Security-Enhanced Push Button Configuration for Home Smart Control †
Abstract
:1. Introduction
- This paper proposes an efficient detection of the pairing establishment with a malicious or unintended device by bookkeeping all of the pairing messages during the setup period (of 2 min) without requiring the exchange of pre-shared keys a priori.
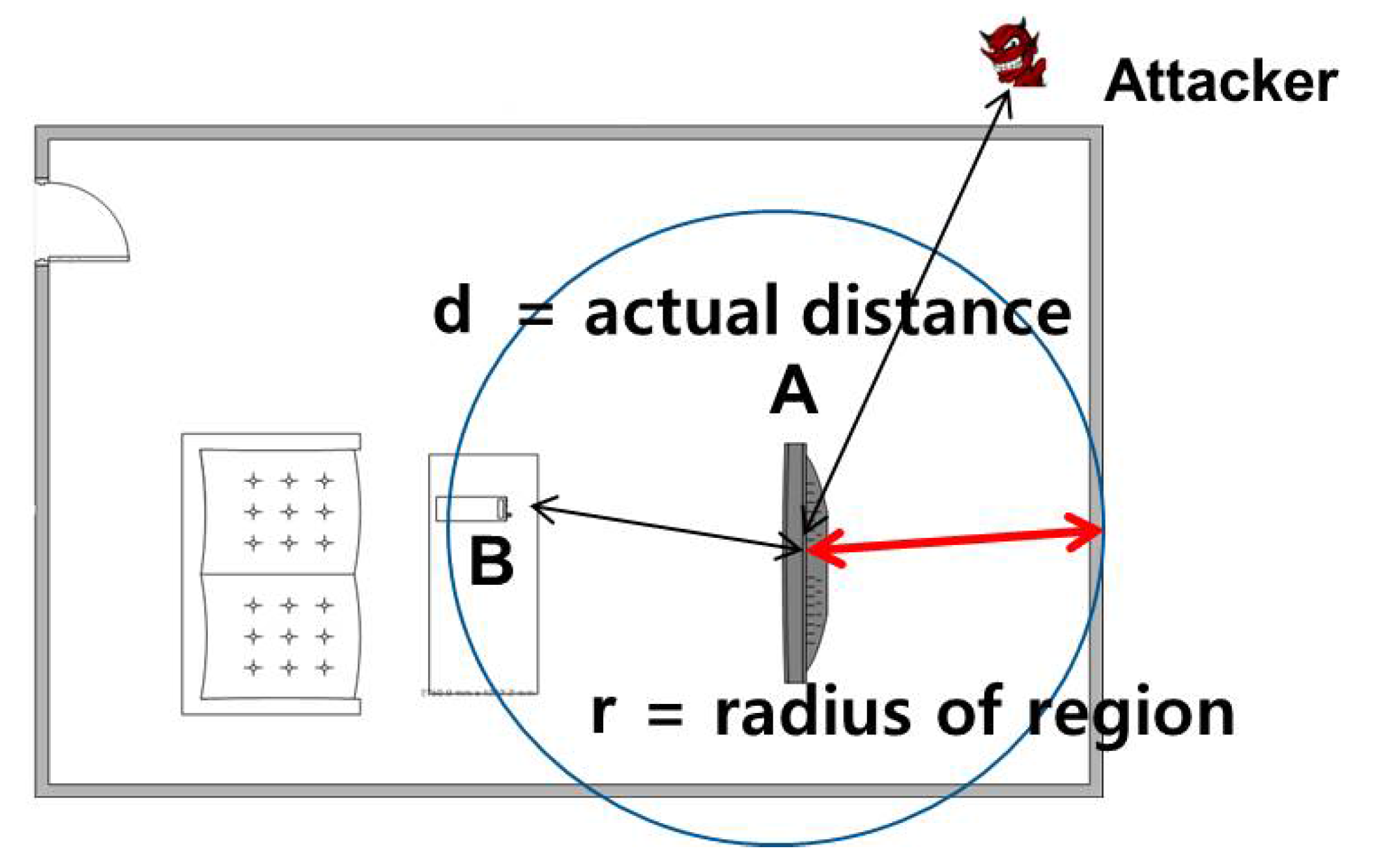
- The proposed approach identifies which pairing message is from a genuine or intended device by estimating the distances to all of the target devices (using ultrasound sensors) and deciding the closest as the pairing counterpart. Note that the proposed distance measurement protocol is not just about accuracy, but more about authenticity.
- Hence, this paper develops a secure handshake distance measurement protocol by preventing an adversary sitting outside the region from maliciously manipulating its distance.
- We actually verified the feasibility of the proposed mechanism by implementing RF and PWM-based ultrasound communication.
2. Related Works
2.1. Smart Home Control
2.2. Push Button Configuration
- Numeric comparison
- Passkey entry
- Out of band
- Just works
3. Problem Statement
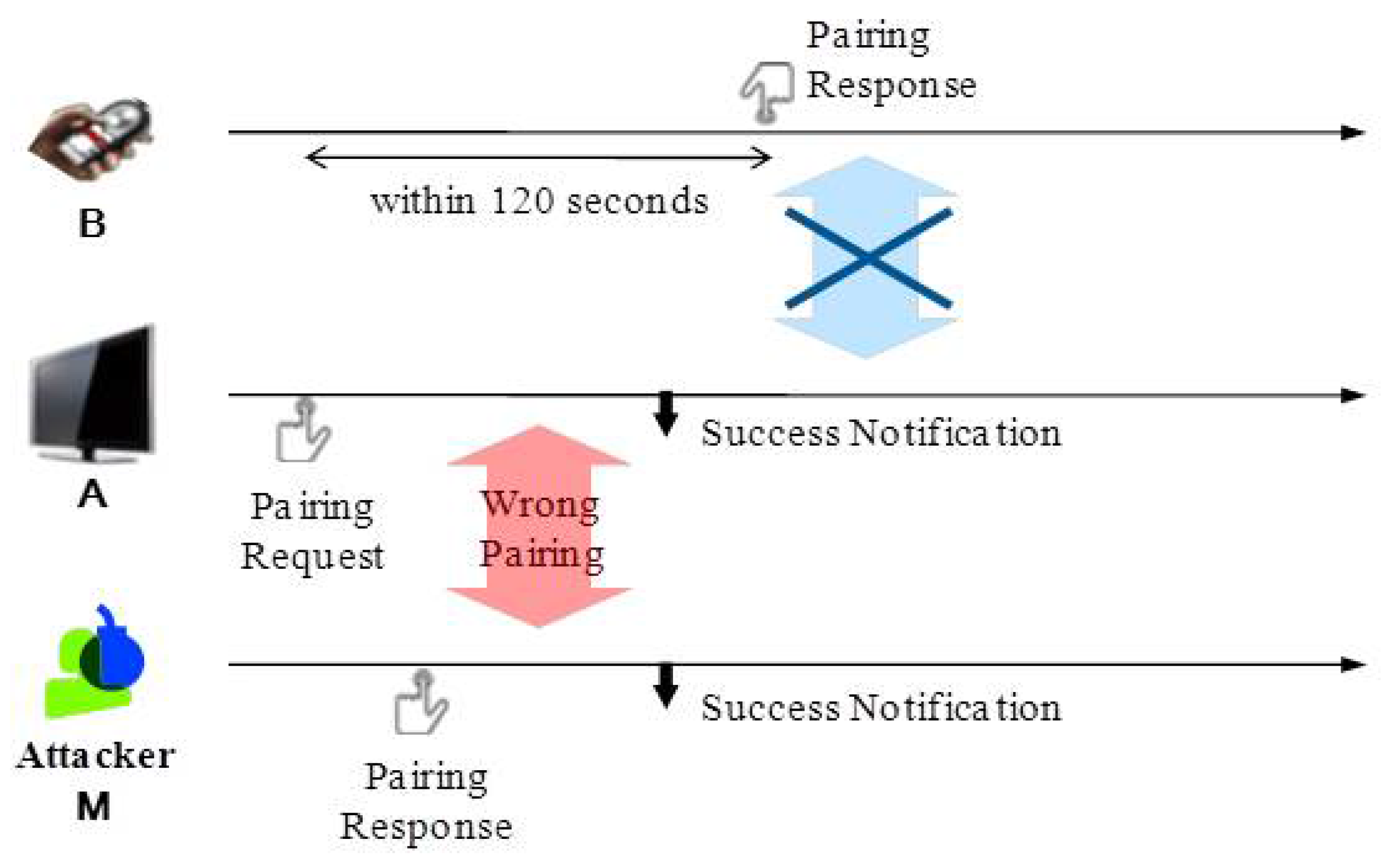
3.1. Attack Scenario
3.2. Design Goals
- Compatibility with the original PBC: It is desirable to keep the PBC-based User Interface (UI) rather than introducing a brand new mechanism, and hence, it is critically important to make SePBC compatible with the original PBC in the sense that a user still presses buttons on devices without worrying about possible attacks. Accordingly, we use PairingRequest and PairingResponse messages defined in the original PBC as is.
- Accuracy of attack detection: SePBC must achieve highly accurate detection of attacks in terms of minimizing both false positives and false negatives.
- Low-cost: SePBC must use lightweight operations and employ inexpensive hardwares . Moreover, it needs to incur little overhead when there is no attack.
4. Proposed Approach
4.1. Key Idea
- Q1. How does one detect if the wrong pairing could have been made with a malicious or misbehaving device?
- Q2. How does one tell which pairing message is from the intended device and thus has to be accepted?
4.2. Assumption
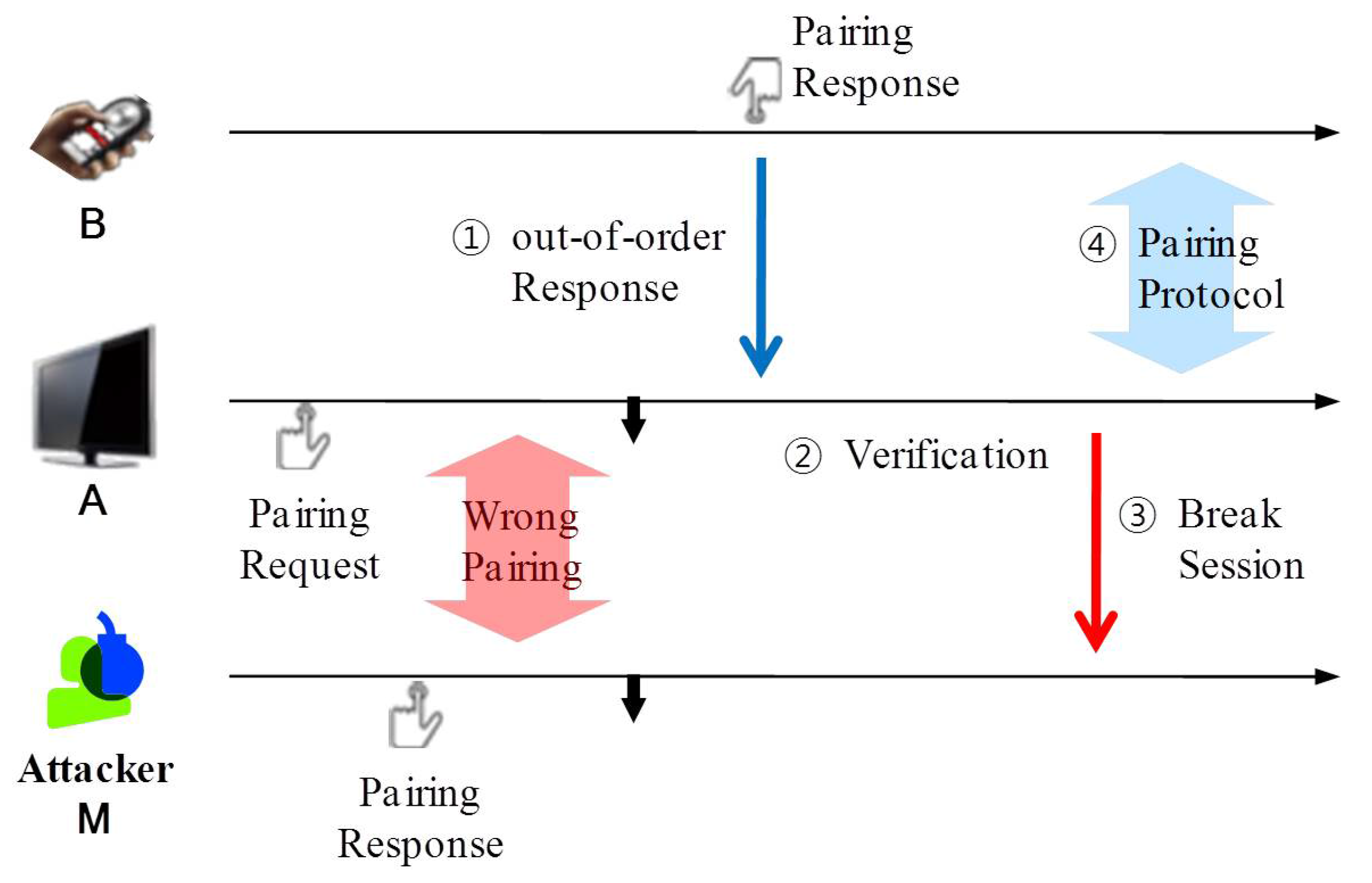
4.3. How Does SePBC Work?
4.4. Verification Scheme
4.4.1. RSS-Based Verification
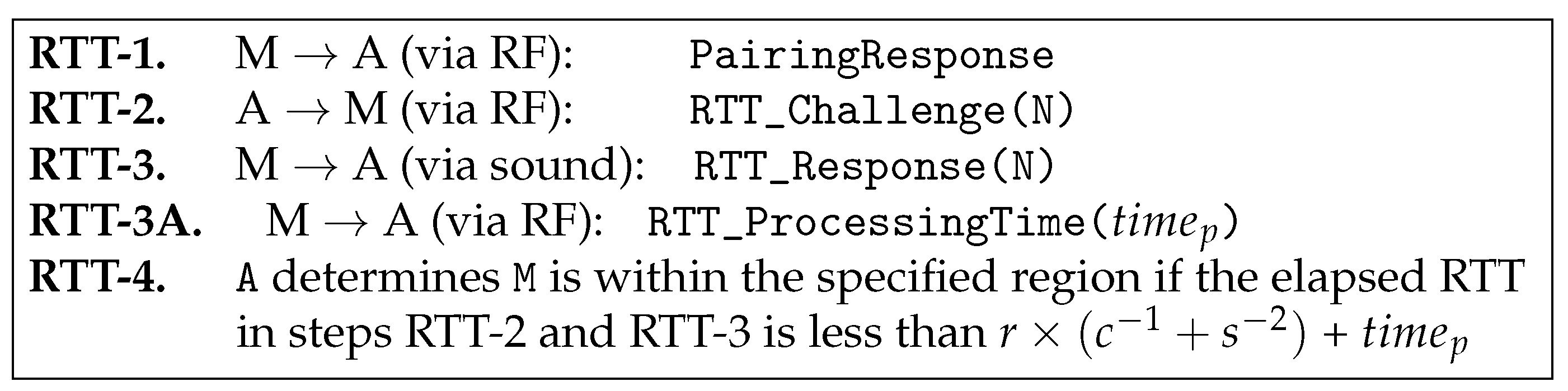
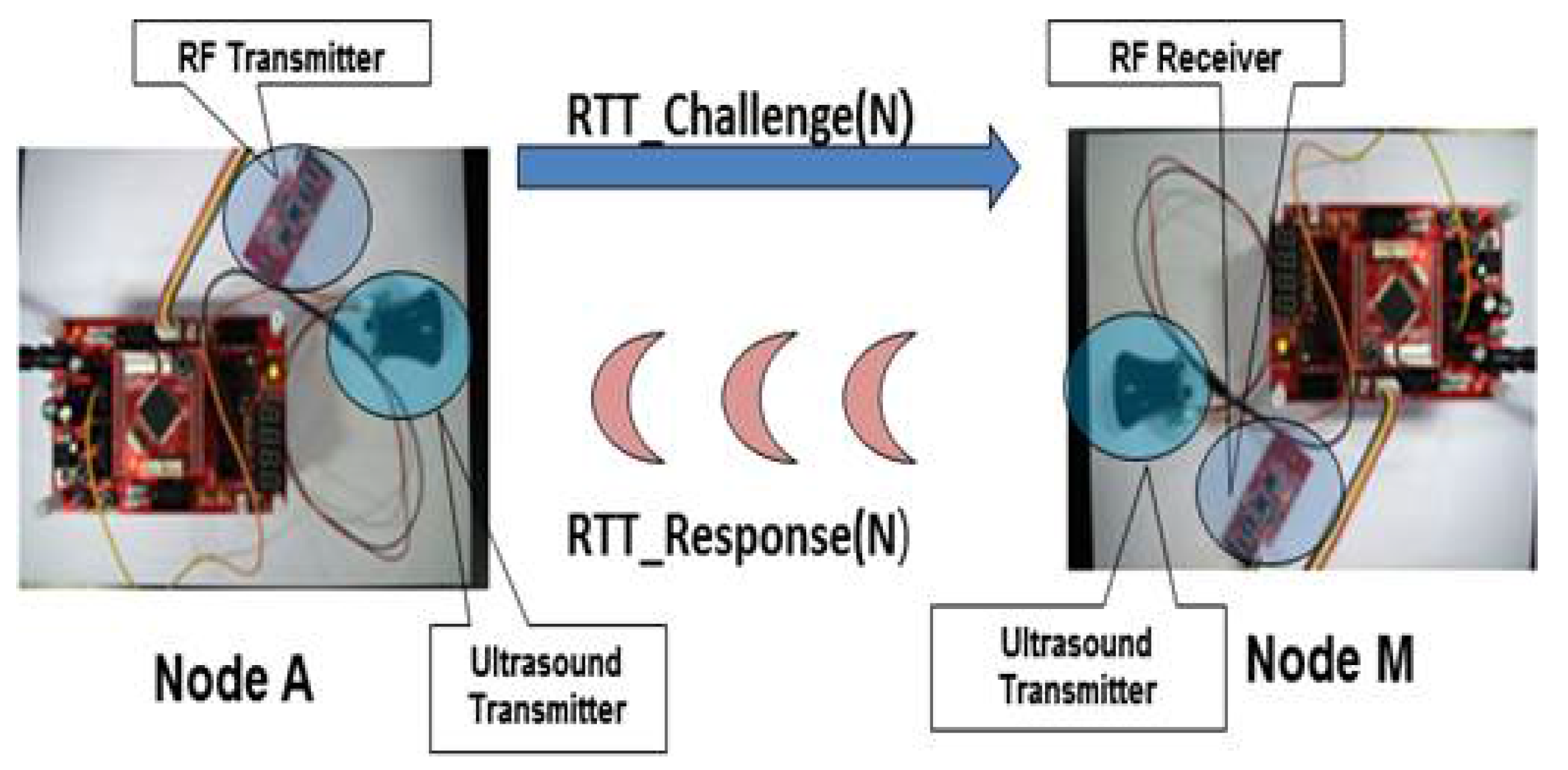
4.4.2. RTT-Based Verification
4.5. Security Challenges
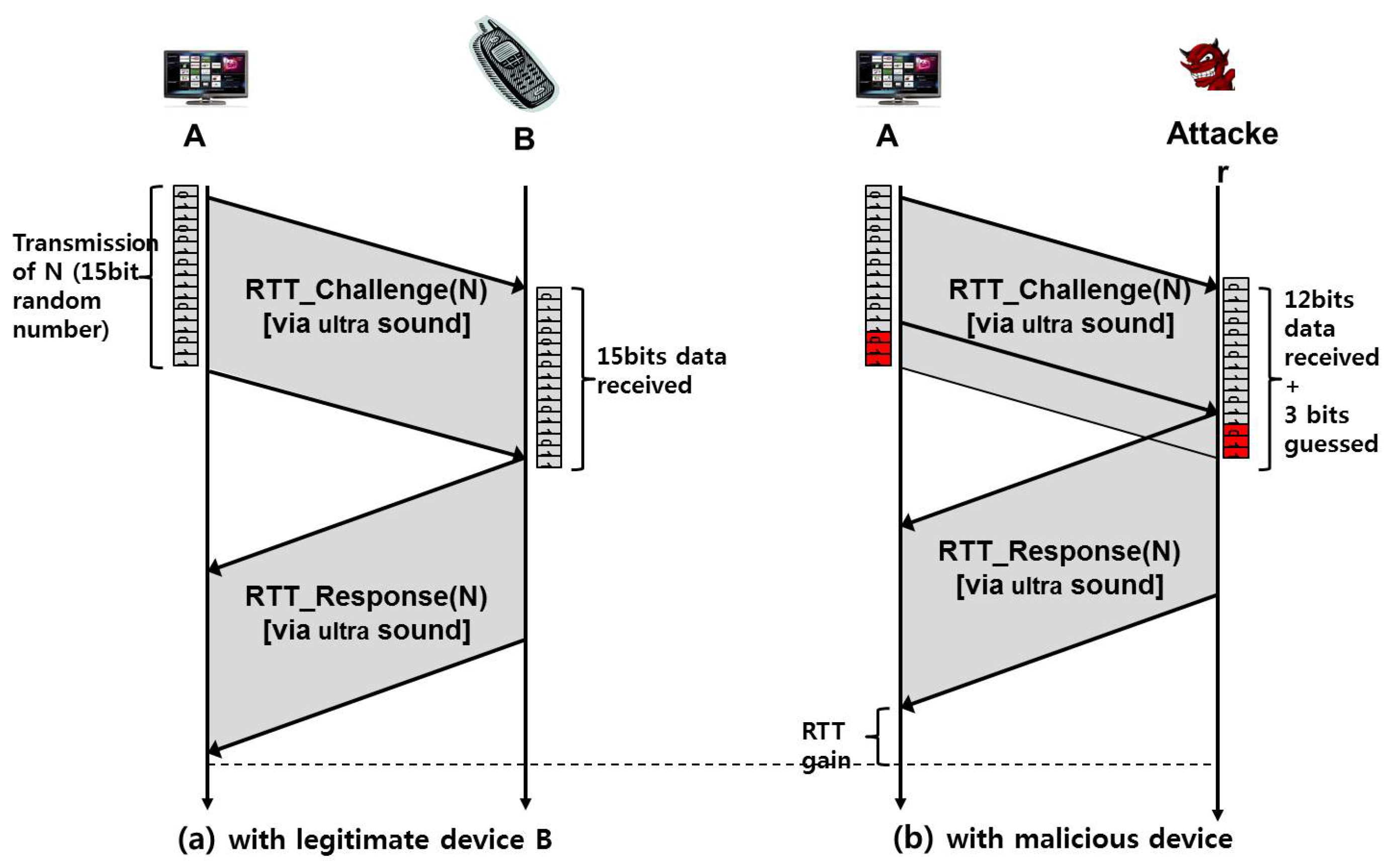
- First, we use a sound (or ultrasound) interface for RTT-3 in Figure 4 instead of using RF communication, mainly because increased RTT measurements by the sound interface makes it less sensitive to the timing jitters, thus increasing the accuracy of verification.
- Second, the two proposed messages, RTT_Challenge(N) and RTT_Response(N), include a random number N. Thanks to this feature, an adversary sitting outside the region cannot fool the verifying node into thinking him/her to be inside, for the following reason. The adversary is unable to get his/her RTT_Response packet to arrive in time at the verifying device due to the law of physics, and hence, he/she has no other way but to start transmitting the packet earlier. However, this is impossible, as well, because the verifying device transmits a random number that cannot be guessed by the adversary and asks the same number to be returned, which means the adversary should wait for the completion of packet reception.
- Third, we use the sound interface only in a return path (RTT-3: RTT_Response(N)), not in a forwarding path (RTT-2: RTT_Challenge(N)). We intentionally design our protocol this way to prevent further potential attacks as described below. Suppose we use the sound interface in RTT-2, as well as in RTT-3. In this case, the attacking node M can return the signal in the middle of the transmission without waiting for the completion of packet reception. For example, in Figure 5, assuming that a random number N consists of 15 bits, a malicious node M can send RTT_Response(N) as soon as it receives the 12th bit without waiting for the last three bits, 13th~15th bits. By guessing the 13th~15th bits to be one of eight combinations (i.e., 000, 001, ..., 111), it can send a response message sooner than otherwise. In other words, with a 12.5% probability of success, an attacker M is able to return a “valid” RTT_Response(N) message without waiting for the completion of packet reception. By intentionally returning RTT_Response(N) earlier than when it was supposed to do, it can shorten the round-trip time. It can result in that the measured distance is shorter than the actual distance. Note that this issue is negligible in high-speed RF communication, but it can be problematic in low-speed ultrasound transmission. To protect the PBC against this potential attack, we send RTT_Challenge(N) via RF instead of sound transmission. On the other hand, in the return path (i.e., RTT_Response(N)), we can use sound transmission without worrying about this problem because we are sure that the destination of the RTT_Response(N) message is a legitimate device, not an attacker.
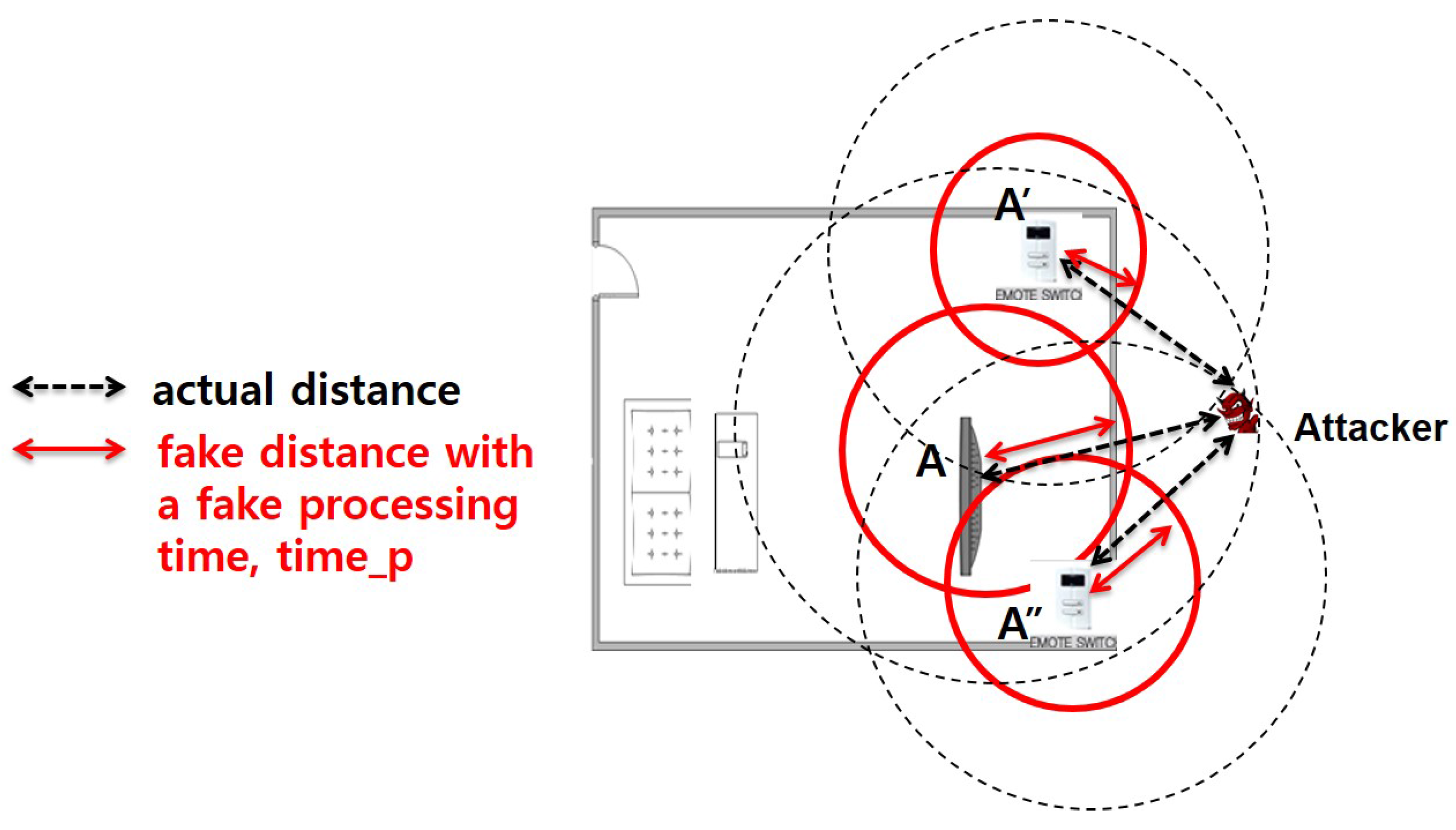
- Finally, there is another issue related to “processing time” at each device. Ideally, each device receives packets and sends them back immediately without any delay on the device. In this case, the round-trip time can be computed as the sum of inbound and outbound packet propagation and transmission times. However, in reality, each device requires some additional time duration to process the packet when it receives the packet before it sends it back. We call this delay the “processing time”. The processing time is not zero in practice, and furthermore, it is not a constant value, but depends on the platform specification of each device, such as CPU, memory, network card, and so on. As a consequence, some legitimate devices with large processing times might be mistakenly considered as attackers. Especially, general small size home appliances are likely to have low computing power CPUs and to generate large processing times. Figure 6 shows an example of such false alarms. In this figure, a remote control device, B, is physically located inside the acceptable range R. Suppose that the processing time of the device B is very large, and hence, its RTT measured at the server is too long. In this case, the device B might be considered as located outside the regions represented as the shaded area in Figure 6. To prevent this false alarm, this paper presents the extended version of the protocol, called eSePBC, in Section 4.6.
4.6. Handling of the Processing Time
5. Implementation and Experimental Results
5.1. Implementation
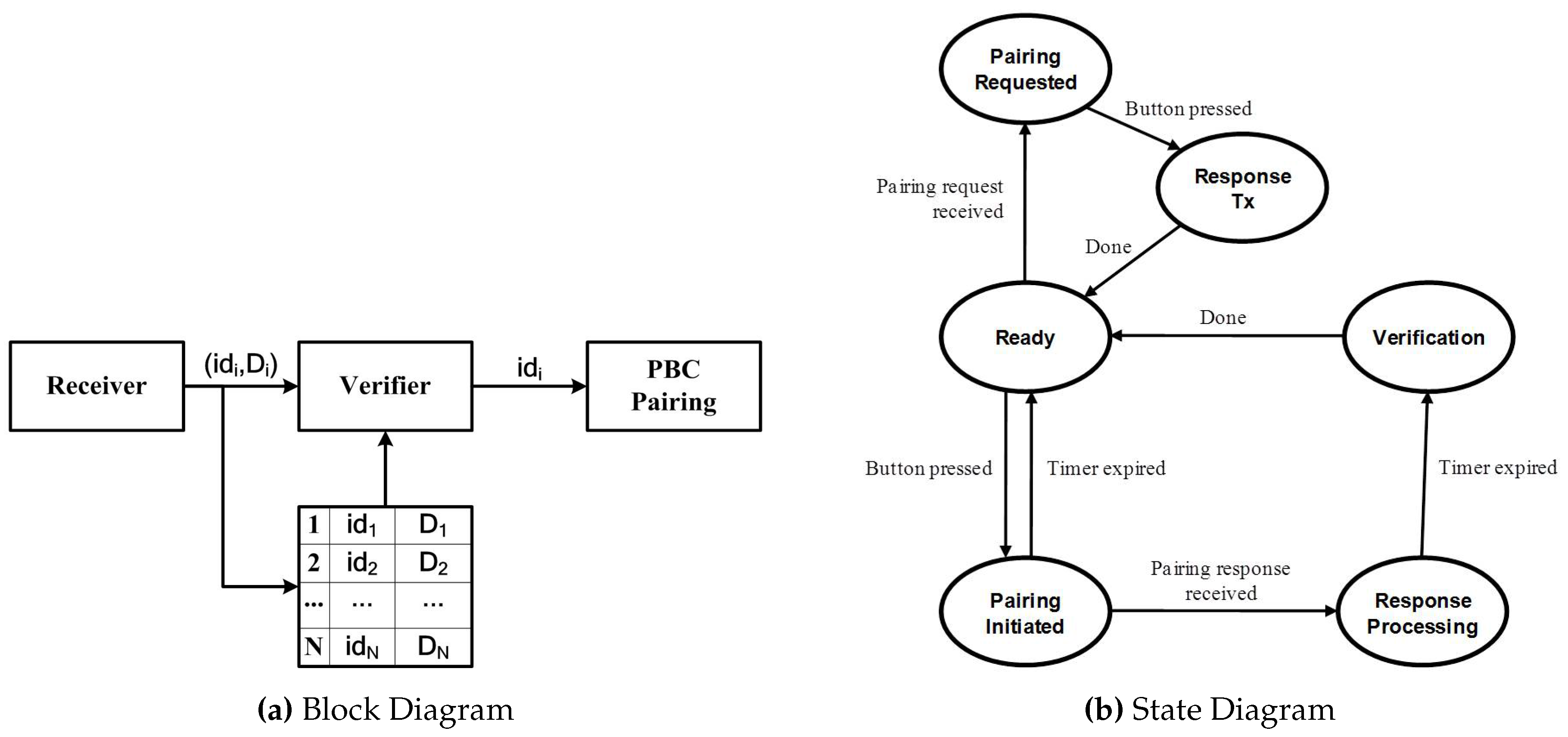
5.1.1. Block Diagram
- accepts PairingRequest or PairingResponse messages from external devices via an RF interface;
- constructs and combines it with the device’s to form ; and
- writes this tuple into the memory, as well as informs the verifier of the arrival of the first message.
- upon receiving notification of the first message arrival, controls the PBC pairing module to set up a secure session with a device, ;
- upon expiration of the timer, verifies, using RSS- and/or RTT-based schemes, each and every PairingResponse message to uncover harmful ones using the information stored in the memory; and
- if the verification results indicate that the pairing in Step (1) is wrong, it breaks the existing session with and executes the pairing protocol with , which has been determined to be the correct device.
5.1.2. State Transition Diagram
- Ready state: A waits for external events to trigger the SePBC; A makes a transition to the Pairing Requested state if receiving the PairingRequest message and to the Pairing Initiated state if its own PBC button is pressed.
- Pairing Requested state: A asks a user to press the PBC button and moves to the Response Sent state.
- Response Sent state: A returns to the Ready state after completing the transmission of the PairingResponse message.
- Pairing Initiated state: A first sends a PairingRequest message within the transmission radius and then waits for the reception of PairingResponse. A makes a transition to the Response Processing state if receiving the message within a setup interval, while going back to the Ready state if the setup timer expires with no message arrival. The latter means that no pairing takes place because it did not hear from any device.
- Response Processing state: A executes the pairing process with the first device, , that has responded to the request. A then waits until the setup timer expires, receiving and storing the PairingResponse messages from other devices. Finally, A goes to the Verification state after the timer runs out.
- Verification state: if no other PairingResponse message was received, A concludes that the current pairing is normal and thus returns to the Ready state. By contrast, if there were multiple receptions of PairingResponse messages, A determines the target device to be paired with, using ’s in the memory. That is, in the case of using RSS values as ’s, it chooses the device that has the largest RSS value among others. Hence, if , it again declares the current pairing as normal, taking no further action; otherwise, it breaks an existing pairing with followed by executing the pairing process with . Finally, A makes a transition to the Ready state.
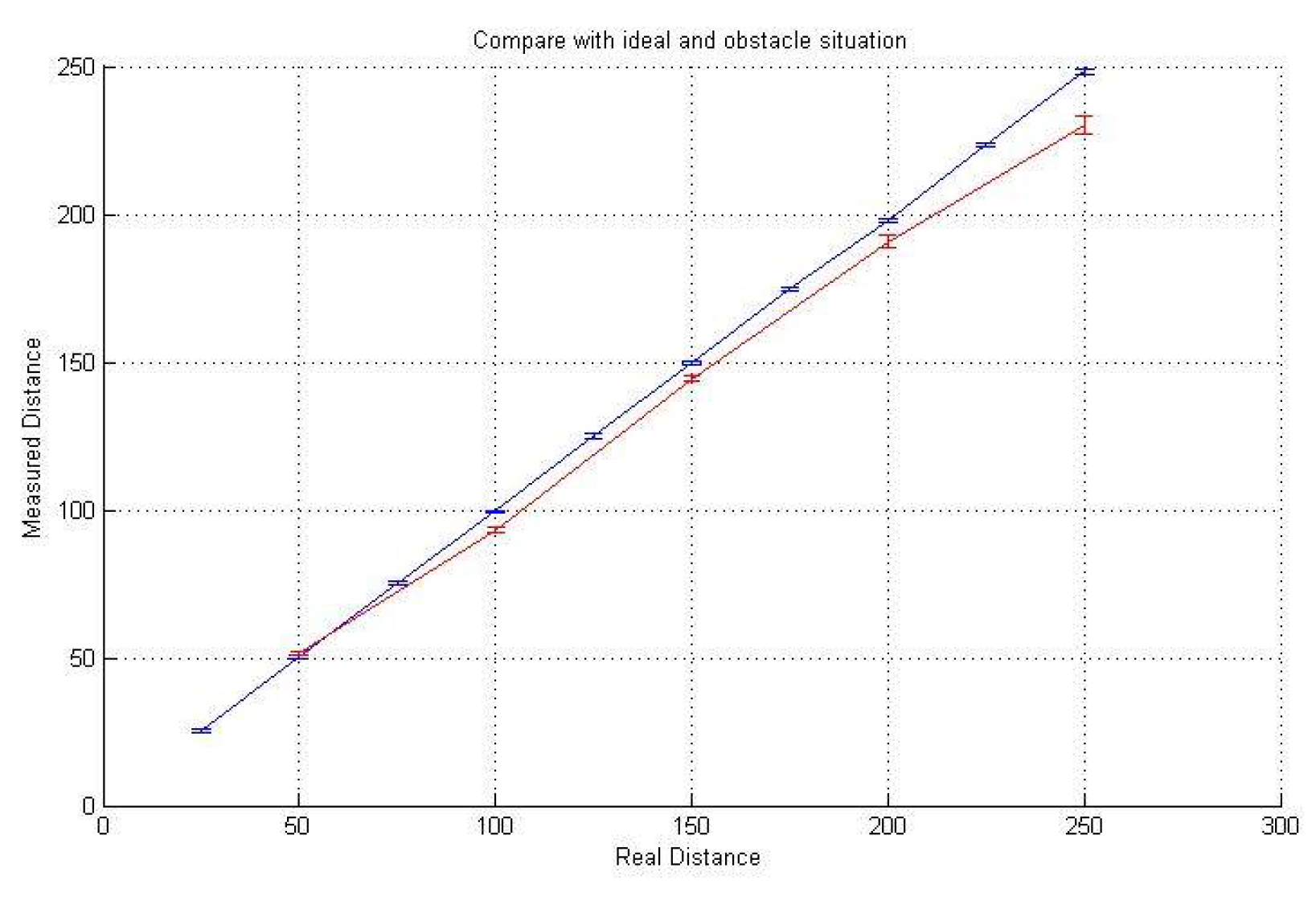
5.2. Experiment
5.3. Discussion
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| PBC | Push Button Configuration |
| SePBC | Secure Push Button Configuration |
| TDOA | Time Difference of Arrival |
| RSS | Received Signal Strength |
| AOA | Angle of Arrival |
References
- Smith, P. Comparing Low-Power Wireless Technologies. Available online: https://www.digikey.com/en/articles/techzone/2011/aug/ comparing-low-power-wireless-technologies (accessed on 15 December 2016).
- Google. Project Weave. Available online: https://developers.google.com/weave/ (accessed on 15 December 2016).
- Samsung. Available online: http://www.smartthings.com/ (accessed on 15 December 2016).
- Apple. HomeKit. Available online: http://www.apple.com/ios/homekit/ (accessed on 15 December 2016).
- Wi-Fi Alliance. Available online: http:ww.wi-fi.org/discover-wi-fi/wi-fi-protected-setup (accessed on 15 December 2016).
- ZigBee RF4CE: ZRC Profile Specification, version 1.0; ZigBee Alliance: San Ramon, CA, USA, 2009.
- BLUETOOTH: User Interface Flow Diagrams for Bluetooth Secure Simple Pairing Devices, Version 1.0. Available online: https://www.bluetooth.org/docman/handlers/downloaddoc.ashx?docid=86173 (accessed on 10 April 2017).
- Park, Y.; Park, T.; Park, M.; Han, J. How to Secure Push Button Configuration for Remote Control of Devices. In Proceedings of the 10th International Conference on Remote Engineering and Virtual Instrumentation (REV), Sydney, Australia, 6–8 February 2013. [Google Scholar]
- Han, J.; Choi, S.; Park, T. Maximizing lifetime of cluster-tree ZigBee networks under end-to-end deadline constraints. IEEE Commun. Lett. 2010, 14. [Google Scholar] [CrossRef]
- Yoon, M.K.; Lee, C.G.; Han, J. Migrating from Per-Job Analysis to Per-Resource Analysis for Tighter Bounds of End-to-End Response Times. IEEE Trans. Comput. 2010, 59, 933–942. [Google Scholar] [CrossRef]
- Han, J. Global Optimization of ZigBee Parameters for End-to-End Deadline Guarantee of Real-Time Data. IEEE Sens. J. 2009, 9, 512–514. [Google Scholar] [CrossRef]
- Collotta, M.; Pau, G. An Innovative Approach for Forecasting of Energy Requirements to Improve a Smart Home Management System Based on BLE. IEEE Trans. Green Commun. Netw. 2017, 1, 112–120. [Google Scholar] [CrossRef]
- Blanco-Novoa, O.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. An Electricity Price-Aware Open-Source Smart Socket for the Internet of Energy. Sensors 2017, 17, 643. [Google Scholar] [CrossRef] [PubMed]
- Longe, O.M.; Ouahada, K.; Rimer, S.; Harutyunyan, A.N.; Ferreira, H.C. Distributed Demand Side Management with Battery Storage for Smart Home Energy Scheduling. Sustainability 2017, 9, 120. [Google Scholar] [CrossRef]
- Collotta, M.; Pau, G. A Solution Based on Bluetooth Low Energy for Smart Home Energy Management. Energies 2015, 8, 11916–11938. [Google Scholar] [CrossRef]
- Bhati, A.; Hansen, M.; Chan, C.M. Energy conservation through smart homes in a smart city: A lesson for Singapore households. Energy Policy 2017, 104, 230–239. [Google Scholar] [CrossRef]
- Acs, G.; Castelluccia, C. Dream: Differentially Private Smart Metering. Available online: http://arxiv.org/abs/1201.2531 (accessed on 10 April 2017).
- Lin, H.; Bergmann, N.W. IoT Privacy and Security Challenges for Smart Home Environments. Information 2016, 7, 44. [Google Scholar] [CrossRef]
- Chitnis, S.; Deshpande, N.; Shaligram, A. An Investigative Study for Smart Home Security: Issues, Challenges and Countermeasures. Wirel. Sens. Netw. 2016, 8, 61–68. [Google Scholar] [CrossRef]
- Denning, T.; Kohno, T.; Levy, H.M. Computer security and the modern home. Commun. ACM 2013, 56, 94–103. [Google Scholar] [CrossRef]
- Earlence, F.; Jung, J.; Prakash, A. Security analysis of emerging smart home applications. In Proceedings of the 2016 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 22–26 May 2016. [Google Scholar]
- Kawaguchi, K. Groovy Sandbox. Available online: http://groovy-sandbox.kohsuke.org (accessed on 10 April 2016).
- Huang, Y.; Li, H.; Campbell, K.A.; Han, Z. Defending false data injection attack on smart grid network using adaptive CUSUM test. In Proceedings of the 2011 45th Annual Conference on Information Science and System Conference (CISS), Baltimore, MD, USA, 23–25 March 2011. [Google Scholar] [CrossRef]
- Singh, S.; Sharma, P.K.; Park, J.H. SH-SecNet: An Enhanced Secure Network Architecture for the Diagnosis of Security Threats in a Smart Home. Sustainability 2017, 9, 513. [Google Scholar] [CrossRef]
- Park, T.; Shin, K.G. Attack-tolerant localization via iterative verification of locations in sensor networks. ACM Trans. Embed. Comput. Syst. 2008, 8. [Google Scholar] [CrossRef]
- Savarese, C.; Rabay, J.; Langendoen, K. Robust positioning algorithms for distributed ad-hoc wireless sensor networks. In Proceedings of the USENIX Annual Technical Conference, USENIX, Monterey, CA, USA, 10–15 June 2002. [Google Scholar]
- Whitehouse, K.; Culler, D. Calibration as parameter estimation in sensor networks. In Proceedings of the 1st ACM International Workshop on Wireless Sensor Networks and Application, New York, NY, USA, 28 September 2002. [Google Scholar]
- Broeck, V.; Skudelny, H.; Stanke, G.V. Analysis and realization of a pulse width modulator based on voltage space vectors. IEEE Trans. Ind. Appl. 1988, 24, 142–150. [Google Scholar] [CrossRef]
- US Secure Hash Algorithm 1 (SHA1). Available online: https://tools.ietf.org/html/rfc3174 (accessed on 30 April 2017).


| Period (Pulse Width) | 3-Bit Data Frame |
|---|---|
| 24 ms | 000 |
| 40 ms | 001 |
| 56 ms | 010 |
| 72 ms | 011 |
| 88 ms | 100 |
| 104 ms | 101 |
| 120 ms | 110 |
| 137 ms | 111 |
| 184 ms | Boundary (flag) |
| Measured End-to-End RTT | Processing Time | Transmission Time of RTT_Response(N) (c) | Propagation Delay (Distance = 6 m) | Noise (e = |a − (b + c + d)|) | ||
|---|---|---|---|---|---|---|
| N(9 Bit Random Number) | (a) | (b) | 1 Purse (Frag Frame) | 3 Purses (9 Bit Data Frame) (= Sum of 3 Frame Widths) | (d) | (e) |
| 001001001 | 325.5 | 2.35 | 184 | 120 | 17.65 | 1.5 |
| 010010010 | 374.376 | 2.35 | 184 | 168 | 17.65 | 2.376 |
| 011011011 | 422.4 | 2.35 | 184 | 216 | 17.65 | 2.4 |
| 100100100 | 466.9 | 2.35 | 184 | 264 | 17.65 | 1.1 |
| 101101101 | 518.48 | 2.35 | 184 | 312 | 17.65 | 2.48 |
| 110110110 | 566.488 | 2.35 | 184 | 360 | 17.65 | 2.488 |
| 111111111 | 613.9 | 2.35 | 184 | 411 | 17.65 | 1.1 |
| Distance (cm) | Min (ms) | Median (ms) | Max (ms) |
|---|---|---|---|
| 100 | 311.184 | 311.200 | 311.200 |
| 150 | 312.480 | 312.480 | 312.528 |
| 200 | 313.856 | 313.904 | 313.968 |
| 250 | 315.264 | 315.296 | 315.312 |
| 300 | 316.688 | 316.688 | 316.704 |
| 350 | 318.160 | 318.176 | 318.176 |
| 400 | 319.632 | 319.648 | 319.648 |
| 450 | 321.120 | 321.200 | 321.232 |
| 500 | 322.592 | 322.608 | 322.704 |
| 550 | 324.032 | 324.080 | 324.160 |
| 600 | 325.536 | 325.584 | 325.568 |
| Method | Processing Time at a Device A | Code Size (bytes) |
|---|---|---|
| SePBC | 2.7 ms | about 1500 |
| SHA-1 | 4.9 ms | about 3900 (only cryptography module) |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Han, J.; Park, T. Security-Enhanced Push Button Configuration for Home Smart Control. Sensors 2017, 17, 1334. https://doi.org/10.3390/s17061334
Han J, Park T. Security-Enhanced Push Button Configuration for Home Smart Control. Sensors. 2017; 17(6):1334. https://doi.org/10.3390/s17061334
Chicago/Turabian StyleHan, Junghee, and Taejoon Park. 2017. "Security-Enhanced Push Button Configuration for Home Smart Control" Sensors 17, no. 6: 1334. https://doi.org/10.3390/s17061334







