Managing Cloud Intelligent Systems over Digital Ecosystems: Revealing Emerging App Technology in the Time of the COVID19 Pandemic
Abstract
:1. Introduction
2. Literature Review
3. Results and Discussion
3.1. Cloud Connectivity Scheduling
3.2. Implementing Cloud Apps Intelligent Systems
3.2.1. Importance of the Intelligent Systems for Enterprises
- Improve Product Time to Market: The systems help businesses roll out their products to customers much faster. The system will eventually gather data and analyze the best development cycle for the business and reach out to the potential customers in the market. The system will automatically advertise the product in the market, hence making the company more recognized and profitable. This will create more profits for the business as the smart system picks/predicts the next best thing for the business.
- Improve Business Revenue: With this system, businesses can improve their revenue based on previous data and analysis, serve current customers and find new potential customers.
- Improve Manufacturing Processes: The system may enhance the existing processes making them more efficient and productive. It also can produce new smarter processes which can control, monitor and predict what the best process is and produce products and at the same time it will improve the time and increase productivity.
- Build Company Loyalty: The system collect data and show results for what should be improved from the customer experience viewpoint. This allows the businesses to improve the products or services that customers need.
- Improve the Supply Chain: The system allows the businesses to track and assess the quality and volume of the supply chain and also monitor everything regarding the supply chain and the quality of products.
3.2.2. Cloud Intelligent Trend
3.2.3. Business Processes: Pandemic COVID19 Issues
- Economic recession affecting businesses especially micro, small, medium enterprises (MSMEs).
- Unemployment will be a major contributor to economic recession as lots of people may lose their jobs due to the current situation and government orders.
- Governments may have to implement economic injection initiatives to boost and stabilize the economy. This can affect the GDP of the nation as when economic activities are not doing great and government must use initiatives to ensure the GDP of the nation will not be badly affected. Examples of economic injection are to give incentives to MSMEs so that they still can do business, give allowances to people which were badly affected so their purchasing power is still viable, network infrastructure must be upgraded due to home and work learning initiatives implemented by the government and private sectors, and any other method that will use by the government to stimulate their economy.
- Lots of business must shut down – during lockdown or due to economic recession. This is what are currently happening throughout the globe. Because of lockdowns or impacted by the economy, a numbers of businesses, especially MSMEs, must shut down as business was not going well and their sources of revenue were affected.
- All economic activities were suspended during lockdown to ensure the outbreak can be minimized and to encourage people to stay at home.
- Most projects will be put on hold. Major projects such as government projects either in terms of infrastructure or others, might have to be suspended for a period of time. The affects the government schedule, return on investment and GDP.
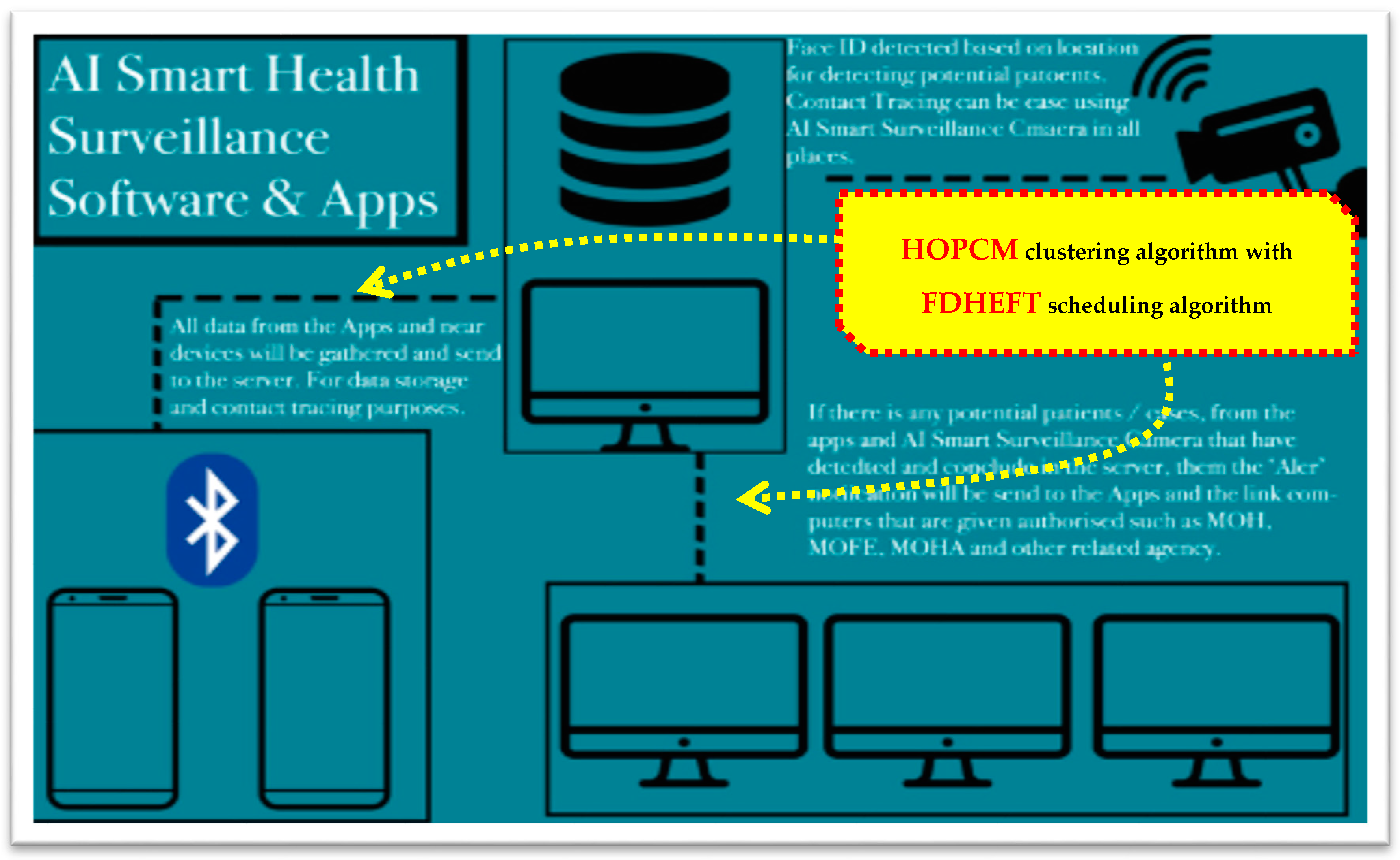
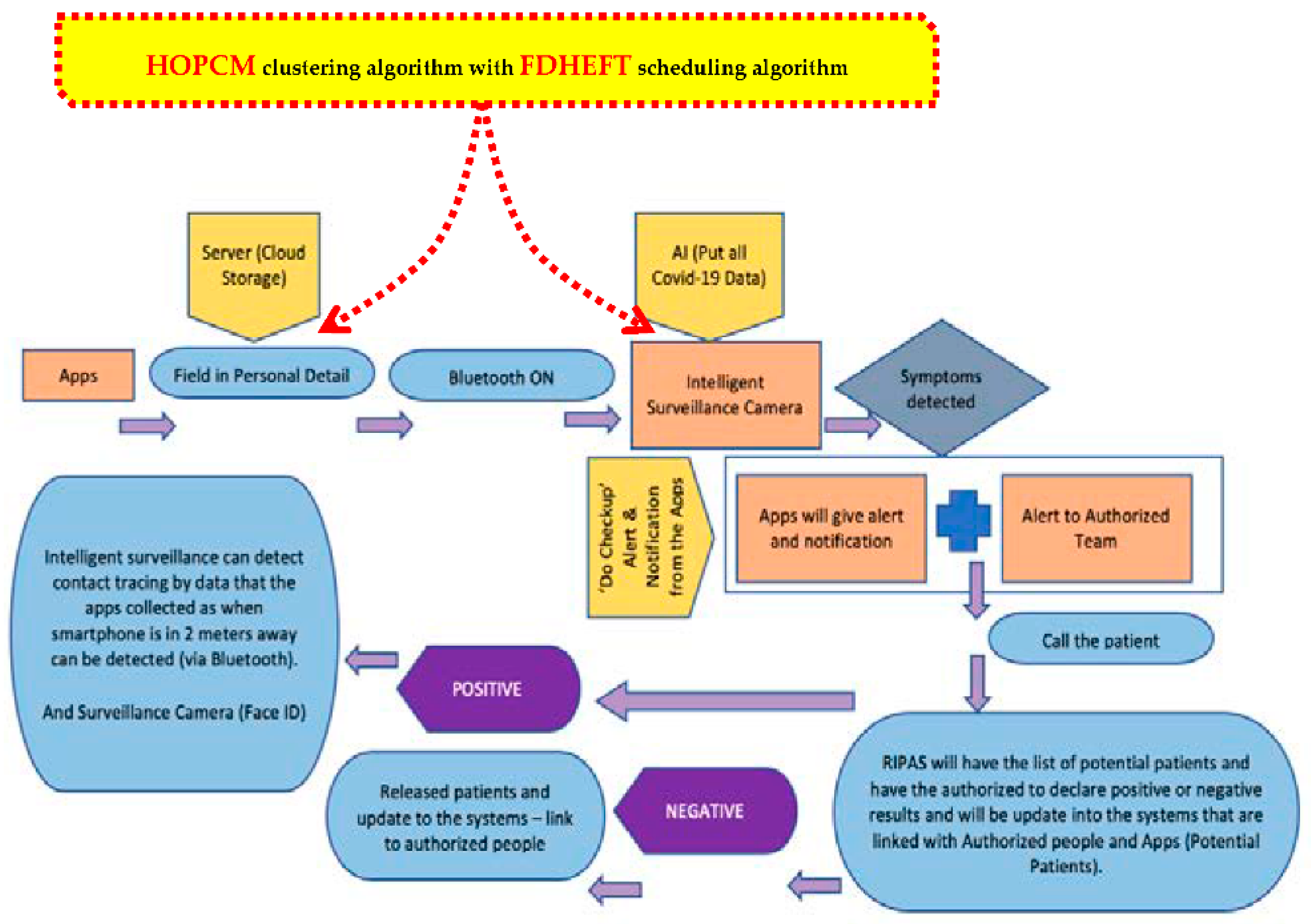
3.2.4. Smart Health Surveillance Software and Apps
- Prime Minister Office—PMO
- Ministry of Health—MOH
- Hospital and National Quarantine Center—HNQC
- Ministry of Finance and Economy—MOFE
- Ministry of Home Affairs—MOHE
- National Disaster Management Centre—NDMC
- The ability of agencies to check the movement of quarantined patients to ensure all patients are obeying the regulations that have been set by the government as there were issues before with cases where quarantined patients tried to escape from quarantine centers.
- The ability to transfer data from app to app so that it is able to gather data when contact tracing. When a smartphone users meets another smartphone user within a specific range, data will be interchanged.
- An efficient way for agencies to do “contact tracing” when a positive case is found, as the current method to contact tracing consumes lots of time, energy and workforce.
- Convenience of use for all users as all the data has been stored on a cloud server and can be analyzed, so there will be no need to use the internal storage capacity of phones.
- The ability of the AI function to analyze the symptoms and other factors in order to detect potential patients. This can be helpful for governments to detect potential COVID19 patients.
- The camera has the function of Face ID detection making it easier for governments to recognize people when doing search activities. Furthermore, the smart surveillance camera has a thermal mode to detect body temperatures.
- When AI Smart Health Surveillance systems are installed throughout the nation, it will make it easier for governments to detect patients and perform contact tracing.
- Agencies can lift a few lockdown restrictions so the economy will still function in the country. This can be done when the pandemic is effectively contained.
- Business can use this software and application as a precaution for their businesses and their workers. It can be help agencies when there is a need for contact tracing if potential COVID19 patients are detected on their premises.
- To ensure the national health systems graphs will be stable, as having this will make sure COVID19 is contained.
- Ability to help MSMEs during this pandemic. When the pandemic is contained, business activity can be resumed like normal.
- Ability to understand the lifestyle patterns, how the outbreak will affect communities and how this pandemic can spread and how it can be encountered.
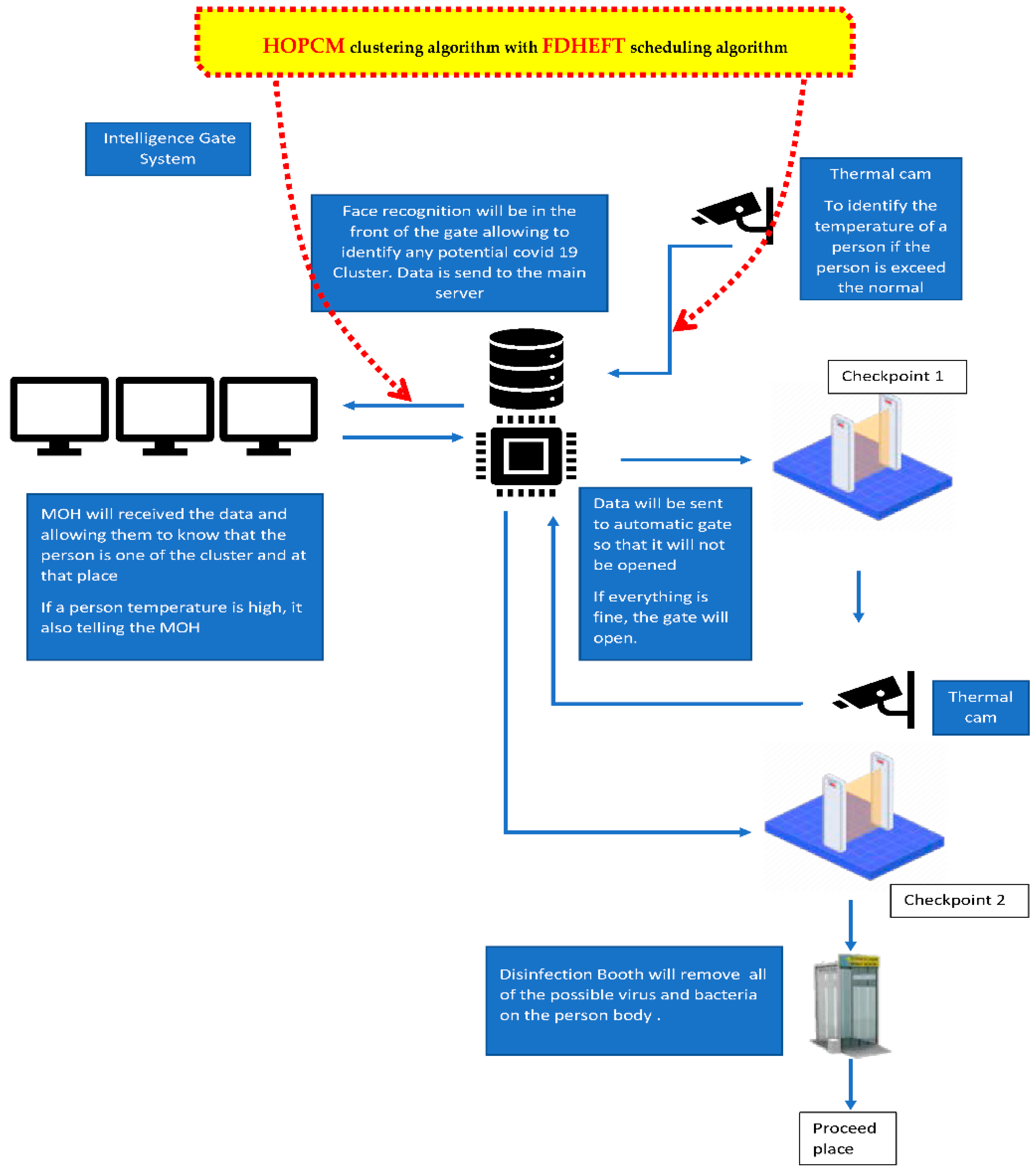
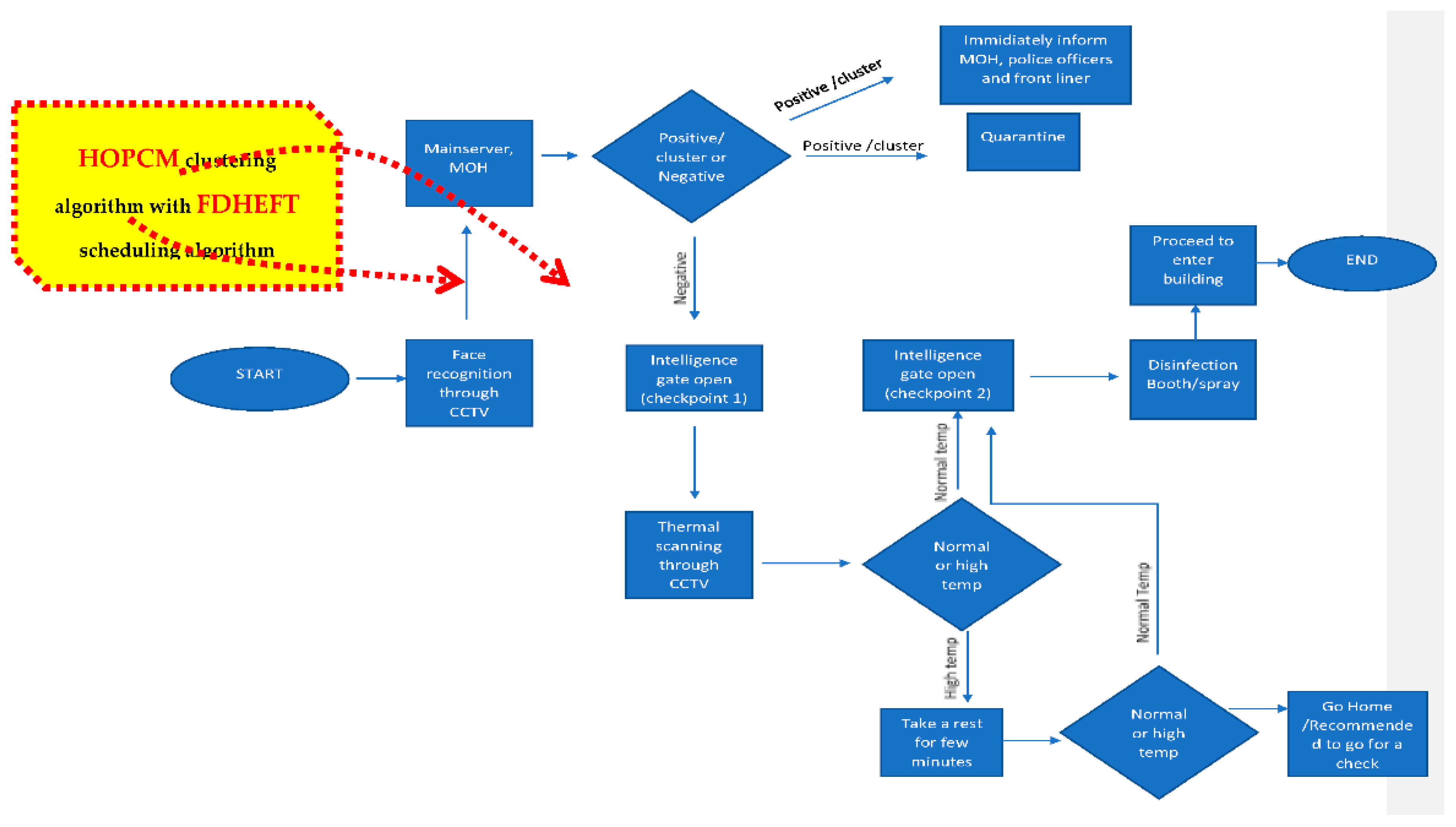
3.2.5. Intelligence Gate System
- Government Accessibility: This system is accessible to specific ministries and organizations such as the Ministry of Health, Prime Minister’s Office, Ministry of Finance and Economy, Ministry of Home Affairs and lastly the Disaster Management Center. This is due to the fact the data provided by the CCTV and system is confidential and needs privacy protection. The data also can be collected from the CCTV and the information delivered to a cloud server, thus, all the above ministries and organizations can access and see what new data have been collected.
- No Human Intervention is Needed: Everything is controlled by the artificial intelligence (AI) system through the internet. Everything from facial recognition, analyzing the data, thermal scanning, gate opening as well as the disinfection booth operations are handled by the AI. There is no human interference unless needed, such as showing potentially infected people detetcted where the quarantine zone place is, maintenance etc. Other than that, it is fully automatic.
- Ability to Know Location: This system will help determine the location of a person’s whereabouts. For example, if the person is infected with COVID19, he won’t be able to go into the building or leave the area and must stay in the quarantine zone provided. He will be monitored in the quarantine area. Thus, the location where a patient was detected is the place or the location where the necessary frontline activity must occur.
- Trigger Notification to the Nearest Frontline: This system will also help to directly inform the MOH and relevant organizations if the system detects an infected person with COVID19 or a potential cluster/infected person or the government is looking for that person. A frontline person such as a medic, nurse and doctor and also police officers will be informed immediately by the system.
- Prevent Spread in Buildings: With this system, only a person who is in very good health and does not have any problems with the current COVID19 as established by the agencies, have any relations with clusters and so on will be able to proceed and enter the building. Thus, this will help prevent the people who are inside the building from getting the COVID19 virus. On the other hand, if symptoms are detected outside the building, people who are already inside the building do not have to worry anymore because they are safe, but those who are outside will need to wait for the frontline worker to come and tighten the checking before entering the building, as they are queuing up to enter the building, they probably have been contacted without distancing from each other.
4. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Ercan, T. Effective use of cloud computing in educational institutions. Procedia Soc. Behav. Sci. 2010, 2, 938–942. [Google Scholar] [CrossRef] [Green Version]
- Rosenthal, A.; Mork, P.; Li, M.H.; Stanford, J.; Koester, D.; Reynolds, P. Cloud computing: A new business paradigm for biomedical information sharing. J. Biomed. Inf. 2010, 43, 342–353. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Clarke, J.; McIlhagger, A.; Archer, E.; Dooher, T.; Flanagan, T.; Schubel, P. A Feature-Based Cost Estimation Model for Wind Turbine Blade Spar Caps. Appl. Syst. Innov. 2020, 3, 17. [Google Scholar] [CrossRef] [Green Version]
- Mahmood, A.; Khan, S.A.; Bahlool, R.A. Hard real-time task scheduling in cloud computing using an adaptive genetic algorithm. Computers 2017, 6, 15. [Google Scholar] [CrossRef] [Green Version]
- Anwar, N.; Deng, H. Elastic scheduling of scientific workflows under deadline constraints in cloud computing environments. Future Internet 2018, 10, 5. [Google Scholar] [CrossRef] [Green Version]
- Leu, F.Y.; Ko, C.Y.; Lin, Y.C.; Susanto, H.; Yu, H.C. Fall Detection and Motion Classification by Using Decision Tree on Mobile Phone. In Smart Sensors Networks; Elsevier: Amsterdam, The Netherlands, 2017; pp. 205–237. [Google Scholar]
- Liu, J.C.; Leu, F.Y.; Lin, G.L.; Susanto, H. An MFCC-based text-independent speaker identification system for access control. Concurr. Comput. Pract. Exp. 2018, 30, e4255. [Google Scholar] [CrossRef]
- Wangsom, P.; Lavangnananda, K.; Bouvry, P. Multi-objective scheduling for scientific workflows on cloud with peer-to-peer clustering. In Proceedings of the 2019 11th International Conference on Knowledge and Smart Technology (KST), Phuket, Thailand, 23–26 January 2019; pp. 175–180. [Google Scholar]
- Sultan, N. Knowledge management in the age of cloud computing and Web 2.0: Experiencing the power of disruptive innovations. Int. J. Inf. Manag. 2013, 33, 160–165. [Google Scholar]
- Han, G.; Que, W.; Jia, G.; Shu, L. An efficient virtual machine consolidation scheme for multimedia cloud computing. Sensors 2016, 16, 246. [Google Scholar] [CrossRef] [Green Version]
- Duan, K.; Fong, S.; Siu, S.W.; Song, W.; Guan, S.S.U. Adaptive incremental genetic algorithm for task scheduling in cloud environments. Symmetry 2018, 10, 168. [Google Scholar] [CrossRef] [Green Version]
- Chew, S. Continuous-Service M/M/1 Queuing Systems. Appl. Syst. Innov. 2019, 2, 16. [Google Scholar] [CrossRef] [Green Version]
- Durillo, J.J.; Prodan, R. Multi-objective workflow scheduling in Amazon EC2. Clust. Comput. 2014, 17, 169–189. [Google Scholar] [CrossRef]
- Yu, J.; Kirley, M.; Buyya, R. Multi-objective planning for workflow execution on grids. In Proceedings of the 2007 8th IEEE/ACM International Conference on Grid Computing, Austin, TX, USA, 19–21 September 2007; pp. 10–17. [Google Scholar]
- Zhou, X.; Zhang, G.; Sun, J.; Zhou, J.; Wei, T.; Hu, S. Minimizing cost and makespan for workflow scheduling in cloud using fuzzy dominance sort based HEFT. Future Gener. Comput. Syst. 2019, 93, 278–289. [Google Scholar] [CrossRef]
- Gupta, A.; Bhadauria, H.S.; Singh, A.; Patni, J.C. A theoretical comparison of job scheduling algorithms in cloud computing environment. In Proceedings of the 2015 1st International Conference on Next Generation Computing Technologies (NGCT), Dehradun, India, 4–5 September 2015; pp. 16–20. [Google Scholar]
- Garg, R.; Singh, A.K. Multi-objective workflow grid scheduling based on discrete particle swarm optimization. In International Conference on Swarm, Evolutionary, and Memetic Computing; Springer: Berlin/Heidelberg, Germany, 2011; pp. 183–190. [Google Scholar]
- Garg, R.; Singh, A.K. Multi-objective workflow grid scheduling using ε-fuzzy dominance sort based discrete particle swarm optimization, J. Supercomput. 2014, 68, 709–732. [Google Scholar] [CrossRef]
- Valente, M.; Silva, H.; Caldeira, J.M.; Soares, V.N.; Gaspar, P.D. Detection of waste containers using computer vision. Appl. Syst. Innov. 2019, 2, 11. [Google Scholar] [CrossRef] [Green Version]
- Khan, T. An Intelligent Microwave Oven with Thermal Imaging and Temperature Recommendation Using Deep Learning. Appl. Syst. Innov. 2020, 3, 13. [Google Scholar] [CrossRef] [Green Version]
- Palmer, S. The Pros and Cons of Artificial Intelligence I DevTeam.Space. DevTeam.Space. 2020. Available online: https://www.devteam.space/blog/the-pros-and-cons-of-artificial-intelligence/ (accessed on 15 March 2020).
- Mikail, A.; Pranggono, B. Securing Infrastructure-as-a-Service Public Clouds Using Security Onion. Appl. Syst. Innov. 2019, 2, 6. [Google Scholar] [CrossRef] [Green Version]
- De Jager, C.; Nel, M. Business Process Automation: A Workflow Incorporating Optical Character Recognition and Approximate String and Pattern Matching for Solving Practical Industry Problems. Appl. Syst. Innov. 2019, 2, 33. [Google Scholar] [CrossRef] [Green Version]
- Anwar, N.; Deng, H. A hybrid metaheuristic for multi-objective scientific workflow scheduling in a cloud environment. Appl. Sci. 2018, 8, 538. [Google Scholar] [CrossRef] [Green Version]
- Domb, M.; Leshem, G. Secured Key Distribution by Concatenating Optical Communications and Inter-Device Hand-Held Video Transmission. Appl. Syst. Innov. 2020, 3, 11. [Google Scholar] [CrossRef] [Green Version]
- Khalil, I.M.; Khreishah, A.; Azeem, M. Cloud computing security: A survey. Computers 2014, 3, 1–35. [Google Scholar] [CrossRef] [Green Version]
- Susanto, H.; Almunawar, M.N. Information Security Management Systems: A Novel Framework and Software as a Tool for Compliance with Information Security Standard; CRC Press: Boca Raton, FL, USA, 2018. [Google Scholar]
- Susanto, H.; Almunawar, M.N. Security and Privacy Issues in Cloud-Based E-Government. In Cloud Computing Technologies for Connected Government; IGI Global: Hershey, PA, USA, 2016; pp. 292–321. [Google Scholar]
- Susanto, H.; Almunawar, M.N. Managing Compliance with an Information Security Management Standard. In Encyclopedia of Information Science and Technology, 3rd ed.; IGI Global: Hershey, PA, USA, 2015; pp. 1452–1463. [Google Scholar]
- Zhang, Q.; Yang, L.T.; Chen, Z.; Li, P. High-order possibilistic c-means algorithms based on tensor decompositions for big data in IoT. Inf. Fusion 2018, 39, 72–80. [Google Scholar] [CrossRef]


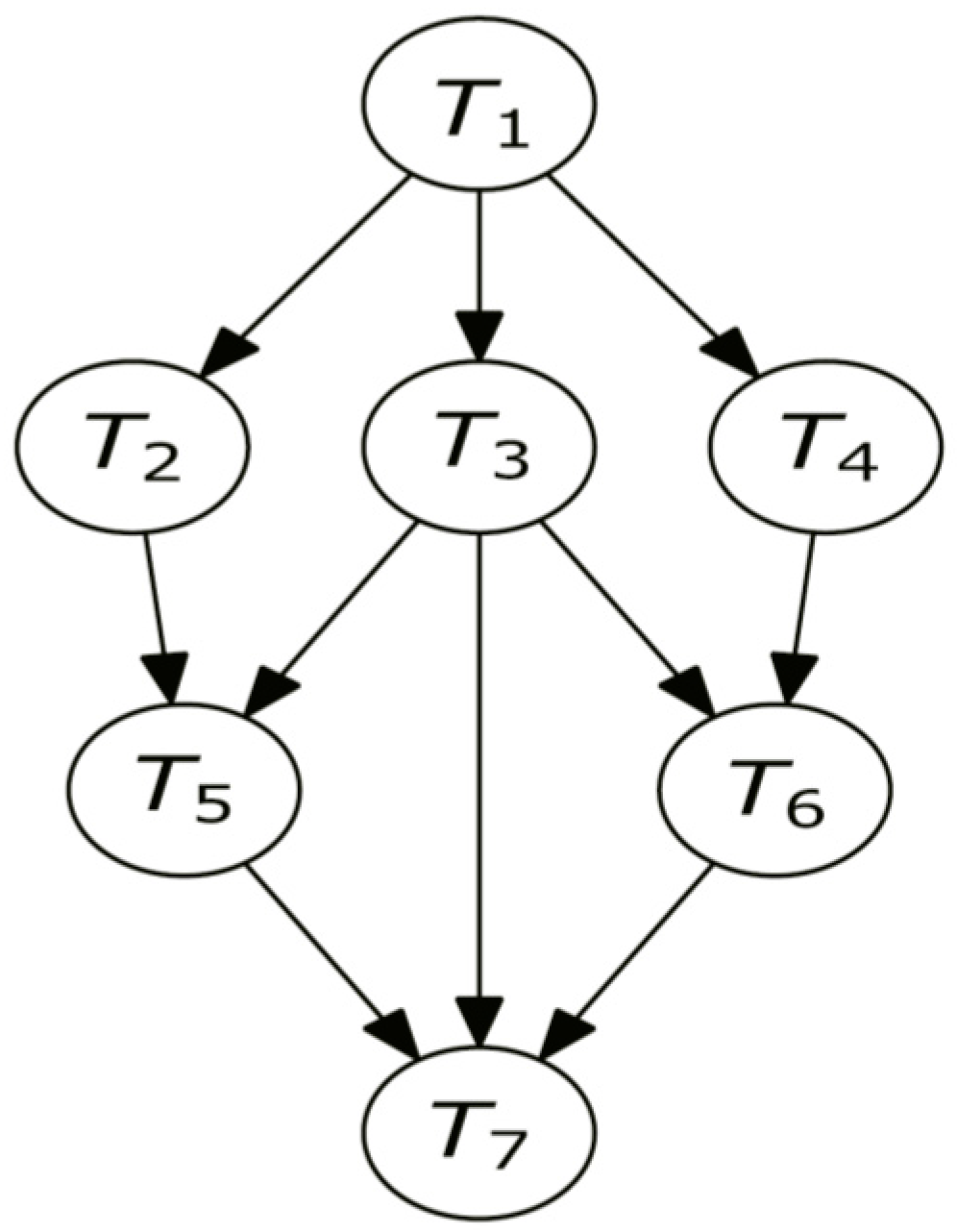
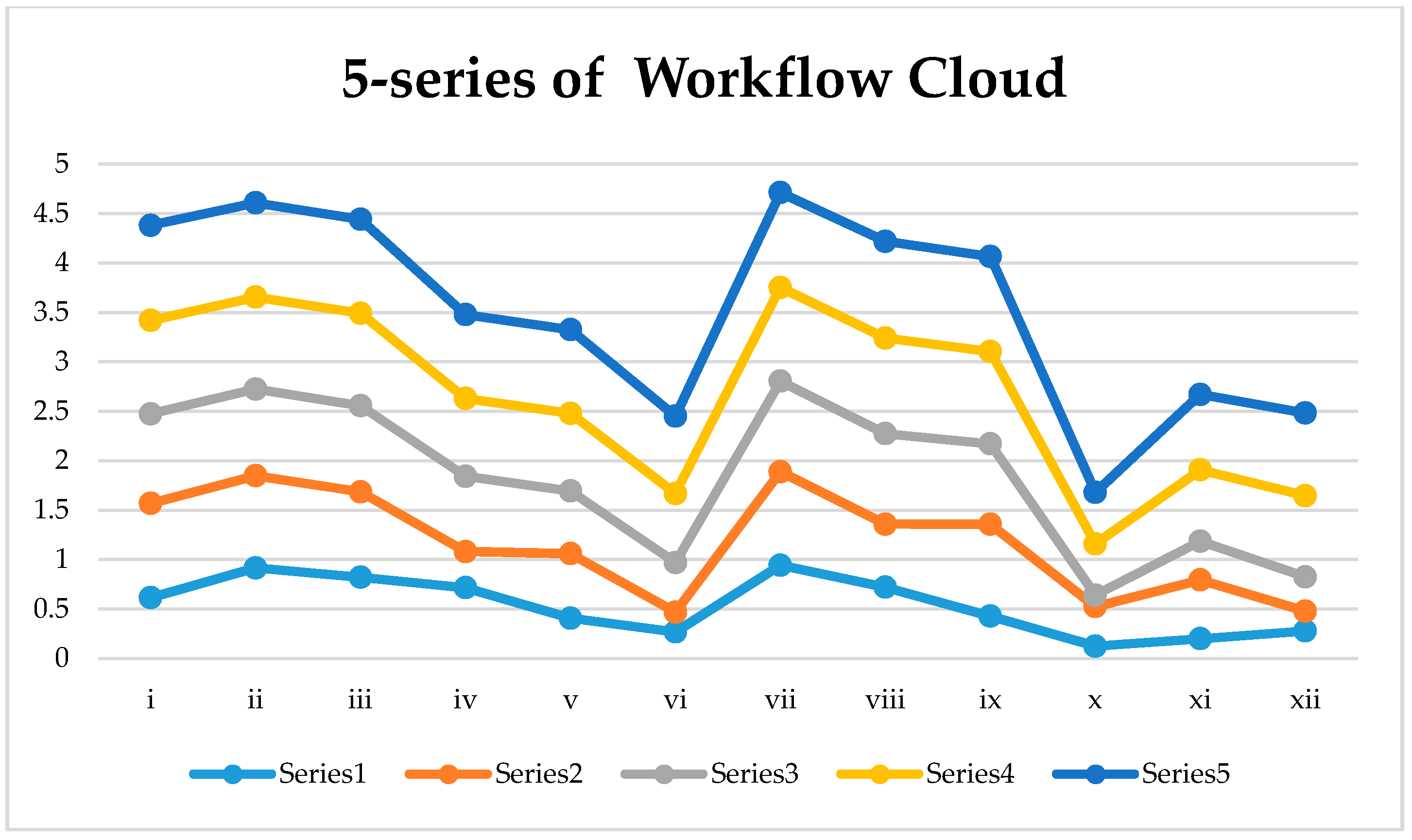

| Cloud Workflow | Algorithms | ||||
|---|---|---|---|---|---|
| Series (1) | Series (2) | Series (3) | Series (4) | Series (5) | |
| i | 0.615 | 0.954 | 0.905 | 0.945 | 0.961 |
| ii | 0.917 | 0.932 | 0.876 | 0.929 | 0.954 |
| iii | 0.822 | 0.863 | 0.871 | 0.935 | 0.949 |
| iv | 0.716 | 0.365 | 0.762 | 0.787 | 0.847 |
| v | 0.408 | 0.652 | 0.634 | 0.785 | 0.846 |
| vi | 0.269 | 0.2 | 0.502 | 0.697 | 0.782 |
| vii | 0.944 | 0.945 | 0.915 | 0.947 | 0.96 |
| viii | 0.721 | 0.637 | 0.916 | 0.966 | 0.978 |
| ix | 0.429 | 0.928 | 0.813 | 0.934 | 0.961 |
| x | 0.126 | 0.398 | 0.117 | 0.519 | 0.519 |
| xi | 0.2 | 0.595 | 0.391 | 0.722 | 0.762 |
| xii | 0.279 | 0.2 | 0.347 | 0.82 | 0.837 |
| Cloud Runtime | Algorithms | ||||
|---|---|---|---|---|---|
| Series (1) | Series (2) | Series (3) | Series (4) | Series (5) | |
| i | 13.96 | 13.13 | 5.12 | 9.55 | 0.13 |
| ii | 36.99 | 35.31 | 5.69 | 43.51 | 0.34 |
| iii | 143.12 | 138.12 | 7.46 | 555.31 | 1.51 |
| iv | 13.06 | 12.38 | 5.93 | 11.93 | 0.54 |
| v | 36.9 | 34.2 | 5.5 | 50.56 | 0.5 |
| vi | 139.05 | 134.09 | 7.02 | 622.71 | 1.19 |
| vii | 10 | 8.93 | 5.15 | 5.6 | 0.11 |
| viii | 36.05 | 34.21 | 5.32 | 46.3 | 0.33 |
| ix | 140 | 135.37 | 6.52 | 552.32 | 1.74 |
| x | 12.74 | 11.94 | 7.97 | 10.52 | 0.12 |
| xi | 48.57 | 45.66 | 8.62 | 74.72 | 0.4 |
| xii | 133.23 | 130.15 | 7.16 | 518.55 | 0.94 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Susanto, H.; Leu, F.-Y.; Caesarendra, W.; Ibrahim, F.; Haghi, P.K.; Khusni, U.; Glowacz, A. Managing Cloud Intelligent Systems over Digital Ecosystems: Revealing Emerging App Technology in the Time of the COVID19 Pandemic. Appl. Syst. Innov. 2020, 3, 37. https://doi.org/10.3390/asi3030037
Susanto H, Leu F-Y, Caesarendra W, Ibrahim F, Haghi PK, Khusni U, Glowacz A. Managing Cloud Intelligent Systems over Digital Ecosystems: Revealing Emerging App Technology in the Time of the COVID19 Pandemic. Applied System Innovation. 2020; 3(3):37. https://doi.org/10.3390/asi3030037
Chicago/Turabian StyleSusanto, Heru, Fang-Yie Leu, Wahyu Caesarendra, Fahmi Ibrahim, Parastou Khodaparast Haghi, Uus Khusni, and Adam Glowacz. 2020. "Managing Cloud Intelligent Systems over Digital Ecosystems: Revealing Emerging App Technology in the Time of the COVID19 Pandemic" Applied System Innovation 3, no. 3: 37. https://doi.org/10.3390/asi3030037





