1. Introduction
UAVs play a critical role in modern warfare. With the increasingly complex and dynamic nature of the battlefield, UAVs are being equipped with diverse functionalities. In addition to traditional scout and attack tasks, modern military UAVs now possess more capabilities such as a communication relay, electronic countermeasures, and damage assessment. In unmanned combat scenarios, multiple tasks may need to be executed against the same target, necessitating the collaboration of heterogeneous platforms. An efficient task assignment algorithm enables rational assignment and orderly execution of combat tasks within a UAV cluster, enhancing overall combat effectiveness and reducing the workload of operators [
1].
Cluster task assignment is a combinatorial optimization problem, and various mathematical models have been proposed to address it, such as Mixed Integer Linear Programming (MILP) [
2,
3], Multiple Traveling Salesmen Problem (MTSP) [
4,
5], Network Flow Optimization (NFO) [
6], Vehicle Routing Problem (VRP) [
7,
8], Cooperative Multiple Task Assignment Problem (CMTAP) [
9,
10], etc. In the context of multi-objective task assignment models, two types of algorithms are commonly used: traditional optimization algorithms and intelligent optimization algorithms. The former mainly includes weight-based methods, constraint-based methods, linear programming methods, etc. However, as the size of the problem or the number of constraints increases, the intelligent optimization algorithms, which have inherent randomness, demonstrate superior solving capability compared with the traditional ones. Intelligent optimization algorithms encompass Evolutionary Algorithms (EA) [
11,
12], Particle Swarm Optimization (PSO) [
13,
14], Genetic Algorithm (GA) [
15], Ant Colony Optimization (ACO) [
16,
17], and others.
When solving the task assignment problem, decision-makers take into account various factors including the total time and total reward required to complete the task; the damage level of the UAV cluster and the range are also involved. This constitutes a multi-objective optimization problem. Many traditional methods attempt to transform this into a single-objective optimization problem, which goes against the nature of multi-objective optimization and conflicts with the inherent feature of uncertainty in the real-world. Traditional methods usually provide decision-makers with a single optimal solution, which heavily relies on the assigned weights for the objective function. However, it is more reasonable to present decision-makers with a set of feasible optimal solutions, considering the uncertainty involved.
Many scholars have made significant improvements to intelligent algorithms for the multi-objective optimization problem. Reference [
18] proposed the Multiple Objective Particle Swarm Optimization (MOPSO) method, which utilizes Pareto dominance to determine the direction of each particle. It sets a global repository of non-dominant vectors, which could be used as the reference of other particles to guide their movements. Reference [
19] introduced the Multi-Objective Evolutionary Algorithm based on Decomposition (MOEA/D), which decomposes a multi-objective optimization problem into several scalar sub-problems and optimizes them simultaneously. For this algorithm, each sub-problem only utilizes information from neighboring sub-problems, which effectively reduces the computational complexity in each generation. Reference [
20] proposed the Multi-Objective Particle Cluster Optimization based on Adaptive Grid Algorithms (AGA-MOPSO). It incorporates an adaptive grid algorithm for evaluating particle density estimation in non-inferior solution sets, along with the AGA-based Pareto optimal solution search technology that maintains a balance between the global and local search capabilities. Reference [
21] advanced the Multi-Objective Particle Swarm Optimization algorithm based on Shared-learning and Dynamic Crowding Distance (MOPSO-SDCD), which incorporates a shared-learning factor to modify the velocity updating equation. The global and local search accuracies are both enhanced. It also maintains external files using a dynamic crowding distance sorting strategy to improve the diversity and distribution of Pareto optimal solutions. Reference [
22] focused on optimizing the total flight distance and mission completion time of UAVs, while also accounting for practical constraints like heterogeneous UAV types and task execution sequences, a collaborative multi-task assignment model for heterogeneous UAVs based on multiple constraints has been developed. The Knee point-based coevolution multi-objective particle swarm optimization (KnCMPSO) algorithm has been introduced to effectively address the described model.
According to the number of task types, the cluster task assignment problems can be categorized into two classes. The first one is the class of single-type task assignment problems (each target has only one task to be executed), and the second one is the class of multi-type task assignment ones (each target has multiple tasks to be executed). This research primarily focuses on the second class. Taking the constraints of assignment, load, task time window, task order, and range into account, a multi-objective optimization model for task assignment was formulated.
In
Section 2, the optimization objectives are set as follows: total task completion time, total task reward, and the level of cluster damage. In
Section 3, the NSGA-II algorithm is improved. The original NSGA-II algorithm utilizes the number of constraint violations (
NumVio) as a measure to determine the non-dominance relationship by comparing the magnitude of
NumVio. However, when faced with a situation where there are numerous constraints with varying degrees of importance like this paper, it is easy for the population to be guided in the wrong direction, resulting in optimization failure. To address this issue, the concept of “constraint tolerance” is proposed to differentiate the impact of different constraints on the non-dominance sorting process. This allows the population to evolve towards satisfying the more important constraints first. In
Section 4, simulation results are compared before and after the algorithm improvement under the same task scale, demonstrating better performance of the proposed algorithm. Additionally, the improved NSGA-II algorithm was also compared with the IMOQQPSO algorithm in the same application scenario, demonstrating the superiority of the enhanced NSGA-II algorithm. The main contributions of this paper are as follows:
A task assignment method based on the NSGA-II algorithm is proposed to tackle the problem of multi-type task assignment with incomplete state information. Furthermore, a new encoding and decoding method specifically for this problem is designed.
Introducing the enhancement of “constraint tolerance” in the NSGA-II algorithm addresses the challenge of converging to Pareto optimal solutions under complex and coupled task constraints. This enhancement enables task assignment results that more effectively meet complex constraint requirements.
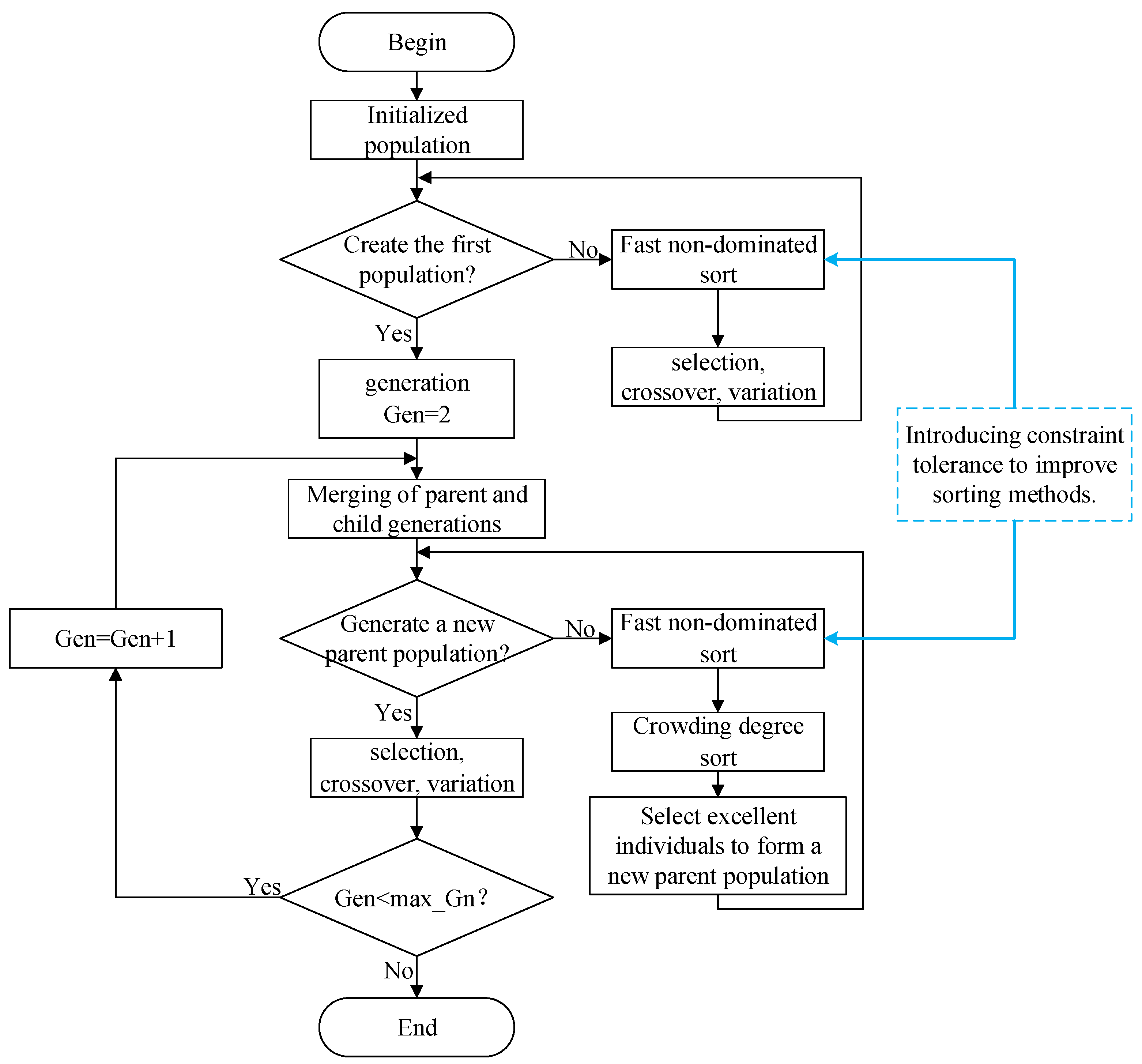
3. Improved NSGA-II Algorithm
The Non-dominated Sorting Genetic Algorithm (NSGA) was proposed by Srinivas and Deb in 1995 [
23]. It is a genetic algorithm based on the concept of Pareto optimality. It performs non-dominated sorting on the population based on the dominance and non-dominance relationships among individuals. The selection operation is then performed based on the results of non-dominated sorting.
In 2002, they further proposed an improved algorithm called NSGA-II, which incorporates an elitist strategy into the non-dominated sorting genetic algorithm [
24]. NSGA-II adopts a fast non-dominated sorting technique to enhance computational speed and robustness. It also introduces “crowding distance” to sort individuals within the same dominance level, promoting a more uniform distribution of non-dominated solutions in the solution space. Moreover, NSGA-II’s fast non-dominated sorting method demonstrates significant computational efficiency advantages when dealing with optimization problems with many constraints, similar to the ones discussed in this paper. The whole process of the algorithm and area for improvement are shown in
Figure 1.
This section outlines the overall workflow of improving the algorithm, the specific improvement principles, and the encoding and decoding methods designed for addressing the multi-type task assignment problem for heterogeneous UAV cluster.
3.1. Improved Non-Dominated Sorting Method
Firstly, introduce the non-dominated sorting method before improvement. In the process of non-dominated sorting, two parameters need to be defined: (1) ni represents the number of individuals in the current population that can dominate individual i, and (2) Si represents the set of individuals in the current population that can be dominated by individual i. The steps are as follows:
① Compare the objective function values of each individual to determine ni and Si for all individuals in the population.
② Find the individuals in the population that are not dominated by any other individual, i.e., individuals with ni = 0. Let k = 0, and put these individuals into set Fk.
③ For each individual in set Fk and its corresponding set Si, for each individual l in Si. Let nl = nl − 1. If nl = 0, store this individual in set H.
④ Assign a non-dominated rank (Rank) to all individuals in set Fk and set Rank = k. Let Fk be referred to as the kth non-dominated set.
⑤ Let k = k + 1, Fk = H, and repeat steps 2–4 until all individuals in the current population are sorted into different ranks.
Non-dominated sorting essentially involves the following steps: Firstly, select the set of individuals in the population that cannot be dominated by any other individual and name this set Rank0. Then, temporarily exclude these individuals from the population and consider the remaining individuals to find the set of individuals that cannot be dominated by any other individual, naming it Rank1. This process is repeated, and all individuals in the population are sorted based on the dominance relationship, resulting in non-dominated ranks for each individual. Lower rank values indicate better solutions.
When determining the dominance relationship between two solutions, the most direct approach is to compare all their objective function values. If one solution performs better than the other in all objective functions, it dominates the other solution. However, comparing all objective function values for all individuals is inefficient. In fast non-dominated sorting, the number of constraint violations (NumVio) is introduced as part of the sorting process. First, the comparison is made based on the magnitude of NumVio, where a solution with a larger NumVio is dominated by a solution with a smaller NumVio. If two solutions have the same NumVio, then the comparison is made based on the objective function values.
In the context of improving NSGA-II in this paper, the determination of NumVio for an individual solution brings in the concept of “constraint tolerance”. This means that different increments in NumVio correspond to violating constraints of different tolerance levels. For example, consider a problem with two constraints, A and B, where Constraint A has a higher tolerance level while Constraint B has a lower tolerance level. If individual solution i violates only Constraint A, then NumVioi = 1. If it violates only Constraint B, then NumVioi = 2. Translating this to the constraints in the problem under study in this paper, time window constraints have a higher tolerance level compared to task sequencing constraints. This means that the system can tolerate some tasks not being completed within the desired time windows but cannot tolerate tasks being executed out of order.
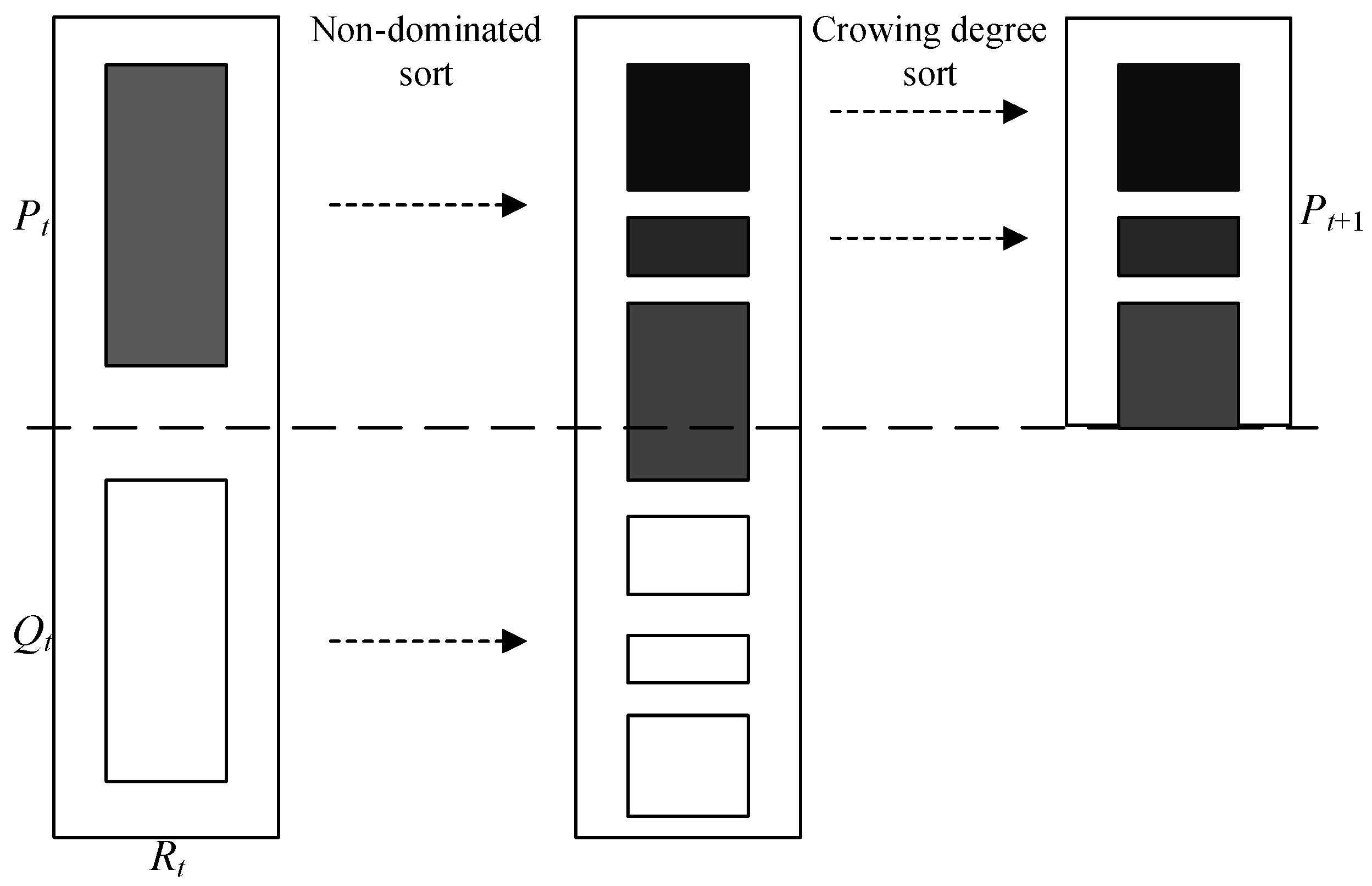
3.2. Elitist Strategy
During each iteration, the parent population
Pt is used to generate the offspring population Q
t through selection, crossover, and mutation operations. The union of individuals from both the parent and offspring populations is denoted as
Rt. Firstly, the merged population
Rt is sorted and divided into ranks using non-dominated sorting. Then, within each rank, individuals are further sorted based on crowding distance. Finally, the top
N individuals from the twice-sorted population
Rt are selected as the new parent population
Pt+1 for the next iteration. This process is illustrated in
Figure 2. By incorporating an elitism strategy, the excellent individuals from each parent population can be preserved.
Since the population size
N is fixed, the selection process first chooses the set of individuals that are not dominated by any other individual, which corresponds to
Rank0. Then, individuals in Rank1, Rank2, Rank3, and so on are selected sequentially. However, it is possible to encounter situations like the one shown in
Figure 2—that is,
To address the issue described above, it is necessary to sort individuals within the same
Rank. Therefore, the concept of “crowding distance”
Di is used to evaluate the quality of individuals within the same rank. It is assumed that when two random individuals are in the same non-dominated rank, the one with a larger crowding distance is considered better than the one with a smaller crowding distance. In comparison to the NSGA algorithm that uses a sharing radius, NSGA-II incorporates the concept of crowding distance. Within the same non-dominated rank, the crowding distance is utilized to assess the density of individuals, promoting a more uniform distribution of non-dominated solutions in the solution space. This eliminates the need for setting a sensitive sharing radius parameter, leading to improved algorithm efficiency and population diversity preservation compared to the NSGA algorithm. The crowding distance is defined as the sum of differences in distances on all sub-objectives between an individual
i and its neighboring individuals
i−1 and
i+1:
3.3. Individual Encoding Method and Generation Method
3.3.1. Individual Encoding and Decoding Rules
The algorithm in this paper uses the form of real number encoding to generate individuals and maps them to the task assignment scheme using multi-layer decoding. The specific coding form is as
Figure 3:
Among them, the elements in the individual are all real numbers in the range of (1,
NU+1).
k is the total number of tasks. Take the scene with
k = 9 as an example; then, the code of an individual is as in
Figure 4:
Taking the decoding of the above individual as an example, the specific process is as in
Figure 5,
Figure 6 and
Figure 7:
Firstly, split the integer part and the decimal part of the element:
Secondly, sort the decimal elements in the second line from small to large, where the sorted number represents the task number Mk; then, according to the belonging variable of task Mk, generate line 3, and based on the type of Mk, generate line 4:
Finally, according to the original position of line 2, line 3 and line 4 are extended and line 2 is deleted. The decoding result is obtained:
Columns 2 and 6 of the above matrix represent the task list for platform 1: task 2 of
T3 and task 1 of
T1. Then, the task assignment results represented by the whole matrix are shown in
Table 4:
3.3.2. Individual Generation Method
Based on the number of tasks
NM, and the number of UAVs
NU, the length of the individual vector is determined as
NM and the range of values for individual elements is (1,
NU + 1). According to the aforementioned encoding and decoding rules, let
x1 = [1, 1, 1, 1, …, 1] and
x2 = (
NU + 1)∙[1, 1, 1, 1, …, 1]. All individuals in the population can be generated according to the following equation, and the population size can be set based on the requirements.
According to the above method, most of the individuals generated in the population do not satisfy the constraints. Originally, five constraints were proposed: assignment constraint, payload constraint, task order constraint, time window constraint, and range constraint. Among them, the assignment constraint is satisfied by the encoding method. The time window and task order constraints are the most difficult to satisfy, and satisfying these two constraints is the goal of the algorithm. Therefore, it is only necessary to improve the individual generation method to satisfy the payload constraint.
The improved individual generation method for the payload constraint is “modify the integer part according to the type of task represented by decimal part”:
① For element “a. xx”, determine the sorting position k of its decimal part “0. xx”.
② By the task type of Mk, the matching relationship with the execution platform represented by the integer part “a” of the element determines how to change the value of “a”. When they do not match, the value of “a” is changed to the number of a random platform matching the task—that is, the task represented by “0. xx” is executed on a new platform. When they match, the value of “a” is not changed.
③ Put the newly formed element “a. xx” back to its original position in the individual.
5. Conclusions
This paper investigates the problem of multi-type task assignment for a cluster of heterogeneous UAVs. The NSGA-II algorithm was improved by introducing the concept of “constraint tolerance” to differentiate the impact of different constraints on the non-dominance sorting process.
In the simulation verification, both the original and improved versions of the NSGA-II algorithm were utilized to address assignment problem characterized by three optimization objectives. The results indicate that the improved NSGA-II algorithm introduces “constraint tolerance”, effectively guiding the population towards evolutionary paths that satisfy constraints under low tolerance levels. This ultimately produces a Pareto solution set where 100% of solutions satisfy all constraints, while the original NSGA-II algorithm yields assignments that violate temporal constraints.
Furthermore, both the improved NSGA-II algorithm and the IMOQPSO algorithm were employed to address assignment problems involving four optimization objective functions. The results indicate that in three objectives, the optimization outcomes of the IMOQPSO algorithm surpassed those of the improved NSGA-II algorithm. However, the assignment results of the IMOQPSO algorithm involve a considerable number of target tasks that are not executed in the prescribed order. In contrast, the optimization results of the improved NSGA-II algorithm strictly adhere to the sequencing constraints for the execution of each target task set in all assignment schemes and ultimately outperform the IMOQPSO algorithm by 7% in Total Task Reward.