- Article
Denoising Adaptive Multi-Branch Architecture for Detecting Cyber Attacks in Industrial Internet of Services
- Ghazia Qaiser and
- Siva Chandrasekaran
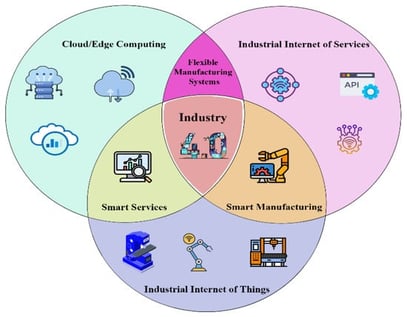
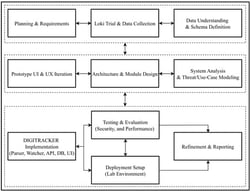
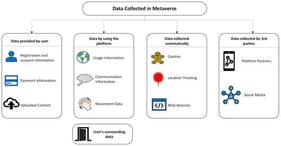
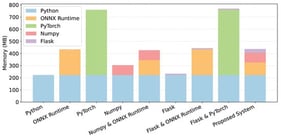
The emerging scope of the Industrial Internet of Services (IIoS) requires a robust intrusion detection system to detect malicious attacks. The increasing frequency of sophisticated and high-impact cyber attacks has resulted in financial losses and catastrophes in IIoS-based manufacturing industries. However, existing solutions often struggle to adapt and generalize to new cyber attacks. This study proposes a unique approach designed for known and zero-day network attack detection in IIoS environments, called Denoising Adaptive Multi-Branch Architecture (DA-MBA). The proposed approach is a smart, conformal, and self-adjusting cyber attack detection framework featuring denoising representation learning, hybrid neural inference, and open-set uncertainty calibration. The model merges a denoising autoencoder (DAE) to generate noise-tolerant latent representations, which are processed using a hybrid multi-branch classifier combining dense and bidirectional recurrent layers to capture both static and temporal attack signatures. Moreover, it addresses challenges such as adaptability and generalizability by hybridizing a Multilayer Perceptron (MLP) and bidirectional LSTM (BiLSTM). The proposed hybrid model was designed to fuse feed-forward transformations with sequence-aware modeling, which can capture direct feature interactions and any underlying temporal and order-dependent patterns. Multiple approaches have been applied to strengthen the dual-branch architecture, such as class weighting and comprehensive hyperparameter optimization via Optuna, which collectively address imbalanced data, overfitting, and dynamically shifting threat vectors. The proposed DA-MBA is evaluated on two widely recognized IIoT-based datasets, Edge-IIoT set and WUSTL-IIoT-2021 and achieves over 99% accuracy and a near 0.02 loss, underscoring its effectiveness in detecting the most sophisticated attacks and outperforming recent deep learning IDS baselines. The solution offers a scalable and flexible architecture for enhancing cybersecurity within evolving IIoS environments by coupling feature denoising, multi-branch classification, and automated hyperparameter tuning. The results confirm that coupling robust feature denoising with sequence-aware classification can provide a scalable and flexible framework for improving cybersecurity within the IIoS. The proposed architecture offers a scalable, interpretable, and risk sensitive defense mechanism for IIoS, advancing secure, adaptive, and trustworthy industrial cyber-resilience.
5 February 2026