1. Introduction
The monitoring and localization of objects have been an active research and development field in recent years. Existing techniques include Global Position System (GPS), infrared, Local Area Network (LAN) and ultrasound-based methods,
etc. [
1]. However, these technologies have some disadvantages. Thus, GPS technology is often used to locate outdoor objects, and is not suitable for indoor monitoring and localization due to its requirement of a direct line-of-sight communication to the satellites. Infrared methods also require a direct line-of-sight and involve a short-range signal transmission, and thus are not suitable for indoor monitoring and localization either. Wireless LAN technology is used to monitor and locate the objects by signal strength, and the target objects must be in the coverage area of wireless LAN, hence it might not be a good solution. Ultrasonic technology utilizes the Time of Flight (TOF) method to locate target objects. It usually requires either a transmitter or a receiver to accurately determine the location. Radio Frequency Identification (RFID) technology has become popular and been widely used in many fields due to its advantages [
2], such as contactless communications, high data rate and security, no need for line-of-sight readability and low cost. With these advantages, RFID is a good candidate for workpiece monitoring and localization in manufacturing workshops.
RFID technology uses radio frequency waves to transfer data between readers and tagged objects, and provides fast data collection with precise identification of objects with unique IDs without line-of-sight, so it can be used for identifying, locating, tracking and monitoring physical objects [
3]. With such significant technology advantages, RFID has been widely used for access control, objects tracking, smart box, highway tolls, logistics and supply chain, security and healthcare,
etc. [
4]. In particular, RFID has been adopted and deployed to collect various types of data in the manufacturing field [
5].
With the integration and development of information technology and manufacturing technology, a number of advanced manufacturing models [
6] have been proposed and applied, such as Lean Manufacturing (LM), Agile Manufacturing (AM), Virtual Manufacturing (VM), Virtual Enterprises (VE) and Intelligent Manufacturing (IM). Advanced manufacturing concerns not only manufacturing process, but also the full life cycle of market analysis, product design, manufacturing, assembly, sales, maintenance, services and recycle. Under the development and maturity of industrial wireless networks, Wireless Sensor Networks (WSN), RFID, Micro-Electrical Mechanical Systems (MEMS), Cyber-Physical Systems (CPS), and so on, the concept of Wisdom Manufacturing (WM) [
7] is emerging.
As a service-oriented and knowledge-based humans-computers-things collaborative manufacturing model [
8], WM puts emphasis on the fusion of the social, cyber and physical worlds, which form a Socio-Cyber-Physical System (SCPS). The main manufacturing resources consist of workers, machines, workpieces,
etc. Manufacturing processes are prone to unexpected disturbances or disruptions such as workpiece anomaly, machine breakdown, urgent job arrival, lead time modification or changes in order quantities on short notice, the production of incorrect job quantities, materials or supplies failing to arrive when expected, misplaced parts, and tool defects [
9]. Workpiece machining will be influenced by all these abnormal conditions in wisdom manufacturing workshops. Workers are obliged to respond to these disturbances in a timely manner, so as to reduce their impacts as much as possible. RFID technology has the potential to build an efficient real-time monitoring system.
Everything in the WM system can be aware of both itself and others to provide the right service for the right object at a right time and context [
10]. The SCPS is the fusion of social, cyber and physical worlds. A WM model based on SCPS is illustrated in
Figure 1 [
11].
Figure 1.
Wisdom manufacturing model based on SCPS [
11].
Figure 1.
Wisdom manufacturing model based on SCPS [
11].
There are workshops, machines, workers, raw materials, workpieces, products,
etc. in the physical world of wisdom manufacturing. These real physical things are called u-things if they are attached, embedded, or blended with computers, networks, and/or some other devices such as sensors, actuators, e-tags [
12]. Through SEA-nets such as sensors net, embedded devices net and actuators net, manufacturing data such as the workshop environment data, machines state data, inventory data of raw materials and production data are transmitted to the web.
In the cyber world, the data level is involved with various data management and preprocessing technologies, including data collection, cleaning, integration and storage, etc. for completing the “things-data” conversion; data is converted into information through some methods such as metadata construction, data mining, event driven actions and the study of human information processing, The information level is involved with information extraction, information storage and information organization, etc. for completing the “data-information” conversion; Information is converted into knowledge through some methods such as space/user/thing modeling, model integration, knowledge retrieval and study of human knowledge expression. The knowledge level is involved with knowledge extraction and knowledge expression, etc. for completing the “information-knowledge” conversion; Knowledge is converted into wisdom through some methods such as autonomy-oriented computing, granular computing, complex network and study of human intelligence. The wisdom level is involved with cyber individuals, wisdom web and smart u-things, etc. for completing the “knowledge-wisdom” conversion; Wisdom is applied in various fields to provide active, transparent, security and reliable services. The service level is involved with services construction, services publishing and services integration for completing the “services-human” conversion.
In the social world, clients, social groups and enterprises implement effectively the implicit knowledge conversion and the integration of humans with the aid of social software (such as Blog, Tag, (Social Network Site) SNS and Wiki.). They use and enjoy a variety of products and services through the transparent service middleware and service platform, at the same time, and propose more personalized requirements for different products and services. These personalized requirements are converted into the product parameters to update the product gradually. Therefore, based on SCPS, the wisdom manufacturing model is formed.
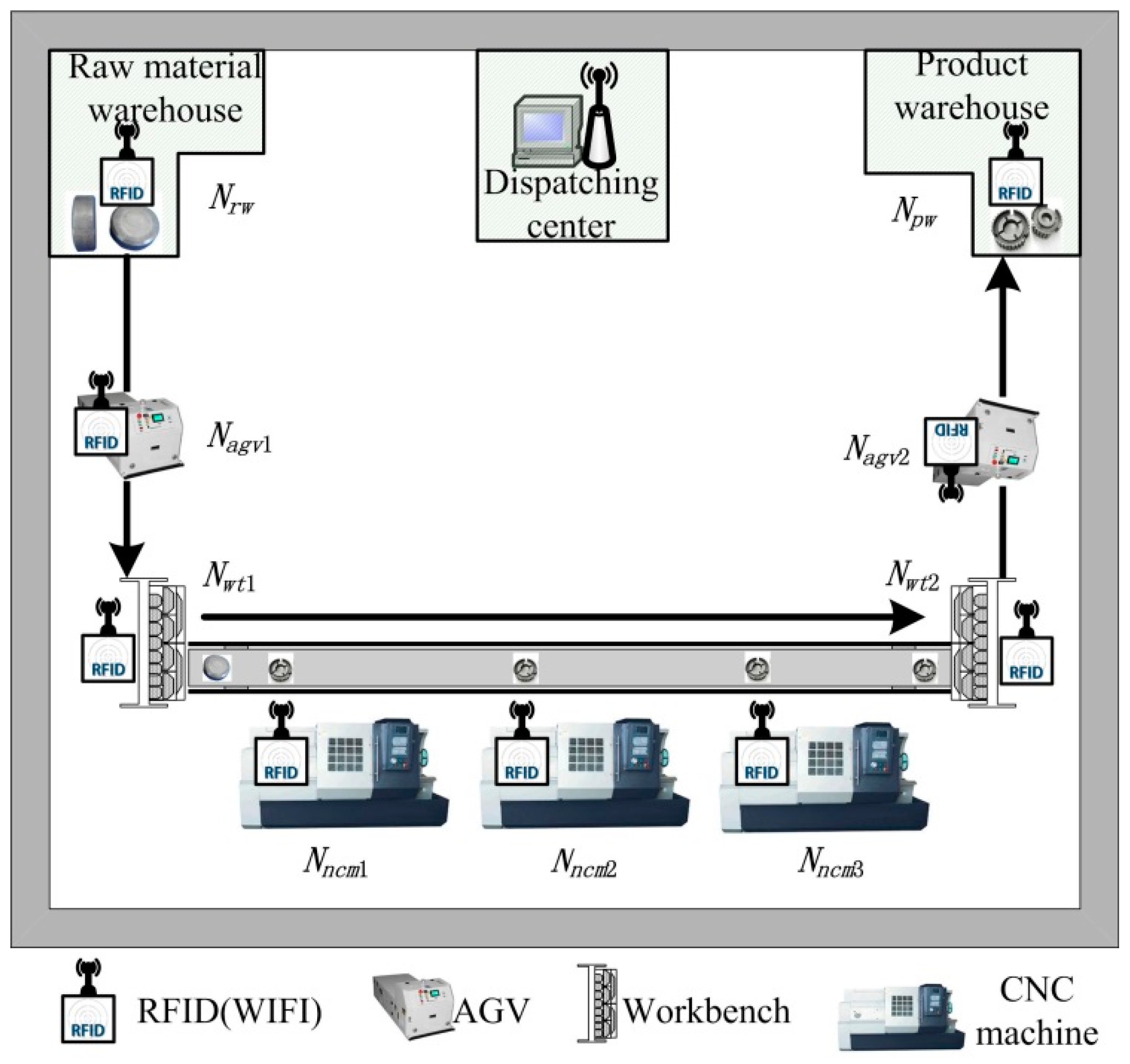
In a wisdom manufacturing environment, the entire manufacturing workshop is covered by internet (such as LAN and WIFI). The sensing-aware environment of a wisdom manufacturing workshop is constructed based on cyber-physical systems, as shown in
Figure 2. The manufacturing workshop contains dispatching center, raw material warehouse, (Automated Guided Vehicle) AGV, numerical control machines, workbenches, product warehouse, and so on. Directional (Ultra High Frequency) UHF RFID readers with LAN (WIFI) are installed on every workstation. Anti-metal ceramic RFID tags are pasted on every workpiece. The whole process from raw material to product is monitored. Each workstation is equipped with RFID sensing nodes, which sense ID numbers, time, location and other data of arrived workpieces in real time. Abnormal events can be monitored through data analysis in real time.
RFID applications in wisdom manufacturing are typically classified into two types [
3]: (1) real-time-oriented monitoring applications; (2) history-oriented tracking applications. The fundamental characteristics of RFID data are temporal, dynamic, implicit semantic, inaccurate, integrated, flowing and large volume. Raw data provides no explicit semantic meaning for applications or business logics. It has to be transformed into semantic data properly represented with its own data models before it can be integrated into applications. Thus, RFID data model translates the physical world into its corresponding virtual (cyber) world. In this paper, passive tags are adopted, and RFID event processing models based on data mining are proposed to realize the monitoring of workpieces in wisdom manufacturing workshops.
Figure 2.
Sensing-aware environment of a wisdom manufacturing workshop.
Figure 2.
Sensing-aware environment of a wisdom manufacturing workshop.
The remainder of this paper is organized as follows:
Section 2 reviews the literature of product monitoring, data cleaning and data mining based on RFID in manufacturing, and states the problems to be solved.
Section 3 gives RFID event models consisting of tag event, simple event, and complex event.
Section 4 proposes RFID data cleaning and data mining methods.
Section 5 shows simulation and physical experiments to test the system functions. Conclusions and suggestions for future work are given in
Section 6.