Cryptographic Considerations for Automation and SCADA Systems Using Trusted Platform Modules
Abstract
:1. Introduction
2. Related Work
2.1. Vulnerabilities of SCADA and Automation Systems
2.2. Security Solutions for Industry 4.0
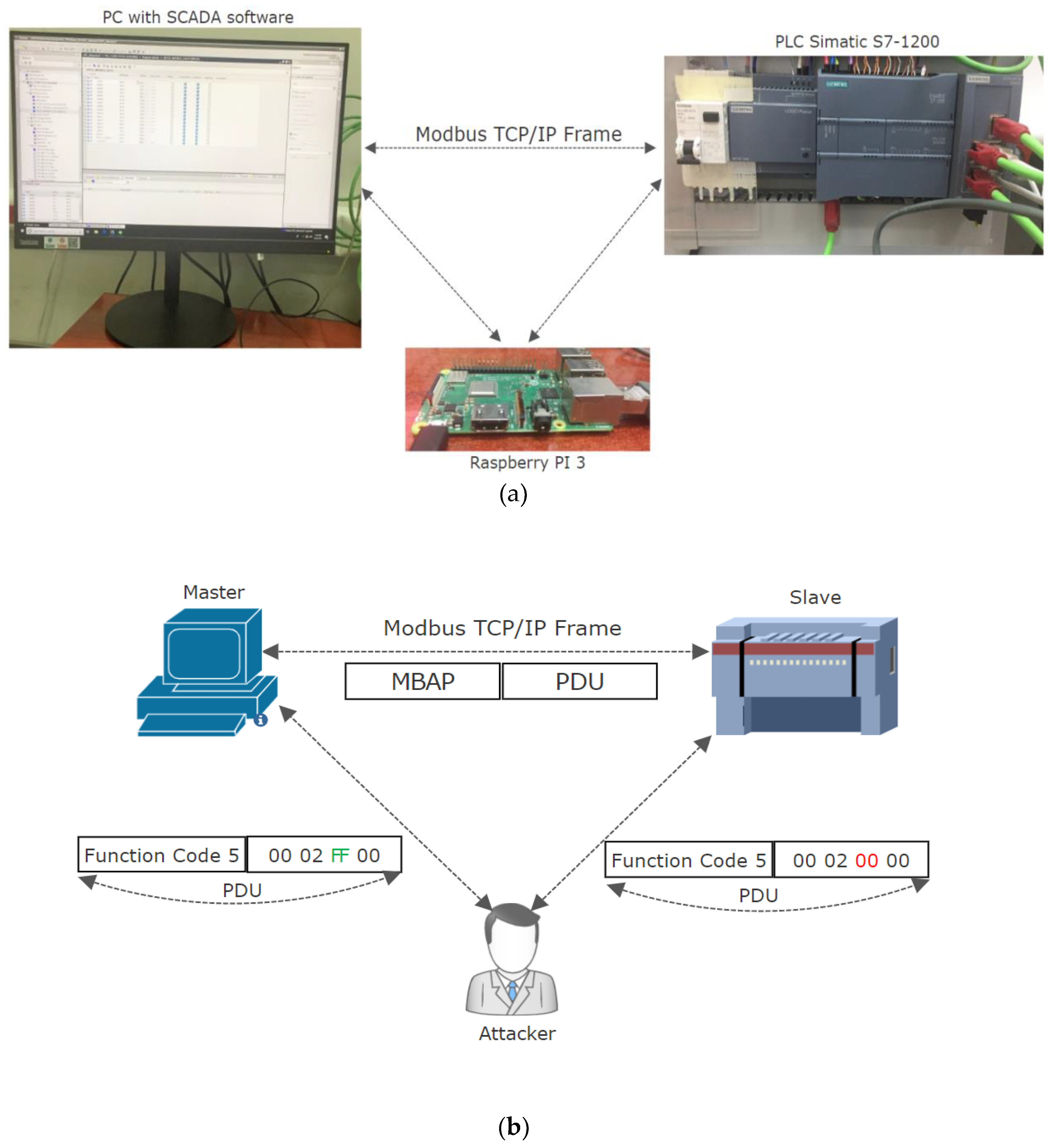
3. SCADA and Local Automation System Setup: Man-In-The-Middle Attack on Modbus TCP Protocol
- Kali Linux as operating system since it is designed for allowing the integration of a variety of tools used for penetration testing and hacking.
- Ettercap tool for performing the MITM attack since it allows Address Resolution Protocol (ARP) sniffing, ARP poisoning and it allows to design filters for manipulation of Modbus TCP protocol [45].
- T-shark for communication monitoring in order to analyze the Modbus TCP traffic [46].
4. Proposed Concept
4.1. Secure Key Storage with TPM
- TPM2_CreatePrimary which allows the creation of a key with an associated seed stored in the persistent memory.
- TPM2_Create is used to create an encrypted private and public key which, with the correct settings, can be associated in the hierarchy under the primary key. In these cases, the keys will not be saved in the persistent memory, since they will be loaded from the TMP cache or recreated.
- TPM2_Load and TPM2_LoadExternal will be used to load the keys.
- TPM2_NVWrite is used for writing and protecting the keys considered to be critical for the proposed concept.
4.2. Cryptographic Authentication Scheme
- Generate externally from the TPM a HMAC key k of 256 bit which will be used for all the devices which will have an associated TPM, where k is considered a symmetric key used for TPM keyed hashing.
- Generate through each TPM associated an RSA key pair (kPriv, kPub) for each of the devices intended to be used, where kPriv is the private key stored securely in the TPM persistent memory and the kPub is stored in the public key in the non-secure memory.
- Export kPub and load it into the non-secure memory of each device.
- Encrypt the HMAC key k with the RSA kPub through the TPM and store it encrypted in the non-secure memory of each device. Afterwards, when the system is running, an adversary will not be able to decrypt the HMAC key without the RSA kPriv stored securely in the TPM memory. Worth mentioning is that each device will have a different RSA key pair (kPriv, kPub) since it is created by each TPM connected to each device. Furthermore, the proposed concept for the authentication scheme is described as follows:
- At system startup both master and slave will perform:
- Decrypt the HMAC key using the TPM with the RSA kPriv.
- Load the decrypted HMAK key into the TPM and remove it from volatile memory of the device.
- At system runtime the communication between master and slave will be performed:
- ComputeHMAC (k, m) where the master device computes a keyed hash with k as secret key of the message m obtaining a keyed-hash hash h.
- ConcatenateHash (m, h) where the master device adds the hashed message h to the message m and send it to the slave device.
- CheckHash (m, h) where the slave device computes a keyed-hash with k as secret key of the message m and compares it with what it received from the master device.
- AcceptRequest where the slave device accepts the request received from the master device because the keyed hash values were the same.
- AbortCommunication where the slave device does not execute the command requested by the master device because the keyed hash values were different.
- (a)
- StartHMAC sequence using SHA-256 as algorithm for transmitted message m digest.
- (b)
- UpdateHMAC sequence with the Modbus TCP m in order to be hashed with the HMAC key k.
- (c)
- CompleteHMAC sequence by returning the hashed message h, which will have 256 bit length.
- ComputeHMAC (k, (nonce || m)) where the device computes a keyed hash with k as secret key of the message m concatenated with a randomly generated nonce or
- ComputeHMAC (k, (timestamp || m)) where the device computes a keyed hash with k as secret key of the message m concatenated with the message timestamp.
- Generate the key pair (kPrivECDSA, kPubECDSA) by the TPM using ECC-256 for each device.
- Store the kPrivECDSA in the persistent memory of the TPM and kPubECDSA in the context of the TPM.
- Load externally the kPubECDSA of the master device into the TPM of the slave device.
- Load externally the kPubECDSA of the slave device into the TPM of the master device.
- At system startup the following actions will be performed:
- Load the kPubECDSA of the slave device into the TPM of the master device from the master device non-secure persistent memory.
- Load the kPubECDSA of the master device into the TPM of the slave device from the slave device non-secure persistent memory.
- At system runtime the communication between master and slave will be performed:
- SignMessage (kPrivECDSA, m), where the master device computes a digital signature with kPrivECDSA as a secret key of the message m, obtaining a signature S of 512 bit length.
- ConcatenateSignature (m, S) where the master device adds the signature S to the message m and sends it to the slave device.
- VerifySignature (kPubECDSA, S) where the slave device computes a verification of the received signature using the master kPubECDSA and compares it with the expected response.
- AcceptRequest where the slave device accepts the request received from the master device because the signature is valid.
- AbortCommunication where the slave device ends the communication with the master device because the signature is not valid.
4.3. Experimental Setup
5. Experimental Results and Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Gerrikagoitia, J.K.; Unamuno, G.; Urkia, E.; Serna, A. Digital manufacturing platforms in the Industry 4.0 from private and public perspectives. Appl. Sci. 2019, 9, 2934. [Google Scholar] [CrossRef]
- Banyai, A.; Illes, B.; Glistau, E.; Machado, N.I.C.; Tamás, P.; Manzoor, F.; Bányai, T. Smart cyber-physical manufacturing: Extended and real-time optimization of logistics resources in matrix production. Appl. Sci. 2019, 9, 1287. [Google Scholar] [CrossRef]
- Muller, J.M.; Kiel, D.; Voigt, K.I. What drives the implementation of Industry 4.0? The role of opportunities and challenges in the context of sustainability. Sustainability 2018, 10, 247. [Google Scholar] [CrossRef]
- Müller, J.M. Antecedents to digital platform usage in Industry 4.0 by established manufacturers. Sustainability 2019, 11, 1121. [Google Scholar] [CrossRef]
- Becmeur, T.; Boudvin, X.; Brosset, D.; Heno, G.; Coste, B.; Kermarrec, Y.; Laso, P.M. Generating data sets as inputs of reference for cyber security issues and industrial control systems. In Proceedings of the 2017 11th International Conference on Research Challenges in Information Science (RCIS), Brighton, UK, 10–12 May 2017; pp. 453–454. [Google Scholar]
- Bezerra, A.; Silva, I.; Guedes, L.A.; Silva, D.; Leitão, G.; Saito, K. Extracting value from industrial alarms and events: A data-driven approach based on exploratory data analysis. Sensors 2019, 19, 2772. [Google Scholar] [CrossRef] [PubMed]
- Korodi, A.; Radu, M.A.; Crisan, R. Non-Invasive control solution inside higher-level OPC UA based wrapper for optimizing groups of wastewater systems. In Proceedings of the 2018 IEEE 23rd International Conference on Emerging Technologies and Factory Automation (ETFA), Turin, Italy, 4–7 September 2018; pp. 597–604. [Google Scholar]
- Jaloudi, S. Communication protocols of an industrial internet of things environment: A comparative study. Future Int. 2019, 11, 66. [Google Scholar] [CrossRef]
- Gutierrez-Guerrero, J.M.; Holgado-Terriza, J.A. Automatic configuration of OPC UA for Industrial Internet of Things environments. Electronics 2019, 8, 600. [Google Scholar] [CrossRef]
- Calderón Godoy, A.; González Pérez, I. Integration of sensor and actuator networks and the scada system to promote the migration of the legacy flexible manufacturing system towards the industry 4.0 concept. J. Sens. Actuator Netw. 2018, 7, 23. [Google Scholar] [CrossRef]
- Kiangala, K.S.; Wang, Z. An Industry 4.0 approach to develop auto parameter configuration of a bottling process in a small to medium scale industry using PLC and SCADA. Procedia Manuf. 2019, 35, 725–730. [Google Scholar] [CrossRef]
- Korodi, A.; Silea, I. Achieving interoperability using low-cost middleware OPC UA wrapping structure. case study in the water industry. In Proceedings of the 2017 IEEE 15th International Conference on Industrial Informatics (INDIN), Emden, Germany, 24–26 July 2017; pp. 1223–1228. [Google Scholar]
- Cavalieri, S.; Regalbuto, A. Integration of IEC 61850 SCL and OPC UA to improve interoperability in Smart Grid environment. Comput. Stand. Interfaces 2016, 47, 77–99. [Google Scholar] [CrossRef]
- Dai, W.; Vyatkin, V.; Christensen, J.H.; Dubinin, V.N. Bridging service-oriented architecture and IEC 61499 for flexibility and interoperability. IEEE Trans. Ind. Inf. 2015, 11, 771–781. [Google Scholar] [CrossRef]
- Salhaoui, M.; Guerrero-González, A.; Arioua, M.; Ortiz, F.J.; El Oualkadi, A.; Torregrosa, C.L. Smart industrial IoT monitoring and control system based on UAV and cloud computing applied to a concrete plant. Sensors 2019, 19, 3316. [Google Scholar] [CrossRef] [PubMed]
- Shahzad, A.; Kim, Y.G. Secure SCADA-IoT platform for industrial automation and control: A collaborative-communication designed model. Proceedings 2018, 2, 78. [Google Scholar] [CrossRef]
- De Araujo, P.R.C.; Filho, R.H.; Rodrigues, J.J.P.C.; Oliveira, J.P.C.M.; Braga, S.A. Infrastructure for integration of legacy electrical equipment into a smart-grid using wireless sensor networks. Sensors 2018, 18, 1312. [Google Scholar] [CrossRef] [PubMed]
- Irmak, E.; Erkek, I. An overview of cyber-attack vectors on SCADA systems. In Proceedings of the 2018 6th International Symposium on Digital Forensic and Security (ISDFS), Antalya, Turkey, 22–25 March 2018; pp. 1–5. [Google Scholar]
- Nardone, R.; Rodríguez, R.J.; Marrone, S. Formal security assessment of Modbus protocol. In Proceedings of the 2016 11th International Conference for Internet Technology and Secured Transactions (ICITST), Barcelona, Spain, 5–7 December 2016; pp. 142–147. [Google Scholar]
- Serhane, A.; Raad, M.; Raad, R.; Susilo, W. PLC code-level vulnerabilities. In Proceedings of the 2018 International Conference on Computer and Applications (ICCA), Beirut, Lebanon, 25–26 August 2018; pp. 348–352. [Google Scholar]
- Nourian, A.; Madnick, S. A systems theoretic approach to the security threats in cyber physical systems applied to stuxnet. IEEE Trans. Dependable Secur. Comput. 2015, 15, 2–13. [Google Scholar] [CrossRef]
- Karnouskos, S. Stuxnet worm impact on industrial cyber-physical system security. In Proceedings of the IECON 2011-37th Annual Conference of the IEEE Industrial Electronics Society, Melbourne, VIC, Australia, 7–10 November 2011; pp. 4490–4494. [Google Scholar]
- Kaspersky Lab ICS CERT. Threat Landscape for Industrial Automation Systems in H1 2018. 2018. Available online: https://securelist.com/threat-landscape-for-industrial-automation-systems-in-h1-2018/87913/ (accessed on 14 May 2019).
- Bolshev, A.; Yushkevich, I. SCADA and Mobile Security in The Internet of Things Era. 2018. Available online: https://ioactive.com/scada-and-mobile-security-in-iot-era/ (accessed on 14 May 2019).
- Babu, B.; Ijyas, T.; Muneer, P.; Varghese, J. Security issues in SCADA based industrial control systems. In Proceedings of the 2017 2nd International Conference on Anti-Cyber Crimes (ICACC), Abha, Saudi Arabia, 26–27 March 2017; pp. 47–51. [Google Scholar]
- Rizzetti, T.A.; Wessel, P.; Rodrigues, A.S.; da Silva, B.M.; Milbradt, R.; Canha, L.N. Cyber security and communications network on SCADA systems in the context of smart grids. In Proceedings of the 2015 50th International Universities Power Engineering Conference (UPEC), Stoke on Trent, UK, 1–4 September 2015; pp. 1–6. [Google Scholar]
- Xu, Y.; Yang, Y.; Li, T.; Ju, J.; Wang, Q. Review on cyber vulnerabilities of communication protocols in industrial control systems. In Proceedings of the 2017 IEEE Conference on Energy Internet and Energy System Integration (EI2), Beijing, China, 26–28 November 2017; pp. 1–6. [Google Scholar]
- Rosa, L.; Freitas, M.; Mazo, S.; Monteiro, E.; Cruz, T.; Simões, P. A comprehensive security analysis of a scada protocol: From OSINT to Mitigation. IEEE Access 2019, 7, 42156–42168. [Google Scholar] [CrossRef]
- Liao, G.Y.; Chen, Y.J.; Lu, W.C.; Cheng, T.C. Toward authenticating the master in the modbus protocol. IEEE Trans. Power Deliv. 2008, 23, 2628–2629. [Google Scholar] [CrossRef]
- Phan, R.C.W. Authenticated modbus protocol for critical infrastructure protection. IEEE Trans. Power Deliv. 2012, 27, 1687–1689. [Google Scholar] [CrossRef]
- Hayes, G.; El-Khatib, K. Securing modbus transactions using hash-based message authentication codes and stream transmission control protocol. In Proceedings of the 2013 Third International Conference on Communications and Information Technology (ICCIT), Beirut, Lebanon, 19–21 June 2013; pp. 179–184. [Google Scholar]
- Li, S.C.; Huang, Y.; Tai, B.C.; Lin, C.T. Using data mining methods to detect simulated intrusions on a modbus network. In Proceedings of the 2017 IEEE 7th International Symposium on Cloud and Service Computing (SC2), Kanazawa, Japan, 22–25 November 2017; pp. 143–148. [Google Scholar]
- Taylor, J.M.; Sharif, H.R. Enhancing integrity of modbus TCP through covert channels. In Proceedings of the 2017 11th International Conference on Signal Processing and Communication Systems (ICSPCS), Kanazawa, Japan, 22–25 November 2017; pp. 1–6. [Google Scholar]
- Modbus. MODBUS/TCP Security. Available online: http://modbus.org/docs/MB-TCP-Security-v21_2018-07-24.pdf (accessed on 10 April 2019).
- Ádámkó, É.; Jakabóczki, G.; Szemes, P.T. Proposal of a Secure Modbus RTU communication with Adi Shamir’s secret sharing method. Int. J. Electron. Telecommun. 2018, 64, 107–114. [Google Scholar] [CrossRef]
- Volkova, A.; Niedermeier, M.; Basmadjian, R.; de Meer, H. Security challenges in control network protocols: A survey. IEEE Commun. Surv. Tutor. 2018, 21, 619–639. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R. Towards an optimized blockchain for IoT. In Proceedings of the Second International Conference on Internet-of-Things Design and Implementation, Pittsburgh, PA, USA, 18–21 April 2017; pp. 173–178. [Google Scholar]
- Liang, G.; Weller, S.R.; Luo, F.; Zhao, J.; Dong, Z.Y. Distributed blockchain-based data protection framework for modern power systems against cyber attacks. IEEE Trans. Smart Grid 2018, 10, 3162–3173. [Google Scholar] [CrossRef]
- Bauer, J.; Staudemeyer, R.; Fragkiadakis, A.; Pöhls, H. ECDSA on things: IoT integrity protection in practise. In International Conference on Information and Communications Security; Springer: Cham, Switzerland, 2016. [Google Scholar]
- Fischer, T.; Lesjak, C.; Hoeller, A.; Steger, C. Security for building automation with hardware-Based node authentication. In Proceedings of the 2017 22nd IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Limassol, Cyprus, 12–15 September 2017; pp. 1–6. [Google Scholar]
- Esfahani, A.; Mantas, G.; Matischek, R.; Saghezchi, F.B.; Rodriguez, J.; Bicaku, A.; Maksuti, S.; Tauber, M.G.; Schmittner, C.; Bastos, J. A Lightweight Authentication Mechanism for M2M Communications in Industrial IoT Environment. IEEE Int. Things J. 2019, 6, 288–296. [Google Scholar] [CrossRef]
- Lu, Y.; Feng, T. Research on trusted DNP3-BAE protocol based on hash chain. EURASIP J. Wirel. Commun. Netw. 2018, 2018, 108. [Google Scholar] [CrossRef] [Green Version]
- Fournaris, A.P.; Lampropoulos, K.; Koufopavlou, O. Trusted hardware sensors for anomaly detection in critical infrastructure systems. In Proceedings of the 2018 7th International Conference on Modern Circuits and Systems Technologies (MOCAST), Thessaloniki, Greece, 7–9 May 2018; pp. 1–4. [Google Scholar]
- Rosa, L.; Cruz, T.; Simões, P.; Monteiro, E.; Lev, L. Attacking SCADA systems: A practical perspective. In 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM); IEEE: Lisbon, Portugal, 2017; pp. 741–746. [Google Scholar]
- Ornaghi, A.; Valleri, M. ETTERCAP PROJECT. Available online: https://www.ettercap-project.org/index.html (accessed on 17 March 2019).
- Wireshark. tshark Terminal-based Wireshark. Available online: https://www.wireshark.org/docs/wsug_html_chunked/AppToolstshark.html (accessed on 17 May 2019).
- Group, T.C. Trusted Platform Module Library Specification, Family “2.0”, Level 00, Revision 01.38. 2016. Available online: https://trustedcomputinggroup.org/resource/tpm-library-specification (accessed on 17 July 2019).
- Raimbault, S. Libmodbus. Available online: https://github.com/stephane/libmodbus (accessed on 1 July 2019).
- epsilonnrt. Mbpoll. Available online: https://github.com/epsilonrt/mbpoll (accessed on 15 July 2019).
- wolfSSL Inc. wolfTPM Portable TPM 2.0 Library. 2019. Available online: https://www.wolfssl.com/products/wolftpm/ (accessed on 15 July 2019).
- Community, D. wolfTPM. Available online: https://github.com/wolfSSL/wolfTPM (accessed on 15 July 2019).
- Community, D. TCG TPM2 Software Stack. Available online: https://github.com/tpm2-software/tpm2-tss (accessed on 15 June 2019).
- NIST Special Publication 800-57 Recommendation for Key Management—Part 1: General. 2012. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-57pt1r4.pdf (accessed on 5 May 2019).
- OPTIGATM TPM SLM 9670 Industrial Grade TPM. Available online: https://www.infineon.com/cms/en/product/security-smart-card-solutions/optiga-embedded-security-solutions/optiga-tpm/slm-9670/ (accessed on 15 July 2019).
- Vistion. Available online: http://vistion.si/en/products/plc/ (accessed on 11 June 2019).
- Standmount Embedded Automation Controller, UNO-2000 Series. Available online: https://www.advantech.com/products/standmount-embedded-automation-controller-uno-2000-series/sub_1-2mlj9a (accessed on 10 May 2019).





| TPM Function | Duration (s) |
|---|---|
| TPM2_GetKeyTemplate_RSA_EK | 0.000007 |
| TPM2_CreatePrimaryKey | 0.040547 |
| TPM Function | Duration (s) | Applicable to Proposed Method |
|---|---|---|
| TPM2_CreateAndLoadRSAKey | 0.096907 | HMAC-SHA256 |
| TPM2_LoadExternal (RsaPublicKey) | 0.002226 | HMAC-SHA256 |
| TPM2_RsaEncrypt | 0.008255 | HMAC-SHA256 |
| TPM2_CreateAndLoadEccKey | 0.122234 | ECDSA ECC-256 |
| TPM2_LoadExternal (EccPublicKey) | 0.005993 | ECDSA ECC-256 |
| TPM Function | Duration (s) |
|---|---|
| TPM2_RsaDecrypt | 0.159672 |
| TPM2_LoadHashedKey | 0.068886 |
| TPM2_HmacStart | 0.006950 |
| TPM2_HmacUpdate | 0.002146 |
| TPM2_HmacFinish | 0.008667 |
| TPM Function | Duration (s) |
|---|---|
| TPM2_LoadEccPublicKey | 0.005892 |
| TPM2_Sign | 0.068411 |
| TPM2_VerifySignature | 0.103083 |
| Proposed Method | Key Size (bit) | Key Strength (bit) | Output Size (bit) |
|---|---|---|---|
| HMAC-SHA256 | 256 | 256 | 256 |
| ECDSA ECC-256 | 256 | 128 | 512 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tidrea, A.; Korodi, A.; Silea, I. Cryptographic Considerations for Automation and SCADA Systems Using Trusted Platform Modules. Sensors 2019, 19, 4191. https://doi.org/10.3390/s19194191
Tidrea A, Korodi A, Silea I. Cryptographic Considerations for Automation and SCADA Systems Using Trusted Platform Modules. Sensors. 2019; 19(19):4191. https://doi.org/10.3390/s19194191
Chicago/Turabian StyleTidrea, Alexandra, Adrian Korodi, and Ioan Silea. 2019. "Cryptographic Considerations for Automation and SCADA Systems Using Trusted Platform Modules" Sensors 19, no. 19: 4191. https://doi.org/10.3390/s19194191





