LEO Satellite Downlink Distributed Jamming Optimization Method Using a Non-Dominated Sorting Genetic Algorithm
Abstract
:1. Introduction
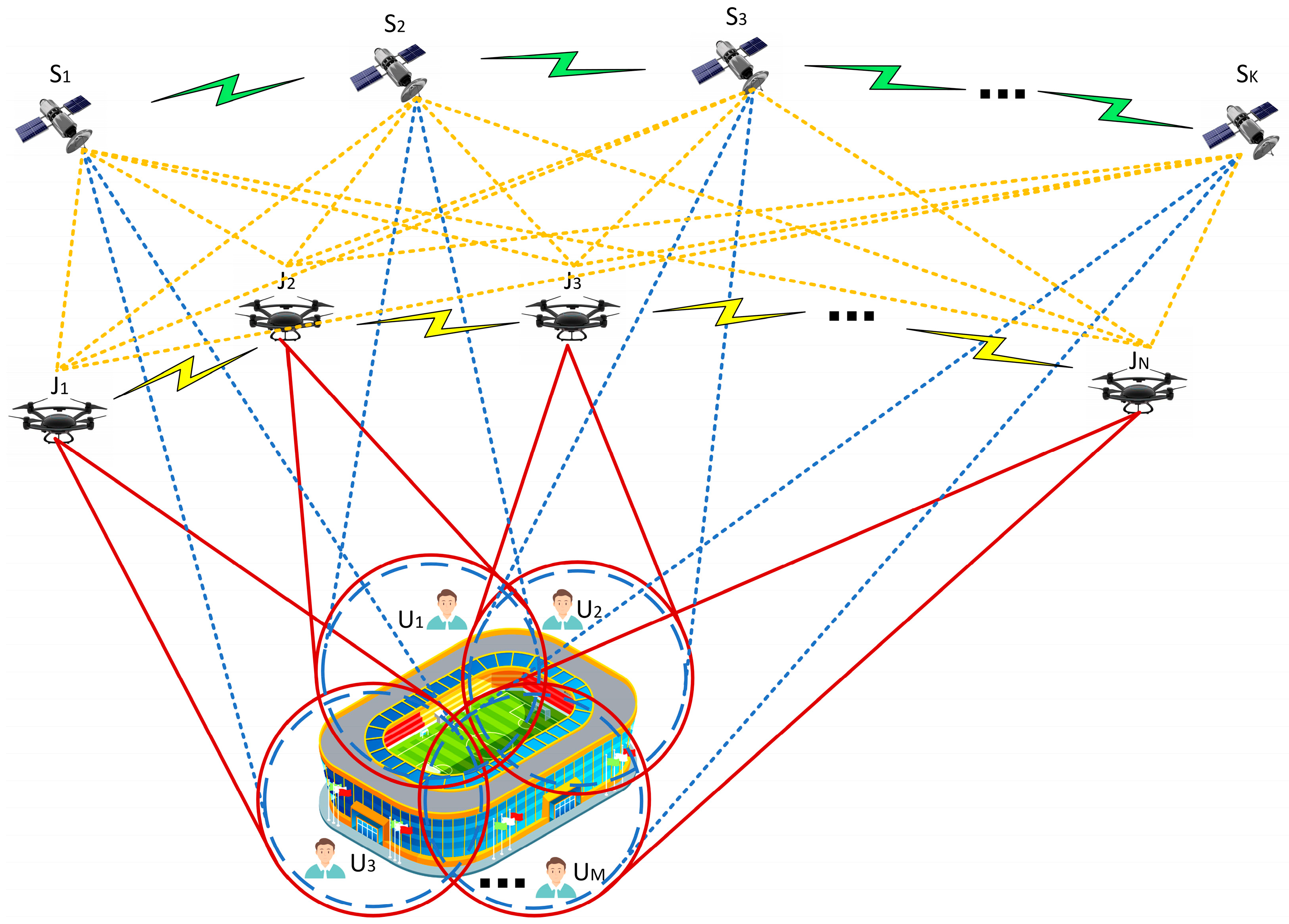
- This study proposes a distributed jamming cooperative control model. Distributed jammers determine the specific orientation of visible satellites through intercepting LEO satellite signals, exchange information with surrounding distributed jammers, continuously update and adjust their positions in real time, and achieve continuous switching for different LEO satellites with high speeds.
- This study utilizes the third-generation non-dominated sorting genetic algorithm for multi-objective optimization, optimizing jamming signals in the power, time, and frequency domains to maintain solution set diversity; improve optimization efficiency; avoid the algorithm falling into local optima; and jam the downlink of LEO satellites.
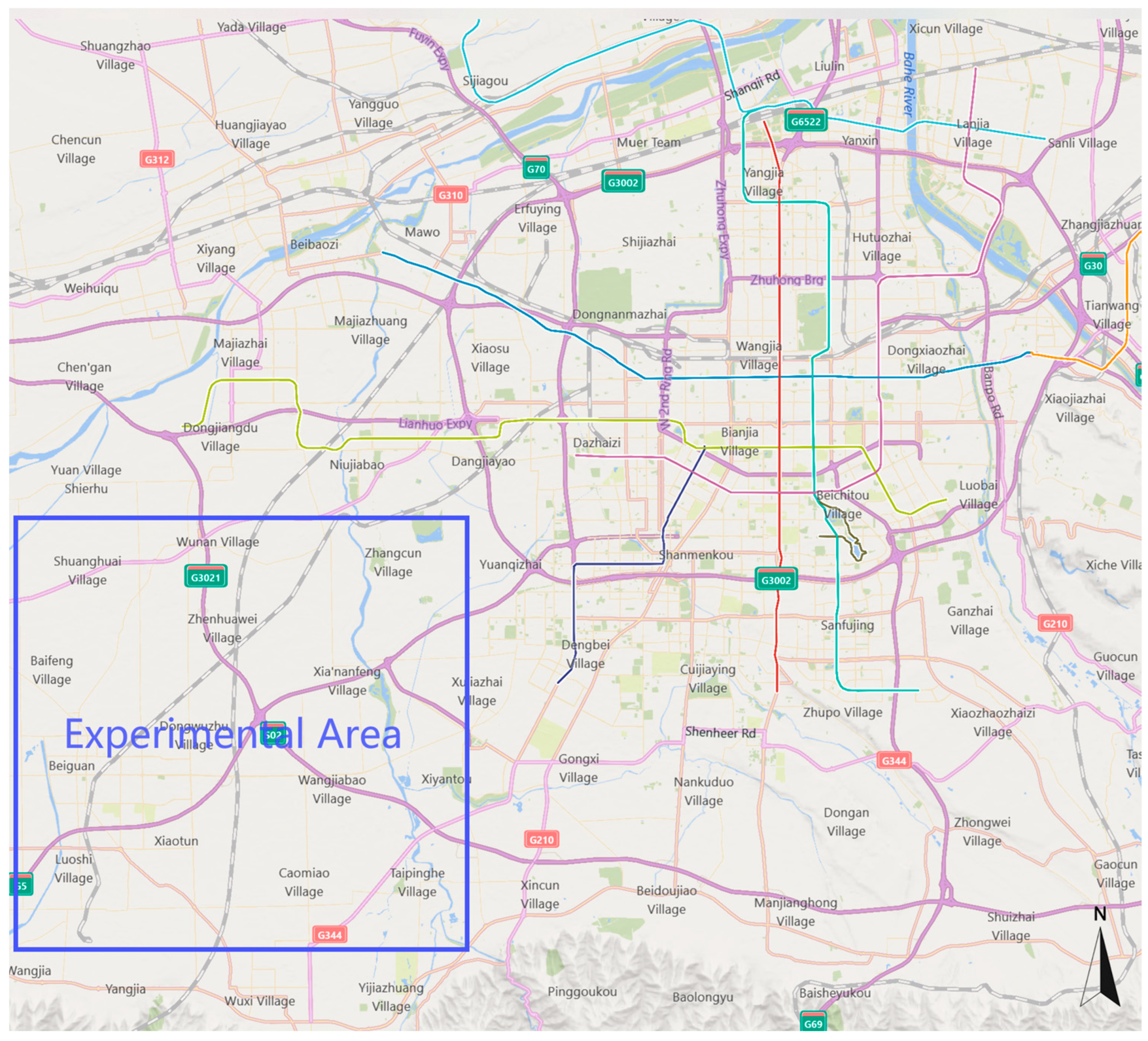
- This study constructs a jamming experimental comparison platform and implements it as hardware. Jamming optimization tests are conducted, targeting the LEO constellation of the China Satellite Network in the southwest outskirts of Xi’an, China, in order to verify the effectiveness of the proposed method for jamming the downlink of LEO satellites compared to existing methods.
2. Related Work
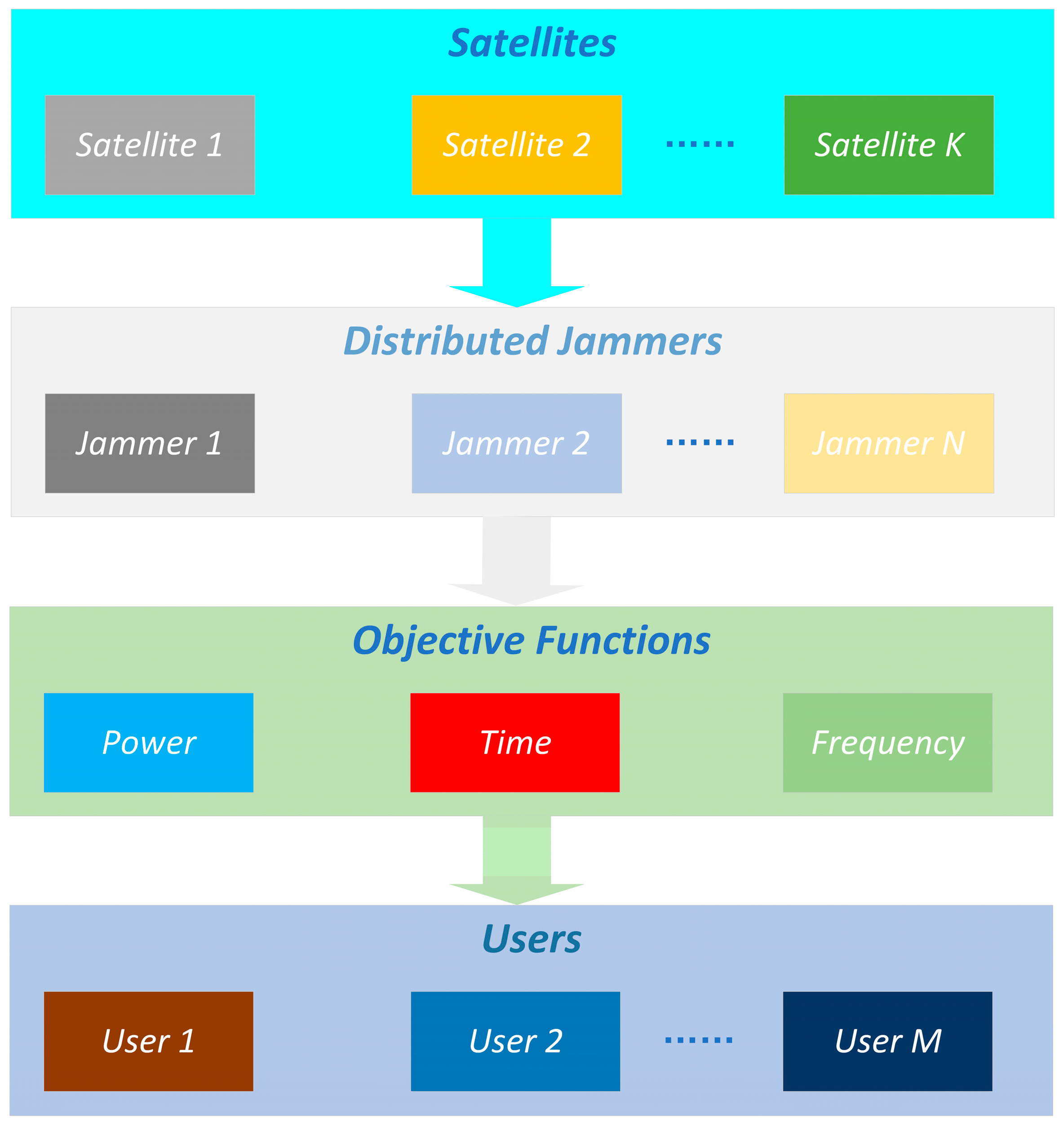
3. Distributed Jamming System Model for LEO Constellation Downlink
3.1. Jamming Evaluation Metrics
3.1.1. Total Jamming Power
3.1.2. Time Delay
3.1.3. Frequency Compensation
3.1.4. Jamming Coverage Rate
3.2. Multi-Objective Optimization Objective Functions and Constraints
4. Third-Generation Non-Dominated Sorting Genetic Algorithm
4.1. Algorithm Flow
4.1.1. Population Division Based on Non-Dominated Layers
- Perform non-dominated sorting on , resulting in multiple non-dominated layers .
- Starting from , construct a new population by sequentially adding members from non-dominated layers ranked 1 to . If , set directly. If , eliminate solutions from layers beyond . The remaining part for the next generation () is selected from , and these solutions constitute .
4.1.2. Determination of Reference Points on the Hyperplane
- Let be a two-dimensional variable, taking values from the set .
- For each (the th element of the th combination in ), .
- Use as the set of jamming reference points and obtain coordinates for each objective function:
4.1.3. Adaptive Normalization of Population Individuals
- Find the ideal point.
- 2.
- Calculate extreme points and construct hyperplanes.
- 3.
- Objective Adaptive Normalization.
4.1.4. Association Operation
4.1.5. Individual Retention
- Select the jamming reference point with the least number of associations. If there are multiple such jamming reference points, randomly choose one . represents the individuals associated with jamming reference point in the layer.
- If is empty, re-select the jamming reference point. If is not empty, check whether the number of associations in all non-dominated layers before with jamming reference point is 0. If , select the individual with the minimum distance to from for the next generation. If , randomly choose an individual from for the next generation.
- Repeat the operation until the size of the next generation equals .
5. Experimental Analysis
- The first scenario compares the target function with the optimal solution set;
- The second scenario compares coverage optimization over time;
- The third scenario compares the success rate of jamming within a certain region.
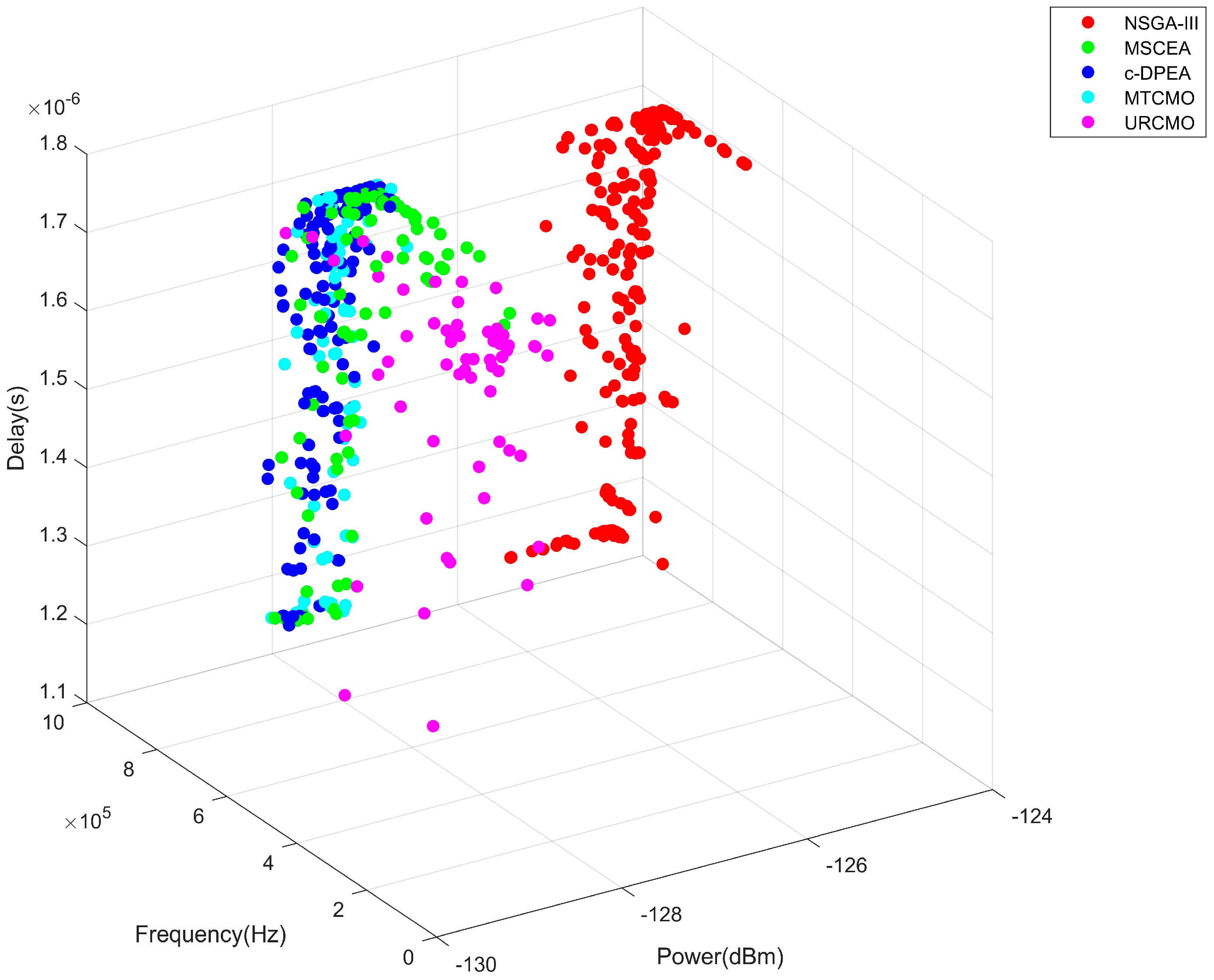
5.1. Objective Function and Optimal Solution Set Optimization
5.1.1. Objective Function Comparison
5.1.2. Dominant Solution Set Comparison
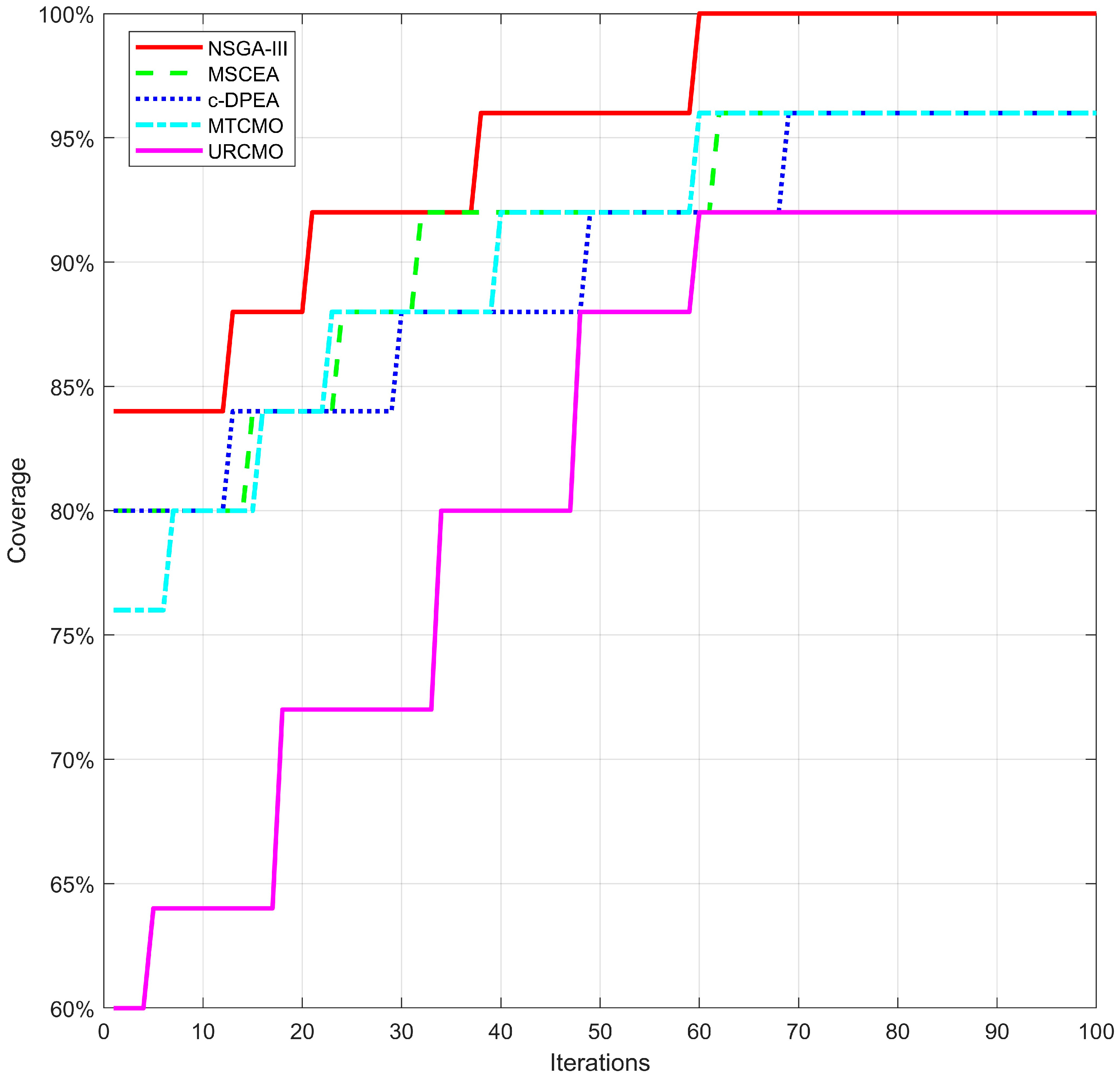
5.2. Coverage Optimization
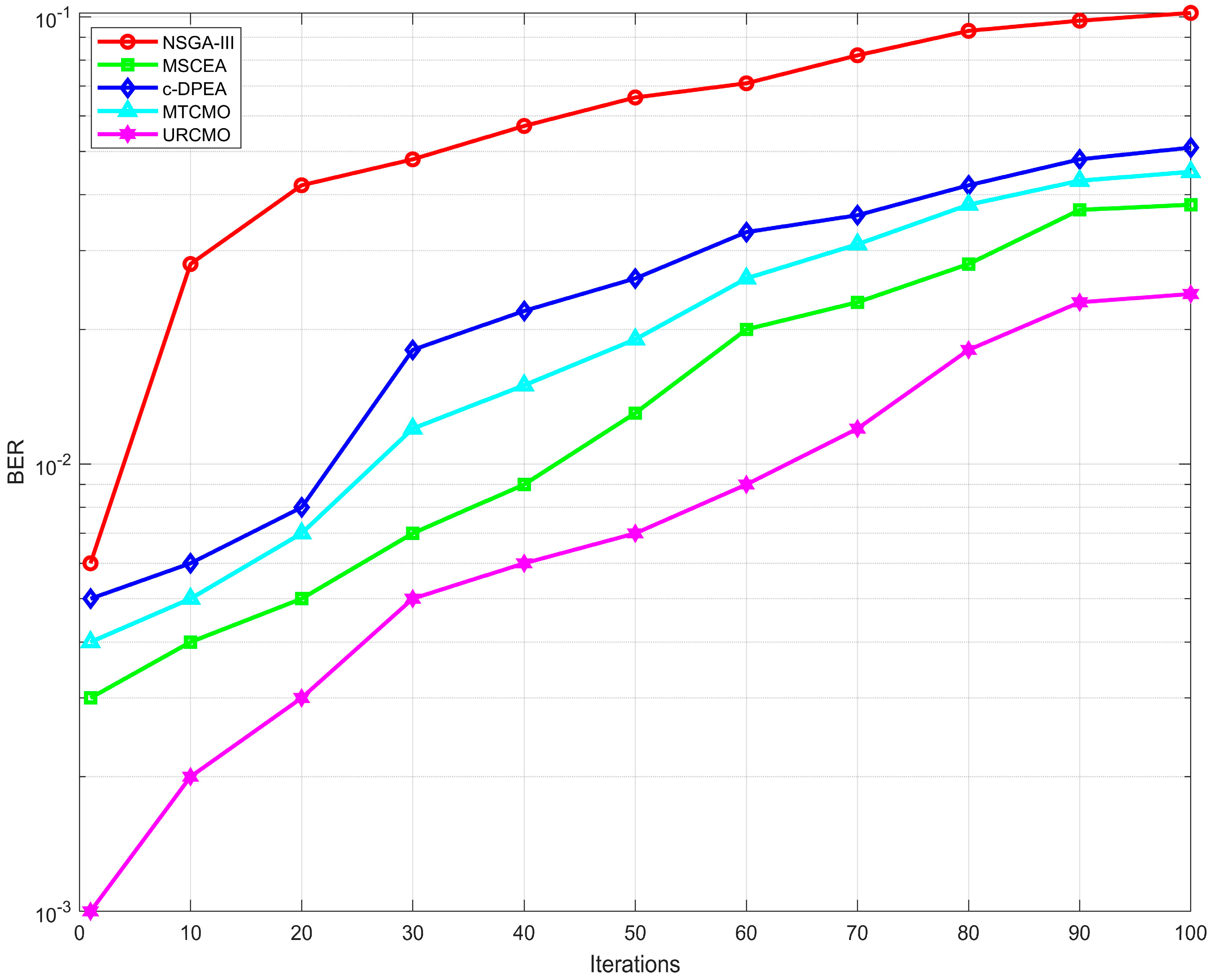
5.3. Jamming Success Rate Optimization
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Lin, Z.; Niu, H.; An, K.; Wang, Y.; Zheng, G.; Chatzinotas, S.; Hu, Y. Refracting RIS-aided hybrid satellite-terrestrial relay networks: Joint beamforming design and optimization. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 3717–3724. [Google Scholar] [CrossRef]
- Lin, X.; Cioni, S.; Charbit, G.; Chuberre, N.; Hellsten, S.; Boutillon, J.-F. On the path to 6G: Embracing the next wave of low Earth orbit satellite access. IEEE Commun. Mag. 2021, 59, 36–42. [Google Scholar] [CrossRef]
- Yue, P.; An, J.; Zhang, J.; Ye, J.; Pan, G.; Wang, S.; Xiao, P.; Hanzo, L. Low earth orbit satellite security and reliability: Issues, solutions, and the road ahead. IEEE Commun. Surv. Tutor. 2023, 25, 1604–1652. [Google Scholar] [CrossRef]
- An, K.; Lin, M.; Ouyang, J.; Zhu, W.-P. Secure transmission in cognitive satellite terrestrial networks. IEEE J. Sel. Areas Commun. 2016, 34, 3025–3037. [Google Scholar] [CrossRef]
- An, K.; Liang, T.; Zheng, G.; Yan, X.; Li, Y.; Chatzinotas, S. Performance limits of cognitive-uplink FSS and terrestrial FS for Ka-band. IEEE Trans. Aerosp. Electron. Syst. 2018, 55, 2604–2611. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; Champagne, B.; Zhu, W.-P.; Al-Dhahir, N. Secure and energy efficient transmission for RSMA-based cognitive satellite-terrestrial networks. IEEE Wirel. Commun. Lett. 2020, 10, 251–255. [Google Scholar] [CrossRef]
- Monzon Baeza, V.; Ortiz, F.; Herrero Garcia, S.; Lagunas, E. Enhanced Communications on Satellite-Based IoT Systems to Support Maritime Transportation Services. Sensors 2022, 22, 6450. [Google Scholar] [CrossRef]
- Alrefaei, F.; Alzahrani, A.; Song, H.; Alrefaei, S. A survey on the jamming and spoofing attacks on the unmanned aerial vehicle networks. In Proceedings of the 2022 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Toronto, ON, Canada, 1–4 June 2022; pp. 1–7. [Google Scholar]
- Shi, Q.; Wang, Y.; Wang, C.; Feng, Q.; Yuan, N. A novel deceptive and blanket joint jammer. In Proceedings of the 2017 IEEE International Conference on Signal Processing, Communications and Computing (ICSPCC), Xiamen, China, 22–25 October 2017; pp. 1–4. [Google Scholar]
- Yang, Z.; Zhang, B.; Zhang, K.; Shi, J.; Li, Z.; Huang, C.; Zhou, Q. Efficient Waveform Design with Jamming Characteristics for Precision Electronic Warfare. Signal Process. 2023, 212, 109162. [Google Scholar] [CrossRef]
- Pärlin, K.; Riihonen, T.; Le Nir, V.; Bowyer, M.; Ranstrom, T.; Axell, E.; Asp, B.; Ulman, R.; Tschauner, M.; Adrat, M. Full-duplex tactical information and electronic warfare systems. IEEE Commun. Mag. 2021, 59, 73–79. [Google Scholar] [CrossRef]
- Meng, L.; Yang, L.; Yang, W.; Zhang, L. A Survey of GNSS Spoofing and Anti-Spoofing Technology. Remote Sens. 2022, 14, 4826. [Google Scholar] [CrossRef]
- Wu, Z.; Zhang, Y.; Yang, Y.; Liang, C.; Liu, R. Spoofing and anti-spoofing technologies of global navigation satellite system: A survey. IEEE Access 2020, 8, 165444–165496. [Google Scholar] [CrossRef]
- Tedeschi, P.; Sciancalepore, S.; Di Pietro, R. Satellite-based communications security: A survey of threats, solutions, and research challenges. Comput. Netw. 2022, 216, 109246. [Google Scholar] [CrossRef]
- Ni, S.; Cui, J.; Cheng, N.; Liao, Y. Detection and elimination method for deception jamming based on an antenna array. Int. J. Distrib. Sens. Netw. 2018, 14, 1550147718774466. [Google Scholar] [CrossRef]
- Wang, H.; Chang, Q.; Xu, Y. Deception jamming detection based on beam scanning for satellite navigation systems. IEEE Commun. Lett. 2021, 25, 2703–2707. [Google Scholar] [CrossRef]
- Meggs, R.; Watson, R. Spoofing and Jamming of GNSS Signals: Are They Real and What Can We Do about Them? In Proceedings of the Conference Proceedings of iSCSS, Delft, The Netherlands, 6–8 October 2020. [Google Scholar]
- Wang, P.; Lu, X.; Wang, R. Research on Blanket Jamming to Beidou Navigation Signals Based on BOC Modulation. Int. J. Commun. Netw. Syst. Sci. 2016, 9, 135–144. [Google Scholar] [CrossRef]
- Xu, R.; Hu, Y.H.; Zhang, T.; Zhang, F. Research on Effect of Blanket Jamming on GNSS Signal. Adv. Mater. Res. 2014, 846, 956–961. [Google Scholar] [CrossRef]
- Silva Lorraine, K.J.; Ramarakula, M. A comprehensive survey on GNSS interferences and the application of neural networks for anti-jamming. IETE J. Res. 2023, 69, 4286–4305. [Google Scholar] [CrossRef]
- Dovis, F. GNSS Interference Threats and Countermeasures; Artech House: Sydney, NSW, Australia, 2015. [Google Scholar]
- Garcia-Pena, A.; Julien, O.; Macabiau, C.; Mabilleau, M.; Durel, P. GNSS degradation model in presence of continuous wave and pulsed interference. Navigation 2021, 68, 75–91. [Google Scholar] [CrossRef]
- Qiao, J.; Lu, Z.; Lin, B.; Song, J.; Xiao, Z.; Wang, Z.; Li, B. A survey of GNSS interference monitoring technologies. Front. Phys. 2023, 11, 1133316. [Google Scholar] [CrossRef]
- Lei, Z.; Ding, P.; Zheng, W.; Fei, X.; Fan, H. UAV Countermeasure Technology Based on Partial-band Noise Jamming. In Proceedings of the 2021 33rd Chinese Control and Decision Conference (CCDC), Kunming, China, 22–24 May 2021; pp. 1456–1461. [Google Scholar]
- Karpe, R.V.; Kulkarni, S. Software defined radio based global positioning system jamming and spoofing for vulnerability analysis. In Proceedings of the 2020 International Conference on Electronics and Sustainable Communication Systems (ICESC), Coimbatore, India, 2–4 July 2020; pp. 881–888. [Google Scholar]
- Wang, Z.; Wang, H.; Cao, N. Research on Spoofing Jamming of Integrated Navigation System on UAV. In Proceedings of the Artificial Intelligence and Security: 7th International Conference, ICAIS 2021, Dublin, Ireland, 19–23 July 2021; pp. 3–13. [Google Scholar]
- Li, X.; Chen, L.; Lu, Z.; Wang, F.; Liu, W.; Xiao, W.; Liu, P. Overview of Jamming Technology for Satellite Navigation. Machines 2023, 11, 768. [Google Scholar] [CrossRef]
- Youda, W.; Pengcheng, M.A.; Junwei, N.; Guangfu, S. Study of Multi-Station Retransmission Spoofing Methods Based on Protection of Fixed Target. GNSS World China 2016, 41, 60–65. [Google Scholar]
- Tang, C.; Ding, J.; Qi, H.; Zhang, L. Smart forwarding deceptive jamming distribution optimal algorithm. IET Radar Sonar Navig. 2024, 1–12. [Google Scholar] [CrossRef]
- Wang, Y.; Sun, F.; Wang, X.; Hao, J.; Xiao, K. Full-domain collaborative deployment method of multiple interference sources and evaluation of its deployment effect. Def. Technol. 2023, 32, 572–595. [Google Scholar] [CrossRef]
- Hao, Z.; Wang, X.; Wang, J. A Study of Jamming Resource Allocation Based on a Hyperheuristic Framework. Res. Sq. 2022; preprint. [Google Scholar] [CrossRef]
- Fang, F.; Chunming, Y.; Haibo, L. Jammer Placement Algorithm Based on Particle Swarm Optimization. J. Syst. Simul. 2019, 31, 1101–1110. [Google Scholar] [CrossRef]
- Xinxin, Z.; Chengjun, G.; Yawen, C. Optimal Design of Interference Source Based on Ant Colony Algorithm. GNSS World China 2017, 42, 20. [Google Scholar] [CrossRef]
- Luo, Z.; Deng, M.; Yao, Z.; Leng, X.; Chen, Y. Distributed blanket jamming resource scheduling for satellite navigation based on particle swarm optimization and genetic algorithm. In Proceedings of the 2020 IEEE 20th International Conference on Communication Technology (ICCT), Nanning, China, 28–31 October 2020; pp. 611–616. [Google Scholar]
- Ye, F.; Che, F.; Gao, L. Multiobjective Cognitive Cooperative Jamming Decision-Making Method Based on Tabu Search-Artificial Bee Colony Algorithm. Int. J. Aerosp. Eng. 2018, 2018, 7490895. [Google Scholar] [CrossRef]
- Qingwen, Q.; Wenfeng, D.; Meiqing, L.; Yang, Y. Cooperative jamming resource allocation of UAV swarm based on multi-objective DPSO. In Proceedings of the 2018 Chinese Control and Decision Conference (CCDC), Shenyang, China, 9–11 June 2018; pp. 5319–5325. [Google Scholar]
- Maseng, T.; Bakken, P. A Stochastic Dynamic Model of Rain Attenuation. IEEE Trans. Commun. 1981, 29, 660–669. [Google Scholar] [CrossRef]
- Baeza, V.M.; Lagunas, E.; Al-Hraishawi, H.; Chatzinotas, S. An Overview of Channel Models for NGSO Satellites. In Proceedings of the 2022 IEEE 96th Vehicular Technology Conference (VTC2022-Fall), London, UK, 26–29 September 2022; pp. 1–6. [Google Scholar]




| Parameter | Value |
|---|---|
| LEO Satellite Frequency Bands | 37.5–42.5 GHz |
| Altitude of LEO Satellites | 900 km |
| Number of Visible LEO Satellites | 11 |
| Number of Jammers | 20 |
| Altitude of Jammers | 10–20 km |
| Jamming Radius | 20 km |
| Area Size | |
| Number of Target Central Points | 25 |
| Population Size | 1000 |
| Maximum Iteration Count | 100 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tang, C.; Ding, J.; Zhang, L. LEO Satellite Downlink Distributed Jamming Optimization Method Using a Non-Dominated Sorting Genetic Algorithm. Remote Sens. 2024, 16, 1006. https://doi.org/10.3390/rs16061006
Tang C, Ding J, Zhang L. LEO Satellite Downlink Distributed Jamming Optimization Method Using a Non-Dominated Sorting Genetic Algorithm. Remote Sensing. 2024; 16(6):1006. https://doi.org/10.3390/rs16061006
Chicago/Turabian StyleTang, Chengkai, Jiawei Ding, and Lingling Zhang. 2024. "LEO Satellite Downlink Distributed Jamming Optimization Method Using a Non-Dominated Sorting Genetic Algorithm" Remote Sensing 16, no. 6: 1006. https://doi.org/10.3390/rs16061006






