A Review on Communications Perspective of Flying Ad-Hoc Networks: Key Enabling Wireless Technologies, Applications, Challenges and Open Research Topics
Abstract
:1. Introduction
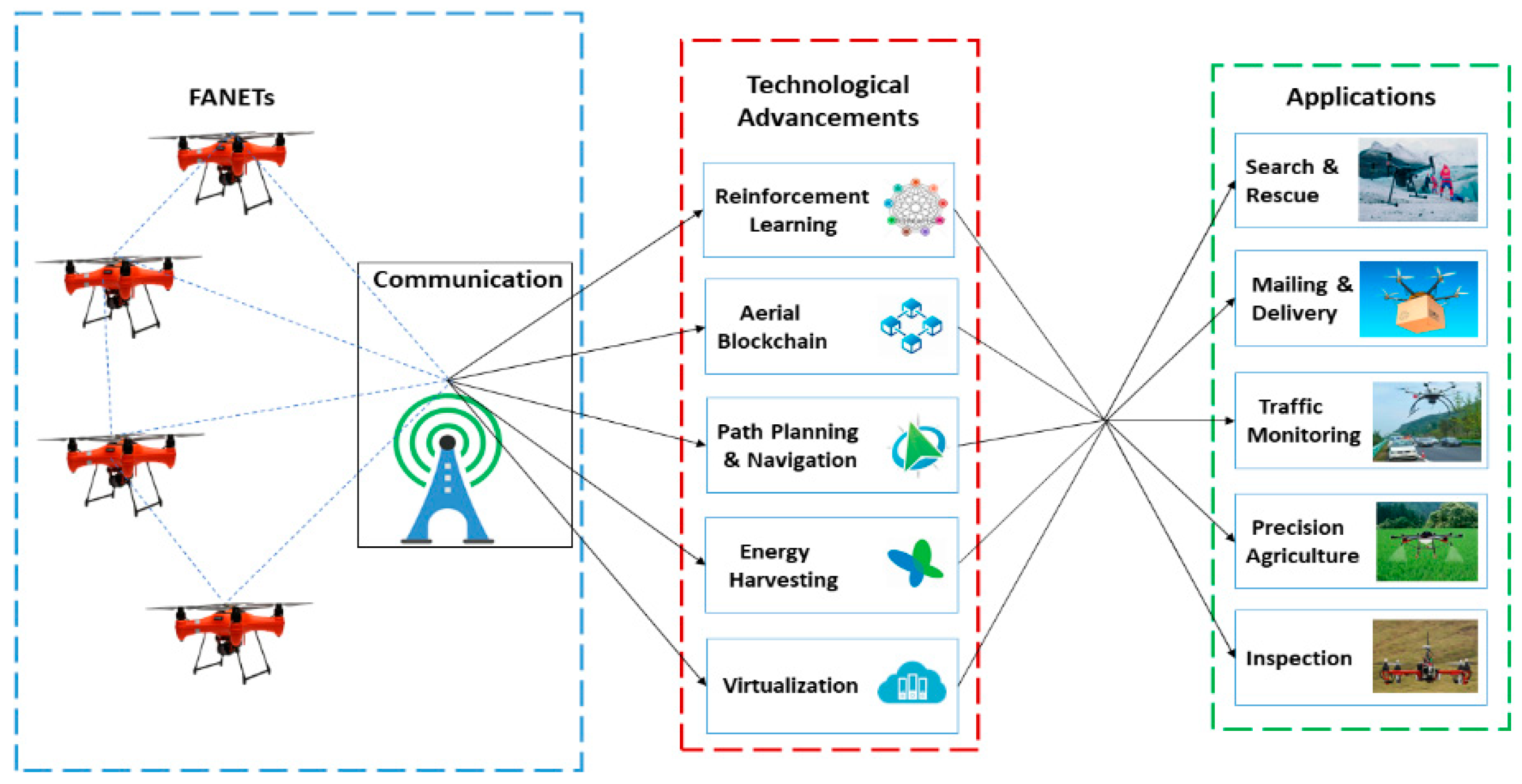
2. Key Enabling Wireless Technologies
3. Applications and Feasibility of the Wireless Technologies
3.1. Search and Rescue (SAR)
3.2. Mailing and Delivery
3.3. Traffic Monitoring
3.4. Precision Agriculture
3.5. Reconnaissance
4. Challenges
4.1. Security and Privacy
4.2. Safety
4.3. Energy Limitations
4.4. Storage and Computation Restrictions
4.5. Routing
4.6. Path Planning and Navigation
5. Open Research Topics
5.1. Aerial Blockchain
5.2. High-Speed Backhaul Connectivity
5.3. Deep Reinforcement Learning
5.4. Energy Harvesting Technologies
5.5. Virtualization of Unmanned Aerial Vehicles (UAV)-Enabled 5G Networks
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| UAV | Unmanned Aerial Vehicle |
| FANETs | Flying Ad-Hoc Networks |
| IMU | Inertial Measurement Unit |
| GPS | Global Positioning System |
| BS | Base Station |
| FSO | Free Space Optics |
| DSE | Decision Support Engine |
| NDVI | Normalized Vegetation Difference Index |
| 6G | Sixth-Generation |
| B5G | Beyond Fifth-Generation |
| mmWave | Millimeter Wave |
| SAR | Search and Rescue |
| LPWAN | Low-Power Wide Area Networks |
| MEC | Multi-Access Edge Computing |
References
- Shakoor, S.; Kaleem, Z.; Baig, M.I.; Chughtai, O.; Duong, T.Q.; Nguyen, L.D. Role of UAVs in Public Safety Communications: Energy Efficiency Perspective. IEEE Access 2019, 7, 140665–140679. [Google Scholar] [CrossRef]
- Yanmaz, E.; Yahyanejad, S.; Rinner, B.; Hellwagner, H.; Bettstetter, C. Drone networks: Communications, coordination, and sensing. Ad Hoc Netw. 2018, 68, 1–15. [Google Scholar] [CrossRef]
- Sharma, V. Advances in Drone Communications, State-of-the-Art and Architectures. Drones 2019, 3, 21. [Google Scholar] [CrossRef] [Green Version]
- Oubbati, O.S.; Atiquzzaman, M.; Lorenz, P.; Tareque, M.H.; Hossain, M.S. Routing in Flying Ad Hoc Networks: Survey, Constraints, and Future Challenge Perspectives. IEEE Access 2019, 7, 81057–81105. [Google Scholar] [CrossRef]
- Guillen-Perez, A.; Cano, M.-D. Flying Ad Hoc Networks: A New Domain for Network Communications. Sensors 2018, 18, 3571. [Google Scholar] [CrossRef] [Green Version]
- Khan, M.A.; Qureshi, I.M.; Khanzada, F. A Hybrid Communication Scheme for Efficient and Low-Cost Deployment of Future Flying Ad-Hoc Network (FANET). Drones 2019, 3, 16. [Google Scholar] [CrossRef] [Green Version]
- Khan, M.A.; Khalid, A.; Khanzada, F. Dual-Radio Dual-Band Configuration for Flexible Communication in Flying Ad-hoc Networks (FANET). In Proceedings of the International Conference on Communication Technologies (ComTech’2019), Rawalpindi, Pakistan, 20–21 March 2019. [Google Scholar]
- Marchese, M.; Moheddine, A.; Patrone, F. IoT and UAV Integration in 5G Hybrid Terrestrial-Satellite Networks. Sensors 2019, 19, 3704. [Google Scholar] [CrossRef] [Green Version]
- Saad, W.; Bennis, M.; Chen, M. A Vision of 6G Wireless Systems: Applications, Trends, Technologies, and Open Research Problems. arXiv 2019, arXiv:1902.10265. [Google Scholar] [CrossRef] [Green Version]
- Lin, C.; He, D.; Kumar, N.; Choo, K.-K.R.; Vinel, A.; Huang, X. Security and Privacy for the Internet of Drones: Challenges and Solutions. IEEE Commun. Mag. 2018, 56, 64–69. [Google Scholar] [CrossRef]
- Zhi, Y.; Fu, Z.; Sun, X.; Yu, J. Security and Privacy Issues of UAV: A Survey. Mobile Netw. Appl. 2019, 25, 95–101. [Google Scholar] [CrossRef]
- Hassanalian, M.; Abdelkefi, A. Classifications, applications, and design challenges of drones: A review. Prog. Aerosp. Sci. 2017, 91, 99–131. [Google Scholar] [CrossRef]
- Sharma, A.; Vanjani, P.; Paliwal, N.; Basnayaka, C.M.W.; Jayakody, U.N.K.; Wang, H.-C.; Muthuchidambaranathan, P. Communication and networking technologies for UAVs: A survey. J. Netw. Comput. Appl. 2020, 168, 02739. [Google Scholar] [CrossRef]
- Zhang, S.; Zhang, H.; Song, L. Beyond D2D: Full Dimension UAV-to-Everything Communications in 6G. IEEE Trans. Veh. Technol. 2020, 69, 6592–6602. [Google Scholar] [CrossRef] [Green Version]
- Van den Bergh, B.; Chiumento, A.; Pollin, S. Ultra-Reliable IEEE 802.11 for UAV Video Streaming: From Network to Application. In Advances in Ubiquitous Networking 2. UNet 2016; El-Azouzi, R., Menasche, D., Sabir, E., De Pellegrini, F., Benjillali, M., Eds.; Lecture Notes in Electrical Engineering; Springer: Singapore, 2016; Volume 397. [Google Scholar]
- Bluetooth Core Specification, Bluetooth Special Interest Group (SIG). 2016. Available online: https://www.bluetooth.com/specifications/bluetooth-core-specification (accessed on 1 September 2020).
- Sharma, V.; You, I.; Pau, G.; Collotta, M.; Lim, J.D.; Kim, J.N. LoRaWAN-Based Energy-Efficient Surveillance by Drones for Intelligent Transportation Systems. Energies 2018, 11, 573. [Google Scholar] [CrossRef] [Green Version]
- Neumann, P.; Montavont, J.; Noël, T. Indoor deployment of low-power wide area networks (LPWAN): A LoRaWAN case study. In Proceedings of the 2016 IEEE 12th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), New York, NY, USA, 17–19 October 2016; pp. 1–8. [Google Scholar]
- Bardyn, J.P.; Melly, T.; Seller, O.; Sornin, N. IoT: The era of LPWAN is starting now. In Proceedings of the 42nd European Solid-State Circuits Conference (ESSCIRC Conference 2016), Lausanne, Switzerland, 12–15 September 2016; pp. 25–30. [Google Scholar]
- Sanchez-Iborra, R.; Gamez, J.S.; Santa, J.; Fernandez, P.J.; Skarmeta, A.F. Integrating LP-WAN Communications within the Vehicular Ecosystem. J. Internet Serv. Inf. Secur. 2017, 7, 45–56. [Google Scholar]
- Garcia, D.; Marin, R.; Kandasamy, A.; Pelov, A. LoRaWAN Authentication in RADIUS Draft-Garcia-RadextRadius-Lorawan-03. 2 May 2017. Available online: https://www.ietf.org/archive/id/draft-garcia-radextradius-lorawan-03.txt (accessed on 26 December 2017).
- Garcia, D.; Marin, R.; Kandasamy, A.; Pelov, A. LoRaWAN Authentication in Diameter Draft-Garcia-DimeDiameter-Lorawan-00. 30 May 2016. Available online: https://tools.ietf.org/html/draft-garcia-dimediameter-lorawan-00 (accessed on 26 December 2017).
- LoRa Alliance Technology. Available online: https://www.lora-alliance.org/technology (accessed on 25 January 2018).
- Casals, L.; Mir, B.; Vidal, R.; Gomez, C. Modeling the Energy Performance of LoRaWAN. Sensors 2017, 17, 2364. [Google Scholar] [CrossRef] [Green Version]
- Naoui, S.; Elhdhili, M.E.; Saidane, L.A. Enhancing the security of the IoT LoraWAN architecture. In Proceedings of the International Conference on Performance Evaluation and Modeling in Wired and Wireless Networks (PEMWN), Paris, France, 22–25 November 2016; pp. 1–7. [Google Scholar]
- Sornin, N.; Luis, M.; Eirich, T.; Kramp, T.; Hersent, O. LoRaWAN Specification V1.0.2; Technical Report; LoRa Alliance: Beaverton, OR, USA, 2016. [Google Scholar]
- Mozaffari, M.; Saad, W.; Bennis, M.; Nam, Y.; Debbah, M. A tutorial on UAVs for wireless networks: Applications, challenges, and open problems. IEEE Commun. Surv. Tutor. 2019, 21, 2334–2360. [Google Scholar] [CrossRef] [Green Version]
- Hayat, S.; Yanmaz, E.; Muzaffar, M. Survey on unmanned aerial vehicle networks for civil applications: A communications viewpoint. IEEE Commun. Surveys Tutor. 2016, 18, 2624–2661. [Google Scholar] [CrossRef]
- Półka, M.; Ptak, S.; Kuziora, Ł. The use of UAV’s for search and rescue operations. Procedia Eng. 2017, 192, 748–752. [Google Scholar] [CrossRef]
- Zafar, W.; Khan, B.M. Flying Ad-Hoc Networks: Technological and Social Implications. IEEE Technol. Soc. Mag. 2016, 35, 67–74. [Google Scholar] [CrossRef]
- Allmer, T.; Fuchs, C.; Kreilinger, V.; Sevignani, S. Social networking sites in the surveillance society. In Media, Surveillance, and Identity: Social Perspectives; Jansson, A., Christensen, M., Eds.; Peter Lang: New York, NY, USA, 2014; pp. 49–70. [Google Scholar]
- Alsaeedy, A.A.R.; Chong, E.K.P. 5G and UAVs for Mission-Critical Communications: Swift Network Recovery for Search-and-Rescue Operations. Mob. Netw. Appl. 2020, 1–19. [Google Scholar] [CrossRef]
- Gharibi, M.; Boutaba, R.; Waslander, S.L. Internet of drones. IEEE Access 2016, 4, 1148–1162. [Google Scholar] [CrossRef]
- Gross, D. Amazon’s Drone Delivery: How Would it Work? 2013. Available online: http://www.cnn.com/2013/12/02/tech/innovation/amazondrones-questions/ (accessed on 14 August 2020).
- FedEx Corporation. Q1 Fiscal 2015 Statistics. 2015. Available online: http://investors.fedex.com/files/docdownloads/statistical/FedEx-Q1-FY15-Stat-Bookv001t195uu.pdf (accessed on 14 August 2020).
- Khan, M.A.; Alvi, B.A.; Safi, A.; Khan, I.U. Drones for Good in Smart Cities: A Review. In Proceedings of the International Conference on Electrical, Electronics, Computers, Communication, Mechanical and Computing (EECCMC), Tamil Nadu, India, 28–29 January 2018. [Google Scholar]
- Ke, R.; Li, Z.; Kim, S.; Ash, J.; Cui, Z.; Wang, Y. Real-time bidirectional traffic flow parameter estimation from aerial videos. IEEE Trans. Intell. Transp. Syst. 2017, 18, 890–901. [Google Scholar] [CrossRef]
- Guido, G.; Gallelli, V.; Rogano, D.; Vitale, A. Evaluating the accuracy of vehicle tracking data obtained from unmanned aerial vehicles. Int. J. Transp. Sci. Technol. 2016, 5, 136–151. [Google Scholar] [CrossRef]
- Leitloff, J.; Rosenbaum, D.; Kurz, F.; Meynberg, O.; Reinartz, P. An operational system for estimating road traffic information from aerial images. Remote Sens. 2014, 6, 11315–11341. [Google Scholar] [CrossRef] [Green Version]
- Tsouros, D.C.; Bibi, S.; Sarigiannidis, P.G. A review on UAV-based applications for precision agriculture. Information 2019, 10, 349. [Google Scholar] [CrossRef] [Green Version]
- Shafi, U.; Mumtaz, R.; García-Nieto, J.; Hassan, S.A.; Zaidi, S.; Iqbal, N. Precision Agriculture Techniques and Practices: From Considerations to Applications. Sensors 2019, 19, 3796. [Google Scholar] [CrossRef] [Green Version]
- Berrahal, S.; Kim, J.H.; Rekhis, S.; Boudriga, N.; Wilkins, D.; Acevedo, J. Border Surveillance Monitoring Using Quadcopter UAV-Aided Wireless Sensor Networks. J. Commun. Softw. Syst. 2016, 12, 67–82. [Google Scholar] [CrossRef]
- Zeng, Y.; Zhang, R.; Lim, T.J. Wireless communications with unmanned aerial vehicles: Opportunities and challenges. IEEE Commun. Mag. 2016, 54, 36–42. [Google Scholar] [CrossRef] [Green Version]
- Hooper, M.; Tian, Y.; Zhou, R.; Cao, B.; Lauf, A.P.; Watkins, L.; Robinson, W.H.; Alexis, W. Securing commercial Wi-Fi-based UAVs from common security attacks. In Proceedings of the Military Communications Conference, Baltimore, MD, USA, 1–3 November 2016. [Google Scholar]
- Khan, M.A.; Ullah, I.; Nisar, S.; Noor, F.; Qureshi, I.M.; Khanzada, F.; Khattak, H.; Aziz, M.A. Multi-access Edge Computing (MEC) Enabled Flying Ad-hoc Networks with Secure Deployment Using Identity Based Generalized Signcryption. Mob. Inf. Syst. 2020, 2020, 8861947. [Google Scholar]
- Khan, M.A.; Ullah, I.; Qureshi, I.M.; Noor, F.; Khanzada, F. An Efficient and Provably Secure Certificateless Key-Encapsulated Signcryption Scheme for Flying Ad-Hoc Network. IEEE Access 2020, 8, 36807–36828. [Google Scholar] [CrossRef]
- Khan, M.A.; Qureshi, I.M.; Ullah, I.; Khan, S.; Khanzada, F.; Noor, F. An Efficient and Provably Secure Certificateless Blind Signature Scheme for Flying Ad-Hoc Network Based on Multi-Access Edge Computing. Electronics 2020, 9, 30. [Google Scholar] [CrossRef] [Green Version]
- Jiang, B.; Yang, J.; Song, H. Protecting Privacy From Aerial photography: State of the Art, Opportunities, and Challenges. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; pp. 799–804. [Google Scholar]
- Guo, Y.; Wu, M.; Tang, K.; Tie, J.; Li, X. Covert Spoofing Algorithm of UAV Based on GPS/INS-Integrated Navigation. IEEE Trans. Veh. Technol. 2019, 68, 6557–6564. [Google Scholar] [CrossRef]
- Eldosouky, A.; Ferdowsi, A.; Saad, W. Drones in Distress: A Game-Theoretic Countermeasure for Protecting UAVs Against GPS Spoofing. IEEE Internet Things J. 2020, 7, 2840–2854. [Google Scholar] [CrossRef] [Green Version]
- Krishna, C.G.L.; Murphy, R.R. A review on cybersecurity vulnerabilities for unmanned aerial vehicles. In Proceedings of the 2017 IEEE International Symposium on Safety, Security and Rescue Robotics (SSRR), Shanghai, China, 11–13 October 2017; pp. 194–199. [Google Scholar]
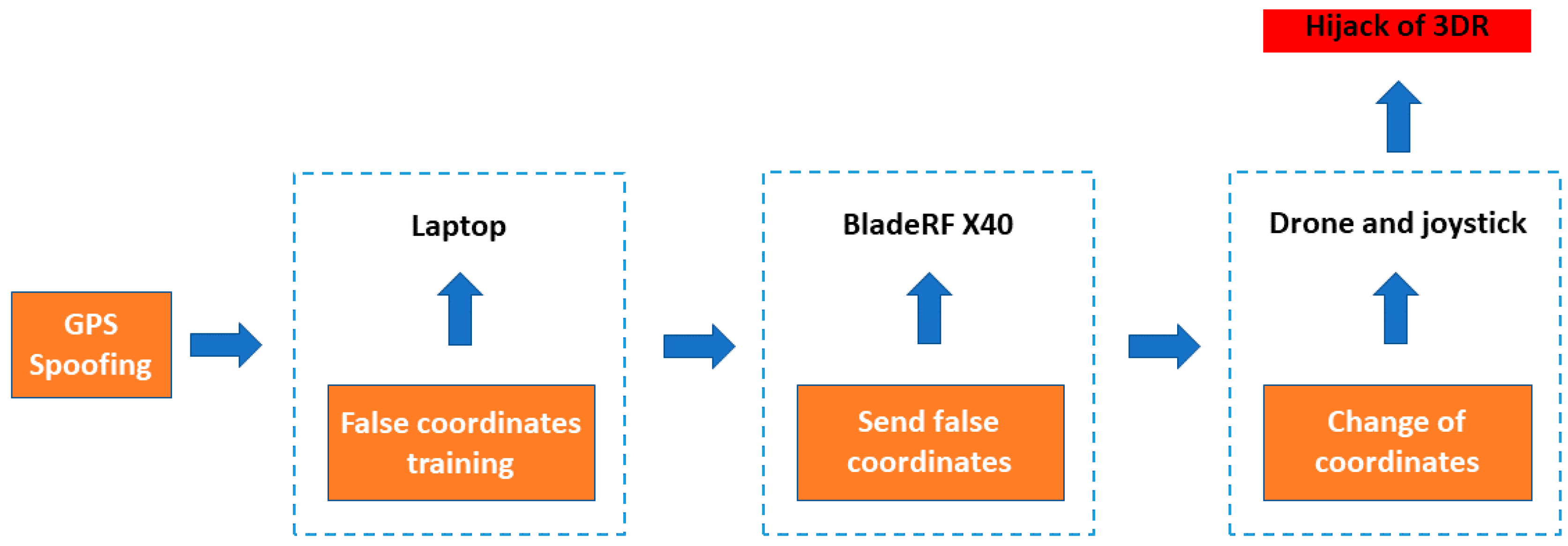
- Arteaga, S.P.; Hernández, L.A.M.; Pérez, G.S.; Orozco, A.L.S.; Villalba, L.J.G. Analysis of the GPS Spoofing Vulnerability in the Drone 3DR Solo. IEEE Access 2019, 7, 51782–51789. [Google Scholar] [CrossRef]
- Feng, Z.; Guan, N.; Lv, M.; Liu, W.; Deng, Q.; Liu, X.; Yi, W. Efficient drone hijacking detection using onboard motion sensors. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Lausanne, Switzerland, 27–31 March 2017; pp. 1414–1419. [Google Scholar]
- Wang, J. Counter-Unmanned Aircraft System(s) (C-UAS): State of the Art, Challenges and Future Trends. arXiv 2020, arXiv:2008.12461. [Google Scholar]
- Kerns, A.J.; Shepard, D.P.; Bhatti, J.A.; Humphreys, T.E. Unmanned aircraft capture and control via GPS spoofing. J. Field Robot. 2014, 31, 617–636. [Google Scholar] [CrossRef]
- Kang, W.C.; Aimin, S.P. Time and position spoong with open source projects. Proc. Black Hat Eur. 2015, 148, 1–8. [Google Scholar]
- Fotouhi, A.; Qiang, H.; Ding, M.; Hassan, M.; Giordano, L.G.; Garcia-Rodriguez, A.; Yuan, J. Survey on UAV cellular communications: Practical aspects, standardization advancements, regulation, and security challenges. IEEE Commun. Surv. Tutor. 2019, 21, 3417–3442. [Google Scholar] [CrossRef] [Green Version]
- Bolkcom, C.; Bone, E. Unmanned aerial vehicles: Background and issues for congress, report for congress, congressional research service. In Library of Congress; UNT Digital Library: Washington, DC, USA, 2003. [Google Scholar]
- Li, B.; Fei, Z.; Zhang, Y. UAV communications for 5G and beyond: Recent advances and future trends. IEEE Internet Things J. 2018, 6, 2241–2263. [Google Scholar] [CrossRef] [Green Version]
- Sang, Q.; Wu, H.; Xing, L.; Xie, P. Review and Comparison of Emerging Routing Protocols in Flying Ad Hoc Networks. Symmetry 2020, 12, 971. [Google Scholar] [CrossRef]
- Khan, M.A.; Khan, I.U.; Safi, A.; Quershi, I.M. Dynamic Routing in Flying Ad-Hoc Networks Using Topology-Based Routing Protocols. Drones 2018, 2, 27. [Google Scholar] [CrossRef] [Green Version]
- Lakew, D.S.; Sa’ad, U.; Dao, N.-N.; Na, W.; Cho, S. Routing in Flying Ad Hoc Networks: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2020, 22, 1071–1120. [Google Scholar] [CrossRef]
- Khan, M.A.; Qureshi, I.M.; Safi, A.; Khan, I.U. Flying Ad-Hoc Networks (FANETs): A Review of Communication architectures, and Routing protocols. In Proceedings of the 2017 First International Conference on Latest Trends in Electrical Engineering and Computing Technologies (INTELLECT), Karachi, Pakistan, 15–16 November 2017; pp. 692–699. [Google Scholar]
- Ashraf, A.; Majd, A.; Troubitsyna, E. Online Path Generation and Navigation for Swarms of UAVs. Sci. Program. 2020, 2020, 8530763. [Google Scholar] [CrossRef]
- Li, B.; Fei, Z.; Zhang, Y.; Guizani, M. Secure UAV communication networks over 5G. IEEE Wirel. Commun. 2019, 26, 114–120. [Google Scholar] [CrossRef]
- Mehta, P.; Gupta, R.; Tanwar, S. Blockchain envisioned UAV networks: Challenges, solutions, and comparisons. Comput. Commun. 2020, 151, 518–538. [Google Scholar] [CrossRef]
- Kumari, A.; Gupta, R.; Tanwar, S.; Kumar, N. A taxonomy of blockchain-enabled softwarization for secure UAV network. Comput. Commun. 2020, 161, 304–323. [Google Scholar] [CrossRef]
- Chowdhury, M.Z.; Shahjalal, M.; Ahmed, S.; Jang, Y.M. 6G Wireless Communication Systems: Applications, Requirements, Technologies, Challenges, and Research Directions. arXiv 2019, arXiv:1909.11315. [Google Scholar] [CrossRef]
- Chen, Y.; Lin, X.; Khan, T.; Mozaffari, M. Efficient Drone Mobility Support Using Reinforcement Learning. In Proceedings of the 2020 IEEE Wireless Communications and Networking Conference (WCNC), Seoul, Korea, 25–28 May 2020; pp. 1–6. [Google Scholar]
- Challita, U.; Saad, W.; Bettstetter, C. Deep Reinforcement Learning for Interference-Aware Path Planning of Cellular-Connected UAVs. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–7. [Google Scholar]
- Liu, Q.; Shi, L.; Sun, L.; Li, J.; Ding, M.; Shu, F. Path Planning for UAV-Mounted Mobile Edge Computing With Deep Reinforcement Learning. IEEE Trans. Veh. Technol. 2020, 69, 5723–5728. [Google Scholar] [CrossRef] [Green Version]
- Liu, Q.; Li, M.; Yang, J.; Lv, J.; Hwang, J.; Hossain, A.S.; Muhammad, G. Joint power and time allocation in energy harvesting of UAV operating system. Comput. Commun. 2020, 150, 811–817. [Google Scholar] [CrossRef]
- Sekander, S.; Tabassum, H.; Hossain, E. Multi-tier drone architecture for 5G/B5G cellular networks: Challenges, trends, and prospects. IEEE Commun. Mag. 2018, 56, 96–103. [Google Scholar] [CrossRef] [Green Version]

| Communication Technology | Standard/Service Category | Spectrum Type | Frequency/Medium | Device Mobility | Theoretical Data Rate | Range Indoor-Outdoor | Latency |
|---|---|---|---|---|---|---|---|
| Wi-Fi | 802.11 | Unlicensed | 2.4 GHz IR | Yes | Up to 2 Mbps | 20–100 m | <5 ms |
| 802.11a | Unlicensed | 5 GHz | Yes | Up to 54 Mbps | 35–120 m | ||
| 802.11b | Unlicensed | 2.4 GHz | Yes | Up to 11 Mbps | 35–140 m | ||
| 802.11n | Unlicensed | 2.4/5 GHz | Yes | Up to 600 Mbps | 70–250 m | ||
| 802.11g | Unlicensed | 2.4 GHz | Yes | Up to 54 Mbps | 38–140 m | ||
| 802.11ac | Unlicensed | 5 GHz | Yes | Up to 866.7 Mbps | 35–120 m | ||
| ZigBee | 802.15.4 | Unlicensed | 2.4 GHz | Yes | Up to 25 kbps | 10–100 m | 15 ms |
| Bluetooth V5 | 802.15.1 | Unlicensed | 2.4 GHz | Yes | Up to 2 Mbps | 10–200 m | 3 ms |
| LoRaWAN | IEEE 802.15.4g | Unlicensed | 868 MHz, 915 MHz | Yes | Up to 50 kbps | 05–15 km | Device Class Dependent |
| Sigfox | - | Unlicensed | 868 MHz, 902 MHz | Yes | Up to 100 bps | 03–30 km | 2 s |
| NB-IoT |
| licensed | 200 KHz | Yes | Up to 250 kbps | 10–35 km | 1.6–10 s |
| 5G |
| licensed |
| Yes | Up to 1 Gbps | Wide Area | 1 ms |
| B5G |
| licensed |
| Yes | Up to 100 Gbps | Wide Area | 1 ms |
| 6G |
| licensed |
| Yes | Up to 1 Tbps | Wide Area | <1 ms |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Noor, F.; Khan, M.A.; Al-Zahrani, A.; Ullah, I.; Al-Dhlan, K.A. A Review on Communications Perspective of Flying Ad-Hoc Networks: Key Enabling Wireless Technologies, Applications, Challenges and Open Research Topics. Drones 2020, 4, 65. https://doi.org/10.3390/drones4040065
Noor F, Khan MA, Al-Zahrani A, Ullah I, Al-Dhlan KA. A Review on Communications Perspective of Flying Ad-Hoc Networks: Key Enabling Wireless Technologies, Applications, Challenges and Open Research Topics. Drones. 2020; 4(4):65. https://doi.org/10.3390/drones4040065
Chicago/Turabian StyleNoor, Fazal, Muhammad Asghar Khan, Ali Al-Zahrani, Insaf Ullah, and Kawther A. Al-Dhlan. 2020. "A Review on Communications Perspective of Flying Ad-Hoc Networks: Key Enabling Wireless Technologies, Applications, Challenges and Open Research Topics" Drones 4, no. 4: 65. https://doi.org/10.3390/drones4040065






