Detection of Anomalies in Large-Scale Cyberattacks Using Fuzzy Neural Networks
Abstract
1. Introduction
2. Literature Review
2.1. Large-Scale Problems
2.2. Cybernetic Invasions and Intrusion Detectors
- -
- A connection is a sequence of TCP packets starting and ending at some well-defined times, between which data flows to and from a source IP address to a destination IP address in some well-defined protocol.
- -
- Each connection is labeled regular or as an attack, with precisely one type of attack specific.
- -
- Each connection record consists of about 100 bytes.
- -
- DOS: denial of service;
- -
- R2L: unauthorized access of a remote machine;
- -
- U2R: unauthorized access to root superuser privileges;
- -
- Poll: Surveillance and other polls.
2.3. Anomaly Detection
2.4. Related Work
3. Fuzzy Neural Networks
Fuzzy Neural Networks and Their Practical Applications
4. Fuzzy Neural Networks Model
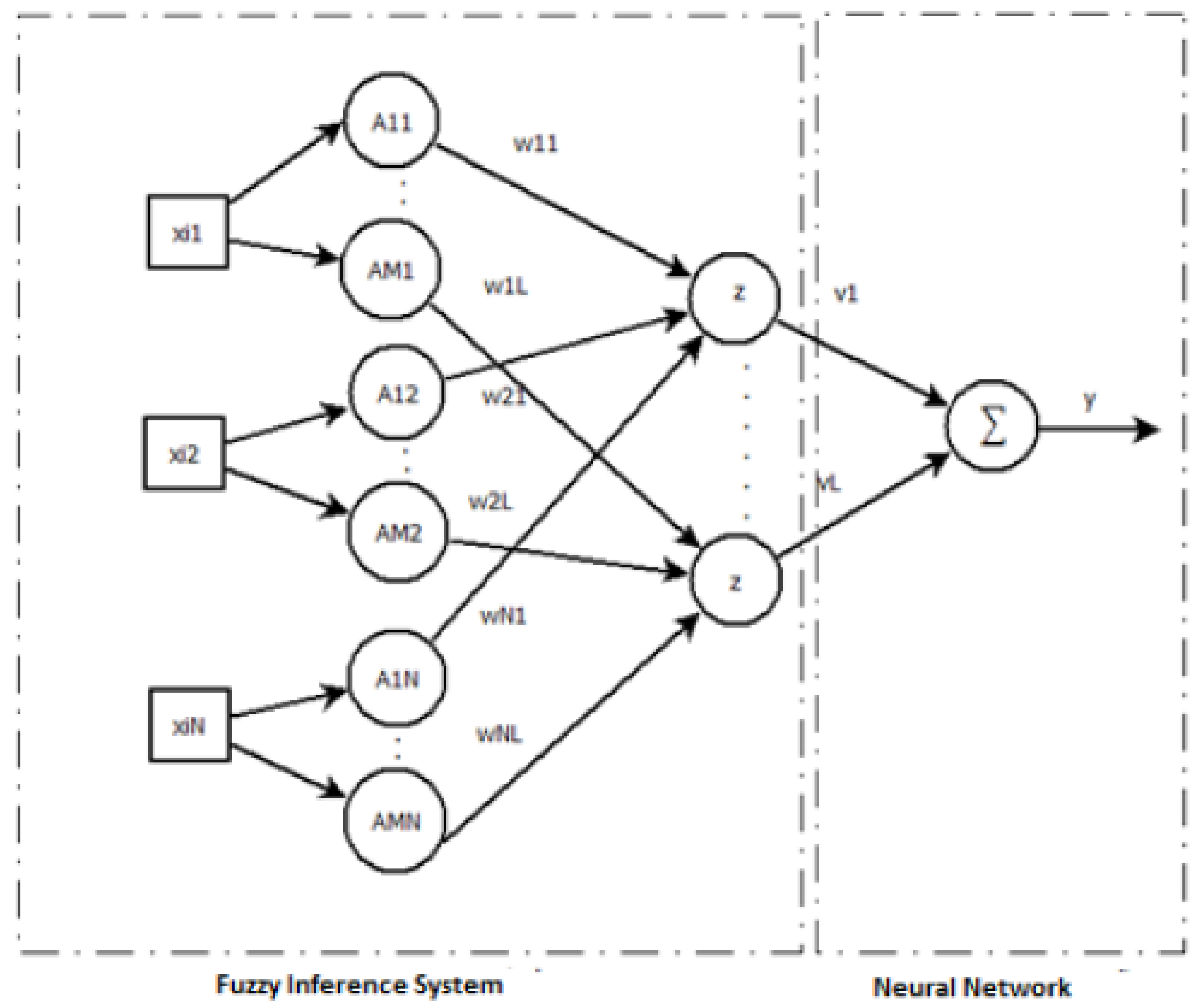
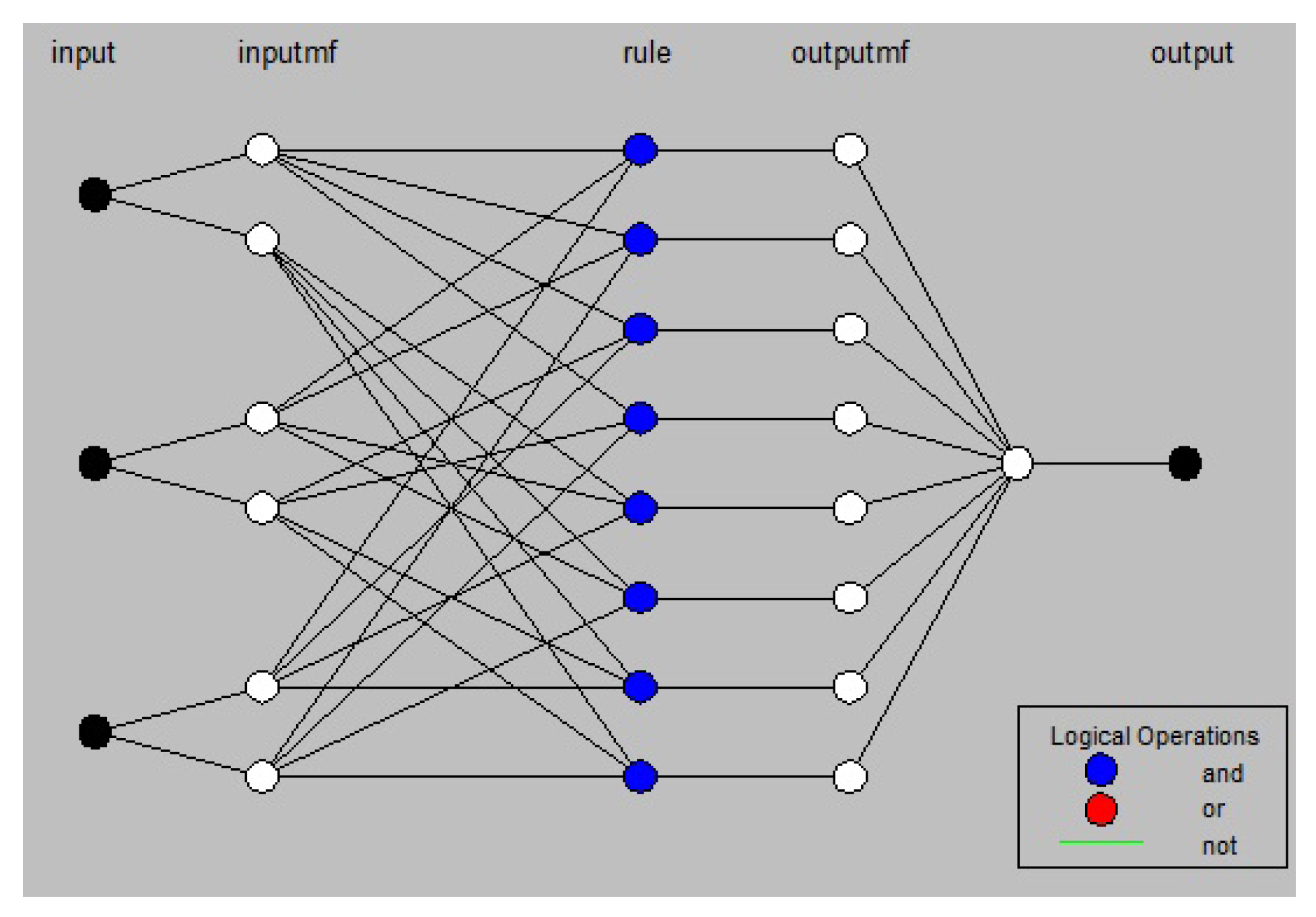
4.1. Network Architecture
- ach pair (, ) is transformed into a single value = h(, );
- calculate the unified aggregation of the transformed values U (), where n is the number of inputs.
4.2. Training Fuzzy Neural Network
5. Proposed Detection of Cyber Invasions Through Detection of Anomalies Through Hybrid Models and the Creation of Expert Systems
- the number of membership functions, M;
- the type of fuzzy logic neuron, andneuron or unineuron;
| Algorithm 1: Fuzzy Neural Network for anomaly detection -FNN training. |
| (1) Define the number of membership functions, M. |
| (2) Calculate M neurons for each characteristic in the first layer using ANFIS. |
| (3) Construct L fuzzy neurons with Gaussian membership functions constructed with center and values derived from ANFIS. |
| (4) Define the weights and bias of the fuzzy neurons randomly. |
| (5) Construct L fuzzy logical neurons with random weights and bias on the second layer of the network by welding the L fuzzy neurons of the first layer. |
| (6) For all K input do |
| (6.1) Calculate the mapping using andneurons |
| end for |
| (7) Estimate the weights of the output layer using Equation (11). |
| (8) Calculate output y using leaky ReLU using Equation (1). |
6. Anomaly Detection Test
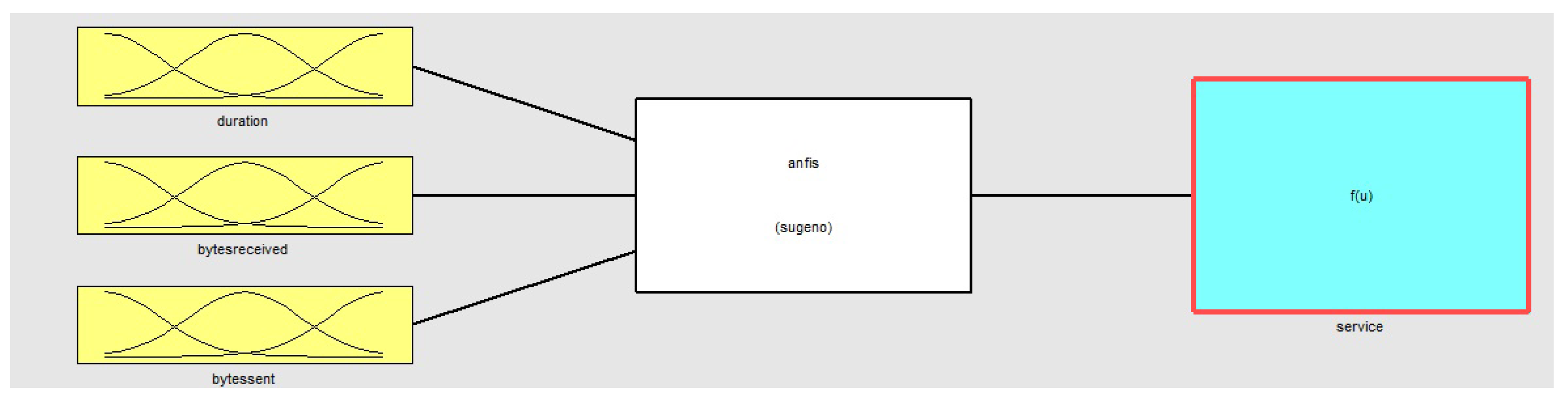
6.1. Dataset Uses
6.2. Definitions and Models Used in the Tests
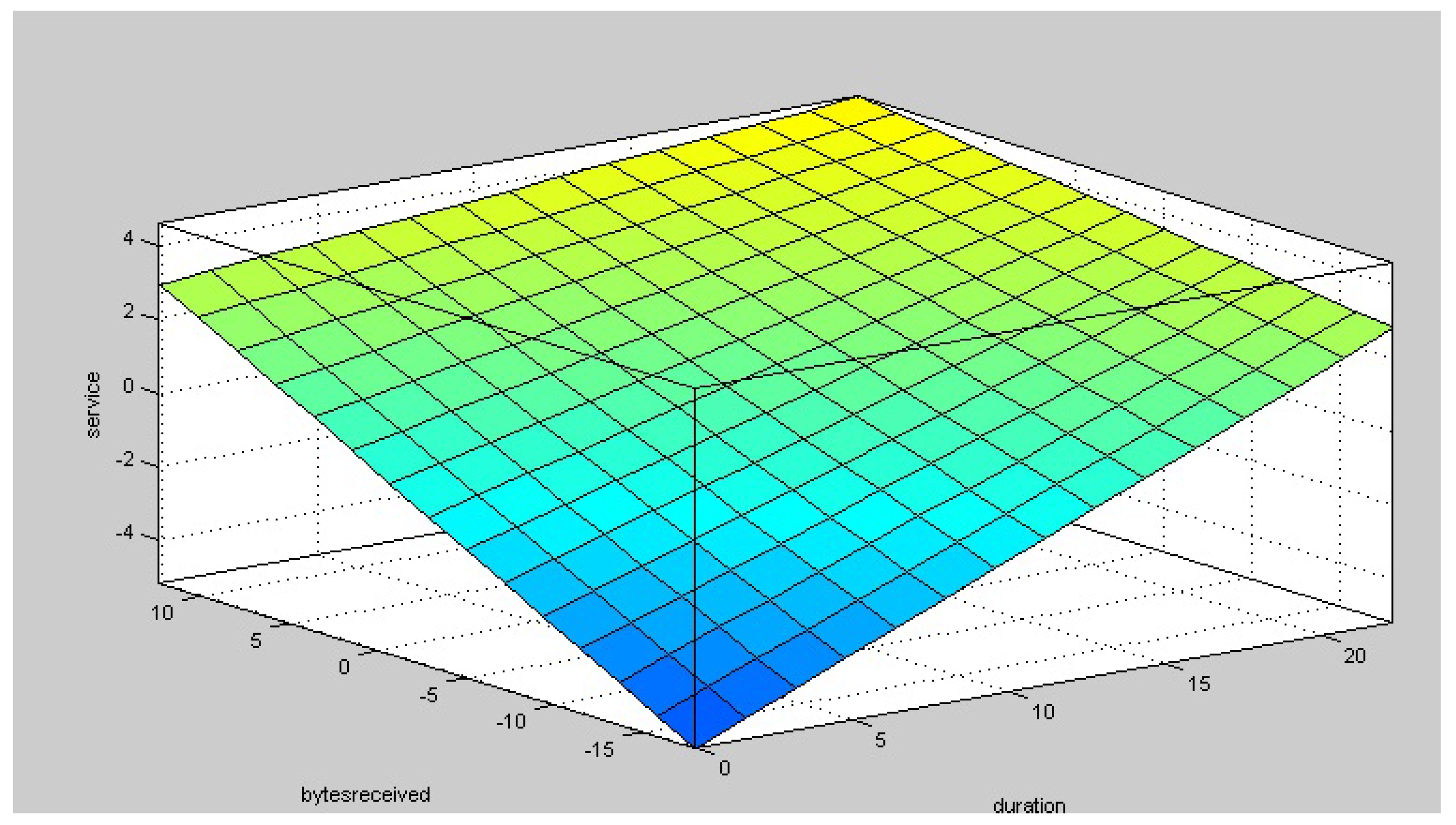
6.3. Results of Anomaly Detection
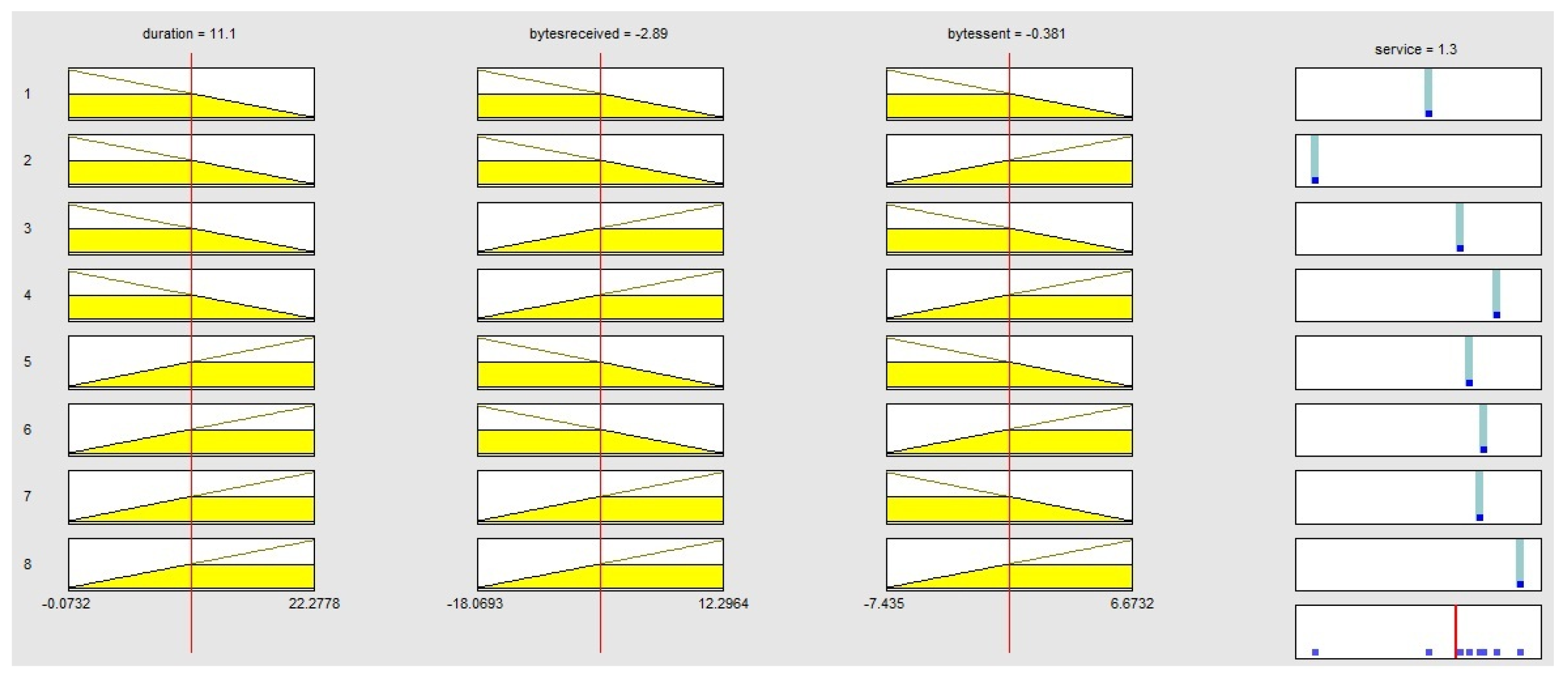
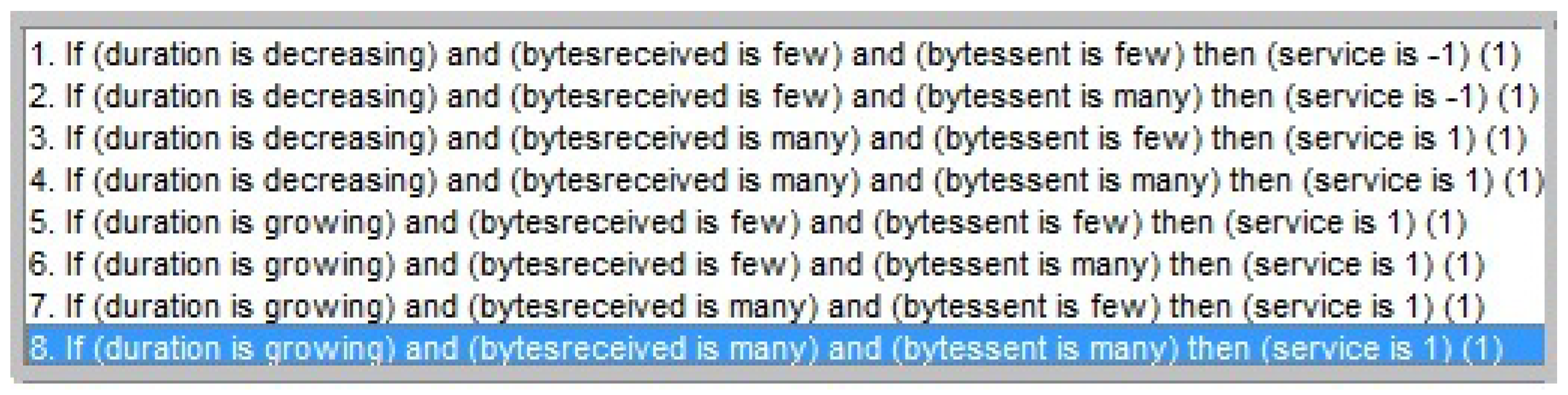
6.4. Expert Systems in Detecting Anomalies in Cyberattacks Through Fuzzy Rules
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| MDPI | Multidisciplinary Digital Publishing Institute |
| DOAJ | Directory of open access journals |
| FNN | Fuzzy Neural Network |
| ANFIS | Adaptive neuro-fuzzy inference system |
| DOS | Disk Operating System |
| ReLU | Rectified Linear Activation |
References
- Duggal, P. # Cyberlaw: Global trends in 2014. AI Soc. 2014. [Google Scholar] [CrossRef]
- Jansen, C.; Jeschke, S. Mitigating risks of digitalization through managed industrial security services. AI Soc. 2018, 33, 163–173. [Google Scholar] [CrossRef]
- Shoji, H.; Hori, K. S-Conart: An interaction method that facilitates concept articulation in shopping online. AI Soc. 2005, 19, 65–83. [Google Scholar] [CrossRef]
- Gill, K.S. The transformation of the human dimension in the cyberspace. AI Soc. 2012, 27, 429–430. [Google Scholar] [CrossRef][Green Version]
- Enli, G. Twitter as arena for the authentic outsider: Exploring the social media campaigns of Trump and Clinton in the 2016 US presidential election. Eur. J. Commun. 2017, 32, 50–61. [Google Scholar] [CrossRef]
- Green, J.N. Brazil faces its most important election. Green Left Wkly. 2018, 1200, 15. [Google Scholar]
- Gandomi, A.; Haider, M. Beyond the hype: Big data concepts, methods, and analytics. Int. J. Inf. Manag. 2015, 35, 137–144. [Google Scholar] [CrossRef]
- Wang, C.; Wang, Q.; Ren, K.; Lou, W. Privacy-preserving public auditing for data storage security in cloud computing. In Proceedings of the 2010 Proceedings IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–9. [Google Scholar]
- Pasqualetti, F.; Dörfler, F.; Bullo, F. Attack detection and identification in cyber-physical systems. IEEE Trans. Autom. Control 2013, 58, 2715–2729. [Google Scholar] [CrossRef]
- Ball, J.; Borger, J.; Greenwald, G. Revealed: How US and UK spy agencies defeat internet privacy and security. Guardian 2013, 6, 2–8. [Google Scholar]
- Greenwald, G. NSA collecting phone records of millions of Verizon customers daily. Guardian 2013, 6, 2013. [Google Scholar]
- Yueai, Z.; Junjie, C. Application of unbalanced data approach to network intrusion detection. In Proceedings of the 2009 First International Workshop on Database Technology and Applications, Wuhan, China, 25–26 April 2009; pp. 140–143. [Google Scholar]
- Ngai, E.W.; Hu, Y.; Wong, Y.; Chen, Y.; Sun, X. The application of data mining techniques in financial fraud detection: A classification framework and an academic review of literature. Decis. Support Syst. 2011, 50, 559–569. [Google Scholar] [CrossRef]
- Friedberg, M.K.; Silverman, N.H.; Moon-Grady, A.J.; Tong, E.; Nourse, J.; Sorenson, B.; Lee, J.; Hornberger, L.K. Prenatal detection of congenital heart disease. J. Pediatr. 2009, 155, 26–31. [Google Scholar] [CrossRef]
- Fugate, M.; Gattiker, J.R. Anomaly detection enhanced classification in computer intrusion detection. In Pattern Recognition with Support Vector Machines; Springer: New York, NY, USA, 2002; pp. 186–197. [Google Scholar]
- Hadeli, H.; Schierholz, R.; Braendle, M.; Tuduce, C. Leveraging determinism in industrial control systems for advanced anomaly detection and reliable security configuration. In Proceedings of the IEEE Conference on Emerging Technologies & Factory Automation (ETFA 2009), Mallorca, Spain, 22–25 September 2009; pp. 1–8. [Google Scholar]
- Kumarage, H.; Khalil, I.; Tari, Z.; Zomaya, A. Distributed anomaly detection for industrial wireless sensor networks based on fuzzy data modelling. J. Parallel Distrib. Comput. 2013, 73, 790–806. [Google Scholar] [CrossRef]
- Zhou, D.-H.; Wei, M.-H.; Si, X.-S. A survey on anomaly detection, life prediction and maintenance decision for industrial processes. Acta Autom. Sin. 2013, 39, 711–722. [Google Scholar] [CrossRef]
- Eskin, E. Anomaly detection over noisy data using learned probability distributions. In Proceedings of the International Conference on Machine Learning. Citeseer, San Francisco, CA, USA, 29 June–2 July 2000. [Google Scholar]
- Meroni, M.; Fasbender, D.; Rembold, F.; Atzberger, C.; Klisch, A. Near real-time vegetation anomaly detection with MODIS NDVI: Timeliness vs. accuracy and effect of anomaly computation options. Remote Sens. Environ. 2019, 221, 508–521. [Google Scholar] [CrossRef]
- Zamanian, Z.; Feizollah, A.; Anuar, N.B.; Kiah, L.B.M.; Srikanth, K.; Kumar, S. User Profiling in Anomaly Detection of Authorization Logs. In Computational Science and Technology; Springer: New York, NY, USA, 2019; pp. 59–65. [Google Scholar]
- Borghesi, A.; Bartolini, A.; Lombardi, M.; Milano, M.; Benini, L. Anomaly detection using autoencoders in high performance computing systems. In Proceedings of the AAAI Conference on Artificial Intelligence, Honolulu, HI, USA, 27 January–1 February 2019; Volume 33, pp. 9428–9433. [Google Scholar]
- Wang, N.; Zhang, Z.; Zhao, X.; Miao, Q.; Ji, R.; Gao, Y. Exploring High-Order Correlations for Industry Anomaly Detection. IEEE Trans. Ind. Electron. 2019, 66, 9682–9691. [Google Scholar] [CrossRef]
- Ben-Asher, N.; Gonzalez, C. Effects of cyber security knowledge on attack detection. Comput. Hum. Behav. 2015, 48, 51–61. [Google Scholar] [CrossRef]
- Lin, C.T.; Lee, C.G.; Lin, C.T.; Lin, C. Neural fUzzy Systems: A Neuro-Fuzzy Synergism to Intelligent Systems; Prentice Hall PTR: Upper Saddle River, NJ, USA, 1996; Volume 205. [Google Scholar]
- Pal, S.K.; Mitra, S. Neuro-Fuzzy Pattern Recognition: Methods in Soft Computing; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 1999. [Google Scholar]
- Pedrycz, W.; Gomide, F. Fuzzy Systems Engineering: Toward Human-Centric Computing; John Wiley & Sons: Hoboken, NJ, USA, 2007. [Google Scholar]
- Lin, C.T.; Yeh, C.M.; Liang, S.F.; Chung, J.F.; Kumar, N. Support-vector-based fuzzy neural network for pattern classification. IEEE Trans. Fuzzy Syst. 2006, 14, 31–41. [Google Scholar]
- Meesad, P.; Yen, G.G. Pattern classification by a neurofuzzy network: Application to vibration monitoring. ISA Trans. 2000, 39, 293–308. [Google Scholar] [CrossRef]
- Lin, J.W.; Hwang, M.I.; Becker, J.D. A fuzzy neural network for assessing the risk of fraudulent financial reporting. Manag. Audit. J. 2003, 18, 657–665. [Google Scholar] [CrossRef]
- Kuo, R.J.; Chen, C.; Hwang, Y. An intelligent stock trading decision support system through integration of genetic algorithm based fuzzy neural network and artificial neural network. Fuzzy Sets Syst. 2001, 118, 21–45. [Google Scholar] [CrossRef]
- Wang, Y.; Zhu, Y.S.; Thakor, N.V.; Xu, Y.H. A short-time multifractal approach for arrhythmia detection based on fuzzy neural network. IEEE Trans. Biomed. Eng. 2001, 48, 989–995. [Google Scholar] [CrossRef] [PubMed]
- Cheng, H.; Cui, M. Mass lesion detection with a fuzzy neural network. Pattern Recognit. 2004, 37, 1189–1200. [Google Scholar] [CrossRef]
- Li, X.; Lim, B.; Zhou, J.; Huang, S.; Phua, S.; Shaw, K.; Er, M. Fuzzy neural network modelling for tool wear estimation in dry milling operation. In Proceedings of the Annual Conference of the Prognostics and Health Management Society, San Diego, CA, USA, 27 September–1 October 2009; pp. 1–11. [Google Scholar]
- Chang, P.C.; Liu, C.H.; Fan, C.Y. Data clustering and fuzzy neural network for sales forecasting: A case study in printed circuit board industry. Knowl.-Based Syst. 2009, 22, 344–355. [Google Scholar] [CrossRef]
- Hsiao, S.W.; Tsai, H.C. Applying a hybrid approach based on fuzzy neural network and genetic algorithm to product form design. Int. J. Ind. Ergon. 2005, 35, 411–428. [Google Scholar] [CrossRef]
- Batista, L.O.; de Silva, G.A.; Araújo, V.S.; Araújo, V.J.S.; Rezende, T.S.; Guimarães, A.J.; Souza, P.V.d.C. Fuzzy neural networks to create an expert system for detecting attacks by SQL Injection. Int. J. Forensic Comput. Sci. 2018, 13, 8–21. [Google Scholar] [CrossRef]
- Wang, G.; Hao, J.; Ma, J.; Huang, L. A new approach to intrusion detection using Artificial Neural Networks and fuzzy clustering. Expert Syst. Appl. 2010, 37, 6225–6232. [Google Scholar] [CrossRef]
- de Campos Souza, P.V.; Rezende, T.S.; Guimaraes, A.J.; Araujo, V.S.; Batista, L.O.; da Silva, G.A.; Silva Araujo, V.J. Evolving fuzzy neural networks to aid in the construction of systems specialists in cyber attacks. J. Intell. Fuzzy Syst. 2019, 36, 6743–6763. [Google Scholar] [CrossRef]
- Demertzis, K.; Iliadis, L. A hybrid network anomaly and intrusion detection approach based on evolving spiking neural network classification. In Proceedings of the International Conference on e-Democracy, Athens, Greece, 5–6 December 2013; pp. 11–23. [Google Scholar]
- Demertzis, K.; Iliadis, L. Evolving smart URL filter in a zone-based policy firewall for detecting algorithmically generated malicious domains. In Proceedings of the International Symposium on Statistical Learning and Data Sciences, Egham, UK, 20–23 April 2015; pp. 223–233. [Google Scholar]
- Demertzis, K.; Iliadis, L. Computational intelligence anti-malware framework for android OS. Vietnam. J. Comput. Sci. 2017, 4, 245–259. [Google Scholar] [CrossRef]
- Yusob, B.; Mustaffa, Z.; Sulaiman, J. Anomaly Detection in Time Series Data Using Spiking Neural Network. Adv. Sci. Lett. 2018, 24, 7572–7576. [Google Scholar] [CrossRef]
- Maas, A.L.; Hannun, A.Y.; Ng, A.Y. Rectifier nonlinearities improve neural network acoustic models. Proc. ICMl 2013, 30, 3. [Google Scholar]
- Jang, J.S. ANFIS: Adaptive-network-based fuzzy inference system. IEEE Trans. Syst. Man Cybern. 1993, 23, 665–685. [Google Scholar] [CrossRef]
- Huang, G.B.; Zhu, Q.Y.; Siew, C.K. Extreme learning machine: Theory and applications. Neurocomputing 2006, 70, 489–501. [Google Scholar] [CrossRef]
- Souza, P.V.C. Regularized Fuzzy Neural Networks for Pattern Classification Problems. Int. J. Appl. Eng. Res. 2018, 13, 2985–2991. [Google Scholar]
- Cukier, K.; Mayer-Schoenberger, V. The rise of big data: How it’s changing the way we think about the world. Foreign Aff. 2013, 92, 28. [Google Scholar]
- Tankard, C. Big data security. Netw. Secur. 2012, 2012, 5–8. [Google Scholar] [CrossRef]
- Zikopoulos, P.; Eaton, C. Understanding Big Data: Analytics for Enterprise Class Hadoop and Streaming Data; McGraw-Hill Osborne Media: New York, NY, USA, 2011. [Google Scholar]
- Stolfo, J.; Fan, W.; Lee, W.; Prodromidis, A.; Chan, P.K. Cost-based modeling and evaluation for data mining with application to fraud and intrusion detection. Results Jam Proj. Salvatore 2000, 1–15. [Google Scholar]
- Chandola, V.; Banerjee, A.; Kumar, V. Anomaly detection: A survey. ACM Comput. Surv. CSUR 2009, 41, 15. [Google Scholar] [CrossRef]
- Patcha, A.; Park, J.M. An overview of anomaly detection techniques: Existing solutions and latest technological trends. Comput. Netw. 2007, 51, 3448–3470. [Google Scholar] [CrossRef]
- Bhuyan, M.H.; Bhattacharyya, D.K.; Kalita, J.K. Network anomaly detection: Methods, systems and tools. IEEE Commun. Surv. Tutor. 2014, 16, 303–336. [Google Scholar] [CrossRef]
- Hartigan, J.A.; Wong, M.A. Algorithm AS 136: A k-means clustering algorithm. J. R. Stat. Soc. Ser. C Appl. Stat. 1979, 28, 100–108. [Google Scholar] [CrossRef]
- Chandola, V.; Banerjee, A.; Kumar, V. Anomaly detection for discrete sequences: A survey. IEEE Trans. Knowl. Data Eng. 2012, 24, 823–839. [Google Scholar] [CrossRef]
- Ahmed, M.; Mahmood, A.N.; Hu, J. A survey of network anomaly detection techniques. J. Netw. Comput. Appl. 2016, 60, 19–31. [Google Scholar] [CrossRef]
- Estevez-Tapiador, J.M.; Garcia-Teodoro, P.; Diaz-Verdejo, J.E. Anomaly detection methods in wired networks: A survey and taxonomy. Comput. Commun. 2004, 27, 1569–1584. [Google Scholar] [CrossRef]
- Sabahi, F.; Movaghar, A. Intrusion detection: A survey. In Proceedings of the 3rd International Conference on Systems and Networks Communications (ICSNC’08), Sliema, Malta, 26–31 October 2008; pp. 23–26. [Google Scholar]
- Xie, M.; Han, S.; Tian, B.; Parvin, S. Anomaly detection in wireless sensor networks: A survey. J. Netw. Comput. Appl. 2011, 34, 1302–1325. [Google Scholar] [CrossRef]
- Stein, D.W.; Beaven, S.G.; Hoff, L.E.; Winter, E.M.; Schaum, A.P.; Stocker, A.D. Anomaly detection from hyperspectral imagery. IEEE Signal Process. Mag. 2002, 19, 58–69. [Google Scholar] [CrossRef]
- Garcia-Teodoro, P.; Diaz-Verdejo, J.; Maciá-Fernández, G.; Vázquez, E. Anomaly-based network intrusion detection: Techniques, systems and challenges. Comput. Secur. 2009, 28, 18–28. [Google Scholar] [CrossRef]
- Kruegel, C.; Vigna, G. Anomaly detection of web-based attacks. In Proceedings of the 10th ACM Conference on Computer and Communications Security, Washington, DC, USA, 27–31 October 2003; pp. 251–261. [Google Scholar]
- Sekar, R.; Gupta, A.; Frullo, J.; Shanbhag, T.; Tiwari, A.; Yang, H.; Zhou, S. Specification-based anomaly detection: A new approach for detecting network intrusions. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; pp. 265–274. [Google Scholar]
- Noble, C.C.; Cook, D.J. Graph-based anomaly detection. In Proceedings of the Ninth ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Washington, DC, USA, 24–27 August 2003; pp. 631–636. [Google Scholar]
- Depren, O.; Topallar, M.; Anarim, E.; Ciliz, M.K. An intelligent intrusion detection system (IDS) for anomaly and misuse detection in computer networks. Expert Syst. Appl. 2005, 29, 713–722. [Google Scholar] [CrossRef]
- Krügel, C.; Toth, T.; Kirda, E. Service specific anomaly detection for network intrusion detection. In Proceedings of the 2002 ACM symposium on Applied Computing, Madrid, Spain, 10–14 March 2002; pp. 201–208. [Google Scholar]
- Thottan, M.; Ji, C. Anomaly detection in IP networks. IEEE Trans. Signal Process. 2003, 51, 2191–2204. [Google Scholar] [CrossRef]
- Nychis, G.; Sekar, V.; Andersen, D.G.; Kim, H.; Zhang, H. An empirical evaluation of entropy-based traffic anomaly detection. In Proceedings of the 8th ACM SIGCOMM Conference on Internet Measurement, Vouliagmeni, Greece, 20–22 October 2008; pp. 151–156. [Google Scholar]
- Feng, H.H.; Kolesnikov, O.M.; Fogla, P.; Lee, W.; Gong, W. Anomaly detection using call stack information. In Proceedings of the 2003 Symposium on Security and Privacy, Berkeley, CA, USA, 11–14 May 2003; pp. 62–75. [Google Scholar]
- Lee, W.; Xiang, D. Information-theoretic measures for anomaly detection. In Proceedings of the 2001 IEEE Symposium on Security and Privacy (S&P 2001), Oakland, CA, USA, 14–16 May 2001; pp. 130–143. [Google Scholar]
- Ye, N. A markov chain model of temporal behavior for anomaly detection. In Proceedings of the 2000 IEEE Systems, Man, and Cybernetics Information Assurance and Security Workshop, West Point, NY, USA, 6–7 June 2000; Volume 166, p. 169. [Google Scholar]
- Xie, Y.; Yu, S.Z. A large-scale hidden semi-Markov model for anomaly detection on user browsing behaviors. IEEE/ACM Trans. Netw. 2009, 17, 54–65. [Google Scholar] [CrossRef]
- Greensmith, J.; Aickelin, U.; Cayzer, S. Introducing dendritic cells as a novel immune-inspired algorithm for anomaly detection. In Proceedings of the International Conference on Artificial Immune Systems, Banff, AB, Canada, 14–17 August 2005; pp. 153–167. [Google Scholar]
- Zhang, J.; Gong, J. An anomaly detection method based on fuzzy judgment. J. Comput. Res. Dev. 2003, 40, 776–783. [Google Scholar]
- Hu, W.; Liao, Y.; Vemuri, V.R. Robust Support Vector Machines for Anomaly Detection in Computer Security. In Proceedings of the ICMLA, Los Angeles, CA, USA, 23–24 June 2003; pp. 168–174. [Google Scholar]
- Aleskerov, E.; Freisleben, B.; Rao, B. Cardwatch: A neural network based database mining system for credit card fraud detection. In Proceedings of the IEEE/IAFE 1997 Computational Intelligence for Financial Engineering (CIFEr), New York City, NY, USA, 24–25 March 1997; pp. 220–226. [Google Scholar]
- Schmidt, A.D.; Peters, F.; Lamour, F.; Scheel, C.; Çamtepe, S.A.; Albayrak, S. Monitoring smartphones for anomaly detection. Mob. Netw. Appl. 2009, 14, 92–106. [Google Scholar] [CrossRef]
- Saligrama, V.; Chen, Z. Video anomaly detection based on local statistical aggregates. In Proceedings of the 2012 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Providence, RI, USA, 16–21 June 2012; pp. 2112–2119. [Google Scholar]
- Xue, L.; Zhang, D.; Chen, Q.; Rao, H.; Xu, P. Tactile sensor of hardness recognition based on magnetic anomaly detection. In Proceedings of the Young Scientists Forum 2017, Shanghai, China, 5 March 2018; Volume 10710, p. 107102J. [Google Scholar]
- Liu, N.; Rebentrost, P. Quantum machine learning for quantum anomaly detection. Phys. Rev. A 2018, 97, 042315. [Google Scholar] [CrossRef]
- Capozzoli, A.; Piscitelli, M.S.; Brandi, S.; Grassi, D.; Chicco, G. Automated load pattern learning and anomaly detection for enhancing energy management in smart buildings. Energy 2018, 157, 336–352. [Google Scholar] [CrossRef]
- Lyons, P.; Suen, D.; Galusha, A.; Zare, A.; Keller, J. Comparison of prescreening algorithms for target detection in synthetic aperture sonar imagery. In Proceedings of the Detection and Sensing of Mines, Explosive Objects, and Obscured Targets XXIII, Orlando, FL, USA, 16–18 April 2018; Volume 10628, p. 1062811. [Google Scholar]
- Zhang, J.; Vukotic, I.; Gardner, R. Anomaly detection in wide area network mesh using two machine learning anomaly detection algorithms. arXiv 2018, arXiv:1801.10094. [Google Scholar]
- Sabokrou, M.; Fayyaz, M.; Fathy, M.; Moayed, Z.; Klette, R. Deep-anomaly: Fully convolutional neural network for fast anomaly detection in crowded scenes. Comput. Vis. Image Underst. 2018, 172, 88–97. [Google Scholar] [CrossRef]
- Min, R.; Song, D.; Cosatto, E. Large Margin High-Order Deep Learning With Auxiliary Tasks For Video-Based Anomaly Detection. US Patent 9,864,912, 9 January 2018. [Google Scholar]
- Settanni, G.; Filzmoser, P. Time Series Analysis: Unsupervised Anomaly Detection Beyond Outlier Detection. Inf. Secur. Pract. Exp. 2018, 11125, 19. [Google Scholar]
- Bittner, D.M.; Sarwate, A.D.; Wright, R.N. Using Noisy Binary Search for Differentially Private Anomaly Detection. In Proceedings of the International Symposium on Cyber Security Cryptography and Machine Learning, Beer-Sheva, Israel, 21–22 June 2018; pp. 20–37. [Google Scholar]
- Wang, X.; Zhou, Q.; Harer, J.; Brown, G.; Qiu, S.; Dou, Z.; Wang, J.; Hinton, A.; Gonzalez, C.A.; Chin, P. Deep learning-based classification and anomaly detection of side-channel signals. Cyber Sens. 2018, 10630, 1063006. [Google Scholar]
- Pedrycz, W. Granular Computing: Analysis and Design of Intelligent Systems; CRC Press: Boca Raton, FL, USA, 2016. [Google Scholar]
- Lemos, A.; Caminhas, W.; Gomide, F. New uninorm-based neuron model and fuzzy neural networks. In Proceedings of the 2010 Annual Meeting of the North American Fuzzy Information Processing Society (NAFIPS), Toronto, ON, Canada, 12–14 July 2010; pp. 1–6. [Google Scholar]
- Dunn, J.C. A Fuzzy Relative of the ISODATA Process and Its Use in Detecting Compact Well-Separated Clusters. J. Cybern. 1973, 3, 32–57. [Google Scholar] [CrossRef]
- Bezdek, J.C. Objective function clustering. In Pattern Recognition with Fuzzy Objective Function Algorithms; Springer: New York, NY, USA, 1981; pp. 43–93. [Google Scholar]
- Angelov, P.; Yager, R. A new type of simplified fuzzy rule-based system. Int. J. Gen. Syst. 2012, 41, 163–185. [Google Scholar] [CrossRef]
- Angelov, P. Evolving Takagi-Sugeno Fuzzy Systems from Streaming Data (eTS+). In Evolving Intelligent Systems: Methodology and Applications; Wiley: Hoboken, NJ, USA, 2010; pp. 21–50. [Google Scholar]
- Lima, E.; Gomide, F.; Ballini, R. Participatory evolving fuzzy modeling. In Proceedigs of the 2006 International Symposium on Evolving Fuzzy Systems, Ambleside, UK, 7–9 September 2006; pp. 36–41. [Google Scholar]
- Jang, J.S. Structure determination in fuzzy modeling: A fuzzy CART approach. In Proceedings of the Third IEEE Conference on Fuzzy Systems, Orlando, FL, USA, 26–29 June 1994; pp. 480–485. [Google Scholar]
- Han, S.J.; Cho, S.B. Evolutionary neural networks for anomaly detection based on the behavior of a program. IEEE Trans. Syst. Man Cybern. Part B Cybern. 2005, 36, 559–570. [Google Scholar]
- Meneganti, M.; Saviello, F.S.; Tagliaferri, R. Fuzzy neural networks for classification and detection of anomalies. IEEE Trans. Neural Netw. 1998, 9, 848–861. [Google Scholar] [CrossRef] [PubMed]
- Mahoney, M.V.; Chan, P.K. Learning rules for anomaly detection of hostile network traffic. In Proceedings of the Third IEEE International Conference on Data Mining, Melbourne, FL, USA, 22 November 2003; pp. 601–604. [Google Scholar] [CrossRef]
- Wiig, K.M. Knowledge-based systems and issues of integration: A commercial perspective. AI Soc. 1988, 2, 209–233. [Google Scholar] [CrossRef]
- de Campos Souza, P.V.; Guimaraes, A.J.; Araújo, V.S.; Rezende, T.S.; Araújo, V.J.S. Fuzzy Neural Networks based on Fuzzy Logic Neurons Regularized by Resampling Techniques and Regularization Theory for Regression Problems. Intel. Artif. 2018, 21, 114–133. [Google Scholar] [CrossRef][Green Version]
- Han, M.; Zhong, K.; Qiu, T.; Han, B. Interval Type-2 Fuzzy Neural Networks for Chaotic Time Series Prediction: A Concise Overview. IEEE Trans. Cybern. 2018, 49, 2720–2731. [Google Scholar] [CrossRef]
- de Campos Souza, P.V.; Torres, L.C.B. Regularized fuzzy neural network based on or neuron for time series forecasting. In Proceedings of the North American Fuzzy Information Processing Society Annual Conference, Fortaleza, Brazil, 4–6 July 2018; pp. 13–23. [Google Scholar]
- d. C. Souza, P.V.; Guimares, A.J.; Rezende, T.S.; Araujo, V.S.; Araujo, V.J.S.; Batista, L.O. Bayesian Fuzzy Clustering neural network for regression problems. In Proceedings of the 2019 IEEE International Conference on Systems, Man and Cybernetics (SMC), Bari, Italy, 6–9 October 2019; pp. 1492–1499. [Google Scholar] [CrossRef]
- Guimarães, A.J.; Araújo, V.J.; de Oliveira Batista, L.; Souza, P.V.C.; Araújo, V.; Rezende, T.S. Using Fuzzy Neural Networks to Improve Prediction of Expert Systems for Detection of Breast Cancer. In Anais do XV Encontro Nacional de Inteligência Artificial e Computacional; SBC: Porto Alegre, Brasil, 2018; pp. 799–810. [Google Scholar] [CrossRef]
- Silva Araújo, V.J.; Guimarães, A.J.; de Campos Souza, P.V.; Silva Rezende, T.; Souza Araújo, V. Using resistin, glucose, age and bmi and pruning fuzzy neural network for the construction of expert systems in the prediction of breast cancer. Mach. Learn. Knowl. Extr. 2019, 1, 466–482. [Google Scholar] [CrossRef]
- de Campos Souza, P.V.; Guimaraes, A.J. Using fuzzy neural networks for improving the prediction of children with autism through mobile devices. In Proceedings of the 2018 IEEE Symposium on Computers and Communications (ISCC), Natal, Brazil, 25–28 June 2018; pp. 01086–01089. [Google Scholar]
- Guimarães, A.J.; Araujo, V.J.S.; de Campos Souza, P.V.; Araujo, V.S.; Rezende, T.S. Using Fuzzy Neural Networks to the Prediction of Improvement in Expert Systems for Treatment of Immunotherapy. In Proceedings of the Ibero-American Conference on Artificial Intelligence, Trujillo, Peru, 13–16 November 2018; pp. 229–240. [Google Scholar]
- Camci, E.; Kripalani, D.R.; Ma, L.; Kayacan, E.; Khanesar, M.A. An aerial robot for rice farm quality inspection with type-2 fuzzy neural networks tuned by particle swarm optimization-sliding mode control hybrid algorithm. Swarm Evol. Comput. 2018, 41, 1–8. [Google Scholar] [CrossRef]
- Souza, P.V.d.C.; Guimaraes, A.J.; Araujo, V.S.; Rezende, T.S.; Araujo, V.J.S. Regularized Fuzzy Neural Networks to Aid Effort Forecasting in the Construction and Software Development. arXiv 2018, arXiv:1812.01351. [Google Scholar]
- Souza, P.V.C.; dos Reis, A.G.; Marques, G.R.R.; Guimaraes, A.J.; Araujo, V.J.S.; Araujo, V.S.; Rezende, T.S.; Batista, L.O.; da Silva, G.A. Using hybrid systems in the construction of expert systems in the identification of cognitive and motor problems in children and young people. In Proceedings of the 2019 IEEE International Conference on Fuzzy Systems (FUZZ-IEEE), New Orleans, LA, USA, 23–26 June 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Araujo, V.S.; Rezende, T.S.; Guimarães, A.J.; Araujo, V.J.S.; de Campos Souza, P.V. A hybrid approach of intelligent systems to help predict absenteeism at work in companies. SN Appl. Sci. 2019, 1, 536. [Google Scholar] [CrossRef]
- Hirota, K.; Pedrycz, W. OR/AND neuron in modeling fuzzy set connectives. IEEE Trans. Fuzzy Syst. 1994, 2, 151–161. [Google Scholar] [CrossRef]
- de Campos Souza, P.V.; Silva, G.R.L.; Torres, L.C.B. Uninorm based regularized fuzzy neural networks. In Proceedings of the 2018 IEEE Conference on Evolving and Adaptive Intelligent Systems (EAIS), Rhodes, Greece, 25–27 May 2018; pp. 1–8. [Google Scholar]
- Nair, V.; Hinton, G.E. Rectified linear units improve restricted boltzmann machines. In Proceedings of the 27th International Conference on Machine Learning (ICML-10), Haifa, Israel, 21–24 June 2010; pp. 807–814. [Google Scholar]
- Pedrycz, W. Neurocomputations in relational systems. IEEE Trans. Pattern Anal. Mach. Intell. 1991, 13, 289–297. [Google Scholar] [CrossRef]
- Yager, R.R.; Rybalov, A. Uninorm aggregation operators. Fuzzy Sets Syst. 1996, 80, 111–120. [Google Scholar] [CrossRef]
- Lemos, A.P.; Caminhas, W.; Gomide, F. A fast learning algorithm for uninorm-based fuzzy neural networks. In Proceedings of the 2012 Annual Meeting of the North American Fuzzy Information Processing Society (NAFIPS), Berkeley, CA, USA, 6–8 August 2012; pp. 1–6. [Google Scholar]
- Rosa, R.; Gomide, F.; Ballini, R. Evolving hybrid neural fuzzy network for system modeling and time series forecasting. In Proceedings of the 2013 12th International Conference on Machine Learning and Applications, Miami, FL, USA, 4–7 December 2013; Volume 2, pp. 378–383. [Google Scholar]
- Wang, L.X.; Mendel, J.M. Generating fuzzy rules by learning from examples. IEEE Trans. Syst. Man, Cybern. 1992, 22, 1414–1427. [Google Scholar] [CrossRef]
- Albert, A. Regression and the Moore-Penrose Pseudoinverse; Elsevier: Amsterdam, The Netherlands, 1972. [Google Scholar]
- Yamanishi, K.; Takeuchi, J.I.; Williams, G.; Milne, P. On-line unsupervised outlier detection using finite mixtures with discounting learning algorithms. Data Min. Knowl. Discov. 2004, 8, 275–300. [Google Scholar] [CrossRef]
- Williams, G.; Baxter, R.; He, H.; Hawkins, S.; Gu, L. A comparative study of RNN for outlier detection in data mining. In Proceedings of the 2002 IEEE International Conference on Data Mining, Maebashi City, Japan, 9–12 December 2002; pp. 709–712. [Google Scholar]
- Liu, F.T.; Ting, K.M.; Zhou, Z.H. Isolation forest. In Proceedings of the 2008 Eighth IEEE International Conference on Data Mining, Pisa, Italy, 15–19 December 2008; pp. 413–422. [Google Scholar]
- Ting, K.; Tan, S.; Liu, F. Mass: A New Ranking Measure for Anomaly Detection; Monash University: Melbourne, Australia, 2009. [Google Scholar]
- Ting, K.M.; Zhou, G.T.; Liu, F.T.; Tan, J.S.C. Mass estimation and its applications. In Proceedings of the 16th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Washington, DC, USA, 24–28 July 2010; pp. 989–998. [Google Scholar]
- Tan, S.C.; Ting, K.M.; Liu, T.F. Fast anomaly detection for streaming data. In Proceedings of the IJCAI Proceedings-International Joint Conference on Artificial Intelligence, Barcelona, Spain, 16–22 July 2011; Volume 22, p. 1511. [Google Scholar]
- Hall, M.; Frank, E.; Holmes, G.; Pfahringer, B.; Reutemann, P.; Witten, I.H. The WEKA Data Mining Software: An Update. SIGKDD Explor. 2009, 11, 10–18. [Google Scholar] [CrossRef]
- Rumelhart, D.E.; Hinton, G.E.; Williams, R.J. Learning Internal Representations by Error Propagation; Technical Report; California Univ San Diego La Jolla Inst for Cognitive Science: La Jolla, CA, USA, 1985. [Google Scholar]
- Lewis, D.D. Naive (Bayes) at forty: The independence assumption in information retrieval. In Proceeedings of the European Conference on Machine Learning, Chemnitz, Germany, 21–23 April 1998; pp. 4–15. [Google Scholar]
- Aldous, D. The continuum random tree III. Ann. Probab. 1993, 21, 248–289. [Google Scholar] [CrossRef]
- Cortes, C.; Vapnik, V. Support-vector networks. Mach. Learn. 1995, 20, 273–297. [Google Scholar] [CrossRef]
- de Campos Souza, P.V.; Guimaraes, A.J.; Araujo, V.S.; Rezende, T.S.; Araujo, V.J.S. Incremental regularized Data Density-Based Clustering neural networks to aid in the construction of effort forecasting systems in software development. Appl. Intell. 2019, 49, 3221–3234. [Google Scholar] [CrossRef]
- de Campos Souza, P.V.; Guimaraes Nunes, C.F.; Guimares, A.J.; Silva Rezende, T.; Araujo, V.S.; Silva Arajuo, V.J. Self-organized direction aware for regularized fuzzy neural networks. Evol. Syst. 2019. [Google Scholar] [CrossRef]
- Rupa Devi, T.; Badugu, S. A Review on Network Intrusion Detection System Using Machine Learning. In Advances in Decision Sciences, Image Processing, Security and Computer Vision; Satapathy, S.C., Raju, K.S., Shyamala, K., Krishna, D.R., Favorskaya, M.N., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 598–607. [Google Scholar]

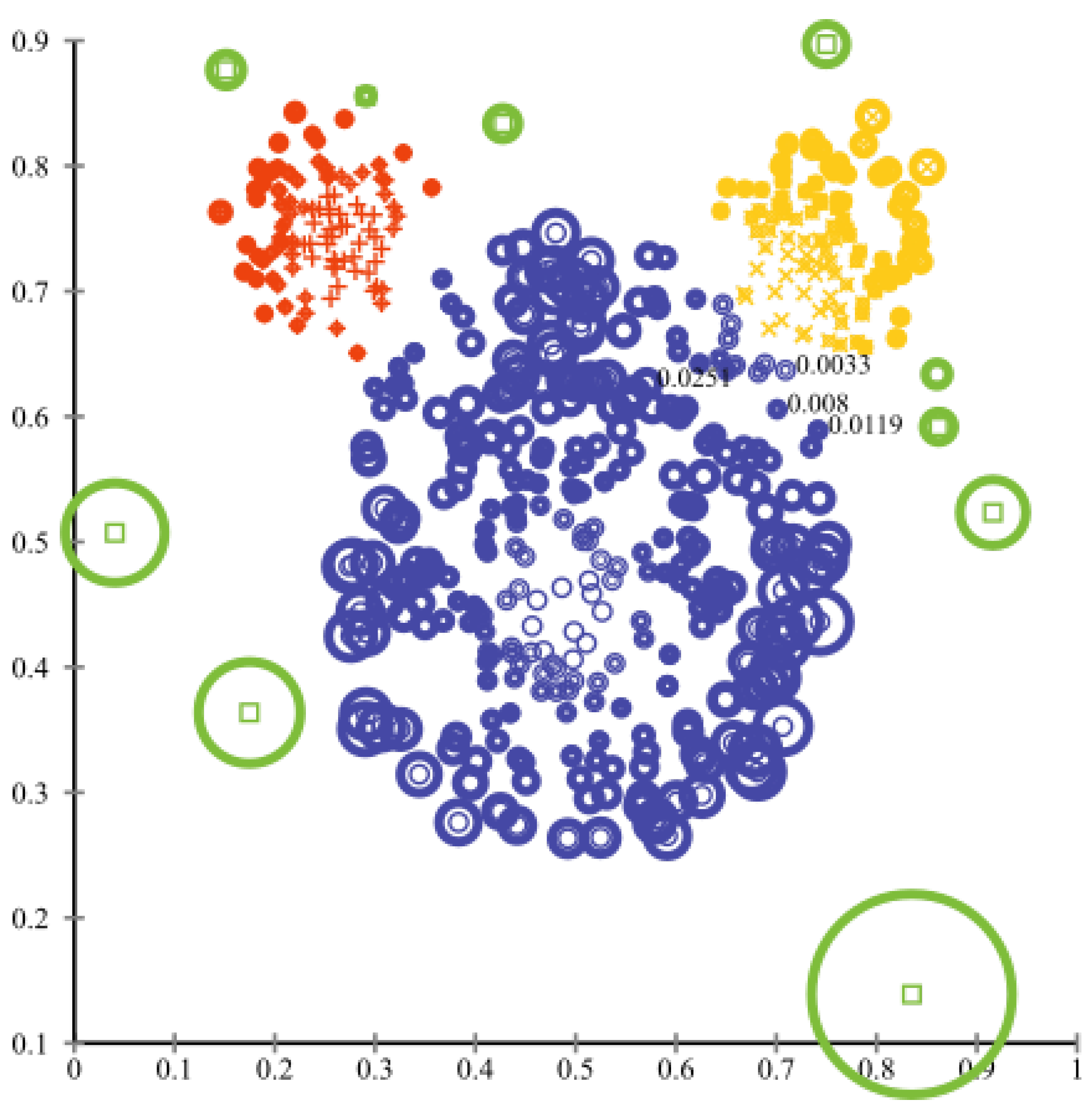

| Model | Training | Sensitivity | Specificity | AUC | Test | Training and Test Time | |
|---|---|---|---|---|---|---|---|
| FNN | 99.99 (0.01) | 27 (0.00) | 100 (0.00) | 98.81 (0.35) | 99.90 (0.01) | 98.76 (1.67) | 2140.35 (59.02) |
| SFNN | 98.18 (0.01) | 27 (0.00) | 99.92 (0.00) | 98.14 (0.16) | 99.03 (0.01) | 97.25 (0.42) | 162.31 (14.27) |
| EFNN | 96.18 (0.16) | 12.25 (4.07) | 94.65 (0.29) | 94.33 (0.19) | 94.49 (0.20) | 95.99 (0.84) | 512.25 (21.17) |
| IFNN | 97.99 (0.17) | 28.68 (6.67) | 100 (0.00) | 97.89 (0.15) | 98.94 (0.02) | 96.76 (2.47) | 1587.78 (28.02) |
| MLP | 98.78 (0.00) | 28.14 (0.78) | 100 (0.00) | 94.81 (1.35) | 97.41 (0.46) | 98.16 (1.67) | 2090.13 (71.02) |
| NB | 97.45 (0.35) | 8.64 (0.14) | 98.87 (0.05) | 97.15 (0.75) | 98.01 (0.12) | 96.54 (2.05) | 67.45 (15.53) |
| RT | 98.02 (0.14) | 32.00 (2.41) | 97.87 (0.54) | 96.81 (0.35) | 97.34 (0.87) | 97.34 (1.54) | 134.36 (12.52) |
| SVM | 99.15 (0.01) | 56.98 (6.87) | 98.14 (0.25) | 92.17 (0.76) | 95.15 (0.53) | 98.29 (1.54) | 434.36 (65.67) |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
de Campos Souza, P.V.; Guimarães, A.J.; Rezende, T.S.; Silva Araujo, V.J.; Araujo, V.S. Detection of Anomalies in Large-Scale Cyberattacks Using Fuzzy Neural Networks. AI 2020, 1, 92-116. https://doi.org/10.3390/ai1010005
de Campos Souza PV, Guimarães AJ, Rezende TS, Silva Araujo VJ, Araujo VS. Detection of Anomalies in Large-Scale Cyberattacks Using Fuzzy Neural Networks. AI. 2020; 1(1):92-116. https://doi.org/10.3390/ai1010005
Chicago/Turabian Stylede Campos Souza, Paulo Vitor, Augusto Junio Guimarães, Thiago Silva Rezende, Vinicius Jonathan Silva Araujo, and Vanessa Souza Araujo. 2020. "Detection of Anomalies in Large-Scale Cyberattacks Using Fuzzy Neural Networks" AI 1, no. 1: 92-116. https://doi.org/10.3390/ai1010005
APA Stylede Campos Souza, P. V., Guimarães, A. J., Rezende, T. S., Silva Araujo, V. J., & Araujo, V. S. (2020). Detection of Anomalies in Large-Scale Cyberattacks Using Fuzzy Neural Networks. AI, 1(1), 92-116. https://doi.org/10.3390/ai1010005






