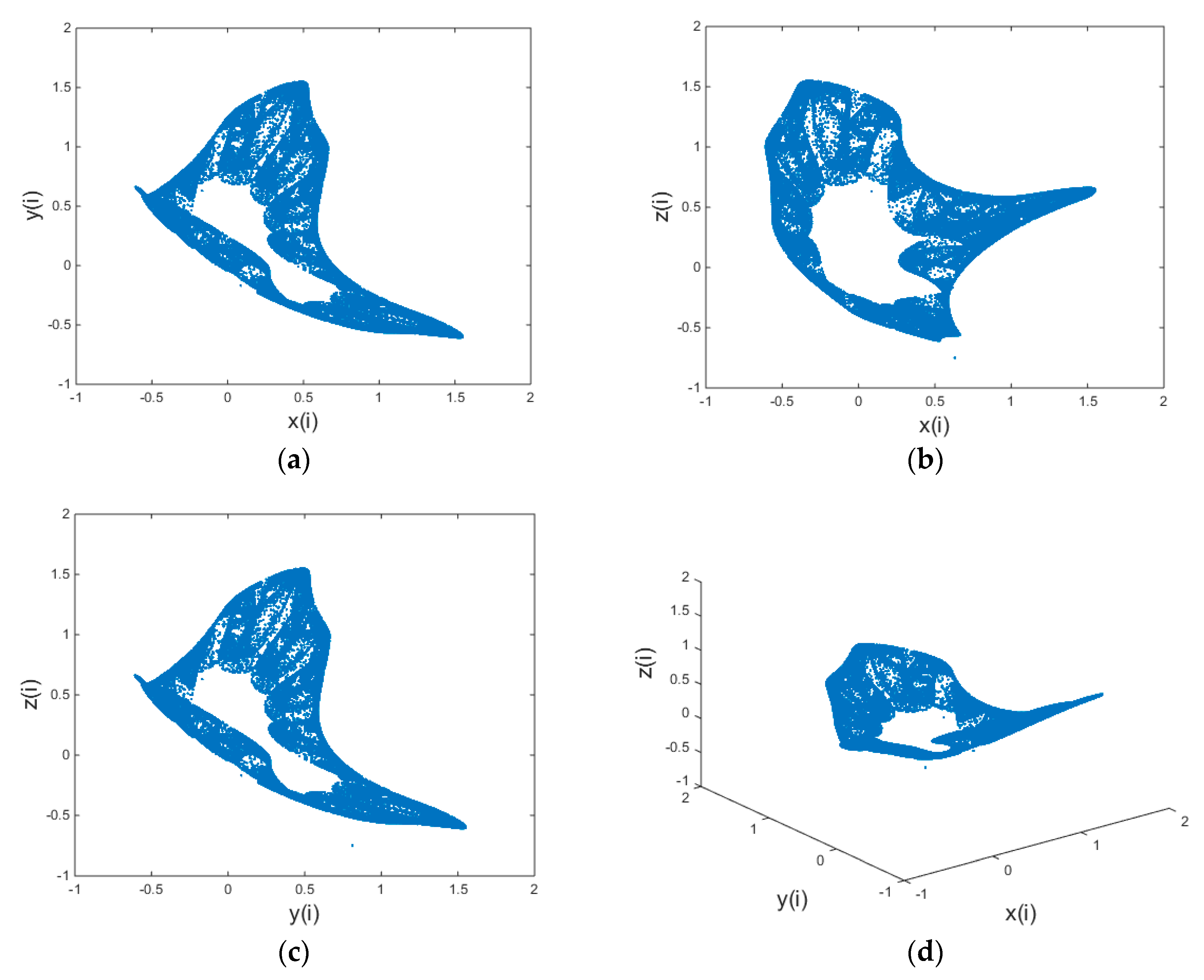
1. Introduction
With the rapid development of data network transmission technology, security issues regarding information transmission in communication systems have attracted wide attention from scholars who are devoted to solving them. Today’s society has also turned its focus in this direction. The awareness of cybersecurity protection in all areas of society has generally increased, and research on information security transmission mechanisms has become increasingly crucial [
1]. Today, with the continuous growth of transmission bandwidth and data rates, images have become the mainstream form of multimedia information transmission. This is reflected in the fields of remote sensing telemetry and digital watermarking [
2,
3]; an effective means of ensuring the secure transmission of digital images would be to design a secure and efficient encryption algorithm to encrypt plaintext images, and to ensure that the encryption algorithm is safe, robust, and resistant to attack.
The wide spectrum, noise-like and random characteristics of chaotic systems comprising chaotic-based digital image encryption methods have been widely concerned by many scholars [
4]. However, with the increasing demand for digital image transmission, how to reduce the data transmission amount and storage capacity under the premise of ensuring the security, robustness and anti-attack of the encryption method is the key problem in the practical application of the image encryption method. This is also the purpose of this article.
Related research on enhancing image encryption effects focuses on the following aspects: First, the complexity of the chaotic system can be increased through complex chaos or by using chaos with higher dimensions, thereby improving the image encryption effect. Zhou combined two types of one-dimensional chaos to generate a new one-dimensional chaos domain with larger chaotic range and more complex chaotic behavior, and improved the encryption effect of digital images [
5]. Chen extended Cat Chaos to 3D and designed a real-time secure symmetric encryption algorithm to solve the problem of fast and high-security image encryption [
6]. Mirzae used hyperchaos to design a parallel encryption scheme [
7], which improved local encryption robustness. Second, the combination of chaotic systems and other algorithms can increase the complexity of the algorithm and enhance the security of digital images. In this respect, by using chaotic and DNA sequences, Wen used DNA coding and spatiotemporal chaos for encryption [
8]. The core idea behind both scholars’ work was to diffuse spatial pixels using chaos. Furthermore, Ye [
9] proposed the use of chaotic maps and information entropy for image encryption, thereby avoiding the transformation of pixel positions before traditional diffusion encryption. Liu [
10] proposed an S-box non-destructive quantum image encryption scheme, combining linear transformations and nonlinear transformations to improve the complexity of the encryption scheme. Chai [
11] shuffled the pixels in digital images by assigning new random access locations to them, which enhanced the sensitivity of plaintext images. Third, minimizing finite precision improves the randomness of chaotic systems and enhances the encryption effect. Li [
12] found that some chaotic characteristics degenerate due to the limited precision used in computers. In [
13], the author considers finite precision and uses a binary method to deal with the short period of chaos to prevent chaotic degradation; Nardo uses limited precision error to encrypt the image [
14]. This method makes the chaotic system have sufficient randomness and improves the encryption effect of the chaotic system.
In recent years, compressed sensing has undergone extremely rapid development. In 2006, Candes [
15,
16] proposed the theory of compressed sensing. Compared with the Shannon sampling theorem, compressed sensing greatly reduces the sampling rate and computational complexity. As a non-linear technology, compressed sensing can be incorporated into an image encryption scheme, which minimizes the resource occupancy rate of image transmission. In addition, the chaotic system itself has features such as pseudo-randomness and sensitivity, and is often used in the image encryption process [
17,
18]. Therefore, the combination of compressed sensing and a chaotic system is expected to produce an excellent implementation of compressed image encryption.
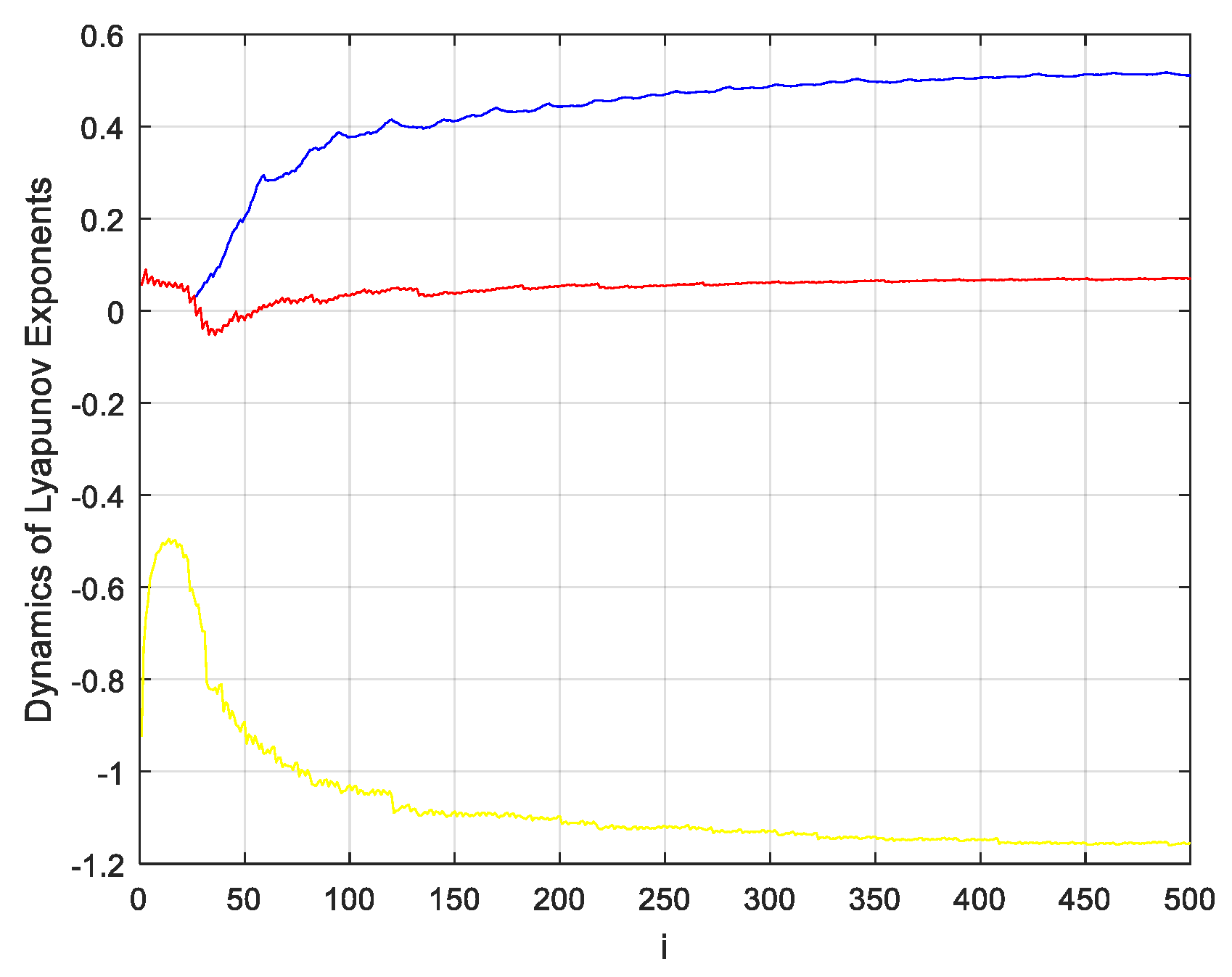
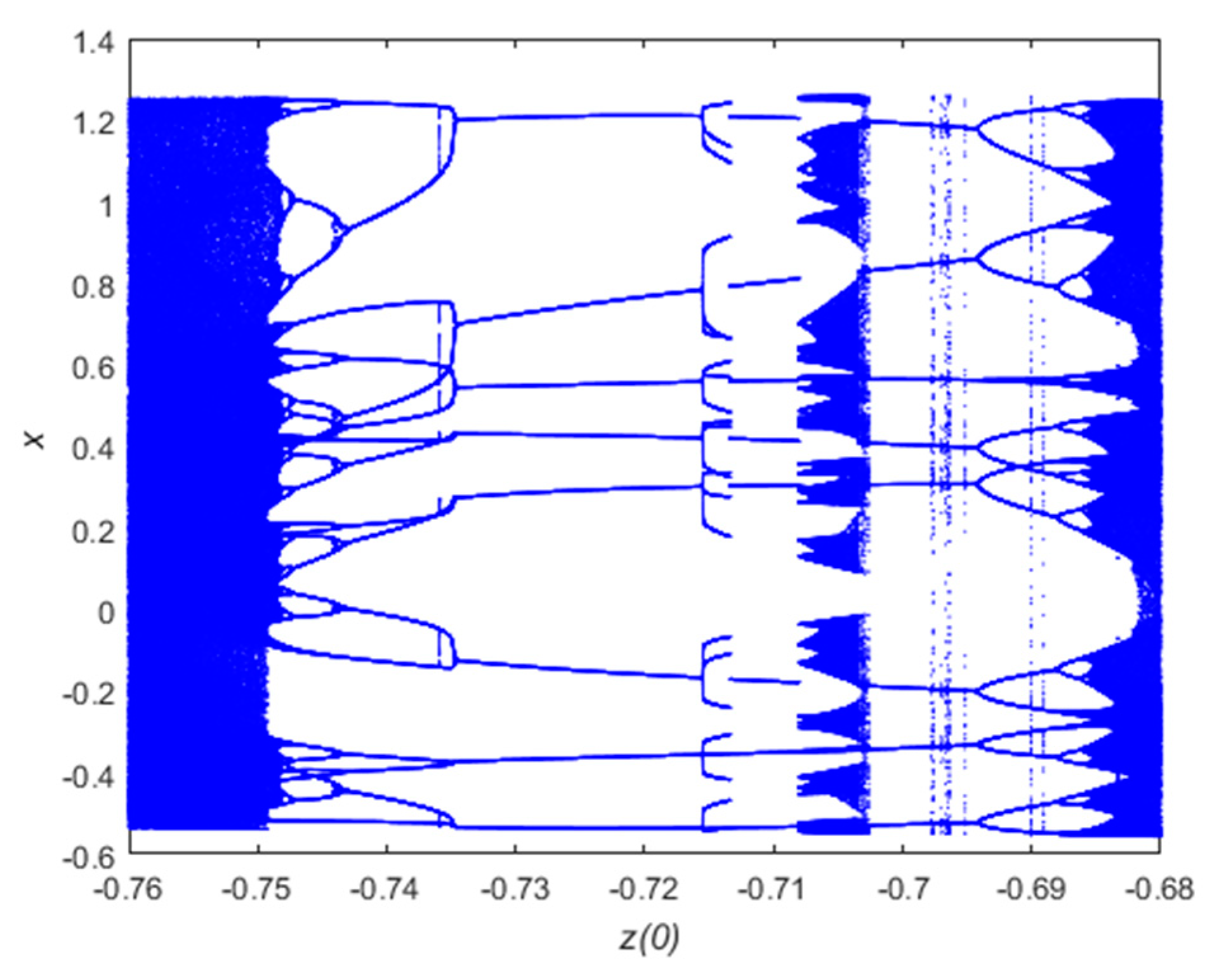
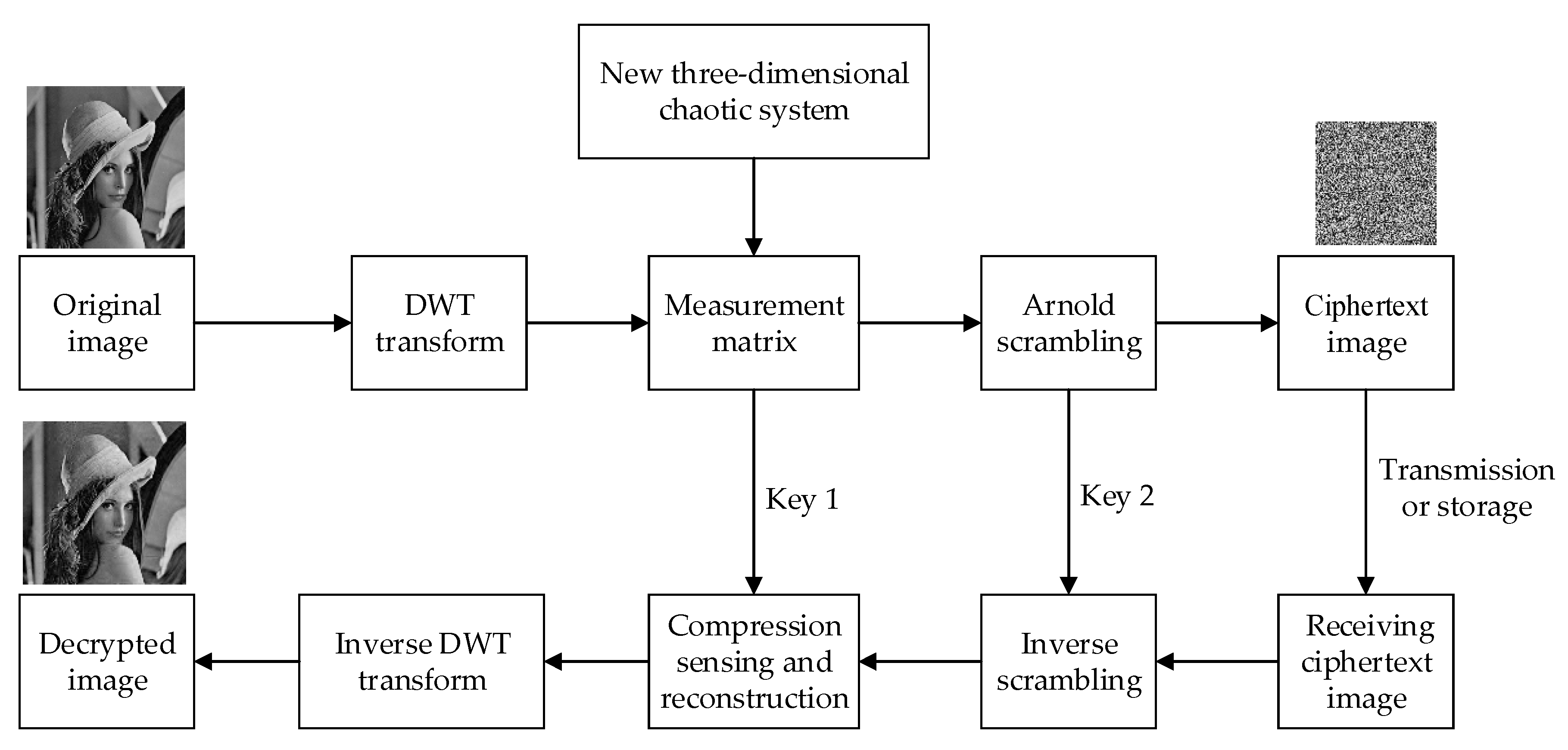
Therefore, in order to better enhance the reconstruction effect of compressed images and improve the security of encrypted images, this paper proposes a compressed sensing image encryption scheme based on new three-dimensional chaos. Firstly, the security of a new three-dimensional hyper-chaotic system enhancement algorithm is designed, and the chaotic Lyapunov exponent, bifurcation diagram and complexity are analyzed. Second, in the encryption scheme, a new chaotic system is used as the measurement matrix for compressed sensing, and Arnold is used to scramble the image further. Third, the image compression reconstruction method proposed in this paper is better than other methods. Finally, the security of the encryption algorithm is analyzed, and the proposed encryption algorithm is verified from the aspects of key space, statistical analysis, information entropy and differential analysis, which can resist various attacks.
5. Simulation Experiments and Performance Analysis
5.1. Simulation Conditions
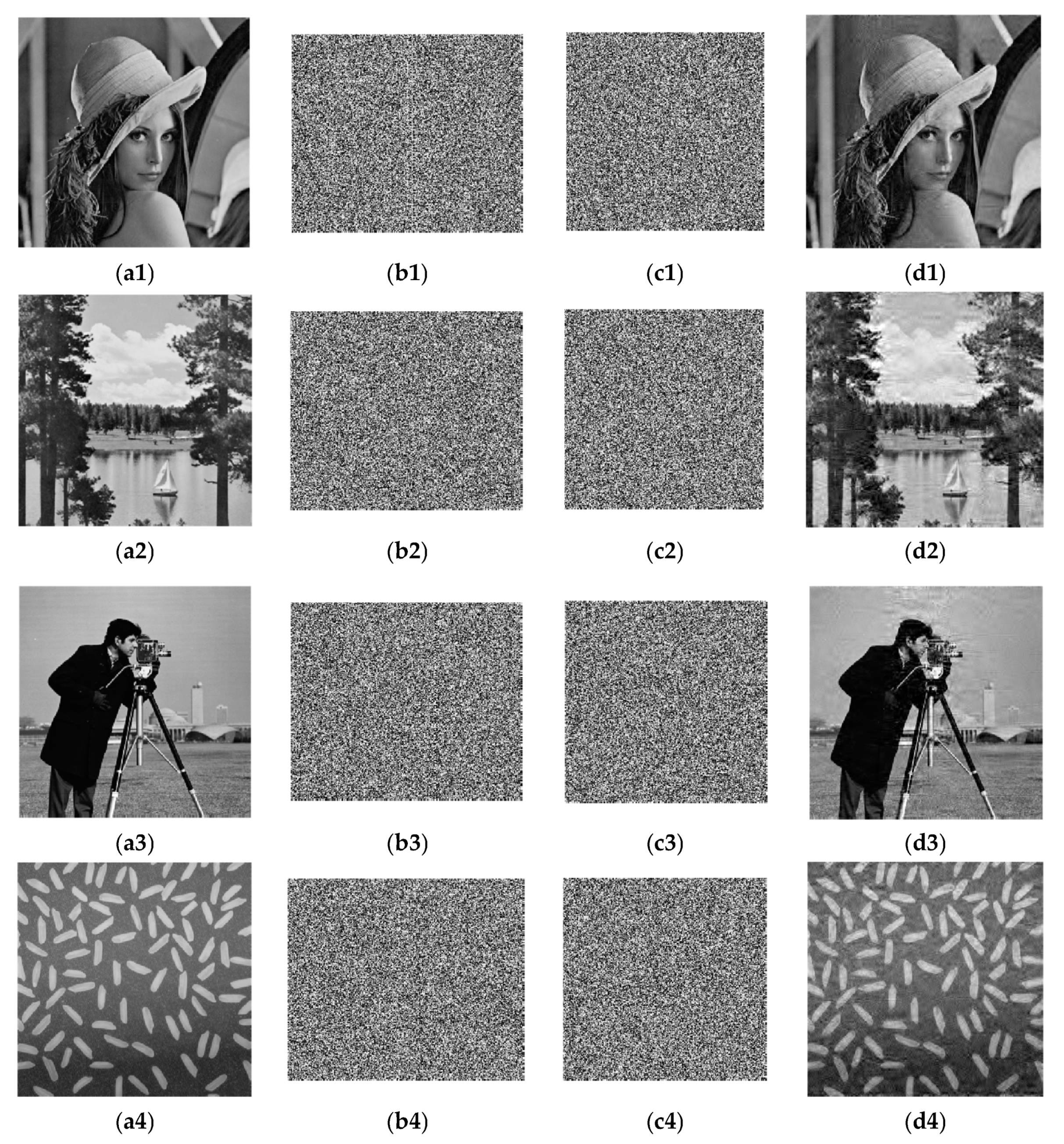
In this paper, 256 × 256 grayscale images of Lena, Lake, Cameraman, and Rice are used for testing purposes. Matlab R2010a is used to implement the encryption algorithm. First, the sparsity in the simulation is set as K = 50, and the compression ratio is 0.74, i.e., a 256 × 256 image would be compressed to a 220 × 256 image. After secondary sampling and Arnold scrambling, the ciphertext images are compressed to 220 × 220. The original images, images with chaotic encryption, images with scrambling encryption, and decrypted images are shown in
Figure 5.
It can be seen from the simulation results that after a plaintext image passes through the compressed sensing measurement matrix generated by chaos and is scrambled and encrypted, the image size changes, and the ciphertext image completely loses the characteristics of the plaintext image. In terms of visual resolution, the resolution of a decrypted image is lower than the original plaintext image. To accurately evaluate the performance of the compressed image and the security of the encrypted image, detailed analysis is conducted, including algorithm complexity, compression ratio, key space, pictorial diagram analysis, adjacent pixel correlation, information entropy, and resistance to differential attacks.
5.2. Compression Ratio
As the image size and decryption algorithm do not change throughout the simulation, the relative complexity of the algorithm also does not change. With the same algorithm complexity, while ensuring the encryption effect of images, the relationship between the image compression rate and the quality of reconstructed images will now be analyzed. In this paper, the image compression ratio is defined as
where
is the size of a plaintext image, and
is the size of a ciphertext image.
The structural similarity (SSIM) is used to evaluate the accuracy of a reconstructed image [
41]. The value of SSIM is between 0 and 1. When two signals are identical, the structural similarity is 1. The SSIM is defined as
PSNR is an important indicator for evaluating the quality of decoded images after image processing. It is defined as [
42]:
where
M × N is the size of the image, and
X(i, j) and
Y(i, j) are the pixel values of the plain image and decrypted image respectively. The larger the PSNR is, the smaller the distortion.
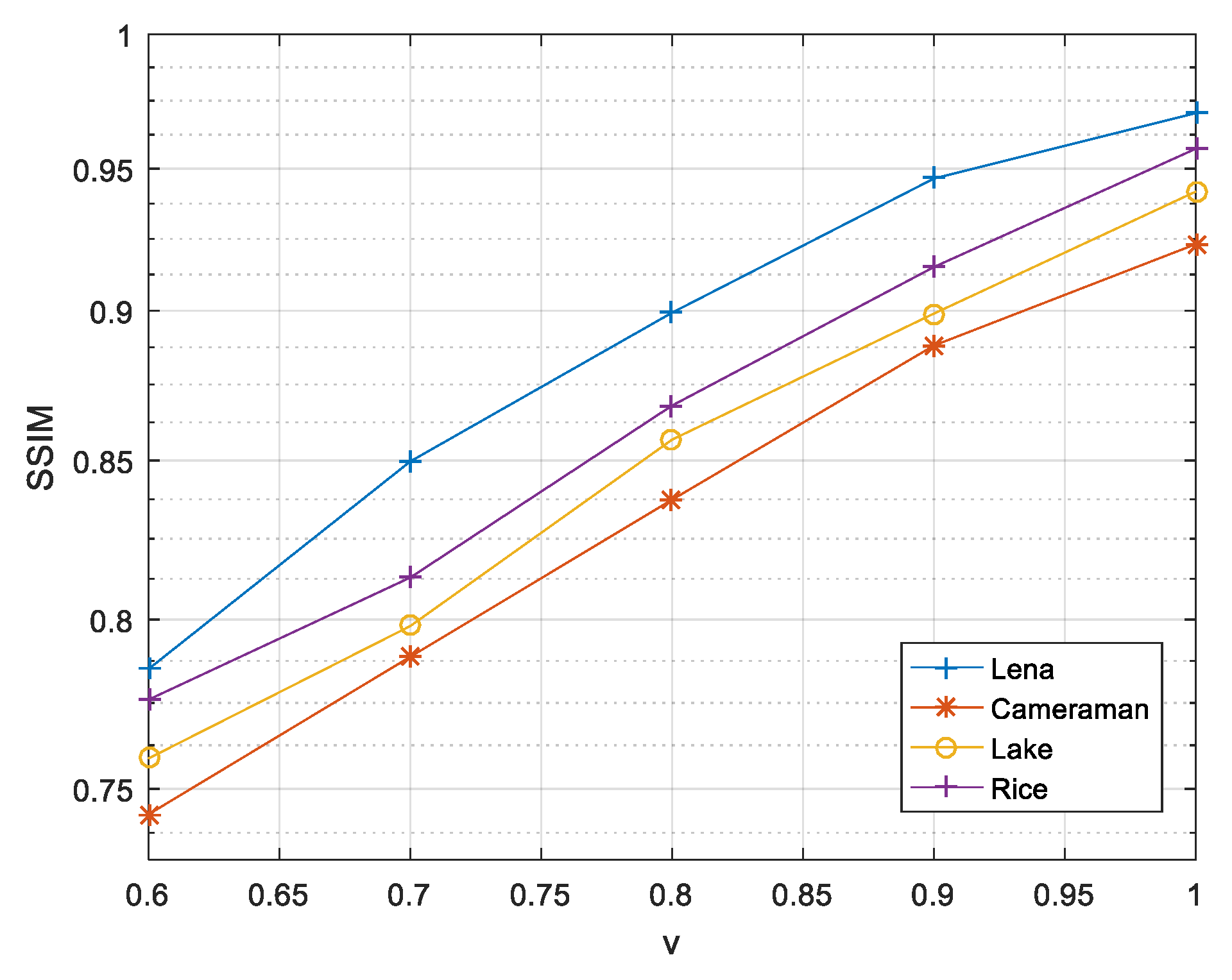
The following will analyze the limits of the image compression rate while ensuring the encryption effect and transmission security. In the CoSaMP algorithm, the sparsity is limited to
, so when selecting a sparsity of K = 50, the compression ratio cannot be smaller than 0.6. Therefore, in the compressible range, the image reconstruction effects corresponding to different compression ratios are shown in
Figure 6.
It can be seen from
Figure 6 that as the compression ratio decreases, the structural similarity coefficient between the reconstructed image and the original image is reduced, but in the compressible range, the reconstruction can be achieved relatively well. Under the same compression ratio and sparsity, the reconstruction effects of different images vary; the reconstruction effect of Lena is significantly better than the other three images.
To compare our compression encryption algorithm with other methods,
Table 2 shows that the PSNR value of Lena is reconstructed by different methods in the case of compression ratio
.
It can be seen from
Table 2 that in the different hyperchaotic systems when the image and compression ratio are the same, the PSNR value of the image recovered by the compression encryption method proposed in this paper is relatively large, so the effect of reconstructing the image is better than other methods.
5.3. NIST Test
Pseudo-randomness is an important indicator of the security of encryption algorithms. To further verify the cryptographic characteristics of new chaotic pseudo-random sequences, it is necessary to quantitatively evaluate the pseudo-randomness of cryptographic algorithms [
46]. Among the many methods for testing pseudo-randomness, this paper selects sts-2.1.2 [
47] in the NIST version. The pseudo-randomness of a sequence is determined by the
p-value generated by the test results. According to the selected significance level
α, if
p-value ≥
α, it can be considered to have passed the test. With
selected, a 106-bit sequence was taken in the experiment and 100 sequences of this were tested. The test results are shown in
Table 3.
The results show that in this sequence of NIST tests, all
p-values exceed 0.0001, which indicates that the test sequence is uniform. Therefore, the generated sequence is random and this system is suitable for encryption algorithms [
48].
5.4. Key Space Analysis
Key space analysis is primarily conducted to evaluate the capability of an algorithm to resist exhaustive attacks. For an algorithm with good resistance to exhaustive attacks, the key space must exceed 2
100 [
49,
50]. In this paper, there are a total of two encryption algorithm keys; one is composed of the initial values and the parameters of the chaos: key
, with a total of nine parameters; and the other is the scrambling parameter and the number of iterations in Arnold scrambling: key
, with a total of three parameters. Since there are 12 parameters in the key space in this paper, it is difficult to accurately locate each parameter. According to the international standard ieee 754, in order to simplify the comparison, the index part is expressed in the form of a positive value. So we calculate the exponent bit of 12 sign bits to about 52 bits, and our key space must be greater than
.
It can be seen from
Table 4 that the proposed algorithm has a key space that is greater than those published in the literature [
10,
51,
52,
53]. Therefore, the key space of this algorithm is large enough to resist exhaustive attack.
5.5. Analysis of Resistance to Statistical Attacks
5.5.1. Histogram Analysis
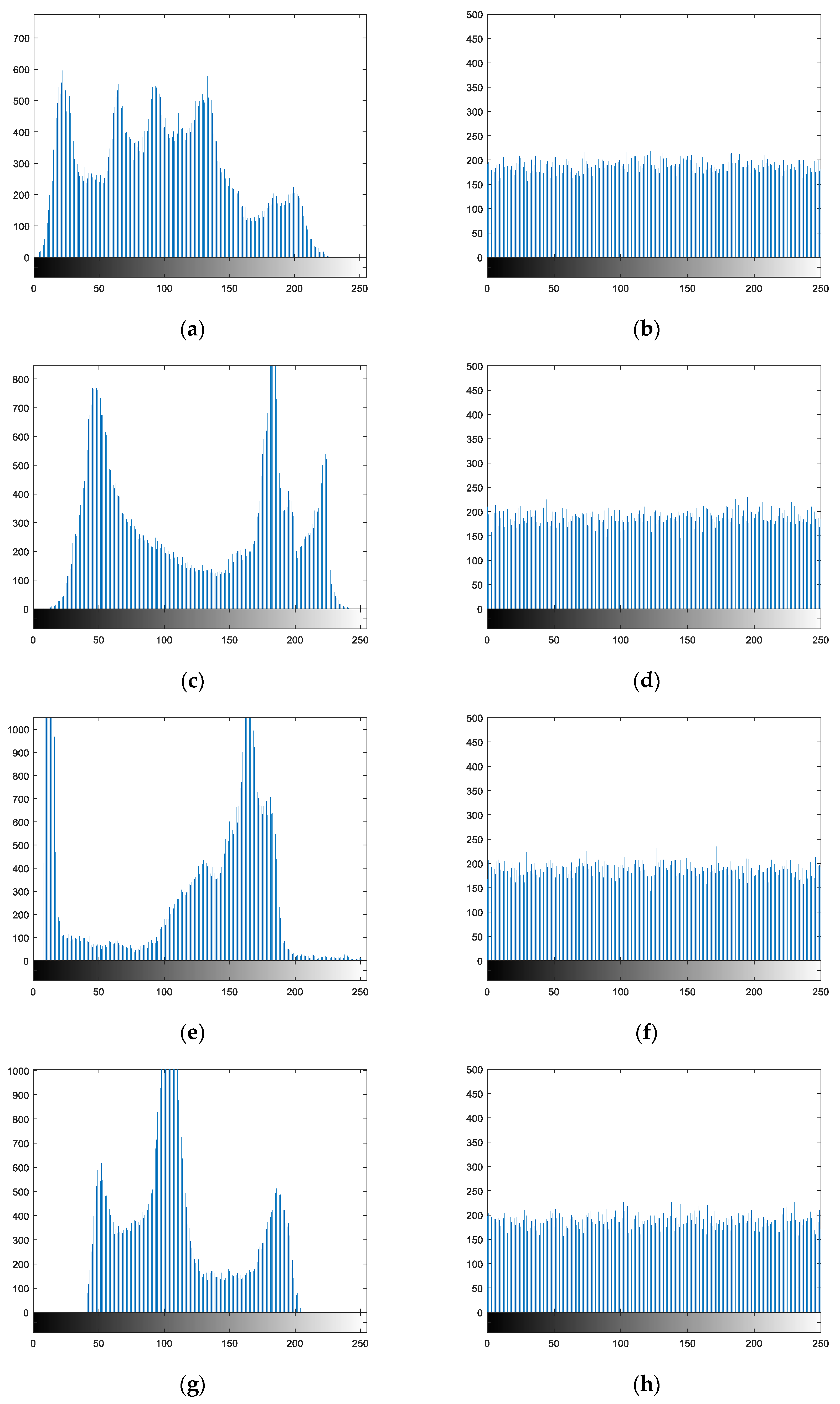
The plaintext and ciphertext histograms of different images in the encryption and decryption process are shown in
Figure 7.
As can be seen from
Figure 7, the distribution ranges and intensities of pixels in the plaintext image histograms are uneven. After encryption using the algorithm in this paper, the pixel values in the ciphertext images are distributed within the range of 0 to 255, and the probability of occurrence of each pixel value is largely equivalent. This suggests that the statistical properties of the plaintext pixels have fundamentally changed. Therefore, the encryption algorithm proposed in this paper can effectively resist attacks based on statistical analysis.
5.5.2. Analysis of Correlation between Adjacent Pixels
The correlation coefficients of adjacent pixels can be used to evaluate the effect of image encryption. In general, a relatively good digital image encryption scheme can result in relatively low correlation between adjacent pixels of a ciphertext image [
7,
54]. The closer to 0 the correlation coefficient of adjacent pixels is, the better the effect of encryption. In this paper, the correlation coefficients of adjacent pixels are calculated for 10,000 selected pairs of pixels in the images, and the calculation formula is
In Formula (18), the adjacent pixels in the image to be measured are expressed by
x and
y, respectively, while
are the average values of all x and y values.
N pairs of pixels are selected, and
is the correlation coefficient. To analyze the encryption algorithm proposed in this paper, 10,000 pairs of pixels are selected from the plaintext and ciphertext images of Lena, Lake, Cameraman, and Rice. For each plaintext and ciphertext image, correlation coefficients of adjacent pixels are calculated from the horizontal, vertical, and diagonal directions, with the results summarized in
Table 5.
As can be seen from
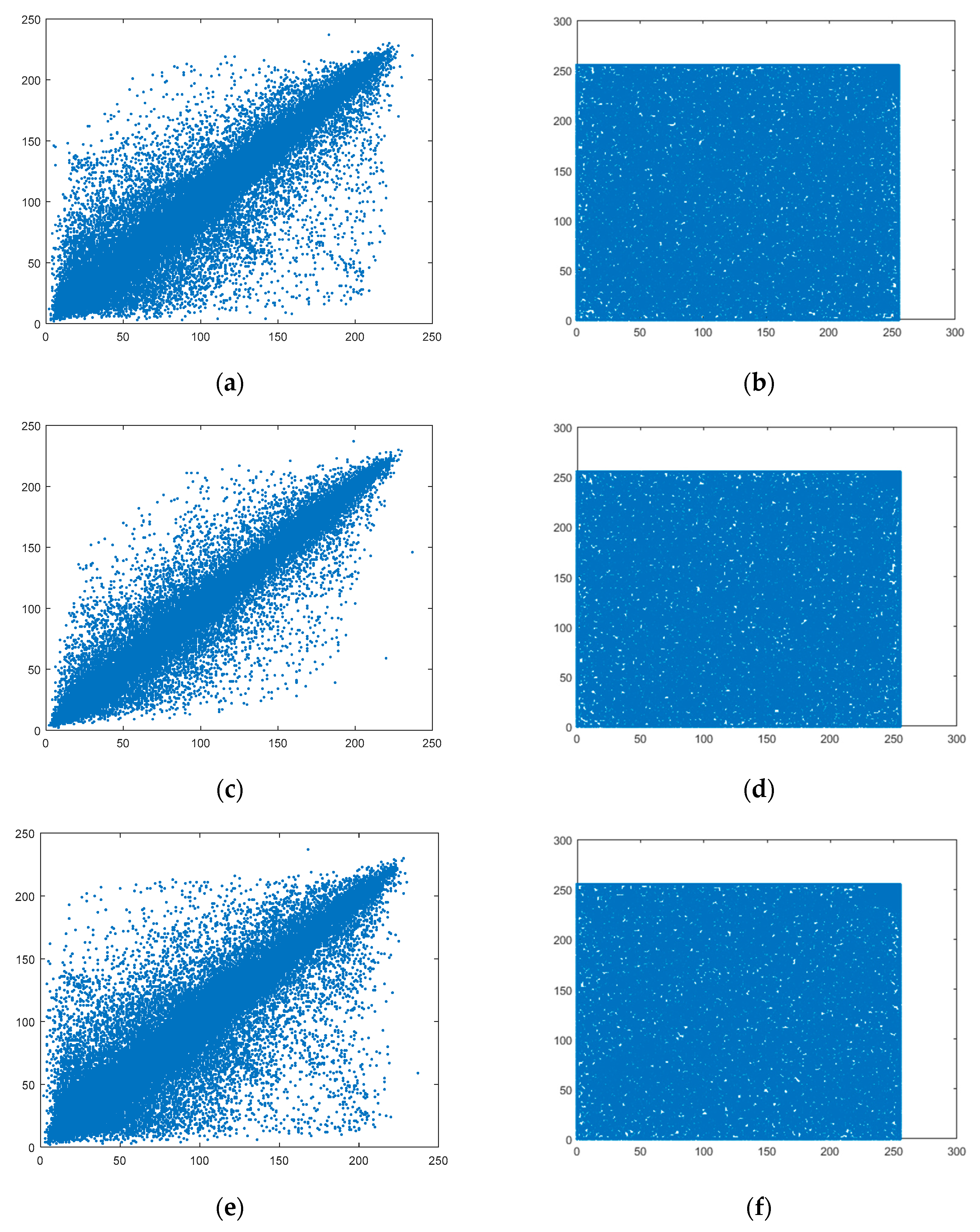
Table 5, the correlation coefficients of adjacent pixels in plaintext images from all three directions are greater than 0.9, suggesting a high correlation degree between adjacent pixels. The correlation of adjacent pixels in the images encrypted by the algorithm proposed in this paper approaches 0. Taking Lena as an example, 10,000 pairs of pixels are selected from the original image and encrypted image among the horizontal, vertical, and diagonal directions. The gradation value relationships of adjacent pixels are shown in
Figure 8.
As can be seen from
Figure 8, the gray values of horizontal, vertical, and diagonal adjacent pixels from the plaintext image are distributed around
y = x, while those from the ciphertext image are randomly distributed between 0 and 255.
5.5.3. Information Entropy Analysis
In image encryption analysis, information entropy is the main parameter used for analyzing the randomness of information distribution in encrypted images [
5]. The more random (uniform) the gray value distribution is, the greater the information entropy, and the better the effect of image encryption; conversely, the weaker the randomness, the lower the information entropy is. The information entropy
H can be expressed as
In Formula (19),
represents the probability of
appearing in the image m. In this paper, the 8-bit Lena image is selected, with an ideal information entropy value of
. In 8-bit digital image analysis, the more random the encrypted image is, the closer the information entropy is to 8. The information entropies of plaintext and ciphertext images are listed in
Table 6.
In
Table 7, the information entropy of the ciphertext Lena image with a size of 256 × 256 obtained in this paper is compared with that from other studies [
55,
56]. As can be seen from the data, the algorithm proposed in this paper has achieved good results under the premise of data compression to save storage space. The information entropy of the plaintext image is relatively low, but the information entropy is very close to 8 after encryption.
5.6. Analysis of Resistance to Differential Attacks
The resistance of an encryption algorithm to differential attacks can be used to assess the sensitivity of a plaintext image. If a small change in the plaintext image does not result in a significant change in the ciphertext image, then the encryption algorithm is not resistant to differential attacks. If it results in a significant change, then the encryption algorithm can resist differential attacks. The resistance to differential attacks targeting an algorithm can be evaluated by calculating the pixel change rate (NPCR) and the unified average changing intensity (UACI) [
57]. The formulae are as follows:
In Formulas (20) and (21), m × n indicates the size of the image. and respectively indicate the pixel value of point in the corresponding encrypted images of two plaintext images with only one different pixel. When the two plaintext images are only different by one pixel, the pixel value of point is represented in the two ciphertext images as and .
The resistance to a differential attack is tested in the simulation experiment with the grayscale images of Lena, Lake, Cameraman, and Rice, each of size 256 × 256. The average NPCR and UACI values of the algorithm proposed in this paper are listed in
Table 8. The ideal values of NPCR and UACI are 99.6093% and 33.4635%, respectively [
10].
It can be seen from the experimental results that the NPCR values and UACI values obtained by the encryption algorithm proposed in this paper are very close to the ideal values, indicating that the proposed algorithm has strong resistance to differential attacks.
6. Conclusions
In this paper, a new three-dimensional chaotic system is proposed for image encryption. The core of the encryption algorithm is the combination of chaotic system and compressed sensing, which is practical and can complete compression and encryption simultaneously. The Lyapunov exponent, bifurcation diagram and complexity of the new three-dimensional chaotic system are analyzed. The performance analysis shows that the chaotic system has two positive Lyapunov exponents and high complexity. It is verified that the new three-dimensional chaos proposed in this paper is practical and can be used in encryption. In the encryption scheme, a new chaotic system is used as the measurement matrix for compressed sensing, and Arnold is used to scramble the image further. The results of the encrypted scheme are analyzed and evaluated from two aspects. First, analyze the effects of reconstructed images. The proposed method has better reconfiguration ability in the compressible range of the algorithm compared with other methods. Second, analyze the security of the encryption algorithm. The proposed encryption algorithm can resist various attacks from key space, statistical analysis, information entropy and differential analysis. Finally, the proposed encryption scheme has good encryption effect and image compression capability.