Securing Access to Internet of Medical Things Using a Graphical-Password-Based User Authentication Scheme
Abstract
:1. Introduction
2. Literature Review
2.1. Graphical Authentication Schemes
2.2. Authentication in IoMT
- Firstly, there is limited work on creating, managing, and moving cryptographic keys in resource-constrained environments, which has remained a challenge in security architectures.
- Secondly, the IoT needs to improve its usability and user interface to make security solutions more efficient. Neglecting end users in the creation of security solutions has resulted in a gap in usability and utility in security standards.
- Thirdly, there is still a need for exploration of end-to-end user authentication in the context of IoT infrastructures and limited resource availability. Current security standards and authentication techniques have been limited to certain security threats, ignoring other potential attacks such as cloning, node compromise, desynchronization, and masquerading.
- Finally, revamping authentication techniques for different types of IoT users can improve the overall security and privacy of the platform, maintaining users’ interest in keeping themselves secure. Updating security standards, specifically authentication techniques, is crucial for enhancing the overall security of the IoT platform.
| Study | Main Contributions | Attacks Countered | Limitations |
|---|---|---|---|
| [77] | An ECG authentication technique is proposed using the method of extracting Legendre polynomials. Additionally, a multilayer perception neural network is employed for training, recognition, and authentication, which utilizes ECG signals. | Eavesdropping, replay, and man-in-the-middle attacks | The system does not consider the possible inaccuracies that may occur during the acquisition of ECG signals. Additionally, security evaluations that go beyond the scope of machine learning should be carried out. |
| [78] | An advanced three-factor authentication system is designed particularly for remote patient monitoring using wireless sensor networks (WSNs). The proposed approach aims to provide enhanced security to protect sensitive patient information during remote monitoring. To ensure the security of the proposed approach, an AVIS PA tool is used for formal security analysis. Overall, this approach is claimed to ensure the confidentiality, integrity, and availability of the patient’s data. | DOS, Reply, password guessing, smart card loss attacks, etc. | The cost of communication may be relatively high, but it has been thoroughly evaluated. |
| [79] | In order to enhance the efficiency of data transfer and improve overall throughput, a layered framework is proposed. This framework, spark, not only optimizes data transfer but also adds a layer of security and authentication, ensuring the safety and integrity of the transferred data. The proposed framework architecture is designed to transmit sensitive information securely. The added layers prevent unauthorized access to private data, thus making the data transfer more reliable, secure, and efficient. | Insider attack | Network simulations are employed to analyze the data transmission such as ECG. However, there is no information on the security and privacy analysis being performed. |
| [80] | A service-oriented structure is proposed, allowing for dynamic security elements to be implemented. This approach adapts to the specific medical services being provided at remote locations and continuously adjusts the level of security based on the service being performed. The dynamic approach ensures that the level of security is always appropriate for any specific medical service. Additionally, this approach improves scalability and flexibility by supporting various medical services and providing appropriate security measures. | Spoofing, device masquerade, eavesdropping, and DoS attacks | Only a simple assessment and security analysis without disclosure of its details have been conducted. Both formal and informal security evaluations were supposed to be carried out. |
| [81] | An authentication system is designed that works with the combination of cryptographic mechanisms, such as symmetric encryption, bitwise exclusive-OR operator, and one-way hash function, to deliver authentication and authorization features. Using these cryptographic mechanisms ensures the protection of sensitive information and addresses issues of authentication, integrity, privacy, and nonrepudiation. The authors claim that by using these cryptographic mechanisms, the system can provide a secure method for identity authentication and authorization, making it a reliable and trustable solution for access control in the cloud. This approach provides a secure, reliable, and efficient way for the user to access the service, data, and system through the cloud. | Offline password guessing, replay, impersonation, man-in-the-middle, andinsider attacks | In an emergency, it can be challenging to access information that has been overly secured. Moreover, if an attacker manages to obtain a patient’s mobile device or spoofs the IMEI on their cell phone, they may enter the system without authorization. |
| [83] | A system is proposed to increase the efficiency and security of data storage and transmission. It utilizes a scalable and efficient authentication technique involving an agent dedicated to encryption. However, this approach has some limitations, such as increased computational and communication costs due to multiple servers, which can lead to a less efficient system. Additionally, the lack of data headers for transmission may cause additional overhead costs, which can impact the system’s overall performance. | Brute force, man-in-the-middle, and dimming | The overall computational and communication expense of the system may be high due to the use of multiple servers in the proposed architecture. The data headers for transmission were not found to be labeled, which can later result in extra computational overhead. |
3. Motivation
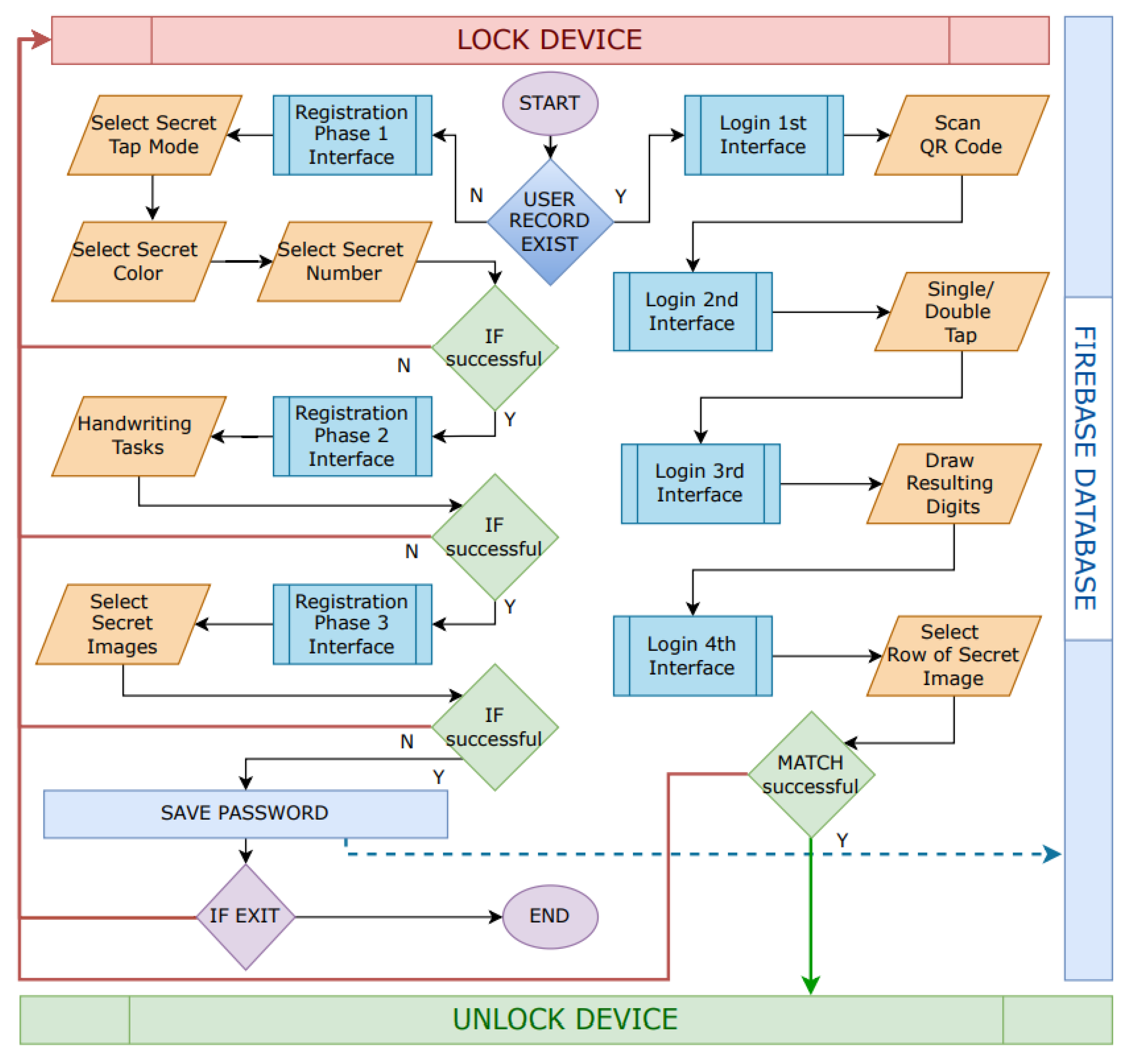
4. Proposed Solution
4.1. Architecture
4.2. Development
4.3. Algorithms
4.3.1. Registration Phase
| Algorithm 1 Registration Phase |
(, , , , ) Procedure: Registration Phase
|
4.3.2. Authentication Phase
| Algorithm 2 Authentication Phase |
(ACCESS GRANTED/ACCESS DENIED) Procedure: Authentication Phase
|
5. Methods
5.1. Sampling
5.2. Experiments
5.3. Hypotheses
5.3.1. Null Hypotheses
- Our proposed authentication technique and simple authentication techniques available on smartphones have no significant difference in overall quality.
- Our proposed authentication technique and simple authentication techniques available on smartphones have no significant difference in system quality.
- Our proposed authentication technique and simple authentication techniques available on smartphones have no significant difference in information quality.
- Our proposed authentication technique and simple authentication techniques available on smartphones have no significant difference in interface quality.
5.3.2. Alternate Hypotheses
- Our proposed authentication technique has significantly better overall quality compared to simple authentication techniques available on smartphones.
- Our proposed authentication technique has significantly better system quality compared to simple authentication techniques available on smartphones.
- Our proposed authentication technique has significantly better information quality compared to simple authentication techniques available on smartphones.
- Our proposed authentication technique has significantly better interface quality compared to simple authentication techniques available on smartphones.
6. Results and Analysis
7. Discussion
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Roy, M.; Chowdhury, C.; Aslam, N. Designing Transmission Strategies for Enhancing Communications in Medical IoT Using Markov Decision Process. Sensors 2018, 18, 4450. [Google Scholar] [CrossRef] [Green Version]
- Vishnu, S.; Ramson, S.J.; Jegan, R. Internet of Medical Things (IoMT)—An overview. In Proceedings of the 2020 5th International Conference on Devices, Circuits and Systems (ICDCS), Coimbatore, India, 5–6 March 2020; pp. 101–104. [Google Scholar] [CrossRef]
- Navarro, V. Assessment of the world health report 2000. Lancet 2000, 356, 1598–1601. [Google Scholar] [CrossRef]
- Aghdam, Z.N.; Rahmani, A.M.; Hosseinzadeh, M. The role of the Internet of Things in healthcare: Future trends and challenges. Comput. Methods Programs Biomed. 2021, 199, 105903. [Google Scholar] [CrossRef]
- Ketu, S.; Mishra, P.K. Internet of Healthcare Things: A contemporary survey. J. Netw. Comput. Appl. 2021, 192, 103179. [Google Scholar] [CrossRef]
- Ahmad, M.O.; Siddiqui, S.T. The Internet of Things for Healthcare: Benefits, Applications, Challenges, Use Cases and Future Directions. In Advances in Data and Information Sciences; Springer: Berlin/Heidelberg, Germany, 2022; pp. 527–537. [Google Scholar]
- Mohamad Jawad, H.H.; Bin Hassan, Z.; Zaidan, B.B.; Mohammed Jawad, F.H.; Mohamed Jawad, D.H.; Alredany, W.H.D. A Systematic Literature Review of Enabling IoT in Healthcare: Motivations, Challenges, and Recommendations. Electronics 2022, 11, 3223. [Google Scholar] [CrossRef]
- Ahmadi, H.; Arji, G.; Shahmoradi, L.; Safdari, R.; Nilashi, M.; Alizadeh, M. The application of internet of things in healthcare: A systematic literature review and classification. Univers. Access Inf. Soc. 2019, 18, 837–869. [Google Scholar] [CrossRef]
- Da Xu, L.; He, W.; Li, S. Internet of things in industries: A survey. IEEE Trans. Ind. Inform. 2014, 10, 2233–2243. [Google Scholar]
- Ashton, K. That ‘internet of things’ thing. RFID J. 2009, 22, 97–114. [Google Scholar]
- Kumar, S.; Tiwari, P.; Zymbler, M. Internet of Things is a revolutionary approach for future technology enhancement: A review. J. Big Data 2019, 6, 1–21. [Google Scholar] [CrossRef] [Green Version]
- Analytics, I. State of IoT 2022: Number of Connected IoT Devices Growing 18% to 14.4 Billion Globally. 2022. Available online: https://iot-analytics.com/number-connected-iot-devices/ (accessed on 1 March 2023).
- IDC. Worldwide Internet of Things Spending Guide. 2022. Available online: https://www.idc.com/getdoc.jsp?containerId=US49576022&pageType=PRINTFRIENDLY (accessed on 14 March 2023).
- Risteska Stojkoska, B.L.; Trivodaliev, K.V. A review of Internet of Things for smart home: Challenges and solutions. J. Clean. Prod. 2017, 140, 1454–1464. [Google Scholar] [CrossRef]
- Pirbhulal, S.; Zhang, H.; E Alahi, M.E.; Ghayvat, H.; Mukhopadhyay, S.C.; Zhang, Y.T.; Wu, W. A novel secure IoT-based smart home automation system using a wireless sensor network. Sensors 2016, 17, 69. [Google Scholar] [CrossRef] [PubMed]
- Ghayvat, H.; Liu, J.; Babu, A.; Alahi, E.; Gui, X.; Mukhopadhyay, S. Internet of Things for smart homes and buildings: Opportunities and Challenges. J. Telecommun. Digit. Econ. 2015, 3, 33–47. [Google Scholar] [CrossRef]
- Silva, B.N.; Khan, M.; Han, K. Towards sustainable smart cities: A review of trends, architectures, components, and open challenges in smart cities. Sustain. Cities Soc. 2018, 38, 697–713. [Google Scholar] [CrossRef]
- Yigitcanlar, T.; Kamruzzaman, M.; Foth, M.; Sabatini-Marques, J.; da Costa, E.; Ioppolo, G. Can cities become smart without being sustainable? A systematic review of the literature. Sustain. Cities Soc. 2019, 45, 348–365. [Google Scholar] [CrossRef]
- Syed, A.S.; Sierra-Sosa, D.; Kumar, A.; Elmaghraby, A. IoT in smart cities: A survey of technologies, practices and challenges. Smart Cities 2021, 4, 429–475. [Google Scholar] [CrossRef]
- Farooq, M.S.; Riaz, S.; Abid, A.; Abid, K.; Naeem, M.A. A Survey on the Role of IoT in Agriculture for the Implementation of Smart Farming. IEEE Access 2019, 7, 156237–156271. [Google Scholar] [CrossRef]
- Jaiganesh, S.; Gunaseelan, K.; Ellappan, V. IOT agriculture to improve food and farming technology. In Proceedings of the 2017 Conference on Emerging Devices and Smart Systems (ICEDSS), Piscataway, NJ, USA, 3–4 March 2017; pp. 260–266. [Google Scholar]
- Zhao, J.C.; Zhang, J.F.; Feng, Y.; Guo, J.X. The study and application of the IOT technology in agriculture. In Proceedings of the 2010 3rd International Conference on Computer Science and Information Technology, Chengdu, China, 9–11 July 2010; Volume 2, pp. 462–465. [Google Scholar]
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial internet of things: Challenges, opportunities, and directions. IEEE Trans. Ind. Informatics 2018, 14, 4724–4734. [Google Scholar] [CrossRef]
- Cheng, J.; Chen, W.; Tao, F.; Lin, C.L. Industrial IoT in 5G environment towards smart manufacturing. J. Ind. Inf. Integr. 2018, 10, 10–19. [Google Scholar] [CrossRef]
- Zantalis, F.; Koulouras, G.; Karabetsos, S.; Kandris, D. A review of machine learning and IoT in smart transportation. Future Internet 2019, 11, 94. [Google Scholar] [CrossRef] [Green Version]
- Muthuramalingam, S.; Bharathi, A.; Gayathri, N.; Sathiyaraj, R.; Balamurugan, B. IoT based intelligent transportation system (IoT-ITS) for global perspective: A case study. In Internet of Things and Big Data Analytics for Smart Generation; Springer: Berlin/Heidelberg, Germany, 2019; pp. 279–300. [Google Scholar]
- Chand, H.V.; Karthikeyan, J. Survey on the role of IoT in intelligent transportation system. Indones. J. Electr. Eng. Comput. Sci. 2018, 11, 936–941. [Google Scholar] [CrossRef]
- Selvaraj, S.; Sundaravaradhan, S. Challenges and opportunities in IoT healthcare systems: A systematic review. SN Appl. Sci. 2020, 2, 139. [Google Scholar] [CrossRef] [Green Version]
- Qadri, Y.A.; Nauman, A.; Zikria, Y.B.; Vasilakos, A.V.; Kim, S.W. The future of healthcare internet of things: A survey of emerging technologies. IEEE Commun. Surv. Tutor. 2020, 22, 1121–1167. [Google Scholar] [CrossRef]
- Cauteruccio, F.; Cinelli, L.; Fortino, G.; Savaglio, C.; Terracina, G.; Ursino, D.; Virgili, L. An approach to compute the scope of a social object in a Multi-IoT scenario. Pervasive Mob. Comput. 2020, 67, 101223. [Google Scholar] [CrossRef]
- Ojagh, S.; Cauteruccio, F.; Terracina, G.; Liang, S.H. Enhanced air quality prediction by edge-based spatiotemporal data preprocessing. Comput. Electr. Eng. 2021, 96, 107572. [Google Scholar] [CrossRef]
- Manavalan, E.; Jayakrishna, K. A review of Internet of Things (IoT) embedded sustainable supply chain for industry 4.0 requirements. Comput. Ind. Eng. 2019, 127, 925–953. [Google Scholar] [CrossRef]
- Boukerche, A.; Coutinho, R.W. Crowd management: The overlooked component of smart transportation systems. IEEE Commun. Mag. 2019, 57, 48–53. [Google Scholar] [CrossRef]
- Qureshi, F.; Krishnan, S. Wearable hardware design for the internet of medical things (IoMT). Sensors 2018, 18, 3812. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Balestrieri, E.; Boldi, F.; Colavita, A.R.; De Vito, L.; Laudato, G.; Oliveto, R.; Picariello, F.; Rivaldi, S.; Scalabrino, S.; Torchitti, P.; et al. The architecture of an innovative smart T-shirt based on the Internet of Medical Things paradigm. In Proceedings of the 2019 IEEE International Symposium on Medical Measurements and Applications (MeMeA), Istanbul, Turkey, 26–28 June 2019; pp. 1–6. [Google Scholar]
- Balica, R.Ş. Networked Wearable Devices, Machine Learning-based Real-Time Data Sensing and Processing, and Internet of Medical Things in COVID-19 Diagnosis, Prognosis, and Treatment. Am. J. Med. Res. 2022, 9, 33–48. [Google Scholar]
- Rajavi, Y.; Taghivand, M.; Aggarwal, K.; Ma, A.; Poon, A.S. An energy harvested ultra-low power transceiver for Internet of Medical Things. In Proceedings of the ESSCIRC Conference 2016: 42nd European Solid-State Circuits Conference, Lausanne, Switzerland, 12–15 September 2016; pp. 133–136. [Google Scholar]
- Ahmed, S.; Naga Srinivasu, P.; Alhumam, A.; Alarfaj, M. AAL and Internet of Medical Things for Monitoring Type-2 Diabetic Patients. Diagnostics 2022, 12, 2739. [Google Scholar] [CrossRef] [PubMed]
- Wei, K.; Zhang, L.; Guo, Y.; Jiang, X. Health monitoring based on internet of medical things: Architecture, enabling technologies, and applications. IEEE Access 2020, 8, 27468–27478. [Google Scholar] [CrossRef]
- Askar, N.A.; Habbal, A.; Mohammed, A.H.; Sajat, M.S.; Yusupov, Z.; Kodirov, D. Architecture, Protocols, and Applications of the Internet of Medical Things (IoMT). J. Commun. 2022, 17, 900–918. [Google Scholar] [CrossRef]
- Zachos, G.; Essop, I.; Mantas, G.; Porfyrakis, K.; Ribeiro, J.C.; Rodriguez, J. An anomaly-based intrusion detection system for internet of medical things networks. Electronics 2021, 10, 2562. [Google Scholar] [CrossRef]
- Yang, B.; Cao, X.; Han, Z.; Qian, L. A machine learning enabled MAC framework for heterogeneous Internet-of-Things networks. IEEE Trans. Wirel. Commun. 2019, 18, 3697–3712. [Google Scholar] [CrossRef]
- Fersi, G. Study of middleware for Internet of healthcare things and their applications. In Proceedings of the International Conference on Smart Homes and Health Telematics, Hammamet, Tunisia, 24–26 June 2020; pp. 223–231. [Google Scholar]
- Ivanov, R.; Nguyen, H.; Weimer, J.; Sokolsky, O.; Lee, I. Openice-lite: Towards a connectivity platform for the internet of medical things. In Proceedings of the 2018 IEEE 21st International Symposium on Real-Time Distributed Computing (ISORC), Nashville, TN, USA, 19–21 May 2018; pp. 103–106. [Google Scholar]
- da Cruz, M.A.; Rodrigues, J.J.P.; Al-Muhtadi, J.; Korotaev, V.V.; de Albuquerque, V.H.C. A reference model for internet of things middleware. IEEE Internet Things J. 2018, 5, 871–883. [Google Scholar] [CrossRef]
- Phan, D.T.; Nguyen, C.H.; Nguyen, T.D.P.; Tran, L.H.; Park, S.; Choi, J.; Lee, B.I.; Oh, J. A Flexible, Wearable, and Wireless Biosensor Patch with Internet of Medical Things Applications. Biosensors 2022, 12, 139. [Google Scholar] [CrossRef]
- Rubí, J.N.S.; Gondim, P.R.D.L. Interoperable internet of medical things platform for e-health applications. Int. J. Distrib. Sens. Networks 2020, 16, 1550147719889591. [Google Scholar] [CrossRef] [Green Version]
- Nayyar, A.; Puri, V.; Nguyen, N.G. BioSenHealth 1.0: A novel internet of medical things (IoMT)-based patient health monitoring system. In Proceedings of the International Conference on Innovative Computing and Communications, Delhi, India, 5–6 May 2018; Springer: Berlin/Heidelberg, Germany, 2019; pp. 155–164. [Google Scholar]
- Hatzivasilis, G.; Papaefstathiou, I.; Manifavas, H. Software Security, Privacy and Dependability: Metrics and Measurement. IEEE Software 2016, 33, 46–54. [Google Scholar] [CrossRef]
- Khan, L.U.; Saad, W.; Han, Z.; Hossain, E.; Hong, C.S. Federated learning for internet of things: Recent advances, taxonomy, and open challenges. IEEE Commun. Surv. Tutor. 2021, 23, 1759–1799. [Google Scholar] [CrossRef]
- Agrawal, M.; Zhou, J.; Chang, D. A survey on lightweight authenticated encryption and challenges for securing industrial IoT. In Security and Privacy Trends in the Industrial Internet of Things; Springer: Berlin/Heidelberg, Germany, 2019; pp. 71–94. [Google Scholar]
- Hazratifard, M.; Gebali, F.; Mamun, M. Using machine learning for dynamic authentication in telehealth: A tutorial. Sensors 2022, 22, 7655. [Google Scholar] [CrossRef]
- El-Hajj, M.; Fadlallah, A.; Chamoun, M.; Serhrouchni, A. A survey of internet of things (IoT) authentication schemes. Sensors 2019, 19, 1141. [Google Scholar] [CrossRef] [Green Version]
- Koutras, D.; Stergiopoulos, G.; Dasaklis, T.; Kotzanikolaou, P.; Glynos, D.; Douligeris, C. Security in IoMT communications: A survey. Sensors 2020, 20, 4828. [Google Scholar] [CrossRef] [PubMed]
- Khan, M.A.; Din, I.U.; Majali, T.; Kim, B.S. A Survey of Authentication in Internet of Things-Enabled Healthcare Systems. Sensors 2022, 22, 9089. [Google Scholar] [CrossRef] [PubMed]
- Baig, A.F.; Eskeland, S. Security, privacy, and usability in continuous authentication: A survey. Sensors 2021, 21, 5967. [Google Scholar] [CrossRef] [PubMed]
- Reese, K.; Smith, T.; Dutson, J.; Armknecht, J.; Cameron, J.; Seamons, K. A usability study of five two-factor authentication methods. In Proceedings of the 15th Symposium on Usable Privacy and Security, Santa Clara, CA, USA, 11–13 August 2019. [Google Scholar]
- Lennartsson, M.; Kävrestad, J.; Nohlberg, M. Exploring the meaning of usable security–a literature review. Inf. Comput. Secur. 2021, 29, 647–663. [Google Scholar] [CrossRef]
- Lewis, J.R. Psychometric Evaluation of the PSSUQ Using Data from Five Years of Usability Studies. Int. J. Human–Comput. Interact. 2002, 14, 463–488. [Google Scholar] [PubMed]
- Davis, D.; Monrose, F.; Reiter, M.K. On User Choice in Graphical Password Schemes. In Proceedings of the 13th USENIX Security Symposium (USENIX Security 04), San Diego, CA, USA, 9–13 August 2004; USENIX Association: San Diego, CA, USA, 2004. [Google Scholar]
- Dhamija, R.; Perrig, A. Deja Vu–A User Study: Using Images for Authentication. In Proceedings of the 9th USENIX Security Symposium (USENIX Security 00), Denver, CO, USA, 14–17 August 2000; USENIX Association: Denver, CO, USA, 2000. [Google Scholar]
- Hayashi, E.; Dhamija, R.; Christin, N.; Perrig, A. Use Your Illusion: Secure Authentication Usable Anywhere. In Proceedings of the 4th Symposium on Usable Privacy and Security, Pittsburgh, PA, USA, 23–25 July 2008; Association for Computing Machinery: New York, NY, USA, 2008; pp. 35–45. [Google Scholar] [CrossRef]
- Khan, W.; Aalsalem, M.; Xiang, Y. A Graphical Password Based System for Small Mobile Devices. arXiv 2011, arXiv:1110.3844. [Google Scholar]
- Jermyn, I.; Mayer, A.; Monrose, F.; Reiter, M.K.; Rubin, A.D. The Design and Analysis of Graphical Passwords. In Proceedings of the 8th Conference on USENIX Security Symposium, Washington, DC, USA, 23–26 August 1999; USENIX Association: Berkeley, CA, USA, 1999; Volume 8, p. 1. [Google Scholar]
- Varenhorst, C.; Van Kleek, M.; Rudolph, L. Passdoodles: A Lightweight Authentication Method; Research Science Institute: Cambridge, MA, USA, 2004. [Google Scholar]
- Weiss, R.; De Luca, A. PassShapes: Utilizing Stroke Based Authentication to Increase Password Memorability; Association for Computing Machinery: New York City, NY, USA, 2008; NordiCHI ’08; pp. 383–392. [Google Scholar] [CrossRef]
- Lin, D.; Dunphy, P.; Olivier, P.; Yan, J. Graphical passwords & qualitative spatial relations. ACM 2007, 229, 161–162. [Google Scholar] [CrossRef]
- Liu, X.; Qiu, J.; Ma, L.; Gao, H.; Ren, Z. A Novel Cued-recall Graphical Password Scheme. In Proceedings of the 2011 6th International Conference on Image and Graphics, Hefei, China, 12–15 August 2011; pp. 949–956. [Google Scholar] [CrossRef]
- van Oorschot, P.C.; Wan, T. TwoStep: An Authentication Method Combining Text and Graphical Passwords. In MCETECH 2009: E-Technologies: Innovation in an Open World; Babin, G., Kropf, P., Weiss, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 233–239. [Google Scholar]
- Ray, P.P. Ray’s Scheme: Graphical Password Based Hybrid Authentication System for Smart Hand Held Devices. J. Inf. Eng. Appl. 2012, 2, 1–11. [Google Scholar]
- Gao, H.; Liu, X. A new graphical password scheme against spyware by using CAPTCHA. In Proceedings of the SOUPS, Mountain View, CA, USA, 15–17 July 2009. [Google Scholar]
- Joshi, A.M.; Muniyal, B. Authentication Using Text and Graphical Password. In Proceedings of the 2018 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Bangalore, India, 19–22 September 2018; pp. 381–386. [Google Scholar] [CrossRef]
- Bianchi, A.; Oakley, I.; Kim, H. PassBYOP: Bring Your Own Picture for Securing Graphical Passwords. IEEE Trans. -Hum. -Mach. Syst. 2016, 46, 380–389. [Google Scholar] [CrossRef]
- Kausar, N.; Din, I.U.; Khan, M.A.; Almogren, A.; Kim, B.S. GRA-PIN: A Graphical and PIN-Based Hybrid Authentication Approach for Smart Devices. Sensors 2022, 22, 1349. [Google Scholar] [CrossRef]
- Jirjees, S.W.; Mahmood, A.M.; Nasser, A.R. Passnumbers: An approach of graphical password authentication based on grid selection. IJSSE 2022, 12, 21–29. [Google Scholar] [CrossRef]
- Alsaeed, N.; Nadeem, F. Authentication in the Internet of Medical Things: Taxonomy, Review, and Open Issues. Appl. Sci. 2022, 12, 7487. [Google Scholar] [CrossRef]
- Rathore, H.; Fu, C.; Mohamed, A.; Al-Ali, A.; Du, X.; Guizani, M.; Yu, Z. Multi-layer security scheme for implantable medical devices. Neural Comput. Appl. 2020, 32, 4347–4360. [Google Scholar] [CrossRef]
- Soni, P.; Pal, A.K.; Islam, S.H. An improved three-factor authentication scheme for patient monitoring using WSN in remote health-care system. Comput. Methods Programs Biomed. 2019, 182, 105054. [Google Scholar] [CrossRef] [PubMed]
- Akrivopoulos, O.; Chatzigiannakis, I.; Tselios, C.; Antoniou, A. On the deployment of healthcare applications over fog computing infrastructure. In Proceedings of the 2017 IEEE 41st AnnualComputer Software and Applications Conference (COMPSAC), Turin, Italy, 4–8 July 2017; Volume 2, pp. 288–293. [Google Scholar]
- Lee, J.D.; Yoon, T.S.; Chung, S.H.; Cha, H.S. Service-oriented security framework for remote medical services in the Internet of Things environment. Healthc. Inform. Res. 2015, 21, 271–282. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Chen, C.L.; Yang, T.T.; Leu, F.Y.; Huang, Y.L. Designing a healthcare authorization model based on cloud authentication. Intell. Autom. Soft Comput. 2014, 20, 365–379. [Google Scholar] [CrossRef]
- Al-Saggaf, A.A.; Sheltami, T.; Alkhzaimi, H.; Ahmed, G. Lightweight Two-Factor-Based User Authentication Protocol for IoT-Enabled Healthcare Ecosystem in Quantum Computing. Arab. J. Sci. Eng. 2022, 48, 2347–2357. [Google Scholar] [CrossRef] [PubMed]
- Moghaddam, F.F.; Moghaddam, S.G.; Rouzbeh, S.; Araghi, S.K.; Alibeigi, N.M.; Varnosfaderani, S.D. A scalable and efficient user authentication scheme for cloud computing environments. In Proceedings of the 2014 IEEE Region 10 Symposium, Kuala Lumpur, Malaysia, 14–16 April 2014; pp. 508–513. [Google Scholar]
- James R, L. Handbook of Human Factors and Ergonomics, 4th ed.; Chapter Usability Testing; Wiley: Hoboken, NJ, USA, 2012; pp. 1267–1312. [Google Scholar] [CrossRef]
- Sauro, J.; Lewis, J.R. Quantifying the User Experience: Practical Statistics for User Research; Morgan Kaufmann: Burlginton, MA, USA, 2016. [Google Scholar]









| Variables | t | df | Sig. (2-Tailed) | Cohen’s d |
|---|---|---|---|---|
| Overall Quality | 4.06 | 8.64 | 0.003 | 1.92 |
| System Quality | 2.54 | 8.97 | 0.03 | 1.2 |
| Information Quality | 3.48 | 8.62 | 0.007 | 1.64 |
| Interface Quality | 6.31 | 9.92 | 0 | 2.96 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, M.A.; Din, I.U.; Almogren, A. Securing Access to Internet of Medical Things Using a Graphical-Password-Based User Authentication Scheme. Sustainability 2023, 15, 5207. https://doi.org/10.3390/su15065207
Khan MA, Din IU, Almogren A. Securing Access to Internet of Medical Things Using a Graphical-Password-Based User Authentication Scheme. Sustainability. 2023; 15(6):5207. https://doi.org/10.3390/su15065207
Chicago/Turabian StyleKhan, Mudassar Ali, Ikram Ud Din, and Ahmad Almogren. 2023. "Securing Access to Internet of Medical Things Using a Graphical-Password-Based User Authentication Scheme" Sustainability 15, no. 6: 5207. https://doi.org/10.3390/su15065207





