Password-Hashing Status
Abstract
:1. Introduction
2. Background Theory
2.1. Passwords
2.2. PHS Security and Threat Model
- Preimage resistance,
- Second preimage resistance, and
- Collision resistance
- Input-dependent, input-independent, or hybrid memory addressing? In input-dependent indexing the timing information enables very fast password-searching and can be exploited by side-channel attacks. On the other hand, in input-independent indexing the read addresses in memory are known beforehand, deriving the time-space tradeoff attacks quite straightforward as the cracker can precompute the missing block when it is needed.
- Is it better to fortify the result by passing over the memory more times, or fill higher amounts of memory and being vulnerable to time-space tradeoffs? As there were no general tradeoff tools to analyze the two defence strategies against these vulnerabilities or unified metrics that could estimate the cost for an attacker, it was difficult to give a concrete answer.
- Which are the proper strategies to compute the input-independent addresses? Different approaches that were considered secure were eventually found vulnerable to attacks.
- What is the proper size for a single block of memory? The spacial locality of modern cache memories makes slower, in terms of cycles per byte, the reading of small and randomly-placed blocks. On the other hand, the small amount of available long registers derives inefficient the processing of larger blocks.
- Which are the features of the proper internal compression function when large blocks are used? Can lightweight functions that implement simple mixing being used or do we need cryptographically secure functions? Several of the candidate schemes simply adopted iterative constructions, contributing against the appliance of cryptographically secure compression functions.
- When multiple CPU cores are available, which is the proper strategy to utilize them? Parallel hash function invocations without any interaction can be exploited by simple tradeoff attacks.
2.3. Applications
3. Mainstream Password-Hashing Schemes
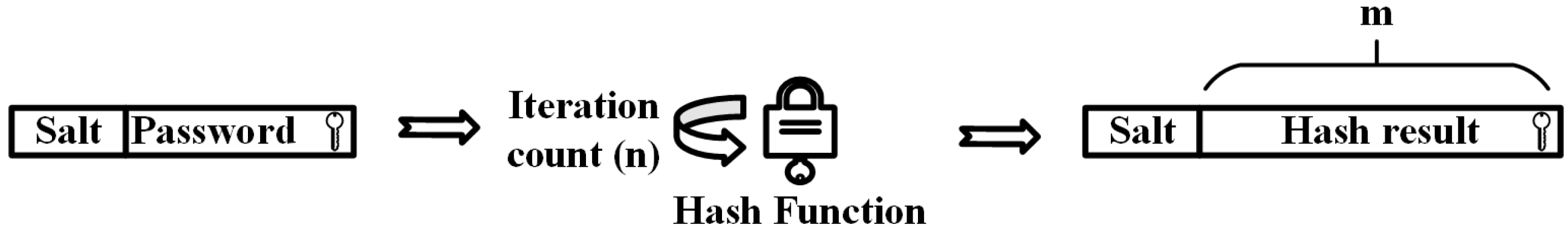
3.1. PBKDF2
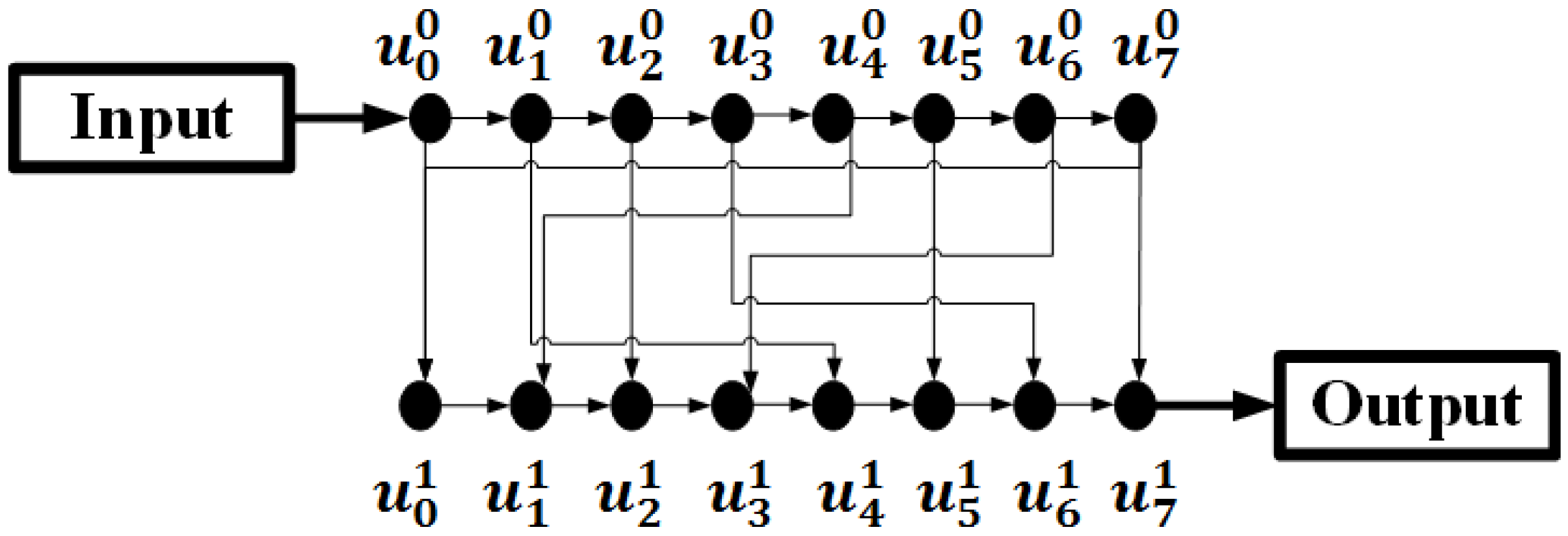
3.2. Bcrypt
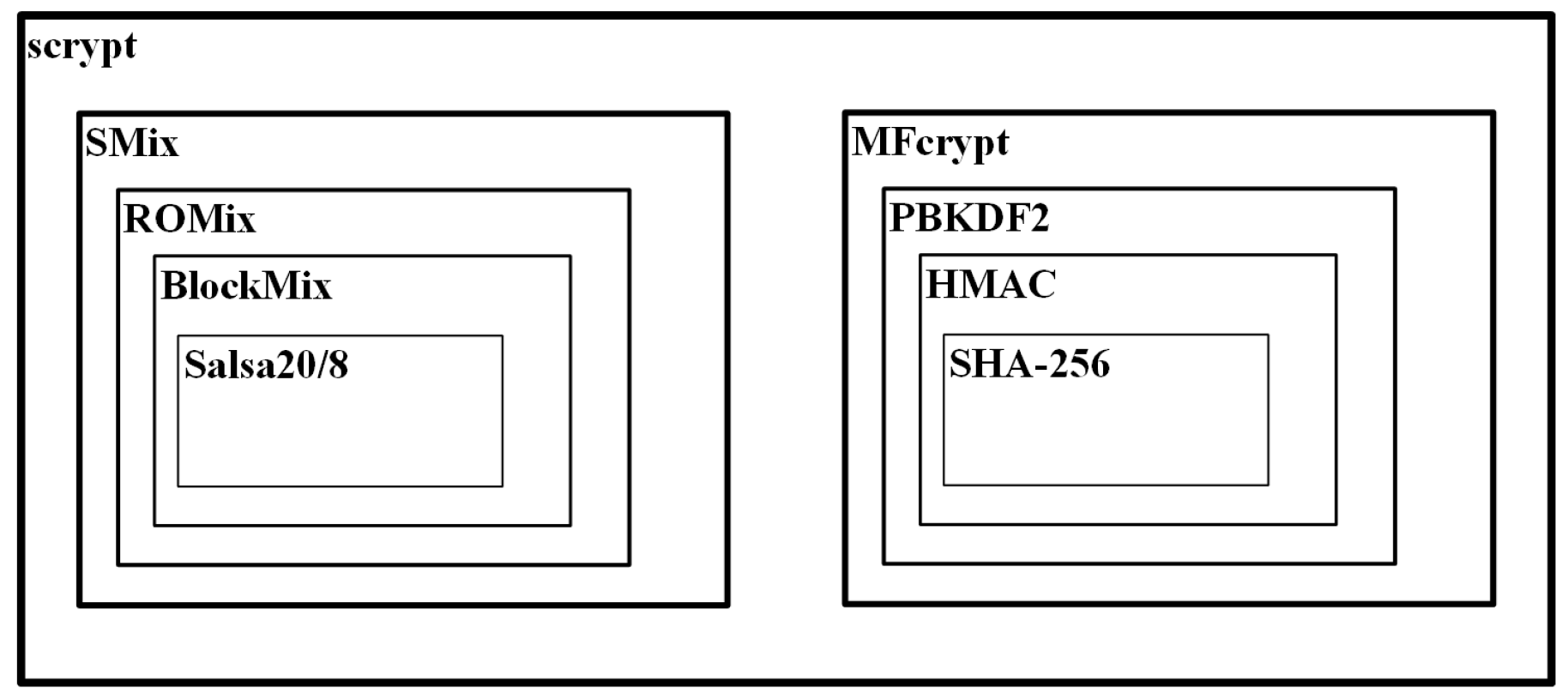
3.3. Scrypt
4. The Password Hashing Competition
- Passwords of any size between 0 and 128 bytes, regardless of the encoding
- Salt values of 16 bytes
- Output length of 32 bytes
- One or more cost parameters to configure time (t_cost) and/or memory demands (m_cost)
4.1. Evaluation Criteria
4.2. Finalists
4.2.1. Argon/Argon2
4.2.2. Battcrypt
4.2.3. Catena
4.2.4. Lyra2
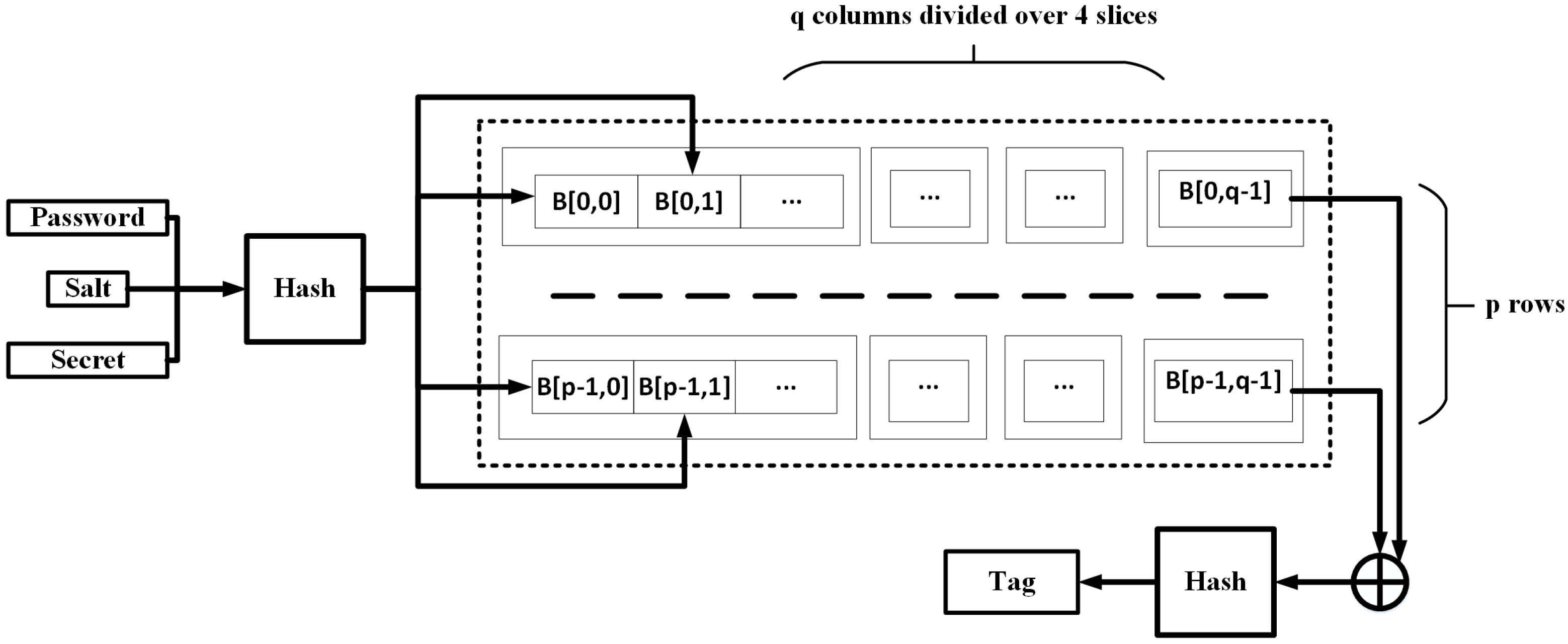
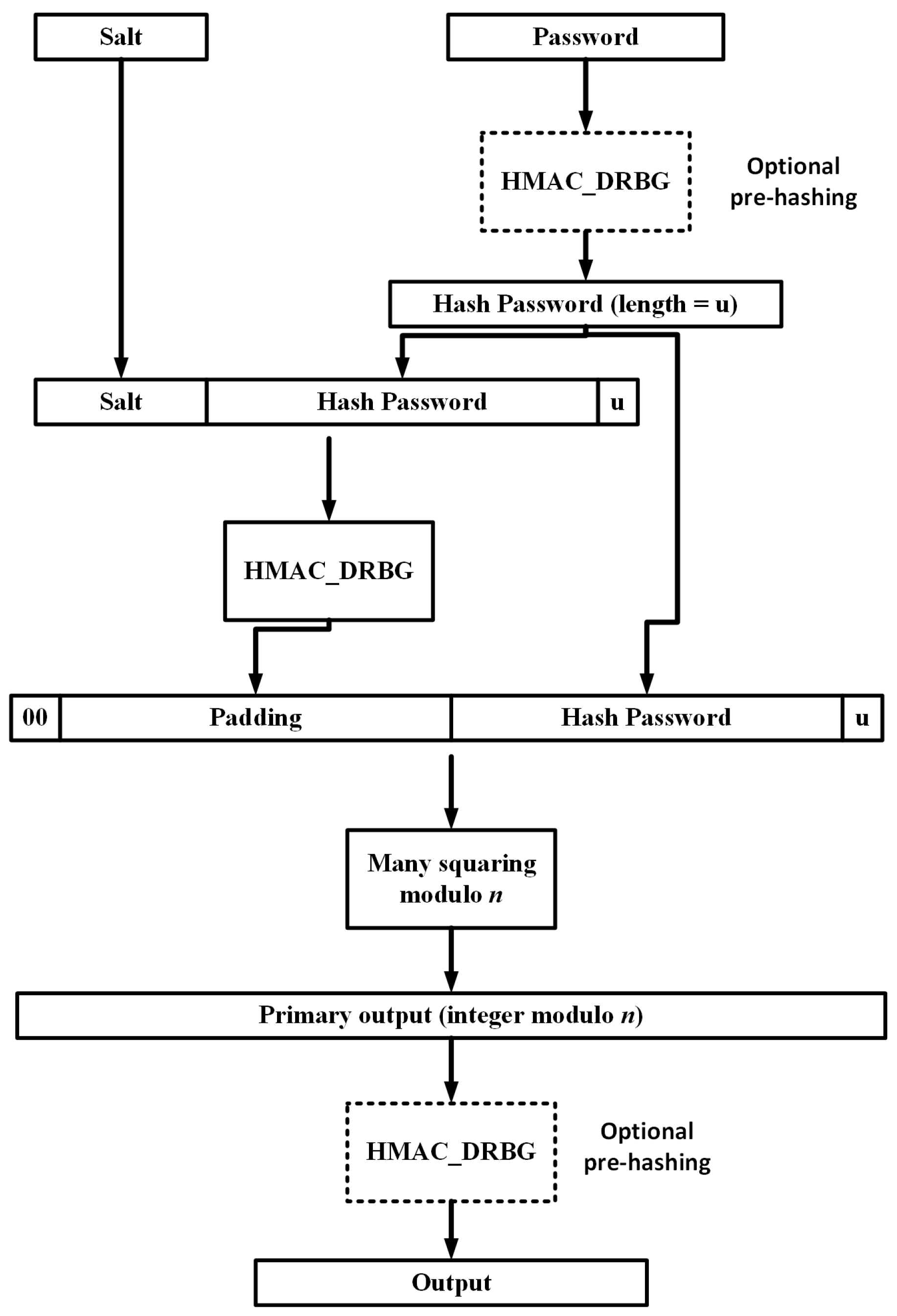
4.2.5. MAKWA
4.2.6. Parallel
4.2.7. POMELO
4.2.8. Pufferfish
4.2.9. Yescrypt
5. The Day after the PHC
5.1. Resistance to Parallel Cracking Attacks
5.2. Acceptability and Security Issues
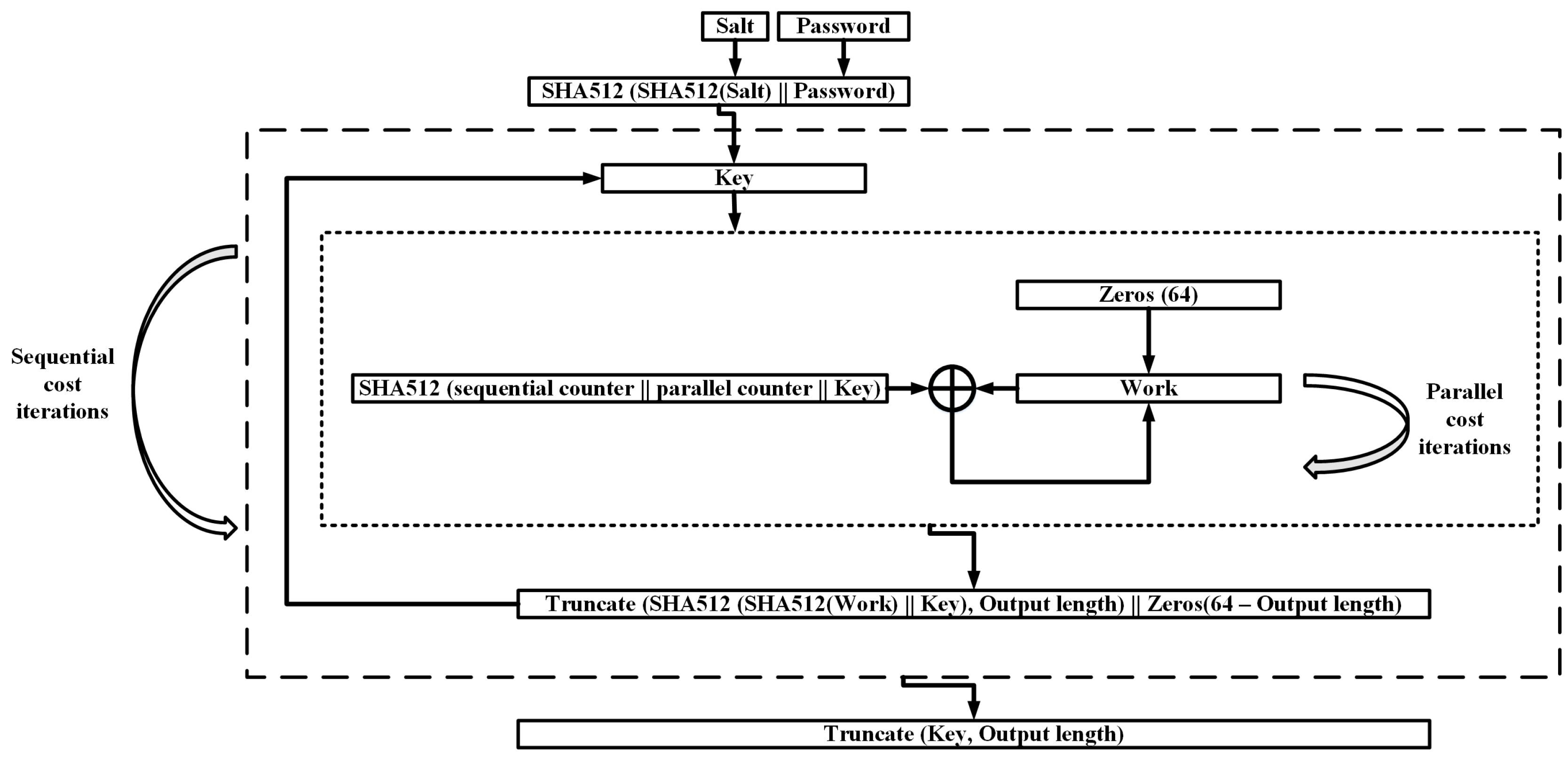
5.3. Balloon PHS
6. Materials and Methods
6.1. General Features
6.2. Results—Software Benchmark
6.3. Discussion
7. Conclusions
Acknowledgments
Conflicts of Interest
Abbreviations
| Battcrypt | Blowfish All The Things |
| BRG | Bit-Reversal Graph |
| CIU | Client-Independent Update |
| DBG | double-butterfly graphs |
| EksBlowfishSetup | Expensive Blowfish key schedule |
| H/s | Hashes per second |
| HMAC | Keyed-Hash Message Authentication Code |
| KDF | Key Derivation Function |
| PBKDF2 | Password-Based Key Derivation Function 2 |
| PPBKDF | Parallel password based key derivation function |
| PRF | Pseudo-Random Function |
| PHC | Password Hashing Competition |
| PHS | Password-Hashing Scheme |
| PKCS | Public-Key Cryptography Standards |
| SIMD | Single Instruction Multiple Data |
| SR | Server relief |
Appendix A. This Appendix Summarizes the GPU Results of Several PHSs
| PHS | Hashes per Second (H/s) | GPU Model |
|---|---|---|
| SHA1 [108] | 794,600,000.00 | ATI HD 6870 |
| HMAC-SHA1 [108] | 395,210,000.00 | ATI HD 6870 |
| SHA2 [109] | 290,000,000.00 | NVIDIA GRID K520 |
| SHA3 [110] | 113,116,250.00 | NVIDIA GeForce GTX580 |
| PBKDF2-SHA1 [108] | 424,780.00 | ATI HD 6870 |
| PBKDF2-SHA2 [14] | 219,480.00 | NVIDIA Tesla C2070 |
| Bcrypt [108] | 2868.00 | NVIDIA GeForce GTX480 |
| -||- | 319.37 | NVIDIA GeForce GTX480 |
| -||- | 33.73 | NVIDIA GeForce GTX480 |
| -||- | 2.71 | NVIDIA GeForce GTX480 |
| Scrypt [108] | 42,650.00 | NVIDIA GeForce GTX480 |
| -||- | 2333.00 | NVIDIA GeForce GTX480 |
| -||- | 49.06 | NVIDIA GeForce GTX480 |
| -||- | 0.37 | NVIDIA GeForce GTX480 |
| Argon2 [111] | 2.64 | AMD Radeon HD 7900 |
| -||- | 0.70 | AMD Radeon HD 7900 |
| -||- | 0.04 | AMD Radeon HD 7900 |
| Lyra2 [112] | 2688.00 | NVIDIA Tesla K20X |
| -||- | 300.00 | NVIDIA Tesla K20X |
| Lyra2 [113] | 0.018 | NVIDIA GeForce GTX TITAN |
| -||- | 0.0018 | NVIDIA GeForce GTX TITAN |
Appendix B. This Appendix Summarizes the General Features of the Examined PHSs
| PHS | Cryptographic Primitives | Internal Memory | Functionality | Security Analysis/Attacks |
|---|---|---|---|---|
| PBKDF2 | PRF (HMAC-SHA1) | negl. | PHS, KDF | GPU and FPGA attacks [14], multi-FPGA attacks [15] |
| Bcrypt | Blowfish | 4 KB | PHS, KDF | Attacks in several low-cost parallel platforms [16] |
| Scrypt | PBKDF2 HMAC, Salsa20/8 | 1 GB | PHS, KDF | Security analysis [9], Attacks on GPUs [17], Cache-timing attacks [18], Garbage-collector attacks [19] |
| Balloon | Blake2b | 1 MB–32 MB | PHS, KDF | Security analysis [9,25] |
| Argon | AES128 | 1 KB–1 GB | PHS, KDF, SR, CIU | Security analysis [83] |
| Argon2d | BlaMka | 200 MB–4 GB | PHS, KDF, SR, CIU | Security analysis [84], effective attacks [22,23,24,25] |
| Argon2i | BlaMka | 1 GB–6 GB | PHS, KDF, SR, CIU | Security analysis [84], effective attacks [22,23,24,25] |
| Battcrypt | Blowfish-CBC, SHA512 | 128 KB–128 MB | PHS, KDF, SR, CIU | Security claims [85], weak garbage-collector [96] |
| Catena | Blake2b/SHA512 | 8 MB | PHS, KDF, SR, CIU | Security analysis [19], effective attacks [23] |
| Catena-DBG | Blake2b/SHA512 | 4 MB | PHS, KDF, SR, CIU | Security analysis [19], effective attacks [23] |
| Catena-BRG | Blake2b/SHA512 | 128 MB | PHS, KDF, SR, CIU | Security analysis [19], effective attacks [23] |
| Lyra2 | Blake2b / BlaMka | 400 MB–1 GB | PHS, KDF, SR, CIU | Security analysis [87] |
| MAKWA | HMAC_DRBG, SHA256 | 335 KB | PHS, KDF, SR, offline hash upgrade, password escrow | Security analysis [88], Optimization on GPU and CPU [99] |
| Parallel | SHA512 | negl. | PHS, KDF, SR, CIU | Security claims [89], weak garbage-collector [96] |
| POMELO | - | 8 KB, 256 GB | PHS, CIU | Security analysis [90] |
| Pufferfish | Blowfish, HMAC-SHA512 | 4 KB–16 KB | PHS, KDF, SR | Security claims [91] |
| Yescrypt | Scrypt | 3 MB (RAM), 3 GB (ROM) | PHS, KDF, SR, CIU | Security claims [92], garbage-collector and weak garbage-collector [96] |
Appendix C. This Appendix Includes the Evaluation Results for the Examined PHSs
| PHS | Password | Salt | Output | t_cost | m_cost | ROM | RAM | CPU |
|---|---|---|---|---|---|---|---|---|
| (bytes) | (bytes) | (bytes) | (KB) | (KB) | ||||
| PBKDF2 | 24 | 8 | 64 | 1000 | 0 | 30 | 0 | 0.002024 |
| PBKDF2 | 24 | 8 | 64 | 2048 | 0 | 30 | 0 | 0.004150 |
| PBKDF2 | 24 | 8 | 64 | 4096 | 0 | 30 | 0 | 0.008141 |
| PBKDF2 | 24 | 8 | 64 | 10,000 | 0 | 30 | 0 | 0.019386 |
| PBKDF2 | 24 | 8 | 64 | 1,000,000 | 0 | 30 | 0 | 1.908592 |
| PBKDF2 | 24 | 8 | 64 | 16,777,216 | 0 | 30 | 0 | 32.969576 |
| Bcrypt | 12 | 16 | 54 | 12 | 0 | 27 | 492 | 2.668653 |
| Scrypt | 8 | 32 | 64 | 5 | 0 | 182 | 450,656 | 2.837654 |
| Balloon | 8 | 8 | 32 | 8 | 1,048,576 | 430 | 3384 | 0.443758 |
| Balloon | 8 | 8 | 32 | 10 | 1,048,576 | 430 | 3428 | 0.807338 |
| Balloon | 8 | 8 | 32 | 20 | 1,048,576 | 430 | 3432 | 1.328957 |
| Balloon | 8 | 8 | 32 | 40 | 1,048,576 | 430 | 3440 | 2.20058 |
| Balloon | 8 | 8 | 32 | 8 | 2,359,296 | 430 | 4716 | 1.175839 |
| Balloon | 8 | 8 | 32 | 10 | 2,359,296 | 430 | 4728 | 1.364459 |
| Balloon | 8 | 8 | 32 | 20 | 2,359,296 | 430 | 4730 | 2.315945 |
| Balloon | 8 | 8 | 32 | 8 | 4,194,304 | 430 | 6504 | 2.017822 |
| Balloon | 8 | 8 | 32 | 10 | 4,194,304 | 430 | 6588 | 2.358291 |
| Balloon | 8 | 8 | 32 | 20 | 4,194,304 | 430 | 6648 | 4.446284 |
| Argon | 32 | 32 | 32 | 3 | 2 | 82 | 192 | 0.008917 |
| Argon | 32 | 32 | 32 | 254 | 1 | 82 | 144 | 0.037167 |
| Argon | 32 | 32 | 32 | 236 | 10 | 82 | 172 | 0.285078 |
| Argon | 32 | 32 | 32 | 56 | 100 | 82 | 244 | 0.674987 |
| Argon | 32 | 32 | 32 | 3 | 1000 | 82 | 1216 | 0.551141 |
| Argon | 32 | 32 | 32 | 3 | 10,000 | 82 | 10,172 | 5.520845 |
| Argon | 32 | 32 | 32 | 3 | 100,000 | 82 | 100,168 | 55.457062 |
| Argon2d | 32 | 32 | 32 | 3 | 2 | 110 | 44 | 0.000524 |
| Argon2d | 32 | 32 | 32 | 254 | 1 | 110 | 44 | 0.028593 |
| Argon2d | 32 | 32 | 32 | 236 | 10 | 110 | 68 | 0.026851 |
| Argon2d | 32 | 32 | 32 | 56 | 100 | 110 | 136 | 0.077891 |
| Argon2d | 32 | 32 | 32 | 3 | 1000 | 110 | 1064 | 0.043209 |
| Argon2d | 32 | 32 | 32 | 3 | 10,000 | 110 | 10,112 | 0.434536 |
| Argon2d | 32 | 32 | 32 | 3 | 100,000 | 110 | 100,064 | 4.325295 |
| Argon2i | 32 | 32 | 32 | 3 | 2 | 111 | 40 | 0.000522 |
| Argon2i | 32 | 32 | 32 | 254 | 1 | 111 | 40 | 0.028412 |
| Argon2i | 32 | 32 | 32 | 236 | 10 | 111 | 44 | 0.045702 |
| Argon2i | 32 | 32 | 32 | 56 | 100 | 111 | 136 | 0.080158 |
| Argon2i | 32 | 32 | 32 | 3 | 1000 | 111 | 1088 | 0.042961 |
| Argon2i | 32 | 32 | 32 | 3 | 10,000 | 111 | 10,112 | 0.431438 |
| Argon2i | 32 | 32 | 32 | 3 | 100,000 | 111 | 100,064 | 4.194904 |
| Battcrypt | 8 | 4 | 64 | 0 | 0 | 27 | 18 | 0.000310 |
| Battcrypt | 8 | 4 | 64 | 1 | 0 | 27 | 18 | 0.000394 |
| Battcrypt | 8 | 4 | 64 | 1 | 1 | 27 | 30 | 0.000760 |
| Battcrypt | 8 | 4 | 64 | 1 | 2 | 27 | 42 | 0.001987 |
| Battcrypt | 8 | 4 | 64 | 1 | 3 | 27 | 74 | 0.004286 |
| Battcrypt | 8 | 4 | 64 | 1 | 4 | 27 | 138 | 0.016476 |
| Battcrypt | 8 | 4 | 64 | 1 | 5 | 27 | 266 | 0.022355 |
| Battcrypt | 8 | 4 | 64 | 1 | 6 | 27 | 520 | 0.045729 |
| Battcrypt | 8 | 4 | 64 | 1 | 7 | 27 | 1000 | 0.091153 |
| Battcrypt | 8 | 4 | 64 | 1 | 8 | 27 | 2000 | 0.149327 |
| Battcrypt | 8 | 4 | 64 | 1 | 9 | 27 | 4000 | 0.254832 |
| Battcrypt | 8 | 4 | 64 | 1 | 10 | 27 | 8000 | 0.418654 |
| Battcrypt | 8 | 4 | 64 | 1 | 11 | 27 | 16,000 | 0.766934 |
| Battcrypt | 8 | 4 | 64 | 1 | 12 | 27 | 32,000 | 1.472502 |
| Battcrypt | 8 | 4 | 64 | 1 | 13 | 27 | 64,000 | 2.853102 |
| Battcrypt | 8 | 4 | 64 | 2 | 1 | 27 | 25 | 0.001090 |
| Battcrypt | 8 | 4 | 64 | 3 | 1 | 27 | 25 | 0.001630 |
| Battcrypt | 8 | 4 | 64 | 4 | 1 | 27 | 25 | 0.002192 |
| Catena–blake2b | 8 | 16 | 64 | 3 | 18 | 25 | 16,384 | 0.353742 |
| Catena–blake2b | 8 | 16 | 64 | 3 | 20 | 25 | 65,596 | 2.619238 |
| Catena–blake2b | 8 | 16 | 64 | 3 | 21 | 25 | 128,484 | 5.461030 |
| Catena–Dragonfly | 8 | 16 | 64 | 3 | 18 | 34 | 16,496 | 0.093241 |
| Catena–Dragonfly | 8 | 16 | 64 | 3 | 20 | 34 | 65,764 | 0.379892 |
| Catena–Dragonfly | 8 | 16 | 64 | 3 | 21 | 34 | 131,428 | 0.797481 |
| Catena–Butterfly | 8 | 16 | 64 | 3 | 18 | 35 | 24,668 | 1.450987 |
| Catena–Butterfly | 8 | 16 | 64 | 3 | 20 | 35 | 98,448 | 6.402041 |
| Catena–Butterfly | 8 | 16 | 64 | 3 | 21 | 35 | 196,852 | 13.508681 |
| Lyra2 | 8 | 16 | 64 | 5 | 5 | 98 | 44 | 0.000084 |
| Lyra2 | 8 | 16 | 64 | 5 | 100 | 98 | 696 | 0.001463 |
| Lyra2 | 8 | 16 | 64 | 5 | 1000 | 98 | 6104 | 0.015104 |
| Lyra2 | 8 | 16 | 64 | 5 | 10,000 | 98 | 60,128 | 0.159651 |
| Lyra2 | 8 | 16 | 64 | 5 | 131,071 | 98 | 787,416 | 2.916398 |
| MAKWA | 8 | 16 | 64 | 0 | 0 | 95 | 335 | 0.000096 |
| MAKWA | 8 | 16 | 64 | 10 | 0 | 95 | 335 | 0.000132 |
| MAKWA | 8 | 16 | 64 | 100 | 0 | 95 | 335 | 0.000273 |
| MAKWA | 8 | 16 | 64 | 1000 | 0 | 95 | 335 | 0.002035 |
| MAKWA | 8 | 16 | 64 | 4000 | 0 | 95 | 335 | 0.007838 |
| MAKWA | 8 | 16 | 64 | 8192 | 0 | 95 | 335 | 0.015621 |
| Parallel | 8 | 16 | 64 | 0 | 0 | 71 | 0 | 0.001000 |
| Parallel | 8 | 16 | 64 | 0 | 10 | 71 | 0 | 0.001018 |
| Parallel | 8 | 16 | 64 | 10 | 0 | 71 | 0 | 0.047020 |
| Parallel | 8 | 16 | 64 | 10 | 10 | 71 | 0 | 0.047051 |
| POMELO | 8 | 16 | 64 | 0 | 0 | 67 | 12 | 0.000031 |
| POMELO | 8 | 16 | 64 | 0 | 7 | 67 | 1064 | 0.003537 |
| POMELO | 8 | 16 | 64 | 0 | 17 | 67 | 1,048,648 | 7.951508 |
| POMELO | 8 | 16 | 64 | 7 | 0 | 67 | 12 | 0.001270 |
| POMELO | 8 | 16 | 64 | 7 | 7 | 67 | 1064 | 0.171375 |
| POMELO | 8 | 16 | 64 | 20 | 0 | 67 | 12 | 8.504152 |
| Pufferfish–ref | 8 | 16 | 64 | 0 | 0 | 103 | 156 | 0.000057 |
| Pufferfish–ref | 8 | 16 | 64 | 6 | 2 | 103 | 120 | 0.003359 |
| Pufferfish–ref | 8 | 16 | 64 | 6 | 10 | 103 | 1192 | 2.225718 |
| Pufferfish–ref | 8 | 16 | 64 | 10 | 10 | 103 | 1188 | 38.341005 |
| Pufferfish–ref | 8 | 16 | 64 | 6 | 11 | 103 | 2236 | 19.884300 |
| Pufferfish–opt | 8 | 16 | 64 | 0 | 0 | 398 | 220 | 0.000055 |
| Pufferfish–opt | 8 | 16 | 64 | 6 | 2 | 398 | 180 | 0.002980 |
| Pufferfish–opt | 8 | 16 | 64 | 6 | 10 | 398 | 1140 | 2.183917 |
| Pufferfish–opt | 8 | 16 | 64 | 10 | 10 | 398 | 1132 | 37.668099 |
| Yescrypt-ref | 8 | 16 | 64 | 0 | 0 | 36 | 44 | 0.000094 |
| Yescrypt-ref | 8 | 16 | 64 | 0 | 7 | 36 | 1516 | 0.004173 |
| Yescrypt-ref | 8 | 16 | 64 | 0 | 8 | 36 | 2112 | 0.007209 |
| Yescrypt-ref | 8 | 16 | 64 | 1 | 8 | 36 | 2112 | 0.008901 |
| Yescrypt-ref | 8 | 16 | 64 | 2 | 8 | 36 | 2112 | 0.012088 |
| Yescrypt-ref | 8 | 16 | 64 | 3 | 8 | 36 | 2112 | 0.015313 |
| Yescrypt-ref | 8 | 16 | 64 | 0 | 11 | 36 | 16,448 | 0.058253 |
| Yescrypt-opt | 8 | 16 | 64 | 0 | 0 | 44 | 72 | 0.000116 |
| Yescrypt-opt | 8 | 16 | 64 | 0 | 7 | 44 | 1148 | 0.003296 |
| Yescrypt-opt | 8 | 16 | 64 | 0 | 8 | 44 | 2124 | 0.005796 |
| Yescrypt-opt | 8 | 16 | 64 | 1 | 8 | 44 | 2124 | 0.006885 |
| Yescrypt-opt | 8 | 16 | 64 | 2 | 8 | 44 | 2124 | 0.009448 |
| Yescrypt-opt | 8 | 16 | 64 | 3 | 8 | 44 | 2124 | 0.011544 |
| Yescrypt-opt | 8 | 16 | 64 | 0 | 11 | 44 | 16,460 | 0.046733 |
References
- Farcasin, M.; Chan-tin, E. Why we hate IT: Two surveys on pre-generated and expiring passwords in an academic setting. In Security and Communication Networks; Wiley: Hoboken, NJ, USA, 2015. [Google Scholar]
- Furnell, S. An assessment of website password practices. Comput. Secur. 2007, 26, 445–451. [Google Scholar] [CrossRef]
- Richmond, S.; Williams, C. Millions of Internet Users Hit by Massive Sony PlayStation Data Theft, the Telegraph. London, 26 April 2011. Available online: http://www.telegraph.co.uk/technology/news/8475728/Millions-of-internet-users-hit-by-massive-Sony-PlayStation-data-theft.html (accessed on 28 January 2017).
- Finkle, J.; Saba, J. LinkedIn Suffers Data Breach—Security Experts, Reuters. June 2012. Available online: http://in.reuters.com/article/2012/06/06/linkedin-breach-idINDEE8550EN20120606 (accessed on 28 January 2017).
- Cavusoglu, H.; Cavusoglu, H.; Raghunathan, S. Efficiency of Vulnerability Disclosure Mechanisms to Disseminate Vulnerability Knowledge. IEEE Trans. Softw. Eng. 2007, 33, 171–185. [Google Scholar] [CrossRef]
- Telang, R.; Wattal, S. An Empirical Analysis of the Impact of Software Vulnerability Announcements on Firm Stock Price. IEEE Trans. Softw. Eng. 2007, 33, 544–557. [Google Scholar] [CrossRef]
- Kaliski, B. RFC 2898—PKCS #5: Password-Based Cryptography Specification Version 2.0; Technical Report; IETF: Fremont, CA, USA, 2000. [Google Scholar]
- Provos, N.; Mazieres, D. A Future-Adaptable Password Scheme. In Proceedings of the USENIX Annual Technical Conference, Monterey, CA, USA, 6–11 June 1999; pp. 81–92. [Google Scholar]
- Percival, C. Stronger Key Derivation via Sequential Memory-Hard Functions. In Proceedings of the BSD Conference, Ottawa, ON, Canada, 8–9 May 2009. [Google Scholar]
- Belenko, A.; Sklyarov, D. “Secure Password Managers” and “Military-Grade Encryption” on Smartphones: Oh, Really, 3rd ed.; Hack to Ergo Sum (HES); Elcomsoft Co. Ltd.: Moscow, Russia, 2012. [Google Scholar]
- Fan, D.-R.; Li, X.-W.; Li, G.-J. New Methodologies for Parallel Architecture. J. Comput. Sci. Technol. 2011, 26, 578–587. [Google Scholar] [CrossRef]
- Orman, H. Twelve Random Characters: Passwords in the Era of Massive Parallelism. IEEE Int. Comput. 2013, 17, 91–94. [Google Scholar] [CrossRef]
- Kim, J.W.; Seo, J.; Hong, J.; Park, K.; Kim, S.-R. High-speed parallel implementations of the rainbow method based on perfect tables in a heterogeneous system. Softw. Pract. Exper. 2015, 45, 837–855. [Google Scholar] [CrossRef]
- Durmuth, M.; Guneysu, T.; Kasper, M.; Paar, C.; Yalcin, T.; Zimmermann, R. Evaluation of Standardized Password-Based Key Derivation against Parallel Processing Platforms. In LNCS; Springer: Berlin, Germany, 2012; pp. 716–733. [Google Scholar]
- Abbas, A.; Voss, R.; Wienbrandt, L.; Schimmler, M. An efficient implementation of PBKDF2 with RIPEMD-160 on multiple FPGAs. In Proceedings of the 20th IEEE International Conference on Parallel and Distributed Systems (ICPADS), Hsinchu, Taiwan, 16–19 December 2014; pp. 454–461. [Google Scholar]
- Malvoni, K.; Designer, S.; Knezovic, J. Are Your Passwords Safe: Energy-Efficient Bcrypt Cracking with Low-Cost Parallel Hardware. In Proceedings of the 8th USENIX Workshop on Offensive Technologies (WOOT’14), San Diego, CA, USA, 19 August 2014. [Google Scholar]
- Durmuth, M.; Kranz, T. On Password Guessing with GPUs and FPGAs. In Proceedings of the International Conference on PASSWORDS 2014, Trondheim, Norway, 8–10 December 2014. [Google Scholar]
- Forler, C.; Lucks, S.; Wenzel, J. Memory-Demanding Password Scrambling. In LNCS, Proceedings of the ASIACRYPT, Kaohsiung, Taiwan, 7–11 December 2014; Springer: Berlin, Germany, 2014; Volume 8874, pp. 289–305. [Google Scholar]
- Forler, C.; Lucks, S.; Wenzel, J. The Catena Password Scrambler, PHC Submission. 15 May 2014. Available online: https://www.uni-weimar.de/de/medien/professuren/mediensicherheit/research/catena/ (accessed on 28 January 2017).
- Cryptographic Competition: Password Hashing Competition (PHC). 25 April 2013. Available online: https://password-hashing.net/ (accessed on 28 January 2017).
- Forler, C.; List, E.; Lucks, S.; Wenzel, J. Overview of the Candidates for the Password Hashing Competition and their Resistance against Garbage-Collector Attacks; Cryptology ePrint Archive; Report 2014/881; Springer: Berlin, Germany, 2014. [Google Scholar]
- Alwen, J.; Serbinenko, V. High parallel complexity graphs and memory-hard functions. In Proceedings of the Forty-Seventh Annual ACM Symposium on Theory of Computing (STOC’15), Portland, OR, USA, 14–17 June 2015; pp. 595–603. [Google Scholar]
- Alwen, J.; Blocki, J. Efficiently Computing Data-Independent Memory-Hard Functions; Cryptology ePrint Archive; Report 2016/115; Springer: Berlin, Germany, 2016. [Google Scholar]
- Boneh, D.; Corrigan-Gibbs, H.; Schechter, S. Balloon hashing: A memory-hard function providing provable protection against sequential attacks. In Proceedings of the ASIACRYPT, Hanoi, Vietnam, 4–8 December 2016. [Google Scholar]
- Alwen, J.; Blocki, J. Towards Practical Attacks on Argon2i and Balloon Hashing; Cryptology ePrint Archive; Report 2016/759; Springer: Berlin, Germany, 2016. [Google Scholar]
- Biryukov, A.; Dinu, D.; Khovratovich, D. The Memory-Hard Argon2 Password Hash and Proof-of-Work Function, IETF, Draft-Irtf-Cfrg-Argon2-01. 22 September 2016. Available online: https://tools.ietf.org/html/draft-irtf-cfrg-argon2-01 (accessed on 28 January 2017).
- Bonneau, J.; Schechter, S. Towards reliable storage of 56-bit secrets in human memory. In Proceedings of the 23rd USENIX Conference on Security Symposium (SEC’14), San Diego, CA, USA, 20–22 August 2014; pp. 607–623. [Google Scholar]
- Vaidya, B.; Park, J.H.; Yeo, S.-S.; Rodrigues, J.J.P.C. Robust one-time password authentication scheme using smart card for home network environment. Comput. Commun. 2011, 34, 326–336. [Google Scholar] [CrossRef]
- Mannan, M.; van Oorschot, P.C. Leveraging personal devices for stronger password authentication from untrusted computers. J. Comput. Secur. 2011, 19, 703–750. [Google Scholar] [CrossRef]
- Lee, S.; Han, K.; Kang, S.-K.; Kim, K.; Ine, S.R. Threshold Password-Based Authentication Using Bilinear Pairings. In Proceedings of the First European PKI Workshop: Research and Applications (EuroPKI 2004), Samos Island, Greece, 25–26 June 2004; pp. 350–363. [Google Scholar]
- Chen, L.; Lim, H.W.; Yang, G. Cross-Domain Password-Based Authenticated Key Exchange Revisited. ACM Trans. Inf. Syst. Secur. 2014, 16, 15. [Google Scholar] [CrossRef]
- Acar, T.; Belenkiy, M.; Kupcu, A. Single password authentication. Comput. Netw. Int. J. Comput. Telecommun. Netw. 2013, 57, 2597–2614. [Google Scholar] [CrossRef]
- HSU, F.; Chen, H.; Machiraju, S. WebCallerID: Leveraging cellular networks for Web authentication. J. Comput. Secur. 2011, 19, 869–893. [Google Scholar] [CrossRef]
- NIST: Recommendation for Password-Based Key Derivation, NIST Special Publication 800-132. December 2010. Available online: http://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-132.pdf (accessed on 28 January 2017).
- Zheng, M.-H.; Zhou, H.-H.; Li, J.; Cui, G.-H. Efficient and provably secure password-based group key agreement protocol. Comput. Stand. Interfaces 2009, 31, 948–953. [Google Scholar] [CrossRef]
- Liao, Y.-P.; Wang, S.-S. A secure dynamic ID based remote user authentication scheme for multi-server environment. Comput. Stand. Interfaces 2009, 31, 24–29. [Google Scholar] [CrossRef]
- Catuogno, L.; Galdi, C. Analysis of a two-factor graphical password scheme. Int. J. Inf. Secur. 2014, 13, 421–437. [Google Scholar] [CrossRef]
- Liu, X.-Y.; Gao, H.-C.; Wang, L.-M.; Chang, X.-L. A vision based graphical password. J. Integr. Des. Process Sci. 2010, 14, 43–52. [Google Scholar]
- Van Oorschot, P.C.; Thorpe, J. On predictive models and user-drawn graphical passwords. ACM Trans. Inf. Syst. Secur. 2008, 10. [Google Scholar] [CrossRef]
- Van Oorschot, P.C.; Thorpe, J. Exploiting predictability in click-based graphical passwords. J. Comput. Secur. 2011, 19, 669–702. [Google Scholar] [CrossRef]
- Sklavos, N. Towards to SHA-3 Hashing Standard for Secure Communications: On the Hardware Evaluation Development. IEEE Lat. Am. Trans. 2012, 10, 1433–1434. [Google Scholar] [CrossRef]
- Sklavos, N.; Koufopavlou, O. Implementation of the SHA-2 hash family standard using FPGAs. J. Supercomput. 2005, 31, 227–248. [Google Scholar] [CrossRef]
- Kontaxis, G.; Polychronakis, M.; Markatos, E.P. Minimizing information disclosure to third parties in social login platforms. Int. J. Inf. Secur. 2012, 11, 321–332. [Google Scholar] [CrossRef]
- Oechslin, P. Making a faster cryptanalytical time-memory trade-Off. Adv. Cryptol. 2003, 2729, 617–630. [Google Scholar]
- Shay, R.; Bertino, E. A comprehensive simulation tool for the analysis of password policies. Int. J. Inf. Secur. 2009, 8, 275–289. [Google Scholar] [CrossRef]
- Reichl, D. KeePass Password Safe. Version 2.35. 2017. Available online: http://keepass.info/ (accessed on 28 January 2017).
- Florencio, D.; Herley, C. A large scale study of web password habits. In Proceedings of the 16th International Conference on World Wide Web (WWW 2007), Banff, AB, Canada, 8–12 May 2007; pp. 657–666. [Google Scholar]
- Zhao, R.; Yue, C. Toward a secure and usable cloud-based password manager for web browsers. Comput. Secur. 2014, 46, 32–47. [Google Scholar] [CrossRef]
- Van Oorschot, P.C.; Stubblebine, S. On countering online dictionary attacks with login histories and humans-in-the-loop. ACM Trans. Inf. Syst. Secur. 2006, 9, 235–258. [Google Scholar] [CrossRef]
- Patel, A.; Nordin, R.; Al-Haiqi, A. Beyond ubiquitous computing: The Malaysian HoneyBee Project for Innovative Digital Economy. Comput. Stand. Interfaces 2014, 36, 844–854. [Google Scholar] [CrossRef]
- Chaurasia, B.K.; Verma, S. Secure pay while on move toll collection using VANET. Comput. Stand. Interfaces 2014, 36, 403–411. [Google Scholar] [CrossRef]
- Fysarakis, K.; Hatzivasilis, G.; Papaefstathiou, I.; Manifavas, C. RtVMF—A secure Real-time Vehicle Management Framework with critical incident response. IEEE Pervasive Comput. Mag. 2016, 15, 22–30. [Google Scholar] [CrossRef]
- Fysarakis, K.; Hatzivasilis, G.; Askoxylakis, I.G.; Manifavas, C. RT-SPDM: Real-time Security, Privacy & Dependability Management of Heterogeneous Systems. In LNCS, Proceedings of the International Conference on Human Aspects of Information Security, Privacy and Trust (HCI International 2015), Los Angeles, CA, USA, 2–7 August 2015; Springer: Berlin, Germany, 2015; Volume 9190, pp. 619–630. [Google Scholar]
- Hatzivasilis, G.; Papaefstathiou, I.; Manifavas, C. Real-time management of railway CPS. In Proceedings of the 5th EUROMICRO/IEEE Workshop on Embedded and Cyber-Physical Systems (ECYPS 2017), Bar, Montenegro, 11–15 June 2017. [Google Scholar]
- Fournaris, A.P.; Sklavos, N. Secure embedded system hardware design—A flexible security and trust enhanced approach. Comput. Electr. Eng. 2014, 40, 121–133. [Google Scholar] [CrossRef]
- Fournaris, A.P.; Kitsos, P.; Sklavos, N. Embedded Computing Systems: Applications, Optimization, and Advanced Design. In Security and Cryptographic Engineering in Embedded Systems (Chapter 21); IGI Global: Hershey, PA, USA, 2013; pp. 420–438. [Google Scholar]
- Hatzivasilis, G.; Floros, G.; Papaefstathiou, I.; Manifavas, C. Lightweight Authenticated Encryption for Embedded On-Chip Systems. Inf. Secur. J. Glob. Perspect. 2016, 25, 1–11. [Google Scholar] [CrossRef]
- Hatzivasilis, G.; Fysarakis, K.; Papaefstathiou, M.C. A review of lightweight block ciphers. J. Cryptogr. Eng. 2017, 7, 1–44. [Google Scholar] [CrossRef]
- Manifavas, C.; Hatzivasilis, G.; Fysarakis, K.; Papaefstathiou, I. A survey of lightweight stream ciphers for embedded systems. Secur. Commun. Netw. 2015, 9, 1226–1246. [Google Scholar] [CrossRef]
- Hatzivasilis, G.; Gasparis, E.; Theodoridis, A.; Manifavas, C. ULCL: An Ultra-Lightweight Cryptographic Library for embedded systems. In Proceedings of the Measurable security for Embedded Computing and Communication Systems (MeSeCCS 2014), Lisbon, Portugal, 7–9 January 2014; pp. 11–18. [Google Scholar]
- Fysarakis, K.; Hatzivasilis, G.; Rantos, K.; Papanikolaou, A.; Manifavas, C. Embedded systems security challenges. In Proceedings of the Measurable security for Embedded Computing and Communication Systems (MeSeCCS 2014), Lisbon, Portugal, 7–9 January 2014; pp. 1–10. [Google Scholar]
- Roman, R.; Alcaraz, C.; Lopez, J.; Sklavos, N. Key Management Systems for Sensor Networks in the Context of the Internet of Things. Comput. Electr. Eng. 2011, 37, 147–159. [Google Scholar] [CrossRef]
- Hatzivasilis, G.; Papaefstathiou, G.; Fysarakis, A.I.G. SecRoute: End-to-End Secure Communications for Wireless Ad-hoc Networks. In Proceedings of the 22nd IEEE Symposium on Computers and Communications (ISCC 2017), Heraklion, Greece, 3–6 July 2017. [Google Scholar]
- Hatzivasilis, G.; Papaefstathiou, I.; Manifavas, C. ModConTR: A Modular and Configurable Trust and Reputation-based system for secure routing. In Proceedings of the 11th ACS/IEEE International Conference on Computer Systems and Applications (AICCSA’2014), Doha, Qatar, 10–13 November 2014; pp. 56–63. [Google Scholar]
- Hatzivasilis, G.; Manifavas, C. Building trust in ad hoc distributed resource-sharing networks using reputation-based systems. In Proceedings of the 16th Panhellenic Conference on Informatics (PCI 2012), Piraeus, Greece, 5–7 October 2012; pp. 416–421. [Google Scholar]
- Manifavas, C.; Hatzivasilis, G.; Fysarakis, K.; Rantos, K. Lightweight cryptography for embedded systems—A comparative analysis. In LNCS, Proceedings of the 8th International Workshop on Data Privacy Management and Autonomous Spontaneous Security, Egham, UK, 12–13 September 2013; Springer: New York, NY, USA, 2013; Volume 8247, pp. 333–349. [Google Scholar]
- Regan, G.; Caffery, F.M.; Daid, K.M.; Flood, D. Medical device standards’ requirements for traceability during the software development lifecycle and implementation of a traceability assessment model. Comput. Stand. Interfaces 2013, 36, 3–9. [Google Scholar] [CrossRef]
- Dini, G.; Savino, I.M. LARK: A Lightweight Authenticated ReKeying Scheme for Clustered Wireless Sensor Networks. ACM Trans. Embed. Comput. Syst. 2011, 10, 41. [Google Scholar] [CrossRef]
- Dong, Q.; Liu, D. Using Auxiliary Sensors for Pairwise Key Establishment in WSN. ACM Trans. Embed. Comput. Syst. 2012, 11, 59. [Google Scholar] [CrossRef]
- Chung, H.-R.; Ku, W.-C.; Tsaur, M.-J. Weaknesses and improvement of Wang et al.’s remote user password authentication scheme for resource-limited environments. Comput. Stand. Interfaces 2009, 31, 863–868. [Google Scholar] [CrossRef]
- Wu, G.; Shu, F.; Wang, M.; Chen, W. Requirements specifications checking of embedded real-time software. J. Comput. Sci. Technol. 2002, 17, 56–63. [Google Scholar] [CrossRef]
- Hatzivasilis, G.; Papaefstathiou, I.; Manifavas, C. Software Security, Privacy and Dependability: Metrics and Measurement. IEEE Softw. 2016, 33, 46–54. [Google Scholar] [CrossRef]
- Hatzivasilis, G.; Papaefstathiou, I.; Manifavas, C.; Papadakis, N. A reasoning system for composition verification and security validation. In Proceedings of the 6th IFIP International Conference on New Technologies, Mobility & Security (NTMS 2014), Dubai, UAE, 30 March–2 April 2014; pp. 1–4. [Google Scholar]
- Dhurjati, D.; Kowshik, S.; Adve, V.; Lattner, C. Memory safety without garbage collection for embedded applications. ACM Trans. Embed. Comput. Syst. 2005, 4, 73–111. [Google Scholar] [CrossRef]
- RSA Laboratories: PKCS #5: Password-Based Cryptographic Standard. Version 2.0. 2000. Available online: http://www.emc.com/emc-plus/rsa-labs/standards-initiatives/pkcs-5-password-based-cryptography-\standard.htm (accessed on 28 January 2017).
- Kaliski, B. RSA Laboratories: PKCS #5: Password-Based Cryptography Specification Version 2.0, IETF, RFC2898. September 2000. Available online: http://tools.ietf.org/html/rfc2898 (accessed on 28 January 2017).
- NIST: Secure Hash Standard, FIPS 180-2. April 1995. Available online: http://csrc.nist.gov/publications/fips/fips180-2/\fips180-2.pdf (accessed on 28 January 2017).
- Avoine, G.; Junod, P.; Oechslin, P. Characterization and Improvement of Time-Memory Trade-Off Based on Perfect Tables. ACM Trans. Inf. Syst. Secur. 2008, 11. [Google Scholar] [CrossRef]
- Schneier, B. Description of a New Variable-Length Key, 64-Bit Block Cipher (Blowfish). In LNCS, Proceedings of the Fast Software Encryption, Cambridge Security Workshop, Cambridge, UK, 9–11 December 1993; Springer: London, UK, 1994; Volume 809, pp. 191–204. [Google Scholar]
- Percival, C.; Josefsson, S. The Scrypt Password-Based Key Derivation Function, IETF. 18 May 2016. Available online: https://tools.ietf.org/html/draft-josefsson-scrypt-kdf-05 (accessed on 28 January 2017).
- Bernstein, D.J. The Salsa20 Family of Stream Ciphers, eSTREAM Project. 2007. Available online: http://cr.yp.to/papers.html#salsafamily (accessed on 28 January 2017).
- Password Hashing Competition (PHC): Candidates. 31 March 2014. Available online: https://password-hashing.net/candidates.html (accessed on 28 January 2017).
- Biryukov, A.; Khovratovich, D. Argon v1: Password Hashing Scheme. 8 April 2014. Available online: https://www.cryptolux.org/images/0/0c/Argon-v1.pdf (accessed on 28 January 2017).
- Biryukov, A.; Dinu, D.; Khovratovich, D. Argon2. 3 March 2016. Available online: https://www.cryptolux.org/images/0/0d/Argon2.pdf (accessed on 28 January 2017).
- Thomas, S. Battcrypt (Blowfish All the Things), PHC Submission. 16 February 2014. Available online: https://password-hashing.net/submissions/specs/battcrypt-v0.pdf (accessed on 28 January 2017).
- Lucks, S.; Wenzel, J. Catena Variants—Different Instantiations for an Extremely Flexible Password-Hashing Framework. In LNCS, Proceedings of the 9th International Conference on Passwords, London, UK, 7–9 December 2015; Springer: Berlin, Germany, 2015; Volume 9551, pp. 95–119. [Google Scholar]
- Simplicio, M.A.; Almeida, L.C.; Andrade, E.R.; Santos, P.C.F.; Barreto, P.S.L.M. Lyra2: Password Hashing Scheme with Improved Security against Time-Memory Trade-Offs; Cryptology ePrint Archive; Report 2015/136; Poli-USP: São Paulo, Brazil, 2015. [Google Scholar]
- Thomas, P. The MAKWA Password Hashing Function, PHC Submission. 22 April 2015. Available online: http://www.bolet.org/makwa/makwa-spec-20150422.pdf (accessed on 28 January 2017).
- Thomas, S. Parallel, PHC Submission. 16 February 2014. Available online: https://password-hashing.net/submissions/\specs/Parallel-v1.pdf (accessed on 28 January 2017).
- Hongjun, W. POMELO: A Password Hashing Algorithm (Version 2), PHC Submission. 13 April 2015. Available online: http://www3.ntu.edu.sg/home/wuhj/research/pomelo/POMELO-v2-2015-04-13.pdf (accessed on 28 January 2017).
- Gosney, J. The Pufferfish Password Hashing Scheme, PHC Submission. 31 January 2015. Available online: https://github.com/epixoip/pufferfish (accessed on 28 January 2017).
- Peslyak, A. Yescrypt—A Password Hashing Competition Submission, PHC Submission. 31 January 2015. Available online: https://password-hashing.net/submissions/specs/yescrypt-v2.pdf (accessed on 28 January 2017).
- NIST: Advanced Encryption Standard, FIPS-197. November 2001. Available online: http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf (accessed on 28 January 2017).
- Biryukov, A.; Dinu, D.; Khovratovich, D. Fast and Tradeoff-Resillient Memory-Hard Functions for Crytocurrencies and Password Hashing; Cryptology ePrint Archive; Report 2015/430; Springer: Berlin, Germany, 2015. [Google Scholar]
- Aumasson, J.-P.; Neves, S.; Wilcox-O’Hearn, Z.; Winnerlein, C. BLAKE2: Simpler, Smaller, Fast as MD5. In LNCS, Proceedings of the 11th International Conference on Applied Cryptography and Network Security, Banff, AB, Canada, 25–28 June 2013; Springer: New York, NY, USA, 2013; Volume 7954, pp. 119–135. [Google Scholar]
- Forler, C.; List, E.; Lucks, S.; Wenzel, J. Overview of the candidates for the password hashing competition and their resistance against garbage-collector attacks. In LNCS, Proceedings of the International Conference on Passwords (PASSWORDS’14), Trondheim, Norway, 8–10 December 2014; Springer: Berlin, Germany, 2014; Volume 9393, pp. 3–18. [Google Scholar]
- RSA Laboratories: PKCS #1: RSA Cryptography Standard Version 2.2. 2012. Available online: http://www.emc.com/emc-plus/rsa-labs/pkcs/files/h11300-wp-pkcs-1v2-2-rsa-cryptography-\standard.pdf (accessed on 28 January 2017).
- NIST: Recommendation for Random Number Generation Using Deterministic Random Bit Generators (Revised), NIST Special Publication 800-90A. January 2012. Available online: http://csrc.nist.gov/publications/nistpubs/800-90A/SP800-90A.pdf (accessed on 28 January 2017).
- Thomas, P. Optimizing MAKWA on GPU and CPU; Cryptology ePrint Archive; Report 2015/678; Springer: Berlin, Germany, 2015. [Google Scholar]
- Chandra, R.; Menon, R.; Dagum, L.; Kohr, D.; Maydan, D.; McDonald, J. Parallel Programming in OpenMP. 2000. Available online: http://lib.mdp.ac.id/ebook/Karya%20Umum/Parallel_Programming_in_OpenMP.pdf (accessed on 28 January 2017).
- Sodium Crypto Library: Libsodiom Version 1.0.11. 2016. Available online: https://download.libsodium.org/doc/ (accessed on 28 January 2017).
- Simplicio, M.A.; Almeida, L.C.; Andrade, E.R.; Santos, P.C.F.; Barreto, P.S.L.M. Node-Multi-Hashing with Lyra2reV2. 2015. Available online: https://github.com/upgradeadvice/node-multi-hashing (accessed on 28 January 2017).
- Hatzivasilis, G.; Papaefstathiou, I.; Manifavas, C.; Askoxylakis, I. Lightweight password hashing scheme for embedded systems. In LNCS, Proceedings of the 9th WG 11.2 International Conference on Information Security Theory and Practice (WISTP), Heraklion, Greece, 24–25 August 2015; Springer: Berlin, Germany, 2015; Volume 9311, pp. 249–259. [Google Scholar]
- Alwen, J.; Chen, B.; Kamath, C.; Kolmogorov, V.; Pietrzak, K.; Tessaro, S. On the complexity of Scrypt and proofs of space in the parallel random oracle model. In LNCS, Proceedings of the 35th Annual International Conference on Advances in Cryptology—EUROCRYPT, Vienna, Austria, 8–12 May 2016; Springer: Berlin, Germany, 2016; Volume 9666, pp. 358–387. [Google Scholar]
- CyaSSL: Pwdbased.c. wolfSSL, CyaSSL 3.2.0. 2014. Available online: https://www.wolfssl.com/wolfSSL/Source/output/\wolfcrypt/src/pwdbased.c.html (accessed on 28 January 2017).
- Garcia, R. Bcrypt. Openwall, Solar Designer. Available online: https://github.com/rg3/bcrypt (accessed on 28 January 2017).
- Tarsnap: Scrypt-1.1.6. Tarsnap Online Backups for the Truly Paranoid. January 2010. Available online: http://www.tarsnap.com/scrypt/scrypt-1.1.6.tgz (accessed on 28 January 2017).
- Durmuth, M.; Kranz, T. On Password Guessing with GPUs and FPGAs. In LNCS, Proceedings of the International Conference on Passwords (PASSWORDS’14), Cambridge, UK, 7–9 December 2015; Springer: Berlin, Germany, 2015; Volume 9393, pp. 19–38. [Google Scholar]
- Aggarwal, A.; Chaphekar, P.; Mandrekar, R. Cryptanalysis of Bcrypt and SHA-512 using Distributed Processing over the Cloud. Int. J. Comput. Appl. 2015, 128, 13–16. [Google Scholar] [CrossRef]
- Papaefstathiou, I.; Bilanakos, A.; Fysarakis, K.; Hatzivasilis, G.; Manifavas, C. An efficient anti-malware intrusion detection system implementation, exploiting GPUs. In Proceedings of the International Conference on Advanced Technology & Sciences (ICAT 2014), Antalya, Turkey, 12–15 August 2014; pp. 1–9. [Google Scholar]
- Bielec, A. PHC: Argon2 on GPU. Openwall. 2015. Available online: http://www.openwall.com/lists/john-dev/2015/08/16/6 (accessed on 28 January 2017).
- Andrade, E.R.; Simplicio, M.A.; Barreto, P.S.L.M.; Santos, P.C.F. Lyra2: Efficient password hashing with high security against time-memory trade-offs. IEEE Trans. Comput. 2016, 65, 3096–3108. [Google Scholar] [CrossRef]
- Simplicio, M.A.; Almeida, L.C.; Andrade, E.R.; Santos, P.C.F.; Barreto, P.S.L.M. The Lyra2 Reference Guide, PHC Submission. 15 January 2015. Available online: https://password-hashing.net/submissions/specs/Lyra2-v3.pdf (accessed on 28 January 2017).






© 2017 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hatzivasilis, G. Password-Hashing Status. Cryptography 2017, 1, 10. https://doi.org/10.3390/cryptography1020010
Hatzivasilis G. Password-Hashing Status. Cryptography. 2017; 1(2):10. https://doi.org/10.3390/cryptography1020010
Chicago/Turabian StyleHatzivasilis, George. 2017. "Password-Hashing Status" Cryptography 1, no. 2: 10. https://doi.org/10.3390/cryptography1020010





