Impact of Cyber Attacks on High Voltage DC Transmission Damping Control
Abstract
:1. Introduction
1.1. Motivation
1.2. Literature Survey
1.3. Contributions
1.4. Organization of Paper
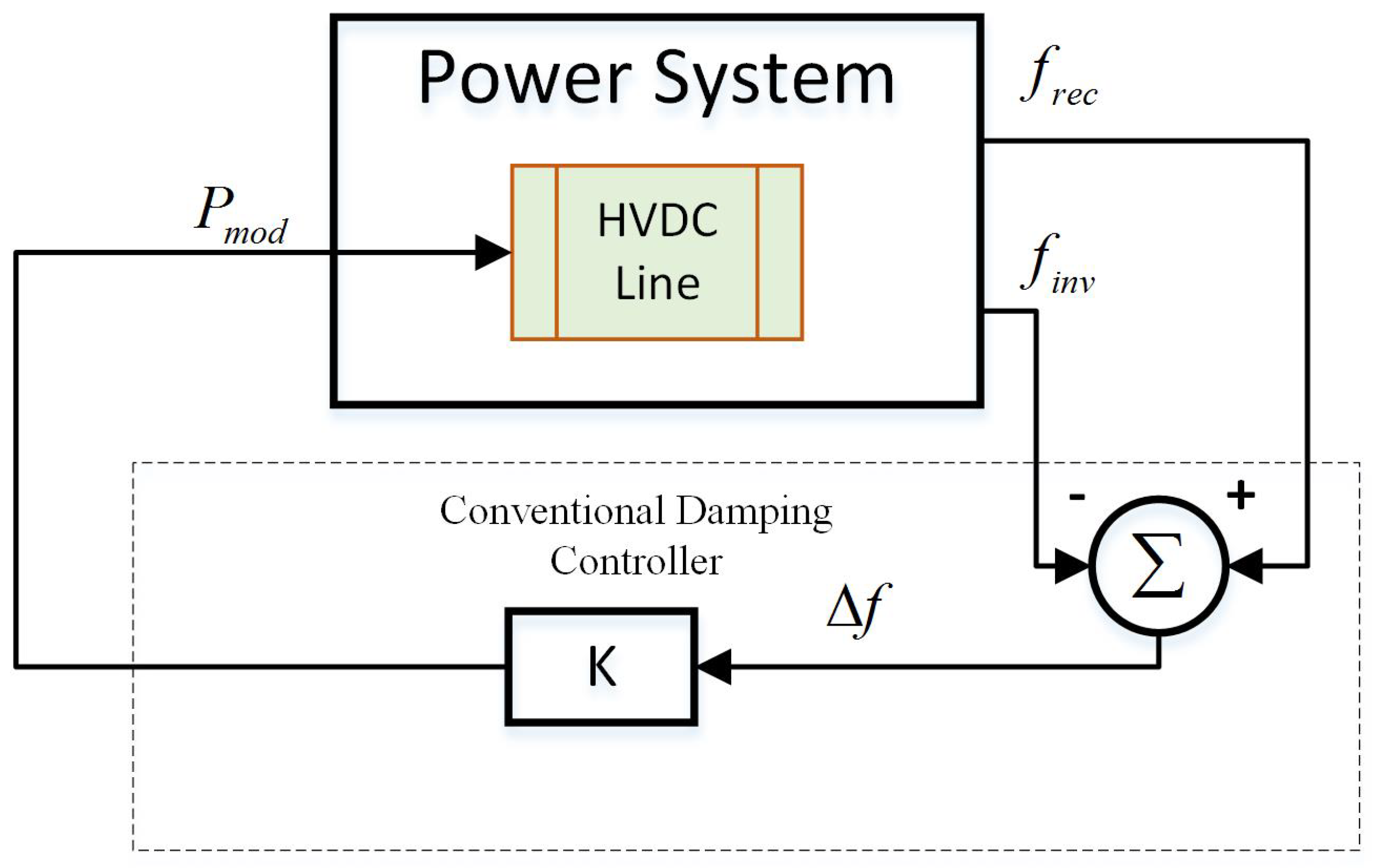
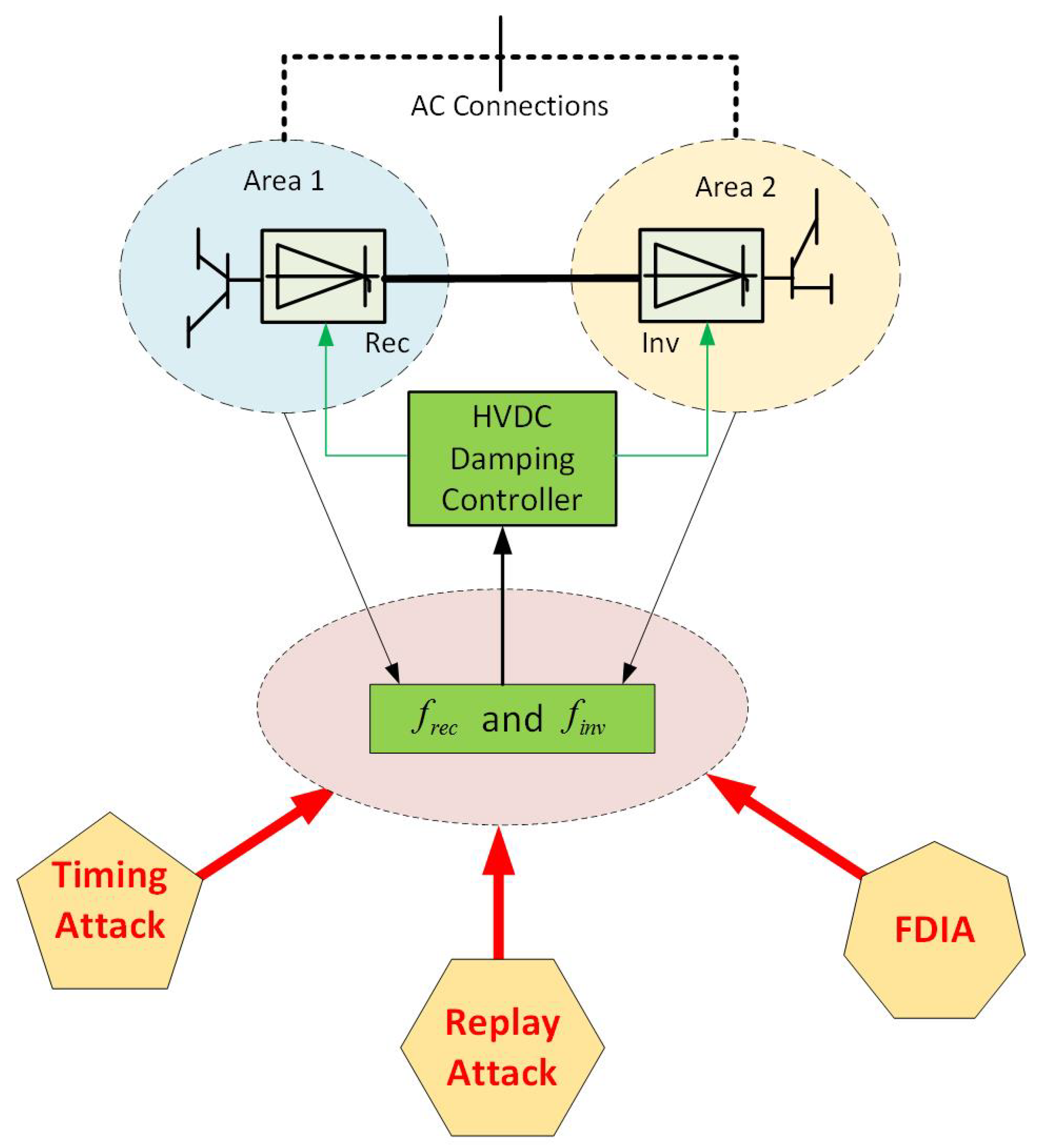
2. HVDC System with Damping Control
2.1. HVDC Models
2.2. Conventional HVDC Oscillation Damping Control
3. Construction of the Cyber Attack Model
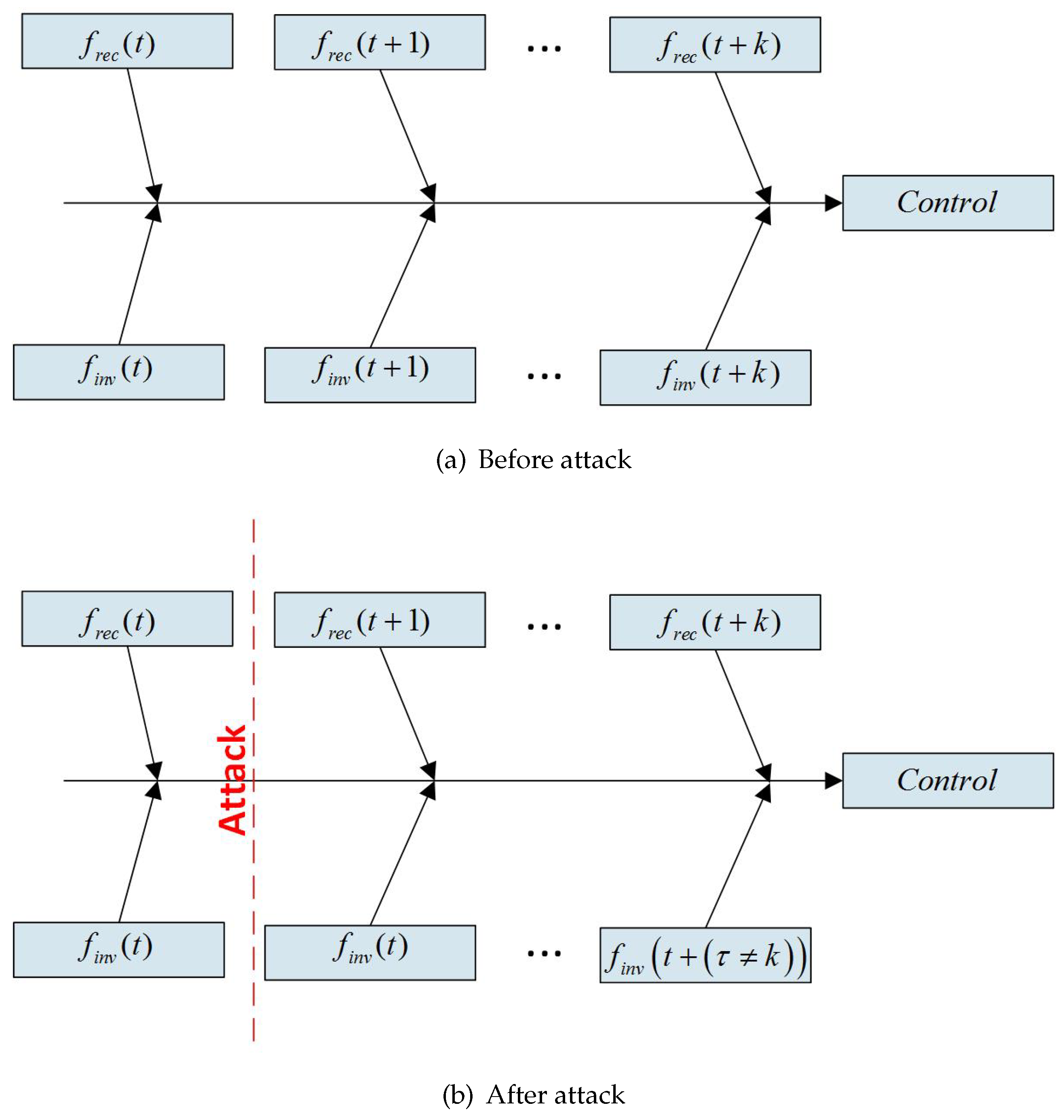
3.1. Timing Attack
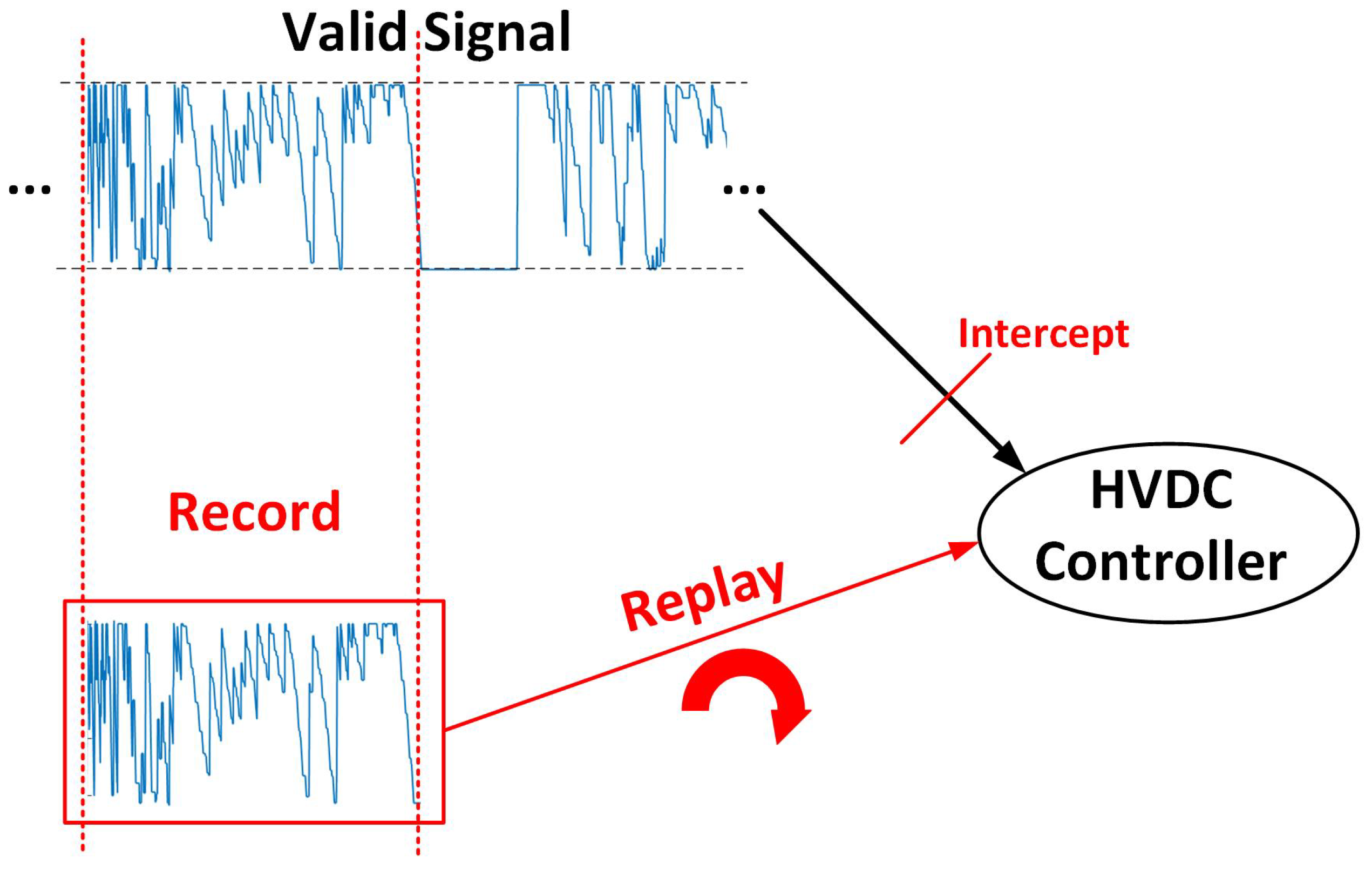
3.2. Replay Attack
3.3. False Data Injection Attack
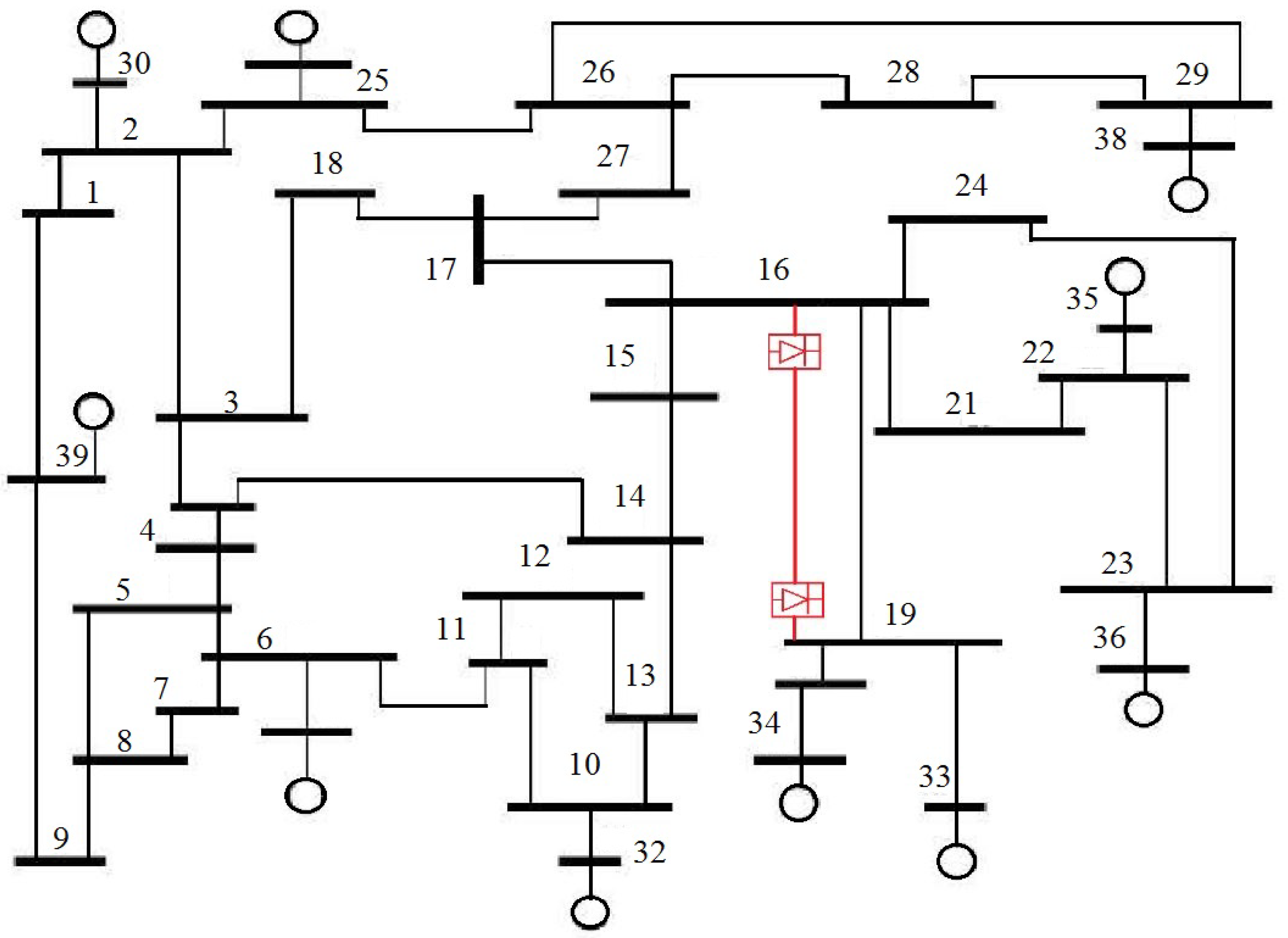
4. Test System and Simulation Overview
5. Simulation Results
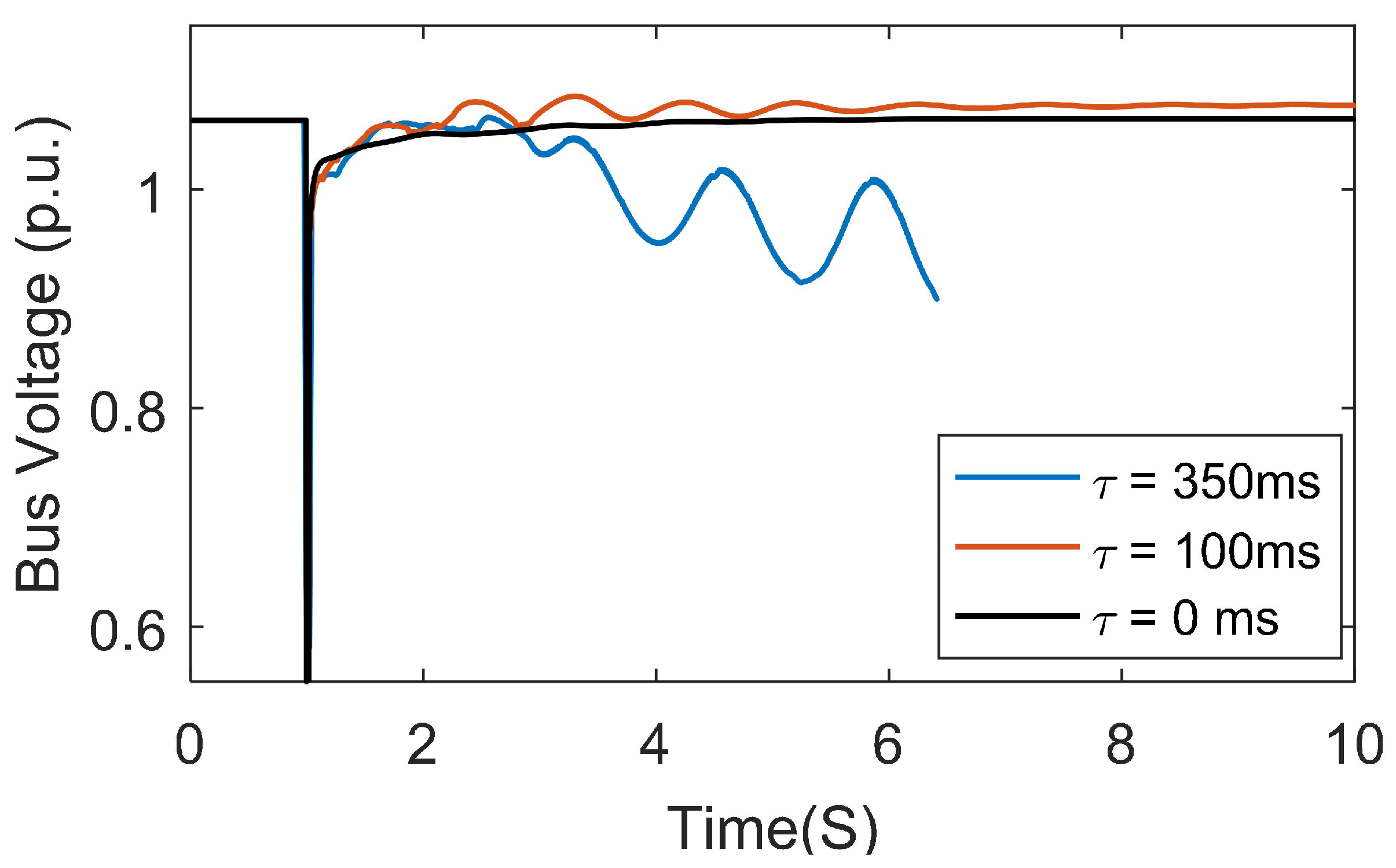
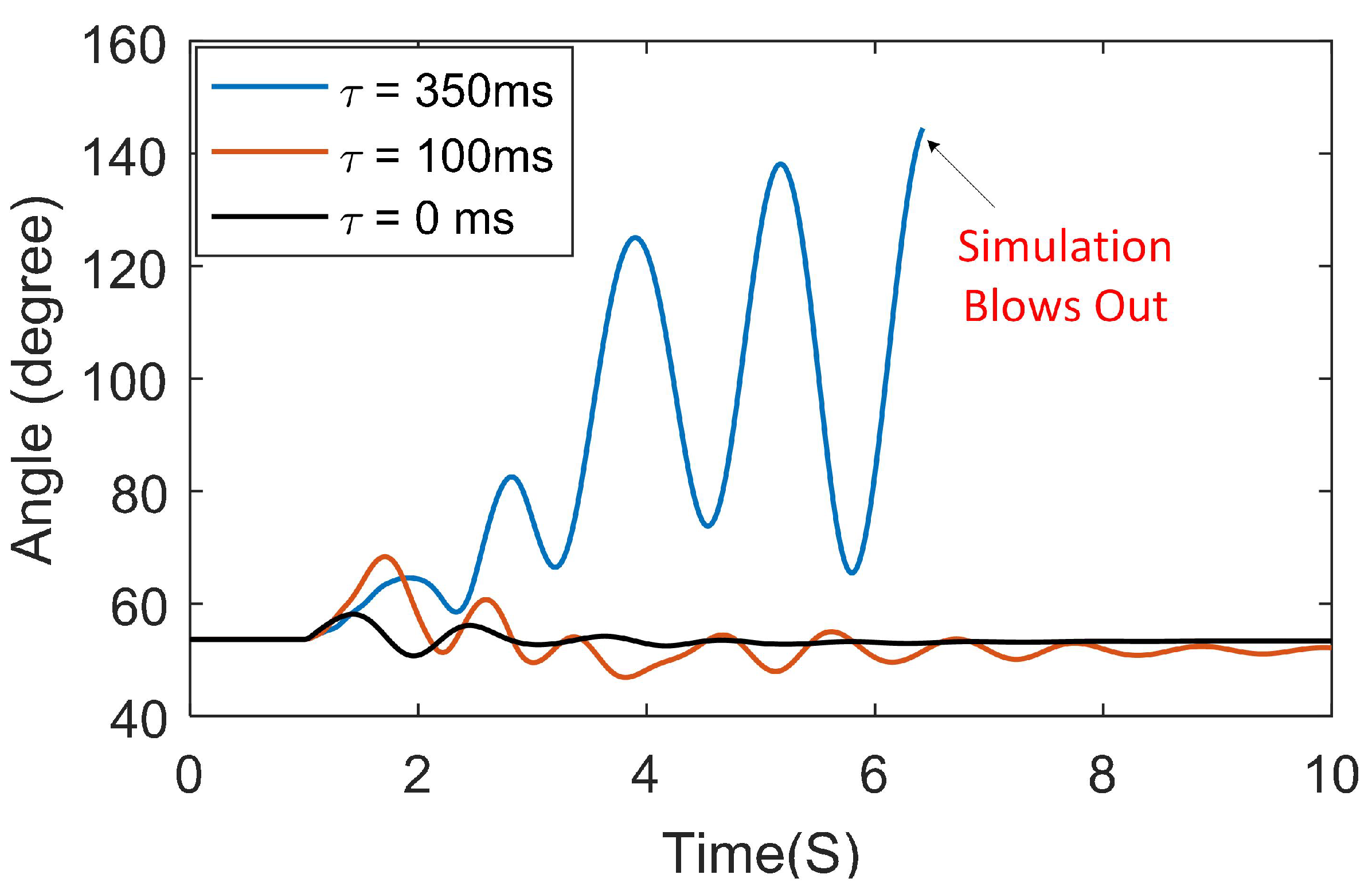
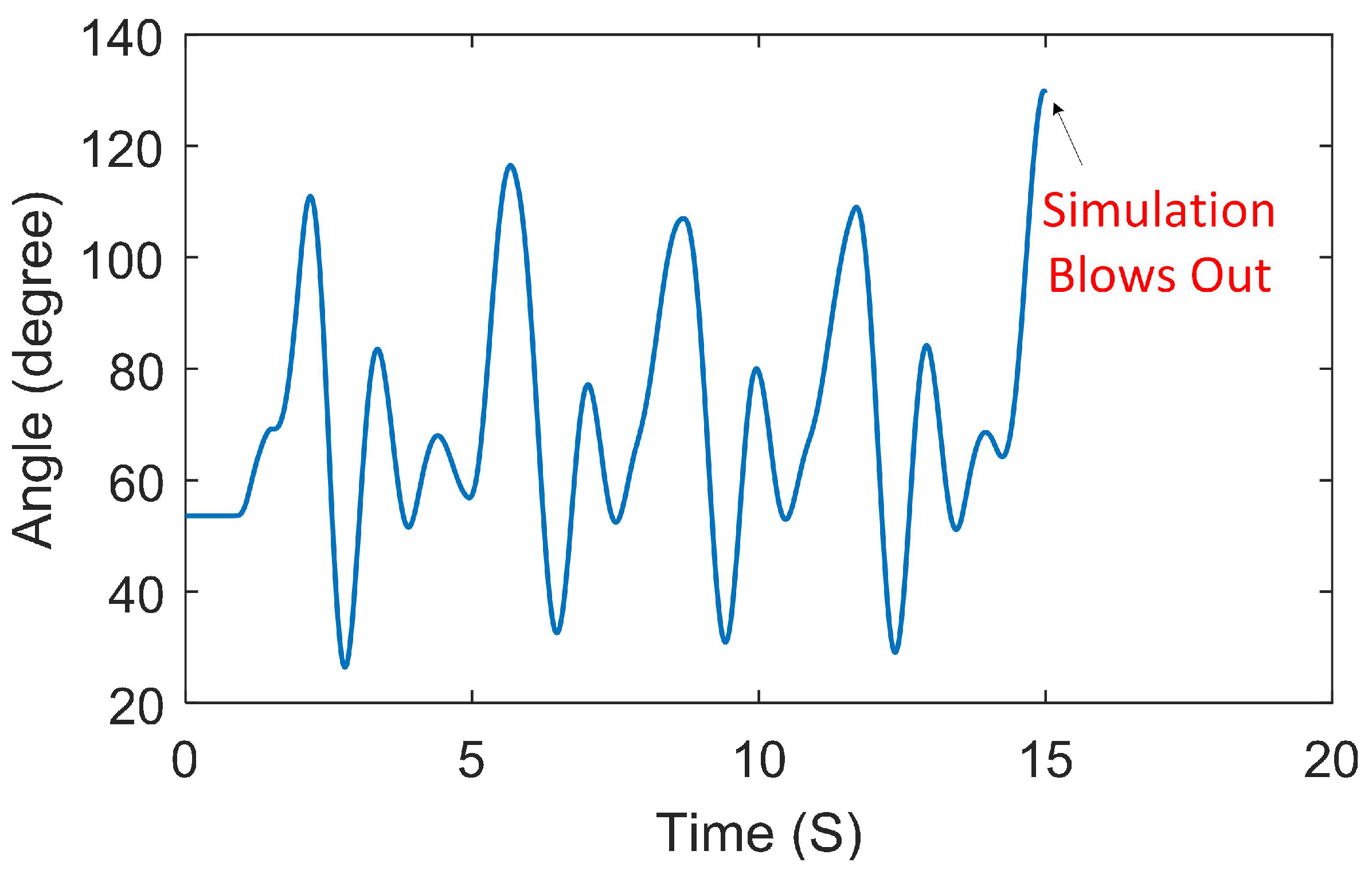
5.1. Timing Attack Results
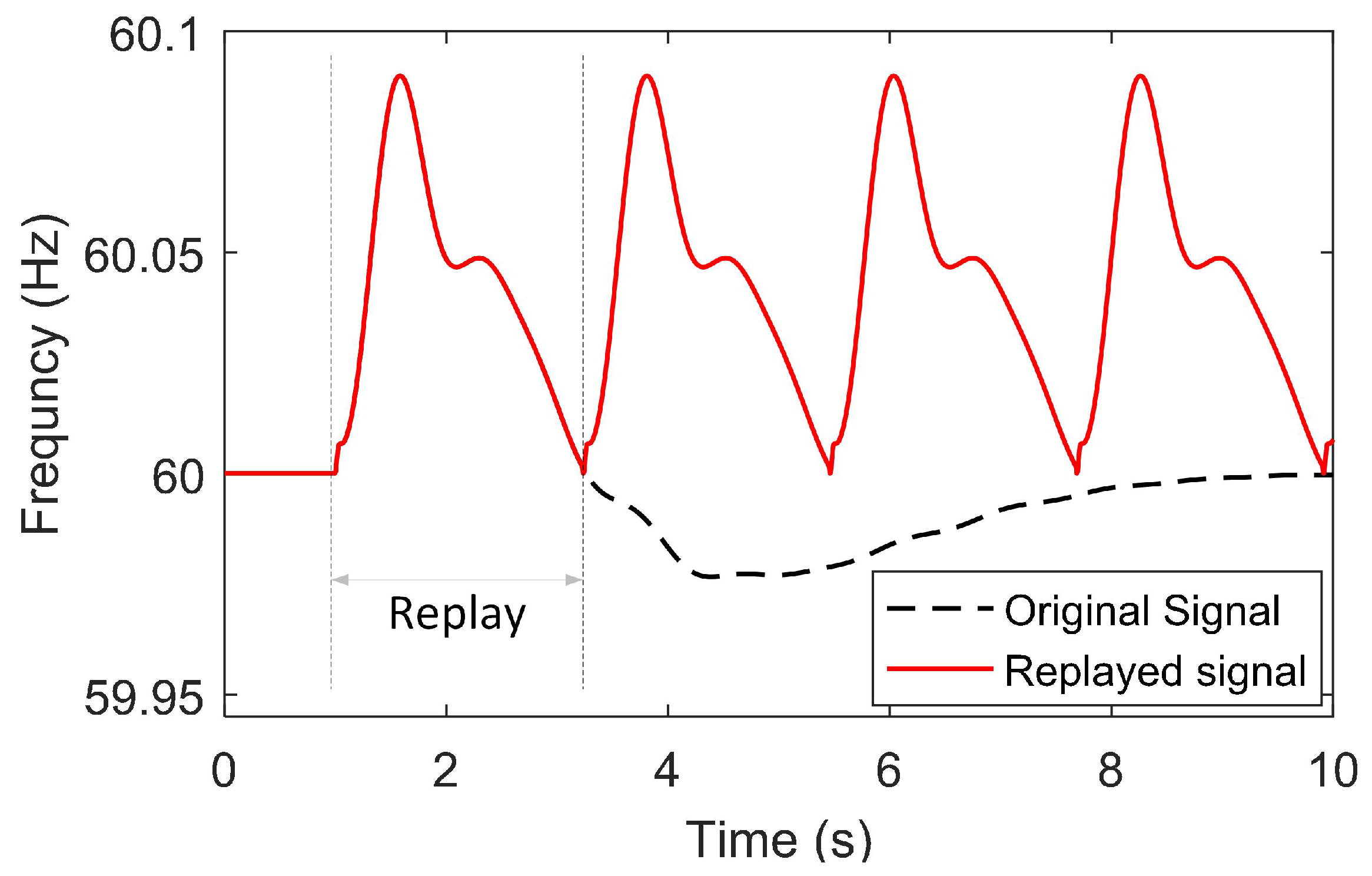
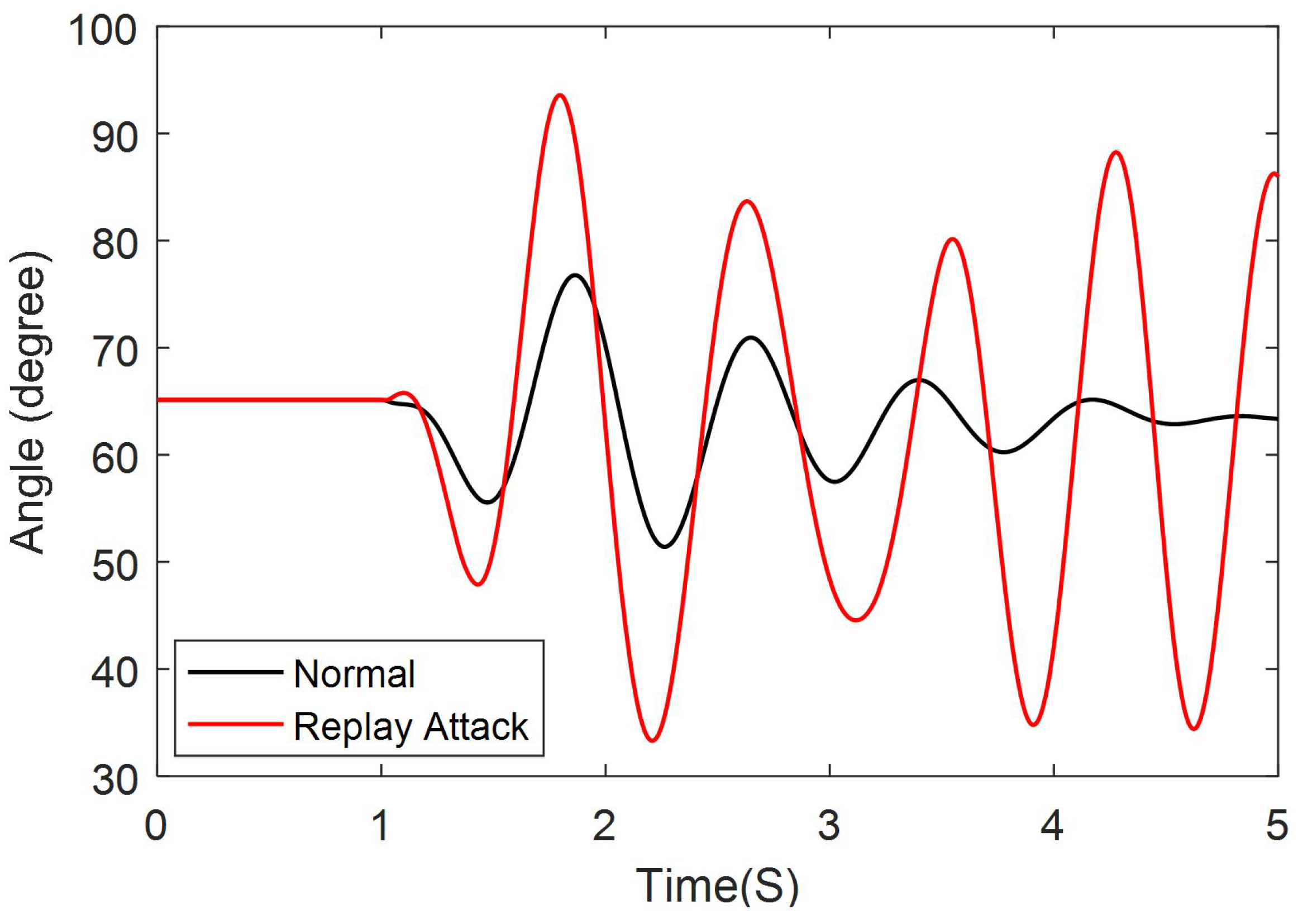
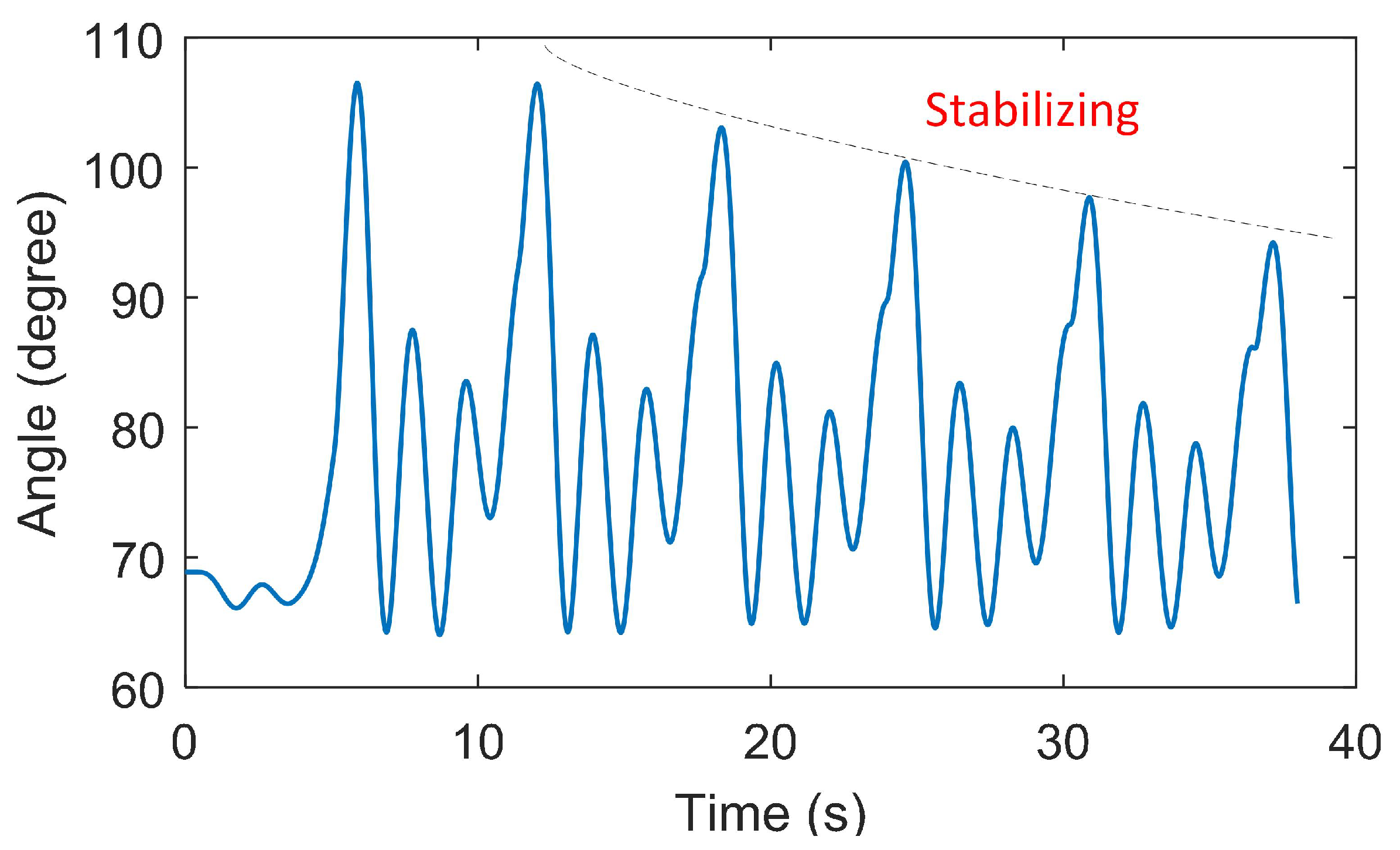
5.2. Replay Attack Results
5.2.1. Attack Occurs During Normal Operation
5.2.2. Attack Occurs During Transient Events
5.3. FDIA Attack Results
6. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
Nomenclature
| DC line resistance | |
| DC line inductance | |
| DC line capacitance | |
| DC voltage | |
| voltage at the rectifier | |
| voltage at the inverter | |
| DC current at the rectifier | |
| DC current at the inverter | |
| AC active power at the HVDC terminal | |
| AC reactive power at the HVDC terminal | |
| rectifier firing angle | |
| inverter extinction angle | |
| feedback signal for HVDC power modulation | |
| frequency at the rectifier terminal | |
| frequency at the inverter terminal | |
| K | proportional gain for the damping controller |
| valid data received during period T | |
| instantaneous valid data received at time t | |
| instantaneous corrupted data at time t | |
| T | time period between and |
| M | indicator function |
| z | measurement from sensors |
| x | system states |
| e | measurement errors |
| H | Jacobian matrix of the system |
| W | diagonal weight matrix |
| variance of the measurement errors associated with the i-th meter | |
| solution of the WLS optimization problem | |
| threshold for the largest normalized residual | |
| compromised measurements | |
| false system states | |
| difference between compromised and true measurements | |
| difference between false states and true states | |
| largest normalized residual | |
| largest normalized residual under FDIA | |
| perturbed system states for small-signal stability studies | |
| v | vector of the network bus voltages |
| current injection into the network | |
| prefix representing perturbed value | |
| system coefficient matrices | |
| admittance matrix of the system | |
| state matrix of the system |
References
- Bahrman, M.P.; Johnson, B.K. The ABCs of HVDC transmission technologies. IEEE Power Energy Mag. 2007, 5, 32–44. [Google Scholar] [CrossRef]
- Smed, T.; Andersson, G. Utilizing HVDC to damp power oscillations. IEEE Trans. Power Deliv. 1993, 8, 620–627. [Google Scholar] [CrossRef]
- Guo, J.; Han, Y.; Guo, C.; Lou, F.; Wang, Y. Modeling and vulnerability analysis of cyber-physical power systems considering network topology and power flow properties. Energies 2017, 10, 87. [Google Scholar] [CrossRef]
- Meliopoulos, A.P.S.; Cokkinides, G.; Fan, R.; Sun, L. Data Attack Detection and Command Authentication via Cyber-Physical Comodeling. IEEE Des. Test 2017, 34, 34–43. [Google Scholar] [CrossRef]
- Dougherty, J.J.; Hillesland, T. Power System Stability Considerations with Dynamically Responsive DC Transmission Lines. IEEE Trans. Power Appar. Syst. 1970, PAS-89, 34–45. [Google Scholar] [CrossRef]
- Grund, C.; Hauer, J.; Crane, L.; Carlson, D.; Wright, S. Square Butte HVDC modulation system field tests. IEEE Trans. Power Deliv. 1990, 5, 351–357. [Google Scholar] [CrossRef]
- Cresap, R.; Mittelstadt, W.; Scott, D.; Taylor, C. Operating experience with modulation of the Pacific HVDC intertie. IEEE Trans. Power Appar. Syst. 1978, 4, 1053–1059. [Google Scholar] [CrossRef]
- Long, W.; Nilsson, S. HVDC transmission: yesterday and today. IEEE Power Energy Mag. 2007, 5, 22–31. [Google Scholar] [CrossRef]
- Hossain, E.; Perez, R.; Nasiri, A.; Bayindir, R. Development of lyapunov redesign controller for microgrids with constant power loads. Renew. Energy Focus 2017, 19, 49–62. [Google Scholar] [CrossRef]
- Azad, S.P.; Iravani, R.; Tate, J.E. Damping Inter-Area Oscillations Based on a Model Predictive Control (MPC) HVDC Supplementary Controller. IEEE Trans. Power Syst. 2013, 28, 3174–3183. [Google Scholar] [CrossRef]
- Roberson, D.; O’Brien, J.F. Loop Shaping of a Wide-Area Damping Controller Using HVDC. IEEE Trans. Power Syst. 2017, 32, 2354–2361. [Google Scholar] [CrossRef]
- Pipelzadeh, Y.; Chaudhuri, N.R.; Chaudhuri, B.; Green, T.C. Coordinated Control of Offshore Wind Farm and Onshore HVDC Converter for Effective Power Oscillation Damping. IEEE Trans. Power Syst. 2017, 32, 1860–1872. [Google Scholar] [CrossRef]
- Fan, R.; Sun, L.; Tan, Z. Linear Quadratic Control of SSSC to Increase Power Oscillations Damping of HVDC-AC Power System. In Proceedings of the IEEE Power Energy Society General Meeting, Denver, CO, USA, 26–30 July 2015; pp. 1–5. [Google Scholar]
- Li, Y.; Rehtanz, C.; Ruberg, S.; Luo, L.; Cao, Y. Wide-area robust coordination approach of HVDC and FACTS controllers for damping multiple interarea oscillations. IEEE Trans. Power Deliv. 2012, 27, 1096–1105. [Google Scholar] [CrossRef]
- Meliopoulos, S.; Cokkinides, G.; Fan, R.; Sun, L.; Cui, B. Command Authentication via Faster than Real Time Simulation. In Proceedings of the IEEE Power and Energy Society General Meeting (PESGM), Boston, MA, USA, 17–21 July 2016; pp. 1–5. [Google Scholar]
- AFTER. AFTER Publishable Report. Available online: http://afterproject.eu/wp-content/uploads/2014/07/AFTER-Publishable-report.pdf (accessed on 1 July 2014).
- Netkachov, O.; Popov, P.; Salako, K. Quantification of the impact of cyber attack in critical infrastructures. In International Conference on Computer Safety, Reliability, and Security; Springer: Berlin/Heidelberg, Germany, 2014; pp. 316–327. [Google Scholar]
- Tøndel, I.A.; Mostue, B.A.; Jaatun, M.G.; Kjølle, G. Towards improved understanding and holistic management of the cyber security challenges in power transmission systems. In International Conference on Availability, Reliability, and Security; Springer: Berlin/Heidelberg, Germany, 2013; pp. 240–255. [Google Scholar]
- Fan, X.; Du, L.; Duan, D. Synchrophasor Data Correction under GPS Spoofing Attack: A State Estimation Based Approach. IEEE Trans. Smart Grid 2017, PP, 1. [Google Scholar] [CrossRef]
- Fu, R.; Huang, X.; Sun, J.; Zhou, Z.; Chen, D.; Wu, Y. Stability analysis of the cyber physical microgrid system under the intermittent DoS attacks. Energies 2017, 10, 680. [Google Scholar] [CrossRef]
- Mo, Y.; Sinopoli, B. Secure Control Against Replay Attacks. In Proceedings of the 47th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 30 September–2 October 2009; pp. 911–918. [Google Scholar]
- Zhu, S.; Setia, S.; Jajodia, S.; Ning, P. An Interleaved Hop-by-Hop Authentication Scheme for Filtering of Injected False Data in Sensor Networks. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 9–12 May 2004; pp. 259–271. [Google Scholar]
- Ashok, A.; Govindarasu, M.; Wang, J. Cyber-Physical Attack-Resilient Wide-Area Monitoring, Protection, and Control for the Power Grid. Proc. IEEE 2017, 105, 1389–1407. [Google Scholar] [CrossRef]
- Sridhar, S.; Hahn, A.; Govindarasu, M. Cyber–physical system security for the electric power grid. Proc. IEEE 2012, 100, 210–224. [Google Scholar] [CrossRef]
- He, H.; Yan, J. Cyber-physical attacks and defences in the smart grid: a survey. IET Cyber Phys. Syst. Theory Appl. 2016, 1, 13–27. [Google Scholar] [CrossRef]
- Bahrami, S.; Toulabi, M.; Ranjbar, S.; Moeini-Aghtaie, M.; Ranjbar, A.M. A Decentralized Energy Management Framework for Energy Hubs in Dynamic Pricing Markets. IEEE Trans. Smart Grid 2017. [Google Scholar] [CrossRef]
- Mohammadi, A.; Mehrtash, M.; Kargarian, A. Diagonal quadratic approximation for decentralized collaborative TSO+ DSO optimal power flow. IEEE Trans. Smart Grid 2018. [Google Scholar] [CrossRef]
- Sheikhi, A.; Rayati, M.; Bahrami, S.; Ranjbar, A.M.; Sattari, S. A cloud computing framework on demand side management game in smart energy hubs. Int. J. Elect. Power Energy Syst. 2015, 64, 1007–1016. [Google Scholar] [CrossRef]
- Beg, O.A.; Johnson, T.T.; Davoudi, A. Detection of False-Data Injection Attacks in Cyber-Physical DC Microgrids. IEEE Trans. Ind. Inf. 2017, 13, 2693–2703. [Google Scholar] [CrossRef]
- Zhong, X.; Yu, L.; Brooks, R.; Venayagamoorthy, G.K. Cyber Security in Smart DC Microgrid Operations. In Proceedings of the IEEE 1st International Conference on DC Microgrids (ICDCM), Atlanta, GA, USA, 27–29 June 2015; pp. 86–91. [Google Scholar]
- Mantooth, H.A.; Liu, Y.; Farnell, C.; Zhang, F.; Li, Q.; Di, J. Securing DC and Hybrid Microgrids. In Proceedings of the IEEE 1st International Conference on DC Microgrids (ICDCM), Atlanta, GA, USA, 27–29 June 2015; pp. 285–286. [Google Scholar]
- Ni, Y.X.; Fouad, A. A simplified two-terminal HVDC model and its use in direct transient stability assessment. IEEE Trans. Power Syst. 1987, 2, 1006–1012. [Google Scholar] [CrossRef]
- Trudnowski, D.; Kosterev, D.; Undrill, J. PDCI Damping Control Analysis for the Western North American Power System. In Proceedings of the IEEE Power Energy Society General Meeting, San Diego, CA, USA, 21–25 July 2013; pp. 1–5. [Google Scholar]
- Fan, R.; Elizondo, M.; Kirkham, H.; Lian, J.; Wilches-Bernal, F.; Schoenwald, D. Oscillation Damping Control Using Multiple High Voltage DC Transmission Lines: Controllability Exploration. In Proceedings of the IEEE/PES Transmission and Distribution Conference and Exposition, Denver, CO, USA, 16–19 April 2018. [Google Scholar]
- Kocher, P.C. Timing attacks on implementations of Diffie-Hellman, RSA, DSS, and other systems. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1996; pp. 104–113. [Google Scholar]
- Andrade, S.B.; Pignati, M.; Dan, G.; Paolone, M.; Boudec, J.Y.L. Undetectable PMU Timing-Attack on Linear State-Estimation by Using Rank-1 Approximation. IEEE Trans. Smart Grid 2017, PP, 1. [Google Scholar]
- Amini, M.; Ilić, M.D.; Karabasoglu, O. DC power flow estimation utilizing bayesian-based LMMSE estimator. In Proceedings of the Power & Energy Society General Meeting, Denver, CO, USA, 26–30 July 2015; pp. 1–5. [Google Scholar]
- Meliopoulos, A.P.S.; Cokkinides, G.J.; Myrda, P.; Liu, Y.; Fan, R.; Sun, L.; Huang, R.; Tan, Z. Dynamic State Estimation-Based Protection: Status and Promise. IEEE Trans. Power Deliv. 2017, 32, 320–330. [Google Scholar] [CrossRef]
- Kundur, P.; Rogers, G.; Wong, D.; Wang, L.; Lauby, M. A comprehensive computer program package for small signal stability analysis of power systems. IEEE Trans. Power Syst. 1990, 5, 1076–1083. [Google Scholar] [CrossRef]


| Mode | Frequency (Hz) | Damping Ratio (%) |
|---|---|---|
| 1 | 0.231 | 4.47 |
| 2 | 0.552 | 2.83 |
| 3 | 0.781 | 3.56 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fan, R.; Lian, J.; Kalsi, K.; Elizondo, M.A. Impact of Cyber Attacks on High Voltage DC Transmission Damping Control. Energies 2018, 11, 1046. https://doi.org/10.3390/en11051046
Fan R, Lian J, Kalsi K, Elizondo MA. Impact of Cyber Attacks on High Voltage DC Transmission Damping Control. Energies. 2018; 11(5):1046. https://doi.org/10.3390/en11051046
Chicago/Turabian StyleFan, Rui, Jianming Lian, Karanjit Kalsi, and Marcelo A. Elizondo. 2018. "Impact of Cyber Attacks on High Voltage DC Transmission Damping Control" Energies 11, no. 5: 1046. https://doi.org/10.3390/en11051046





