Can Ternary Computing Improve Information Assurance?
Abstract
:1. Introduction
2. Limitations of Current Security Protocols
2.1. Threats in the Cyber-Space
- Malware, worms, and viruses inserted by malicious entities. These threats can be dormant for years, but when activated, cause large scale damage;
- Breaches in access control due to password guessing, identity theft, insider and side channel attacks, and exposure of user account databases. Such breaches can result in illegitimate user access;
- Eavesdropping by listening over open network connections. This can compromise the integrity of the networks, confidential files, passwords, and other personal and corporate information;
- Man-in-the-middle attacks and war dialing, in which malicious agents pretend to be legitimate actors, and acquire information that can enable the exploitation of vulnerabilities;
- Protocol-based attacks, which can occur when the attacker has access to partial knowledge of security protocols. This can include host attacks, which exploit vulnerabilities of CPSs and their operating systems;
- Distributed denial-of-service (DDoS) attacks having with the objective to of overwhelming the communication between hosts and client devices. Often the constellation of IoTs does not have enough embedded security.
2.2. Risk Mitigation
3. Ternary Computing
3.1. Brief History of Ternary Computing
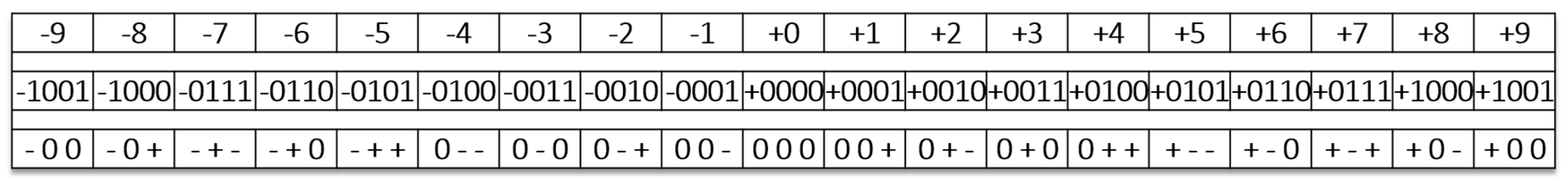
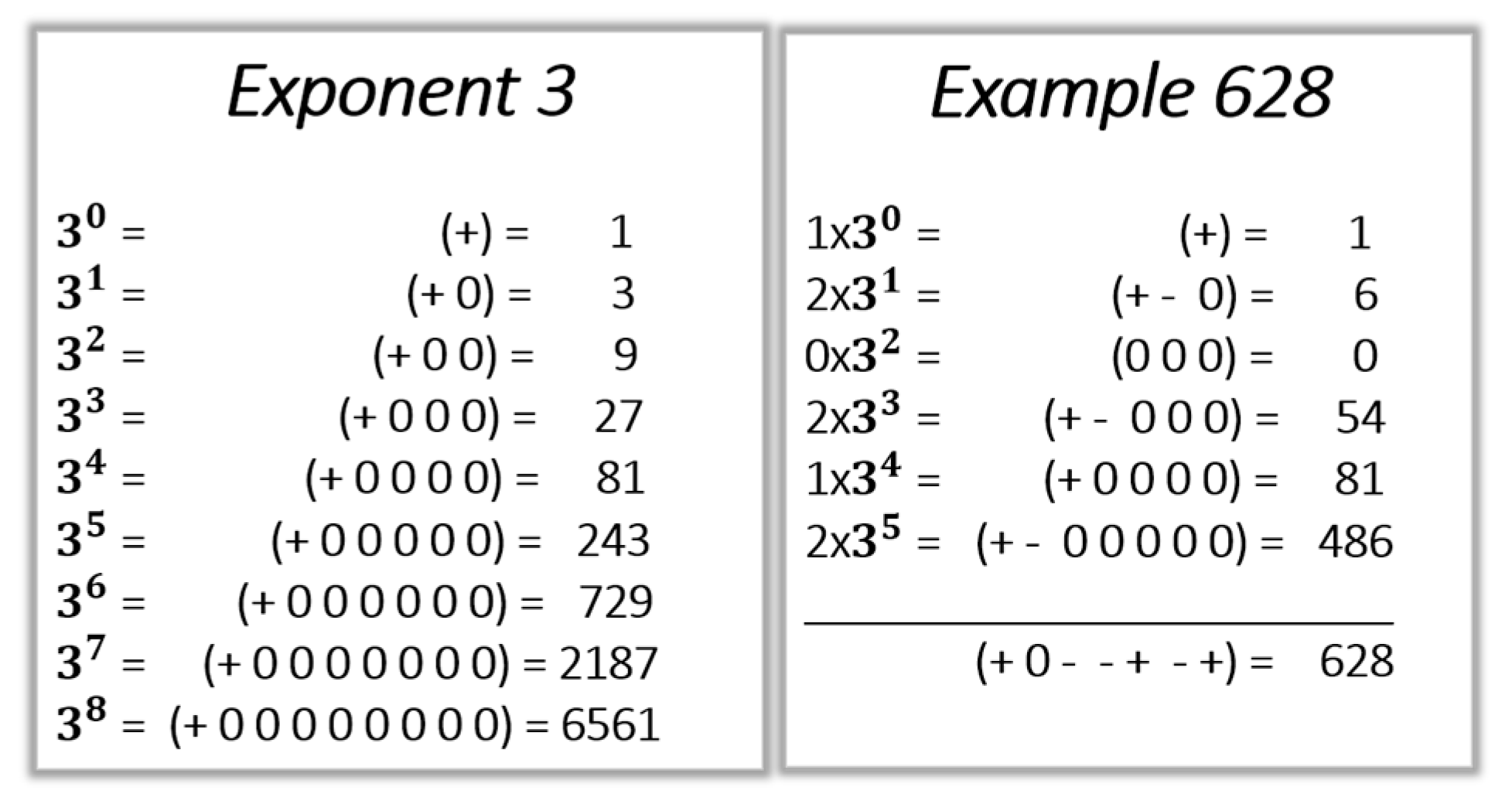
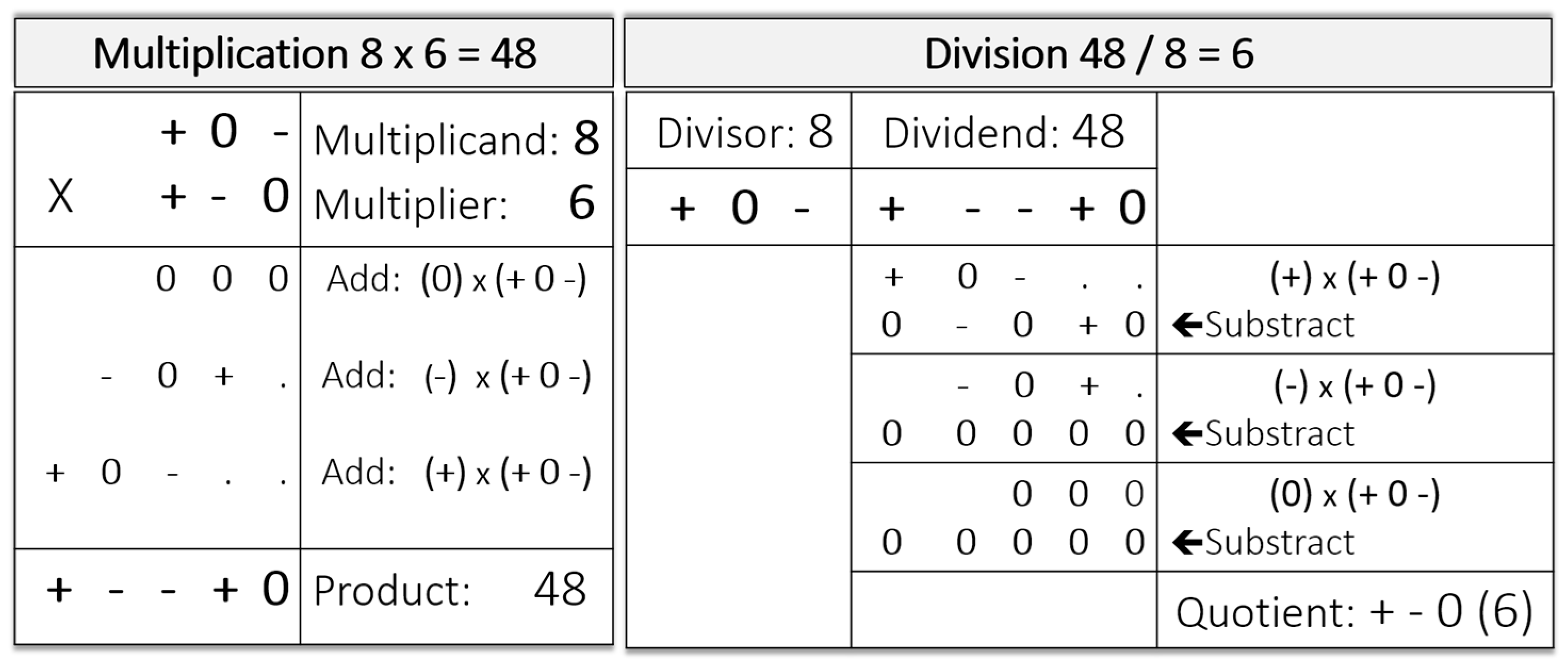
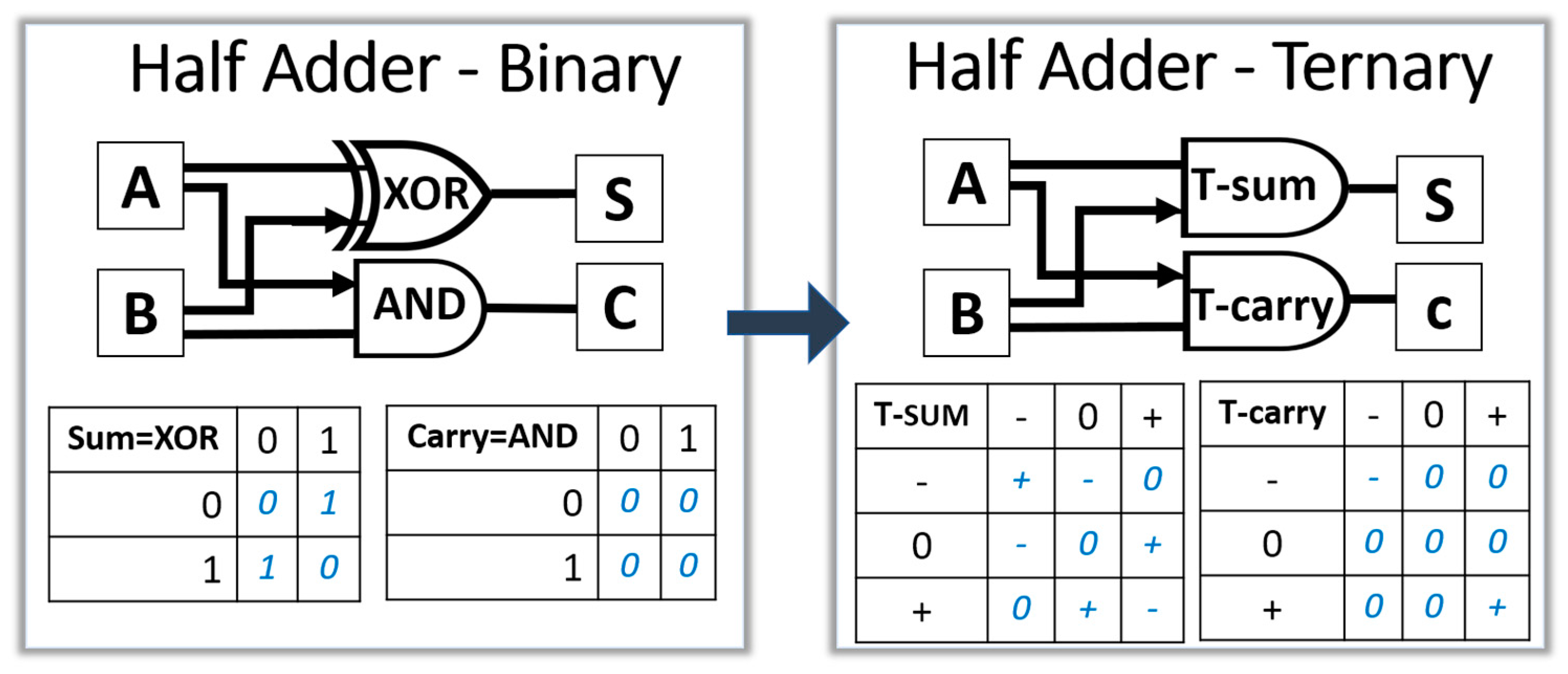
3.2. Ternary Arithmetic
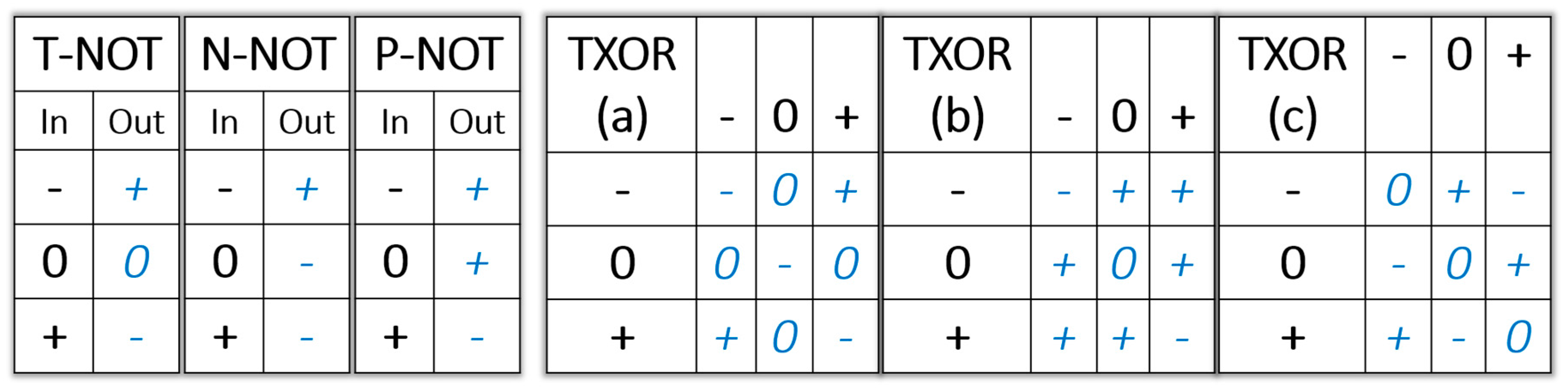
3.3. Ternary Boolean Logic
3.4. Microelectronics for Ternary Computers
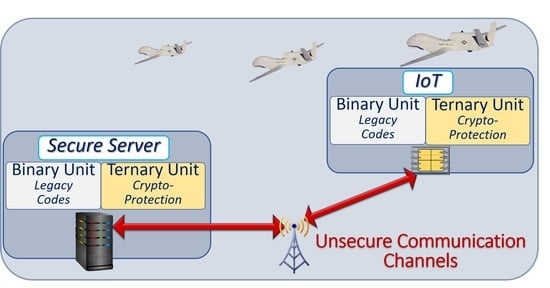
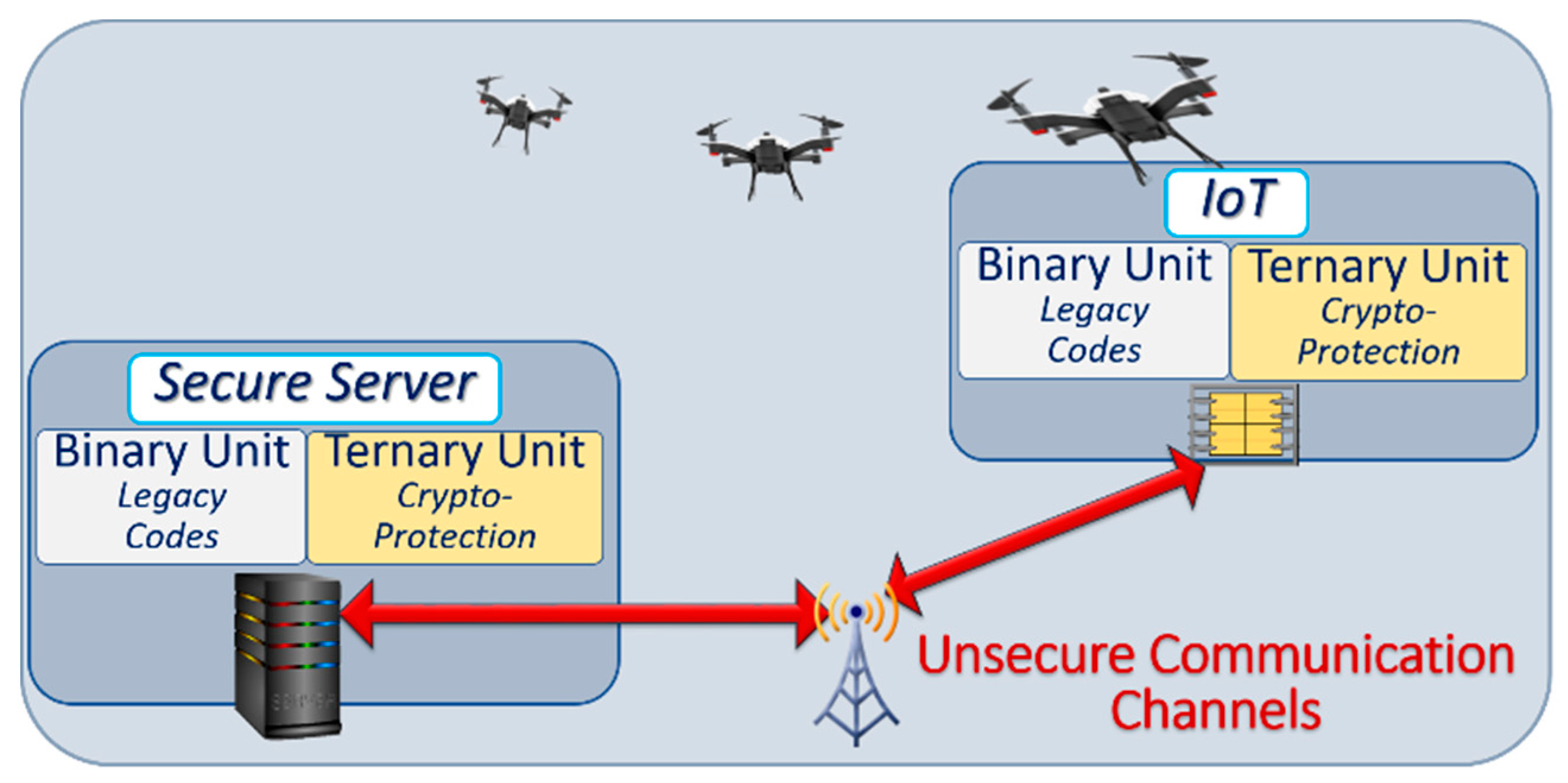
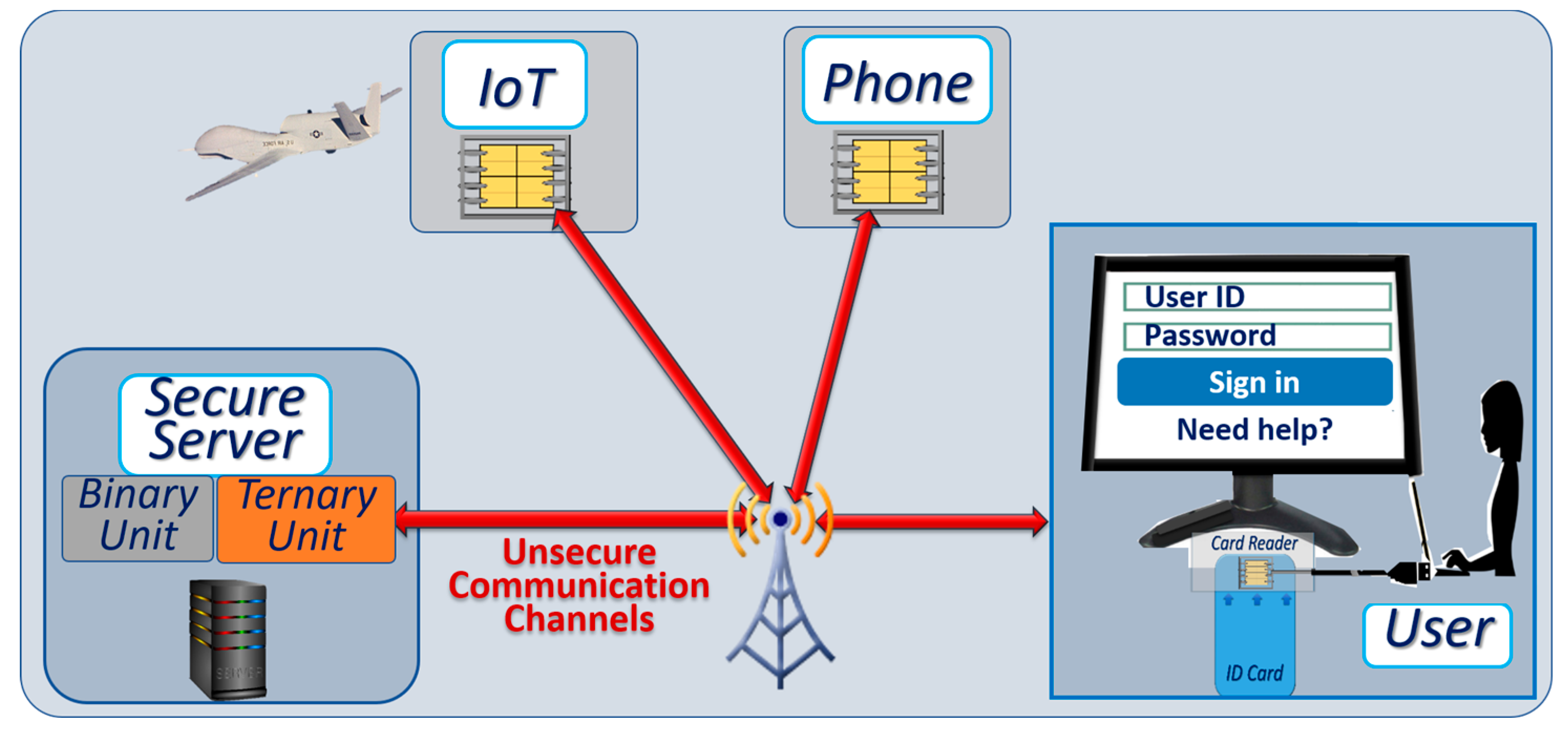
4. Securing Client Devices
- ○
- Communication busses and peripherals are used such that ternary systems may integrate with binary systems.
- ○
- All communicating parties are equipped with low cost secure microcontrollers with at least one ternary computing unit, one binary computing unit, and secure embedded memories.
- ○
- Cryptographic protocols are based on native ternary logic for access control, including dynamically changing sets of passwords for access control with public–private key exchanges, and dynamically changing sets of ternary instructions that implement native ternary functions;
- ○
- Secure ternary memory to store cryptographic tables;
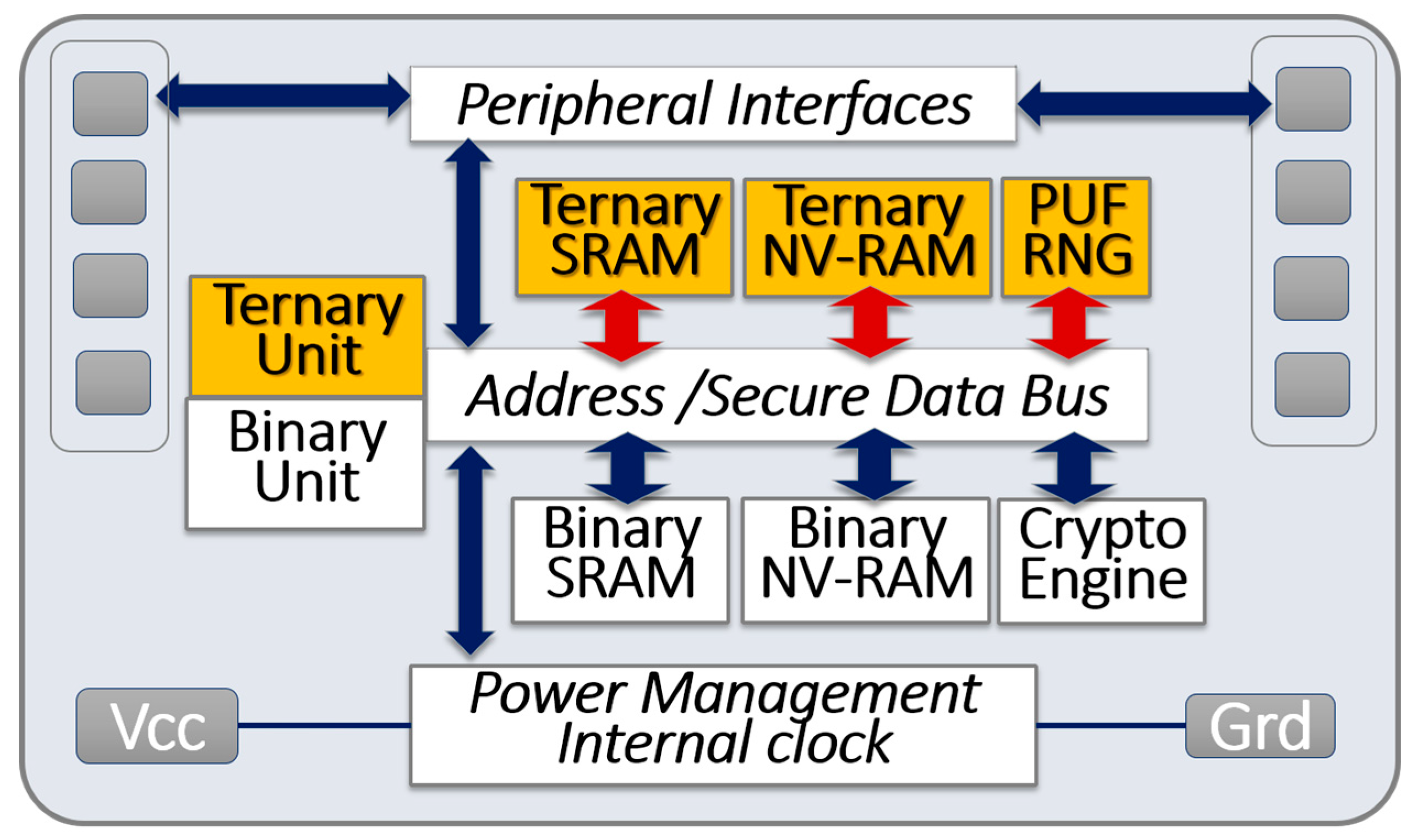
4.1. Heterogeneous Secure Microcontrollers
4.2. Cryptography with Ternary Tables
- ○
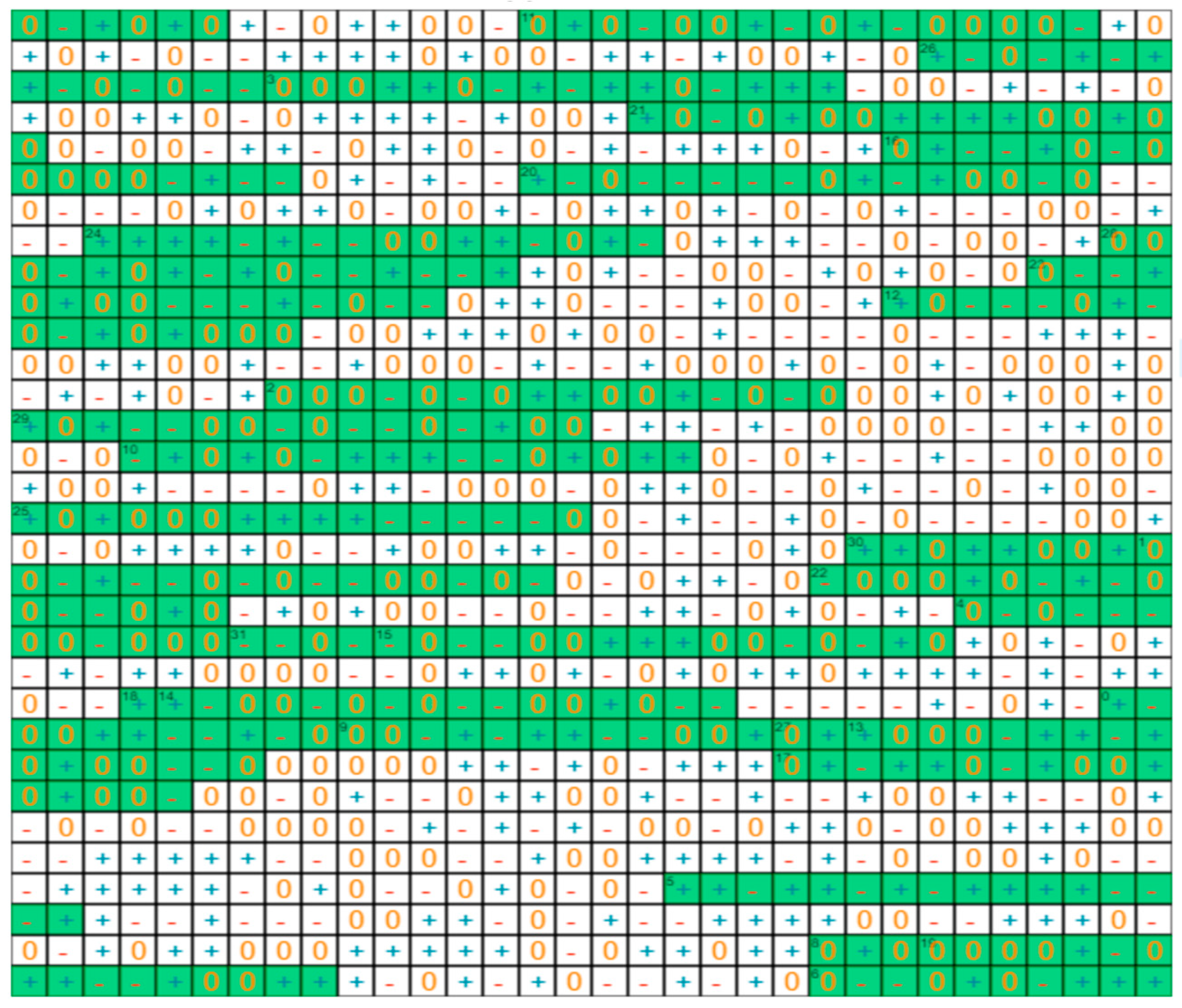
- The first portion of the public key is a stream of 512 bits, hexadecimal in the table.
- ○
- A hash message digest is generated from this key with SHA-2; 32 different addresses are generated from the message digest, and 16 trits are extracted at each address, in green in Figure 10.
- ○
- The mask is created with the knowledge of the location of the cells storing ternary state “0s” [48].
- ○
- The private key is generated by selecting only the “−” and “+”, as shown in green in Figure 11, and converting them to binary 0s and 1s.
- ○
- The public key is the combination of the initial random number and the mask XORed with the message digest.
- ○
- The client device with the same cryptographic table, and public key is in the same state and will generate the same private key.
- ○
- Public keys can be changed at every communication to become one-time use only;
- ○
- Hash functions can be combined with multi-factor authentication to protect the public keys;
- ○
- Masking operations prevent third parties from randomly generating private keys;
- ○
- Power consumption and computing times are low and compatible with low cost IoT networks.
4.3. Ternary Physically Unclonable Functions
4.4. Development of Ternary Computing Units
4.5. System Implementation of Ternary Computing
5. Conclusions and Future Work
- ○
- Malware, viruses and worms will not affect the ternary unit unless the malware is converted to native ternary logic. Continuously changing sets of ternary instructions on each machine, based on public key exchanges, are expected to make conversions between binary and ternary non-trivial;
- ○
- Breaches in access control will be reduced with the ternary PKD proposed here with the one-time public/private key pair minimizing the impact of a potential loss of the keys. The use of multi-factor authentication with subject–object pairing and passwords is suggested;
- ○
- Eavesdropping problems will be greatly reduced because all aspects of the ternary architecture can change constantly, such as the keys, the set of ternary instructions, and the authentication messages.
Acknowledgments
Author Contributions
Conflicts of Interest
Disclaimer
References
- Kamara, S.; Fahmy, S.; Schultz, E.; Kerschbaum, F.; Frantzen, M. Analysis of Vulnerabilities in the Internet Firewall. Comput. Secur. 2003, 22, 214–232. [Google Scholar] [CrossRef]
- Liu, A.X.; Gouda, M.G. Diverse Firewall Designs. IEEE Trans. Parallel Distrib. Syst. 2008, 19, 1237–1251. [Google Scholar] [CrossRef]
- Yuan, L.; Chen, H.; Mai, J.; Chua, C.N.; Su, Z.; Mohapatra, P. Fireman: A Tool Kit for Firewall Modelling and Analysis. In Proceedings of the 2006 IEEE Symposium on Security and Privacy, Berkeley/Oakland, CA, USA, 21–24 May 2006. [Google Scholar]
- Kumar, R.; Talwar, I.M. Network Security using Firewall and Cryptographic Authentication. Int. J. Comput. Appl. 2012, 57, 13–19. [Google Scholar] [CrossRef]
- Dua, S.; Du, X. Data Mining and Machine Learning in Cybersecurity; CRC Press of Taylor & Francis Group: Boca Raton, FL, USA, 2016. [Google Scholar]
- Buczak, A.; Guven, E. A Survey of Data Mining and Machine Learning Methods for Cybersecurity Intrusion Detection. IEEE Commun. Surv. Tutor. 2016, 18, 1153–1176. [Google Scholar] [CrossRef]
- Borgesltink, R.C.; Beaver, J.M.; Buckner, M.; Morris, T.; Adhikari, U.; Pan, S. Machine Learning for Power Systems Disturbance and Cyberattacks Discrimination. In Proceedings of the 7th International Symposium on Resilient Controls and Systems (ISRCS), Denver, CO, USA, 19–21 August 2014. [Google Scholar]
- Shiva, S.; Roy, S.; Dasgupta, D. Game Theory for Cybersecurity. In Proceedings of the 6th Annual Workshop on Cybersecurity and Information Intelligence Research, Oak Ridge, TN, USA, 21–23 April 2010. [Google Scholar]
- Linda, M.; Vollmer, T.; Wright, J. Fuzzy Logic Based Anomaly Detection for Embedded Network Security Cyber Sensor. In Proceedings of the IEEE Symposium on Computational Intelligence in Cyber Security (CICS), Paris, France, 11–15 April 2011. [Google Scholar]
- Elovici, Y.; Shabtai, A.; Moskovitch, R.; Tahan, G.; Glezer, C. Applying Machine Learning Technique for Detection of Malicious Code in Network Traffic. In Proceedings of the IEEE Symposium on Annual Conference on Artificial Intelligence, Alcala de Henares, Spain, 3–5 October 2007. [Google Scholar]
- Gandrotra, E.; Bansal, D.; Sofat, S. Malware Analysis and Classification—A survey. J. Inf. Secur. 2014, 5, 56–64. [Google Scholar]
- Cambou, B.; Afghah, F. PUF with Multi-states and Machine Learning. In Proceeding of the CryptArchi, La Grande Motte, France, 21–24 June 2016. [Google Scholar]
- Glusker, M.; Hogan, D.M.; Vass, P. The ternary calculating machine of Thomas Fowler. IEEE Ann. Hist. Comput. 2005, 27, 4–22. [Google Scholar] [CrossRef]
- Obiniyi, A.A.; Absalom, E.E.; Adako, K. Arithmetic Logic Design with Color Coded Ternary for Ternary Computing. Int. J. Comput. Appl. 2011, 26, 31–37. [Google Scholar]
- Brousentov, N.P.; Maslov, S.P.; Alvarez, J.R.; Zhogolev, E.A. Development of Ternary Computers at Moscow State University; Russian Virtual Computer Museum: Moscow, Russian, 2002. [Google Scholar]
- Dijkstra, E.W. Notes on Structured Programming; EWD 249 Technical University: Eindhoven, The Netherlands, 1969. [Google Scholar]
- Frieder, G. Ternary Computers, part 1: Motivation for ternary computers. In Proceedings of the Micro 5 Conference Record of the 5th Annual Workshop on Microprogramming, Urbana, IL, USA, 25–26 September 1972. [Google Scholar]
- Zadeh, L.A. Fuzzy algorithms. Inf. Control 1968, 12, 94–102. [Google Scholar] [CrossRef]
- Shor, P. Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer. J. Soc. Ind. Appl. Math. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Caraiman, S.; Manta, V. Image Representation and Processing Using Ternary Quantum Computing. In ICANNGA 2013; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2013; Volume 7824. [Google Scholar]
- Cambou, B. Multi-Factor Authentication Using a Combined Secure Pattern. U.S. Patent 9,514,292, 16 July 2015. [Google Scholar]
- Cambou, B.; Orlowski, M. Design of PUFs with ReRAM and ternary states. In Proceedings of the 11th Annual Cyber and Information Security Research Conference, Oak Ridge, TN, USA, 5–7 April 2016. [Google Scholar]
- Cambou, B. PUF Generating Systems and Related Methods. U.S. Patent Disclosure No. 62/204912, 13 August 2015. [Google Scholar]
- Cambou, B. A XOR data compiler combined with PUF for TRNG. In Proceedings of the SAI/IEEE Computing Conference, London, UK, 18–20 July 2017. [Google Scholar]
- Gundersen, H. Aspect of Balanced Ternary Arithmetic Implemented Using CMOS Recharged Semi-Floating Gate Device. Ph.D. Thesis, Oslo University, Oslo, Norway, 2008. [Google Scholar]
- Profeanu, I. A ternary Arithmetic and Logic. In Proceedings of the World Congress on Engineering, London, UK, 30 June–2 July 2010. [Google Scholar]
- Ahmad, S.; Alam, M. Balanced Ternary Logic For improving Computing. Int. J. Comput. Sci. Inf. Technol. 2014, 5, 5157. [Google Scholar]
- Wu, X.W. CMOS Ternary Logic Circuits. IEE Proc. 1990, 137, 21–27. [Google Scholar] [CrossRef]
- Srivastava, A.; Venkatapathy, K. Design and Implementation of a Low Power Ternary Full Adder. VLSI Des. 1996, 4, 75–81. [Google Scholar] [CrossRef]
- Balla, P.C.; Antoniou, A. Low Power Dissipation MOS Ternary Logic Family. IEEE J. Solid State Circ. 1984, 19, 739–749. [Google Scholar] [CrossRef]
- Miller, D.M.; Thornton, M.A. Multiple Valued Logic: Concepts and Representations; Synthesis Lectures on Digital Circuits and Systems; Morgan & Claypool Publishers: London, UK, 2007. [Google Scholar]
- Wanjari, N.P.; Hajare, S.P. VLSI Design and Implementation of Ternary Logic Gates and Ternary SRAM Cell. Int. J. Electron. Comput. 2013, 2, 610–618. [Google Scholar]
- Nagaraju, P.; Vishnuvardhan, N. Ternary Logic Gates and Ternary SRAM Implementation in VLSI. Int. J. Sci. Res. 2014, 3, 1920–1924. [Google Scholar]
- Bennett, S.; Sullivan, J. The Characterization of TLC NAND Flash Memory, Leading to a Definable Endurance/Retention Trade-Off. WASET Int. J. Ind. Manuf. Eng. 2016, 10, 716–723. [Google Scholar]
- Zhirnov, V.; Mikolajick, T. Chapter 26: Flash Memories; Nanoelectronics and Information Technology; Waser, R., Ed.; Wiley: Berlin, Germany, 2012. [Google Scholar]
- Schroder, U.; Schroder, H.; Kingon, A.I.; Bottger, U. Capacitor-Based Random-Access Memories; Nanoelectronics and Information Technology; Waser, R., Ed.; Wiley-Vch: Berlin, Germany, 2012; pp. 635–654. [Google Scholar]
- Chang, K.K.; Yağlıkçı, A.G.; Ghose, S.; Agrawal, A.; Chatterjee, N.; Kashyap, A.; Lee, D.; O’Connor, M.; Hassan, H.; Mutlu, O. Understanding Reduced-Voltage Operation in Modern DRAM Chips: Characterization, Analysis, and Mechanisms; Cornell Technical Library: Ithaca, NY, USA, 2017. [Google Scholar]
- Lin, S.; Kim, Y.-B.; Lombardi, F. CNTFET-Based Design of Ternary Logic Gates and Arithmetic Circuits. IEEE Trans. Nanotechnol. 2011, 10, 217–225. [Google Scholar] [CrossRef]
- Cambou, B. Multilevel Magnetic Element. U.S. Patent 8,630,112, 14 January 2014. [Google Scholar]
- Khalid, M.; Singh, J. Memristor based unbalanced ternary logic gates. Anal. Integr. Circ. Signal Proc. 2016, 87, 399–406. [Google Scholar] [CrossRef]
- Cambou, B. Enhancing Secure Elements—Technology and Architecture. In Foundations of Hardware IP Protection; Springer Int. Publishing: New York, NY, USA, 2017. [Google Scholar]
- Paar, C.; Pezl, J. Understanding Cryptography—A Text Book for Students and Practitioners; Springer: New York, NY, USA, 2011. [Google Scholar]
- Mel, H.X.; Baker, D. Cryptography Decrypted; Addison-Wesley: New York, NY, USA, 2001. [Google Scholar]
- Diffie, W.; Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Rivest, R.; Shamir, A.; Adleman, L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Pfleeger, C.P.; Pfleeger, S.L.; Margulies, J. Security in Computing, 5th ed.; Prentice Hall: Upper Saddle River, NJ, USA, 2015. [Google Scholar]
- Flikkema, P.G.; Cambou, B. Adapting Processor Architectures for the Periphery of the IoT Nervous System. In Proceedings of the IEEE 3rd World Forum on Internet of Things (WF-IoT), Reston, VA, USA, 12–14 December 2016. [Google Scholar]
- Cambou, B.; Chipana, R.; Habib, B. Securing PUFs with Additional Random Ternary States; NAU Disclosure D2017-19; Northern Arizona University: Flagstaff, AZ, USA, 2016. [Google Scholar]
- Jin, Y. Introduction to hardware security. Electronics 2015, 4, 763–784. [Google Scholar] [CrossRef]
- Prabhu, P.; Akel, A.; Grupp, L.M.; Yu, W.-K.S.; Suh, G.E.; Kan, E.; Swanson, S. Extracting Device Fingerprints from Flash Memory by Exploiting Physical Variations. In Proceedings of the 4th International Conference on Trust and Trustworthy Computing, Pittsburgh, PA, USA, 22–24 June 2011. [Google Scholar]
- Holcomb, D.E.; Burleson, W.P.; Fu, K. Power up SRAM state as an identifying Fingerprint and Source of True Random Numbers. IEEE Trans. Comput. 2009, 58, 1198–1210. [Google Scholar] [CrossRef]
- Chen, A. Comprehensive Assessment of RRAM-based PUF for Hardware Security Applications. In Proceedings of the 2015 IEEE International Electron Devices Meeting (IEDM), Washington, DC, USA, 7–9 December 2015. [Google Scholar]
- Beckmann, N.; Potkonjak, M. Hardware-Based Public-Key Cryptography with Public Physically Unclonable Functions. In Information Hiding; Springer: New York, NY, USA, 2009; pp. 206–220. [Google Scholar]
- Kang, H.; Hori, Y.; Katashita, T.; Hagiwara, M.; Iwamura, K. Cryptographic Key Generation from PUF Data Using Efficient Fuzzy Extractors. In Proceedings of the 2014 16th International Conference on Advanced Communication Technology (ICACT), Pyeongchang, South Korea, 16–19 February 2014; pp. 23–26. [Google Scholar]





© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cambou, B.; Flikkema, P.G.; Palmer, J.; Telesca, D.; Philabaum, C. Can Ternary Computing Improve Information Assurance? Cryptography 2018, 2, 6. https://doi.org/10.3390/cryptography2010006
Cambou B, Flikkema PG, Palmer J, Telesca D, Philabaum C. Can Ternary Computing Improve Information Assurance? Cryptography. 2018; 2(1):6. https://doi.org/10.3390/cryptography2010006
Chicago/Turabian StyleCambou, Bertrand, Paul G. Flikkema, James Palmer, Donald Telesca, and Christopher Philabaum. 2018. "Can Ternary Computing Improve Information Assurance?" Cryptography 2, no. 1: 6. https://doi.org/10.3390/cryptography2010006