
| CHs impersonation | Yes | No | Yes | Yes |
| Schedule disruption | No | No | Yes | Yes |
The first attack under observation is the passive attack, eavesdropping. In this attack, an adversary with a strong receiver can eavesdrop and intercept the transmitted packets. SLEACH does not prevent this attack since it does not provide confidentiality services, especially for the sensor readings and the aggregated result. SecLEACH also poses the same problem. In the other hand, MS-LEACH uses encryption to protect those data, and even the schedule messages are encrypted as well. The proposed protocol provides encrypted transmission for the sensitive data. Hence eavesdropping can be tackled.
The second attack is the message tampering. It attacks the data integrity properties. SLEACH suffers from this attack. This attack can target the join request message, the schedule message or the sensor reading transmissions of SLEACH. This is because its join request and schedule message transmission do not employ data integrity protection algorithms. In the case of its sensor reading transmissions, the transmissions are guarded by the keyed MAC using the key shared between the cluster member node and the BS, and furthermore, the sensor reading is not the input of the MAC computation. This allows adversaries to tamper with the message within cluster transmission, especially the sensor reading part, without being detected by the CH. If we observe the performance of SecLEACH against this attack, then SecLEACH also allows message tampering to take place on advertisement messages and schedule messages. MS-LEACH and the proposed protocol prevent this attack from happening. MS-LEACH uses MAC in every transmission to guarantee data integrity. The proposed protocol uses digital signatures or MAC to guarantee the data integrity of each message. Readers may refer to
Table 2.
The third is the replay attack. In facing replay attacks, all these protocols are equipped with countermeasures. Though the approaches are different, all can prevent replay attacks.
As for the next two attacks, they are both node impersonation attacks but with different targeted nodes. The ordinary nodes impersonation means the adversary impersonates ordinary nodes using any valid identity while the CHs impersonation means the targeted nodes are the CHs.
In the case of ordinary nodes impersonation, since SLEACH does not authenticate any node that joins the network, adversaries can insert intruder nodes to the network by taking any valid node ids (a problem caused by unauthenticated join request messages). These intruder nodes are able to insert false readings into the aggregated data that later on will be detected by the BS. The BS drops any aggregated data which contains data from unauthenticated nodes. Even though MS-LEACH also suffers from this attack, the best thing those intruder nodes can do is just to crowd the time slots since MS-LEACH has a pairwise key mechanism, while the pair-wise key mechanism in SecLEACH prevents the insertion of these intruder nodes into the network. Using the non-interactive identity-based key agreement we provide the pair-wise key mechanism to the proposed protocol.
However, the impact would be worse if this attack is launched to impersonate CHs. SecLEACH allows CHs impersonation to take place since the advertisement messages are not authenticated. In SLEACH and MS-LEACH, the BS verifies the authenticity of the claimed CHs on behalf of the network. The proposed protocol inserts a digital signature into the advertisement messages to provide source authentication. An adversary node with strong radio power transmission may lure a lot of nodes to join its cluster. This attack can lead to many other types of attacks such as selective forwarding and sinkhole attacks.
For LEACH-based protocols, the security aspect of the schedule message should be considered. The schedule message contains the TDMA schedule for nodes within a certain cluster to take turns in reporting their sensor readings. SLEACH and SecLEACH do not facilitate source authentication services to this message distribution. They allow any intruder to disrupt the transmission schedule in any cluster. The security analysis of
Section 3.3.1 and
Section 3.3.2 describes how it happens. MS-LEACH and the proposed protocol provide source authentication service for this message distribution via keyed MAC. To generate MAC MS-LEACH uses a pair-wise key while ours uses a cluster key.
Therefore, in comparison with the other LEACH-based secure routing protocols, the proposed protocol can address all possible attacks under observation. The proposed protocol is really in tight competition with MS-LEACH. MS-LEACH fails to provide authenticated join request messages though it has a pairwise key mechanism that can help to achieve this, while the proposed protocol provides authenticated join request messages that block illegitimate nodes from joining the network. Therefore justifying carefully the security requirements for every involved message in the protocol is important.
The next evaluation is done on any possible attacks that attempt to hinder the proper data aggregation process. Here we compare the proposed protocol and its counterpart, ESPDA. The summary is presented in
Table 4. Here we consider four attacks: eavesdropping, replay attack, node impersonation for specific CHs impersonation and message tampering.
Both protocols provide message confidentiality service for the actual data and aggregated data transmission. Therefore they address eavesdropping attacks.
Table 4.
Possible attacks addressed, in comparison with other secure data aggregation protocols.
Table 4.
Possible attacks addressed, in comparison with other secure data aggregation protocols.
| Possible Attacks Observed | ESPDA | Proposed Protocol |
|---|
| Eavesdropping | Yes | Yes |
| Replay | No | Yes |
| CHs impersonation | No | Yes |
| Message tampering | No | Yes |
The data aggregation process can be disrupted via replay attacks. In ESPDA, the distribution of , pattern seed and permutation seed are encrypted using a static network-wide key. Therefore ESPDA allows replay attacks to take place. The proposed protocol prevents this attack using a counter mechanism. We include a cluster counters into the MAC computation of those data distributions.
In ESPDA, a cluster member does not authenticate its CH (ESPDA does not provide a cluster formation description) since every node only shares a pairwise key with the BS. Any adversary can impersonate CHs and then launch other types of attack such as selective forwarding or sinkhole attacks. But one type of attack which is of concern in many secure data aggregation protocols is the stealth attack. In this attack the malicious nodes, especially the CHs, insert false sensor readings tricking the BS into accepting aggregated results which are significantly different from the actual data. As mentioned earlier our evaluation does not include attacks launched by compromised nodes, so here we consider only stealth attacks launched by inserted intruder nodes. Since the proposed protocol provides authenticated advertisement messages using digital signatures, we guarantee that the CHs are legitimate nodes and therefore the proposed protocol can address these attacks.
Another attack we observed is message tampering attacks. This attack can disrupt data aggregation in ESPDA, particularly when its target is the pattern code messages. ESPDA does not provide any data integrity service for this message, while the proposed protocol provides it by using keyed MAC.
Therefore, from
Table 4 we can see that ESPDA fails to provide protection against all possible attacks observed but eavesdropping. ESPDA does not employ any countermeasure that can provide data freshness service. Its lack of pairwise key providence among sensor nodes invites CH impersonation attacks and message tampering to take place. These attacks can affect the data aggregation process outcome in very bad way since the BS may receive false reports of the network, while in the proposed protocol, the role of the pair-wise key that is affordable using identity-based key agreement and the counter mechanism gives great contribution in dealing with those attacks.
6.2. Communication and Computational Complexity Evaluation
This section presents an evaluation on the communication and computational cost of the proposed protocol. In order to compare our protocol with others, we make some assumptions for message sizes and computational cost.
First we provide our assumption for the length of message component.
Table 5 gives the length assumption in bits for every message component. We also assume the length of the cluster key, sensor reading, pattern seed and mapping permutation to be 64 bits. That is for an approximate calculation of the encrypted data size, which is equal to the input data. The size can be varied depending on the WSN application.
Table 5.
Assumption for the length of message components.
Table 5.
Assumption for the length of message components.
| Message Component | Length (in bits) | Description |
|---|
| 16 | Identity of node |
| 64 | Random number |
| 480 | Digital signature |
| 160 | MAC |
| 64 | Key identifier/index |
| 64 | TDMA message size |
| 16 | Pattern code |
| 32 | Timestamp |
Table 6 and
Table 7 detail the approximate size of various message types involved in the setup phase and data aggregation phase for the protocols under study. Some messages are variable-sized, some are fixed. The variable
and
represent the number of cluster member and selected members whose pattern codes get selected, respectively.
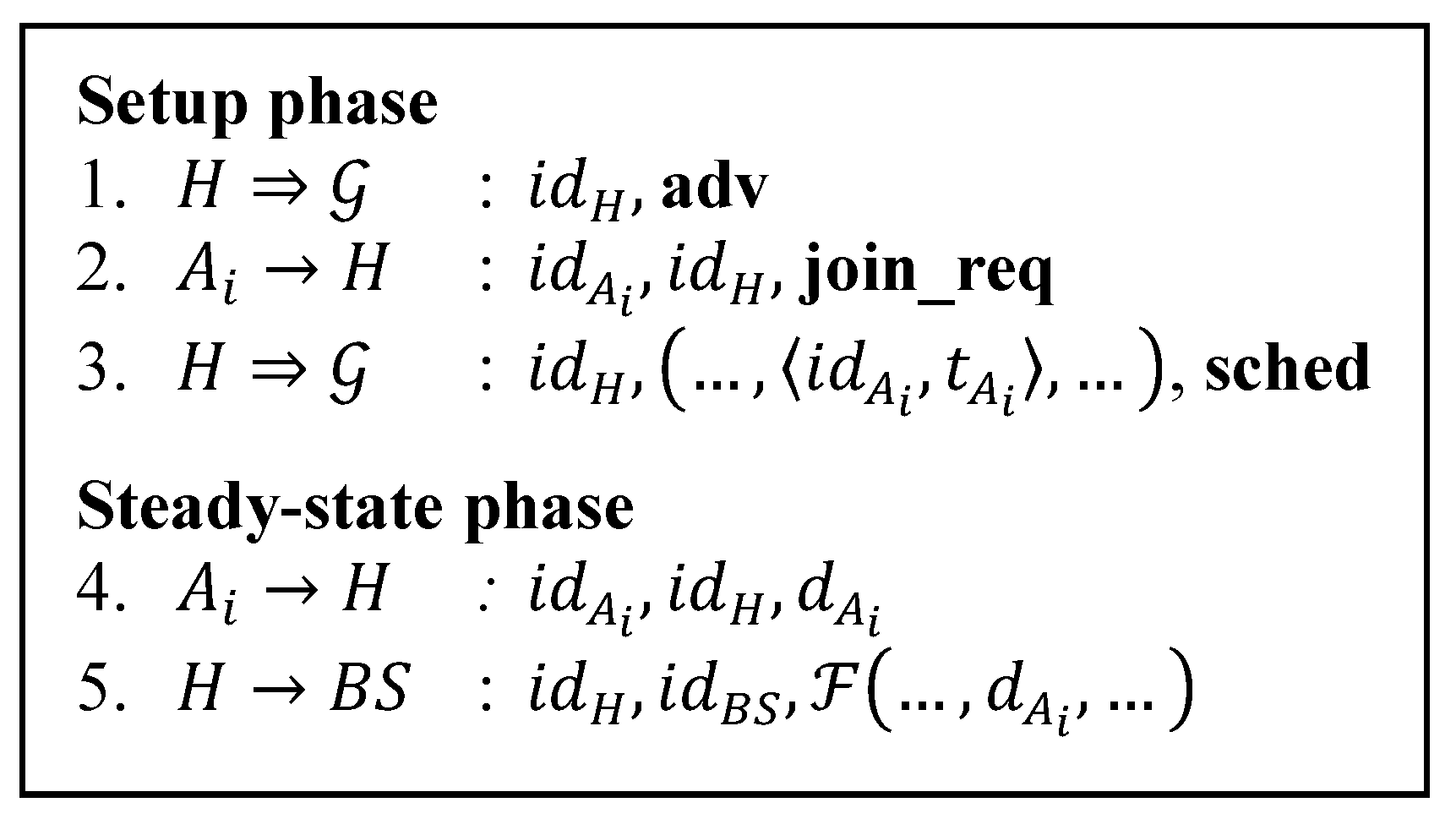
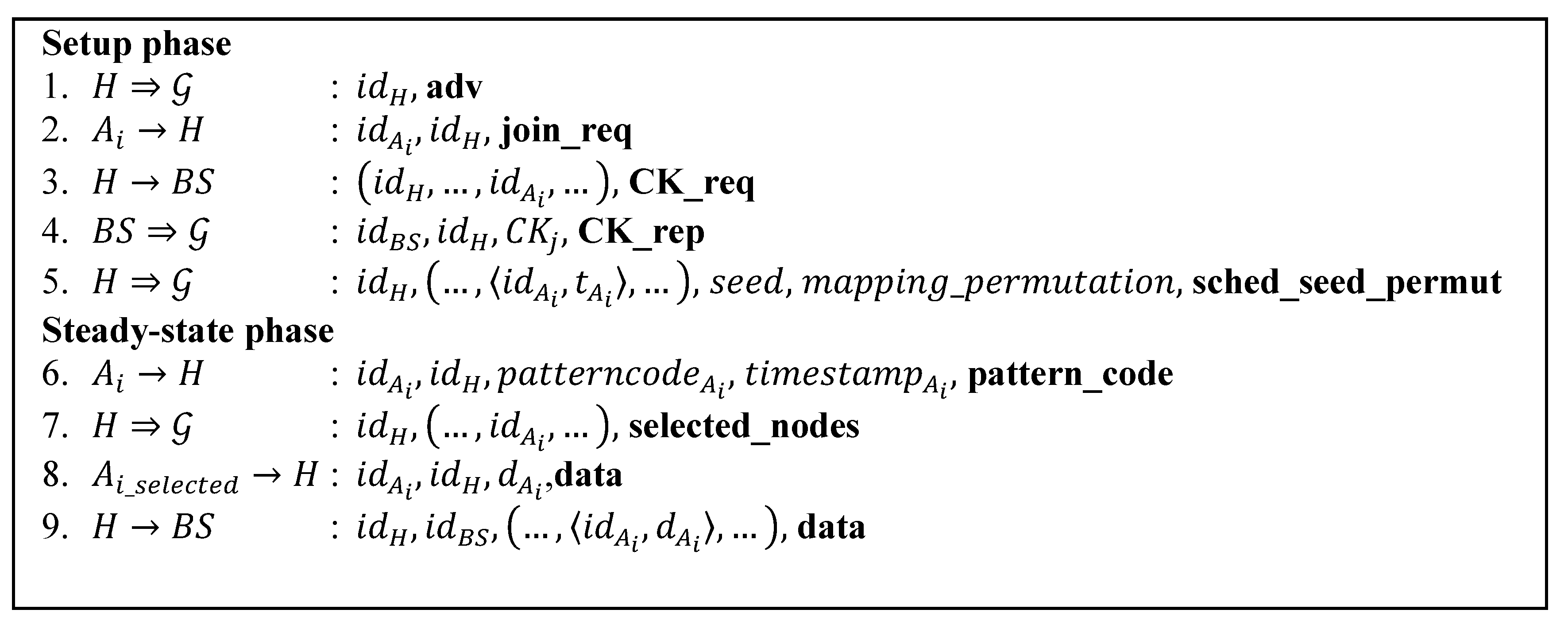
Table 6 details the message size comparison for our protocol and other secure routing protocol. We also include LEACH protocol here since all other protocols have their roots in LEACH. We only consider the cluster formation phase in which the routing paths get established. Since SLEACH and MS-LEACH have extra transmissions for the legitimate CHs list and group key (steps 1.2 and 1.3 of
Figure 2 and
Figure 4), we add the message size for them. We assume the number of legitimate CHs for every round to be 10 CHs. The size of the message that contains the information of this list then can be calculated as 10 times the size of the id plus the MAC size, 320 bit, while the size of the message that contains group key information is 64 bits.
Table 6 provides clear calculations for other message types.
Table 6.
Message size comparison for setup phase.
Table 6.
Message size comparison for setup phase.
| Message Type | The Proposed Protocol (in bits) | SLEACH (in bits) | SecLEACH (in bits) | MS-LEACH (in bits) | LEACH (in bits) |
|---|
| adv a | | | | | |
| join_req | | | | | |
| sched b | | | | | |
| CK_req c | | NA | NA | NA | NA |
| CK_rep c | |
| Legitimate_List | NA | 320 | NA | 320 | NA |
| Group_key | NA | 64 | NA | 64 | NA |
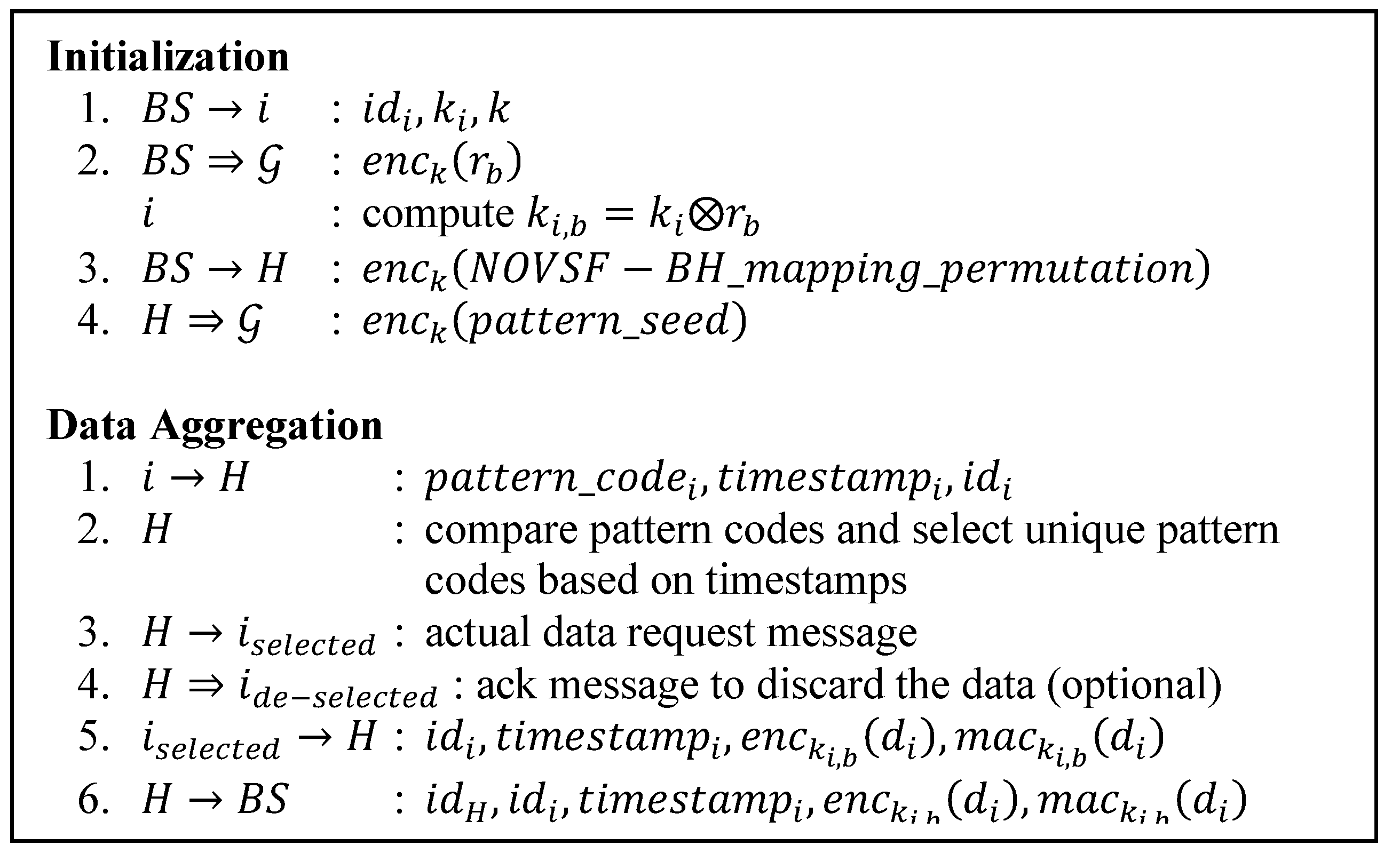
Table 7 details the message size comparison involved in data aggregation phase. Therefore only our protocol and ESPDA get compared in this study. Since the transmission uses wireless medium, the unicast transmission is actually a local broadcast transmission. Therefore we consider either unicast or broadcast as one unit transmission. We also consider the wake up state where nodes do not turn off their radios. This state takes place in the setup phase of the secure routing protocols and in the ESPDA protocol (no TDMA used). Therefore, if a node sends something via unicast or broadcast transmission, the other member nodes still receive the message even though further process may not take place. We count it as receiving cost.
Based on these assumptions, we calculate the communication cost for each protocol by calculating how many bits of message get processed in each transmission. Radio energy consumption is proportional to the number of conveyed bits.
Table 8,
Table 9,
Table 10,
Table 11,
Table 12 and
Table 13 provide details of the calculation for the communication costs in number of bits involved. They are calculated based on the number of transmission of each protocol shown in
Figure 1,
Figure 2,
Figure 3,
Figure 4,
Figure 5 and
Figure 7. Each step number in the tables corresponds to each protocol step number of the Figures. We differentiate the communication cost of CHs and ordinary nodes into transmitting and receiving cost (Tx and Rx).
Table 7.
Message size comparison for data aggregation phase.
Table 7.
Message size comparison for data aggregation phase.
| Message Type | The Proposed Protocol (in bits) | ESPDA (in bits) |
|---|
| pattern_code | | |
| selected_nodes | | |
| data(within cluster) | 2|id| + |enc| + |MAC| = 192 + |enc| ≅ 256 | |id| + |T| + |enc| + |MAC| = 208 + |enc| ≅ 272 |
| data(from CH to BS) | (2 +ns)|id| + ns|enc| + |MAC| = 16ns + 192 + ns|enc| ≅ 80ns + 192 | 2|id| + |T| + |enc| + |MAC| = 224 + |enc| ≅ 288 |
Table 8.
Communication cost of LEACH in setup phase.
Table 8.
Communication cost of LEACH in setup phase.
| Step | CH | Ordinary Node |
|---|
| Tx Cost (in bits) | Rx Cost (in bits) | Tx Cost (in bits) | Rx Cost (in bits) |
|---|
| 1 | 1 × adv = 16 | — | — | 1 × adv = 16 |
| 2 | - | n × join_req = 32 | 1 × join_req = 32 | (n − 1) × join_req = 32n − 32 |
| 3 | 1 × sched = 80 | — | — | 1 × sched = 80 |
| Total | 96 | 32n | 32 | 32n + 64 |
Table 9.
Communication cost of SLEACH in setup phase.
Table 9.
Communication cost of SLEACH in setup phase.
| Step | CH | Ordinary Node |
|---|
| Tx Cost (in bits) | Rx Cost (in bits) | Tx Cost (in bits) | Rx Cost (in bits) |
|---|
| 1.1 | 1 × sec_adv = 176 | — | — | 1 × sec_adv = 176 |
| 1.2 | — | 1 × Legitimate_List = 320 | — | 1 × Legitimate_List = 320 |
| 1.3 | — | 1 × Group_Key = 64 | — | 1 × Group_Key = 64 |
| 2 | — | n × join_req = 32n | 1 × join_req = 32 | (n − 1) × join_req = 32n − 32 |
| 3 | 1 × sched = 80 | — | — | 1 × sched = 80 |
| Total | 256 | 32n+ 384 | 32 | 32n + 608 |
Table 10.
Communication cost of SecLEACH in setup phase.
Table 10.
Communication cost of SecLEACH in setup phase.
| Step | CH | Ordinary Node |
|---|
| Tx Cost (in bits) | Rx Cost (in bits) | Tx Cost (in bits) | Rx Cost (in bits) |
|---|
| 1 | 1 × adv = 80 | — | — | 1 × adv = 80 |
| 2 | — | n × join_reg = 256n | 1 × join_reg = 256 | (n − 1) × join_reg = 256n − 256 |
| 3 | 1 × sched = 80 | — | — | 1 × sched = 80 |
| Total | 160 | 256n | 256 | 256n − 96 |
Table 11.
Communication cost of MS-LEACH in setup phase.
Table 11.
Communication cost of MS-LEACH in setup phase.
| Step | CH | Ordinary Node |
|---|
| Tx Cost (in bits) | Rx Cost (in bits) | Tx Cost (in bits) | Rx Cost (in bits) |
|---|
| 1 | 1 × sec_adv = 176 | — | — | 1 × sec_adv = 176 |
| 1.2 | — | 1 × Legitimate_List = 320 | — | 1 × Legitimate_List = 320 |
| 1.3 | — | 1 × Group_Key = 64 | — | 1 × Group_Key = 64 |
| 2 | — | n × join_req = 32n | 1 × join_req = 32 | (n − 1) × join_req = 32n − 32 |
| 4 | n × sched = 224n | — | — | n × sched = 224n |
| Total | 224n + 176 | 32n + 384 | 32 | 256n + 528 |
Table 12.
Communication cost of the proposed protocol in setup phase and steady state phase.
Table 12.
Communication cost of the proposed protocol in setup phase and steady state phase.
| Step | CH | Ordinary Node |
|---|
| Tx Cost (in bits) | Rx Cost (in bits) | Tx Cost (in bits) | Rx Cost (in bits) |
|---|
| 1 | 1 × adv = 560 | — | — | 1 × adv = 560 |
| 2 | — | n × join_req = 192n | 1 × join_req = 192 | (n − 1) × join_req = 192n − 192 |
| 3 | 1 × CK_req = 16n + 176 | — | — | 1 × CK_req= 16n + 176 |
| 4 | — | 1 × CK_rep = 80n + 608 | — | 1 CK_rep = 80n + 608 |
| 6 | 1 × sched_seed_permut = 368 | — | — | 1 × sched_seed_permut = 368 |
| Total (setup phase) | 16n + 1104 | 272n + 608 | 192 | 288n + 1520 |
| 7 | — | n × pattern_code = 240n | 1 × pattern_code = 240 | — |
| 8 | 1 × selected_nodes = 16ns + 176 | — | — | 1 × selected_nodes = 16ns + 176 |
| 9 (within cluster) | — | ns × data = 256ns | 1 × data = 256 if selected, otherwise 0 | — |
| 10 (from CH to BS) | 1 × data = 80ns + 192 | — | — | — |
| Total (steady state) | 96ns + 368 | 240n + 256ns | 496 if selected, otherwise 240 | 16ns + 176 |
In order to simplify our study on cluster expenditure for radio transmission in each protocol, we assume that both transmitting and receiving cost are equal. Note that their energy may differ significantly for different radio instruments. For comparison in the data aggregation phase, we assume a worst case where all cluster members get selected, so
. Since the transmission cost for ordinary node in
Table 8,
Table 9,
Table 10,
Table 11,
Table 12 and
Table 13 is for individual cluster members, it should be multiplied by
to capture the whole expenditure of cluster members. Therefore the cost of one cluster is cost of 1 CH plus its
member nodes.
Table 14 summarizes the comparison of the total expenditure for radio transmission within a cluster.
Table 13.
Communication cost of ESPDA in data aggregation phase.
Table 13.
Communication cost of ESPDA in data aggregation phase.
| Step | CH | Ordinary Node |
|---|
| Tx Cost (in bits) | Rx Cost (in bits) | Tx Cost (in bits) | Rx Cost (in bits) |
|---|
| 1 | — | n × pattern_code = 64n | 1 × pattern_code = 64 | (n − 1) × pattern_code = 64n − 64 |
| 3 | ns × selected_nodes = 32ns | — | — | ns × selected_nodes = 32ns |
| 5 (within cluster) | — | ns × data = 272ns | 1 × data = 272 if got selected, otherwise 0 | (ns − 1) × data = 272ns − 272 if selected, otherwise ns × data = 272ns |
| 6 (from CH to BS) | ns × data = 288ns | — | — | ns × data = 288ns |
| Total | 320ns | 64n + 272ns | 336 if selected, otherwise 64 | 64n + 592ns − 336 if selected, otherwise 64n + 592ns − 64 |
Table 14.
Comparison of intra-cluster radio transmission expenditure
Table 14.
Comparison of intra-cluster radio transmission expenditure
| Phase | Protocol | Total Expenditure (in bits) |
|---|
| Setupphase | LEACH | 32n2 + 128n + 96 |
| SLEACH | 32n2 + 672n + 640 |
| SecLEACH | 256n2 + 416n + 160 |
| MS-LEACH | 256n2 + 816n + 560 |
| Ours | 288n2 + 2000n + 1712 |
| Data aggregation phase | Ours | 16n2 + 1264n + 368 |
| ESPDA | 656n2 + 656n |
From
Table 14 we are able to see each protocols’ radio communication cost in polynomial form. For radio communication cost, with the increasing number of member nodes, we find the following:
SLEACH is the cheapest secure routing protocol for the setup phase. Its radio communication expenditure is not much different from LEACH’s. This is because its modified advertisement message adds a small number of bits to the transaction. Its transmission for the list of legitimate CH and group key (in step 1.2 and 1.3,
Figure 2) add some more bits. However it is still the cheapest among secure routing protocols under evaluation.
Our protocol is the most expensive for the setup phase category. The size of the join request message and cluster key reply message are the main contributors to this cost. We have designed our protocol to have multiple steady-state phases in order to mitigate this costly setup phase. However our protocol is robust against all six possible attacks as shown in
Table 3. We achieve these enhanced security features with some extra communication cost.
Though our protocol setup phase is the most expensive, its data aggregation cost is much cheaper than its baseline protocol, ESPDA. This is because we use TDMA scheduling in our protocol design. With about 40 times of
lesser transmissions than ESPDA, our scheme has three more enhanced security features than ESPDA as shown in
Table 4. As the number of member nodes increases, the gap between the two schemes will increase. Because the data aggregation phase is executed more often than the setup phase, our scheme has merits compared to ESPDA.
For the practical use of the LEACH-style routing schemes introduced in our paper, they need to add more steps in their data aggregation phase when they are combined with a specific data aggregation scheme such as ESPDA. This will introduce additional communication costs. By considering this fact, because the setup phase is relatively infrequent compared to the data aggregation phase, our protocol is comparable to the other LEACH-style routing schemes when they are combined with a specific data aggregation scheme.
Another evaluation is for the amount of computation of cryptographic algorithms that takes place. Those cryptographic algorithms include hash function, symmetric encryption/decryption, MAC computation, digital signature generation and verification. We denote by the computation cost of operation .
We consider hash operation cost and MAC computation equal since MAC computation employs a hash function, therefore we represent each of both as one unit of hash operation,
. Since it is symmetric encryption/decryption, we consider both costs of operation equal and represent each of them as one unit of encryption operation,
. An exception is digital signature generation and verification. Both of them do not have equal computational costs, therefore we represent the signing operation as
and its verification operation as
. As here we do not strict the proposed protocol to any specific digital signature algorithm, the computation cost can be expanded according to the chosen digital signature algorithm.
Table 15 presents the cryptographic computation cost.
Since we cannot tell exactly the execution time of each algorithm, we still can compare them by ordering them based on computation complexity. Let’s say is modular multiplication in , is exponentiation in (equivalent to scalar multiplication in ECC), is the multiplication in (equivalent to point addition in ECC) and, previously stated, is hash operation and is symmetric encryption/decryption. We can sort the computational complexity of the algorithms as follows: .
Table 15.
Computational cost comparison.
Table 15.
Computational cost comparison.
| Phase | Node’s Role | SLEACH | SecLEACH | MS-LEACH | ESPDA | The Proposed Protocol |
|---|
| Setup | CH | | | | NA | |
| Ord. Node | | | | |
| Data Aggregation | CH | NA | NA | NA | 0 | |
| Ord. Node | (*), Otherwise 0 | (*), otherwise |
In [
24], Liu
et al. measured that their digital signing operation equals
and the signature verification equals to
. We can tell that the verification is more costly than their signing operation. From the comparison of computational complexity shown in
Table 15, it is very obvious that the proposed protocol is the most expensive one in its classes, especially in setup phase. If we refer to the
Table 2 on how we fulfill the security requirements of the proposed protocol summarized in
Table 1, we can see that the proposed protocol uses cryptographic approaches to meet them. This cryptographic approach is a kind of trade-off between computation cost and security level since the proposed protocol can tackle all listed possible attacks at the sacrifice of computational burden (readers may refer to
Table 3 and
Table 4 in the security evaluation section).