Strong Authentication Scheme Based on Hand Geometry and Smart Card Factors
Abstract
:1. Introduction
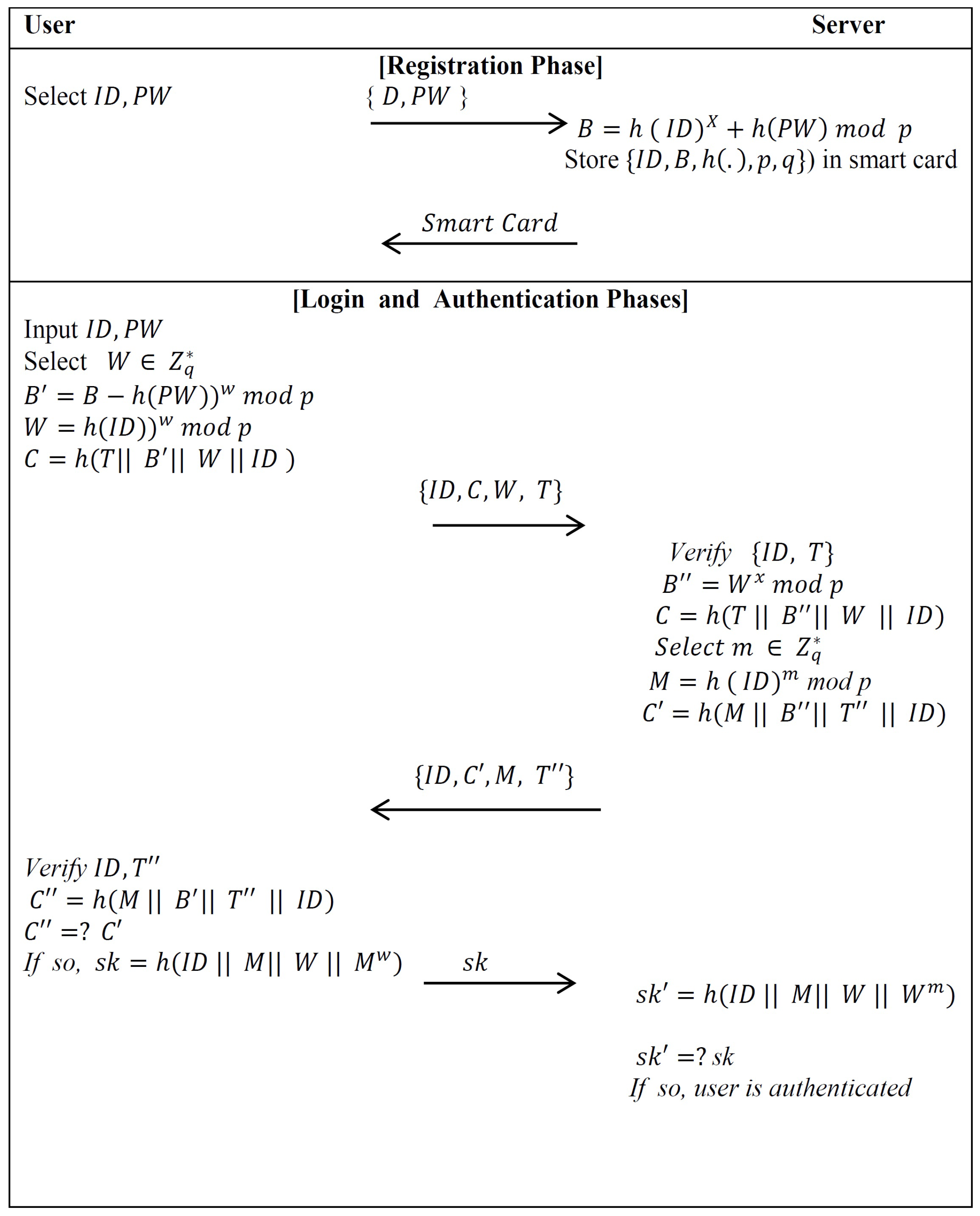
2. The Xu–Zhu–Feng Scheme
2.1. Review of the Xu–Zhu–Feng Scheme
- NotationsIn order to make future references more easy to understand, frequently repeated notations are enumerated below with their descriptions (see Table 1).
- Initial PhaseThe server picks large prime numbers, p and q, such that , and selects its secret key .
- Registration PhaseThe user sends his identity ID and password PW to the authentication server via a secure channel. Then, the server calculates when he receives the registration request message {ID,PW} from the valid user. After that, the server saves the important data into a new smart card and pushes it to the user.
- Login PhaseThe user attaches his smart card to a device reader and enters his ID and PW. The smart card selects a random number , establishes the time-stamp with the current time, and computes the following:.It then submits the login message to the server. However, we notice that the smart card is required to run the modulus exponentiation computation twice in this phase.
- Authentication PhaseAfter receiving the user’s login message at time , the server verifies the identity of the user ID and the time-stamp T by checking , where is a threshold defined in advance. Then, the server calculates and tests whether C is equal to . If the above validations go through effectively, the user is genuine and the server continues with the following procedure. Otherwise, it terminates the login request. The server selects a random number , sets the time-stamp , , and submits the message to the user. After receiving the message, the smart card verifies and and then compares with . If they are equal, the server is valid. Both the user and server compute .
2.2. Cryptanalysis of the Xu–Zhu–Feng Scheme
- ,
- ,
- .
3. Design Issues
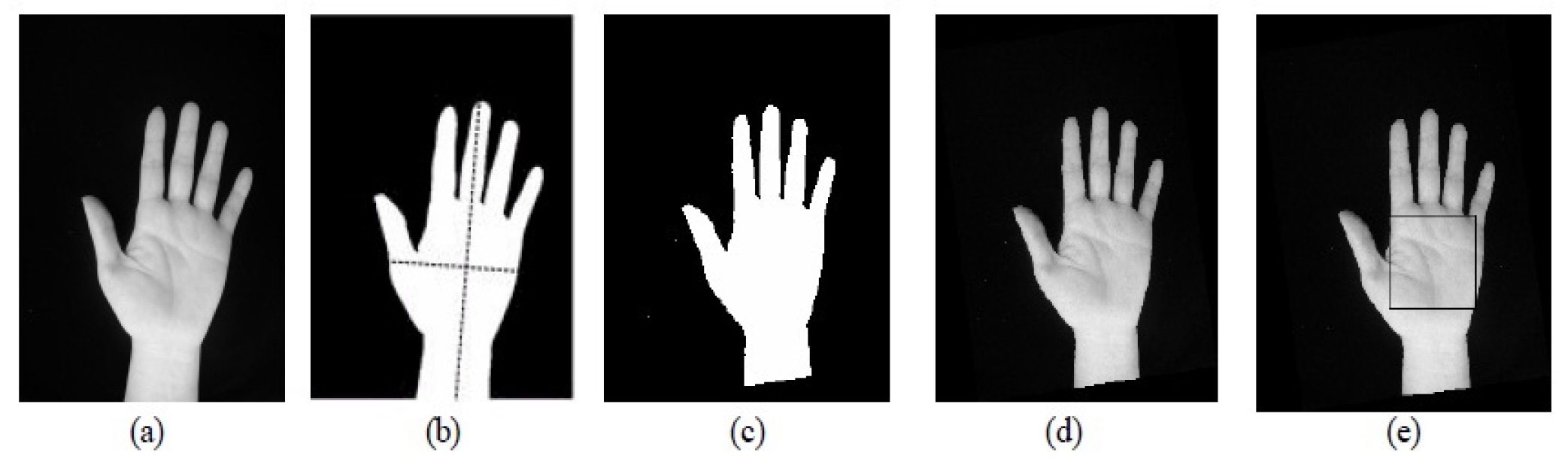
3.1. Feature Extraction of Hand Geometry Images
- (1)
- Lengths connection the base of the hand and tips of finger;
- (2)
- Points viewing the base point of each finger;
- (3)
- Area surrounded by the registered points.
3.2. Our Proposed Scheme for Design Issues
3.3. Comparison
4. Our Proposed Scheme
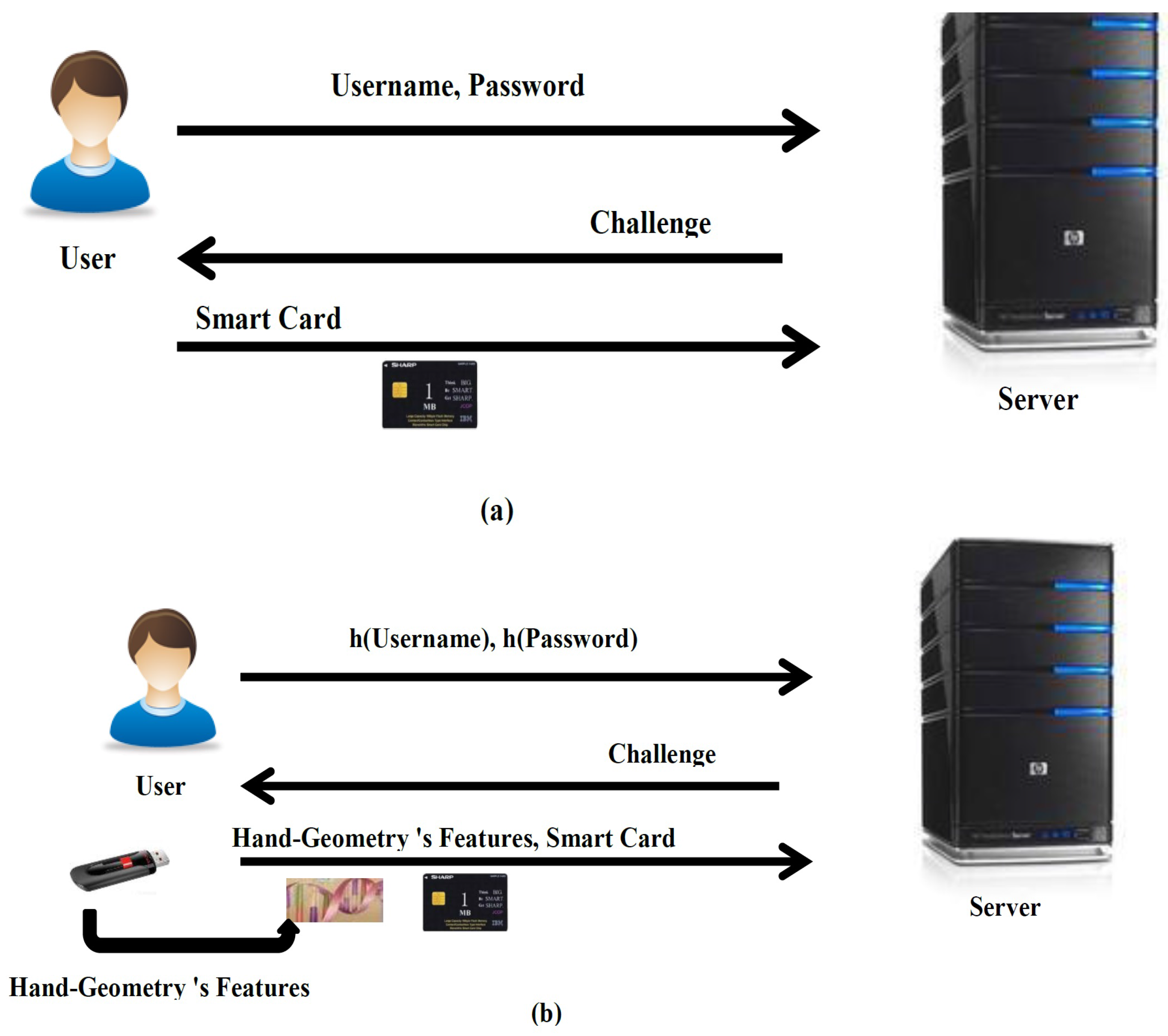
- Registration PhaseIn this phase, everyone that will be registered on the remote server is provided with a smart card and features of hand geometry. To initialize, the user submits his biometric hand geometry , and his hashed password and identity to the remote server over a secure channel. Upon receiving the user’s registration request, the server performs the following operations:
- (1)
- S extracts the features of the user’s hand geometry and computes , where is a secret key kept by S in private;
- (2)
- S saves the data on a new smart card. S sends each of the user’s smart cards and hashes of his personal biometrics (hand-geometry’s features) to over a secure channel;: smart card, ;
- (3)
- saves in his USB.
- Login PhaseWhen the user wishes to login to S, then attaches his smart card in the card reader, his USB in the USB device to read , and inputs his password . The smart card fulfills the following steps:
- (1)
- Compute and ;
- (2)
- Generate a random number and perform the following steps:
- –
- Compute ;
- –
- Calculate , where T is the current time-stamp of the input device;
- –
- Encrypt by using ;
- (3)
- The user’s smart card sends a login request message M to the remote server;Smart card→S: .
- Authentication PhaseUpon receiving the user’s login request message at time , S performs the following computations:
- (1)
- S computes , and decrypts ;
- (2)
- S checks the legitimacy of the time-stamp T. If , then the authenticated server S accepts user’s login request and then executes the next step. Otherwise, S terminates this phase;
- (3)
- S computes , and checks whether is equal to . If so, S accepts the user’s login request;
- (4)
- S computes and sends message to .;
- (5)
- When receives the message at time executes the following steps:
- –
- Check whether . If this does not hold, then overthrows the message and terminates this phase. Otherwise, continues the next step;
- –
- decrypts message by using , computes , and compares a with . If so, decides that the remote server S is authenticated.
- Password Change PhaseWhen wants to change his password from to , runs this phase. The password change phase needs to go through the following steps:
- (1)
- needs to be executed in the above phases login and mutual authentication. The server S authenticates his old password ;
- (2)
- After the successful mutual authentication, enters a new password . Then, the smart card computes and replaces the old with a new .
5. Security Analysis of Our Proposed Scheme
6. Discussion and Comparison with the State-of-the-Art Methods
- C1 :
- Freely chosen password;
- C2 :
- User anonymity;
- C3 :
- Secure password change;
- C4 :
- Session key agreement;
- C5 :
- Mutual authentication;
- C6 :
- No password revealed;
- C7 :
- Revocation by using personal biometrics.
- (1)
- : Time for performing a one-way hash function.
- (2)
- : Time for performing the XOR operation.
- (3)
- : Time for performing a concatenation function.
- (4)
- : Time performing for exponentiation function.
- (5)
- :Time performing for a symmetric encryption function.
- (6)
- :Time performing for a symmetric decryption function.
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Lamport, L. Password Authentication With Insecure Communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Khan, S.H.; Akbar, M.A.; Shahzad, F.; Farooq, M.; Khan, Z. Secure biometric template generation for multi-factor authentication. Pattern Recognit. 2015, 48, 458–472. [Google Scholar] [CrossRef]
- Xu, J.; Zhu, W.T.; Feng, D.G. An improved smart card based password authentication scheme with provable security. Comput. Standards Interfaces 2009, 31, 723–728. [Google Scholar] [CrossRef]
- Acar, T.; Belenkiy, M.; Kupsu, A. Single password authentication. Comput. Netw. 2013, 57, 2597–2614. [Google Scholar] [CrossRef]
- Gao, C.; Chang, C.C.; Sun, C.Y. Chaotic Maps-Based Mutual Authentication and Key Agreement using Smart Cards for Wireless Communications. J. Inf. Hiding Multimed. Signal Process. 2013, 4, 99–109. [Google Scholar]
- Marimuthu, K.; Saravanan, R. A secure remote user mutual authentication scheme using smart cards. J. Inf. Secur. Appl. 2014, 19, 282–294. [Google Scholar]
- Madhusudhan, R.; Mittal, R.C. Dynamic ID-based remote user password authentication schemes using smart cards: A review. J. Netw. Comput. Appl. 2012, 35, 1235–1248. [Google Scholar] [CrossRef]
- Xu, L.; Wu, F. An improved and provable remote user authentication scheme based on elliptic curve cryptosystem with user anonymity. Secur. Commun. Netw. 2015, 8, 245–260. [Google Scholar] [CrossRef]
- Chuang, M.C.; Chen, M.C. An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. Expert Syst. Appl. 2014, 41, 1411–1418. [Google Scholar] [CrossRef]
- Chien, H.Y.; Jan, J.K.; Tseng, Y.M. An efficient and practical solution to remote authentication: Smart card. Comput. Secur. 2002, 21, 372–375. [Google Scholar] [CrossRef]
- Lin, H.Y. Improved chaotic maps-based password-authenticated key agreement using smart cards. Commun. Nonl. Sci. Numer. Simul. 2015, 20, 482–488. [Google Scholar] [CrossRef]
- Awasthi, A.K.; Lal, S. An enhanced remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 2004, 50, 583–586. [Google Scholar] [CrossRef]
- Tang, H.B.; Liu, X.S. Cryptanalysis of a dynamic ID-based remote user authentication with key agreement scheme. Int. J. Commun. Syst. 2012, 25, 1639–1644. [Google Scholar] [CrossRef]
- Das, M.L.; Saxena, A.; Gulati, V.P. A dynamic ID-based remote user authentication scheme. IEEE Trans. Consum. Electron. 2004, 50, 629–631. [Google Scholar] [CrossRef]
- Liao, I.E.; Lee, C.C.; Hwang, M.S. Security enhancement for a dynamic ID-based remote user authentication scheme. In Proceedings of the 2005 Inernational Conference on Next Generation Web Services Practice, Souel, Korea, 22–26 August 2006; pp. 437–440.
- Shih, W.; Hsiang, H.C. Improvement of the secure dynamic ID based remote user authentication scheme for multi-server environment. Comput. Standards Interfaces 2009, 31, 1118–1123. [Google Scholar]
- Lee, N.Y.; Chiu, Y.C. Improved remote authentication scheme with smart card. Comput. Standards Interfaces 2005, 27, 177–180. [Google Scholar] [CrossRef]
- Lee, S.W.; Kim, H.S.; Yoo, K.Y. Improvement of Chien et al.’s remote user authentication scheme using smart cards. Comput. Standards Interfaces 2005, 27, 181–183. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. On the anonymity of two-factor authentication schemes for wireless sensor networks: Attacks, principle and solutions. Comput. Netw. 2014, 73, 41–57. [Google Scholar] [CrossRef]
- Kumar, M. New remote user authentication scheme using smart cards. Trans. IEEE Trans. Consum. Electron. 2004, 50, 597–600. [Google Scholar] [CrossRef]
- Li, C.T.; Lee, C.C.; Weng, C.Y. A dynamic identity-based user authentication scheme for remote login systems. Secur. Commun. Netw. 2015, 8, 3372–3383. [Google Scholar] [CrossRef]
- Khan, M.K.; Kim, S.K.; Alghathbar, K. Cryptanalysis and security enhancement of a more efficient and secure dynamic ID-based remote user authentication scheme. Comput. Commun. 2011, 34, 305–309. [Google Scholar] [CrossRef]
- Otsu, N. A threshold selection method from gray-scale histogram. IEEE Trans. Syst. Man Cyber. Syst. 1978, 9, 62–66. [Google Scholar]
- Luque-Baena, R.M.; Elizondo, D.; Lopez-Rubio, E.; Palomo, E.J.; Watson, T. Assessment of geometric features for individual identification and verification in biometric hand systems. Expert Syst. Appl. 2013, 40, 3580–3594. [Google Scholar] [CrossRef]
- Wang, Y.Y.; Liu, J.Y.; Xiao, F.X.; Dan, J. A more efficient and secure dynamic ID-based remote user authentication scheme. Comput. Commun. 2009, 32, 583–585. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Khan, M.K. An enhanced smart card based remote user password authentication scheme. J. Netw. Comput. Appl. 2013, 36, 1365–1371. [Google Scholar] [CrossRef]
- Yoon, E.J.; Yoo, K.Y. Improving the Dynamic ID-Based Remote Mutual Authentication Scheme. In Meaningful Internet Systems 2006: OTM 2006 Workshops; Meersman, R., Tari, Z., Herrero, P., Eds.; Springer: Berlin, Germany, 2006; pp. 499–507. [Google Scholar]
- Huang, X.; Xiang, Y.; Chonka, A.; Zhou, J.; Deng, R.H. A Generic Framework for Three-Factor Authentication: Preserving Security and Privacy in Distributed Systems. IEEE Trans. Parall. Distrib. Syst. 2011, 22, 1390–1397. [Google Scholar] [CrossRef]
- Huang, X.; Xiang, Y.; Bertino, E.; Zhou, J.; Xu, L. Robust Multi-Factor Authentication for Fragile Communications. IEEE Trans. Depend. Secur. Comput. 2014, 11, 568–581. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C.H. Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Depend. Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. On the usability of two-factor authentication. In Proceedings of the Secure Comm 2014, Beijing, China, 9–11 December 2015; pp. 1–9.
- Wang, D.; Wang, P.; Liu, J. Improved privacy-preserving authentication scheme for roaming service in mobile networks. In Proceedings of 15th IEEE Wireless Communications and Networking Conference (WCNC’2014), Istanbul, Turkey, 6–9 April 2014; pp. 3178–3183.
- Ma, C.G.; Wang, D.; Zhao, S.-D. Security flaws in two improved remote user authentication schemes using smart cards. Int. J. Commun. Syst. 2014, 27, 2215–2227. [Google Scholar] [CrossRef]
- Wang, D.; Ma, C.-G.; Zhang, Q.-M.; Zhao, S.-D. Secure password-based remote user authentication scheme against smart card security breach. J. Netw. 2013, 8, 148–155. [Google Scholar] [CrossRef]
- Wang, D.; Ma, C.-G.; Wang, Y.H. On the security of an improved password authentication scheme based on ECC. In Proceedings of the Third International Conference (ICICA’2012), Chengde, China, 14–16 September 2012; pp. 181–188.
- Hafizul, S.K. Design and analysis of an improved smartcard based remote user password authentication scheme. Int. J. Commun. Syst. 2014. [Google Scholar] [CrossRef]
- Li, C.-T. A new password authentication and user anonymity scheme based on elliptic curve cryptography and smart card. IET Inf. Sec. 2013, 7, 3–10. [Google Scholar] [CrossRef]
- Tsai, J.-L.; Lo, N.-W.; Wu, T.-C. Novel anonymous authentication scheme using smart cards. IEEE Trans. Ind. Inf. 2013, 9, 2004–2013. [Google Scholar] [CrossRef]
- Wang, D.; Wan, N.; Wang, P.; Qing, S. Preserving privacy for free: Efficient and provably secure two-factor authentication scheme with user anonymity. Inf. Sci. 2015, 321, 162–178. [Google Scholar] [CrossRef]
- Kim, T.-H.; Kim, C.-K.; Park, H. Side channel analysis attacks using AM demodulation on commercial smart cards with SEED. J. Syst. Softw. 2012, 85, 2899–2908. [Google Scholar] [CrossRef]
- Liu, J.; Yu, Y.; Standaert, F.-X.; Guo, Z.; Gu, D.; Sun, W.; Ge, Y.; Xie, X. Small Tweaks Do Not Help: Differential Power Analysis of MILENAGE Implementations in 3G/4G USIM Cards. In Proceedings of the 20th European Symposium on Research in Computer Security (ESORICS’2015), Vienna, Austria, 23–25 September 2015; pp. 1–20.


| Symbol | Description |
|---|---|
| Identity of user A. | |
| Identity of user B. | |
| Password of user A. | |
| The one-time random number generated by the user A. | |
| The time-stamp of user A. | |
| The time-stamp of server S. | |
| Threshold’s time defined in advance by the system. | |
| h(.) | A cryptography one-way hash function. |
| The message M encrypted by session key K. | |
| x mod p | The remainder of x divided by p. |
| ⊕ | The bitwise XOR operation. |
| The concatenation operation. | |
| p,q | The two large prime numbers. |
| The multiplicative set of . | |
| The ring of integers modulo q. |
| Symbol | Description |
|---|---|
| A legitimate user . | |
| S | A trustworthy server. |
| Identity of user . | |
| Password of user . | |
| Hashed password of user . | |
| Hashed identity of user . | |
| Hand geometry of user . | |
| Features of hand geometry. | |
| A secret key kept by S in private. | |
| h(.) | A cryptography one-way hash function. |
| The one-time random number generated by the user . | |
| The one-time key generated for each user’s login request. | |
| The time-stamp of the user . | |
| The time-stamp of server S. | |
| Threshold’s time defined in advance by the system. | |
| Symmetric encryption function based on key . | |
| M | Login request message from the user to the remote server S. |
| Other miscellaneous values that are applied in the verification. | |
| ⊕ | The bitwise XOR operation. |
| The concatenation operation. |
| Scheme | C1 | C2 | C3 | C4 | C5 | C6 | C7 |
|---|---|---|---|---|---|---|---|
| Our Scheme | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Das et al. [14] | Yes | Yes | No | No | No | No | No |
| Liao et al. [15] | Yes | Yes | Yes | No | Yes | Yes | No |
| Wang et al. [25] | No | No | No | No | Yes | No | No |
| Yoon and Yoo [27] | Yes | Yes | Yes | No | Yes | Yes | No |
| Khan et al. [26] | Yes | No | Yes | No | Yes | Yes | No |
| Xu–Zhu–Feng [3] | Yes | No | Yes | Yes | Yes | No | No |
| Scheme | Registration Phase | Login & Authentication Phase | Total Cost |
|---|---|---|---|
| Our Scheme | |||
| Das et al. [14] | |||
| Liao et al. [15] | |||
| Wang et al. [25] | |||
| Yoon and Yoo [27] | |||
| Khan et al. [26] | |||
| Xu–Zhu–Feng [3] |
| Scheme | From User to Server | From Server to User | Total Communication Cost (Numbers of Bits) | ||
|---|---|---|---|---|---|
| Login Message | Cost (Bits) | Mutual Message | Cost (Bits) | ||
| Our Scheme | 384 | 192 | 576 | ||
| Das et al. [14] | 448 | - | - | 448 | |
| Liao et al. [15] | 448 | 192 | 640 | ||
| Wang et al. [25] | 448 | 192 | 640 | ||
| Khan et al. [26] | 384 | 192 | 576 | ||
| Yoon and Yoo [27] | 448 | 192 | 640 | ||
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yassin, A.A.; Yao, J.; Han, S. Strong Authentication Scheme Based on Hand Geometry and Smart Card Factors. Computers 2016, 5, 15. https://doi.org/10.3390/computers5030015
Yassin AA, Yao J, Han S. Strong Authentication Scheme Based on Hand Geometry and Smart Card Factors. Computers. 2016; 5(3):15. https://doi.org/10.3390/computers5030015
Chicago/Turabian StyleYassin, Ali A., Jian Yao, and Shiyao Han. 2016. "Strong Authentication Scheme Based on Hand Geometry and Smart Card Factors" Computers 5, no. 3: 15. https://doi.org/10.3390/computers5030015
APA StyleYassin, A. A., Yao, J., & Han, S. (2016). Strong Authentication Scheme Based on Hand Geometry and Smart Card Factors. Computers, 5(3), 15. https://doi.org/10.3390/computers5030015






