A Nonlinear Programming Approach to Solving Interval-Valued Intuitionistic Hesitant Noncooperative Fuzzy Matrix Games
Abstract
:1. Introduction
- A novel aggregation operator is introduced in this study, which is referred to as the min-max enclosure operator. This operator is specifically designed for the aggregation of IIHF information. One of the advantages of the proposed operator is its simplicity, which makes it easy to implement and use. Additionally, the operator has the capability to preserve the characteristics of IIHFEs, ensuring that the important features of the information are not lost during the aggregation process.
- A nonlinear programming approach is delineated in this paper to handle interval-valued intuitionistic hesitant fuzzy programming problems to solve IIHF matrix games. In order to achieve the best possible outcomes, these problems are converted into two distinct crisp nonlinear programming problems.
- Like in classical game theory, it is established that the gain floor of the winning player is less than or equal to the loss ceiling of the defeated player.
- The proposed methodology is illustrated through the problem of cybercrime. The superiority of the proposed method is checked and verified by analyzing a comparative study with two existing models.
2. Preliminaries
- for any positive scalar
- (i)
- If then
- (ii)
- If then
- (iii)
- If then
- (a)
- If then
- (b)
- If then
- (c)
- If then
- (i)
- Consider two IIFHEs, and Then and which concludes that
- (ii)
- Suppose and Then and which So, in this case, we cannot assign the ranking based on the score function, and we have to calculate the accuracy function of these two IIHFEs. Now and , which concludes
3. New Aggregation Operator
- (i)
- Monotonicity: If for then
- (ii)
- Idempotency:
- (iii)
- Boundedness:
4. Matrix Games with IIHFE Payoffs
Algorithm
- Step 1:
- Consider a matrix game whose payoffs are taken as IIHFEs, say, where and
- Step 2:
- To solve the game, we have to derive two BOIIHFPMs, as depicted in Problems (16) and (17).
- Step 3:
- To handle the situation, the fuzzy programming problems are converted into two nonlinear programming Problems (29) and (39), respectively, by using the mathematical operations of IIHFEs.
- Step 4:
- To obtain the optimal strategies for Player and for Player the NLPPs (29) and (39) are solved using WOLFRAM MATHEMATICA 9.0 software.
- Step 5:
- Utilizing the optimal strategies and in Equation (4), we can find the aggregated expected payoff of Player
5. Numerical Application
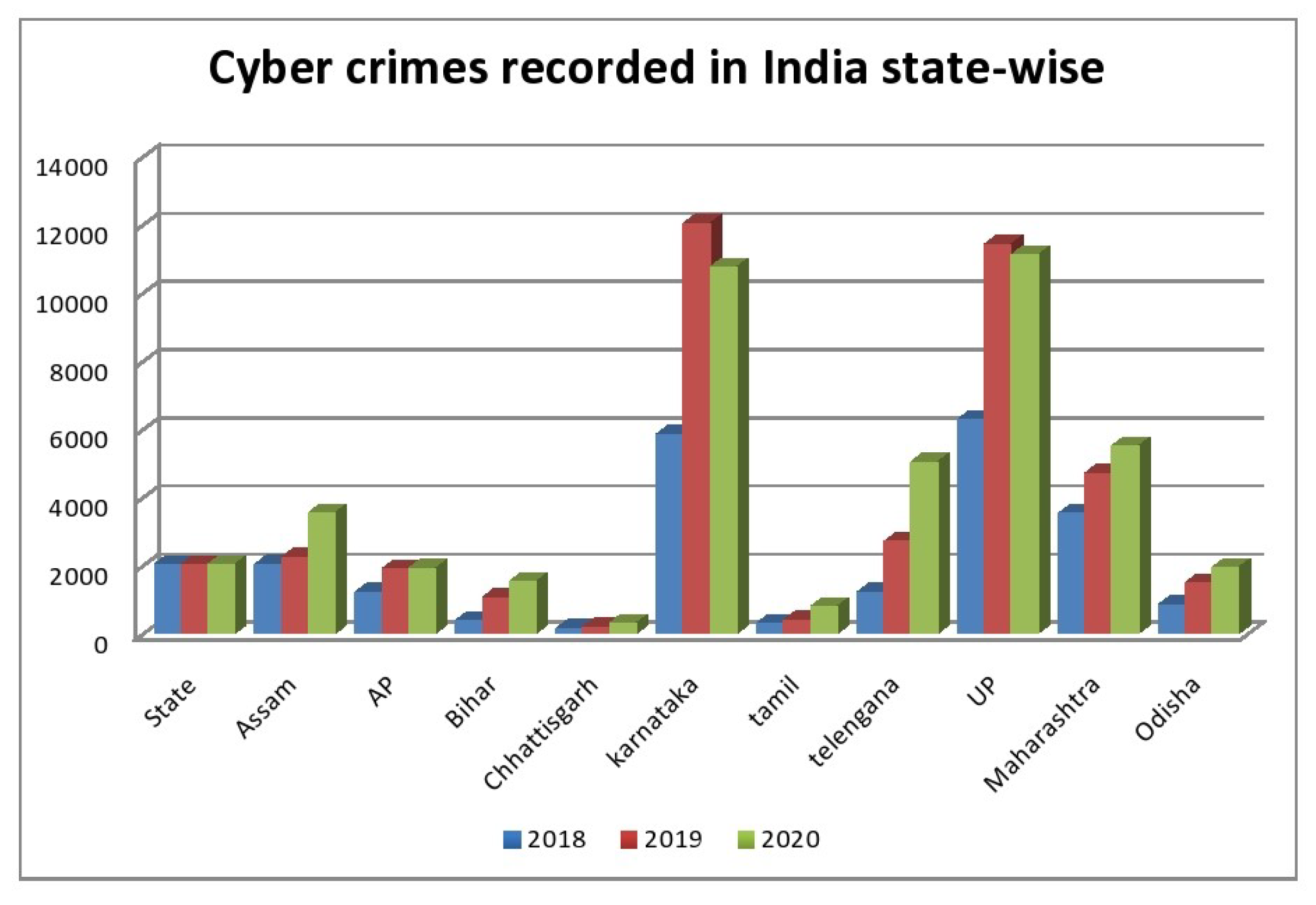
Application to Preventing Cybercrime
- :
- Installing a powerful firewall.
- :
- Using updated software.
- :
- Breaking the security password.
- :
- Sending suspicious links.
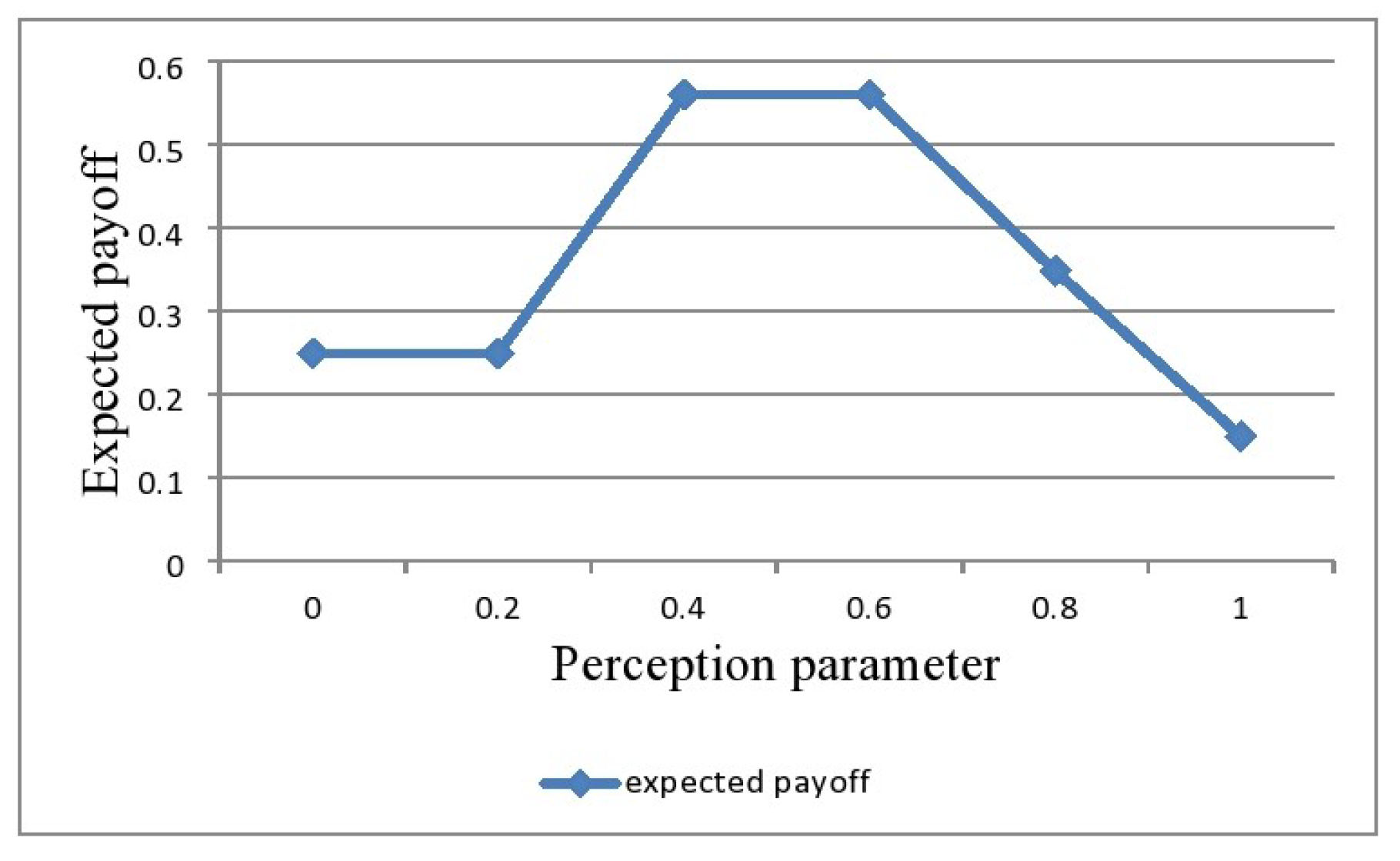
- Table 5 shows that for , we obtain the optimal strategies for the players as and . Furthermore, Player ’s aggregated expected payoff is obtained as ; . In other words, we may say that if Player ’s, i.e., the defenders’, control strategies are with a probability of 0.4518 and with a probability of 0.5482 while Player ’s, i.e., the hackers’, governing strategies are with a probability of 0.0096 and with a probability of 0.9904, and also, Player is very much optimistic toward the information, then the DMs come to an inference that the damage will be reduced with a surety from to and with a disbelief from to
- Table 5 shows that for all the values of the perception parameter This symbolizes that the crisp equivalent of the amount of gain of Player does not exceed the crisp equivalent amount of loss of Player
- Actually, the perception parameter captures the behavior of the players. From Table 5, we can see the crisp equivalent gain of Player and the crisp equivalent loss of Player both are gradually increased with the increment of the perception parameter chosen by the players. That indicates the gain value of Player is maximum when he/she is optimistic enough.
- The score values of expected payoff for Player are increased for and are decreased for This indicates that we can achieve the expected payoff for Player at the maximum level when the players are neutral in nature. This shows the importance of the role of the perception parameter in our proposed model.
- From Table 5, it is observed that the optimal strategies of the players change significantly with the changes in the perception parameter Both of the players use pure strategies only when the perception parameter lies in the interval Otherwise, the players use mixed strategies with some probabilities. For example, when Player uses strategies and with probabilities 0.4518 and 0.5482, respectively, while Player uses strategies and with probabilities 0.0096 and 0.9904, respectively. Therefore, the players have the freedom to change their strategies with the changes in to optimize their expected payoffs.
6. Comparative Analysis and Discussion
6.1. Comparison with Bhaumik and Roy [39]
- (i)
- In our proposed method, the perception parameter plays a significant role. Table 5 shows that Player ’s gain-floor, Player ’s loss ceiling, and Player s expected payoff are changed with the changes in the perception parameter . It is observed that when the players are optimistic toward the information, i.e., when lies in players have better gain values. Hence, the players have the option to choose different parameter values to obtain better gains. However, in Bhaumik and Roy’s [39] methodology, there is no such parameter that can improve the gain of the player.
- (ii)
- In classical game theory, there is a most celebrated result that the gain floor of the winning player never exceeds the loss ceiling of the defeated player. In Theorem 2, we showed that this endures also in the IIHF environment. However, if we solve the same problem by Bhaumik and Roy’s [39] approach, we have . Table 6 shows that the gain floor is greater than the loss ceiling , which contradicts the statement of Theorem 2.
- (iii)
- (iv)
- Furthermore, it is worth noting that we need to preserve the hesitant character of IIHFEs. However, to preserve the character, if we apply mathematical operations for IIHFEs in the interval-valued intuitionistic hesitant fuzzy programming models, it yields two NLPP models instead of LP models. This phenomenon raises an essential question on the validation of Bhaumik and Roy’s [39] approach.
6.2. Comparison with Xue et al. [45]
- (i)
- (ii)
- Using the optimal strategies and for Players and , respectively, if we calculate the expected payoff for Player we have The score function of this expected payoff is which gives a better value than the existing one [45].
- (iii)
- Moreover, Xue et al. [45] considered only the hesitancy of decision makers to portray the matrix game problem. However, occasionally in practical problems, DMs fail to judge the asymmetric information scenario properly. As a result, they cannot assign any precise value. Consequently, they have to choose some interval values to assign the payoffs. In that sense, delineating a matrix game problem in an intuitionistic interval-valued hesitant fuzzy environment is more realistic in the literature.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Neumann, J.V.; Morgenstern, O. Theory of Games and Economic Behaviour; Princeton University Press: Princeton, NJ, USA, 1947. [Google Scholar]
- Dubois, D.; Prade, H. Fuzzy Sets and Systems: Theory and Applications; Academic Press: New York, NY, USA, 1980. [Google Scholar]
- Mi, X.; Liao, H.; Zeng, X.J.; Xu, Z. The two-person and zero-sum matrix game with probabilistic linguistic information. Inf. Sci. 2021, 570, 487–499. [Google Scholar] [CrossRef]
- Chandra, S.; Aggarwal, A. On solving matrix games with pay-offs of triangular fuzzy numbers: Certain observations and generalizations. Eur. J. Oper. Res. 2015, 246, 575–581. [Google Scholar] [CrossRef]
- Atanassov, K.T. Intuitionistic fuzzy sets. Fuzzy Sets Syst. 1986, 20, 87–96. [Google Scholar] [CrossRef]
- Li, D.F. Mathematical-programming approach to matrix games with payoffs represented by Atanassov’s interval-valued intuitionistic fuzzy sets. IEEE Trans. Fuzzy Syst. 2010, 18, 1112–1128. [Google Scholar] [CrossRef]
- Li, D.F. Decision and Game Theory in Management with Intuitionistic Fuzzy Sets; Springer: Berlin, Germany, 2014. [Google Scholar]
- Xia, M. Interval-valued intuitionistic fuzzy matrix games based on archimedean t-conorm and t-norm. Int. J. Gen. Syst. 2018, 47, 278–293. [Google Scholar] [CrossRef]
- Brikaa, M.G.; Zheng, Z.; Ammar, E.S. Resolving indeterminacy approach to solve multi-criteria zero-sum matrix games with intuitionistic fuzzy goals. Mathematics 2020, 8, 305. [Google Scholar] [CrossRef]
- Verma, T.; Kumar, A. Ambika methods for solving matrix games with Atanassov’s intuitionistic fuzzy pay-offs. IEEE Trans. Fuzzy Syst. 2018, 26, 270–283. [Google Scholar] [CrossRef]
- Verma, R.; Aggarwal, A. Matrix games with linguistic intuitionistic fuzzy payoffs: Basic results and solution methods. Artif. Intell. Rev. 2021, 54, 5127–5162. [Google Scholar] [CrossRef]
- Dong, J.Y.; Wan, S.P. Type-2 interval-valued intuitionistic fuzzy matrix game and application to energy vehicle industry development. Expert Syst. Appl. 2024, 249, 123398. [Google Scholar] [CrossRef]
- Seikh, M.R.; Karmakar, S.; Castillo, O. A novel defuzzification approach of type-2 fuzzy variable to solving matrix games: An application to plastic ban problem. Iran. J. Fuzzy Syst. 2021, 18, 155–172. [Google Scholar]
- Yang, Y.D.; Ding, X.F. A q rung orthopair fuzzy non cooperative game method for competitive strategy group decision making problems based on a hybrid dynamic experts’ weight deter-mining model. Complex Intell. Syst. 2021, 7, 3077–3092. [Google Scholar] [CrossRef]
- Bigdeli, H.; Mousazadeh, M. Analytical Hierarchy Process in modeling and solving matrix games in neutrosophic environment and its application in military problems. Mil. Sci. Tactics 2023, 19, 5–33. [Google Scholar]
- Seikh, M.R.; Dutta, S. Solution of matrix games with payoffs of single-valued trape-zoidal neutrosophic numbers. Soft Comput. 2022, 26, 921–936. [Google Scholar] [CrossRef]
- Seikh, M.R.; Dutta, S. Interval neutrosophic matrix game-based approach to counter cybersecurity issue. Granul. Comput. 2023, 8, 271–292. [Google Scholar] [CrossRef]
- Khalil, A.M.; Cao, D.; Azzam, A.; Smarandache, F.; Alharbi, W.R. Combination of the single-valued neutrosophic fuzzy set and the soft set with applications in decision-making. Symmetry 2020, 12, 1361. [Google Scholar] [CrossRef]
- Torra, V. Hesitant fuzzy sets. Int. J. Intell. Syst. 2010, 25, 529–539. [Google Scholar] [CrossRef]
- Xia, M.; Xu, Z.S. Hesitant fuzzy information aggregation in decision making. Int. J. Approx. Reason. 2011, 52, 395–407. [Google Scholar] [CrossRef]
- Xu, Z.S.; Xia, M. Distance and similarity measures for hesitant fuzzy sets. Inform. Sci. 2011, 181, 2128–2138. [Google Scholar] [CrossRef]
- Zeng, W.; Li, D.; Yin, Q. Weighted interval-valued hesitant fuzzy sets and its application in group decision making. Int. J. Fuzzy Syst. 2019, 21, 421–432. [Google Scholar] [CrossRef]
- Jana, J.; Roy, S.K. Linguistic Pythagorean hesitant fuzzy matrix game and its application in multi-criteria decision making. Appl. Intell. 2023, 53, 1–22. [Google Scholar] [CrossRef]
- Seikh, M.R.; Karmakar, S.; Xia, M. Solving matrix games with hesitant fuzzy pay-offs. Iran. J. Fuzzy Syst. 2020, 17, 25–40. [Google Scholar]
- Yang, Z.; Song, Y. Matrix game with payoffs represented by triangular dual hesitant fuzzy numbers. Int. J. Comput. Commun. Control 2020, 15, 3854. [Google Scholar] [CrossRef]
- Naqvi, D.R.; Sachdev, G.; Ahmad, I. Matrix games involving interval-valued hesitant fuzzy linguistic sets and its application to electric vehicles. J. Intell. Fuzzy Syst. 2023, 44, 5085–5105. [Google Scholar] [CrossRef]
- Zhang, Z. Interval-valued intuitionistic hesitant fuzzy aggregation operators and their application in group decision-making. J. Appl. Math. 2013, 2013, 670285. [Google Scholar] [CrossRef]
- Broumi, S.; Smarandache, F. New operations over interval-valued intuitionistic hesi-tant fuzzy set. Math. Stat. 2014, 2, 62–71. [Google Scholar] [CrossRef]
- Joshi, D.K.; Kumar, S. Interval-valued intuitionistic hesitant fuzzy choquet integral based TOPSIS method for multi-criteria group decision making. Eur. J. Oper. Res. 2016, 248, 183–191. [Google Scholar] [CrossRef]
- Yuan, J.; Li, C.; Xu, F.; Sun, B.; Li, W. A group decision making approach in inter-val-valued intuitionistic fuzzy environment with confidence levels. J. Intell. Fuzzy Syst. 2016, 31, 1909–1919. [Google Scholar] [CrossRef]
- Joshi, D.K.; Kumar, S. Entropy of interval-valued intuitionistic hesitant fuzzy set and its application to group decision making problems. Granul. Comput. 2018, 3, 367–381. [Google Scholar] [CrossRef]
- Narayanamoorthy, S.; Geetha, S.; Rakkiyappan, R.; Joo, Y.H. Interval-valued intuitionistic hesitant fuzzy entropy based VIKOR method for industrial robots selection. Expert Syst. Appl. 2019, 121, 28–37. [Google Scholar] [CrossRef]
- De, A.; Das, S.; Kar, S. Multiple attribute decision making based on probabilistic inter-val-valued intuitionistic hesitant fuzzy set and extended TOPSIS method. J. Intell. Fuzzy Syst. 2019, 37, 5229–5248. [Google Scholar] [CrossRef]
- Du, K.; Fan, R.; Wang, Y.; Wang, D.; Qian, R.; Zhu, B. A data-driven group emergency decision-making method based on interval-valued intuitionistic hesitant fuzzy sets and its application in COVID-19 pandemic. Appl. Soft Comput. 2023, 139, 110213. [Google Scholar] [CrossRef]
- Bhaumik, A.; Roy, S.K.; Weber, G.W. Hesitant interval-valued intuitionistic fuzzy-linguistic term set approach in prisoners’ dilemma game theory using TOPSIS: A case study on hu-man-trafficking. Cent. Eur. J. Oper. Res. 2020, 28, 797–816. [Google Scholar] [CrossRef]
- Zhai, Y.; Xu, Z.; Liao, H. Measures of probabilistic interval-valued intuitionistic hesitant fuzzy sets and the application in reducing excessive medical examination. IEEE Trans. Fuzzy Syst. 2018, 26, 1651–1670. [Google Scholar] [CrossRef]
- Zhang, L.; Tang, J.; Meng, F. An approach to decision making with interval-valued in-tuitionistic hesitant fuzzy information based on the 2-additive shapley function. Informatica 2018, 29, 157–185. [Google Scholar] [CrossRef]
- Zhang, G.; Zhou, S.; Xia, X.; Yuksel, S.; Bas, H.; Dincer, H. Strategic mapping of youth unemployment with interval valued intuitionistic hesitant fuzzy DEMATEL based on 2-tuple linguistic values. IEEE Access 2020, 8, 25706–25721. [Google Scholar] [CrossRef]
- Bhaumik, A.; Roy, S.K. Intuitionistic interval-valued hesitant fuzzy matrix games with a new aggregation operator for solving management problem. Granul. Comput. 2021, 6, 359–375. [Google Scholar] [CrossRef]
- Xu, Z.; Gou, X. An overview of interval-valued intuitionistic fuzzy information aggrega-tions and applications. Granul. Comput. 2017, 2, 13–39. [Google Scholar] [CrossRef]
- Chen, N.; Xu, Z.S. Properties of interval-valued hesitant fuzzy sets. J. Telligent Fuzzy Syst. 2014, 27, 143–158. [Google Scholar] [CrossRef]
- Xu, Z.S. Intuitionistic fuzzy aggregation operator. IEEE Trans. Fuzzy Syst. 2007, 15, 1179–1187. [Google Scholar]
- Ishibuchi, H.; Tanaka, H. Multiobjective programming in optimization of the interval objective function. Eur. J. Oper. Res. 1990, 48, 219–225. [Google Scholar] [CrossRef]
- National Crime Records Bureau. 2020. Available online: https://ncrb.gov.in/en/Crime-in-India-2020 (accessed on 27 June 2023).
- Xue, W.; Xu, Z.; Zeng, X.J. Solving matrix games based on Ambika method with hesitant fuzzy information and its application in the counter-terrorism issue. Appl. Intell. 2021, 51, 1227–1243. [Google Scholar] [CrossRef]
| Strategies | ||
|---|---|---|
| Strategies | ||
|---|---|---|
| Strategies | ||
|---|---|---|
(p = 1, 2; q = 1, 2) | Aggregated IIHFEs |
|---|---|
| 〈[0.6858,0.7861], [0.7079,0.8771], [0.7025,0.8263], [0.7234,0.9002], [0.6858,0.8038], [0.7079,0.8873]; [0.5145,0.6284], [0.5145,0.6684], [0.5145,0.6437], [0.5145,0.6846]〉 | |
| 〈[0.4608,0.7358], [0.6104,0.7358], [0.5941,0.7544], [0.5891,0.7544], [0.4608,0.7576], [0.6104,0.7576], [0.5941,0.7747], [0.5941,0.7747]; [0.5365,0.6089], [0.5123,0.7309], [0.4969,0.6089], [0.4745,0.7309]〉 | |
| 〈[0.3304,0.4565], [0.3304,0.4854], [0.3154,0.4565]; [0.4573,0.5936], [0.4573,0.6069], [0.4431,0.5936], [0.4431,0.6069]〉 | |
| 〈[0.6157,0.7160], [0.6157,0.7000], [0.6309,0.7160], [0.6356,0.7359], [0.6356,0.7211], [0.6500,0.7359]; [0.3342,0.4437], [0.3342,0.4573]〉 |
| 0 | (0,1) | 0.5063 | (1,0) | 0.5063 | 0.2492 | |
| 0.2 | (0,1) | 0.5250 | (1,0) | 0.5250 | 0.2492 | |
| 0.4 | (0,1) | 0.5337 | (0,1) | 0.5337 | 0.5601 | |
| 0.6 | (0,1) | 0.5883 | (0,1) | 0.5883 | 0.5601 | |
| 0.8 | (0.4518,0.5482) | 0.6301 | (0.0096,0.9904) | 0.6339 | 0.3481 | |
| 1 | (0.4898,0.5102) | 0.6510 | (0.1336,0.8664) | 0.6682 | 0.1494 |
| (0,1) | 0.5009 | (0.2949,0.7051) | 0.0881 | 0.1482 |
| Strategy | ||||
|---|---|---|---|---|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Karmakar, S.; Seikh, M.R. A Nonlinear Programming Approach to Solving Interval-Valued Intuitionistic Hesitant Noncooperative Fuzzy Matrix Games. Symmetry 2024, 16, 573. https://doi.org/10.3390/sym16050573
Karmakar S, Seikh MR. A Nonlinear Programming Approach to Solving Interval-Valued Intuitionistic Hesitant Noncooperative Fuzzy Matrix Games. Symmetry. 2024; 16(5):573. https://doi.org/10.3390/sym16050573
Chicago/Turabian StyleKarmakar, Shuvasree, and Mijanur Rahaman Seikh. 2024. "A Nonlinear Programming Approach to Solving Interval-Valued Intuitionistic Hesitant Noncooperative Fuzzy Matrix Games" Symmetry 16, no. 5: 573. https://doi.org/10.3390/sym16050573






